TidBITS#1121/09-Apr-2012
In the news this week, we report on Dropbox doubling their referral bonuses — even retroactively! — and the notable release of FileMaker 12. Also, Adam looks in depth at the fast-moving Flashback malware, which has reportedly infected 600,000 Mac users, and he describes how to determine if you’re infected and how to avoid falling prey to Flashback. Continuing on the security kick, Rich Mogull explains just how the security of cloud-based services works and how you can tell if employees of your cloud provider can read your data. Notable software releases this week include TinkerTool 4.8, Hazel 3.0.4, SpamSieve 2.9, and App Tamer 1.2.1.
Dropbox Referral Bonuses Doubled to 500 MB, Retroactively
For every friend that you invite to join Dropbox, the cloud-based storage and file sharing service has long awarded both you and your friend 250 MB of free storage space. It’s a great technique for encouraging people to sign up with the service, and Dropbox just sweetened the deal by doubling the bonus space award to 500 MB. (Educational Dropbox accounts were already receiving 500 MB referral bonuses, and it appears they remain at that level.)
Even better, and this is a truly classy move, Dropbox has applied the doubling retroactively to all your previous referrals. As a result, my account, already at 13.25 GB (2 GB base amount, plus 250 MB from being referred to Dropbox by someone else initially, plus 8 GB of 250 MB referrals, plus 3 GB from the Camera Upload beta test; see “Get More Storage for Testing Dropbox Camera Uploads,” 29 March 2012) has now jumped to 21.25 GB thanks to the 8 GB of referrals being doubled to 16 GB. Speaking of which, 16 GB is the maximum a free Dropbox Basic account can gain from referrals; paid Dropbox Pro accounts earn 1 GB per referral and can get up to a maximum of 32 GB.
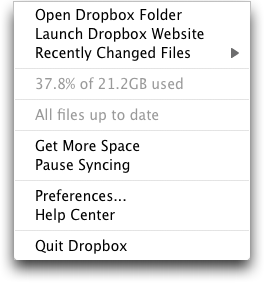
So if you were previously on the edge of filling up your Dropbox account, you may have just received some additional breathing room. To see how much space you have, you can just look in the Dropbox menu, where it will tell you what percentage of your overall space is used. If you check your Account Info page, you can see how your storage breaks down between your files and files shared with you.
FileMaker 12 Adds Power, Clarity, and Free iOS Apps
With the release of the FileMaker 12 suite of software, FileMaker, Inc. is reinvigorating its venerable database platform with robust new versions of Mac and Windows applications, 64-bit server software, and updated iOS apps, now free to download. The new versions are available immediately.
The company has clearly invested considerable effort in developing comprehensive design tools that will enable users to implement clean database interfaces without needing much in the way of design skills. FileMaker Pro 12 offers an expanded and improved collection of “starter solution” database templates users can adopt as is or customize as needed, and 40 different themes to provide a rich and professional-looking visual impression with little additional time or energy on the database designer’s part. Many of the themes offer layouts designed specially for use on an iPhone or iPad.
FileMaker Pro 12 is available for both Mac OS X and Windows for $299, with a $179 upgrade price, and FileMaker Pro 12 Advanced is available for $499, with a $299 upgrade price. FileMaker Server and FileMaker Server Advanced cost $999 and $2,999 respectively, with upgrades priced at $599 and $1,799. Upgrade pricing is available to owners of FileMaker Pro or Server 9, 10, or 11. Owners of FileMaker Pro/Server 8 or earlier versions will need to purchase the full product, and FileMaker Pro/Server 9 users are eligible for upgrade pricing only through 27 September 2012.
In the Palm of Your Hand — We’re not surprised to hear from the FileMaker folks that iPhone, iPod touch, and iPad access to FileMaker Pro databases has become a big deal since the release of the FileMaker Go applications (see Steve McCabe’s “FileMaker Go Brings FileMaker Databases to iOS,” 9 February 2012). These iOS apps, geared toward portable access to databases developed on the desktop, become free with the release of FileMaker Go 12. New versions are available now in the App Store. (The paid versions of FileMaker Go 11 will remain available in the App Store for those who want to continue working with FileMaker
Pro 11 or FileMaker Server 11.)
In line with one of Steve McCabe’s criticisms, FileMaker Go 11 users, especially on the smaller iPhone screen, often found themselves pinching and swiping quite a bit to zoom and pan around layouts designed for use on a laptop or larger desktop screen. For version 12, FileMaker has done that extra work for us; the provided themes, which can be applied even to existing databases with a couple of clicks, not only turn jumbled rows of fields into tidy layouts for the bigger screens, they also seamlessly deliver handheld-sized and tablet-optimized screens — complete with the bigger spaces and controls that come in handy when you’re interacting with a form using your finger, and not a mouse or trackpad.
At the same time, FileMaker has added a richer array of iOS-specific features to the FileMaker Go apps. Database developers can take advantage of iOS location capabilities if allowed by the user, users can record audio and video directly into a database with multimedia fields, and multimedia playback supports AirPlay streaming to devices like the Apple TV.
We’re pleased to see the company has also addressed one of our longstanding frustrations with FileMaker Go. Better wide-area networking support in the software at both ends means iOS users can now access databases that are being served just about anywhere. Earlier versions of FileMaker’s iPhone and iPad apps could only open databases hosted on the same local network, or while using a VPN connection to a remote network.
FileMaker’s layout features have been changed to reflect spacing and sizing based on points rather than pixels, important in a Retina display world where pixel size can vary enormously from device to device. (The company says the apps don’t automatically deliver different graphics optimized for the Retina display in current iPhone and iPad models, but the resolution independence will allow that in the future. In the meantime, text and certain other visual elements drawn by the apps will take advantage of the Retina display.) The iOS apps now even have their own capability to export data into Excel, CSV, and tab-delimited text files, which can be emailed directly.
While the FileMaker Go 12 apps are available at no charge, the average user won’t find them useful in a vacuum; databases accessed via the apps must be created or hosted by FileMaker Pro 12 or FileMaker Server 12.
On the Desktop — The core desktop version of FileMaker Pro hasn’t changed too radically, though there are some nice additions. When working with media, users can now drag images, video files, or documents such as PDFs to the corresponding container field in the database window, rather than having to go through the multiple clicks of selecting the field, navigating around the file selection dialog box, then selecting and attaching or uploading the file. Media incorporated by users in local databases can be stored within the database file or linked to the original on the user’s hard drive.
FileMaker Pro 11 introduced some basic charting capabilities, and the company says the feature proved so popular that in FileMaker Pro 12 they’ve added a Quick Charts tool and several new types of charts, including bubble, scatter, and stacked bar or column charts.
Power to Spare — At the far end of the FileMaker spectrum, the company has revamped its FileMaker Server and FileMaker Server Advanced products to run in 64-bit mode. The company says the resulting access to additional memory can boost performance for large databases. At the same time, FileMaker 12 sports a re-architected Web publishing engine that provides better performance when delivering FileMaker data embedded within Web pages or to users accessing the databases directly via a Web browser.
FileMaker 12 Server and Server Advanced also gain the capability to serve streaming multimedia to database users. Image, audio, and video files can be centrally managed and encrypted, and the content delivered as needed over the available network connection.
Taking the Plunge — We’re more impressed with the progress and improvements we see in this latest FileMaker incarnation than we have been for a few releases, and we think most serious FileMaker users, especially those using the accompanying iPhone and iPad apps, will want to upgrade. It is important to note that FileMaker 11 and FileMaker 12 databases aren’t cross-version compatible, so organizations will need to upgrade all at once, from the handheld to the desktop to the server.
How to Detect and Protect Against Updated Flashback Malware
Apple has released updates to its Java libraries for users of Mac OS X 10.7 Lion and 10.6 Snow Leopard (see “Java for OS X Lion 2012-001 and Java for Mac OS X 10.6 Update 7,” 3 April 2012). The updates bring the Java runtime engine up to version 1.6.0_31 and fix multiple vulnerabilities in Java version 1.6.0_29, “the most serious of which may allow an untrusted Java applet to execute arbitrary code outside the Java sandbox.” What those release notes aren’t saying is that the vulnerabilities in question were being exploited in the wild by a new variant of the Flashback malware (see “Beware
the Morphing Flashback Malware,” 27 February 2012).
[Update: On 12 April 2012, Apple released updates for Lion and Snow Leopard that remove Flashback. Installing the Lion update disables Java on Web pages unless you specifically re-enable Java. Apple also made available a separate Flashback removal tool for Lion users who haven’t installed Java. For more information, see “Apple Releases Flashback Malware Updates,” 12 April 2012.]
Significant Infection Rates — A Russian antivirus developer, Doctor Web, says their research shows more than 550,000 Macs have been infected after users visited compromised Web sites that contain JavaScript code to activate a malicious Java applet. Sorokin Ivan of Doctor Web later raised that estimate to over 600,000 in a tweet. [Update: A week after Flashback hit the news, its infection level had dropped to below 300,000.]
Although we haven’t seen anything from Doctor Web before, the question of who they are came up on TidBITS Talk, where security analyst Brian McNett said:
The first I heard of Doctor Web was when they were referenced, and when Sorokin Ivan later responded via Twitter to Mikko Hypponen, Chief Research Officer of F-Secure. I know and trust Mikko. He uses reliable sources. Doctor Web appears to be a Russian outfit, with largely Russian clientele, so it wouldn’t be unusual for their reputation to be unknown elsewhere. Their key discovery is that Flashback uses the MAC address of the infected machine as the User-Agent when connecting to its command-and-control server. This is a unique pattern that allowed them to track infections before anyone else. That they shared this finding publicly, along with their data, adds to their credibility.
Mikko Hypponen said in a tweet that F-Secure has spoken with Doctor Web and that the infection numbers look real. And Kaspersky Labs has now provided independent confirmation that Doctor Web’s numbers are reasonable and are in fact Macs.
According to Mac security firm Intego, Flashback-infected Macs show no symptoms at all, other than communication with Flashback’s command-and-control servers that could be detected by network monitoring tools. Although we haven’t seen confirmation of this with recent Flashback variants, earlier versions of Flashback tried to capture user names and passwords by injecting code into Web browsers and other network applications, like Skype. In such cases, the affected programs tended to crash frequently. Security firm Sophos says that along with stealing passwords, Flashback can also poison search engine results to perform
advertising fraud (by fraudulently increasing click-through rate) or to direct victims to further malicious content (though that seems unnecessary, if the Mac is already compromised).
More concerning is that Intego says it has seen dozens of variants of Flashback in the past weeks, indicating that the programmers behind Flashback are modifying it quickly to avoid detection and to take advantage of newfound vulnerabilities. That may render obsolete any advice for preventing, detecting, and removing Flashback. On a side note, Intego also says that it has evidence that Flashback was created by the same people who created MacDefender in 2011 (see “Beware Fake
MACDefender Antivirus Software ,” 2 May 2011 and “Apple Responds to Increasingly Serious MacDefender Situation,” 25 May 2011).
Detect Flashback Infection — So how can you tell if you’re infected? Security firm F-Secure posted instructions for detecting current Flashback infections; the instructions also include removal steps that we would dissuade anyone but advanced users from attempting.
That said, detection comes down to issuing the following defaults read commands in Terminal (F-Secure suggests only the first and last; the others extend the technique from Safari to Google Chrome, Firefox, and iCab). In each case, if you see “does not exist” at the end of the response from each command, you are not infected. (The defaults read command is entirely safe — it’s just attempting to determine whether some data exists in the Info.plist file within each application package.)
defaults read /Applications/Safari.app/Contents/Info LSEnvironment
defaults read /Applications/Google\ Chrome.app/Contents/Info LSEnvironment
defaults read /Applications/Firefox.app/Contents/Info LSEnvironment
defaults read /Applications/iCab\ 4/iCab.app/Contents/Info LSEnvironment
defaults read ~/.MacOSX/environment DYLD_INSERT_LIBRARIES
For a simpler approach, Marc Zeedar, publisher of Real Studio Developer magazine, has written a simple Test4Flashback application that encapsulates the defaults read checks and presents a dialog telling you whether or not you’re infected. It doesn’t attempt to do any removal at all.
Protect Yourself Against Flashback — In the meantime, if you are using 10.7 Lion and have not yet installed Java, hold off unless you need it. If you have installed Java in Lion or are using 10.6 Snow Leopard, immediately install Apple’s Java updates via Software Update to prevent infection from this particular variant of Flashback. And although uninstalling Java is difficult, you can disable it, either system-wide or in individual Web browsers (Flashback relies entirely on Web-based attacks, as far as we’re aware).
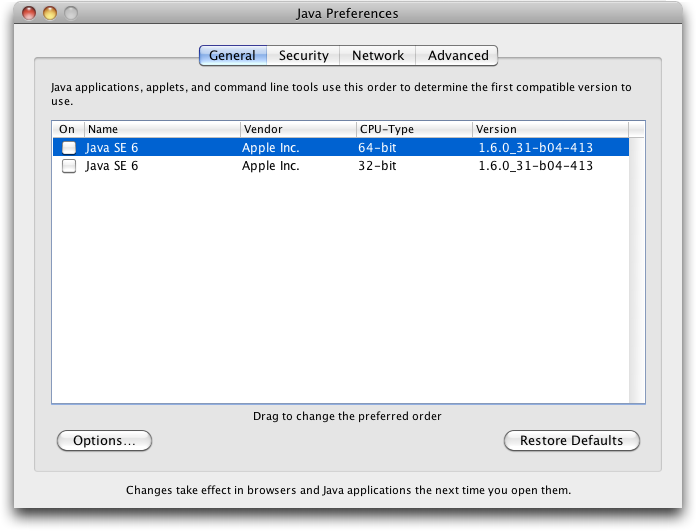
- To disable Java entirely on your Mac, open the Java Preferences utility in
/Applications/Utilitiesand uncheck the checkboxes. Don’t do this if you use CrashPlan or any other Java-based software, including some Adobe applications! -
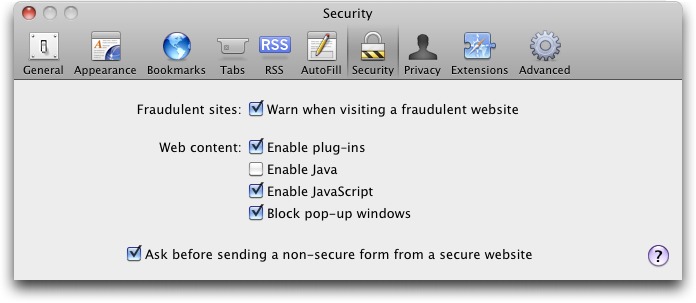
To disable Java in Safari, choose Safari > Preferences, and turn off Java in the Security pane.
-
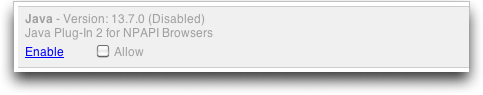
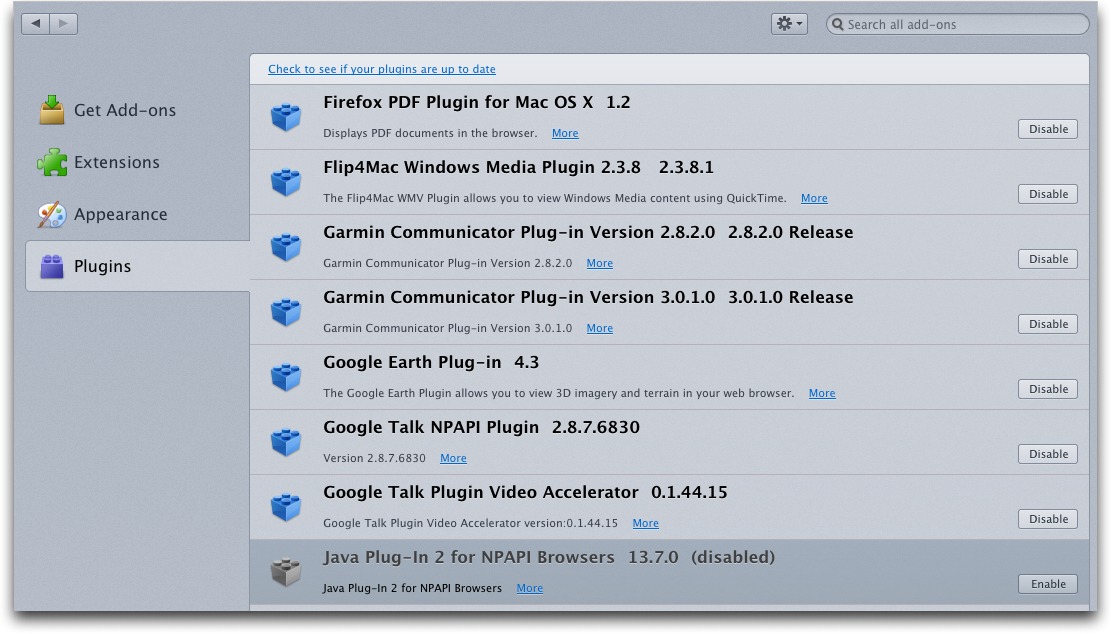
To turn off Java in Google Chrome, type
about:pluginsin the address bar, scroll down, and click the Disable link for Java Plug-In 2 for NPAPI Browsers. -
To turn off Java in Firefox, choose Tools > Add-ons, click the Plugins tab, and disable the Java Plug-In 2 for NPAPI Browsers.
If you need to use Java only occasionally, consider leaving it enabled in a browser that you seldom use, and rely on that browser for those specific sites — like Web conferencing tools — that require Java.
Installing antivirus software like Intego’s VirusBarrier will also provide protection, both from the software’s base functionality and because the Flashback malware doesn’t install itself if it detects certain antivirus programs.
Lastly, it’s worth noting that some variants of Flashback worm their way onto Macs not through exploiting Java vulnerabilities, but by fooling users into entering an administrator password. The only way you can protect yourself against such trickery is by being suspicious of any password request that doesn’t come in direct response to an action that you’ve just taken, such as installing a new piece of software that you downloaded intentionally.
Be careful out there.
How to Tell If Your Cloud Provider Can Read Your Data
With the tremendous popularity of services like Dropbox and iCloud there is, rightfully, an incredible amount of interest in cloud data security. Once we start hosting our most sensitive data with cloud services (or any third-party provider) it’s only natural to wonder how secure our data is when it’s in the hands of others. But sometimes it’s hard to figure out exactly who can look at our information, especially since buzzwords like “secure” and “encrypted” don’t necessarily mean you are the only one who can see your data.
How Cloud Providers Protect Your Data — In part because there are numerous ways cloud providers could protect your data, the actual implementation varies from service to service. All consumer cloud services are what we in the cloud world call public and are built for multi-tenancy.
A public cloud service is one that anyone on the Internet can access and use. To support this the cloud providers need to segregate and isolate customers from each other. Segregation means your data is stored in your own little virtual area of the service, and isolation means that the services use security techniques to keep people from seeing each other’s stuff.
Practically speaking, multi-tenancy means your data is co-mingled with everyone else’s on the back end. For example, with a calendar service your events exist in the same database as all the other users’ events, and the calendar’s code makes sure your appointment never pops up on someone else’s screen. File storage services do the same thing: intermingling everyone’s files and then keeping track of who owns what in the service’s database. Some, like Dropbox, will even store only a single version of a given file and merely point at it from different owners. Thus multiple users who happen to have the same file are technically sharing that single instance; this approach also helps reduce the storage needed for multiple versions
of a file for a single user.
Although multi-tenancy means co-mingling data, the cloud provider uses segregation techniques so you see only your own data when you use the service, and isolation to make sure you can’t maliciously go after someone else’s data when you’re using the system.
The cloud provider’s databases and application code are key to keeping all these bits separate from each other. It isn’t like having a single hard drive, or even a single database, dedicated to your information. That simply isn’t efficient or cost-effective enough for these services to keep running. So multi-tenancy is used for files, email, calendar entries, photos, and every other kind of data you store with a cloud service.
Not all services work this way, but the vast majority do.
Encryption to the Rescue? — A multi-tenancy architecture has two obvious problems. The first is that if there’s a mistake in the application or database the service runs on, someone else might see your data. We’ve seen this happen accidentally; for example, last year Dropbox accidentally allowed any user access to any other user’s account. There is a long history of Internet sites (cloud and otherwise) inadvertently allowing someone to manipulate a Web page or URL to access unauthorized data, and the bad guys are always on the lookout for such vulnerabilities.
The second problem, which has been in the press a lot lately, is that the cloud provider’s employees can also see your data. Yes, the better services usually put a lot of policy and security controls in place to prevent this, but it’s always technically possible.
One way to mitigate some of these concerns is with encryption, which uses a mathematical process coupled with a digital key (a long string of text) to turn your data into what looks like random gibberish. That key is necessary to decrypt and read the data.
Most cloud providers use encryption to protect your Internet connection to them (via SSL/TLS — look for https URLs) so no one can sniff it on the network. (Unfortunately, some large email providers still don’t always encrypt your connection.) Most of the time when you see “encryption” in a list of security features, this is what they mean. But encrypting data in transit is only half the battle — what about your data in the provider’s data center? Encryption of storage is also necessary for any hope of keeping your data secret from the cloud provider’s employees.
Some providers do encrypt your data in their data center. There are three ways to do this:
- Encrypt all the data for all users using a single key (or set of keys) that the cloud provider knows and manages.
- Encrypt each individual user’s data with a per-user key that the cloud provider manages.
-
Encrypt each individual user’s data with a per-user key that the user manages.
By far, most cloud services (if they encrypt at all) use Option #1 — keys that they manage and that are shared among users — because it’s the easiest to set up and manage. The bad news is that it doesn’t provide much security. The cloud provider can still read all your data, and if an attacker compromises the service’s Web application, he can usually also read the data (since it’s decrypted before it hits the Web server).
Why do this level of encryption at all? It’s mostly to protect data if a hard drive is lost or stolen. This isn’t the biggest concern in the world, since cloud providers have vast numbers of drives, and it would be nearly impossible to target a particular user’s data, if the data could be read at all without special software. It also means that providers get to say they “encrypt your data” in their marketing. This is how Dropbox encrypts your data.
Option #2 is a bit more secure. Encrypting every user’s data with an individual key reduces, in some cases, the chance that one user (or an attacker) can get to another’s data. It all depends on where the attacker breaks into the system, and still relies on good programming to make sure the application doesn’t connect the wrong keys to the wrong user. It’s hard to know how many services use this approach, but when done properly it can be quite effective. The major weakness is that the cloud provider’s employees can still read your data, since they have access to the keys.
Option #3 provides the best security. You, the user, are the only one with the keys to your data. Your cloud provider can never peek into your information. The problem? This breaks… nearly everything. First of all it means you are responsible for managing the keys, and if you lose them you lose access to your data. Forever. Also, it is extremely difficult — if not impossible — to allow you to see or work with your data in a Web page since the Web server can’t read your data either. Thus it works for some kinds of services (mostly file storage/sharing) and not others, and only for sophisticated users who are able to manage their own keys.
As is so often the case, these options reveal the tradeoff between security and convenience.
How to Tell if Your Cloud Provider Can Read Your Data — In two of the three options I listed above, the provider can read your data, but how can you tell for yourself if this is the case?
There are three different (but similar) indications that your cloud data is accessible to your provider:
- If you can see your data in a Web browser after entering only your account password, the odds are extremely high that your provider can read it as well. The only way you could see your data in a Web browser and still have it be hidden from your provider is if the service relied on complex JavaScript code or a Flash/Java/ActiveX control to decrypt and display the data locally.
-
If the service offers both Web access and a desktop application, and you can access your data in both with the same account password, odds are high that your provider can read your data. This is because your account password is also probably being used to protect your data (usually your password is used to unlock your encryption key). While your provider could technically architect things so the same password is used in different ways to both encrypt data and allow Web access, that really isn’t done.
-
If you can access the cloud service via a new device or application using your account user name and password, your provider can probably read your data. This is just another variation of the item above.
This is how I knew Dropbox could read my files long before that story hit the press. Once I saw I could log in and see my files, or view them on my iPad without using a password other than my account password, I knew that my data is encrypted with a key that Dropbox manages. The same goes for the enterprise-focused file sharing service Box (even though it’s hard to tell when reading their site). Of course, since Dropbox stores just files, you can apply your own encryption before Dropbox ever sees your data, as I explained last year at Securosis.
And iCloud? With iCloud I have a single user name and password. It offers a rich and well-designed Web interface where I can manage individual email messages, calendar entries, and more. I can register new devices and computers with the same user name and password I use on the Web site. Thus, from the beginning, it was clear Apple had the capability to read my content, just as Ars Technica reported recently.
That doesn’t mean Dropbox, iCloud, and similar services are insecure. They generally have extensive controls — both technical and policy restrictions — to keep employees from snooping. But it does mean that such services aren’t suitable for all users in all cases, especially businesses or governmental organizations that are contractually or legally obligated to keep certain data private.
Doing It Right — The backup service CrashPlan is an example of a service that offers flexible encryption to fit different user needs, with three separate options. (For more on choosing the appropriate encryption method for CrashPlan, see Joe Kissell’s “Take Control of CrashPlan Backups.”)
First, by default, your data is encrypted using a key protected by your account password. This still isolates and protects it from other users, while enabling you to view file information through the CrashPlan Web site and the CrashPlan Mobile app. But CrashPlan’s employees could still access your data.
Second, if you want more security, you can add a separate backup password that only you know. This approach still allows access through the CrashPlan Web site and the CrashPlan Mobile app, but CrashPlan employees can’t see your data except (maybe) during a Web session after you enter your separate password. Attackers can’t access your data either, though your password may be susceptible to brute force cracking or social engineering.
Third and finally, you can generate your own per-device encryption keys, which CrashPlan never sees or knows about, rendering your backups readable only by you (or anyone who can beat the key out of you — never underestimate the power of a wrench — props to xkcd!). You could technically use a different encryption key on each device (or share, your choice) so that even if one system were to be compromised, it wouldn’t allow access to backups from your other devices. Clearly, this is much more difficult to manage and well beyond the needs or capabilities of the average user (heck, even I don’t use it).
So if you want to be certain that your data is safe from both attackers and the cloud provider’s employees snooping, look for services that offer additional options for encrypting data, either with a password or an encryption key known only to you. If such an option isn’t available at the next cloud service you check out, you’ll know that the provider’s employees could technically read your data. And when the next big story of a cloud provider reading data hits the headlines, you can smugly inform your friends that you knew it all along.
TidBITS Watchlist: Notable Software Updates for 9 April 2012
TinkerTool 4.8 — Marcel Bresink has released version 4.8 of TinkerTool, his system utility that lets you adjust a variety of settings under Mac OS X’s hood (covered previously by Matt Neuburg; see “Lion Frustrations? Don’t Forget TinkerTool,” 29 October 2011). While TinkerTool can still be used with Mac OS X 10.6 Snow Leopard, this update focuses on adding new ways to control system behavior in 10.7 Lion, including Launchpad and Mission Control animations, the delay when moving between Spaces and Mission Control, and the capability to open Dock Stacks by
scrolling. You can also add pop-up notifications to the Dock when playing a new track in iTunes 10.4 or later, enable copy operations when previewing text files in Quick Look, and configure a less-precise edge to windows when grabbing to resize them. If you’re running a Mac OS X version prior to 10.6 Snow Leopard, TinkerTool is available in separate applications for use with those previous iterations (TinkerTool Classic for 10.1 Puma, 10.2 Jaguar, and 10.3 Panther; TinkerTool Classic Generation 2 for 10.4 Tiger and 10.5 Leopard). (Free, 1.7 MB, release notes)
Read/post comments about TinkerTool 4.8.
Hazel 3.0.4 — Noodlesoft continues to refine its file cleanup utility with Hazel 3.0.4 after its recent update to version 3.0 (see “Hazel 3.0.1,” 4 March 2012). This release modifies a number of user interface behaviors, including the capability to click on tokens to add them when editing patterns and display of a pause icon for paused folders in the Run Rules submenu. It fixes a problem where a deleted custom token wasn’t deleted from patterns using it and a bug where multiple custom tokens were created with the same name. The update also fixes incorrect formatting of
custom tokens with numbers, prevents Growl messages from converting slashes to colons, prevents a crash when opening rules that used the old keywords attribute, and fixes a bug using the copy action with the Throw Away Duplicate Files option set. ($25 new, $10 upgrade, 5.0 MB, release notes)
Read/post comments about Hazel 3.0.4.
SpamSieve 2.9 — C-Command Software has released SpamSieve 2.9 to address a bevy of maintenance issues. This update improves the spam-filtering software’s training regimen for “good” Exchange messages in Apple Mail as well as handling of incoming messages in Microsoft Outlook. The release adds support for Growl notifications via GNTP and support for training messages as spam via the Herald notification plug-in. Other changes include adding a new auto-training parameter in the score script that can override the setting in preferences on a case-by-case basis, modifying the mailbox moving behavior of the Change Settings
command in Apple Mail, and adjusting drone AppleScripts for better troubleshooting. SpamSieve is also now code-signed for compliance with OS X 10.8 Mountain Lion’s Gatekeeper security feature. The update is rounded out by improvements in handling errors and fixes to other bugs. ($30 new, free update, 9.3 MB, release notes)
Read/post comments about SpamSieve 2.9.
App Tamer 1.2.1 — St. Clair Software has released App Tamer 1.2, which gives some props to our own Adam Engst for the change to its menu bar icon. The St. Clair Software blog writes that this update to the CPU-monitoring utility started as a user request for a colored menu bar icon, but it evolved after reading about Adam’s account of an unseen CPU process draining the battery of his MacBook (see “Solving iCloud-Related Slowdowns in Lion,” 16 February 2012). To better get your attention, App Tamer 1.2 now dynamically
colorizes its menu bar icon (turn it on in App Tamer’s preferences), with the color getting brighter and more alarming (moving from pale yellow to red) as your CPU usage climbs toward 100 percent. The menu bar icon also displays a speedometer-like needle to reflect processor load, and you can choose to display the percentage next to the icon. Version 1.2 also fixes an issue that prevented viewing of all processes launching and quitting, and it enables you to double-click App Tamer to open its window if the application icon isn’t in the Dock. A quick 1.2.1 update solves a problem when running under very high load and fixes the menu bar icon in Mac OS X 10.5 Leopard. ($14.95 new, free update, 3.6 MB, release notes)
Read/post comments about App Tamer 1.2.
ExtraBITS for 9 April 2012
Read on for a comprehensive look from Stephen Fry at how Apple’s competitors have repeatedly dropped the ball since the release of the iPhone, and a perspective-setting article from Nick Bilton of the New York Times about how companies other than Apple that use questionable Chinese labor to manufacture devices have been suspiciously silent about the issue.
Stephen Fry on What the iPhone’s Competitors Missed — Apple is at the top of its game now, but that level of success isn’t entirely attributable to its products. Multi-hyphenate Stephen Fry has been carrying multiple cellular phones — and smartphones — since long before 2007, and he writes about how the failures of Apple’s competition since the introduction of the iPhone have helped Apple reshape the market.
Too Much Silence on Working Conditions — Judging from most press reports over the last couple of months, you’d think Apple has done a horrible job of protecting the safety of the Chinese workers who manufacture most of its devices. Foxconn, one of Apple’s largest manufacturers, is actually a behemoth that builds cell phones, computers, tablets, and other technology for most of the big companies around the world. Nick Bilton of the New York Times started asking these other firms — including Dell, HP, Samsung, and Microsoft — about how they’re
responding to working conditions. The answers? Silence, pat press releases, and very little actual information.