
Photo by typographyimages
“Hacked Account” Blackmail Spam on the Rise—Beware!
You open your inbox and see a message labeled “Change your password immediately. Your account has been hacked.” Inside, the email contains what it claims is one of your passwords, a threat, and a demand for money. The password is indeed one you’ve used in the past—how did the hacker get it? Could you really have been infected with malware?
This “blackmail spam” has been inundating inboxes across the Internet, and while there’s no way to know how effective it is, it has caused plenty of raised pulses. Written in deliciously fractured English, the email message purports to be from a hacker who has taken over your computer and installed spyware that has revealed your brazen browsing habits. The hacker also claims to have taken pictures of you (staring intently, one presumes) while you click through “the big delight of your favorite resources” and threatens to share them with your contacts and brick your computer unless you send a payment using Bitcoin.
What has caused concern for lots of people is that the blackmail spam “proves” that it’s legitimate by showing you a password that you’ve used in the past. (This is often the case, but not universally so. Most copies of this spam that I’ve received include passwords I never used.) Hopefully, the revealed password is not one that you’re still using, since it was extracted from one of the many large password breaches that have occurred over the last decade. To see which breaches might include one of your passwords, check your address at Have I Been Pwned. (It’s worth noting that most of the passwords that attackers have decrypted are short and insecure. If your password was over 12 characters and didn’t use dictionary words or well-known patterns, it may have resisted decryption.)
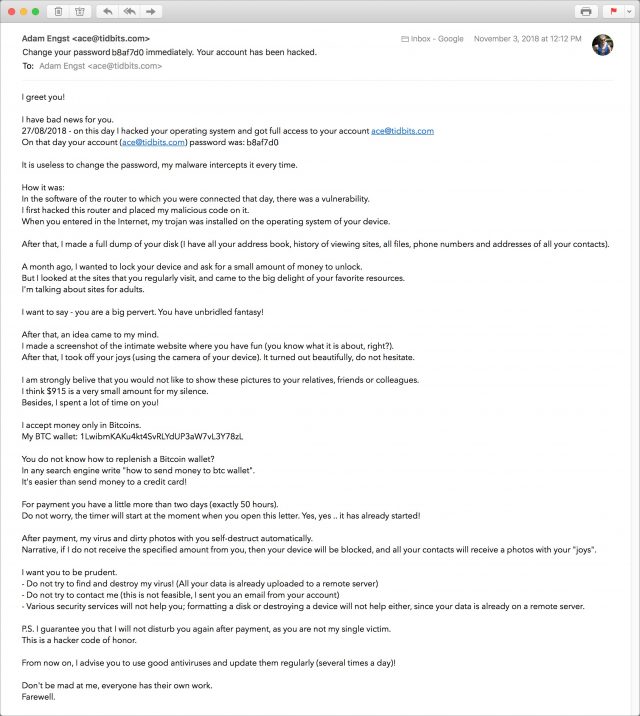
To make this painfully clear, everything in the message other than your email address and breached password is fabricated. Your computer has not been hacked, there is no malware spying on your browsing, no pictures of you have been uploaded to a remote server, and so on. You have nothing to worry about, and you should feel free to mark the message as spam and get on with your life.
If your friends and colleagues ask you about similar blackmail spam, point them to this article and reassure them that they have nothing to worry about. Unless, of course, they’re still using the password that was revealed, in which case they should change it immediately.
Nonetheless, this spam marks what I fear is a turning point in malicious Internet communications. Most spam and phishing messages are almost entirely generic, with their main customization being your email address and occasionally your name. Sometimes they spoof a friend’s address or are even sent from a friend’s compromised account, but that’s about it. Such spam messages are convincing—to the extent that they are—only because of some larger context or because they tap into common desires to get or save money, be more attractive, or partake of some of that brazen browsing. (I’m trying hard to avoid triggering overeager spam filters with more specific words here!)
But not this message. The believability of this blackmail hinges on the fact that—in theory—only you know your password. If the blackmailer can know your password, you think, perhaps their other claims are true too. They’re not, but even people whose browsing habits are always G-rated often report a moment of panic. I presume those who still use ancient insecure passwords experience more than a moment of panic, and well they should.
The problem is that old stolen passwords are just the tip of the iceberg when it comes to information about us that’s readily available online. This blackmail spam combines only two bits of information—your email address and password. What happens when similar attacks expand the amount of information they use?
Some breaches, like the Apollo breach that took place in July 2018, include lots of other types of personal data—places of employment, roles held, locations, and corporate revenue numbers. Even more data is available in public databases. The New York Times recently published an article about apps that use voter registration and voting records to encourage friends to vote, but it’s easy to imagine that data being used for malicious purposes. Then there are real estate records, bankruptcy filings, divorces, and so on.
Blackmail spam taken to its logical extreme is the ultimate example of why we all have something to hide. It’s not that anyone has necessarily done anything that embarrassing, but the chance that we could be blackmailed into paying to keep certain facts under wraps is increasing. Imagine blackmail spam that threatens to reveal your likely voting history to everyone in your neighborhood who is registered with the other party. Or blackmail spam that says it will tell everyone on the Internet with your last name about your bankruptcy or divorce. Blackmail spam doesn’t even have to be true to be damaging. What would be the hit to your career if a spammer targeted everyone at your company’s domain name with an anonymous message that accused you of having committed sexual assault a few years ago and said that the sender was too terrified to identify themselves?
I don’t like to feed privacy paranoia, but as criminal organizations acquire more data science skills and ever larger datasets, such attacks will become all the more sophisticated and believable. It may not happen overnight—people with such skills can usually find legitimate employment more easily—but just as organized crime groups now have or can hire skilled programmers to create malware, they’ll eventually be able to find people who can combine every available piece of data about you and weaponize it in numerous ways. Similarly, it has become clear that governments aren’t above sowing fear, dissension, and confusion in the general populace, and they probably have the resources to do this already.
The worst part is that I can’t imagine a good defense against such attacks. Spam filters work against traditional spam because you’re protected if you don’t see the message. But you not being aware of a threat won’t prevent a blackmailer from carrying it out. Blocking payment methods or tracking payments may be effective in the real world, but cryptocurrency systems make such payments harder to track, if not completely anonymous when the money comes out of an exchange. But even that wouldn’t protect against a dedicated state actor looking to introduce strife into society.
Enhanced privacy legislation that limits the amount of data available about us online could help prevent or reduce the severity of these attacks. Though it’s far from perfect, Europe’s GDPR is a step in that direction. Here in the United States, however, serious privacy legislation probably won’t stand a chance—at least until the politicians who oppose it have had their lives laid bare for all to see, just like the rest of us.
I just got one! But the pw is not one I have ever used. It’s a long randomly generated one.
Diane
Yeah, initially I thought “Well, that’s silly, they can’t even get my password right.” But that’s what made me realize that truth isn’t really an issue here, and part of why I got further into how this sort of attack could be truly problematic even with fabricated details.
I got one too, although it didn’t reveal my password. After a cautionary scan with Sophos, I was sure that it was a scam.
Thanks to TidBits for this article. Once again, this is something that affected me but that no one else covered. It’s why Im a subscriber.
Not sure what you consider “relatively new” but I’ve been dealing with it since Brian Krebs outlined it back in July
https://krebsonsecurity.com/2018/07/sextortion-scam-uses-recipients-hacked-passwords/
-Al-
I think Adam wrote now because over the last several days, the number of such emails exploded. Two days ago, I got one for an email address that is primary a spammer honeypot (the only place it is listed is on my blog, and I never use it to send email). Coincidentally, yesterday, I got a message from Apple requiring me to reset my Apple ID password. I suspect that may have been from an accumulation of failed attempted logins by identities unknown.
Great article, Adam. A lot of people will sleep better after reading it.
I got it too. For one I knew that I had not been to sites such as what was being suggested, but I also immediately saw that the password was bogus. But the real give away was that it was sent to an email address I had only used for one web service about a decade ago and never for anything else. So not only did I immediately know the extortion attempt was bogus (and could be safely ignored and deleted), I also knew which web service had been hacked.
I run my own email server on the same box that hosts my domain. One of the greatest advantages of this setup (apart from the fact that I would never want to rely on a “free” email service like gmail) is that I have an infinite supply of working email addresses that I can define and put into use at any time. So every time I sign up for some kind of online account I use a unique email address that I never use for anything else. When spam starts coming to one of those addresses I know that either the service screwed me over or they got hacked (in which case they essentially also screwed me over). I can then simply discard that account and have any future emails sent to that address rerouted straight to /dev/null on the server. The best part is, you usually know when a service has been hacked before they admit to it in public or you start reading about it in the papers.
I can highly recommend running your own email server. It requires some knowhow (fortunately I have a couple of great friends who were happy to teach me back when I was 100% clueless), but it’s a very rewarding experience once you realize the potential.
Watch last week’s 60 Minutes segment that discusses privacy. Perhaps this is an analogy to security.
The internet was originally all about a cum-by-yah opportunity for the greater good. No one asked the what-if questions - how about the bad guys?
The segment discusses Europe’s GDPR vs USA’s unbridled use on monetizing information to achieve wealth, user’s be damned. Putting the genie back in the bottle is going to be hard.
I think Internet version 2.0 needs to be built.
I like the email server approach - I guess numerous email aliases would work.
Do you have tips for doing this or maybe Tidbits could create an article?
I recommend not running your own email server. It’s not necessary to create distinct email addresses for every site you wish. First, many email providers support subaddressing in some form; the downsides are some poorly written web forms will reject email addresses containing the plus (+) sign most commonly used and a human reading your subaddressed address will know what your real address is (but 99% of spamming is automated and won’t check for this). Some providers, like Fastmail, offer variants that avoid the plus sign issue and are less obvious.
I do recommend having your own domain name for your email. My shared web hosting & domain provider, Dreamhost, also makes it easy for me to create unlimited email addresses (and subdomains). They don’t actually host my email anymore, I got a small, free Google Apps for Domains when they still offered that. I will say it’s more tricky to send email with these email aliases than it used to be as SMTP servers have gotten more finicky and I think Mail.app has as well (that’s probably at least partially because I’m using it with Gmail instead of a “real” IMAP service). Fortunately, it’s almost never necessary to send email with such an address, only receive.
Yes, and we even pointed at Brian’s article back then:
However, as @aforkosh noted, the prevalence of these messages has skyrocketed of late, and lots of people I know outside the computer world are getting them, so I wanted to reiterate the warning and explanation.
Personally, I won’t ever run an email server again—it’s a toxic hellstew, to quote the “Take Control of OS X Server” book where we actively discouraged readers from turning on the Mail service. The attacks are non-stop—we were getting thousands or tens of thousands per day back when we last ran a server earlier this year. And if you make one mistake in setup, you can end up being used as a relay for spam, which can seriously harm your ability to send your own mail (aside from just being icky).
Email is best left to the experts and their security teams.
I forgot to mention that I run my mail server on a Linux box at a hosting provider. I have no idea how it would work on a Mac, but from what you say Adam, it sounds rather unpleasant.
As you say, it’s definitely not something that’s very forgiving, small mistakes can have serious consequences. That’s where savvy UNIX friends really helped me out. But despite that risk there are substantial benefits to running your own show. I really enjoy doing my own server-side filtering and graylisting. Once everything was set up it was really just a matter of editing one text file. That’s basically all I’ve been doing on the mail server side of things for the last decade or so. With all the privacy violations I read about these days, I could never choose something like gmail. Of course I realize those are my priorities. I suppose others can live with Google, Facebook, et al. as long as they then don’t have to worry about things like updating their network stack.
Actually, now that I think about it. when we started out it was still an old Sun workstation running Solaris. A couple of years ago we realized we needed new hardware and then we shifted to Linux on 19" x86 hardware. I miss those old Sun workstations and although I wasn’t a huge fan of Solaris I get all nostalgic just remembering it.
Funny, I was JUST about to start a topic here… the first one I got had what had been a legit password and email address from a forum I used to visit a decade or more ago (which is no longer). I am now being flooded with such messages, none have any passwords and most consist of phony names attached to my domain. We’re talking 4-8 per day.
Oh, my poor domain is being subject to a different abuse. I suspect it’s one person, but they are signing up for MANY ebay accounts using various obviously made up first parts attached to my domain. I get the welcome message then a few days later many times I get the “suspended for suspicious activities” message. I even sacrificed a bunch of my time to try and get through to some human AT ebay (it was NOT easy) to spell it out for them… it took quite a while to convince the person that ANY account using my domain WAS a fraud and they should prevent ANYONE from using my domain (I had had an account but it seems to have died around mid 2017 and I don’t do any business on ebay anyway, if I wanted to do any business I can always use a gmail address). She SAID she would send their “security” team a report, but the pattern I saw before the call has not changed at all… and it’s been over a week.
Not so sure I want to get into the business of creating my own incoming email server… I get the mail, smile at how dumb it is and stick it into a folder. NONE of them even have any attachments… not to mention even if they did, I have yet to hear about any MAC getting infected by just looking at an email attachment or just looking at it.
The other dumb thing about this is I bet 99.9% of them who are GETTING this scam have zero clue how to even use something like a bitcoin to send their money to. Seems to me anyone savvy enough to know HOW are way too smart to fall for such dumb shit in the first place.
What I AM very curious about is they all have what most likely ARE bitcoin addresses that DO lead to whomever they are. CAN they be backtraced Iyeah I know they are not SUPPOSED to, but nothing is 100% secure, a few Isrealies cracked apple a while back)? Maybe if the russian hackers start getting bombarded, we’d see some action!
I’ve been doing my own server-side filtering since about 2010, and I don’t run a mail server. My domain’s email is handled by Fastmail, and I filter using Sieve. I moved my Eudora filters to Sieve (and also switched to IMPA) so that I could change email clients without worrying about filters, and I’ve taken advantage of that flexibility.
I have a Fastmail account which allows me to create email addresses within my domain. I could do most of the filtering with the Fastmail UI, but I already had a long Sieve script by the time they enhanced the UI, plus as a retired programmer I tend to think like a programmer.
Seems to me I have the advantages of running my own mail server without the dangers and time suck.
Edward
What really angers me is that there seems to be little or no consequences for compromising OUR data. For instance the Equifax breach or the Apollo thing that “left a database containing billions of data points publicly exposed with no password”! Someone should be in jail for that. Perhaps then future keepers of our information might put a little more thought into protecting it.
It is very frustrating that we are so often required to provide so much personal information online knowing that chances are good it will end up in the wrong hands. How many times have we heard ‘your information is safe with us’? Bah.
I would imagine that civil lawsuits could apply at least in cases of negligence where it’s easy to show that the company didn’t do what was technically reasonable. @randy2, have you heard of any?
The problem with that is of course that it’s not very realistic for me to take on a huge company and try to prove that they were negligent and that some damage I suffered occurred as the direct consequence of that negligence.
IMHO personal data should be recognized as private property and the burden of proof be reversed. It’s my data. If anybody but myself has it, it’s their responsibility to safeguard it at all and any cost. If they lose it, regardless of how or why, they are liable.
Large data breaches like these could lead to fines, but unless those fines are astronomical, that will likely just be considered the cost of doing (sloppy) business and instead of breaches ending, corporations will just buy insurance. So I then wonder if instead of fines, large-scale negligent data breaches should lead to immediate government takeover and liquidation of the corporate entity responsible for the breach. That might sound drastic, but I’m afraid that’s the only thing that would get the likes of Facebook et al. to take the issue seriously. And if they have only the slightest doubt they can handle my data carefully, well then they can always chose not to take it in the first place. It’s my data after all, not theirs.
Just got this in email from a reader, who said I could share it here:
Thanks for the blackmail spam article. I run my own domains and use custom email addresses and *-addressing for online forums, banking, etc. I use a unique email address for every online resource I register with and have been doing so for 20+ years.
As a result, I’ve been able to track all of the blackmail spam messages back to their hijack source using these “custom” email addresses, that in turn go to my main email via a catch-all mailbox forwarder. For example, my address for your site is <[email protected]>, which goes to my main email address. So basically any email addressed to my domain gets sent to my main email address. I use Gmail and Plesk to filter spam, and the combo is about 98-98% effective while still allowing legit custom email addresses through. Over the years carefully crafted email rules have taken care of addresses which get mistaken for spam, or vice versa. Header filters are a big help, too.
So, for example, if I were to receive spam email addressed to the “unique” address <[email protected]>, I would know your site had been breached–and I’d let you know.
So why am I telling you all this?
Based on the email/password combos I have seen on the 5-6 of these most recent blackmail spam messages I have received, all of the hijacked email address / password combos came from online forums running an unpatched/outdated version of vBulletin. It has been my long experience that many, if not most, forum owners have little interest in keeping their sites secure. Since vBulletin has historically had lingering security issues, it’s long been a ripe target for hacking/harvesting. It’s free and easy to administer, but secure it is not.
In fact, this email address schema allowed me to report to TD Ameritrade some years ago that their servers had been hacked fully eight months before that major breach was made public. I have reported a dozen or more of these breaches over the years.
Your mileage may vary, but that’s been my experience FWIW.
No, I haven’t. And that’s likely because proving negligence requires (among other things) 1) that you prove that the defendant has some sort of legal duty to protect the plaintiff, and 2) that the harm suffered is both real, and it isn’t too attenuated from what might have been foreseeable given the defendant’s negligent act.
I’m not sure that anyone anywhere has defined what the duty of an online host is with respect to keeping their users’ user names and passwords private. There might be a contractually based duty, but I doubt it because it’s the big companies that write these contracts.
And what is the foreseeable harm? Merely that the plaintiff will have to change their password? Is blackmail foreseeable? I doubt that it is legally.
But I haven’t done any research through the literature on this. I’m just going off the top of my head. It’s easily possible that there has been a past case that covers all this. I just don’t know about it.
When I first got one of these a few weeks back I laughed. A week later a parent called in a panic over receiving one. I realized how vulnerable people are or feel!
I got one of these in late October also, mine didn’t give the password they supposedly had. Some things about the mail that signaled “fake” to me were how it carefully avoided including any specific information at all that might have shown they knew “anything” about me. It says we hacked your “operating system”, not mentioning if it is Windows, Mac, or other. It says we accessed your “social accounts”, not mentioning any specific social accounts like Facebook etc. It says we hacked your email, browsing history, contacts, photos and videos, files from your computer, porn sites, etc, etc, yet of all that stuff they supposedly hacked, the email includes no reference to any actual information that from any of my contacts, photos, history, files. It seems to me if they had all that information, I would have expected at least one bit of all that information to have made it into their message to me, even if inadvertently. It would seem to me the fact that there isn’t one bit of actual information about me in the email, is most likely not due to then just not mentioning it, but the most likely explanation is that in fact they have no actual information about me. I would expect since a blackmailer wants to get someone to pay them blackmail, they would make at least a minimal effort to demonstrate that they actually had some blackmail information on you, and if they don’t do that, it’s most likely because they have no such information.
Hi all (long time)
Just a quick data point. I’ve gotten a half dozen of these over the last month or so. They were sent to (and from) an address of one of my own domains.
Rather than blocking the address, I revisited my DMARC records and upped the policy from “none” to “quarantine” (DMARC are instructions mail services may follow if someone spoofs the from address, among other failures; Adam wrote about it here in 2014). Even if set to “reject” my provider does not actually reject mail, it just ups the spam handling signals.
What I found interesting is that I received another one today, virtually identical, but not from my address this time. (Some of previous examples bragged that they were using my account to send the mail as “proof” my account was compromised.)
Anyway, I’m left wondering if the attack might be sophisticated enough to actually check the DMARC policy and adjust to avoid possible rejection or quarantine. I’ll keep monitoring for now and eventually block the address.
I seriously doubt that any of them actually came from your domain. What appears as the "From: " address is almost always faked, ignored and isn’t relevant. You have to look at the header information to determine exactly where it originated and the intermediate locations it passed through. I use https://www.spamcop.net to assist me in this.
If you find that it actually did originate from your domain, then your e-mail has been hacked.
-Al-
The easiest way by far to do this is using spamgourmet.com (cc @mpainesyd). As others have said, I would never go back to running a mail sever, the pain is not worth it with all the options out there today. The nice thing about SpamGourmet, is that you can create email addresses on the fly, as you are filling out a registration form. No need to go to the site or a server to create a new alias or mailbox. It’s a straightforward service, well designed. I highly recommend people check it out. And, @cwilcox, it has a mechanism to allow sending from one of your addresses, too. I’ve been using it for years, and it’s really excellent.
Unfortunately, it’s not accepting new users.
Jeremy
Oh, I wasn’t aware of that. Have just had a look, and it’s upsetting news. The man who runs the site has terminal cancer and has disabled new users until he can figure out what will happen to SpamGourmet. In his position, I don’t know that I would be spending time and energy on SpamGourmet, it is a credit to him and the public service nature of what he has been doing all these years with SG. A difficult post to read:
https://bbs.spamgourmet.com/viewtopic.php?f=5&t=1766&sid=ecd7797eb59f5512879a77eebaa9b40a
@John Warren, thanks for that post about Spamgourmet. I actually registered with this site to comment on the Article, but your post explained to me, in part, what is happening at Spamgourmet. You see I lost my Password wallet in an HDD crash (no backup), and now I not only can’t log in, but seem unable to receive any password reset email.
At least I know what the main problem is. I suspect in blocking some things the guy has inadvertently blocked to password reset email.
I’ve received several of those, probably about 8, there’s probably heaps more, but as I run my own email server on a Linux Box, I have full control over the filters.
At no time did any of the passwords supplied in the email look remotely like any password I have ever used, not that that was much of a clue.
First of all I use a Linux based laptop, so a virus is highly unlikely, not impossible, granted, but not he first, or even the second or third, thing I’d consider.
second I have tape over the built in camera, and a dummy jack in the Microphone socket… paranoia much… but it wouldn’t matter if was doing something salacious in front of my computer.
third all my emails arrive and are display as simple text, not html… which does cause the odd problem reading those emails that insist on html only, but them I check out by viewing the full source first, if it looks suspicious it gets added to my filters, and I never receive one like it again. Fortunately i only need do that at irregular intervals.
And then of course I use lots of Open Source security goodness, and really strong passwords everywhere, to ensure my privacy and security are maintained.
Still ongoing in January 2023, where they only want a mere ‘non-negotiable’ amount of 12.5 Bitcoin (~$17k), lol!
I’m sure they’ll do well asking for such a triflingly small amount – though I may wait a few days when, given it’s volatility, 12.5 bc will likely only be ~$15.00.
Does anyone fall for this? You’d really have to be completely IT illiterate.
I recommend hosting your email with a company that specializes in, well, email hosting, such as Fastmail or Rackspace.
As an example, Rackspace offers email hosting at $2.40/month per address. (They host more than 20 for me.) Among the advantages is a control panel that enables you to configure your own SPAM settings. I’ve had only one SPAM problem with them in the past 10 years. That one was eventually resolved by Cisco’s SpamCop.
Here is the Apple Mail method that works for me. Select the message and choose
View > Message > Raw Source (Opt-CMD-U)
Edit > Select All
Edit > Copy
Paste this into the Report page at SpamCop. Add a note about any particular suspicion you have. (To file a report, you need to open a free account.)
SpamCOP handles the reporting to the offender’s host for you. It even lobbies on your behalf to sites such as Comcast/Xfinity, the worst offender, in my experience. Reporting SPAM to Comcast daily, using your own Comcast account, has no effect. They just don’t care.