TidBITS#1025/26-Apr-2010
It may cost only $29, but Apple’s new iPad Camera Connection Kit features heavily this week, with Glenn Fleishman reviewing it for its primary purpose (transferring photos from your camera to your iPad) and also discovering that it works for audio headsets as well. And then Jeff Carlson found that you can use it to expand your iPad’s media storage capacity, too! On the Mac side of the fence, Glenn covers Orbicule’s Undercover theft-recovery software and Joe Kissell contributes an introduction to file encryption in Mac OS X. We also run down Apple’s stellar second quarter financial results and congratulate the four (!) TidBITS staffers included in the 2010 MacTech 25 list of most influential people in the Macintosh technical community. Notable software releases this week include Nisus Writer Express 3.3.2 and Nisus Writer Pro 1.4.1, HoudahGeo 2.5, Default Folder X 4.3.7, and PageSender 4.6.
Four TidBITS Staffers Honored in 2010 MacTech 25
Congratulations are once again due to my fellow TidBITS staffers – Adam Engst, Tonya Engst, Glenn Fleishman, and Joe Kissell – who were included in the third MacTech 25 list of most influential people in the Macintosh technical community (for the previous lists, see “Adam & Tonya Engst Honored in MacTech 25,” 17 July 2006, and “TidBITS Staffers Honored in 2007 MacTech 25,” 11 June 2007).
A notable addition to the list this year is Ars Technica’s Jacqui Cheng, who joins Tonya as one of only two women on the list. Tonya was the only woman in the 2007 list, and the 2006 list also included Andrina Kelly, Mac OS X system administrator for C.O.R.E. Feature Animation and contributing editor for afp548.com. Though the technology world often appears to be male-dominated, there are in fact many women doing serious technical work at the highest levels, and it’s nice to see at least some recognition of that in the MacTech 25. See MacTech’s Web site for the full list.
Apple Posts $3.07 Billion Profit for Q2 2010
Perhaps the companies that boast they have a “Mac/iPhone/iPod/iPad killer” product can give it a rest for a while. Apple’s latest quarterly earnings revealed that the company is still seeing strong sales of Macs and stellar sales of the iPhone, which accounted for 40 percent of the quarter’s $3.07 billion profit on revenue of $13.5 billion (or $3.33 per diluted share). Gross margin was 41.7 percent. Record revenue for the second quarter was up 49 percent over the year-ago quarter, while profit was up 90 percent, from $1.6 billion to $3.1 billion. The iPad, which has sold over 500,000 units since it was released on 3 April 2010, did not fall into the quarter’s timeline and therefore didn’t contribute to these numbers.
The Mac fared well this quarter with 2.94 million units sold, a 33 percent increase from the year-ago quarter. Continuing an amazing statistic that’s been consistent for some years now, Apple reported that half of those sales were to people who had never owned a Mac before.
Unit sales of the iPod touch grew 63 percent over last year, and were clearly the reason that, while overall quantities of iPods sold were down by one percent, revenue was up: in the year-ago quarter, Apple sold 11 million iPods of all kinds for a $1.67 billion profit; for the last quarter, Apple sold 10.9 million units, earning $1.86 billion. The reportedly higher-margin iPod touch likely also contributed the small increase in overall company gross margins. (Apple doesn’t break out specific unit sales or margins for the iPod touch or other iPod models.)
Sales outside the United States drove part of this quarter’s growth, with the iPhone having the largest impact. International sales contributed 58 percent of the quarter’s revenue. Much has been made of seemingly slow sales of Apple-authorized iPhones in China by its carrier partner, but Apple said Greater China revenue (mainland, Hong Kong, and Taiwan) added up to $1.3 billion, a 200 percent year-over-year increase.
Worldwide, Apple sold 8.75 million iPhones, a 131 percent increase from a year ago, and nearly as good as fiscal 2010’s first quarter, which is always Apple’s biggest due to holiday purchases in December. Apple didn’t provide an updated total of all iPhones and iPod touch units sold ever, but said at the iPhone OS 4 announcement earlier this month that a combined 85 million had sold (see “Steve Jobs Shares iPad Sales Numbers,” 8 April 2010).
During the company’s question-and-answer session, analysts asked many questions about the iPad, including a few related to whether the new mobile device was stealing sales from other kinds of Apple products or from the netbook category. Apple said that it didn’t see any particular slowing in sales of products following the announcement of the iPad, but had nothing to share about the period after the iPad went on sale, as that’s too short a period (just a little over two weeks prior).
As for netbooks, a category that Apple CEO Steve Jobs and COO Tim Cook have been deriding for years, Cook professed an addiction to his iPad, and said he didn’t see anything that a netbook could do that an iPad couldn’t do better. Comparing the iPad to a notebook is like “100 to 0,” Cook said. The expectation of constant comparison to netbooks might explain in part why Apple included Bluetooth keyboard support for iPads in advance of iPhone OS 4, as well as to bolster the iPad’s potential for serious business work.
Undercover Theft-Recovery Software Update Gives You the Details
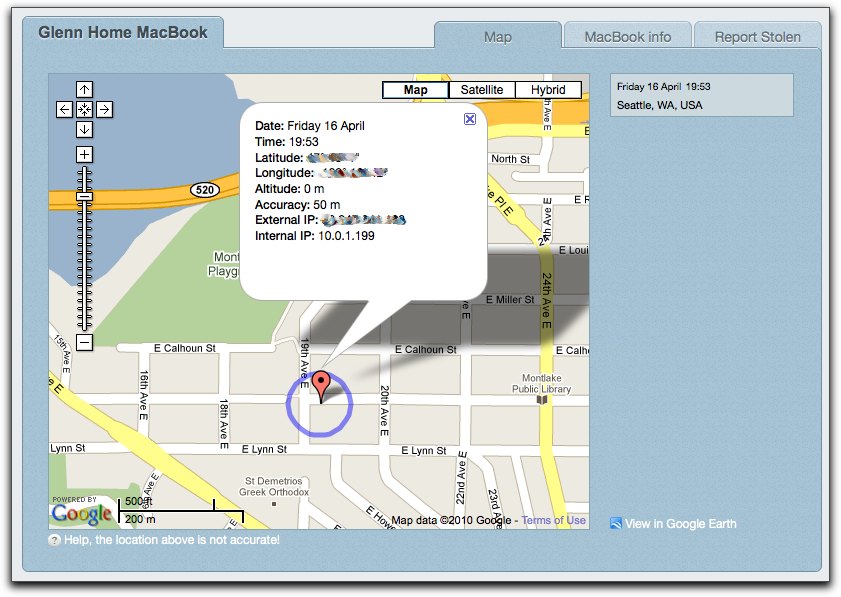
Orbicule’s theft-recovery software Undercover has been revised in version 4 to give customers the same remote screen captures, network data, and location information available to law enforcement.
This kind of software installs itself at a low level of the system, and regularly checks in with a central server to see whether the computer or other device has been marked as stolen, at which point new behavior is triggered. (For more background, see “Help! I’m Being Held Captive, and All I Have Is a Wi-Fi Network!,” 23 May 2008, and “What I Learned from Having My Laptop Stolen,” 24 March 2009.)
The latest version of the software is paired with a recovery/tracking Web site. You can choose whether or not to enable location tracking when the device is still in your possession, and then log into the site to see where (via Wi-Fi positioning) it was estimated to be the last time it was restarted.
In the previous release, you used an Orbicule Web site to enter a unique ID code to report a computer or device stolen. Starting with this release, you use your account to provide information about the theft, including the location, time and date, and any useful comments, such as contact information for local police.
Orbicule provides the details it obtains to local law enforcement, but this release also lets you see the same location information derived from Wi-Fi connections, the network data (IP addresses and other details), the regularly snapped screenshots, as well as pictures snapped via a built-in iSight. This new version is much more like a hybrid of the previous Undercover release and GadgetTrak’s theft-recovery software, which provides information only to you.
The program still features “Plan B,” a mode you can now trigger manually, that simulates a failing screen to trick a thief into taking it into a repair shop. Once there, the software uses text-to-speech to start “yelling” information about recovery, while displaying a full-screen message indicating the computer was stolen. Previously, Plan B was triggered when a computer was booted after 60 days of not having any Internet connectivity; that’s now been disabled.
Orbicule also has an iPhone OS Undercover app ($4.99), which relies on push notifications to try to get the finder or thief to launch the program. Once set up, you can remotely trigger a push notification with a custom message. The app works on any iPhone OS device.
Competitor GadgetTrak released a free program last year – GadgetTrak for iPhone – that relies on misdirection: the program uses a Safari-like icon, and performs the same functions as a browser. The company suggests you put the program in the Home dock. A thief might launch the browser, which triggers location tracking.
Orbicule plans an updated iPhone OS theft-recovery package for iPhone OS 4. With iPhone OS 3, no background services can run, which makes a tracking program tricky. However, iPhone OS 4 will allow background location updates, which would let you launch a tracking program, and have it report updated position remotely. If stolen, unless a thief rebooted the phone, you’d be able to track its position. (It’s unclear whether Apple will allow a launch-at-start set of apps, although that seems unlikely.)
The Mac OS X update is free for Undercover 3 users. A single-user license costs $49, or $39 for students. A household license for up to five computers is $59. Volume pricing is also available.
DealBITS Discount: Save 20% on FotoMagico Pro 3
Congratulations to Janice Ferrera at yahoo.com, Tom Serkowski of serkowski.com, and Kevin Stout at yahoo.com, whose entries were chosen randomly in the last DealBITS drawing and who received a copy of FotoMagico Pro 3, worth $149. Also receiving a copy is Mark Vopat at gmail.com, for referring Kevin to this DealBITS drawing. But don’t fret if you didn’t win, since Boinx Software is offering a 20-percent-off discount on either FotoMagico Home or FotoMagico Pro 3 to all TidBITS readers through 10 May 2010; enter “FMDeal” in the Coupon/Promo Code field on the second screen of Boinx Software’s online store to get
your discount. Thanks to the 810 people who entered this DealBITS drawing, and we hope you’ll continue to participate in the future!
iPad Camera Connection Kit Works Simply and Well
We knew the iPad would be a somewhat different device at its launch party in January 2010 when Apple said that it would both allow keyboard entry and import photos from cameras and SD cards. So much for being a consumption-only device. The iPad allowed Bluetooth keyboard use when it shipped, and the iPad Keyboard Dock appeared several days after.
The iPad Camera Connection Kit, however, didn’t wind up in users’ hands until last week. While the two-piece adapter set is designed for cameras, we ferreted out more kinds of uses, including audio input and video playback.
Let’s look at the ins and outs of importing.
Plug In and Import — The $29 kit comprises two separate parts, both of which plug into the iPad dock connector: a USB adapter and an SD card reader. The adapters project straight out beneath the Home button; unless you have a stand that lets you hold an iPad either sideways or with the Home button at top, you’ll need to lay the iPad flat to use either adapter.
You use these adapters to transfer images from your camera to your iPad when you’re away from the computer you normally use to sync images and other data. The iPad can view the photos and also acts as a repository for the files in their original formats.
The process of importing photos couldn’t be more straightforward; it’s rather like a good hybrid of Image Capture and iPhoto’s import processes. You insert either adapter into the dock connector, then plug in a camera via USB or insert an SD card.
It may also be possible to attach a self-powered USB drive with FAT or FAT32 partitions, the standard disk format for camera images and video storage. I was unable to test this. Flash drives and USB-powered drives will not work, as the iPad doesn’t supply power from the dock connector.
The USB adapter also lets you plug in an iPhone, from which you can grab pictures as if it were a camera, just as in iPhoto. (The iPad can’t charge the iPhone via USB, however.)
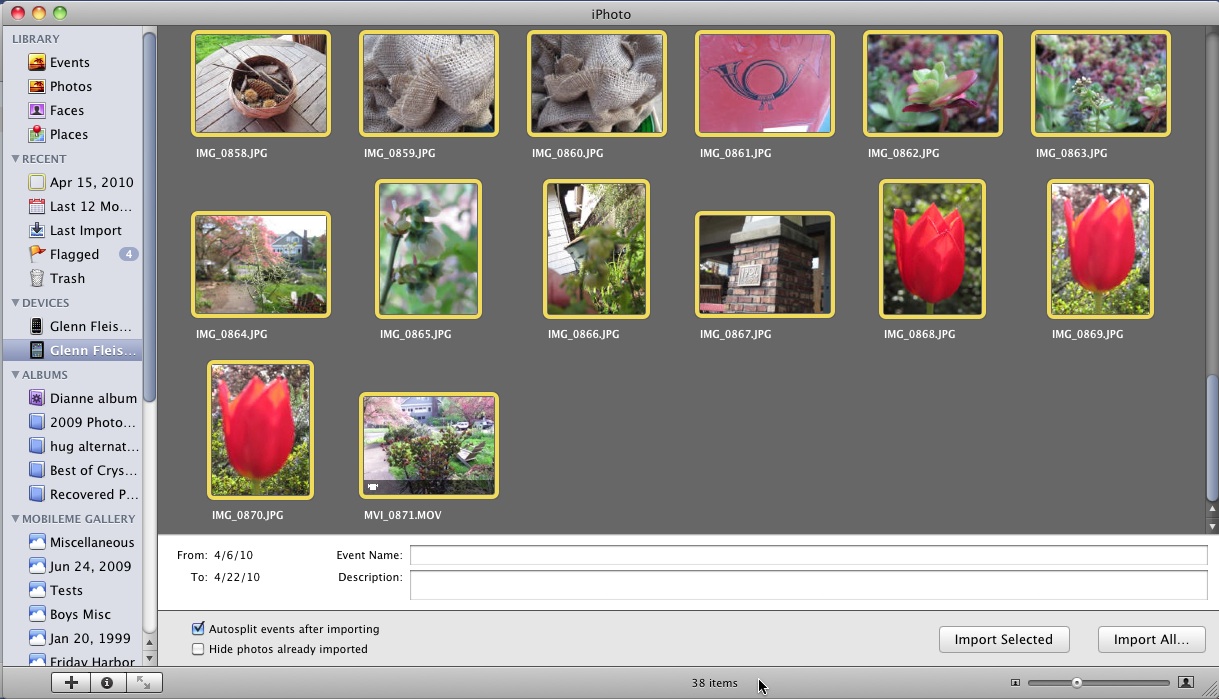
The Photos app launches, and a new tab labeled Camera appears on the far right. This tab shows a preview of stored images and videos on the attached device or camera. Raw, JPEG, and movie files are supported. (See below for more on formats.)
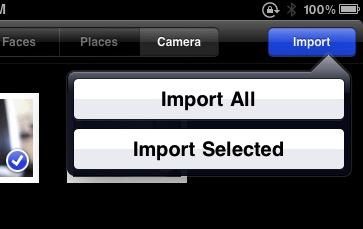
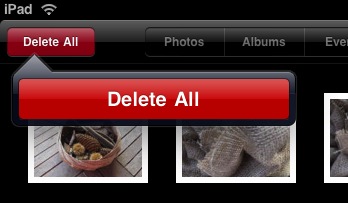
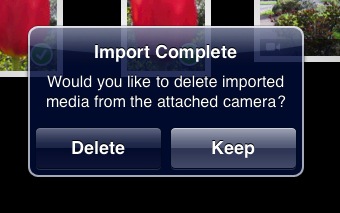
You select images to import by tapping on them. A blue checkmark is placed on the photo when you tap and is removed if you tap again. To transfer the images to the iPad’s memory, tap the Import button: a popover offers Import All and Import Selected if you’ve selected any images. You can halt an import in process by tapping Stop Import in the upper right. (A delete option in the upper left reads either Delete All or Delete Selected, depending on whether any images are selected, if you want to remove images from the card.)
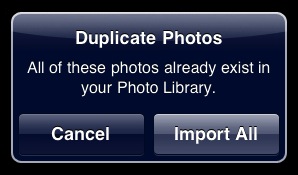
If you’ve already imported some of the images, Photos warns you of the duplication, and lets you cancel or proceed.
As each image is imported, it’s shown with a subtle spinning progress wheel as it’s copied over – look in the lower-right corner of the third thumbnail. The thumbnail is overlaid with a small, green checkmark when its import is completed. As in iPhoto, you’re asked at the completion of an import if you want to keep or delete the imported photos.
My TidBITS colleague Jeff Carlson connected a Flip MinoHD to see if the iPad would import video via the USB connector. The good news: The iPad saw the movies in the MinoHD’s memory, provided thumbnails, and successfully copied clips to the iPad. The bad news: Once transferred, the Photos app displays a Flip’s MPEG-4 formatted clip as a generic MP4 icon, and doesn’t play it when tapped. The clip remained intact when copied from the iPad to iPhoto, however; the iPad just can’t play it.
The only hiccup I saw in whole process was when I inserted a microSD card in a full-sized SD holder. While Apple’s documentation says miniSD and microSD cards can be read via an adapter, my iPad displayed an error message.
When you’re done, you simply pull the adapter out or remove the SD card or USB cable. There’s no eject button, although removing the card or adapter while the iPad is deleting or transferring images is no doubt a bad idea.
In the past, I would have thought that an iPad could serve as a transfer station to avoid running through memory cards you might bring along on a trip. But 16 GB SD cards cost as little as $36, which makes it hard to build a case for why you shouldn’t buy a stack of SD cards for offloading purposes. The cards are also less likely to be stolen or broken on a trip than an iPad.
What’s Supported? — Infuriatingly, Apple doesn’t provide a complete list of supported image and movie formats, nor supported cameras. The tiny user manual that comes with the adapters suggests going to the iPad support mini-site at Apple for a list of cameras (but says nothing about formats); there is no such list at that site, nor anywhere on Apple’s Web site at present. A Knowledge Base article will likely soon appear.
Apple does offer a list of cameras with raw support in Mac OS X 10.6, and one could assume significant overlap. Raw support is updated in Mac OS X via software updates, although often long after new cameras have appeared in the market; the iPad support would likely have to come via a full iPhone OS update. For example, I assume (but can’t test due to lack of equipment) that the cameras supported by last week’s Digital Camera Raw Compatibility Update 3.2 will not work on the iPad until an iPhone OS update arrives.
I’m no expert on raw formats and use neither Aperture nor Lightroom at the moment. However, I tested importing a CR2 raw image from a Canon PowerShot G11, and the workflow seems just right. The image is displayed as a normal photo when viewed in Photos, using a filter (perhaps the same as in iPhoto) to make it look correct. When imported into iPhoto, the original (and quite large) CR2 format file is preserved.
Working with Imported Media — You can view imported photos and videos at full scale, or use Photos or third-party apps to upload to various services, like MobileMe and Flickr.
The Photos app can send single or multiple photos via email, which is one way of uploading to Flickr and some other services. Open a collection of photos; tap the Action button (a square with a curved arrow coming out of it, located at the right edge of the toolbar); tap to select the photos you want; then tap the Email button. Direct the outgoing message to the custom email address that Flickr assigns each member to use for uploading images. Photos must be uploaded to MobileMe one at a time.
Apple claims on its ordering page for the product, “When you sync iPad to your PC or Mac, the photos on your iPad are added to your computer’s photo library,” but I was unable to figure out how this would work. It’s possible that iTunes needs a minor update to provide the necessary support or a checkbox.
Instead, I launched iPhoto, selected the iPad, and used standard import options to bring the photos into the iPhoto library. Images and videos are not downsampled or otherwise manipulated as far as I can tell.
The iPad Camera Connection Kit seems to work well and as expected. Apple needs to update its online documentation quickly, and better explain how to use or enable automatic iPhoto syncing via iTunes. For $29, the kit is quite a deal.
Other Uses for the USB Adapter — As to other purposes of the two adapters, we’ve discovered a few. Because none of these are supported uses documented by Apple, it’s possible the firm would disable these capabilities in future releases.
- You can use the USB adapter to plug in a set of USB headphones or headset. The iPad recognizes the device, and transfers audio to it. Some of our commenters and other users have been able to get external USB microphones and speakers to work, too. For more details, see “iPad USB Camera Adapter Supports Audio Headsets, Too” (23 April 2010).
- The SD card reader imports H.264 movie files (they have the .m4v extension on the Mac), which can be played in the Photos app. As a result, you can use the SD card reader as an inexpensive way to carry movies that exceed the scale of storage on your iPad. Read Jeff’s article, “Increase Your iPad Media Storage for Just $49” (26 April 2010).
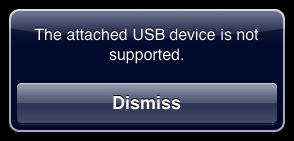
- Low-power USB keyboards also work, although the iPad may balk and say that the USB device isn’t supported. After tapping the Dismiss button on the warning a few times, I was able to confirm that an Apple keyboard that shipped with an old blueberry iMac did work, as did a MacAlly Icekey.
You cannot export anything via USB jack or copy files to an SD card in the card reader. I know you want to; Apple doesn’t allow it.
So much for the widely spread trope of “the iPad doesn’t have a USB jack.” Now, it can become “the iPad’s optional USB jack doesn’t do much.” But, frankly, so far the kit does more than we expected.
iPad USB Camera Adapter Supports Audio Headsets, Too
The iPad Camera Connection Kit has a trick up its sleeve: it handles audio, too, via the USB adapter. Plug in a set of USB headphones or a headset that requires no drivers on a Mac – most use a standard audio profile – and the iPad handles the audio output and/or input properly.
The iPad lacks any visual indicator that audio has been moved over to the USB connector, nor does it offer any controls I can find to choose whether the internal mic and speakers or a USB device will be used.
I tested a Skype call with a USB headset, and the quality was just terrific. This make the iPad even more viable for phone calls, eliminating the need for a Bluetooth headset that requires separate charging and pairing.
The combination of headset, USB connector, and iPad is a little ungainly, but completely workable.
Some readers have also tested using USB microphones and powered USB speakers, and they work, too.
Of course, you can always use the actual audio jack at the top of an iPad with headphones, earphones, and headsets. The compact $29 iPhone Stereo Headset includes a decent mic and earphones. Bluetooth earpieces, headphones, and headsets also work with the iPad. And the built-in mic and speakers on the iPad when used with Skype or other audio chat programs make it into something better than most speakerphones I’ve used.
But I sometimes prefer a full ear headset and a positionable mic for the best sound quality without worrying about charging a Bluetooth device’s batteries.
For a review of the connection kit’s primary picture-related features, see “iPad Camera Connection Kit Works Simply and Well” (22 April 2010).
Increase Your iPad Media Storage for Just $49
Here’s a cool iPad tip suggested by one of our awesome TidBITS readers. In “iPad Camera Connection Kit Works Simply and Well,” 22 April 2010, commenter “Mikey” asks:
"Can you use the SD Card Adapter to watch or import h.264 movies?"
The idea is that if you want to carry more than a few movies or other video content with you, you’d want a lot of storage on your iPad. The base model Wi-Fi-only iPad with 16 GB of storage costs $500. Its 16 GB doesn’t feel too roomy once you start syncing media files to it. But paying $100 more for the 32 GB model, or $200 more for the 64 GB model, may not be in your price range.
What if you could increase that storage for just $49 instead?
Using Apple’s $29 iPad Camera Connection Kit and a $20 8 GB SD memory card (or several), you can take an iPad on vacation without lugging a laptop, and still carry more movies than would fit on the iPad by itself. You could also repurpose older, lower-capacity SD cards you otherwise don’t use any more.
The iPad Camera Connection Kit is designed to import digital photos directly from an SD card or a camera, but because most digital cameras now shoot video as well as still images, incoming video files are supported on the iPad, too.
Not all formats will play, however. I discovered I could import clips from a Flip MinoHD video recorder to the iPad using the USB connector module of the kit, but couldn’t play them on the iPad.
Movies purchased from the iTunes Store, which are wrapped in Apple’s FairPlay digital rights management scheme, won’t play using the following method; those must be synced via iTunes.
To take advantage of this capability, load up the memory card with movies. Let’s say you’ll be gone for a couple of weeks and want to take just the iPad. Before you leave, encode titles from your DVD collection using a tool such as HandBrake, which offers a convenient Apple TV encoding preset. When a file is created, copy it to the DCIM folder on the SD card. I also successfully tested a short 720p HD video, exported from iMovie at the HD setting.
Eject the card from the computer and insert it into the iPad’s SD camera connector, which opens the Photos app in the Camera pane. You can’t watch a movie directly from the memory card, but you can copy it to the iPad’s photo library. Tap to select the movie you want to watch, tap the Import button, and then tap the Import Selected option that appears.
After the movie copies, you’ll find it in the Last Import collection under the Albums pane (as well as the Events pane if you normally sync the iPad’s photos with iPhoto). The movie stays within the Photos app, not in the Videos app. Tap its icon to start playing it.
After you’ve watched a movie, you can delete it from the iPad’s memory by tapping the Trash button at the far right edge of the toolbar. Then load another movie from the SD memory card and watch it at your leisure.
Other higher-capacity card sizes are also available: A 16 GB card runs as little as $36 currently. 32 GB cards are also available, but at $75, the cost savings over upgrading the iPad diminishes.
Unfortunately this trick doesn’t work with USB thumb drives using the USB camera connector, because only powered USB drives formatted as FAT or FAT32 appear as options to the iPad for importing images and videos. (For more on this, see “iPad Camera Connection Kit Works Simply and Well,” 22 April 2010.)
People are looking at the iPad as a laptop replacement, and although this trick doesn’t tackle other issues such as effectively working with business documents or printing, it can be good for travelers with long stretches of time that needs to be filled. Instead of bringing a laptop, with its capacious hard drive, you can bring just the iPad and a pocket full of inexpensive SD memory cards.
An Introduction to File Encryption in Mac OS X
Last year, in between writing Take Control books and Macworld articles, I managed to squeeze in another little project – writing the 900-page “Mac Security Bible,” published in January 2010 by Wiley. Although Rich Mogull is the real staff expert when it comes to Mac security, I’ve also written a good deal on the subject, including Take Control titles dealing with backups, spam, and passwords. This new book is a compendium of everything a typical (or even advanced) Mac user might want to know on a wide range of security topics.
This article is an excerpt from Chapter 13, “Encrypting and Securely Deleting Files,” reprinted with the kind permission of Wiley. File encryption is of course just one tiny piece of the security puzzle, but it’s worth knowing about if you keep confidential data on your Mac, especially if the computer is ever out of your physical control – which would include being lost or stolen.
Think about it this way: Would it bother you or any of your friends or family if the entire contents of your Address Book were made public? Would you be disturbed to know that a stranger could see years’ worth of your family photos, read all your email, and discover every Web site you’ve visited in the past month? Even the least secretive of us would probably agree that all this sounds pretty creepy, and that we have good reasons to keep private information private.
The way to keep your data safe while it’s sitting on your hard disk is to encrypt it – to scramble it in such a way that it looks like garbage to anyone without your password or key. Encryption comes in many forms, some of which are almost trivially easy to use, and others that require extra thought and effort. The chapter from which this article is excerpted explores a variety of different approaches to encrypting some or all of your files.
Encryption Algorithms — An encryption algorithm, also known as a cipher, is a particular method for encrypting data – a sort of mathematical formula that takes the input (sometimes called cleartext), processes it using a secret piece of information (a key), and produces encrypted output (sometimes called ciphertext). Over the centuries, countless thousands of encryption algorithms have been developed, ranging from the extremely simple to the breathtakingly elaborate. In the modern computing world, you’re likely to run into at least a half-dozen common ciphers considered especially well-suited for encrypting and decrypting data on your Mac.
Two factors influence how secure (resistant to being broken) an encryption algorithm is. First is the design of the algorithm itself. Some have weaknesses or design flaws that could enable an attacker to decrypt data even without knowing the key. The other factor is the complexity of the key. If you use the world’s most complex and powerful cipher but give it a simple key, such as the word “cat,” it becomes quite easy for someone to figure out how to decrypt your data. The best results come from combining solid, reliable algorithms with long, random keys.
I could spend many pages simply listing encryption algorithms and their variants, but I want to briefly acquaint you with just a few especially common ones:
- AES. The Advanced Encryption Standard is one of the world’s most commonly used ciphers and one accepted by the U.S. government for protecting secret data. AES can use 128-, 192-, or 256-bit keys (see just ahead for a discussion of key length); these variants are commonly known as AES-128, AES-192, and AES-256, respectively.
- Blowfish. This fast, open-source encryption algorithm, designed by security expert Bruce Schneier, can use key lengths from 32 to 448 bits.
- CAST. The term CAST is used for a family of algorithms; the name comes from the initials of its developers, Carlisle Adams and Stafford Tavar. The original version, with a 128-bit key, was called CAST-128 or CAST5; a modern successor is CAST-256.
- DES. The Data Encryption Standard, which dates back to 1975, was formerly approved for use by the U.S. government and can therefore be regarded as a forerunner to AES. But it supports only 56-bit keys, and because it’s been shown to be breakable with relative ease and speed, it’s no longer considered secure.
- IDEA. The International Data Encryption Algorithm, which uses 128-bit keys, is considered a highly secure cipher, and was designed as a potential replacement for DES.
- Triple DES. Also known as 3DES or TDES, this cipher is based on DES but applies the DES algorithm three times to each block of data, thus increasing the possible key size to 168 bits (that is, three separate 56-bit keys).
- Twofish. Designed by a team of cryptologists, including Bruce Schneier, Twofish is in the same family as Blowfish but considered more modern and advanced. Twofish can use key lengths up to 256 bits.
Passwords and Keys — As previously mentioned, a key is a piece of information that a cipher uses to encrypt (and decrypt) data. If you encrypt two copies of the same data with identical ciphers but different keys, the resulting ciphertext is different; likewise, if you use the same key to encrypt two copies of some data with different ciphers, the results are different.
One form a key can take is a password (or passphrase). In other words, feed your password into an encryption algorithm to encrypt some data; then use the same password later to decrypt it. This example assumes a system in which the same key is used both for encryption and for decryption – a symmetric cipher. Asymmetric, or public-key, ciphers use one key to encrypt data and another one to decrypt it. A key can also be, among other things, a string of data stored on a token, a smart card, an electronic key, or another device.
An algorithm’s key length is the longest key it can use. So, AES-128 can use a key that’s 128 bits long. For those of you unaccustomed to thinking in binary, that translates to 16 characters. Likewise, a 256-bit key can be up to 32 characters in length.
When you choose a password for encrypting data, most encryption algorithms don’t use the password itself as the key. Behind the scenes, the algorithms run your password through some mathematical functions that turn it into a number with the maximum key length the algorithm supports. This is done partly to protect your password from discovery (even if the key is cracked) and partly to make sure the key has exactly the right number of bits. If a cipher uses a 128-bit key but I enter an 8-character (64-bit) password, the software performs its magic to give itself a longer and more secure key to work with. That means if someone attempts to break the encryption by trying every key, that person has a much wider range of possibilities to test.
But if, instead, that person tries to break the encryption by testing passwords directly (running each one through the necessary process to derive a key), he or she might break the encryption sooner.
On the other hand, if I enter a password that’s longer than the supported key length (say, a 20-character password for a 128-bit cipher), the software typically discards the extra characters before deriving its key. The result would be that an attacker trying to decrypt my files by trying all possible password combinations would have just as much trouble as someone trying all possible key combinations.
The upshot of all this is that it’s to your benefit to choose a password that’s as long as possible – but no longer than the maximum key length supported by the algorithm you use. If you use 56-bit DES, a 20-character password is no safer than a 7-character password. However, with AES-256, a 32-character password is exponentially safer than a 31-character password!
For any given encryption algorithm, longer keys (and therefore, to a point, longer passwords) are more secure. However, as I stated earlier, not all algorithms are created equal. That means key length alone doesn’t tell the whole story; one algorithm’s 128-bit keys might be, in practice, just as secure as another’s 256-bit keys if the 256-bit algorithm has flaws that reduce its effective strength. In other words, given the choice of a longer key length with a given algorithm, you should take it; but don’t assume that cipher A is stronger than cipher B just because the former uses longer keys. For all practical purposes, any modern cipher with 128-bit or larger keys is secure against all but the most determined attacks – assuming you’ve
chosen a good password.
Choosing What to Encrypt — How much you encrypt or whether you encrypt anything at all depends on several factors, including where you use your Mac, how sensitive the information on it is, what other security measures you’ve taken (protecting against theft, for example), and what your tolerance for inconvenience is.
Needless to say, the greater the confidentiality of your data and the less physically secure your Mac is, the more important it is to encrypt data. But you shouldn’t overlook the convenience factor. In general, the larger the unit of data you encrypt, the more convenient it is in the long run. That is, it’s less bother (in some senses, at least) to encrypt your entire disk than to encrypt just your home folder; it’s less bother to encrypt your home folder than to encrypt a conventional folder; and it’s less bother to encrypt a folder than to encrypt a single file. That may all sound counterintuitive, but it has to do with things such as the amount of manual effort required to encrypt and decrypt files and how often you have to type a
password.
However, also keep in mind that how and when you use encryption depends on context. For example, in some situations, it may not make sense to encrypt even a very sensitive file when it’s sitting on your hard disk, but if you transfer it to a flash drive to take it with you somewhere or if you send it to someone via email, FTP, or some other method, encryption suddenly becomes quite important because you lose the security otherwise provided by your normal computing environment.
With those thoughts in mind, consider the following units of data you could potentially encrypt, all of which are elaborated on in the full chapter:
- Individual files
- Individual folders
- A disk image
- Your home folder
- An entire volume
- Your startup disk
- A complete hard drive
As I describe in the book, there are good arguments for choosing any point along this continuum. The way you go about encrypting data depends on how much you want to encrypt and what combination of features and trade-offs works best for you.
Encryption Pitfalls and Misunderstandings — Encryption can sound like a magical process that makes your data impervious to discovery. But merely encrypting something doesn’t necessarily make it safe. Encryption involves a number of potential holes and hidden dangers, and if misused (or trusted indiscriminately), it can cause more problems than it solves. Before you embark on an encryption crusade, however worthwhile your ultimate objective may be, keep in mind the following possible gotchas.
Forgetting the Originals: In most cases, when you encrypt a file, you actually create an encrypted copy of the file, leaving the original intact. Even encryption programs that automatically delete the original after encrypting it often do so in such a way that the unencrypted file could later be recovered. Later in the chapter from which this excerpt is taken, I discuss secure deletion as a way to solve this problem.
Leaving Files Unlocked: Encryption protects data on your disk only when it’s not actively in use. For example, your keychain is encrypted, but when you unlock it, you (or someone else) can freely access its contents until you lock it again or it locks on its own (based on your preferences). Similarly, if you encrypt a disk image, it’s safe as long as it’s closed, but when you mount it, its files become available to anyone with access to your computer. Therefore, you should always close, unmount, or lock encrypted files when they’re not actively in use.
Choosing an Insecure Password: Poorly chosen passwords are the Achilles heel of any encryption system. Longer, random (or seemingly random) passwords do a vastly better job at protecting your data than short or easily guessable passwords.
Forgetting Your Password: The flip side of choosing an insecure password (which might let someone else get at your data) is choosing a great password but then forgetting it (which prevents you from seeing your own data). If you’re not sure you can remember your passwords, store them in your keychain or in a third-party password management program.
Not encrypting everything that needs protection: If you’re working on a secret business plan or composing an illicit love letter, it’s easy to see why that one particular file should be encrypted. But one of the most common mistakes in data security is overlooking data that may not appear, at first glance, to be confidential but which can contain extremely sensitive information. Here are some examples:
- Virtual Memory. As you use your Mac, Mac OS X constantly swaps information between physical RAM and virtual memory on disk to improve performance. The result, though, is that something you thought was only fleetingly stored in memory (such as text you copied to the Clipboard) can be stored on disk – sometimes for hours, days, or longer.
- Your Clipboard(s). Speaking of the Clipboard, information that you copy or paste could be recovered, even if not stored in a virtual memory file, by using a cold boot attack (described in the book). And if you use any of the numerous utilities that offer multiple clipboards, they almost certainly store their information on disk long after you copy it.
- Cache Files. Many applications, from your Web browser to your word processor, maintain cache files of recently (or frequently) accessed information to help them run faster. These cache files can contain a surprising amount of personal information.
- The Contents of Your iDisk. If you’re a MobileMe member, you should be aware that anything you put on your iDisk is unencrypted (unless you manually encrypt it), and therefore anyone who knows your MobileMe user name and password can access anything on it.
- Backups. Some programs can store extra backup copies of your files as you work, possibly in locations you wouldn’t expect. Also, some backup programs, particularly those that back up to Internet servers, keep caches of files on your disk, which may be unencrypted.
- Spotlight. Apple’s system-wide Spotlight indexes could contain cleartext traces of data from files you’ve encrypted. Some encryption programs expressly delete such data.
Encrypting Individual Files and Folders — The most basic approach to encryption is to apply it only to the particular items that are especially sensitive. Although it would be extremely awkward to individually encrypt each file you use on a daily basis, encrypting specific files or folders makes sense when sending the info over the Internet (by email, FTP, or otherwise) or if you’re using any other unencrypted transmission or storage method, such as employing a flash drive, external hard drive, or optical disc to move files from one location to another.
As mentioned earlier, it’s important to remember that when you encrypt a file or folder, you actually create an encrypted copy, leaving the original intact and unencrypted. The same is true if you decrypt a file or folder, modify it, and then re-encrypt it. Therefore, the safest practice to follow after encrypting something is to securely delete the original; for example, by dragging it to the Trash and choosing Finder > Secure Empty Trash.
If this is the sort of encryption you want, you have many tools to choose from. Mac OS X includes command-line utilities that can encrypt files (as described in just a moment), although they’re not terribly convenient to use. Numerous third-party vendors offer easy-to-use alternatives, with a wide variety of encryption algorithms, interfaces, and extra features. Regardless of which type of program you use to encrypt your files, consider the following factors when choosing an encryption tool:
- Compatibility. Will someone else have to decrypt this file – or will you have to decrypt it on another computer – and is suitable decryption software available on the target computer? If you choose a Mac-only encryption program, for example, the recipient will be out of luck if she has only Windows available.
- Convenience. How well does the program’s interface fit in with your workflow? Be sure to download the program and try it out a few times with test data before committing to it for live use.
- Sending a Password. The most securely encrypted file isn’t secure at all if an attacker or thief learns its password. So, if you’re sending an encrypted file to someone else, you must also find a secure way to let him or her know how to decrypt it. Sending a password in a cleartext email or writing it on a slip of paper is an insecure method. Better methods include sending it in an encrypted message, using Skype or another encrypted instant messaging service, or delivering the password orally in person.
Encrypting Files on the Command Line — You can encrypt individual files using the openssl program included with Mac OS X, as long as you don’t mind getting your hands dirty on the command line. Basic instructions follow; for more detail, enter “man openssl” in Terminal.
To encrypt a file with openssl, follow these steps:
- Open Terminal (in /Applications/Utilities).
- Choose an encryption algorithm. Openssl supports dozens of ciphers, and your choice is significant in that you must know which cipher was used to encrypt a file when you want to decrypt it later. To get a list of available ciphers, enter “openssl list-cipher-commands”. In this example, I use des3 – that is, Triple DES.
- Enter the following line. Substitute des3 with your preferred cipher. The first filename is the name of the file you’re encrypting, and the second filename is the name of the resulting, encrypted file.
- When prompted, enter and confirm the password. Openssl immediately encrypts the file.
- To decrypt the file later, enter the line below. Again, substitute des3 with your preferred cipher, and replace the filename references with the actual filenames.
- When prompted, enter the password used to encrypt the file.
openssl enc -des3 -salt -in filename -out filename.enc
openssl enc -d -des3 -in filename.enc -out filename
Encrypting Files and Folders with Third-Party Software — Of the many Mac OS X applications that can encrypt individual files and folders, I’ve selected a small sampling to give you an example of your options:
- BitClamp. BitClamp compresses individual files using your choice of AES-256, 256-bit Serpent, or 448-bit Blowfish algorithms. Drag one or more files into the window, click Encrypt, enter and confirm a password, and you’re done. To decrypt files, double-click them and enter your password. ($19.95)
- Drop Secure Pro. Drop Secure Pro is available for Mac OS X, Windows, and Linux. As the name suggests, it lets you encrypt files, folders, and raw text by drag and drop. It offers no fewer than 15 encryption algorithms, including all the usual suspects (such as AES, Blowfish, IDEA, and Triple DES). You can optionally compress the items you encrypt using gzip or bzip2 compression. ($57)
- FileWard. This easy-to-use utility, which relies on the openssl tool built into Mac OS X, lets you encrypt files and folders as well as the contents of the Clipboard by drag and drop using any of the following algorithms: Blowfish, Cast5, Triple DES, DES-X, AES-128, or AES-256. After encrypting files, it securely deletes the unencrypted temporary files created by openssl. ($9.99)
- PGP Desktop Home and PGP Desktop Professional. These security packages, which I discuss in more detail in the book, offer a variety of ways to encrypt data. Among them is the option to encrypt individual files or folders, either with a password or using public-key encryption, which can eliminate the security concerns associated with sending someone else a password to decrypt a file. (Home version, $99; Professional version, $239)
- StuffIt Deluxe. This suite of file compression tools has existed, in one form or another, since the early days of the Mac and is also available on Windows. In its current version, you can compress and/or encrypt files and folders using either StuffIt Archive Manager or DropStuff (the latter of which is designed for quick drag-and-drop operations and also lets you create droplets – stand-alone applications with specific combinations of compression and encryption settings for particular tasks). With these products, you can encrypt files in the StuffItX format using any of four algorithms: 512-bit RC4 (the default), 64-bit DES, 448-bit Blowfish, or AES-256.
You can also use StuffIt Deluxe to encrypt ZIP files (using only the AES-256 algorithm), but because of the way the ZIP format handles encryption, someone could see the names of the files and folders in an encrypted ZIP archive even without decrypting it. ($79.99)
There’s another category of software that can encrypt individual files and folders, but instead of storing them separately on disk, it stores them in a proprietary container, sometimes known as a vault. Often, such programs are used to secure not only files but notes, passwords, credit card numbers, and other random snippets of information. Obviously, such programs are more appropriate for securing data for your own use than for sending it to others. Two examples of software in this category are:
- AllSecure. This snippet keeper can store files, folders, notes, and other confidential information. When you add files to AllSecure, they’re ZIP-compressed with AES-256 encryption. ($25)
- Yojimbo. Yojimbo is a popular repository for random information of all kinds. When you store files or text notes, you can optionally encrypt them individually using AES-256 by clicking an Encrypt button and then typing your password. To view an encrypted item, click the View button and then enter your password; to decrypt it permanently, choose Item > Decrypt and then enter your password. ($39)
More Encryption and Beyond — That’s just the beginning of what I cover in the chapter on encrypting files. I go on to discuss working with encrypted disk images, using FileVault, encrypting an entire disk, using hardware-encrypted drives, securely deleting files, securely erasing disks, and recovering deleted files.
And, of course, encryption is only one of a great many topics pertaining to Mac security that I explore in the book. It also includes complete details on secure email, chat, and Web browsing; protecting your Mac against malware; network security; sharing your Mac’s resources safely; securing Mac OS X Server; and dozens of other subjects. If you’re interested in Mac security and want the ultimate all-in-one reference, I think you’ll find the “Mac Security Bible” to be a valuable reference. The retail price of the book is $49.99; Amazon.com offers it for $31.49 at the moment.
TidBITS Watchlist: Notable Software Updates for 26 April 2010
Nisus Writer Express 3.3.2 and Nisus Writer Pro 1.4.1 — Nisus Software has released maintenance updates for the increasingly powerful word processors Nisus Writer Pro and Nisus Writer Express. Both updates focus on bug fixes, with the Pro version also receiving an improved file importer that uses the OpenOffice 3.2 code (the company has also made a faster Intel-only file importer). Bugs addressed in Nisus Writer Pro 1.4.1 include one that prevented files from saving after Apple’s Make Link contextual menu item had been used, one that caused the program to hang when tables were used in endnotes, one that would cause the Underline
keyboard shortcut to become ineffective after relaunching the program, and one that caused crashes triggered by certain RTF lists emitted by Apple. A full list of changes is available on Nisus Software’s Web site. ($79 new, $45 upgrade, free update, 151 MB)
Nisus Writer Express 3.3.2 has a nearly identical list of changes, and also addresses a bug that caused the program’s document icons to appear blank for users working exclusively with Nisus Writer Express. ($45 new, $30 upgrade, free update, 52 MB)
Read/post comments about Nisus Writer Express 3.3.2 and Nisus Writer Pro 1.4.1.
HoudahGeo 2.5 — Houdah Software has released a minor update to the photo geocoding software HoudahGeo with a handful of new features. Changes include full compatibility with Aperture 3 (previously HoudahGeo would not automatically update Places in Aperture when new metadata had been added), the capability to bypass XMP sidecars during EXIF/XMP exports, and added support for log files created by the Wintec WBT-202 and Sony GPS-CS3. Also, USB connections are now supported for the Holux M-241 track logger, an issue with causing duplicate albums in Flickr has been fixed, and a bug causing incorrect timestamps on image imports has been addressed. ($30 new, free
update, 6.5 MB)
Read/post comments about HoudahGeo 2.5.
Default Folder X 4.3.7 — St. Clair Software has released a maintenance and stability update to the Open/Save dialog enhancement utility Default Folder X. Version 4.3.7 brings drag-and-drop capabilities to the System Preference menu, enabling users to add folders and applications more easily. Also, several shortcuts for working with preferences have been added, and support now exists for the AppleScript commands GetCurrentFolder and GetCurrentSelection, which return the current folder or selection when the file dialog is open. Finally, the update resolves several compatibility issues with FileMaker 11, Word 2008, MacPyMOL, and Apimac’s Compress Files.
A full list of changes is available on St. Clair Software’s Web site. ($34.95 new, free update, 9.9 MB)
Read/post comments about Default Folder X 4.3.7.
PageSender 4.6 — SmileOnMyMac has released a small update to the company’s fax application PageSender. The latest version adds support for eight new international fax-via-email services including Concord Fax, Rogers Business Internet Fax, SRFax, Soho66, Faxmate, Singtel, eCall.ch, and Axiatel. The update also now utilizes the in-product purchasing method FastSpring, addresses a possible crash that could occur when viewing incomplete faxes, and fixes several other unspecified bugs. ($39.95 new, free upgrade from 4.x, 6.2 MB)
Read/post comments about PageSender 4.6.
ExtraBITS for 26 April 2010
While recovering from last week’s massive TidBITS issue and responding to oodles of amazingly kind comments from readers, we didn’t do much reading other than following the Gizmodo stolen iPhone prototype story, which Andy Ihnatko and Scott Adams did a good job of summarizing. Adam also shared some stories from his early Mac days with MacTech Magazine, and we watched as Israel banned the iPad, took flak, and lifted the ban last weekend.
Dilbert Weighs in on Gizmodo Stolen iPhone Prototype — Scott Adams of Dilbert fame has released two comic strips that deftly summarize the entire Gizmodo stolen iPhone prototype story, with the addition of Wally. Since the story will undoubtedly be old by the time these could hit newspapers (there’s a one-month lag time, apparently), Adams decided not to submit them.
Time Magazine Finds No Reason for Israel’s iPad Ban — Time Magazine finds no credible reason for the blockage of iPads into Israel, but notes that the sole authorized Apple importer, iDigital, is owned by the son of Israel’s president. Time talked to wireless experts, the ministry of communications, and others, and the explanations are quite thin. The ministry appears to be relying on the word of iDigital, rather than, say, testing or calling up Apple, on whether the iPad meets the European standards that Israel follows. The ban was lifted over the
weekend.
Andy Ihnatko Analyzes the Gizmodo Stolen iPhone Story — Apple’s famous secrecy has resulted in a salacious story of a prototype iPhone being lost, found, purchased by a blog, connected with a specific engineer, and (presumably) returned to Apple. There’s no real news involved – the confirmed features were commonly expected and it’s unknown whether the next iPhone will use this prototype’s industrial design. Either way, it’s not actionable information until Apple actually releases the next iPhone, probably in June or July. If you’re wondering what all the fuss is about, Andy Ihnatko’s Chicago
Sun-Times column has the best summary we’ve seen.
Adam Shares Pre-TidBITS Mac Stories with MacTech — TidBITS isn’t the only Mac publication that’s been around for a long time, and the venerable MacTech Magazine is celebrating its 25th anniversary this year. To help them commemorate the occasion, Adam reached far back into the depths of time – well before TidBITS! – for some of his most-cherished stories of Mac hacking and usage in the days of the Mac Plus and SE.