Update Immediately to Block the Root Vulnerability Bug
[Update: Enough has changed since we initially wrote this article that we’ve now published a replacement that provides current information. Read it at “Apple Pushes Updates to Block the Root Vulnerability Bug” (30 November 2017). -Adam]
As I predicted in “High Sierra Bug Provides Full Root Access” (28 November 2017), Apple quickly released Security Update 2017-001 to address the root vulnerability bug that enabled anyone to gain admin access without a password. I’ve installed it and confirmed that it works as advertised.
Everyone running macOS 10.13.1 High Sierra should install this security update via Software Update immediately. It does not require a restart. I know that we usually recommend caution when it comes to installing updates, but this vulnerability is so severe that the fix is more important than any trouble it could conceivably cause. That said, make sure you have a backup!
Starting later today, Apple will automatically push this security update to all Macs running High Sierra 10.13.1. If, for some reason, you haven’t updated from 10.13.0 to 10.13.1, we recommend doing that too. 10.13.0 suffers from the bug as well, but the security update is only for 10.13.1.
If you need a standalone installer for Security Update 2017-001 for some reason, Apple has now made such a download available.
Although the community identified the primary attack vectors yesterday, it’s possible that there are others that are not blocked by changing the root password or disabling remote access. We have to assume that black hat hackers are already probing every possible area where this bug could provide access. That’s why it’s entirely reasonable for Apple to push the security update to all systems.
In a statement to John Gruber of Daring Fireball, Apple said:
Security is a top priority for every Apple product, and regrettably we stumbled with this release of macOS.
When our security engineers became aware of the issue Tuesday afternoon, we immediately began working on an update that closes the security hole. This morning, as of 8:00 a.m., the update is available for download, and starting later today it will be automatically installed on all systems running the latest version (10.13.1) of macOS High Sierra.
We greatly regret this error and we apologize to all Mac users, both for releasing with this vulnerability and for the concern it has caused. Our customers deserve better. We are auditing our development processes to help prevent this from happening again.
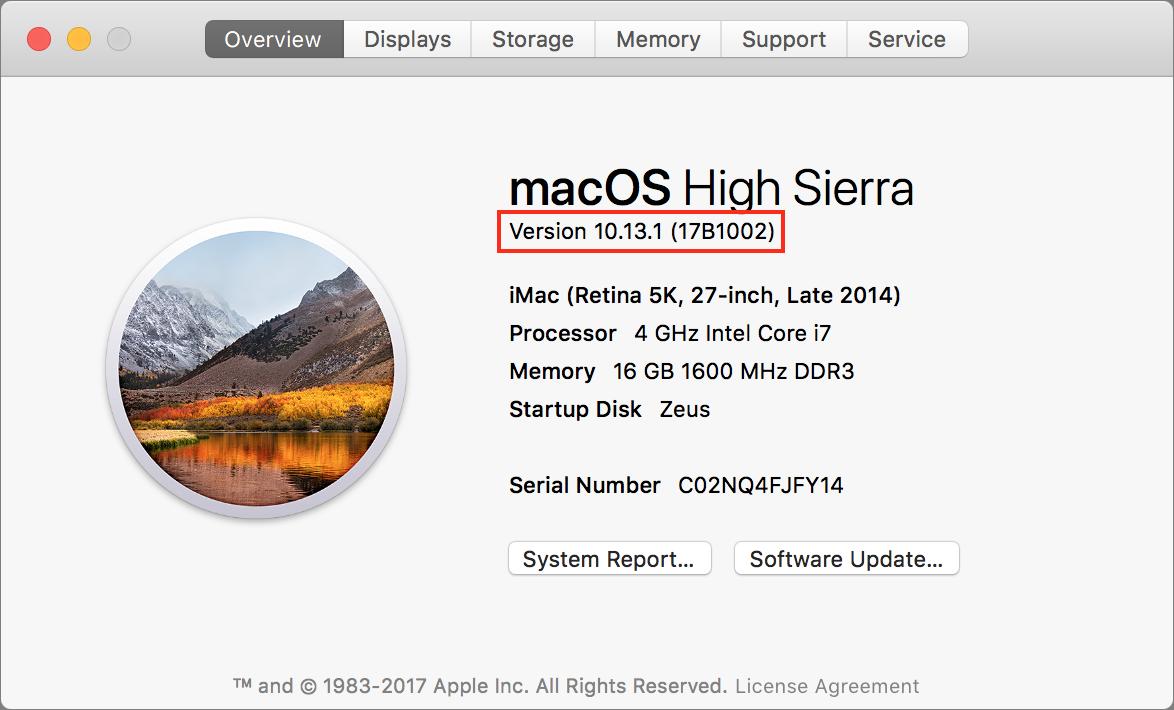
Apple notes that after installation, the build number of macOS will be 17B1002. To verify that number, choose > About This Mac and click the Version 10.13.1 line.
If you have a legitimate use for the root user account on your Mac, you’ll need to reenable it and change its password in Directory Utility after installing the update. Hardly anyone should have to do this.
Apple deserves credit for releasing this security update in less than 24 hours after the bug was publicized on Twitter. That quick reaction time is reassuring, even though I’m sure many developers, testers, and deployment teams at Apple had a truly awful day yesterday.
But the fact that Apple could introduce a security hole the size of a truck into High Sierra is appalling. Ensuring that unauthorized users can’t act as the root user in a Unix system is basic security, because anyone who can become root can do anything they want. That the vulnerability escaped notice in Apple’s security testing is almost worse than the vulnerability itself.
And yes, if you’ve been waiting to upgrade to High Sierra, pat yourself on the back. 10.12 Sierra and earlier versions of OS X don’t suffer from this bug.
Note that the update is not in the Version 5 10.13.2 Beta (I installed it last night). If you have that Beta installed, follow the previous instructions to manually enable the root user.
Just got your email. So switched Mac on - (i had switched it off when I heard about the bug - I don't use it as much these day - ) and installed it. It says installed, but I do not have the Build No at all on my About Me. I trust that isn't a problem. My imac is a 27" mid 2010 always been updated as new OS come out.
In the "About this Mac" click on the version number (ie 10.13.1) and it should show the build number.
Checking the build number in the way suggested here tends to cause some confusion since it requires an extra click to reveal hidden information. A straightforward alternative is
System Profiler > Software > System Version
(the build is indicated in parentheses after the OS version no.)
By the way, for those who prefer to access System Profiler in a quick way rather than going to /Applications/Utilities, an option click on
Apple Menu > About this Mac
will bring it right up.
The cynic in me can’t help but think that something like this wouldn’t have happened if Apple’s focus was truly on the Mac. I mean, come on, guys, we've had a UNIX-based Mac OS for years now—and securing the root user, that's very basic stuff.
Since this bug didn’t exist on regular Sierra, I’d have to assume something regarding the security system was changed...and they wouldn’t test the root user? Really?
I get it—Apple's focus has moved on to iOS and iOS devices. It makes sense. But there still is a Mac community out there that cares about the Mac, and at a certain point, I kind of wish Apple would just open-source the Mac OS and let said community help maintain it.
I have to agree with that.
How many developers does Apple have testing beta versions? How many public beta testers do they have? And something as blatant as this simply falls off the radar? WTH???
Apple's QC has gone down the drain and quite obviously they have lost interest in macOS, or at the very least they simply don't care about the quality of their macOS releases. But let's all hail marketing: a major new release has to ship once a year, quality be damned.
I sure miss Steve and his Apple.
"The cynic in me can’t help but think that something like this wouldn’t have happened if Apple’s focus was truly on the Mac. "
Apple's always had show stopper bugs, even when it was doing nothing but Mac.
So apparently Apple's patch for yesterday's blunder broke File Sharing thereby becoming today's blunder. Awesome week Apple's having.
There's a fix here:
https://www.macrumors.com/2017/11/29/apple-macos-high-sierra-file-sharing-fix
Today the HS system I patched yesterday is offering another security update. I have no idea why there are two patches and as usual Apple's terse release notes shed no light on the matter. In fact, according to Apple there's only one update AFAICT.
So yesterday I installed "Security Update 2017-001" which updated my build to 17B1002.
Today I was prompted to install "Security Update 2017-001" which updated my build to 17B1003.
Apple claims only one update was released and that that was released yesterday. :/
https://support.apple.com/en-us/HT201222
https://support.apple.com/en-us/HT208315
It's being hard to track everything that's happening, but I've published a rewrite of this article to cover it.
http://tidbits.com/article/17655
In short, the first update broke file sharing, so Apple updated that one silently. The 1003 build is what you want; if you have 1002, file sharing authentication may be broken. The automatic update is giving people 1003, but if you already installed the update once, you'll need to do so again to get it.