TidBITS#1202/09-Dec-2013
This week, we’re kicking off our annual membership drive. Your generous contributions have enabled us to bring you more great content than ever before, and as an example, check out Geoff Duncan’s in-depth examination of what Edward Snowden’s revelations about NSA spying could mean for the future of the Internet. We’re also thankful for our corporate sponsors, and happy to welcome a new one: game publisher Aspyr Media. In tech news, Adam Engst explains how Time Machine backups now work with the AirPort Extreme’s AirDisk feature, but only for the new 802.11ac models, and Mark Anbinder covers the release of FileMaker 13. On a lighter note, we round up seven geek gift guides for your review, and in FunBITS, Josh Centers looks at the iPad version of Star Wars: Knights of the Old Republic. Also this week, TidBITS members can read the latest chapter of Josh’s “Take Control of Apple TV,” which focuses on controlling, buying, ripping, importing, and managing video. Notable software releases since our Thanksgiving hiatus include Apple Remote Desktop 3.7.1, Sandvox 2.8.7, 1Password 4.1.1, BBEdit 10.5.6 and TextWrangler 4.5.4, ScreenFlow 4.5, Piezo 1.2.3, Airfoil 4.8.2, Fission 2.2, Marked 2.2, Nisus Writer Pro 2.0.7 and Nisus Writer Express 3.4.6, Fantastical 1.3.11, DEVONagent 3.6, DEVONthink and DEVONnote 2.7.2, and KeyCue 7.1.
Aspyr Media Sponsoring TidBITS
Please welcome our latest long-term TidBITS sponsor, Aspyr Media, an Austin, Texas-based publisher of games for Mac and iOS.
Since 1996, Aspyr has been a shining light in Mac gaming. Until recently, Apple users were the unloved stepchildren of the video game world. Blockbuster titles were rarely ported to the Mac, and if they were, it took years. Aspyr was there in the darkest of days for Apple users, porting quality games to the Mac. In fact, the first Mac game I ever bought was Aspyr’s version of Unreal.
Since then, Aspyr’s Mac ports have become even faster and better. They brought BioShock: Infinite to the Mac within a few months of PC release, in a flawless translation that runs beautifully on my 2011-vintage MacBook Pro (for my review, see “FunBITS: In Praise of BioShock Infinite for Mac,” 6 September 2013). Not only that, but they’ve somehow managed to bring the new BioShock Infinite: Burial at Sea expansion to the Mac at the same time as PC and console releases.
Aspyr has recently jumped into gaming for the iPhone and iPad. If you’re a Star Wars fan, try their iPad version of the classic Star Wars: Knights of the Old Republic (reviewed recently here; see “FunBITS: Star Wars: Knights of the Old Republic for iPad,” 6 December 2013.) Of course, it’s also available for the Mac. It’s without a doubt one of the finest role-playing games of all
time, and now you can play it from the comfort of your couch. Knights of the Old Republic is one Star Wars prequel that won’t disappoint, and it has one of the best plot twists ever.
Aspyr also runs the GameAgent game directory service, and if you’re a Mac gamer, you have to check it out. GameAgent lists all games available for the Mac, regardless of the publisher, and even lets you filter by which titles are on sale. Add one to your wishlist, and the site sends you email when the price drops. Who else does that?
A particularly welcome feature of GameAgent is Mac Match, which lets you know if a game will play on your Mac, once you’ve signed up for a free account. You can either let the GameAgent app scan your hardware, or you can tell Mac Match about your system manually. Either way, it takes just a few minutes and eliminates the headache of figuring out system requirements.
Even though most of my TidBITS colleagues don’t share my experience in the gaming world, video games play a significant — and growing! — role in the Apple ecosystem, thanks in part to Aspyr’s longtime support. For that, we’re proud to have them as a TidBITS sponsor.
Use Time Machine with the 802.11ac AirPort Extreme Base Station
In betas of Mac OS X 10.5 Leopard, Apple introduced a feature that enabled Time Machine backup to a USB hard drive attached to an AirPort Extreme Base Station. However, by the time Leopard shipped, Apple had pulled the feature (see “Time Machine via AirPort Disk Is Unsupported, Apple Says,” 7 April 2008), focusing networked Time Machine backups on the Time Capsule (now called AirPort Time Capsule). On subsequent updates to Mac OS X, we checked to see if the feature had returned, and some users managed to make it work, but Apple steadfastly maintained that
backing up to an AirPort Disk was unsupported, and eventually we stopped looking.
In fact, Apple still makes that statement in “AirPort base stations: Time Machine hard drive compatibility,” saying clearly:
“Time Machine is not supported with USB hard drives that are connected to an AirPort Express or AirPort Extreme device.”
But a release note for the recent “AirPort Base Station Firmware Update 7.7.2” (21 November 2013) caught my eye while I was editing our coverage (this update applies only to the newest 802.11ac base stations released in June 2013). Apple says:
“Addresses an issue that prevents a USB hard drive connected to an AirPort Extreme from appearing as an available disk in Time Machine”
And once I went looking for confirmation, I found it in Apple’s “Mac Basics: Time Machine backs up your Mac” document, which says:
“Time Machine can only back up to an external drive connected to an AirPort Extreme 802.11ac base station. Time Machine cannot back up data to external drives connected to other AirPort Extreme base station models”
That’s in complete contradiction to the 5-year-old prohibition against pointing Time Machine at an AirPort Disk, and the change has gone almost entirely unnoticed since June 2013, despite being prominently mentioned on page 13 of the manual for the new AirPort Extreme Base Station. Apparently, Mac users really don’t usually read the manual.
In fact, someone did notice — the late Time Machine expert James “Pondini” Pond called it out on his site in June; alas, he passed away in September 2013 at the age of 70 and will be missed.
What’s most compelling about backing up to an AirPort Disk, as opposed to an AirPort Time Capsule, is that you’re not combining two entirely unrelated pieces of hardware in one package. If the AirPort Time Capsule’s hard drive fails, it’s difficult to replace, and if you want to upgrade the wireless gateway side of the equation, there’s no easy way to bring your backups over to the new device. With an AirPort Extreme Base Station and attached USB hard drive, you gain more flexibility.
I don’t have one of the new 802.11ac AirPort Extreme Base Stations to test the return of Time Machine backups to AirPort Disks, and everything I’ve read indicates that it works only with the newest hardware, not any of the older, flatter base stations. Nevertheless, if you have the necessary hardware and curiosity, I’d encourage you to hook up a USB hard drive and see if Time Machine backs up to it reliably (since 10.8 Mountain Lion, Time Machine has allowed you to back up to multiple destinations, alternating between the different destinations). Let me know how it works out in the comments!
FileMaker 13 Gains a Smooth New Web Presence
Some of us at TidBITS have been using FileMaker for over two decades, which isn’t something we can say about many software products. Apple subsidiary FileMaker, Inc. has now released version 13 of its eponymous database tool, focusing heavily on mobile integration (with the free FileMaker Go apps for iOS) and a completely revamped Web publishing approach.
If pushed, I’d say that the focus for FileMaker 12 was its vast improvement in design tools for building attractive and navigable database user interfaces, and the theme for FileMaker 13 is making the database accessible everywhere.
FileMaker on the Web — Since the very beginning of the World Wide Web, we’ve wanted to publish our databases on it, and for the first few years, getting FileMaker data onto Web sites required creative scripting with WebSTAR, or using third-party tools like Lasso. With FileMaker WebDirect (available in Filemaker Server 13) replacing the company’s previous Instant Web Publishing solution in the latest release, FileMaker has built a completely new tool for making databases available in a Web browser.
Making a Web interface behave more like a desktop interface was a major goal for FileMaker 13, FileMaker senior product manager Eric Jacobson told me, and perhaps the most dramatic example of that is the ability to drag images or other content into suitable fields in a database layout, right in your Web browser, eliminating the need to select a field, click an upload button, and navigate around a file selection dialog. That may sound like an obvious feature, but it’s one that the company added to the desktop version of FileMaker only last year.
Even better, and more important, is that a change to data anywhere in a FileMaker database is instantly transmitted to, and reflected by, views of that database on any platform. Edit a record at home before leaving for work, and that change is pushed right out to everyone viewing that record in the field, whether they’re accessing the source database via the FileMaker Pro desktop application at the office, a Web browser while on the road, or an iOS app on the train.
FileMaker acknowledges mobile Web support still has a way to go. WebDirect officially supports Safari, Chrome, and Internet Explorer, but not mobile browsers at this time. The company says there’s no reason you can’t access the Web version of a FileMaker database using a mobile browser, but it has put its energy thus far into compatibility for desktop Web browsers — and iOS app support via FileMaker Go. Full mobile browser support will come in a future release. Similarly, FileMaker says you can use Mozilla’s Firefox on the desktop, but it’s not certified to be fully compatible.
Handheld Data — FileMaker Go, the iOS app for iPhone and iPad for accessing and updating FileMaker databases, became free last year with the release of FileMaker 12; FileMaker rightly saw the iOS app not as a separate product, but as a vital avenue for working with databases (see “FileMaker 12 Adds Power, Clarity, and Free iOS Apps,” 4 April 2012).
Mobile layouts must still be designed on the desktop; FileMaker Go is not a standalone development tool. But database developers now have a suite of new pre-designed mobile layouts at their disposal, and these layouts can be added to a database in any of several pre-designed shapes, such as iPad and iPad mini, 3.5-inch iPhone (iPhone models through the iPhone 4S), and 4-inch iPhone (the iPhone 5 and later).
Layouts designed for the iOS apps are as resolution-independent as it’s possible to make them; FileMaker says text will always be rendered at the highest resolution of the device you’re using, and images stored in the database will be rendered at resolutions sufficient for Retina displays, assuming there’s enough data present in the original. At the other end of the spectrum, FileMaker has taken care to leave buttons, links, and fields in their mobile layouts big enough, and spaced widely enough, for a fingertip, rather than the pinpoint accuracy of a mouse pointer.
One nifty new capability of FileMaker Go 13 is by no means revolutionary, but it’s a nice touch; FileMaker Go can now scan just about any type of bar code as an aid to data entry. Doing inventory? Just aim your iPhone or iPad camera at a UPC code, or a QR code, or whatever similar printed-but-scannable data is in front of you.
Other Improvements — FileMaker 13 may not be as focused on design as version 12 was, but FileMaker has added new templates, new themes, new styles, and a layout tool that’s especially attractive: a field picker. Instead of having to select the fields for a new layout all at once when creating it, or adding one field at a time after the fact, users can search their databases for fields, select as many as they need, and drag them right to a layout, complete with labels and spacing suitable for the target device.
Especially as more and more database access leaves the relative safety of the corporate network, what with Web access and handheld apps, I’m glad to see some extra attention to secure transport of information between user and server. FileMaker Pro 13 Advanced now offers AES 256-bit encryption from end to end, even when you’re using an iOS app to access or update your database.
FileMaker 13 is available immediately, either via traditional purchase or monthly license model along the lines of Adobe’s controversial Creative Cloud (see “Adobe Flies from Creative Suite into the Creative Cloud,” 8 May 2013). New copies of FileMaker Pro 13 costs $329, whereas FileMaker Pro 13 Advanced is $549, and FileMaker Pro 13 Server starts at $1,044 for one connection; additional concurrent connections cost $180 each, in bundles of five. Upgrades cost $179 for FileMaker Pro 13 and $299 for FileMaker Pro 13 Advanced. If you’re more interested in the monthly licensing approach, it will set you back $9 for FileMaker Pro and $15 for FileMaker Pro Advanced, and starts at $29 for
FileMaker Server with one connection; additional concurrent connections each cost $5 per month, in bundles of five. The FileMaker Go apps for iPhone and iPad remain free. A 30-day trial version is available.
Chapter 6 of “Take Control of Apple TV” Available
The raison d’être of the Apple TV is to play movies and TV shows, and that’s where Josh Centers now turns his attention in our streamed ebook “Take Control of Apple TV.” Chapter 6, “Apple TV at the Movies,” looks at controlling video playback (I’m a little embarrassed at how much I learned from this section), buying and watching videos from the iTunes Store, and playing video stored in iTunes on your Mac. But where the chapter really makes its bones is in its step-by-step instructions for ripping your DVDs via HandBrake, adding metadata to the resulting files with iFlicks, and importing them into iTunes. Josh even covers merging multi-disc movies and ripping Blu-ray discs,
but beware that Blu-ray movies take a long time to rip and chew through hard drive space. Finally, he looks at two ways of storing all these massive files on an external disk, which is likely necessary for anyone with a small SSD.
As with Chapter 5, “Master AirPlay,” Chapter 4, “Discover What’s on Offer,” Chapter 3, “Control Your Apple TV” and Chapter 2, “Set Up Your Apple TV,” this chapter is available for free, but only to TidBITS members; everyone is welcome to read Chapter 1, “Introducing Apple TV,” to see what’s still coming. Please leave comments — we’re already planning tweaks based on questions readers have asked! Everyone will be able to buy
the full ebook in PDF, EPUB, and Mobipocket (Kindle) formats once it’s complete, and TidBITS members can save 30 percent on this and all other Take Control titles.
Publishing this book in its entirety for TidBITS members as it’s being written is one of the ways we thank TidBITS members for their support. We also hope it encourages those of you who have been reading TidBITS for free for years to help us continue to bring you carefully considered, professionally written and edited articles each week (for more details, see “Support TidBITS in 2014 via the TidBITS Membership Program,” 9 December 2013).
Seven Geek Gift Guides for 2013
It’s that gift-giving time of year again, and if you’re thinking about giving that special someone a high tech gift — or putting such an item on your wishlist — the collective wisdom of the Internet’s technology publications is here to help.
But you won’t find one from us. After many years of producing entire gift issues of TidBITS (our most recent, with links to previous years, was in “TidBITS Gift Guide 2010,” 6 December 2010), we decided once again not to venture there — while the technology world has grown by leaps and bounds, it feels like the sort of items that generally end up on tech-related gift guides, including our own, are either obvious (who wouldn’t want an iPad mini) or perennial suggestions that appear each year. In short, we didn’t feel we could add enough value to make it worth doing.
That said, we know many of you may be looking for ideas, or at least help with choosing a particular digital camera or ebook reader. To aid in that effort, here are seven geek gift guides we’ve found worth a look.
The Wirecutter — Where the Wirecutter normally focuses on the “best” technology based on extensive research and hours of testing, their gift guide is, well, unusual. Organized by price, the Wirecutter’s suggestions are wonderfully eclectic, and don’t bother with the standard suggestions that you’ll read about in all the other gift guides.
When you scroll through the Wirecutter’s guide, you’ll find well over 100 items, including beard oil (yes, such a thing exists), a Mars globe, a corkboard map of the world, and a Lego Architecture Studio. It’s well worth reading to get ideas for those on your list who are hard to shop for.
The Verge — Less a list than a Web app, the Verge’s 2013 Holiday Gift Guide looks great and is fun to click around in, but is awkward to use. You can either click callout links in the umbrella collections (Cook It Up, At Play, On The Street, etc.), or just scan the more obvious categories (Appliances, Audio & Speakers, Food & Drink, and so on). Each item’s card can display more info (but only a few sentences), and links to the product’s Web page. Some, but not all, items also link to reviews on the site.
The Verge’s approach works relatively well in the categories where it feels that they’re picking the best variants from a wide selection of products, such as in Cameras and TVs, but in Books, Games, and Movies, the recommendations seem random. And in categories like Game Consoles, Phones, Set-top Boxes, and Tablets, where there aren’t many competitors, the Verge seems to punt on choosing and just lists them all.
iMore — Being an Apple-centric site, it’s no surprise that iMore’s gift guide focuses exclusively on Apple products. If you’re considering an iPhone, iPad, iPod, or Mac as a gift, it’s a useful overview of the pros and cons of each model.
Of course, that focus is also limiting; it won’t help you go beyond the narrow world of Apple’s product line, even for software, accessories, or peripherals.
Engadget — Tech blog Engadget broke its holiday gift guide into separate articles, each focusing on a particular category, such as Smartphones, Gaming, E-readers, Cameras, and Household. In each category, Engadget sorts by cost, ranging from On the Cheap to Money Is No Object although you won’t find many items under $100 at all.
It’s a lot of information to sort through, but if you’re looking for something in one of their categories, it might be useful. What you won’t find in Engadget’s gift guide are the quirky ideas that you wouldn’t have thought of on your own.
CNET — Of the guides we’ve seen so far, CNET’s gift guide is the hardest to navigate and the most confusing. It’s split into categories such as Smartphones, Gaming, Portable Audio, and Wearable Tech, but each category has a number of sub-categories, so the Portable Audio category actually encompasses Gifts for Mobile Music Lovers, Wireless Speakers, Wired Headphones, and Wireless Headphones. That’s confusing enough, but a set of More Holiday Suggestions that appears both in a top-mounted scrolling banner and in a right-hand sidebar cuts across the categories for collections with titles like Editors’ Top
Picks, Best Tech Under $50, and Ultimate Luxuries. Worse, once you get into a category, the actual recommendations are presented in slideshow format, making it impossible to compare easily.
If you can get past the awful presentation, CNET seems to have gone beyond many of the obvious recommendations to suggest items that you might not have considered, particularly on the low end of the price spectrum.
Wired — At least CNET offers a landing page that brings together all their different categories. Although Wired has a Wish List 2013 article, it collects only five articles at the moment, despite there being quite a few more. The only commonality seems to be the “wishlist-2013” tag. Each article is a slideshow, and luckily, the Next link and navigation thumbnails scroll the page appropriately for viewing, since the layout is otherwise maddening.
Without a comprehensive overview of the various articles, it’s hard to get a sense of everything that Wired has covered, but major categories include outdoor gear, health-related items, things that are reusable, and the more expected suggestions for photographers, audiophiles, dog lovers, and car buffs. Thanks to a variety of ideas that deviate from the beaten path, it’s worth a look, but be prepared to put in some effort navigating.
Boing Boing — The eclectic editors of Boing Boing have compiled an equivalently eclectic gift guide that reflects their personal tastes. As such, there’s no sorting by price or category, but you can filter by editor, if you have your favorites.
There’s a bit of everything in this highly scannable list — by far the easiest to read! — including tech gizmos, comic books, DIY kits, low-tech gadgets, odd toys, clever games, and much more. You’re certain to find some great ideas here.
We’re sure there are many other tech-focused gift guides out there, so please let us know in the comments which you’ve found particularly interesting!
Support TidBITS in 2014 via the TidBITS Membership Program
Two years ago, we took a deep breath and leapt off a cliff. TidBITS wasn’t operating on a sustainable basis, and we needed help to pay our staff to produce articles and to cover the costs of developing and maintaining our Web site and mailing lists. Our plan was to throw ourselves at the mercy of you, our readers, the people for whom we spend our days testing, troubleshooting, researching, writing, and editing.
Happily, through the TidBITS membership program unveiled in “Support TidBITS by Becoming a TidBITS Member” (12 December 2011), you caught us. With contributions from nearly 2,200 TidBITS readers in 2012, we were able to put the publication on stable financial footing (for last year’s recap, see “TidBITS Needs Your Support in 2013: Join Our Membership Program,” 17 December 2012). In 2013, more of you joined, pushing our membership over 2,500. Since we don’t have funding from deep-pocketed venture capitalists or a corporate behemoth like many Apple news sites, your direct support
was essential in helping us keep bringing you fresh and useful content.
We’ve done just that, as you can read in the TidBITS Index below. Compared to the same portion of 2012, we published almost 200 more articles, and commissioned 26 more feature articles from outside authors than last year. That was possible in large part because your financial support enabled us to lure Josh Centers away from his corporate cubicle and two-hour commute to become our new managing editor.
That’s all great, but it merely underscores our need for ongoing funding. Our 23-year record shows that we’re in this for the long haul, and if we’re going to keep working for you in the future, we need your continued support.
Early supporters who joined the TidBITS membership program when it launched in December 2011 have started receiving email from me about renewing, along with a subsequent message from eSellerate with reminders and links for those who chose a manual renewal and confirmations for those who prefer to renew automatically. But not everyone reading this is a TidBITS member.
So, if you find reading TidBITS regularly useful and enjoyable, can you help? Between the 21,000 people who receive TidBITS via email and the 15,000 who subscribe via RSS, only about 7 percent have joined the TidBITS membership program. And that doesn’t even count the 123,000 people who visit our Web site in an average month. I don’t expect much from the one-off visitors who come for a key article like Joe Kissell’s “Mail in Mavericks Changes the Gmail Equation” (22 October 2013), which garnered 169,000 page views and smashed our record for number of comments, at 446. But if you benefit from our writing on a regular basis, such as with Alicia Katz-Pollock’s “Making the Most of Contacts in Mavericks” (15 November 2013), Josh Centers’s “All about Tagging in the Mavericks Finder” (14 November 2013) or my “Using Tabs in the Mavericks Finder” (31 October 2013), please consider joining.
Along with content like those articles, we also thank all TidBITS members with a number of perks, including:
- A version of the TidBITS Web site free of graphical banner ads.
- A full-text RSS feed (non-members get a summary-only feed).
-
The option to receive articles in email as soon as they are posted.
-
The ability to post longer article comments, with live URLs.
-
Recognition of your membership (with colorful apple icons) when commenting.
-
A 30 percent discount on all Take Control ebooks.
-
Discounts on an ever-increasing number of Mac-related products, including 1Password, LaunchBar, DEVONthink Pro, TextExpander, Airfoil, PDFpen, SpamSieve, Keyboard Maestro, Audio Hijack Pro, PopChar, CloudPull, Default Folder X, MarsEdit, Voila, Dejal Simon, Password Wallet, Fetch, and even the stunning SizzlPix high-definition photographic prints. (If you’d like us look into a discount on a particular app or want to include your company’s products in our list, drop me a note.)
In 2013 we added more Mac apps to our member-discount list and released chapter-by-chapter streamed versions of two Take Control ebooks — Jeff Carlson’s “Take Control of Your Digital Photos on a Mac” and Josh’s in-progress “Take Control of Apple TV” — so TidBITS members could read and comment on them before publication.
You can choose among five different levels of annual support: $20, $50, $100, $250, and $1,000. They default to a manual renewal, but if you don’t want to fuss with the cart each year, an automatic renewal option is available. The membership perks are the same at each level, with one exception: the $1,000 level is a lifetime membership that includes a fine dinner with the staff at Macworld/iWorld in San Francisco or with me and Tonya any time you’re in Ithaca. Seriously — we enjoyed dinner with a pair of our lifetime members last year during the show.
Assuming you so wish, we’ll acknowledge your membership on the site in the TidBITS Members list and with an apple icon next to your comments. You can control your acknowledgement status, name, and URL in the Account Info page. That page also lists your membership status and expiration date, and if our system ever stops email delivery due to too many bounces, you can restart delivery with a single click there.
Again, if you have found TidBITS valuable, or if you’ve received personal help from one of our staff members simply because you asked, please become a TidBITS member to help us continue publishing the kind of articles you’ve become accustomed to reading each week. You’ll have our undying gratitude, and more importantly, you can rest assured that every article you read was made possible in some small part by your generosity. Thank you!
TidBITS Index 2013 — I’d like to leave you with a sense of what the TidBITS membership program has enabled us to do in the past year, along with some select stats on the benefits it has provided for members this year compared to last (via a snapshot taken just before membership renewals started). Without further ado, the TidBITS Index 2013!
-
Articles, including TidBITS Watchlist items, published in 2012: 671. In 2013: 867.
-
Articles commissioned and paid for with membership funds in 2012: 14. In 2013: 40.
-
TidBITS articles read on the Web in 2013: 1.9 million.
-
Estimated number of TidBITS issues sent in email in 2013: 1.06 million.
-
Comments left on TidBITS articles published in 2013: 4490.
-
Number of TidBITS members in 2012: 2179. In 2013: 2534.
-
Percentage of TidBITS members who wish to be listed on our public members page: 44.
-
Total amount a TidBITS member could save on member-discounted Mac products in 2012: $331. In 2013: $448.
-
Amount actually saved on Take Control ebook orders by TidBITS members in 2012: $1408. In 2013: $2400.
Are We Ready for the Post-Snowden Internet?
It has been nearly six months since government surveillance revelations from Edward Snowden began to be published in the Guardian, Washington Post, and other outlets. Snowden turned over as many as 200,000 classified documents to journalists, and they’ve revealed a myriad of intelligence-gathering tools and operations aimed squarely at our electronic lives, regardless of location, citizenship, activities, or legal status. And the hits keep coming: nearly every week sees new details published from Snowden’s cache, momentum that has stirred up many independent revelations. Some have been minor, but others — like PRISM, tapping internal network links at services like Google and Yahoo, and collecting location data on mobile phones worldwide — have been astonishing.
It’s easy to enjoy “Snowden schadenfreude.” (Or perhaps “Snowdenfreude?”) Who doesn’t like seeing the powers-that-be taken down a notch or two? It’s also easy to believe the ongoing scandals don’t matter to ordinary people. After all, who cares if the NSA knows about your online pizza order last Saturday?
The disclosures are clearly impacting government policy and diplomacy, but may also change the fundamental architecture of the Internet. A broad range of countries and companies are openly talking about forming isolated and compartmentalized networks to protect themselves (and their citizens) from surveillance regimes.
And that might break up the Internet.
It Just Works — It seems obvious, but the Internet’s greatest strength is interoperability. If you can get an IP “dialtone” on any of the Internet’s 40,000+ networks, you can access any site, app, or service anywhere else in the world. Sure, there are practical concerns: you might not have much bandwidth, access might be expensive, your device or software may not be compatible, a site might be down or blocked, your connection might be unreliable, et cetera. But that fundamental interoperability is the heart and soul of why the Internet has become humanity’s dominant communications medium, and has made things ranging from smartphones to the Arab Spring
possible.
This year’s mass surveillance revelations — and the legal frameworks behind them — may represent the biggest interoperability challenge the Internet has faced. Now, being part of the Internet community means being subject to monitoring by the Five Eyes — the intelligence agencies of the United States, the United Kingdom, Canada, Australia, and New Zealand — in addition to lawful intercept and domestic surveillance conducted by national and local governments. Countries can pass laws to monitor communications amongst their own people or within their own borders — most countries have — but those same
countries almost certainly consider the activity of the Five Eyes an infringement on their sovereignty. And they’re not happy about it.
Slouching Towards Balkanization — The human reaction to external threats is predictable: circle the wagons, bar the gates, hide the children, and raise the drawbridge. In the extreme, a country could block Internet access at its borders, creating a walled garden. Internet services would work domestically, but be disconnected from (or even incompatible with) the global Internet, keeping out the Internet’s broadest dangers and the Five Eyes.
Few nations would risk the economic damage that would come from disconnecting from the global Internet. A more realistic option is requiring Internet behemoths like Google, Facebook, Yahoo, Amazon, and Apple to locate services and store data within a country’s borders — where they would be subject to the country’s laws. The Five Eyes’ surveillance regime is effective because so much everyday Internet traffic is routed through data centers in North America and Europe — where major Internet companies are headquartered — and subject to those countries’ laws. As of January 2013, more than 100 countries had no domestic Internet exchanges,
meaning they were entirely dependent on foreign services. Requiring major providers to locate data centers within a country’s borders means local traffic would stay local, theoretically beyond the reach of the NSA’s legal and clandestine tentacles into American companies.
It’s not a new idea. China mandates that Internet businesses comply with the censorship and data handover requirements of the so-called “Great Firewall.” It’s not just a pro-forma requirement: China has imprisoned a number of dissident bloggers, some on the basis of information turned over by Yahoo’s Chinese subsidiary, and in 2010 Google moved its Chinese search engine from Beijing to Hong Kong to sidestep Chinese censorship requirements. The same year, countries like India,
Saudi Arabia, and Indonesia moved to shut down the BlackBerry service unless they were granted a way to intercept messages. BlackBerry kept running, most likely by parking servers in those jurisdictions where they can be monitored without involving international law. Of course, Internet users may not be comfortable with what their governments do and don’t allow within their online borders: according to the latest World Wide Web Foundation’s Web Index (founded by Web creator Sir Tim Berners-Lee), 30 percent of the world’s nations engage in moderate to extensive blocking of online content and services they deem
objectionable or sensitive.
Some of these examples predate recent surveillance disclosures. Who might be next? Consider Brazil. Brazil had previously pondered its own national secure email service (through its post office), but is now getting serious, with President Dilma Rousseff laying out proposals to bolster Brazil’s domestic bandwidth (keeping Brazilian traffic in Brazil), require Internet companies to locate data centers within its borders, and encourage network operators to use networking equipment designed and produced in Brazil.
The notion of Brazilian-designed networking gear could be important. In the next two years Brazil is scheduled to light up five new undersea fiber links to Africa, Europe, and Asia, (and, yes, to the United States), potentially enabling Brazil (and its overseas partners like China and South Africa) to bypass the Five Eyes. If those links — or Brazil’s expanded networks — eventually work only with Brazilian gear, the country could become the Internet’s largest walled garden. But Rousseff sees the moves as a way to protect values that historically have been championed by the United States.
“In the absence of the right to privacy, there can be no true freedom of expression or opinion, and therefore no effective democracy,” she told the UN General Assembly. Then, driving her point home, Rousseff announced (ironically, via Twitter) that Brazil will be hosting an ICANN summit on Internet privacy and security in April 2014, and cancelled a state dinner with the Obamas.
Brazil is not alone in considering carving away from the Five Eyes. In the European Union, France and Germany have been highly critical of recent surveillance revelations. The EU’s internal market commissioner Michel Barnier has called for a “European data cloud”, and EU justice commissioner Viviane Reding characterized the European Parliament’s vote on data protection regulations as a declaration of independence, requiring non-EU companies to “deal responsibly” with user data or be fined up to 5 percent of their annual
worldwide revenue. If EU member states adopt the policies, Internet users will see warnings when their personal data is about to leave servers covered by EU data protection laws.
Some “Email Made In Germany” services piggybacking on popular concern over NSA surveillance already do something similar. Raising the ante, Deutsche Telekom is currently proposing an “all-German” domestic Internet with an eye towards encompassing the whole Schengen Area, twenty-six European countries that have mutually set aside passport and immigration controls. (The UK and Ireland opted out.)
Think Global, Act Local — If Internet balkanization can protect privacy, is it a bad thing? On some levels, keeping user information, data processing, and communication within a country or region is just common sense. Do we need to use a server halfway around the world to send a quick message across town? It certainly isn’t efficient, purely on the basis of resource consumption, electricity, network infrastructure, and complexity.
The flip side is that balkanization — even when well-intentioned — can impact the interoperability and communicative power of the Internet. Requiring companies to run separate facilities in each country in which they operate is both expensive and cumbersome. Those costs could impede innovation if companies have to choose between setting up a data center in (say) Austria or investing in R&D.
Sometimes Internet services pick up their most loyal followings in unexpected places — that would be far less likely to happen with a balkanized Internet. Remember Orkut, Google’s early experiment in social networking? Most people don’t, but it was huge in Brazil and India for years — and Google eventually moved it to Brazil entirely. Similarly, Canadian instant messaging service Plurk never managed to rival Twitter, but it became so popular in Taiwan it accepted millions to relocate there in early 2013. How about San Francisco’s social/gaming service Hi5? It’s now part of Tagged, but its biggest audience has always been in Latin
America.
Can social networks and modern apps survive in a world with online border checkpoints? Imagine installing a new collaborative music app or game from the App Store, only to find you can’t use it with your friends because it hasn’t been approved in their jurisdiction. Want to share a tagged photo? Maybe you can’t because your preferred social network doesn’t support a “right to be forgotten.” Maybe you’re travelling and want to check back in with family via FaceTime, but it’s blocked because Apple has not granted the local government a back door to tap into video chats. Or maybe all these services will work great once you register your devices, verify your identity, and pay a fee to another country. A global patchwork of
Internet regimes — each with its own quirks and requirements — quickly undermines the free exchange of data and information on which the modern Internet has thrived.
Perhaps most importantly, countries that decide to require Internet services host and process data locally will have the capability to monitor that data much more closely — and decide what can and cannot flow across their borders, what they will and won’t collect. This might not be a major issue in democratic countries like Brazil and Germany — although they operate their own sophisticated intelligence regimes. However, authoritarian states may decide to engage in (more) internal censorship and surveillance. Further, some firms will choose not to operate in particular countries — like Google in China — due to legal requirements, technical complexity, or the burden setting up subsidiaries. What if Facebook and Twitter
had been required to run data centers in Tunisia, Egypt, or Yemen under the thumb of those countries’ former governments? Could the Arab Spring have taken place without the extra-territorial communications channels made possible by Facebook and Twitter?
What About International Law? — Before we start carving the Internet into separate fiefdoms with unique rules, border guards, and access requirements, isn’t there some legal remedy to the Five Eyes’ increasingly exposed surveillance regime? Perhaps secret U.S. law can enable the NSA to collect metadata on hundreds of millions of Americans, but how can U.S. law legally empower the NSA to collect phone records on hundreds of millions of German, French, Dutch, Italian, and Spanish citizens, and others — not to mention dozens of world leaders? Couldn’t these people — or these nations —
just take the United States to court?
The short answer is the mass surveillance regime is probably not legal in many nations where individuals’ data is being collected. The United States can authorize the NSA and other agencies to spy on other nations’ communications under U.S. law, but that does nothing to de-criminalize those acts under other nations’ laws. So the unofficial eleventh commandment of intelligence agencies — “Thou shalt not get caught” — holds true. Because if they’re caught they’ll go to prison.
The long answer is much more complicated. The United States and many other countries have data-sharing and safe-harbor agreements that permit international sharing of communications and business information — these facilitate communications, finance, and business all around the world. Once that information is in the United States (legally) and being processed by U.S. businesses and agencies, it’s subject to U.S. law and, essentially, fair game to intelligence agencies. Further, Internet traffic that transits the United States is subject to U.S. law — and possibly even if it’s handled entirely overseas by U.S. companies. Warrants from the Federal Intelligence Surveillance Court (FISA) are sealed, so we don’t currently know if the United States has extended its reach overseas this way. Maybe future disclosures will tell us.
In addition, the United States and the Five Eyes have a number of intelligence-sharing arrangements. The most significant is with Britain’s GCHQ but the Five Eyes do some sharing with at least a dozen allies ranging from Singapore to Sweden. Few details have been disclosed, but elements of other governments probably have had some knowledge of NSA activity within their borders. If mass surveillance is conducted with a government’s permission — perhaps as a quid pro quo arrangement — it may be legal.
Can mass surveillance be prosecuted under international law? Probably not. Most agreements dealing with surveillance only address government and diplomatic communication, not mass collection of commercial or private data. For instance, the Vienna Convention on Diplomatic Relations of 1961 bars espionage and is the basis for the modern concept of “diplomatic immunity.” It’s ratified by 189 countries but seems to be regularly ignored. Some early disclosures from Snowden include the NSA tapping communications at
the United Nations, the Atomic Energy Agency, NATO, and EU offices — almost certainly in violation.
What about the United Nations? The 1966 International Covenant on Civil and Political Rights (ICCPR) lays out specific provisions that prohibit signatories from “unlawful or arbitrary interference” with any person’s privacy, whether by individuals, businesses, foreign countries, or a nation itself. Violations of the ICCPR are handled by the Human Rights Committee, a quasi-judicial group of 18 experts at the UN that meets three times a year.
The ICCPR sounds promising, but the devil is in the details. The ICCPR has been ratified by 74 countries, but the United States got around to it only in 1992 and, curiously, has not made legal changes to meet its requirements. (The U.S. has also refused optional portions that prohibit torture.) In 2006, a Human Rights Committee review all but declared the U.S. in violation — another review could start as early as March 2014. The United States and the UK also don’t accept the right of “individual complaint” under the Covenant, meaning a specific person cannot bring them up before the Human Rights Committee. However, entire nations (or coalitions like Latin
America or the EU) could bring inter-state complaints under the ICCPR.
Even nations would find it tricky to bring ICCPR complaints against the Five Eyes. The privacy provision in the Covenant is quite short, and doesn’t include limitations or legal tests. In other words, it’s wide open to interpretation that could keep politicians, diplomats, and lawyers busy for years — and it’s not like the UN or the Human Rights Committee moves quickly even when members are in widespread agreement. The United States and its allies have consistently argued their mass surveillance regime is legal and all about going after international terrorists — and the ICCPR does not apply to espionage.
One option might be changing the ICCPR. Brazil and Germany have just put forward a proposal that would add a right to online privacy to the ICCPR, asserting the “same rights that people have offline must also be protected online, including the right to privacy,” and that “highly intrusive” online surveillance would violate rights to freedom of expression. If it’s ratified, digital privacy could become an international human right alongside things like freedom of movement, freedom of association, and non-discrimination. The United States has already delineated its objections, and the proposal has wiggle room allowing collection of sensitive information in the name of public safety.
What if the United States or the Five Eyes were found in violation of the ICCPR? Despite its worthy ideals, the Covenant is essentially toothless, relying on nations’ goodwill to correct their own behavior. If the Human Rights Committee were to find the United States or its allies violated the Covenant — highly unlikely considering the economic and diplomatic pressure the U.S. can bring to bear — the only requirement is that countries in violation submit updates every three months about how they’re trying to fix the problems. That’s it. The committee cannot invalidate or change U.S. law, assess financial punishments, enact trade sanctions, or anything else. Being in violation would certainly be an embarrassment to the United
States and the Five Eyes — one that would be trumpeted loudly and frequently by critics — but that sort of international shaming hasn’t closed the U.S. prison camp at Guantanamo Bay.
The inefficacy of trying to go through the UN is one reason Brazil, Germany, and other nations are taking steps to cordon off their domestic Internet networks from the NSA. It’s a more practical solution under their control.
What About Encryption? — If balkanization could wreak havoc with the Internet and there’s no realistic legal or international recourse to shut down mass surveillance, what can we little people do? Just accept the Five Eyes (and their friends)? Trust that our small, insignificant lives are beneath their notice, that agencies will never abuse their capabilities, and never make mistakes that matter to us?
One bright spot is data encryption. While documents disclosed by Snowden revealed that the NSA has worked to weaken encryption standards and devised methods to aggressively attack encrypted data, other documents also indicated that well-implemented, strong cryptography can still stymie the NSA — and the math seems to hold up. Sure, the NSA might be able to crack strong encryption, given enough time and
resources, but they have to be motivated: it won’t happen for every email message or tweet generated by hundreds of millions of people every day. As a result, the NSA has preferred to conduct its surveillance before data gets encrypted or after it’s decrypted — like in the guts of data centers.
Internet companies are responding. Google was already beginning to encrypt its internal network before the Snowden revelations, and has since sped up the work; Yahoo says all connections in its data centers will be encrypted by April 2014. Disclosed documents indicate Microsoft assisted the NSA in accessing its services — ironic since the company’s new PR campaign claims Google
can’t be trusted with private data. That said, although the company has taken flak recently for failing to encrypt data, Microsoft just announced ambitious plans to encrypt user data and its networks by the end of 2014, with many protections already in place. Dropbox, Facebook, Twitter and several others have taken major steps to encrypt communications internally and between each other: the EFF is maintaining a summary.
However, most Internet companies must process unencrypted data from or about their users at some point: it’s impossible to run something like Google’s vast online advertising business (and extensive user profiling) and keep all user data encrypted all the time. Securing internal data links may take away one avenue the NSA has used to collect data from major Internet companies, but others almost certainly exist.
Strong encryption is available to everyday people, too: we can encrypt our email, use VPNs or Tor to shield our network connections, and use services that don’t store information about us. Joe Kissell’s “Take Control of Your Online Privacy” goes through the details and suggests real-world strategies for keeping our online lives private, but it focuses more on advertisers, local villains, and big media than on Big Brother.
Slouching Towards Transparency — Encryption alone is no guarantee data will be safe from the NSA’s prying eyes, but, done well, broader use of strong encryption can at least reduce weak points being leveraged by the NSA or others.
So what about all those other bugs and exploitable problems that compromise encryption and security? There’s no easy answer other than fixing those problems and making better systems. Most companies handle this process behind closed doors (if they handle it at all), often considering the details proprietary. But the Internet industry as a whole might be able to move forward via transparency and certification authorities — if only companies would get on board.
In general terms, transparency would mean companies being open not only about problems and errors in their software and hardware products, but also about how they create their products so customers can understand their risks. For hardware makers, that might include information about design, parts, supply chain, firmware, and physical security at manufacturing facilities; for software makers, it might include what libraries and tools they use or license and details of how their software communicates. The idea is not just to let users (and customers) know whether products are vulnerable to a known problem (rather like the widely used CVE system that catalogs security vulnerabilities) but also
to identify whether manufacturing or development processes are vulnerable to the end-runs the NSA seems to prefer.
When problems turn up — and they always do — solutions and case studies can be made available to the entire industry to be refined or perhaps adopted as a best practice. Such a process will inevitably look like the cat-and-mouse game software makers have played with hackers and virus writers for years, except it could be the global Internet and telecommunications industries going up against the NSA and its partners. And, like the fight against malware, it would probably be never-ending.
A big question is who would manage all this. No organization currently acts as a clearinghouse for digital security threats — aside, perhaps, from the NSA — and it’s a gargantuan task. Organizations and frameworks like the ISO, the ISA Security Compliance Institute, Common Criteria, and the National Institute of Standards and Technology (NIST) could play a role here — although NIST is working to regain trust in the computer security community following recent reports the NSA got a
backdoor into a NIST encryption standard. (NIST immediately launched a review.) The Internet Engineering Task Force (IETF) appears ready to engage in a long-term effort to re-evaluate the security of many of the Internet’s core technologies. At least it’s a start.
Internet, mobile, and telecommunications industries could take a cue from standards bodies in other industries like aerospace, healthcare, and safety — consider government agencies like the National Transportation Safety Board and companies like Underwriters Laboratories. Standards bodies and certification agencies identify risks, establish best practices, and develop tests and compliance programs that confirm products meet security standards. NIST has issued a preliminary cybersecurity framework aimed at critical infrastructure, but it includes an appendix on privacy and civil liberties.
Telecommunications giant Huawei is also trying to get the ball rolling on international cybersecurity standards: it recently published a white paper detailing its own internal practices — so far as I can tell, that’s a first for the industry. Huawei is the world’s largest telecommunications gear maker but is essentially barred from the U.S. market over allegations that its equipment might contain secret backdoors for the Chinese government. Thus, Huawei’s call for standards may be self-serving, but the company’s semi-pariah status might enable it to take a leading role. After all, among companies in its industry, Huawei has the fewest
connections to the U.S. government and Internet companies at the heart of this year’s mass surveillance revelations.
“We’re not saying that we have all the answers,” said Huawei USA Chief Security Officer Andy Purdy in a phone interview this October, “but we’ve got to come up with some areas of agreement and we have to have product assessment. That feedback loop is essential for the global industry generally. We know it’s hard — we have thousands of suppliers — but we’ve got to raise the bar.”
Cybersecurity standards and certification could become extremely important if countries like Brazil and Germany — and anyone who wants to partner with them — begin separating themselves from the global Internet and preferring infrastructure and gear designed and produced in their own countries.
What About Disclosure? — One of the insidious things about the legal framework of the NSA’s surveillance regime is that it’s covered by gag orders. American companies can be required to turn over data en masse without saying a word. At that point, encryption, standards, and data center design just don’t matter: the NSA gets everything wrapped up with a nice bow. As other countries set up their own national networks, it’s reasonable to assume they’ll use similar legal frameworks to scoop up not just data about their own citizens, but also any other personal data that transits their networks.
It’s a given that the United States will always have national security concerns, and governments will always spy on each other. However, the ongoing outcry from this year’s mass surveillance disclosures may generate political momentum for legal change. President Obama’s response to the initial Snowden disclosure was to reassure the American public that no one was listening to their phone calls and everything was legal. That stance has since shifted substantially: Obama appointed a review panel to make recommendations (due 15 December 2013) on changes in the U.S. intelligence apparatus, and has been openly talking about “legitimate concerns” that technology has outpaced the legal framework governing the NSA’s activities. Few
expect major changes overnight, but it might be the start of a broader reform process.
Several dozen Internet companies (including Apple, Facebook, Microsoft, Twitter, and Google) have petitioned the government to let them publish aggregate information about national security-related requests they receive. (Many companies, like Google, publish transparency reports for law enforcement requests.) Apple has taken things one step further in its own first transparency report, becoming the first major tech company to employ a so-called “warrant canary” for orders to turn over data under Section 215 of the PATRIOT Act. Apple says it has not received any such orders; if it does, that assertion should disappear when Apple’s next report comes out in six months. That’s a long delay, but the idea behind a warrant canary is that a gag order can legally keep a company quiet, but cannot compel it to lie. Warrant canaries haven’t been tested in court, but Apple has deep pockets to fund a legal challenge.
It’s Complicated — If there were an easy solution to the conflict between individual privacy, personal and national security, and the mass surveillance being carried out by western powers, we would have figured it out by now. The reality is that these issues have been with us for years; solutions are going to be incomplete, long-term, and messy; and conflict will only become more pronounced with our dependency on the Internet and modern communications.
It’s a shame. From a humble beginning more than four decades ago, the Internet has developed into perhaps humanity’s most powerful tool for spanning cultural divides, expanding access to information and education, enabling freedom of expression, protecting human rights, and — despite the trolls — broadening the human experience. Let’s hope we don’t destroy it to spite ourselves.
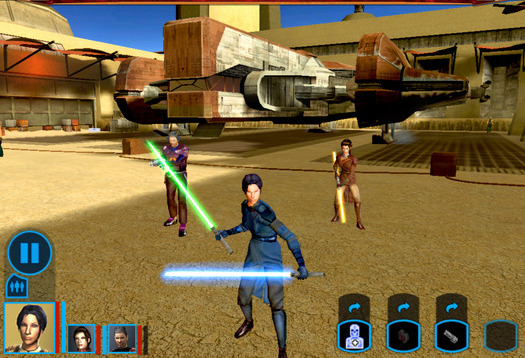
FunBITS: Star Wars: Knights of the Old Republic for iPad
Star Wars: Knights of the Old Republic (commonly called KOTOR) is one of my favorite games. Initially released for the PC and Xbox in 2003, the story takes place 4,000 years before the first Star Wars trilogy, putting you in the middle of a war between the benevolent Galactic Republic and the evil Sith Empire.
The iPad version of Star Wars: Knights of the Old Republic has been ported by Aspyr Media in a nearly flawless translation of the original. It turns out that the classic role-playing game is perfectly suited to touchscreen controls. The large on-screen buttons are just the right size for fingers, and since combat is turn-based, the iPad’s screen doesn’t hamper the action, because gameplay isn’t dependent upon split-second
accuracy.
Gameplay is based on the third edition of Dungeons and Dragons, so if you’re familiar with that system, you’ll be right at home. If not, KOTOR handles the mechanics for you, so there’s no need to track armor class ratings or look for dice. However, you do need to pick out your character’s attributes, initial skills, and feats in the beginning, and choose additional feats and skills at every level, but the game can handle this automatically if you prefer.
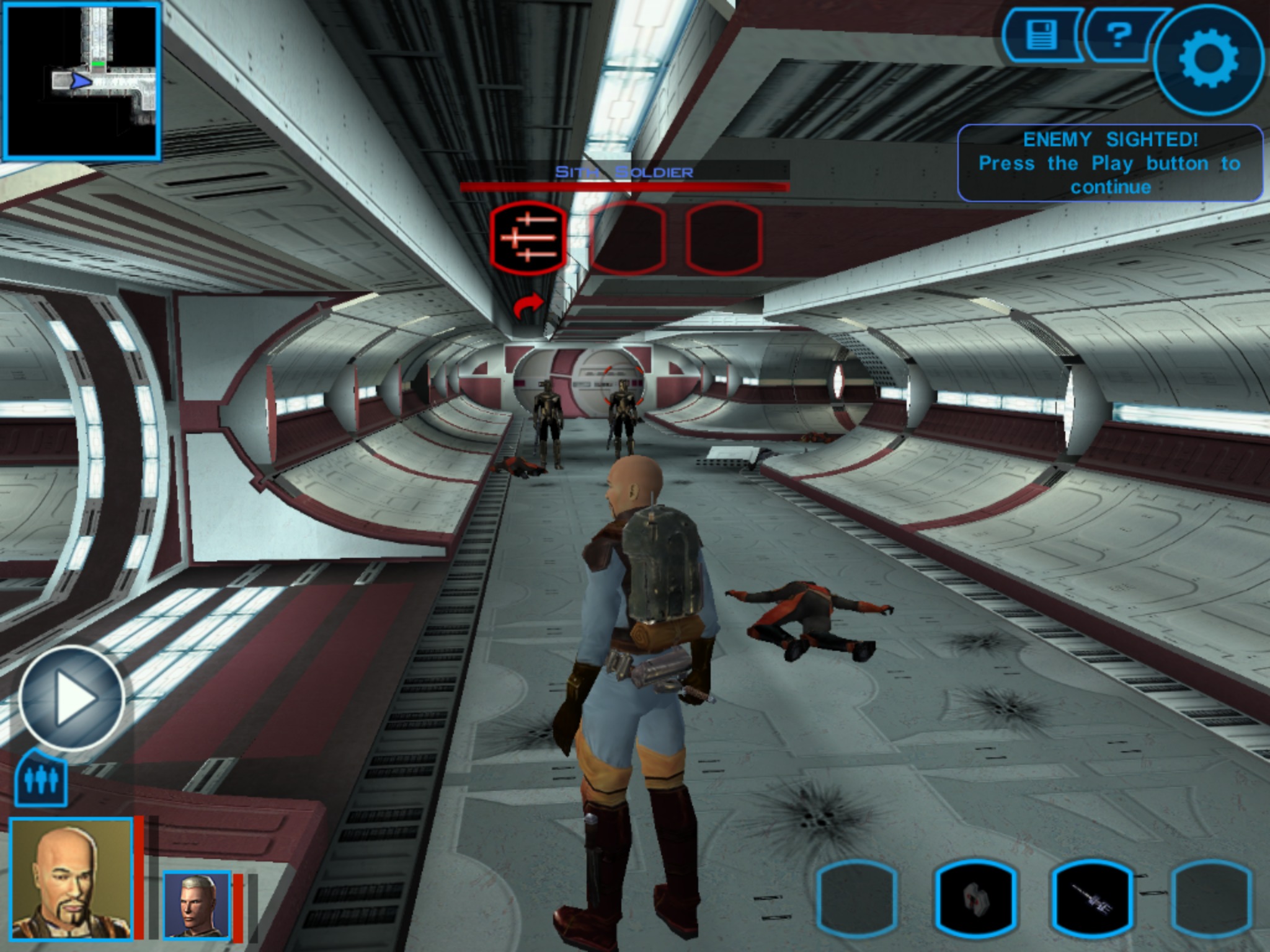
You start KOTOR by creating a character, who wakes up on a Republic ship, the Endar Spire, that’s under Sith attack. After escaping, you travel across the galaxy completing quests, making new friends, and eventually training to become a Jedi Knight, all leading up to the final showdown with the evil Darth Malak and one of the best plot twists of all time.
One of the great things about KOTOR is that it keeps much of the charm of the original trilogy, while adding its own unique touches. There’s a character who’s clearly a stand-in for Han Solo, piloting a ship that might as well be called the Millennium Falcon. But then you have companions like HK-47, a murderous, misanthropic droid who refers to humans as “meatbags.” His lines are often darkly hilarious, which is why he’s considered one of the best video game characters ever.
KOTOR is a free-roaming world — worlds actually. Drag on the left side of the screen to run around and drag on the right to move the camera. You interact with objects by tapping on them, and if you happen across an enemy, the game pauses automatically to let you queue up actions. While the combat is turn-based behind the scenes, the action plays out in real time, but you always have the option of pausing to think out your next move.
The original game was developed by BioWare, in its prime, and like most of BioWare’s role-playing games, KOTOR offers you moral choices. Your character has a gauge that measures whether your character leans more toward the light side or dark side of the Force. Do good and say nice things and you’ll grow in the light side. Do bad and you become more evil. It’s best to stick with one or the other, as the more aligned with a side of the Force you are, the stronger those Force powers are. For example, good characters are better at healing
and protection, while bad characters are better at shooting lightning bolts and telekinetically choking enemies. Your alignment also affects your appearance, what equipment you can wear, and even the course of the game, with multiple endings depending on the decisions you make. Would you rather defeat Darth Malak and the Sith, or kill him to take his place?
You’re not alone in your quest. Two companions can tag along at a time, and you’ll meet a number of them throughout the game that you can switch out. Your companions have different strengths and weaknesses that complement your character’s skills. You can also control a companion manually at any time for fine control.
If you’ve never played KOTOR before, I’d like to offer some tips. First, bear in mind that your character will eventually become a lightsaber-wielding Jedi, so it pays to invest in melee-related attributes and feats early in the game. It’s a while before you have access to lightsabers, but until then you can swing swords. Granted, it makes the beginning tougher, and you’ll feel silly rushing at a guy with a katana while he’s shooting blaster bolts at you, but trust me, it pays off.
Second, focus on your combat, persuasion, and Force abilities. Don’t waste skill points and feats on things like lock-picking and computer hacking, as those are the sort of things your companions can help you with. However, persuasion is an important skill, as it can open up gameplay options that otherwise wouldn’t be available.
Third, I found it helpful to turn up the control sensitivity in Options > Gameplay. The default is set pretty low, which means you’ll be dragging your thumb all over the screen to move around. I cranked it up to the highest level to save my hands the strain.
Finally, consider early on which side of the Force you want to fall on. I’m usually a goody two-shoes in these sorts of games, but for my first play-through, I went with the dark side, as it offers a number of powerful offensive abilities and, in my opinion, somewhat better equipment.
No matter how you play Star Wars: Knights of the Old Republic, it’ll provide dozens of hours of entertainment for the $9.99 asking price. If you’re a fan of Star Wars and are looking for some diversion this holiday season, you won’t want to miss it.
TidBITS Watchlist: Notable Software Updates for 9 December 2013
Apple Remote Desktop 3.7.1 — Apple has released version 3.7.1 of the Admin and Client editions of Apple Remote Desktop, adding support for OS X 10.9 Mavericks, improving the reliability of the kickstart command line utility, and fixing the “Display full screen” option in Control & Observe preferences. The update also improves support for Macs with multiple displays and multiple IP addresses, adds automatic copy and paste between local and remote computers, and improves reliability of screen sharing sessions.
Additionally, the remote desktop management software fixes a bug that caused the OS X firewall to block Remote Desktop connections. Apple notes in a support page that if you previously lost access to Remote Desktop after updating to version 3.7, restarting the client computer after installing version 3.7.1 should automatically add the correct firewall rule. Finally, Apple has updated the app’s companion Dashboard widget to version 3.7. ($79.99 new from the Mac App Store, free update via Software Update (12.9 MB) or as separate Admin (19.6 MB) and Client (5 MB) downloads)
Read/post comments about Apple Remote Desktop 3.7.1.
Sandvox 2.8.7 — Karelia has released Sandvox 2.8 with fixes for minor incompatibilities with OS X 10.9 Mavericks, as well as an issue with partially drawn Site Navigator icons (particularly on Mavericks). The Web site authoring tool also restores word-wrapping to long site menu titles on certain designs (and sub-menu titles on all designs), fixes an alignment issue in the sidebar with Facebook Like buttons, fixes a problem with extracting non-image media files from sites, and improves options for filenames for better compatibility when transferring documents via legacy filesystems. As with many of this week’s software
updates with Mac App Store editions, Sandvox remains at its previous version number (2.8.6) at Apple’s software storefront. ($79.99 new, free update from Karelia or the Mac App Store, 38 MB, release notes)
Read/post comments about Sandvox 2.8.7.
1Password 4.1.1 — AgileBits has released 1Password 4.1.1 with the option of updating an existing Login password directly in the browser extension. And if you have more than one Login for a site, you can choose which one you want to update. The new release also adds a new multi-column display option, a print feature that can handle individual items or a list, the capability to search across all fields, and localizations for Dutch and Afrikaans. It also fixes a problem where syncing won’t start automatically after items are imported and a bug that created generated passwords for “com.apple.Safari” instead of the
current Web site.
The Mac App Store version of 1Password is set to be updated to version 4.1 with these same changes (4.1.1 is for those who purchased through AgileBits). However, 1Password remains stuck on version 4.0.8 at the Mac App Store as of this posting (which makes this writer question why he ever thought it was a good idea to buy his copy from Apple’s storefront). ($49.99 new with a 25 percent discount for TidBITS members when purchased from AgileBits, free update, 35.6 MB, release notes)
Read/post comments about 1Password 4.1.1.
BBEdit 10.5.6 and TextWrangler 4.5.4 — While nary a new feature has been added to BBEdit 10.5.6, Bare Bones Software stuffed this version of its flagship text editor full to the gills with well over 90 fixes. One notable change sees BBEdit no longer requiring items in the Stationery application support folder to have the Finder “Stationery Pad” option turned on in order for them to appear in BBEdit’s Stationery menu or palette. As per usual, the release notes are breezy and sound like they’ve been written by an actual person. Here are just a few of our favorite nuggets from this update:
Application startup performance has been significantly improved. Anyone who has complained that BBEdit is slow to launch is going to have to find something else to complain about.
In a Markdown document, a list which is immediately preceded by a horizontal rule —- or a headline is now recognized as such. The documentation says to put blank lines before and after “block elements” (like lists and horizontal rules), but the implementations all support this format. #likeUnscramblingAnEgg
Hex Dump just got made wicked fast. You’re welcome.
Bare Bones has also updated TextWrangler to version 4.5.4, with the free text editor receiving most of the same fixes and refinements accorded to BBEdit. Note that as of this writing, neither Mac App Store editions of BBEdit or TextWrangler have been updated to the most recent releases. ($49.99 for BBEdit, 12.9 MB, release notes; free for TextWrangler, 9.8 MB, release notes)
Read/post comments about BBEdit 10.5.6 and TextWrangler 4.5.4.
ScreenFlow 4.5 — Telestream has released version 4.5 of its ScreenFlow screencast recording app with a number of improvements and a lengthy list of fixes. The update expands support for publishing screencasts directly to Dropbox and Google Drive as well as sharing them to Facebook, and the Upload Manager now uploads videos in the background. Other changes include the capability to manage transitions and mark favorites, an added search field to the Video & Audio filter popover, a fix for a bug that caused edits to be lost on OS X 10.9
Mavericks, and the added capability to double-click a source to send it to the timeline when in the media library list mode. ScreenFlow 4.5 now requires 10.7 Lion or later. For a complete rundown of the new features, download the PDF release notes from Telestream’s support page. Note that as of this writing, the Mac App Store version of ScreenFlow sits at version 4.0.4. ($99 new from the Telestream Web site or $99.99 from the Mac App Store, 33.8 MB)
Read/post comments about ScreenFlow 4.5.
Piezo 1.2.3 — Rogue Amoeba has updated Piezo to version 1.2.3 to add initial compatibility with OS X 10.9 Mavericks. Like the simultaneously updated Airfoil 4.8.2, Piezo 1.2.3 gains an overhauled audio capture engine to support Mavericks, and some audio capture sources may behave differently. (If you experience problems, you can submit feedback with this handy support form.) Additionally, due to this large under-the-hood change, Piezo can no longer capture audio from Safari in Mavericks (but a Rogue Amoeba blog post notes this limitation can be worked around easily by streaming audio from Google Chrome or Firefox instead). Other changes include added compatibility with the Microsoft Lync instant messaging and conferencing app, a fix for a glitch with the counter and file name on Mavericks, and an update to requiring 10.7 Lion and later. Note that as of this writing, the Mac App Store version of Piezo is stuck at version 1.2.2. ($15 new with a 20 percent discount for TidBITS members when
purchased from Rogue Amoeba, free update, 7.2 MB, release notes)
Read/post comments about Piezo 1.2.3.
Airfoil 4.8.2 — Rogue Amoeba has updated Airfoil audio transmission utility to version 4.8.2 with initial compatibility with OS X 10.9 Mavericks, though Mavericks compatibility for the Airfoil Video Player is still in progress. (A Rogue Amoeba blog post offers more details on Airfoil Video Player compatibility.) The audio capture engine has also been overhauled to support Mavericks, and Rogue Amoeba warns that some audio capture sources may behave differently. (If you experience problems, you can submit
feedback with this handy support form.) The release also updates the Instant On component to version 7.1 to improve System Audio capture and audio capture from Safari, supports enhanced metadata and remote control of Vemedio’s Instacast for Mac as well as iTunes Radio, ensures that Airfoil and App Nap play nicely with one another, and fixes an issue with the Airfoil menu bar icon not appearing at launch on Mavericks. ($25 new with a 20 percent discount for TidBITS members, free update, 14.5 MB, release notes)
Read/post comments about Airfoil 4.8.2.
Fission 2.2 — Rogue Amoeba has released Fission 2.2 with support for importing more audio formats. The audio editor can now import MPEG layer 1 and 2, AIFF-C, Ogg Vorbis, Shorten, RealAudio, Windows Media Audio (WMA), AMR, QDesign Music, WavePack, and Monkey’s Audio. The update also fixes several crashes with the Batch Converter, reports file sizes in powers of ten (matching the Mac OS X Finder), removes outdated references to QuickTime importing, and now always displays the Start window at launch (and if the window is manually closed, Fission will remember not to open it until the next launch). ($32 new from Rogue
Amoeba with a 20 percent discount for TidBITS members, free update, 14.3 MB, release notes)
Read/post comments about Fission 2.2.
Marked 2.2 — Brett Terpstra has released Marked 2.2, calling it a “pretty big update” on his blog (for our review, see “Marked 2: A Must-Have for Markdown Writers,” 1 November 2013). In addition to stability, speed, and rendering fixes, notable changes to the Markdown previewer include the capability to create blank new files and open them in your editor, separate word counts/stats for different panels of the CriticMarkup preview, and the capability to quickly locate and edit nested files within a multi-file
document (Terpstra promises to explain and demonstrate this final feature in screencast soon). Other changes include an update to version 4.4 of MultiMarkdown, tweaks to memory management, a fix for a bug where renaming or moving a file would result in a File Type Fail, and a fix for a crash that occurred when canceling a word repetition processing session. Terpstra has also created a Github repository for sharing custom Marked styles, and he explains how to create and use styles on his blog. ($11.99 new, free update, 16.2
MB)
Read/post comments about Marked 2.2.
Nisus Writer Pro 2.0.7 and Nisus Writer Express 3.4.6 — Nisus Software has released Nisus Writer Pro 2.0.7 and Nisus Writer Express 3.4.6, both maintenance releases offering a festival of fixes. Both editions of the word processing app squash a bug that caused a crash for those running Mac OS X 10.6 Snow Leopard after pasting table cells with an applied list style or when closing documents with some smart content, load language icons in the background to avoid a slowdown with 10.9 Mavericks, and fix an issue that caused a crash when editing an equation in the MathType equation editor. On the
hyphen front, the update ensures that hyphenation patterns are properly respected (some hyphenation for non-English languages was suffering in the previous releases) and that soft hyphens successfully transfer to Microsoft Word. Nisus Writer Pro 2.0.7 also resolves a change-tracking issue that triggered unpredictable behavior after typing over text with a straight quote that was then automatically corrected into a smart quote — since we reported this one, we’re particularly happy to see it fixed so quickly. (Nisus Writer Pro: $79 new, free update, 179 MB, release notes. Nisus Writer Express: $45 new, free update, 50.9 MB, release notes.)
Read/post comments about Nisus Writer Pro 2.0.7 and Nisus Writer Express 3.4.6.
Fantastical 1.3.11 — Bringing the same precise timing capabilities of its calendar entries to reminders, Flexibits has released Fantastical 1.3.11 with the addition of a due time field when you select Due Date in a task. The calendar app also fixes errors when using iCloud, an issue that prevented Outlook events from updating, a bug that made Fantastical appear partially offscreen when using multiple displays on OS X 10.9 Mavericks, and a potential hang when creating events with invitees on Mavericks. ($19.99 new, free update from Flexibits and the Mac App Store, 11.7 MB, release notes)
Read/post comments about Fantastical 1.3.11.
DEVONagent 3.6 — DEVONtechnologies has updated its three editions of DEVONagent (Lite, Express, and Pro) to version 3.6 with new plug-ins for searching IEEE Xplore and EUR-Lex, plus improved plug-ins for searching Blekko, Google Patents Search, and the American Chemical Society. DEVONagent Express and Pro increase the maximum download size to 64 MB, while DEVONagent Pro adds an AppleScript command for retrieving objects of an HTML page for a specified scanner. The Pro edition also improves reliability of newly reported results, adds a new PingUrl to the plug-in API to send an initial request
to an engine before searching (to disable JavaScript), enlarges the icons in the Objects pane of the Search and Browser windows, and fixes CSV export compatibility with Quick Look. As of this writing, all three DEVONagent editions remain at version 3.5.2 in the Mac App Store. (All updates are free. DEVONagent Lite, free, release notes; DEVONagent Express, $4.95 new, release notes; DEVONagent Pro, $49.95 new with a 25 percent discount for TidBITS members, release notes)
Read/post comments about DEVONagent 3.6.
DEVONthink and DEVONnote 2.7.2 — DEVONtechnologies has updated all three versions of DEVONthink (Personal, Pro, and Pro Office) and DEVONnote to version 2.7.2. DEVONnote and all three editions of DEVONthink receive improved support for OpenMeta tagging, the addition of a New Group button to the Take Note panel (plus the Clip to DEVONthink panel in DEVONthink), support for Mavericks tags entered via the title bar of documents or via save dialogs, bug fixes for several freezes in Mavericks, and a workaround for a broken script issue caused
by Evernote and EvernoteHelper.
All three editions of DEVONthink can now convert images to rich text (RTFD) and save PDF forms with entered data on Mavericks, and contextual menus that appear when viewing images now have an Edit command. Additionally, the update provides more reliable thumbnailing of QuickTime movies on Mavericks, enables viewing of PDF document sizes in centimeters and inches instead of just pixels, and improves handling of the Activity panel in Full Screen mode. DEVONthink Pro and Pro Office add RSS feeds without links (such as from Simplenote), and DEVONthink Pro Office adds support for MailTags 4 as well as a Start/Stop Server command in the Tools menu. (All updates are free. DEVONthink Pro Office, $149.95 new, release notes; DEVONthink Professional, $79.95 new, release notes; DEVONthink Personal, $49.95 new, release notes; DEVONnote, $24.95 new, release notes; 25 percent discount for TidBITS members on DEVONnote and all editions of DEVONthink)
Read/post comments about DEVONthink and DEVONnote 2.7.2.
KeyCue 7.1 — Following up on its recent upgrade to version 7.0 (see “KeyCue 7.0,” 10 October 2013), Ergonis has released KeyCue 7.1 with a couple of new features and improvements. The update adds new attributes for custom themes (such as separator lines between menus and uniform menu/submenu widths); adds a keyboard shortcut for searching; ensures the search field works with Chinese, Japanese, and Korean (CJK) input methods; and works around an issue that resulted in incorrect characters instead of key symbols. (€19.99 new with a 25 percent discount for TidBITS members, free update, 3.4 MB, release notes)
Read/post comments about KeyCue 7.1.
ExtraBITS for 9 December 2013
We’re back from Thanksgiving break (sorry for forgetting to warn you of our week off!) with a heaping helping of ExtraBITS. Google has made it easier to move away from Gmail and Google Calendar, President Obama revealed that he’s not allowed to have an iPhone, the value of enterprise hard drives has been questioned, and developer Matt Gemmell explains why one device doesn’t fit all. Apple’s restrictions are putting a chokehold on Smile’s TextExpander touch, there’s a new guide to writing on the go, an Esquire reporter broke the rules of Google Glass to see what would happen, and we have more behind-the-scenes stories from Apple Geniuses.
Google Simplifies Exporting Gmail and Google Calendar Data — Worried about being able to extract your data from the Googleplex? Google has now added Google Calendar export to Google Takeout, which enables you to download a copy of all your data from 16 Google services. Even more important will be Gmail export (rolling out over the next month), particularly for those who are still having trouble with Apple Mail in Mavericks not playing nice with Gmail. We’d like to see all companies with cloud-based services offer similar data export options.
iPhone Not Secure Enough for the President — President Obama has admitted that he isn’t allowed to have an iPhone, due to security concerns. Instead, the president uses a BlackBerry outfitted with secret encryption devices. President Obama was famously a BlackBerry fanatic when elected in 2008, and had to fight with the Secret Service to keep it.
Are Enterprise Drives Worth It? — Cloud backup service Backblaze has conducted another study of hard drive reliability, this time pitting consumer-grade hard drives against the more expensive enterprise-level disks. Over the span of three years, 4.2 percent of the consumer drives failed, while the enterprise drives suffered a 4.6 percent failure rate. The caveats are that Backblaze tested 14,719 consumer-grade drives against 368 enterprise drives, and the two sets were used for different purposes. While more data is needed to compare longer-term reliability, Backblaze noted that longer
warranties are the one clear advantage of enterprise drives.
Acknowledging Compromise: No One Device Fits All Situations — In this article, which originally appeared in Jim Dalrymple’s The Loop Magazine, Matt Gemmell makes the compelling point that we have six categories of consumer computing device (primary work machine, portable machine, tablet, smartphone, gaming device, and reading device), and we shouldn’t fool ourselves into thinking that any one is — or could be — best in all situations. While financial or physical limitations might artificially restrict your options, the piece offers a modern reminder of the age-old adage about choosing
the right tool for the job.
Smile Struggles to Make TextExpander touch Acceptable to Apple — First, Apple changed how persistent pasteboards worked in iOS 7, breaking the integration between Smile’s TextExpander touch and the numerous apps that supported Smile’s text expansion utility. Then Apple rejected a version of the app that stored shared snippet data in long-past completed reminders (not surprising — it was a serious hack). Smile has now worked around the problem by using x-callback-url in TextExpander touch 2.3, but the downside is that you’ll need to do something to acquire and update
snippet data in each supported app. This situation captures perfectly the tension between Apple’s push for complete security and users’ desire for apps to work together.
Find Holiday Gift Ideas in “The Mobile Writer” — Our tech-journalist colleague Julio Ojeda-Zapata has turned his attention to answering the question of whether one can write effectively on mobile devices in his latest book, “The Mobile Writer.” Although it’s available only for the Kindle at the moment (EPUB and print to follow), the $2.99 title is otherwise ecumenical, covering Android tablets, Chromebooks, and Windows mobile devices in addition to the iPad and iPhone gear you’d expect. The key utility of the book at this time of year lies in its
recommendations for accessories and writing apps for the textually active folks on your holiday list.
Google Glass: Doing It Wrong — In Esquire, Google Glass Explorer A. J. Jacobs describes his mission to do everything with Google Glass that his Google handlers told him not to do. He used the controversial wearable to read Moby Dick, cheat at poker (he gave the money back), and help a friend talk to the opposite sex.
More Gonzo Tales from the Apple Store — The pseudonymous Apple Genius “J. K. Appleseed” returns to McSweeney’s with stories submitted by fellow Apple Geniuses. This brief anthology includes a hotshot “pickup artist,” a visit from a homeless man on New Year’s Eve, a song trapped in a USB cable, and how sensationalist Apple stories can be harmful.