TidBITS#1166/25-Mar-2013
“You’re not paranoid, they really are out to get you.” That’s the lesson of this week’s issue, which — we swear we didn’t plan this — focuses largely on security issues. First, Glenn Fleishman explains how a vulnerability in Apple’s iForgot password-reset page made it possible to reset someone’s password knowing only their date of birth. Apple fixed it immediately, but who knows how long it has been available? Apple also released iOS 6.1.3 to fix a month-old bug that allowed someone who gained access to your iPhone to bypass the passcode and get into the Phone app. Going proactive, Apple last week implemented two-factor authentication for Apple IDs to prevent unauthorized password changes, purchases, and support requests — Glenn Fleishman has all the details and necessary instructions. And with the last word on security for the issue, Joe Kissell contributes a FlippedBITS column that thoroughly debunks four common password myths. Beyond security, Glenn also passes on news about RSS reader NetNewsWire’s future, and Adam Engst shares the results of his testing of PDFpen 6.0’s new export-to-Word feature. Notable software releases this week include Skype 6.3 and PopChar X 6.2.
iOS 6.1.3 Blocks Passcode Bypass Bug
Apple has quietly released iOS 6.1.3 to fix a bug that could enable someone to bypass an iPhone’s passcode and access the Phone app. The only other change — beyond a variety of security fixes — is noted merely as “improvements to Maps in Japan.” The passcode bypass bug would allow someone with access to the iPhone to make calls, browse contact information, and access photos — it became public over a month ago.
The update is available for all iOS devices running iOS 6, including the iPhone 3GS and later, the iPad 2 and later, and the fourth-generation iPod touch and later. As always, an over-the-air update accessed from Settings > General > Software Update on the device itself will be faster to download and install, though you can of course download and install via iTunes as well. The over-the-air version is only 18.2 MB for my iPhone 5.
Since none of the security-related bugs fixed are all that serious, unless you’re relying on Maps in Japan, I suggest that you hold off on this update until others have determined whether or not it introduces any new problems.
One additional warning. Since one of the security holes closed by iOS 6.1.3 was relied upon by the evasi0n jailbreak, if you wish to jailbreak your iOS device, don’t upgrade. Of course, that also leaves you open to the passcode bug, but that’s one of the tradeoffs of a jailbroken world.
Black Pixel Sketches Future of NetNewsWire
Many Macintosh eyes have been on Black Pixel since the recent announcement by Google that it would shut down its Google Reader RSS news-feed viewer, aggregator, and synchronization service. Black Pixel is the current owner of NetNewsWire, the most popular Mac newsreading software, which relies on Google Reader for syncing across Macs and iOS devices. Black Pixel posted on its blog that it has been steadily working on a new release of NetNewsWire for Mac and iOS, and has plans to start its own sync service. (For other options, see “Explore Alternatives to Google Reader,” 18 March 2013, and be sure to read
“Thoughts Prompted by Google Reader’s Demise,” 14 March 2013.)
NetNewsWire was originally developed by Brent Simmons and released in 2002. He sold it to NewsGator in 2005, but essentially kept doing the same job, updating the software and expanding it to iOS. In 2008, NewsGator switched from a paid and “lite” release to a single ad-supported free version; you could pay to remove ads. At Simmons’s suggestion, NewsGator sold NetNewsWire to Black Pixel in June 2011. Black Pixel has released compatibility upgrades since then.
In the intervening time, Black Pixel chief Daniel Pasco writes, the company has overhauled the Mac version and rewritten the iOS versions from scratch. At the time of the sale to Black Pixel, Simmons realized the amount of work he saw in front of him as a one-man shop to bring NetNewsWire up to date, and was happy to hand it off to a team of developers.
Pasco writes that Black Pixel knew it would need a Google Reader alternative — since Google+ appeared and then sharing features were removed from Google Reader, it has been clear to observers that Google Reader was operating on borrowed time.
Black Pixel originally pursued using iCloud and its Core Data support for syncing database updates. But, as we’ve heard privately and read publicly from many developers who have tried to build syncing services on top of Apple’s offering, iCloud ultimately disappointed. The cloud service may have robust features, but the interfaces it exposes and its options don’t seem to match up well with developers’ needs. Black Pixel will build its own sync option, instead of using iCloud.
Exploit Allowed Easy Apple ID Password Reset
The Verge reported that Apple’s Apple ID iForgot password-reset page had an exploit documented in a publicly available set of instructions. The exploit required a modified URL to open the iForgot page, coupled with knowledge of a user’s email address and date of birth. (The Verge does not link to the instructions, nor do we.) Apple quickly shut down the iForgot page, and launched a version later in the day that changed the process.
One’s date of birth is unfortunately an easy bit of information to find — it’s asked for by social networking services like Facebook and Google+, and is thus often available to our online “friends” that way. (Makes you wonder if “friending” all those people you barely know was a good idea, doesn’t it?) It’s also easy to search Twitter for birthday wishes and make some educated guesses about what year a particular person was born. And that’s even before you take into account the fact that our information may already be floating around in hacker hideouts due to previous breaches of credit databases and other data stores. Date of birth information can also be obtained through cheap online identity searches.
By the end of the day after the news appeared, Apple had re-enabled iForgot, offering two paths to reset a password: either using the rescue email address specified in an Apple ID account (if that had been set) or by answering a series of security questions and answers created during account setup (or later, when Apple added this feeble validation option to all accounts).
The exploit didn’t affect users who have switched to two-factor authentication, introduced by Apple only a day earlier in a number of English-speaking countries (see “Apple Implements Two-Factor Authentication for Apple IDs,” 21 March 2013). In Apple’s two-factor system, a password can be reset only with possession of a trusted device — one that’s been verified with the Apple ID account — and the recovery key. (Loss of a password and either of those other elements renders an Apple ID account permanently unrecoverable!)
The Verge and other sites don’t explain why resetting your password would be useful to someone wanting to access your account. Surely, if the instructions to create a new password are sent to your email address, the attacker must already have your login credentials? Not necessarily.
The attacker might have found a way to read your email by stealing or gaining temporary physical access to one of your devices, or by cracking an unrelated email account to which the primary address is forwarded. In such cases, he can’t log in to any of the other services or make purchases using that email account.
But if an Apple ID account, for which the hijacker can read email, even temporarily, can have its password reset, that would enable future access to iTunes purchases, contacts and calendar events stored in iCloud, Find My iPhone tracking, and other associated data. Of course, the jig may be up the next time the account owner needs to enter the correct password and finds it doesn’t work. But by then, enough damage may have been done to be troublesome or costly.
That makes it a little peculiar that the revised iForgot page offers to send password-reset instructions to a backup email address since many people have multiple addresses set up with a single email program. If the bad guy has physical access to a device, and hasn’t just figured out to a tap into a single email account, the reset instructions would be in his grasp as well. But there is only so much that Apple can do. There must be ways to reset a password, and sending instructions via email is one reasonable path.
Frankly, the sort of exploit Apple closed is less likely to be used by an anonymous miscreant than by someone close enough to you to find out your date of birth and gain access to your email at just the right moment to receive the reset email and follow its instructions. Teenagers and young adults are probably most susceptible, given promiscuous sharing of devices and information, plus sensitive data. Can you imagine the drama of a jilted lover using this technique to track the other person via Find My iPhone?
FlippedBITS: Four Password Myths
In the course of writing “Take Control of Your Passwords,” I came across — and attempted to debunk — quite a few myths involving password security. Of course, I encourage you to buy the book to read about password problems and my recommended solutions in detail, but for this installment of FlippedBITS, I want to focus on four extremely common misconceptions about passwords, all of which can lead to dangerous behavior.
1: Nine Is Enough — I want to begin with a myth I propagated myself in my now-obsolete 2006 book “Take Control of Passwords in Mac OS X.” Although what I said in that book was reasonable based on the available data at the time, I grossly underestimated the rate of technological progress. So, I hereby retract and apologize for a particular piece of advice I gave back then: I said that if you chose a random 9-character password consisting of upper- and lowercase letters, digits, and punctuation, you’d be effectively safe from any attack, because it would take centuries, on average, for even a supercomputer to crack such a password by brute force.
Well, it turns out that I was off by a few orders of magnitude. Today, with off-the-shelf hardware and freely available cracking software, a nine-character password can be broken in a maximum of five and a half hours (that’s maximum, not minimum!). If your password contains nine or fewer characters, regardless of how random it may be, it’s about as unsafe as a Wi-Fi connection protected with WEP (which is to say, safe against only the most casual snooping).
If nine characters are too few these days, how long should a password be? I wish I could give you a straight answer, but the truth is “it depends.” For example, I could claim, with some justification, that a random 14-character password is effectively safe from brute-force attacks given today’s technology. But I’d have to qualify that in a few different ways.
First, I have no idea what tomorrow’s technology will look like. Maybe a few years from now, someone will develop a quantum computer that can crack any 14-character password in the blink of an eye. I don’t expect that to happen so soon, but I’d be foolish to bet against it.
Second, not all encryption techniques are equally secure. A password that’s protected with a weak encryption algorithm might be crackable in seconds, whereas the same password, encrypted with a better method, could thwart a brute-force attack for years. Related to this is that some password security systems put additional barriers in place to slow down the rate at which passwords can be guessed. Although these aren’t foolproof (as I discuss in a moment), they can, in certain situations, give a simple password much higher effective strength.
Third, length isn’t the only factor that affects a password’s strength. As illustrated brilliantly in the xkcd comic Password Strength, even a password consisting entirely of lowercase English words (such as correct horse battery staple) can be just as strong as a shorter but more random password with a mixed character set. That’s because a password’s entropy (a mathematical approximation of how hard the password is to guess) can come from length, character set complexity, randomness, or any combination of these. Higher-entropy passwords are more resistant to automated attacks, but there’s more than one path to entropy. (If you’d like
to test a given password’s entropy, there are many online tools that let you do so. I quite like the zxcvbn tool for this purpose.)
We can take some comfort in the fact that each additional character in a password increases its strength exponentially. So, if we were to restrict ourselves to just 26 lowercase letters, a 10-character password wouldn’t merely be 10 percent better than a 9-character password — it would be 26 times better! There are over 5 trillion possible passwords consisting of nine lowercase letters (26^9), but make it ten letters (26^10), and there are more than 141 trillion possibilities. That means a system that can crack a 9-character random password in 5.5 hours could take over 500 hours to crack a 10-character random password — a huge difference.
Even so, 500 hours is too little for my comfort. You could make that more than 500 years by choosing a 12-character password, which certainly seems safe enough for all practical purposes. But then, that’s what I thought about 9-character passwords seven years ago. So, when I suggest 14 as a safer number, I’m building in enough of a buffer to account for a few years of technological development, not in any way saying that such a password will in fact be uncrackable for the over 4,000 millennia it would take at today’s rate.
2: Old Tricks from Old Dogs — I’ve encountered quite a few people — including some major names in the Mac world you’d recognize — who have developed mnemonic techniques for creating and remembering passwords that they imagine to be quite strong. Although specifics vary, there tends to be a consistent element or easily constructed pattern in each password, along with some site-specific portion. For example, maybe I use zombieGooCats for Google and zombieAppCats for Apple. (In reality, most people I know who do this sort of thing have far more sophisticated techniques, but you get the general
idea.)
I myself once (cough) advocated such an approach, but I’ve since seen the light. The problem with all such tricks — and that also goes for “leet” or “1337” (replacing letters with similar-looking numbers), using patterns of keys on a keyboard, and so on — is that no matter how clever you think you are, hackers and their advanced cracking algorithms are smarter. These tools can test a vast number of subtle patterns that few humans would notice, which means even a fairly long, fairly random-looking password might in fact be quite easily guessable. Because remember, we’re not worried so much about humans guessing your password but about machines guessing it, and machines are likely to test lower-entropy passwords —
especially those based on common mnemonic techniques — long before higher-entropy passwords. (And, if you use the same technique to construct all your passwords from patterns, an attacker who learns one or more of your passwords has an even bigger leg up in guessing the rest.)
More to the point, any technique that relies on your brain for creating and remembering all your passwords is, in my opinion, a waste of mental effort that could be put toward more useful pursuits, such as thinking up bad puns. We have computers and iPads and iPhones and other devices to do this sort of tedious work for us, and they’re much better at it than we are. Let a password manager such as 1Password or LastPass generate, remember, and enter passwords for you, and then you can make them as long and random as you like — it’s no more effort for an app to make a 32-character password than a 10-character one. Sure, you’ll still need to remember a few
passwords, but if you’re doing it right, it’s only a few. (I have only 5 passwords memorized, out of more than 600.)
3: One Password to Rule Them All — Speaking of password managers, these tools make it easy to create a unique random password for every single site and service that uses passwords, and I recommend doing so. I can’t emphasize strongly enough what a bad idea it is to use the same password in more than one place — even if it’s a great password. The fact that reusing passwords is entirely unnecessary if you rely on an automated tool makes it that much more egregious an offense.
Why is it so bad to reuse passwords? Well, it seems like every week or so, there’s another news report about some big company experiencing a security breach of some sort in which thousands or even millions of passwords are lost, stolen, leaked, or hacked. This happened recently to Evernote; before that, a long list of other companies had passwords compromised – Facebook, LinkedIn, Twitter, and more. You can bet this trend will continue.
Now, if someone hacks Amazon.com’s servers and gets your password, that’s bad news, no question about it. But if all your passwords are unique, at least the damage will be limited to that one account. On the other hand, if you use the same password for iCloud, PayPal, Twitter, Gmail, and so forth, you run the very real risk that the attacker may try your password at all those other sites, too, doing considerably more damage.
I’m saying: using unique passwords — even strong unique passwords — doesn’t guarantee security. But it does enable you to contain the damage if your password for any one site is compromised. The people most likely to be harmed by password breaches are those who are oblivious to the problem of password reuse. Don’t be one of them!
4: Online vs. Offline Attacks — Earlier, I mentioned that some sites and services put barriers in place to slow down or derail automated attacks. For example, if you mistype your password once, you might get one or several additional chances to enter it — but with increasing time delays between guesses. And if you enter it incorrectly several times in a row, you might be locked out entirely for a period of time, or until you take some independent action to confirm your identity. The whole point of these barriers is to prevent an automated system from trying many passwords per second until it breaks into your account.
While it’s an excellent idea for developers to employ such barriers, they aren’t as strong as they might appear. That’s because most successful attacks don’t go through the front door, as it were. The real danger comes when, due to a leak or security breach of some kind, someone gets hold of an encrypted file or database that holds all the passwords for a site. With the file in hand, they can perform what’s known as an “offline” attack — they hammer on the raw file with automated tools that check billions of possible passwords per second. Because they’ve entirely circumvented the security measures that slow down guessing, they can potentially decrypt massive numbers of passwords in a short period of time.
(I’m simplifying the story here. Smart developers can also use a combination of techniques — the key terms to look for are “salting” and “hashing” — to frustrate offline attacks, but all too often, a programming error or infelicitous security choice leaves gaping holes that hackers can exploit.)
So, don’t assume you can use a short, simple password because you can’t see any way an attacker could try billions of passwords a second. You’d be surprised what someone can do, particularly given physical access to the computer where the password is stored. Your best defense is to use high-entropy passwords (which take longer to guess) and make sure each one is unique.
Don’t Worry, Be Happy If I’ve increased your anxiety about passwords by telling you what’s wrong with techniques you depend on, I’m sorry. Well, only a little bit sorry, because I want you to have just enough discomfort that you take action to improve your password security and reduce the chance that bad things could happen to your digital life. For extensive details on passwords, including further threats and risks you might face — and my stress-free, three-point strategy for password security — please pick up a copy of “Take Control of Your Passwords.”
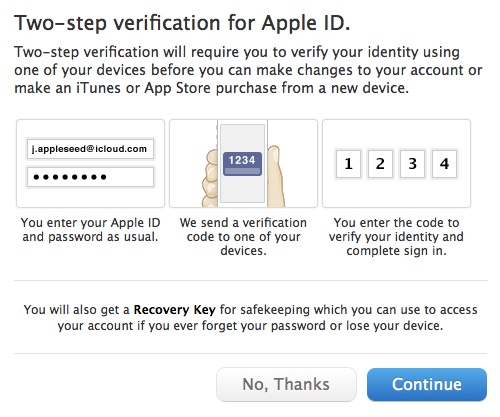
Apple Implements Two-Factor Authentication for Apple IDs
Apple quietly added optional two-factor authentication for Apple ID accounts last week, joining the likes of Google, Dropbox, PayPal, Facebook, and an ever-growing number of other sites. This additional layer of authentication helps protect the increasingly important Apple ID accounts that millions of Mac and iOS users rely on for iTunes Store and App Store purchases, iCloud logins and data sharing, support from Apple, and more.
Although it’s optional, we recommend enabling two-factor authentication as soon as is practical for you. Since online criminals can use compromised Apple ID accounts both to siphon money from credit cards and to take over your digital identity, it’s no longer paranoid to worry about your password being stolen. Although it may seem like a hassle, and setup should be done with care, Apple’s two-factor authentication will not impact your life significantly. Apple says there are only three situations in which two-factor authentication will be invoked:
- When you sign in to the My Apple ID site to manage your account.
- When you make a purchase from the iTunes Store, App Store, or iBookstore from a new device.
-
When you get Apple ID-related support from Apple.
Factoring the Security Equation — The “factors” in two-factor authentication refer to two distinct private elements one must know or have to perform a successful login. The first factor is typically a password, as it still is with Apple IDs. The second is an “out-of-band” element: a code that can only be known or created using separately provided hardware or separately registered software. The out-of-band part is important to ensure that someone who already knows your password or has gained access to your computer cannot also obtain the second factor through the same medium.
Two-factor authentication used to be wonky, but with the rise in online crime, we’re seeing increasingly widespread support. I have two separate keyfobs, one for PayPal/eBay and another for E*Trade, from which I have to enter a six-digit number whenever I log in to those services. That number changes every minute. Google offers Google Authenticator, a mobile app for iOS, Android, and BlackBerry that can provide the same sort of code more
conveniently, once you’ve associated it with your Google account. Dropbox can use Google Authenticator, too, which is handy, relying on a separately registered and generated entry in the app. Even Facebook offers two-factor authentication through both SMS text messages and the Facebook iOS app. Many other services without apps also rely on SMS text messages to send a code to a mobile device under your control in order to provide the out-of-band component.
This two-factor method replaces the “security questions” that Apple has long relied on, much like many other companies. These questions are typically drawn from a list of possibilities like, “Who was your best friend in school?” But the questions may be ambiguous and can often be hacked easily by identity thieves hoovering up your personal details by searching Google, Facebook, or other personal information services. (In “Take Control of Your Passwords,”
Joe Kissell recommends coming up with what is essentially a passphrase — not a truthful answer — for each security question.)
Worse, as Mat Honan amply documented when his own accounts were hijacked, crackers can sometimes take over an account using a combination of social engineering and logical failures in password-reset procedures. At one point, Amazon allowed you to add an email address by phone if you had the last four digits of a credit card on file. However, you could also add a credit card by phone. Crackers realized they could add the credit card in one call, hang up, and then call back to add an email address they owned using the stolen (but still active) or faked (but validly formulated) card number they’d just provided. They could then get a password-reset message sent
to their email address.
Honan documented that with an Amazon account, an attacker could then view the last four digits of other stored credit card numbers for that account, and use that information to reset passwords or add email addresses to an Apple ID or accounts at other sites.
These attacks fail when the miscreant must both reset the password and either have physical possession of an unlocked device owned by the target or intercept SMS messages bound for that person. For sophisticated attacks targeted at an individual — say someone involved in government or corporate espionage or even a particularly messy divorce — two-factor authentication may still not be enough, but it’s more than sufficient to prevent the commonplace drive-by assaults on one’s identity.
Factor Your Decision — Before you set up Apple’s two-factor authentication, consider what the future looks like after the switch, as there are pluses and minuses with the new method.
On the upside, consider:
- No thief with your password alone can change your password, have Apple make account changes by phone, or gain access to your account to make iTunes Store, App Store, or iBookstore purchases from a new device.
-
No more security questions to answer and remember!
-
You can reset your password securely (using a linked device and a special recovery key described below) if you forget it or believe it was compromised.
But there are a few downsides, too:
- You must be able to receive SMS messages, or be set up with notifications via Find My iPhone on a particular iOS device. (Apple’s assumption appears to be that both reception of SMS messages and Find My iPhone require physical possession of a specific piece of hardware, whereas messages sent via iMessage, for instance, could appear on multiple devices.)
-
You can permanently lose access to your account in a particularly complicated scenario that’s unlikely, but possible. As Apple describes in a support note, you can reset access to an account as long as you have two of the following: the account password, access to a “trusted” device associated with the account, and a special recovery key generated when you set up two-factor authentication that’s used as a last resort. But if you have only one or none of those, your account is dead forever. “You will need to create a new Apple ID,” Apple writes, and that is guaranteed to be annoying at best.
And there are two kinds of access that two-factor authentication doesn’t protect:
- It doesn’t prevent email from being accessed with just the knowledge of the password. Someone could still retrieve your email from a me.com, mac.com, or icloud.com address with just the account name and password. That would in turn still let an attacker invoke password resets for other services that you set up using an Apple-managed address.
-
You can log into the iCloud Web site with just the password, and use all the services there, including Mail, Contacts, Calendar, Notes, Reminders, Documents in the Cloud, and even Find My iPhone, from which your devices can be erased (you are backing them up, aren’t you?).
Finally, if you made any significant changes to your Apple ID account in the last few days, Apple won’t let you turn on two-factor authentication for three days. And if your Apple ID password is too weak for Apple’s tastes (see “FlippedBITS: Four Password Myths,” 20 March 2013), Apple forces you to change it, and then forces you to wait for three days.
Enable Apple’s Two-Factor Authentication — If you’re ready to go, follow the steps listed in Apple’s support note if you’re in a supported country, or read our version below. (Apple has rolled out two-factor authentication in the United States, the United Kingdom, Australia, Ireland, and New Zealand, and plans to add additional countries over time. Perhaps it’s a localization issue.)
- Navigate to the My Apple ID site, click Manage Your Apple ID, and log in using your current account information.
-
Click Password and Security on the left, answer the security questions shown, and click Continue.
-
Under the “Two-Step Verification” heading and text at the top, click the Get Started link.
-
Apple then presents three screens of information, benefits, and warnings. Read each one and click Continue on the first two, then Get Started on the last one.
-
Apple displays a list of iOS devices associated with your account and lets you add SMS numbers for mobile phones. When you are finished verifying devices, click Continue.
- If you click Verify, Apple sends a code to the associated device via Find My iPhone. But, cleverly, if your device is locked with a PIN, unlike an SMS or iMessage, Apple prompts you to unlock iOS first to get the code. You may have problems if you have multiple Apple IDs because Find My iPhone can be associated with only one Apple ID. For instance, if you use
[email protected]for calendars and contacts on an iPad, that’s the account Find My iPhone will use, and you won’t be able to associate that iPad with another Apple ID registered under[email protected]. -
If you click “Add an SMS-capable phone number,” Apple sends the code in an SMS message. That works for connecting an iPhone that’s associated with a different Apple ID via Find My iPhone or a completely different mobile phone, even one owned by someone you trust. Happily, the SMS message is free.
- If you click Verify, Apple sends a code to the associated device via Find My iPhone. But, cleverly, if your device is locked with a PIN, unlike an SMS or iMessage, Apple prompts you to unlock iOS first to get the code. You may have problems if you have multiple Apple IDs because Find My iPhone can be associated with only one Apple ID. For instance, if you use
-
Apple now provides you with a 14-character recovery key that, if lost, cannot be recovered by anyone. Click Continue or Print Key to proceed. Apple recommends you write down your recovery key and don’t store it on your Mac. That’s reasonable advice, although if you have a tool that lets you store items with strong encryption (such as 1Password or Yojimbo) and secure that tool’s database with a strong password that’s not stored on the computer, you’re not tempting fate.
-
You have to re-enter the recovery key to prove that you really wrote it down! Type it in again, and click Confirm, which lights up only if you’ve entered the key correctly.
-
A final warning screen explains once again how completely messed up your life will be if you lose two or three of the elements required to reset your account. Select “I Understand the Conditions Above” and click “Enable Two-Step Verification.” The Manage Your Security Settings page now shows “Two-step verification is enabled.”
You will receive email notification of the change to all associated accounts immediately afterwards — and I do mean immediately, as mine arrived within a few seconds.
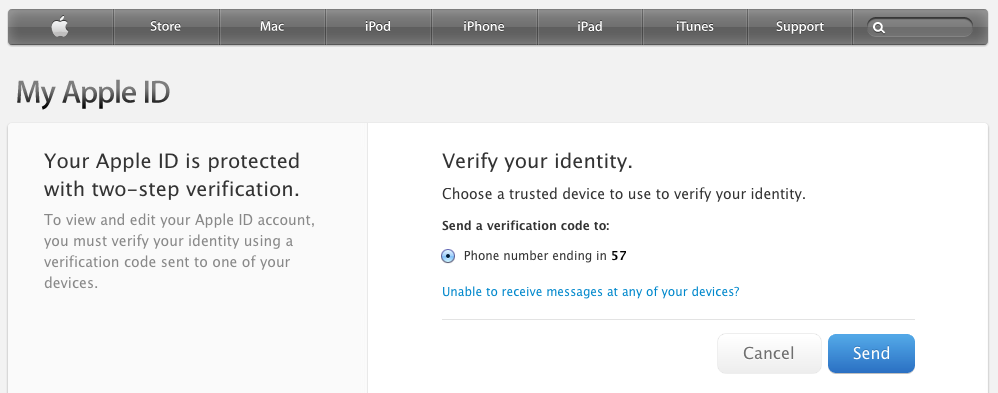
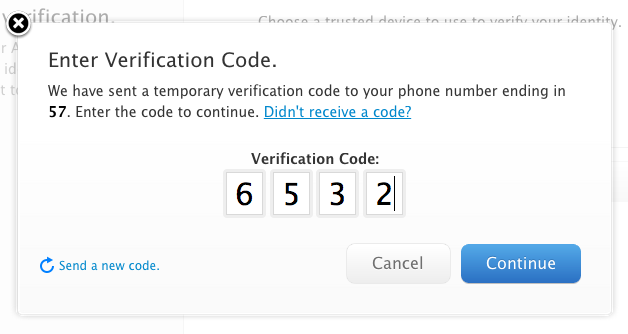
From then on, any time you access one of Apple’s protected services, such as the My Apple ID site’s Manage My Apple ID section, you’re asked which method you want to use to verify. Select it and proceed, and a code is sent. Enter that code, and you’re all set.
Not a Universal Solution — Two-factor authentication doesn’t solve all problems associated with validation and identity theft, but it solves some of the most important ones: password resets for account hijacking, purchases made through Apple-related services on new devices, and phone-based social engineering.
I’ve turned it on for the account I use for purchasing items, and recommend the same for all of you. Just make sure you have all your ducks and devices in a row (associated with the appropriate Apple ID and at hand) before you start!
PDFpen 6.0 Adds Word Export
The latest version of PDFpen, Smile’s PDF manipulation software, adds the capability to export a PDF to Microsoft Word format, supports Auto Save and Versions, adds an editing bar for quick access to common tools, and can print annotations at the end of a document.
TidBITS Watchlist: Notable Software Updates for 25 March 2013
Skype 6.3 — Microsoft has released Skype 6.3, a maintenance release to the Internet telephony app with a smattering of new features. The update adds a slideshow view that displays other participants when you are the current speaker in a group call (including group calls when someone else is screen sharing). It also adds an in-call dial pad for generating DTMF (dual-tone multi-frequency) tones, which is displayed after pressing the dial pad in the call toolbar while you’re on a call with a phone number. The release also brings several improvements, including the capability to sign into
Skype when using Ecamm’s Call Recorder software and optimized preference menus for Danish, Italian, Japanese, and Korean localizations. (Free, 37.5 MB, release notes)
Read/post comments about Skype 6.3.
PopChar X 6.2 — Ergonis Software has released PopChar X 6.2 with a couple of improvements for quickly finding special characters in the font discovery utility. The update adds a Command-F keyboard shortcut to enter the search field, and you can also start typing a search string when the cursor is in PopChar’s character table. The contextual menu gets a couple of additions, including a Copy Character Description command that copies a brief summary of the selected Unicode character and a Copy Font List command that copies a list of font names. The release also adds support for Unicode 6.2, improves appearance of the
group pop-up button (particularly for Retina displays), fixes a bug that prevented some fonts from being detected in certain apps (such as Microsoft Word), and provides a workaround for window flickering on OS X 10.8 Mountain Lion. Finally, you can now manually launch PopChar and open the PopChar window by double-clicking its icon in the Finder. Previously, double-clicking the Finder icon closed the PopChar window if it had already been open. (€29.99 new with a 25-percent discount for TidBITS members, free update, 3.6 MB, release notes)
Read/post comments about PopChar X 6.2.
ExtraBITS for 25 March 2013
One quick recommendation for something else to read this week — a warning about Mac-focused Trojans that install ad-embedding extensions in Safari, Chrome, and Firefox.
Beware Trojans Bearing Ads — According to Russian security firm Doctor Web, there are an increasing number of Mac-focused Trojans that install extensions for Safari, Chrome, and Firefox. These extensions are designed to embed third-party ad code into otherwise unrelated Web pages, funneling the clickthrough revenue back to the malware authors. The Trojans use a variety of techniques to fool users into installation, including masquerading as video plug-ins, media players, download accelerators, and more. To be safe, avoid installing software from sites that prompt you to do so — always get software from
trusted sources.