TidBITS#1248/10-Nov-2014
If your email address is managed by Apple, AOL, or Yahoo, this may be the first issue of TidBITS you’ve received in a while — sorry! Those services were incorrectly blocking us as spam, and Adam Engst explains what he’s done to address the current situation. Microsoft has now brought Office to the iPhone, and opened up more free features for both iPad and iPhone users. Julio Ojeda-Zapata looks at what’s new in the mobile Office apps, and what’s coming down the pike. In a pair of security-related articles, Josh Centers reviews the Authy two-factor authentication app, and Rich Mogull explains why Apple’s biggest security challenge is… you. Finally, Michael Cohen answers a frequent reader question: can iCloud Drive take the place of Dropbox? Notable software releases this week include BBEdit 11.0.1, CrashPlan 3.6.4, Quicken 2015 for Mac 2.2, Pixelmator 3.3, and ReadKit 2.4.2.
TidBITS Delivery Restarted for iCloud, Yahoo, and AOL Subscribers
Do you use an AOL, Yahoo, or iCloud (mac.com, me.com, or icloud.com) email address? If so, and if you subscribed to the email edition of TidBITS at some point in the past but stopped receiving issues along the way, my sincere apologies. Recently, while tracking down a problem that caused significant email deliverability problems for comcast.net addresses (“Comcast Email Delivery Restarted for TidBITS Subscribers,” 3 November 2014), I realized that thousands of subscribers from AOL, iCloud, and Yahoo had also bounced due to inaccurate spam filtering on the part of those email providers. The iCloud bounces happened in the past few weeks, but the AOL and Yahoo bounces took place sometime
earlier. (Note that Yahoo manages email for a number of other domains, many associated with AT&T and the Baby Bells, so this applies to you if your address is at sbcglobal.net, bellsouth.net, att.net, pacbell.net, ameritech.net, swbell.net, and even the Canadian provider rogers.com.)
I have now restarted email delivery for everyone in these domains, so if this is the first issue of TidBITS you’ve received in a while, welcome back, and I’m tremendously sorry for the deliverability problems! If you’d like, you can resend issues to yourself manually, which is also a great way to test if your email provider is blocking TidBITS for some reason. For details, read “Resend TidBITS Issues to Yourself” (8 March 2013).
You can also check on the status of your subscription and restart delivery manually in the event of bounces by logging in to your account. That page also lets you change your name, email address, password, and more.
Of course, if you’ve already resubscribed to TidBITS from another email address, or if you’re no longer interested in Apple-related news and products, unsubscribing is simple. Just scroll to the very bottom of the message and click the Unsubscribe link there.
How Did This Happen? — We’ve been distributing TidBITS via email since 1990, with the technology underlying the list changing a number of times. We currently use a homegrown system that ties in with the overarching account database that also tracks everyone who buys Take Control books, so sending email, whether for TidBITS or Take Control, is a matter of building a list on the fly from a database query.
Because we’ve been doing this for so long, and for the most part successfully, I’ve been lax in keeping up with the latest in the email deliverability world. Or, rather, I was until earlier this year, when I buckled down, implemented technologies like SPF and DKIM, and started signing up for feedback loops that alert me when a subscriber at a major email provider marks one of our mailings as spam instead of unsubscribing.
(Marking a legitimate, if unwanted, message as spam is unfortunately common, but please don’t do it, because it hurts the reputation of the sender for no reason, and that in turn can hurt email deliverability to other users in your domain. To get off a list you subscribed to, always use the unsubscribe link, usually available at the bottom of a message.)
One aspect of our system that’s not ideal, in retrospect, is that the primary reporting it provides is the number of active users sent to each week. In the past, I’ve often gone weeks or months without checking it, since it normally isn’t particularly interesting. Losing 750 Comcast subscribers was noticeable, and the loss of another few thousand iCloud subscribers on 27 October 2014 also got my attention. Unfortunately, the URL in the bounced messages that purported to explain the problem showed that there was no problem, and email to [email protected] is bouncing.
I’ll be keeping a closer eye on both subscription numbers and the bounce logs in the future, and if you notice problems, please let me know and complain to your ISP or email provider.
Microsoft Office Comes to the iPhone, and It’s Free
Microsoft raised eyebrows earlier this year when it released a full iPad version of its flagship Office productivity suite without providing comparable touch-friendly software for its own Windows platform (see “Office for iPad: A Deep Look,” 3 April 2014).
That trend continues in what has clearly become aggressively a cross-platform age for the once Windows-centric software company. Last week, Microsoft made a slew of Office-related announcements involving the iPhone, iPad, and Android, all while continuing to treat Windows as a bit of an afterthought (at least publicly).
Most surprising, many Office features are now available for free. This isn’t Steve Ballmer’s Microsoft anymore.
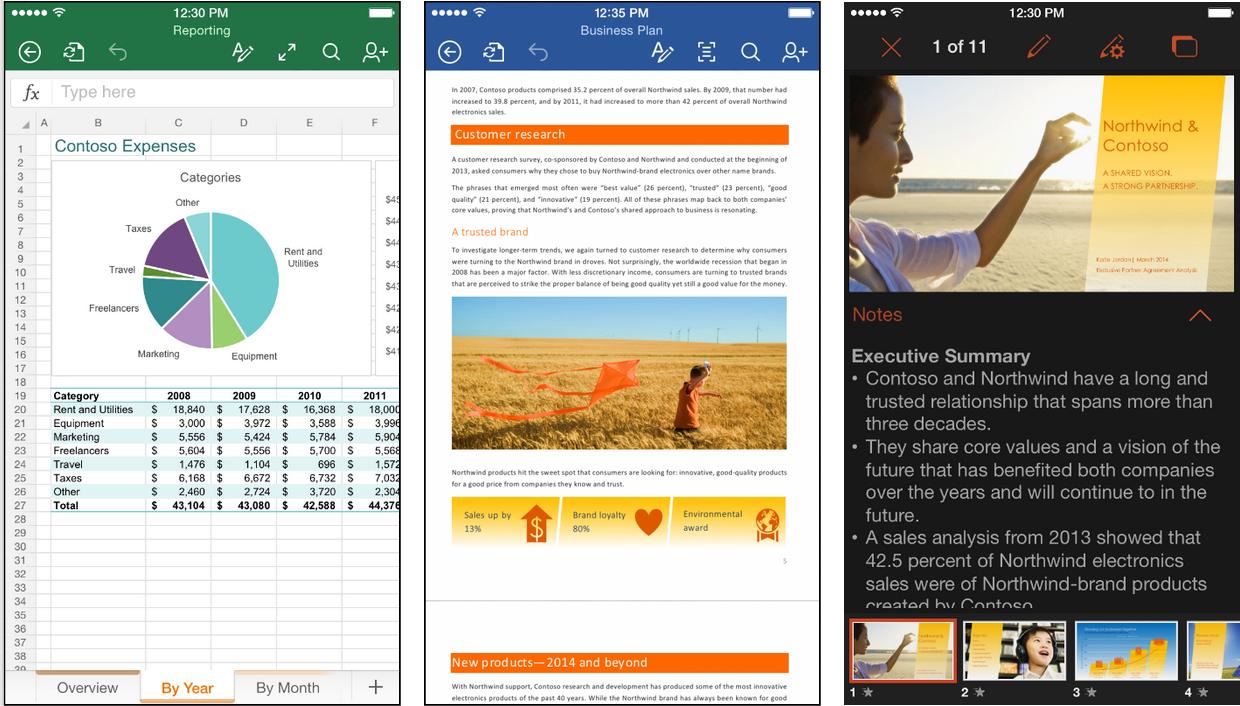
Office for iPhone — Perhaps the biggest Office news for Apple aficionados involves the iPhone. Microsoft released new and universal versions of Word, Excel, and PowerPoint that work on either the iPad or iPhone, with the latter tweaked for the iPhone’s smaller screen.
Word, for instance, makes the most of the iPhone’s limited screen real estate by revealing the formatting pane with the tap of a button. It slides up from the bottom and can be dismissed with another tap.
That formatting pane is nicely designed to save space. The traditional Insert, Layout, Review, and View menus, which are in a toolbar along the top on the iPad, live in a tidy popover on the iPhone. There are lots of controls in that formatting pane, but they’re a cinch to find with a quick scrolling motion.
Word users now have two viewing choices: the default view and one Microsoft calls an “easy-to-read layout” or “reflow view.”
These new, standalone versions of Word, Excel, and PowerPoint for the iPhone replace a single Office Mobile app that iPhone users could use to open and edit Office files. Office Mobile had a limited feature set, didn’t have many fans, and won’t be missed.
Relatively minor feature upgrades apply to both iPhone and iPad. The Office apps have more-customizable charts, for instance (but only for paying premium users). PowerPoint also tweaks animations, theming, zooming, and background formatting.
Microsoft did not announce updates to its OneNote apps for iPhone and iPad, but late last month it pushed out an update with iOS 8 support and optimized viewing on the iPhone 6 and iPhone 6 Plus. Those OneNote updates also added iCloud Drive support and improved security, including compatibility with Touch ID.
Editing for Free — Microsoft’s Office apps for iOS were previously of limited use to those without an Office 365 subscription because they could only open and display Office files — editing and saving wasn’t an option.
Now it is… up to a point. Microsoft has made core editing features in Word, Excel, and PowerPoint free for all users while keeping advanced, business-centric features as premium offerings for Office 365 users.
The new Office apps are now akin to certain iOS games that are technically free to play, but include in-app add-ons for those wanting the full experience. Want to level up? Pay up.
Average Office users might not feel much pressure to upgrade, though, since Microsoft has been generous in what can be done at the free level. I’m writing this article in Word on my iPhone 6 Plus without paying a dime (but I can’t sync my work with Word for the Mac for free).
Figuring out what’s possible in the free apps is a bit tricky, and some of the differences are silly. Only premium users can switch orientations in an existing Word document or create a document in portrait mode. Seriously? Macworld has a detailed rundown of free-versus-paid features. It would be nice to be able to purchase desired features à la carte, rather than having to pony up for Office 365 for just one or two paid features.
Microsoft’s move to make its Office apps essentially free is not much of a stretch when you consider it had already done so with robust browser-based versions of Word, Excel, and PowerPoint, along with OneNote.
Dropbox — Microsoft has expanded saving options, too — including added support for Dropbox. This comes courtesy of a new Dropbox-Microsoft alliance (see “Dropbox Is Coming to Office,” 4 November 2014). As a result, when I fired up the Office apps on my iPhone and logged into my Microsoft account, I was also prompted to connect to my Dropbox account. Naturally, you can still save documents to Microsoft OneDrive.
Dropbox and Microsoft are working to make their offerings more compatible. Other announced features include the option to edit Office files from within the Dropbox app, Dropbox integration with the Office Web apps, and the sharing of Dropbox links from Office, but these features did not appear to be fully active as of this writing.
Hello, Android — Microsoft had promised an Android version of Office, and that has now come to pass. Sort of.
The company has launched a preview program for early adopters who want to kick the tires on beta versions of Word, Excel, and PowerPoint for Android. You must register, but using the apps costs nothing. As of this writing, the preview is by invitation only.
The Android apps look extremely similar to the iPad versions, and are important for those individuals or companies who use a mix of mobile devices and want Office consistency across multiple platforms. Android users previously had only limited Office-like apps from third-party sources. Some such apps are nice, but for many companies only Microsoft’s official Office suite will do.
Poor Windows Users — Those on Windows PCs continue to suffer as they see iOS and Android enjoy the latest in Office goodness. I’m in that group, since I regularly rely on a Microsoft Surface tablet, and I dislike using the traditional versions of Office apps on a touchscreen.
Microsoft has said that touch-optimized Office apps for Windows will be released alongside the Windows 10 operating system, which is slated to ship late next year. No other details were forthcoming, but the company did post a screenshot of the upcoming PowerPoint.
Authy Protects Your Two-Factor Authentication Tokens
Digital security has been a hot topic this year. Between the theft of private celebrity photos (see “iCloud Flaw Not Source of Celebrity Photo Theft,” 2 September 2014) and multiple credit card leaks, it’s hard not to feel a little paranoid.
One of the best ways to improve your online security game is two-factor authentication. In short, two-factor authentication adds an extra layer of security to your password (something you know) in the form of a number that’s regenerated every few seconds, either by a dedicated device or a mobile app (something you have).
The free Google Authenticator has become the de facto industry standard in two-factor authentication. You can use it with your Google account, but it’s also compatible with Dropbox, Evernote, Facebook, Tumblr, and many other online services.
While Google Authenticator gets the job done, it has a number of potentially significant limitations. It offers no backup or sync, so if you lose the device it’s installed on, or wipe the data off that device, you’re in for a world of hurt (for an example, see “Dancing the Two-Step: Coping with the Loss of a Second Factor,” 28 August 2013). One Google Authenticator update accidentally wiped everyone’s two-factor tokens, preventing users from logging into their accounts.
Thankfully, there’s an alternative: Authy, which is free for iPhone and iPad in the App Store.
Authy has numerous features that Google Authenticator lacks. Authy can back up your two-factor tokens to the cloud, so if you wipe your phone or get a new one, you can restore those tokens and not be locked out of your accounts. Authy can also use the cloud to sync to your other devices, and the app is universal, so it works equally well on your iPhone or iPad. And if you own a newer Mac with Bluetooth 4.0 LE (I sadly don’t), you can take advantage of the complementary Authy Bluetooth app to insert your two-factor tokens on the Mac automatically, with no additional typing required.
Authy’s Tradeoffs — Hearing that Authy uploads your two-factor tokens into the cloud might make you nervous. But keep two things in mind. First, cloud-based backups are entirely optional and are off by default. Second, Authy encrypts your backups on your device before uploading them.
Regardless, as with all security decisions, Authy’s cloud features come with a tradeoff. Whenever you store sensitive information on someone else’s server, you increase the risk that it will be stolen, even if only infinitesimally. But also consider the benefits. With Google Authenticator, if you lose your iPhone, you lose access to your accounts, at least temporarily. Which scenario is more likely and/or more frightening: a single account being hacked, or losing access to all accounts due to a software glitch or a broken phone?
Authy also adds a critical security feature that Google Authenticator lacks: the option to lock the app with a PIN or Touch ID, so a thief who got past the device’s overall passcode can’t view your tokens.
Even if Authy were found to be vulnerable, online accounts protected by two-factor authentication would still be more secure than those that rely solely on a password. In addition to cracking the account password, an attacker would also have to crack your Authy password. Conversely, even if an attacker were to infiltrate your Authy account, the tokens would be useless without account passwords. Such accounts are still twice as hard to hack as those that have only a password.
For me, the decision to use Authy is simple. It lets me protect my accounts with two-factor authentication, and it reduces the likelihood of the problems from which Google Authenticator suffers.
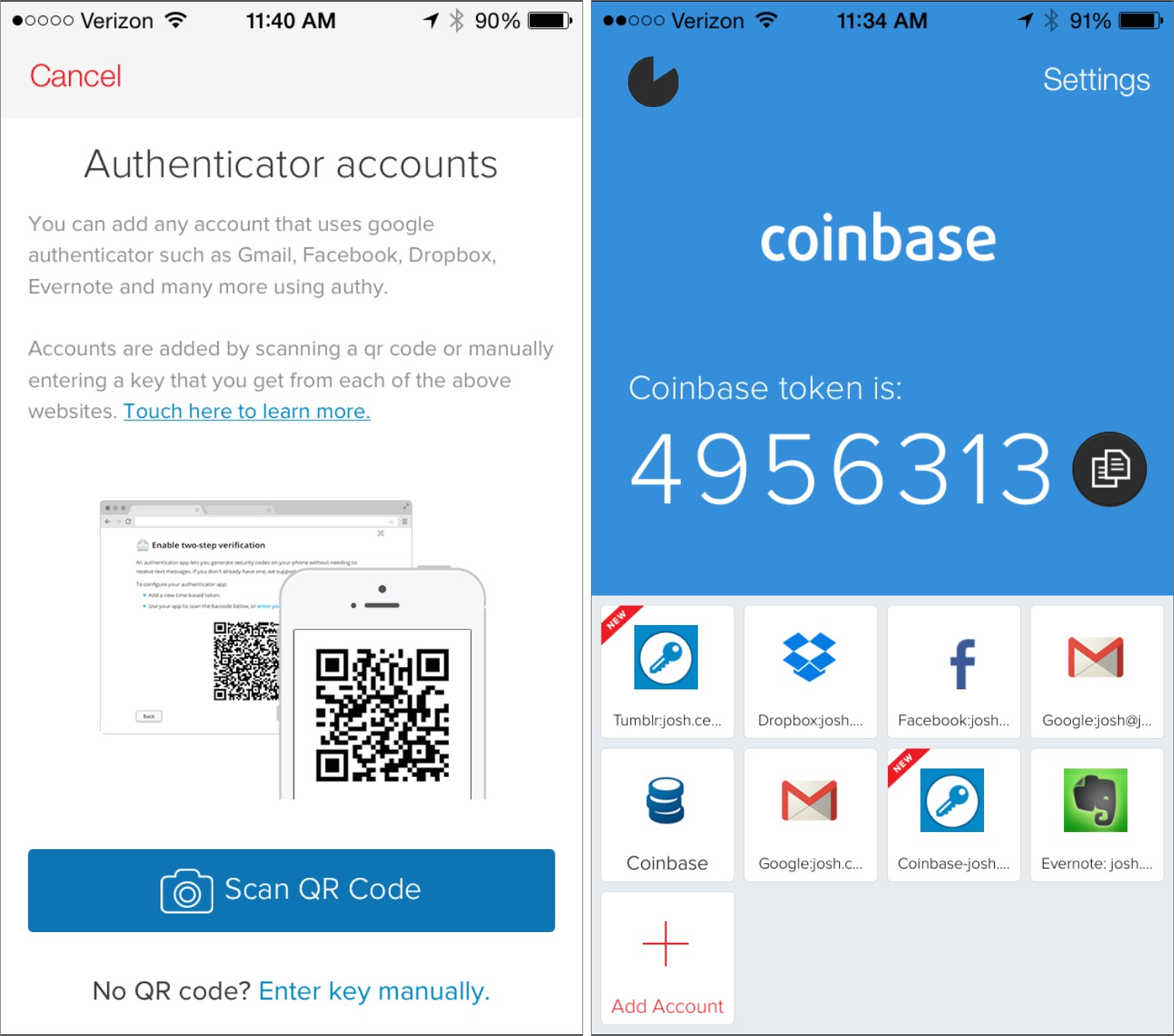
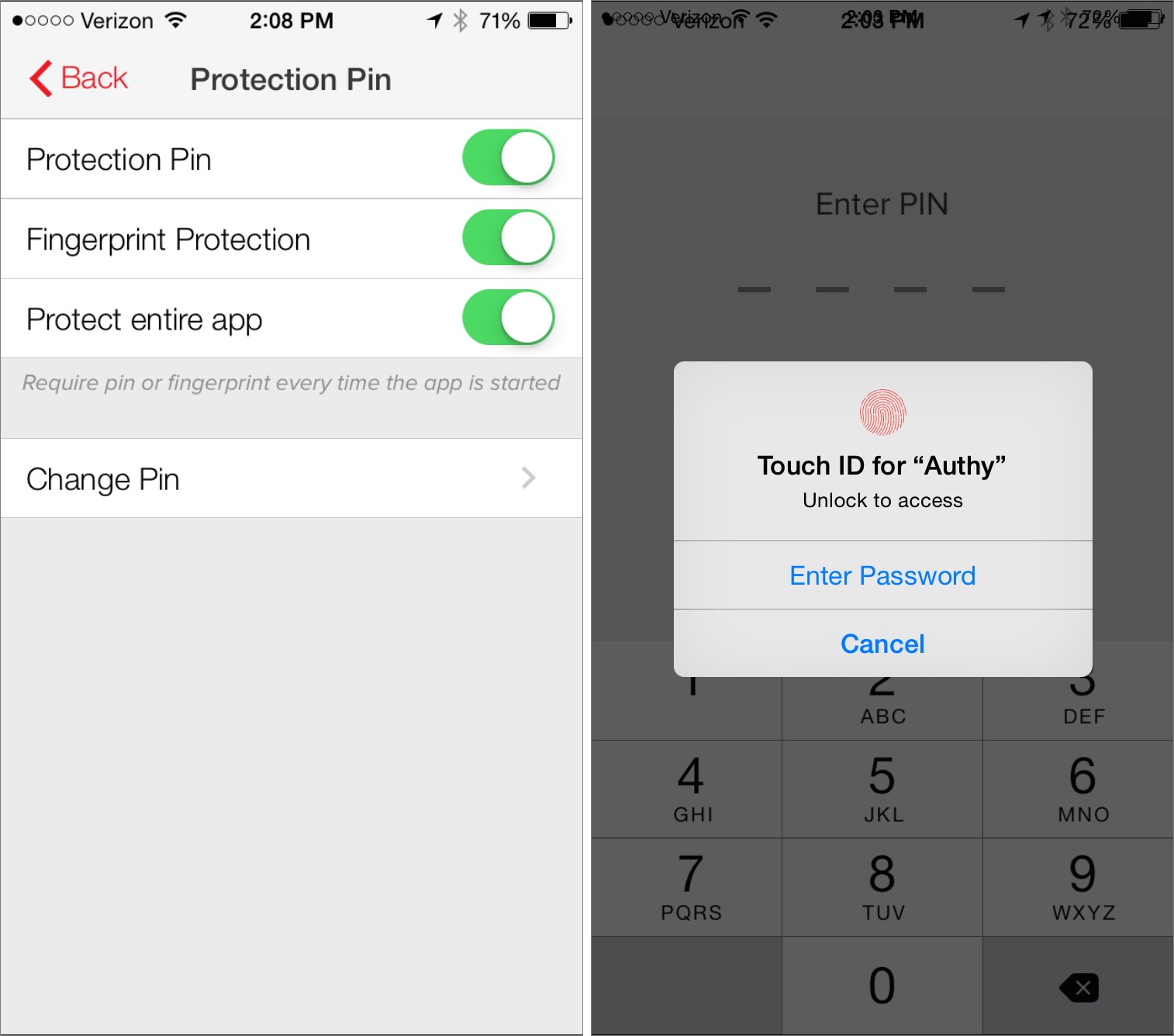
Using Authy — Authy is pretty easy to use, as two-factor authentication goes. First, you need to set up an account token. Tap Add Account at the bottom of the screen, and then either scan the QR code provided by the online service, or enter a provided code. The specifics of how you obtain either will be different with each service.
Once you’ve added one or more accounts, they appear at the bottom of the screen. If you have more than four, the row of buttons at the bottom of the screen turns into a drawer that you can expand to see additional accounts and the Add Account button. To display the necessary time-limited token that you need to enter to log in to a two-factor-protected site, simply tap an account. Be mindful of the timer — a token typically lasts only 30 seconds before it expires. If there are only a few seconds left in a token’s life, it’s easier to wait for the next one. If you’re logging in from the iOS device itself, you can also tap the blue copy button next to the token to put it on the clipboard.
If you want to manage accounts or set up additional security protections, tap Settings in the upper right. In the Settings screen, the My Account pane lets you set what phone number and email address are tied to your Authy account. These are important: when you move to a new iPhone, Authy will ask you to use one of these contact methods to prove your identity. You can also set a Protection PIN and/or Fingerprint Protection here, which I recommend. If your device supports Touch ID, I think it’s silly not to enable
Fingerprint Protection, because it adds that much more security with little hassle.
The Accounts pane lets you manage your tokens and set better names, but perhaps more important to new users, it’s also where you set up cloud backups and change your backup password.
The Bluetooth pane merely lets you allow Authy to use Bluetooth to talk to the Authy Bluetooth app, if that option is available to you.
Finally, the Devices pane lets you set up and manage multi-device support. Activating other devices works by what Authy calls Inherited Trust. In other words, when you try to use the same Authy account on another device, you must approve it from an already authorized device. In practice, this seems like a good balance between security and convenience.
Boarding Up the Windows — These days, digital security is kind of like a zombie apocalypse movie. You can stock up on supplies and board up the windows, but sooner or later, probably through simple human error, a zombie will break in.
But just because your efforts may be futile in the end doesn’t mean you stop nailing boards. At the same time, you don’t want to put up so many that you can’t get out when you need food.
That’s roughly how I see Authy. While, by the developers’ own admission, its cloud features can potentially make you less secure, they also make it harder to lock yourself out of your digital house.
Also keep in mind that Authy does only one thing — it’s not a silver bullet for online security. It won’t prevent your credit card number from being stolen from a retailer, nor, thanks to Apple’s weird two-factor authentication implementation, could it have prevented Jennifer Lawrence’s pictures from being stolen.
Authy is just another tool in your security kit, but a useful one that makes two-factor authentication less intimidating.
iCloud Drive Is Not a Dropbox Replacement
After I wrote “Moving to iCloud Drive” (15 October 2014), I received several messages asking me how to use iCloud Drive as a Dropbox replacement. As I said in several responses to those inquiries, “iCloud Drive is not a replacement for Dropbox.” But I don’t blame the inquirers for the confusion: Apple has not done a stellar job explaining iCloud Drive, nor, for that matter, iCloud in general.
Part of the problem is that iCloud is not just one thing but a whole panoply of services, including calendar and contact storage and syncing, email, location services, media and app sharing, backup, data storage, document storage, and more. From time to time, Apple highlights one or more of these services in its marketing, usually when it is introduced or expanded, but to my knowledge the company has never provided a comprehensive guide to the entire beast. That’s one reason Joe Kissell’s “Take Control of iCloud” has been so successful (and yes, he’s working hard on an update that will be out shortly). As a result, we end up like the blind men in the story about the elephant, each of us thinking that iCloud is whatever part of the elephant that we have happened to have laid our hands upon.
iCloud Drive is one part of the iCloud elephant, but Apple has not gone to great lengths to explain which part of the beast it is, so it’s easy to think that iCloud Drive is a brand new animal. But it’s neither completely new nor its own animal. It’s simply a more mature form of an existing iCloud feature: Documents & Data.
Documents & Data — Before Apple introduced iCloud Drive, each iCloud-compatible app could have its own private storage space in a user’s iCloud account. Only that app could access that space and manipulate the files stored in it. Apple slapped the generic name “Documents & Data” on that capability when talking about it to users and exposing it in interfaces. Here’s how it worked.
If an iCloud-enabled iOS app (like, say, Pages or PDFpen) had a related Mac app that also used iCloud, the Mac app and the iOS app could both access the same private storage space and use the same files. This meant that you could create a file on your iPhone, save it in iCloud, and open it on your Mac or your iPad in the related app.
However, even on the Mac, you had to use the app to create, delete, or modify files in its private iCloud storage space; the Finder had no direct access to it. (Technically, you could delve deep inside your Home folder’s Library with the Finder and find the cached iCloud files, but those cached files inside your Mac’s Library were only local copies and not guaranteed to reflect the current “truth” — that is, the master file as it was stored in iCloud itself.)
With OS X 10.10 Yosemite and iOS 8, Apple introduced iCloud Drive. But it wasn’t a replacement for Documents & Data. What it did was provide a user interface for the Documents part of Documents & Data.
iCloud Drive — On the Mac, iCloud Drive provides a Finder-accessible method for viewing, adding, and removing the documents that apps store in iCloud. In addition, it gives users a way to create their own folders in iCloud and put whatever documents they like in those folders. iCloud Drive appears as a choice in the Favorites sidebar of Finder windows and, when clicked, displays what looks very much like a normal list of folders. Looks, however, can deceive.
Many of the folders shown in iCloud Drive — in fact, all of them if you haven’t added any of your own — are not Finder-type folders at all but “app libraries.” These app libraries are how the formerly private document storage spaces for apps appear in iCloud Drive. They are still managed and maintained by the apps that own them, and what you can do with them is still largely dictated by individual apps. For example, some apps may restrict the kinds of documents you can put into their app libraries. You can’t even Get Info on an
app library “folder” in the Finder; File > Get Info is disabled, and if you try the Command-I shortcut, the Finder beeps at you.
In iOS 8, which has no Finder, iCloud Drive can be accessed from within iCloud-enabled apps — if, of course, the app’s developers provide that capability. In most cases, iCloud-enabled apps in iOS 8 display the iCloud documents they manage in much the same way that they did in earlier versions of iOS.
However, even when they display their documents in the same old way, apps can also provide a method for browsing iCloud Drive and opening compatible documents stored in other app libraries or user folders. For example, in Pages for iOS, tapping the + icon on the document manager toolbar can take you to the iCloud Drive “document picker,” from which you can open user folders and other apps’ libraries (for those apps that allow you; some libraries may be disabled or not even appear in the picker), and, from within those
libraries or folders, choose documents to open.
It’s hard to predict what an app will do when you open a document from another app’s app library or from an iCloud Drive folder. One app may make a copy and store it in its own app library; another may create an alias and store that in its app library.
For the most part, iCloud Drive simply gives you more control and convenience for managing the Documents part of the old Documents & Data service than previous versions of iOS and OS X offered. However, because it also allows you to make your own folders on iCloud Drive — even within some app libraries — and to store whatever documents you want in your folders, you can’t be blamed for thinking, “This here sure looks like I could replace Dropbox with it!” You would most likely be wrong, though.
iCloud Drive Isn’t a Dropbox Replacement — To begin with, Dropbox is far cheaper than iCloud: $99 per year for one terabyte of storage for Dropbox versus $19.99 per month (or $239.88 per year) for the same amount of iCloud storage.
But cost is just part of the reason: the two services also work differently. Take sharing, for instance. iCloud is generally all about sharing, but it’s mostly about sharing your stuff with your devices: that is, sharing the same stuff (calendars, music, mail, your budget in Numbers, and your half-finished novel in Pages) among all of your devices. Sharing stuff with other people, even other iCloud users, is not easy, and worse, the options are limited and tightly focused (such as specific photo streams or explicitly shared documents in Pages or Numbers).
Dropbox, on the other hand, lets you share folders and all the documents therein with other Dropbox users — this is how Take Control manuscripts are made available to authors and editors for writing, editing, and production. Doing the same thing with iCloud Drive would be impossible.
Furthermore, iCloud, unlike Dropbox, doesn’t store previous versions of a file (though some individual apps do), nor does it let you restore deleted files.
Most importantly, though, iCloud Drive is not just a file sharing service. Remember that apps on both Mac and iOS have a lot to say about what you can do with their app libraries. This means that the Finder, in order to create the illusion that iCloud Drive is just another drive with a bunch of folders and yet respect those individual apps’ rights and requirements concerning their own stuff, can behave unpredictably. You can’t tell by sight, for example, which app libraries will accept which files until you try them.
Also, at least in the initial release of Yosemite, the Finder can get confused when you do some seemingly normal file handling things within the confines of an app library, such as changing the name of an alias created by an iOS app. I have seen the Finder go into a spinning beachball mode from which it doesn’t recover when I have done that; other times I have seen the changed filename turn into a long string of letters and numbers. This is not the sort of behavior you want in a file sharing service.
For what it is — a better way to manage, access, and sync your documents stored in iCloud — iCloud Drive is a welcome enhancement.
But it isn’t Dropbox.
You Are Apple’s Greatest Security Challenge
Apple’s focus on the security of its operating systems used to be pretty minimal. Fortunately, it didn’t really matter.
Spend enough time in the security world and you realize that it’s defined by economics and human behavior, not technology. When I first started writing about Apple in 2006, the company had a good security team, but didn’t give it many resources. It’s hard to justify spending a lot on security when you aren’t suffering security losses.
Just ask Microsoft. For years the company didn’t invest much in security, even as Windows came to dominate the computer industry. Then the bad guys showed up, and in 2001 it became nearly impossible to protect Windows-based PCs from attack. Microsoft’s biggest customers, like big banks and the U.S. government, threatened to move to something — anything! — else as the costs to install security defenses and account for security breaches skyrocketed. The result was the Trustworthy Computing Initiative in 2002. Microsoft now has the strongest security program in the industry.
In a series of what look like near-prescient moves, Apple dodged that bullet while coming to dominate the handheld device market and increasing its share of the personal computer market. Apple learned the right lessons from Microsoft’s early failures, and as a result, we haven’t seen any significant iOS malware (most of what there is targets jailbroken devices) or a major Mac malware epidemic. In essence, particularly with iOS, Apple put security in place early, before criminals could build an attack ecosystem.
But the future is in the cloud. And Apple’s future is iCloud, the online glue that holds its entire ecosystem of devices, software, and services together. I spend most of my working hours on cloud security, and it is an indescribably difficult problem that’s only getting worse as our use of these services grows. Apple, like all major cloud providers, now faces the same security issues as banks (cue the Willie Sutton reference about “that’s where the money is”).
Talk to any bank about security, and they’ll all point to the customer account as the problem.
Chum in the Water — Little grabs attention like the words “celebrity nudes.” The phrase “chum in the water” doesn’t even begin to describe the resulting media feeding frenzy. Add in the world’s most popular technology brand, schedule it for a few weeks before the company’s biggest product announcement in years, which also included a major new financial service, and you end up with a special sort of PR nightmare.
You know the story by now. A string of nude photos of about one hundred celebrities hit the Internet over Labor Day weekend. Speculation quickly focused on iCloud backups or photos as the source, given that it came only a few days after the release of a new tool that attacked iCloud directly via a brute-force technique that most cloud services restrict (and that Apple quickly blocked).
The truth was slightly less dramatic, but no less disturbing. Within 48 hours Apple announced that iCloud in general hadn’t been hacked, and the brute-force tool wasn’t the vector. Instead, individual celebrities were deliberately targeted and their photos stolen, most likely via iOS backups to iCloud. The crimes likely occurred over a long period, and the photos didn’t necessarily all come from iCloud.
After more than 40 hours of investigation, we have discovered that certain celebrity accounts were compromised by a very targeted attack on user names, passwords and security questions, a practice that has become all too common on the Internet. None of the cases we have investigated has resulted from any breach in any of Apple’s systems including iCloud® or Find my iPhone. We are continuing to work with law enforcement to help identify the criminals involved.
To protect against this type of attack, we advise all users to always use a strong password and enable two-step verification.
iCloud wasn’t hacked, but it was. Instead of compromising some core vulnerability in the service, the criminals targeted famous users and performed a series of account takeovers. They figured out passwords or password recovery questions. I suspect they then pulled in the victims’ friends and colleagues using phishing techniques based on the initial information taken. They harvested iCloud credentials, and used hacking tools to pull down copies of iCloud backups, circumventing Apple’s normal new-device notifications (primarily used with Messages and FaceTime) and even two-factor authentication, which protected only purchases and core Apple ID changes.
Apple was in a bind. This wasn’t an issue specific to iCloud, and the company essentially blamed its customers for not protecting their accounts well enough. And Apple then recommended a solution, two-factor authentication, that wouldn’t have stopped the attacks at the time (it didn’t then apply to iCloud logins or backups). Ouch.
To be fair, Apple was correct that account takeovers are an all-too-common problem on the Internet. But decisions by Apple, such as limiting the services protected by two-factor authentication, relying on password recovery questions (which are notoriously easy to circumvent, especially for public figures), and not detecting the unusual activity on the server side all conspired to make the attackers’ jobs easier.
iCloud wasn’t compromised in general, but that’s not to say that Apple did all it could have. And even if the company had done more, there’s no guarantee that such persistent attacks could have been prevented. Account takeovers are incredibly serious, impossible to eliminate, and likely the single greatest challenge as we continue to expand our reliance on cloud computing.
Where Password Equals “Gordian” — Proving identity is a complex problem, especially since the concept of identity itself is somewhat ephemeral. Just ask any friend with a common name, like our own Michael Cohen (who is not any of these people). In the digital world, we worry less about proving identity and more about authentication, which is proving to the computer that you are the person associated with a specific account.
We do this using something you know (a password), something you have (a digital token like a smart card or a code from an iPhone app), or something you are (a fingerprint). The more of these things that are checked, the stronger the authentication.
Passwords are nearly always used as one of the authentication factors. Tokens cost money and are easy to lose. Fingerprints, or any biometric factor, raise serious privacy issues and are hard to work with reliably. Neither tokens nor fingerprints are well suited for logging into remote services, since everyone would need their own readers. Imagine having to swipe your credit card to log in to every Web site. The complexity of these systems, at scale, is nearly insurmountable with current technological and social limitations. Who provides the cards? Who manages your fingerprint template? How is this all communicated? In many cases tokens and fingerprints are less secure than passwords which is why we tend to use them as a second
factor, not the primary one.
Reducing our reliance on passwords may not be an impossible problem, but it’s one we’re a long way from solving.
Compounding the problem is the issue of account ownership and recovery. We forget passwords. We lose smart cards. Our fingerprints change. We can’t let those facts restrict access to our accounts, so we add recovery mechanisms. It might be another, stronger, password we tell the user to write down and store safely — but anything written down isn’t safe by definition. Or perhaps we require security questions we hope only the account owner can answer, but to be memorable, they have to be discoverable, as the hacked celebrities experienced.
Apple’s Challenge — Apple, Google, and other cloud providers now manage many of the most private and important aspects of our lives. We trust them with an astonishing range of information that, in some cases, has direct monetary value. They are, effectively, banks.
Securing a bank isn’t easy. Account takeovers still occur on a regular basis, but, based on my experience, at a rate far below most online services. Banks deploy a wide range of security tools with names like “risk-based authentication,” “user behavioral analytics,” and “anti-fraud analysis.” These tools catch many account takeover attempts, but not all, and financial institutions spend more on security than any other vertical market by a wide margin.
Some of the criticism I saw of Apple after the celebrity photo theft was warranted. It didn’t appear that Apple used expected detection and analysis techniques for a cloud provider of Apple’s size and importance, based on the effectiveness of the brute-force tool (even if it wasn’t used in those attacks). Two-factor authentication (your password plus a code sent to your phone) was not applied to most iCloud services and was surprisingly complex to set up. Nor did Apple send activity notifications that could have alerted a customer that someone had accessed her account and restored her data.
Apart from missing the brute-force attack vector, Apple’s security team likely isn’t to blame for most of these decisions. It is one of the best in the business but was clearly constrained by other considerations that can’t be dismissed out of hand. Send too many user notifications, and they quickly lose meaning. Require two-factor authentication too frequently and users will revolt. Still, these were concerns I had even before the incident — I always worried that no matter how strong my password, my data could be exposed to an account takeover. I wouldn’t even use iCloud backup for some of my devices.
Many of the criticisms and proposed solutions were naive. Numerous writers suggested mandating two-factor authentication. That’s fine for someone like me with multiple iPhones and iPads, plus a wife I trust. But what if you have only a single iPhone and no one you trust to recover your account? Email password resets were another option, but what happens when the associated email account is compromised or is accessible only from the device you’ve lost? Go to an Apple store with an ID? That’s fine for urbanites, but a massive inconvenience for a large swath of the population.
Hundreds of millions of customers use Apple products. I don’t know what the iCloud numbers are, but we are talking about a company that sold 10 million iPhones in a weekend. Security complexity increases exponentially as fringe situations encompass millions of users. With Apple operating on that scale, the rules change.
Even behavioral analytics (identifying deviations from normal behavior through big data and automatic analysis) fails at some point. Take our celebrities, who may use their devices from 10 countries in 10 days during a press junket. They would likely have been excluded from the rules that could detect an attack on most accounts.
Apple thus faces one of the most complex security challenges in society, and faces it at a scale only a handful of companies need to consider.
All In — Apple is fully capable of using its design and technical resources to tackle tough security issues. Touch ID is a masterful implementation of fingerprint technology. Apple approached the problem unlike anyone else, and simplified a complex problem to increase both usability and security without exposing privacy. Messages, FaceTime, and iCloud Keychain all leverage ingenious uses of encryption that are nearly transparent to the average user, yet still support more-complex options for those with greater security concerns. Gatekeeper effectively cut off the possibility of a widespread Mac malware market before it could grow. Apple Pay looks to be one of the most
secure and simple payment systems ever implemented.
Contrast these with Apple’s implementation of two-factor authentication, which is no better than anyone else’s, and until recently quite a bit worse. It’s one of those tremendously difficult problems screaming out for an elegant solution. The company’s response to authentication and account ownership requires a Touch ID–like rethinking of the problem. And to be clear, Apple is far from the first to tackle it.
Apple’s initial response to the celebrity photo thefts closed the most significant gaps. Two-factor authentication, if you enable it, now protects everything related to iCloud. Since two-factor authentication breaks third-party software that relies on usernames and passwords alone, Apple also added the capability to create secure application-specific passwords that don’t expose your entire account. App-specific passwords are bit of a hack — most other consumer cloud providers use a standard called OAuth instead — but moving directly to OAuth would break everything until developers could catch up. But Apple will need it
eventually.
Apple is also sending more notifications for logins and changes to your account. This helps, but starts veering into a Windows Vista–level of notifications, especially with all the new device-level privacy notifications in iOS 8.
We don’t know what Apple is doing on the server side, and likely never will. The company may be using a range of technologies similar to those used by banks. We do know it doesn’t use risk-based authentication, which is the technology that causes your bank to occasionally ask you if you logged in from a trusted computer. I doubt that’s the only gap.
I’m not about to tell Apple what to do, even speaking as someone who makes his living advising companies on cloud security. But I suspect there will be two basic facts about Apple’s future cloud security moves:
- Apple will tackle the authentication problem, and likely attack it from multiple angles, all with a focus on simplifying a complex situation. No single approach has ever been shown to work at the scale at which Apple operates, so the challenge will be to simplify a range of options for different user demographics. Today Apple is, at best, average at this. With iCloud becoming the center of the Apple ecosystem, the company will need to break new ground. Even very few banks, if any, face the combination of internationalization, number of users, and diverse customer skills that Apple does.
- Apple will use every cloud security option in the book, and aggressively adopt new approaches and technologies on a continuous basis. It’s the logical progression of a continual cat-and-mouse game as criminals constantly seek new ways of compromising user accounts. Apple has excellent server security, but account security requires different thinking and different tools.
At least I hope this is what Apple will do. One of my greatest fears is that Apple will focus more on trying to change user behavior, rather than improving the engineering of the systems. In a Wall Street Journal interview Tim Cook said, “When I step back from this terrible scenario that happened and say what more could we have done, I think about the awareness piece, I think we have a responsibility to ratchet that up. That’s not really an engineering thing.”
My guiding principle as a security professional is: “Don’t expect human behavior to change. Ever.” No one, not even Apple, is about to eliminate the need for passwords or come up with a single, near-perfect way to protect accounts. Nor can we rely on education or better security habits when hundreds of millions of users are involved. Apple most definitely had, and should have used, engineering options that could have reduced the chances of these attacks.
Apple just invested three years designing the first version of the Apple Watch. I look forward to seeing what the company can do with passwords and account takeovers once it truly focuses on the problem, assuming it chooses to do so.
TidBITS Watchlist: Notable Software Updates for 10 November 2014
BBEdit 11.0.1 — Bare Bones Software has released BBEdit 11.0.1, a wide-ranging maintenance update with a bevy of refinements and fixes for user-reported issues that follows the recent release of version 11.0 (see “BBEdit 11 Overhauls Features for Existing Customers,” 26 October 2014). Among the nearly 50 listed changes, the venerable text editor reduces the amount of time required to restore sleep state at startup, fixes a crash related to applying a color scheme converted from a legacy format, squashes a bug that prevented correct restoration of HTML markup palette
positions on startup, adds an expert preference to disable text smoothing for a specific font, reduces the transient memory requirements of the SGML/HTML parser (which should help with larger documents), and adds ellipses to the Preferences and Setup menu commands “because some people just want to watch the world burn” (Michael Cohen’s personal favorite change). BBEdit 11 is priced at $49.99 for new licenses, while BBEdit 10 users can upgrade for $29.99 and those with licenses for BBEdit 9 or earlier can upgrade for $39.99. Those who bought BBEdit 10 on or after 1 May 2014 are eligible for a free upgrade. ($49.99, free update for version 11 licenses, 11.2 MB, release notes, 10.8.5+)
Read/post comments about BBEdit 11.0.1.
CrashPlan 3.6.4 — Code42 Software has released CrashPlan 3.6.4 with support for OS X 10.10 Yosemite, plus unspecified security updates. The Internet backup software now excludes Time Machine backup files from backups to the Code42 public cloud and from default file selection. The update also logs backups and restores that take place even when CrashPlan is paused and corrects a case sensitivity issue for systems formatted with the Mac OS Extended (Journaled, Case-Sensitive) file system. There’s no need to download CrashPlan 3.6.4 manually, as the app should upgrade itself automatically in the coming days if
it hasn’t already — the version number is displayed prominently in the app’s splash screen and Settings > Account screen. (Free with a 30-day trial of CrashPlan’s online backup service, 51.3 MB, release notes, 10.5+)
Read/post comments about CrashPlan 3.6.4.
Quicken 2015 for Mac 2.2 — Intuit has released version 2.2 of its Quicken 2015 for Mac financial software (recently reviewed by Glenn Fleishman; see “Quicken 2015: Close, But Not Yet Acceptable,” 2 October 2014) with a number of improvements and fixes. The update adds a new feature to aid in setting up automatic downloads for existing accounts from either Quicken Windows or Quicken for Mac 2007. It also improves the Download Matching feature for transactions both manually entered and downloaded from the same account, adds the capability to merge securities in the Security List,
adds support for importing multiple existing accounts from prior Quicken releases into a Quicken 2015 for Mac file, and adds a Control-O keyboard shortcut to open a register or report in a new window. The release also fixes multiple issues related to importing accounts from previous Quicken versions, squashes a bug in the Bill Reminder that produced an incorrect projected balance, and provides multiple fixes and improvements to mobile sync. Note that as of this writing, Quicken 2015 for Mac was still stuck at version 2.1.1 in the Mac App Store, but Intuit promises the latest release will be available soon. ($74.99 new, free update, release notes, 10.7+)
Read/post comments about Quicken 2015 for Mac 2.2.
Pixelmator 3.3 — The Pixelmator Team has released version 3.3 (nicknamed Limestone) of its eponymous image editing app with a redesigned interface that fits in nicely with OS X 10.10 Yosemite. Additionally, Pixelmator 3.3 brings support for such Yosemite features as iCloud Drive and Continuity, enabling you to use Handoff to switch between Pixelmator on your Mac and Pixelmator for iOS on your iPad. The update also provides a Repair Tool extension that enables you to use it to edit images in Apple Mail and TextEdit without having to open the
Pixelmator app. ($29.99 new from the Mac App Store, free update, 42.8 MB, release notes, 10.9.5+)
Read/post comments about Pixelmator 3.3.
ReadKit 2.4.2 — Webin has released ReadKit 2.4.1, which made improvements to compatibility with OS X 10.10 Yosemite as well as with sync performance and handling smart streams with Feed Wrangler. The RSS client and read-later app also added a badge preference to smart folders to display item count or unread items only; fixed several issues related to renaming the feed title in built-in RSS; added a delete confirmation to feeds, folders, and smart folders; squashed a bug affecting the unread badge on folders of read-later services; and fixed selection when navigating through articles. Shortly after releasing version 2.4.1,
Webin released ReadKit 2.4.2 to fix bugs associated with migration issues. ($9.99 new from the Mac App Store, free update, 4.1 MB)
Read/post comments about ReadKit 2.4.2.
ExtraBITS for 10 November 2014
In ExtraBITS this week, the EFF announces that Apple leads the pack in mainstream messaging security, a developer tells us what to expect out of Apple Watch apps, Apple quickly shuts down a strain of Chinese malware, Rob Griffiths bids adieu to Mac OS X Hints, and Microsoft Office and Dropbox will soon be fully integrated.
EFF: Apple Offers Best Mainstream Messaging Security — The Electronic Frontier Foundation has released a scorecard measuring the security of online messaging systems. “Apple’s iMessage and FaceTime products stood out as the best of the mass-market options, although neither currently provides complete protection against sophisticated, targeted forms of surveillance,” the EFF said in a press release. The two areas where iMessage and FaceTime lost points were in helping users verify contacts’ identities and making the code open to independent review.
What to Expect from Apps for the Apple Watch — Developer David Smith has studied Apple’s publicly available information about the Apple Watch to get an idea of what kind of apps we can expect. He realized that there will be a two-phase rollout of the WatchKit APIs developers need to write apps. The first phase will allow apps to create limited actionable notifications and Glances, which will function much like notifications and widgets in iOS 8. Developers will be able to start creating phase-one apps this year, whereas the second phase, which promises fully native apps, will begin sometime
later next year, likely at WWDC in June 2015.
Apple Shuts Down Chinese WireLurker Malware — Apple has quickly shut down the WireLurker malware, which was spreading to Chinese iOS devices via infected Macs (it requires a wired connection between the Mac and the iOS device). WireLurker, which was localized to China, was discovered by Palo Alto Networks. Apple quickly unsigned the code, preventing non-jailbroken iOS devices from being infected. However, researchers warn that the code could be modified for a future attack.
An Unofficial Goodbye to Mac OS X Hints — Although it’s not officially dead, founder Rob Griffiths is saying goodbye to Mac OS X Hints, which hasn’t been updated in over 45 days. He began the site over 14 years ago, then sold it to Macworld in 2006, where he stayed to maintain the site until 2010. Griffiths doesn’t blame mismanagement for the site’s decline, but instead chalks it up to the maturation of OS X.
Dropbox Is Coming to Office — If you use Microsoft Office, but have been frustrated by its lack of support for Dropbox, your frustration is almost at an end. Soon, you will be able to open Dropbox files from within Office and edit Office files in the Dropbox app. Dropbox also plans to integrate its Web site with Office Online next year.