Critical Vulnerability in Adobe Reader and Acrobat
Adobe has issued a security advisory warning about a “critical vulnerability” in all fully patched versions of Adobe Reader 9 and earlier, and in Adobe Acrobat 9 and earlier. Although the security advisory makes no specific mention of the Mac, previous vulnerabilities have been cross-platform, so there’s no reason to believe this one will be any different. Adobe expects to issue an update for the latest versions of Adobe Reader and Acrobat by 11-Mar-09.
Details of the vulnerability? A malicious PDF could cause the affected application to crash and could potentially allow an attacker to take control of the computer. I know that’s what we always say, but in this case, there are reports of this vulnerability being exploited in the wild, at least in the Windows world.
Luckily, the security group Shadowserver has verified the exploit with Adobe Reader 8 and 9 on Windows. Their posting explains that the vulnerability relies in part on JavaScript, such that turning off JavaScript is an easy way to mitigate the problem. In their testing, a malicious PDF could still crash Adobe Reader if JavaScript was turned off, but it couldn’t take over the machine.
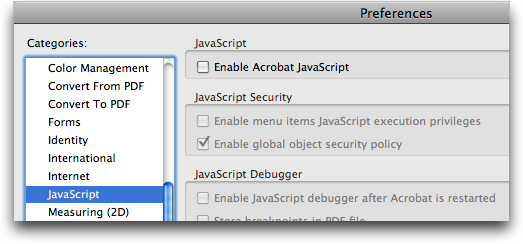
To disable JavaScript, deselect the Enable Acrobat JavaScript checkbox in the JavaScript pane of Adobe Reader’s and Acrobat’s preferences.
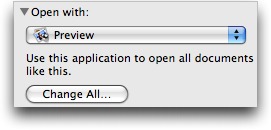
Since Apple’s Preview and most, if not all, other Mac OS X PDF readers cannot interpret JavaScript in a PDF, I suspect that they would be unaffected by a malicious PDF. To change the default so all PDFs open with Preview, choose File > Get Info (Command-I) for any PDF, choose Preview from the Open With pop-up menu, and click the Change All button.
It’s distressing that Adobe’s security advisory provides no practical information that would help users protect themselves until an update appears. Aside from the lack of platform-specific detail, would it have killed Adobe to suggest that users turn off JavaScript and avoid PDF files from dodgy sites?