TidBITS#1261/02-Mar-2015
The Apple Watch is due in April, but smartwatch market leader Pebble is racing to sell its new Pebble Time first; Adam Engst has the details, along with some reasons why it might be preferable to the Apple Watch. Speaking of which, could the amount of gold in the Apple Watch Edition shake up the world economy? Josh Centers runs some numbers that are either stunningly huge or that point out flaws in sales estimates reported by The Wall Street Journal. In other news, Apple has opened up iWork for iCloud to everyone, and Michael Cohen explains how it works for non-Apple users. The FCC last week passed controversial net neutrality rules that place broadband providers under Title II classification. Josh shares what details we know at the moment, and he also offers up a new edition of Keeping Up with the Snoops, with the latest in government surveillance revelations. Finally, we’re pleased to bring you Michael Cohen’s new “Take Control of PDFpen 7,” along with the latest chapticle of Joe Kissell’s “Take Control of Security for Mac Users,” in which he explains how to protect your network connection from eavesdropping. Notable software releases this week include Fetch 5.7.5, Downcast 1.1.7, BusyCal 2.6.5, Logic Pro X 10.1.1, and VLC Media Player 2.2.0.
Apple Opens iWork Web-only Access to All
Apple has opened up its iCloud Web site to anyone who signs up for a free Apple ID, providing access to Apple’s iWork Web apps — Pages, Numbers, and Keynote — plus 1 GB of iCloud storage. The iWork Web apps, which remain labeled as “beta” since their debut in October 2013, are less fully featured than their sibling apps on iOS and OS X. Nonetheless, the Web apps produce documents that are completely compatible with the Mac and iOS apps — and vice-versa.
Anyone who wishes to use the iWork Web apps can sign up for a free account by browsing to icloud.com and clicking Create Apple ID. The signup process requires you to supply an email address, a strong password, and the answers to a set of security questions. Apple then sends a six-digit code to the email address you supplied; you enter that code on the iCloud site to complete the signup process.
After that, you can log in to iCloud on any supported browser — the iCloud site and its Web apps require a recent version of Safari, Google Chrome, Firefox, or Internet Explorer — and use the Web versions of Pages, Numbers, and Keynote.
Web-only users cannot upgrade their iCloud accounts to get more than 1 GB of iCloud storage or access any other iCloud features; owning a Mac or iOS device is required to do that (Mac and iOS device owners get 5 GB of storage for free automatically). An Apple support document provides more information about Web-only iCloud Access.
“Take Control of PDFpen 7” Documents PDFpen for Mac and iOS
If you’re wrangling PDFs using Smile’s PDFpen 7 or PDFpenPro 7 on the Mac, perhaps along with PDFpen for iPad & iPhone, check out Michael Cohen’s new 171-page “Take Control of PDFpen 7.” It provides updated documentation of the Mac versions and an explanation of the touch-based interface of the iOS version, plus help on moving documents between them using iCloud, Dropbox, iOS’s Open In controls, and even iTunes.
As massively useful as PDFpen is, working with PDFs — regardless of the app — can be complex, and Michael clarifies and demystifies the confusing bits. After a quick overview of the PDF format to set the stage, Michael walks you through PDFpen’s tools and navigation, along with the many ways you can create a PDF from within the program. You’ll learn how to take notes on a PDF, copyedit and comment on a PDF, fill out PDF forms (complete with your signature!), add and remove pages, and edit text and graphics in a PDF. You’ll even find out how to export a PDF to a formatted Microsoft Word document.
For PDFpenPro users, Michael explains how to create an interactive PDF form and get user-submitted data back via email or the Web, plus how to control whether a PDF can be printed, modified, and annotated. PDFpenPro users will also learn how to export to Excel and PowerPoint formats, and how to edit the OCR layer in scanned documents. Finally, an appendix describes the many useful AppleScripts that ship with PDFpen.
So if you’re looking for help with PDFpen’s many features, check out the $15 “Take Control of PDFpen 7,” available now in DRM-free PDF (natch), EPUB, and Mobipocket (Kindle) formats. And if you don’t yet own PDFpen and want to go beyond the limited features for working with PDFs in Preview, remember that TidBITS members save 20 percent on PDFpen when bought from Smile’s site, not to mention saving 30 percent on all Take Control orders (for both discounts, click through from your Member Benefits page).
Chapter 6 of “Take Control of Security for Mac Users” Available
Many people dismiss network eavesdropping as a security risk under the assumption that their network traffic isn’t sufficiently interesting, and besides, who would sit around in a coffee shop just to sniff random Wi-Fi packets? Alas, the reality is that most such monitoring is done by software robots — possibly even in the form of malware running in the background of hijacked PCs — slurping up everything and winnowing out the interesting bits, which could include email addresses to spam, passwords to use for identity theft, and credit card numbers to resell.
That’s where Joe Kissell focuses in this week’s installment from “Take Control of Security for Mac Users.” In Chapter 6, “Improve Your Network Security,” he identifies the primary avenues of attack, recommends WPA encryption for Wi-Fi networks you control, and encourages the use of a virtual private network (VPN) for use on public Wi-Fi networks or in any situation where it’s essential that your network traffic remain private.
If you’re just getting started with “Take Control of Security for Mac Users,” the first two chapticles are available to everyone, but subsequent ones are limited to TidBITS members. Those who join the TidBITS membership program receive other benefits too, but what’s most important is that TidBITS members have kept TidBITS afloat the last few years — your support truly is necessary. If you’re already a TidBITS member, log in to the TidBITS site using the email address from which you joined to read and comment on these chapters.
- Chapter 1: “Introducing Mac Security”
- Chapter 2: “Learn Security Basics”
-
Chapter 3: “Perform Quick Security Fixes”
-
Chapter 4: “Beef Up Your Security Settings”
-
Chapter 5: “Improve Your Passwords”
-
Chapter 6: “Improve Your Network Security”
The full ebook of “Take Control of Security for Mac Users” will be available for purchase by everyone in PDF, EPUB, and Mobipocket (Kindle) formats once it’s complete.
Pebble Time Announced Before Apple Watch
Much has been said about how the forthcoming (in April 2015) Apple Watch will dominate the smartwatch market. But market leader Pebble Technology, which got its start on Kickstarter in 2013, isn’t giving up. Instead, the company, which has sold over 1 million smartwatches, is launching Pebble Time, a new smartwatch with a color e-paper screen, 7 days of battery life, a new timeline interface, and a microphone, all wound up in black, white, and red colors.
Although the company says that Pebble Time is nearly done, it’s still “launching” via Kickstarter, where the campaign’s $500,000 goal was met in 18 minutes by 2,850 backers. In essence, the Kickstarter campaign is largely a way to pre-sell the Pebble Time at a discount before the Apple Watch ships — 10,000 people will get the Pebble Time for $159 instead of the $199 retail price, and tens of thousands more can get it for $179. Pebble promises the Pebble Time will ship in May 2015 to the first 50,000 backers; subsequent backers are
being promised June 2015.
It’s interesting to see where Pebble is focusing its efforts, since the company is clearly trying hard both to compete with the Apple Watch and to put the Pebble Time on a different path. Notably:
- The color e-paper display will be easier to read than the Pebble’s current grayscale display, and while it won’t compare to the Apple Watch’s Retina display and touch screen (the Pebble Time relies on side-mounted buttons), it will be cheaper and less power hungry.
- Expect to see Pebble crowing about the Pebble Time’s 7-day battery life, which is what I see with the current Pebble as well. From all reports, the Apple Watch will need to be charged every night, and for some, that will be a problem.
-
Pebble’s microphone provides the capability to record short voice notes and send voice replies to notifications, but it doesn’t offer any of the other Siri-like features that the Apple Watch will have. That would require bi-directional communication with a smartphone, and while that’s at least possible on Android, it’s not on the iPhone.
-
A new timeline interface displays notifications, news, reminders, and events gathered from various different apps. What’s new is that they’re arranged chronologically, starting in the past with previous notifications, coming to the present, and moving to the future with upcoming calendar events. This is the major departure from where Apple is going with the Apple Watch — Pebble found that apps quickly became hard to find in the previous interface. It remains to be seen how fluidly users will be able to navigate within and between Apple Watch apps. Timeline will be available to users of the existing Pebble and Pebble Steel watches sometime in the future.
-
The Pebble Time is thinner than the previous Pebble models at 9.5mm and features a curved design. The Apple Watch is estimated to be 12.6mm thick. The Pebble Time uses a standard 22mm watch band and a quick-release pin to make swapping bands easy.
-
With a retail price of $199, Pebble is staying well under the Apple Watch’s entry level price of $349. That’s key — there’s plenty of room for less expensive smartwatches in the market.
In the 45 minutes it took me to write this article, the Pebble Time Kickstarter campaign exceeded $1.6 million and was over 9,000 backers. After only 5 days, Pebble has raised $11.9 million from over 54,000 people. Those numbers may be chicken feed to Apple, but for a small company like Pebble, that’s confirmation that they’re still producing a smartwatch people want, even when faced with the near-term release of the Apple Watch.
Net Neutrality Passes, Eliminating Broadband Restrictions
The FCC has voted, 3 to 2, in favor of adopting the Open Internet Order, which reclassifies broadband Internet service as a “telecommunications service” under Title II of the Communications Act (for background, see “FCC Goes All-In on Net Neutrality,” 7 February 2015). The FCC also voted to overturn certain state restrictions on municipal broadband networks.
The actual rules have not yet been released publicly, and it could be several days before we know the details. For now, all we have to go by is the FCC’s press release, which summarizes the new rules.
The main provisions are the so-called “Bright Line Rules,” which ban three practices that the FCC said harm the open Internet. To quote:
- No Blocking: broadband providers may not block access to legal content, applications, services, or non-harmful devices.
- No Throttling: broadband providers may not impair or degrade lawful Internet traffic on the basis of content, applications, services, or non-harmful devices.
-
No Paid Prioritization: broadband providers may not favor some lawful Internet traffic over other lawful traffic in exchange for consideration of any kind — in other words, no “fast lanes.” This rule also bans ISPs from prioritizing content and services of their affiliates.
In addition, the rules give the FCC the power to act as a referee between broadband providers and customers, and require broadband providers to disclose promotional rates, fees, surcharges, and data caps in a consistent format. Additionally, the FCC will also act as a referee for interconnection disputes between broadband providers and content providers.
While broadband providers are now technically subject to Title II regulations, there are a few that will not apply, such as rate regulation and Universal Service Fund contributions. Also, broadband service will remain exempt from state and local taxation.
One interesting thing I noticed about the wording of the press release is that the FCC prefers the term “broadband providers” over “Internet service providers.” Given that the FCC recently redefined broadband as transfer speeds of 25 Mbps down and 3 Mbps up, could that mean that slower Internet connections are not covered?
One thing is for sure: the telecommunication companies are hopping mad. Verizon released an angry press release condemning the vote in Morse code, with a translated version appearing to be drafted with a typewriter. The press release, mockingly dated 26 February 1934, claims that the Internet now falls under rules from the 1930s.
There is little doubt that major telecom firms will sue. The Republican Congress isn’t pleased either, but for the most part, it has conceded to the Obama administration. However, some Republicans are still looking to push forward with a bill that would bring some new broadband regulations, but would also defang the FCC on Internet matters.
The FCC also voted to preempt laws in Tennessee and North Carolina that prevented municipalities from expanding their broadband networks (I discussed these in “Net Neutrality Controversy Overshadows U.S. Broadband Woes,” 19 February 2015). However, this move does not affect the 18 remaining states with similar laws.
How Much Gold Will the Apple Watch Edition Consume?
The Apple Watch Edition might be Apple’s most unusual product in years. Questions abound about the 18-karat gold smartwatch. How much will it cost? Will Apple offer an upgrade path for it?
But I have a broader question: how will it affect the world’s gold supply?
The Wall Street Journal has reported that Apple plans to ramp up production of the Apple Watch Edition to over 1 million units per month in its second quarter of production. That’s an unbelievable number of gold watches, especially considering that they could cost as much as $10,000 each. Could this number be realistic?
For the sake of argument, let’s assume that each Apple Watch Edition contains 2 troy ounces of gold (Apple Spotlight estimates 50–75 grams in the Apple Watch Edition; 2 troy ounces equals 62.2 grams). Now, 18-karat gold is only 75 percent pure, because pure gold is too soft for everyday use, but for easier math, let’s also assume that 75 percent still uses 2 troy ounces of gold. (Even if Apple uses only 1 troy ounce, halving all the numbers below, they’re still huge.)
If Apple makes 1 million Apple Watch Edition units every month, that equals 24 million troy ounces of gold used per year, or roughly 746 metric tons.
That’s enough gold to make even a Bond villain blush, but just how much is it? About 2,500 metric tons of gold are mined per year. If Apple uses 746 metric tons every year, we’re talking about 30 percent of the world’s annual gold production.
That’s a sobering thought, but it’s not entirely unbelievable: Apple has a tendency to buy up so many resources that competitors can’t keep up, and it certainly has the cash to do so. But gold is different from aluminum, say, in that it’s a precious metal. Although currencies are no longer backed by gold, governments still hoard it as a “store of value” and as part of the guarantee of a financial system. The Federal Reserve Bank of New York stores about 7,000 metric tons of gold in its Manhattan vault, all owned by governments, banks, and international organizations. It would take Apple less
than a decade to turn all of that gold into watches.
Speaking of vaults, where exactly would Apple store all of this gold? (Besides in a Scrooge McDuck-esque money pit at the very center of the new circular Apple campus.) At today’s price of $1,200 per ounce, Apple’s annual gold needs would be worth $28.8 billion dollars. Granted, it may not hold all of that on hand at any one time, but talk about a supply chain nightmare. Moving that much gold means a high risk of shrink, an industry term for vanishing product. Not to mention the risk of attacks by dragons and SPECTRE.
Meanwhile, while Apple’s annual gold supply alone would be worth $28.8 billion, luxury watchmaker Rolex sells “only” $4.7 billion of product every year, from an estimated 600,000 watches.
There are two conclusions we can draw from this smattering of data. The first is that Apple is about to take over the world. Not only will it be the most valuable company on the planet, but it will also be bidding for a third of the world’s annual gold supply, wreaking havoc on gold prices and doing who knows what to the global economy.
The alternative is that the esteemed Wall Street Journal is off on its Apple Watch Edition sales by an order of magnitude (or more). That would put the number at 100,000 per month, which seems more plausible.
Don’t get me wrong, it’s never safe to underestimate Apple. If anyone can sell 12 million $10,000 quasi-disposable smartwatches a year, it’s Apple. But once you run the numbers, it sounds nuts. Estimates from Watch-Insider.com put the annual unit sales of high-end watches made in Switzerland and Germany at about 27 million in 2013, and another industry site, W The Journal, reported that all of Switzerland exported about 29 million watches in 2012. Could Apple push up against 45 percent of the entire
current luxury watch industry?
Even at 100,000 per month, or 1.2 million units of the Apple Watch Edition sold annually, that’s still a lot of gold — 2.4 million troy ounces or about 75 metric tons. That won’t throw such a big wrench in the global gold market, but it will still have an impact.
I may buy a gold coin or two, just in case.
Keeping Up with the Snoops 8: Snoop Harder
To be honest, I thought “Keeping Up with the Snoops 7: Too Many Snoops” (21 November 2014), might have been the last in this series. The release of Snowden’s documents seemed to be finished, the USA Freedom Act has been defeated, and the battle between the CIA and Senate over hacking has been quietly swept aside.
But as we approach the two-year anniversary of the first Snowden revelations of government mass surveillance, it turns out that the topic still has legs. Here’s the latest in the saga.
Iron Patriot Act — Like many “temporary” measures, the USA PATRIOT Act, signed into law quickly after the 11 September 2001 attacks, isn’t going away anytime soon.
On 25 February 2015, the Patriot Act was extended for yet another year, with all attempts at adding civil liberty protections defeated.
The Patriot Act has often been used to enable or justify NSA mass surveillance. However, its author, Representative Jim Sensenbrenner, has accused the NSA of abusing the law by attempting to collect records of all phone calls in the United States.
Have You Been Spied On? — Since I began this series, I’ve heard a common complaint from critics: “No one is spying on YOU,” a statement that no one could prove or disprove with certainty.
Now, thanks to a UK court ruling, we may be able to find out. The Investigatory Powers Tribunal (IPT) found that secret intelligence sharing between America’s National Security Agency (NSA) and Britain’s Government Communications Headquarters (GCHQ) violated human rights laws. The ruling was especially interesting, given that in its 15-year history, the IPT has never before ruled against intelligence agencies.
So how does this ruling affect you if you live in the United States? Anyone whose data was shared illegally with or by the GCHQ can ask if his or her communications were included. While the IPT will not divulge details, it will give a simple “yes” or “no” determination (which is more like a maybe than a plain “no”).
To make this process easy, Privacy International, one of the plaintiffs in the suit, has set up a Web page where it’s collecting data to make the appropriate requests to the IPT, and also to request that the GCHQ destroy its illegally collected data.
Be aware that it could be a long time before action is taken. Privacy International says that nothing like this has ever happened before, especially not at this scale. It could take years before things are sorted out.
What’s Hiding in Your Hard Drive? — According to a report from Kaspersky Lab, your hard drive might have malware hiding in its firmware.
The work of the so-called Equation Group of malware authors has been traced all the way back to 2001. One piece of the Equation Group’s malware is able to hijack the hard drive itself, preventing users from deleting data, or even enabling attackers to create hidden partitions that can be used to bypass encryption or collect data.
Some malware from the Equation Group bears several similarities to the Stuxnet worm that destroyed many of Iran’s nuclear centrifuges between 2009 and 2010. Stuxnet is largely attributed to a collaboration between the United States and Israel.
Indeed, malware linked to the Equation Group is prolific and highly sophisticated, leading many to believe that the Equation Group is linked to, or even part of, the NSA.
Should you worry about your hard drive being hijacked by government snoops? Probably not. Despite the furor this story has sparked, the victims that Kaspersky has discovered so far have been highly targeted, either individually or through Web sites linked to religious radicals.
Still, the work of the Equation Group goes to show just how inherently insecure computers can be — even down to the bare metal.
Mr. Obama Goes to Silicon Valley — In a time of rising tensions between Silicon Valley and the U.S. federal government, President Obama held a White House Summit on Cybersecurity and Consumer Protection at Stanford University on 12 February 2015.
The president attempted to make peace with the tech community by inviting top CEOs to the summit. However, Facebook’s Mark Zuckerberg, Google’s Larry Page and Eric Schmidt, and Yahoo’s Marissa Mayer all declined.
Apple’s Tim Cook was in attendance, and he gave a speech reiterating Apple’s commitment to privacy. He also touted Apple Pay, announcing that Apple Pay will soon be available for federal government transactions. You can watch the full speech here.
The focus of the summit was an executive order, signed by President Obama at the event, that encourages greater sharing of security information between tech companies and the federal government. The order, which is advisory and not prescriptive, calls for central clearinghouses for information between the government and private enterprise.
The president also agreed to a few interviews, mostly notably with Re/code’s Kara Swisher. You can watch the entire interview here.
In the interview, Obama admitted to a strained relationship with Silicon Valley, mostly pinning the blame on Edward Snowden’s revelations of NSA spying. Indeed, revelations about mass surveillance have caused the Chinese government to drop many American technology brands, including Apple. However, the president did acknowledge that the NSA had gone too far in its intelligence gathering efforts. “There have been abuses on U.S. soil,” the president said.
One of the main tussles between the government and the tech sector has been over encryption. The NSA has been caught weakening encryption standards (see “The NSA’s Campaign to Undermine Internet Security,” 5 September 2013), and law enforcement has complained about stronger encryption measures in consumer products (see “Apple and Google Spark Civil Rights Debate,” 10 October 2014). Swisher asked the president about this, but his response was something of a waffle.
But the intelligence agencies’ biggest win over encryption had yet to be revealed…
The Great SIM Heist — Just when the Snowden revelations seemed to be fading away, The Intercept dropped another bombshell.
Britain’s GCHQ, with help from the NSA, infiltrated Gemalto, the world’s leading producer of SIM cards. Gemalto produces 2 billion SIM cards a year for AT&T, Sprint, T-Mobile, Verizon, and others. Intelligence operatives mined the private communications of engineers to steal SIM encryption keys.
In effect, the NSA and GCHQ may have the capability to decrypt voice and data from almost any cell phone in the world. “Once you have the keys, decrypting traffic is trivial,” Christopher Soghoian of the American Civil Liberties Union told The Intercept. “The news of this key theft will send a shockwave through the security community,” he said.
In fact, the ramifications for cellular security could be significant. Matthew Green, a cryptographer at Johns Hopkins University, called it, “bad news for phone security. Really bad news.” He continued, “Gaining access to a database of keys is pretty much game over for cellular encryption.”
Gemalto has admitted that it was hacked, but has downplayed the severity of the intrusion. The company said that the infiltrators gained few, if any, SIM card keys, and that the ones that might have been stolen were outdated anyway. However, many are skeptical that Gemalto could have performed a thorough security audit in such a short amount of time.
The Gemalto story has caused even more tension between the federal government and security experts. At a New America Foundation conference on cybersecurity on 23 February 2015, things got heated when NSA Director Mike Rogers was grilled by Yahoo’s chief information security officer, Alex Stamos, about the NSA’s desire for encryption backdoors (a term Rogers rejected). Rogers dismissed concerns that foreign nations could also demand their own encryption backdoors with, “I think we can work our way through
this.” (As an aside, this picture of Admiral Rogers does not inspire confidence.)
The silver lining in this cloud is that this may have finally alerted technology companies to the stark reality that many of the technologies we rely on every day are inherently insecure. Let’s hope it causes the tech world to focus more on fundamental security practices.
TidBITS Watchlist: Notable Software Updates for 2 March 2015
Fetch 5.7.5 — Fetch Softworks has released Fetch 5.7.5 with improved support for Retina displays. The venerable file transfer client also resolves a problem downloading iBooks Author documents, fixes an issue with TLS/SSL connections on systems running Mac OS X 10.7 Lion and earlier, avoids slowdowns in multi-file downloads on high-speed networks, and fixes problems with code signing for the Mac App Store. ($29 new from Fetch Softworks or the Mac App Store with a 20 percent discount for TidBITS members and
free for educational users, 11.9 MB, release notes, 10.5+)
Read/post comments about Fetch 5.7.5.
Downcast 1.1.7 — Jamawkinaw Enterprises has released Downcast 1.1.7 with a fix for an issue in OS X 10.8 Mountain Lion that caused the media library location to change. (For a full review, see “Downcast Comes to Mac, but Lacks Instacast’s Polish,” 3 August 2013.) The updated podcatcher app also fixes issues with the context menu and shortcuts when using the available episodes list, fixes a problem that prevented application of incoming iCloud changes, and resolves several instances of crashes. ($9.99 new from the Mac App Store, free update, 20.6 MB, release notes, 10.8+)
Read/post comments about Downcast 1.1.7.
BusyCal 2.6.5 — BusyMac has released BusyCal 2.6.5 with improved handling of Exchange cookies in order to avoid repeated login dialogs. The calendar app also improves Quick Entry parsing of 24-hour times, re-syncs alarm snoozes that conflict with an acknowledgement, displays change notifications for WebDAV feeds, fixes an issue with dragging events to the sidebar in Week View, improves handling of Exchange Push subscriptions, and fixes the Time Zone menu. As of this writing, BusyCal remains stuck at version 2.6.4 in the Mac App Store.
($49.99 new from BusyMac or the Mac App Store, free update, 10.3 MB, release notes, 10.9+)
Read/post comments about BusyCal 2.6.5.
Logic Pro X 10.1.1 — Apple has released Logic Pro X 10.1.1 with a large number of documented changes (a rarity for Apple software updates) for the professional audio app. The release ensures the app remains responsive when it’s opened with Euphonix control surfaces installed, fixes an issue where the Brush Tool could get stuck in fixed pitch mode when selected after using the Pencil Tool, makes sure that pre-fader sends are no longer affected by VCA faders, resolves a problem that could cause the Download Manager to appear empty, ensures that VoiceOver can access audio channels as well as track header volume and pan
controls, and restores undo reliability after moving events in the Piano Roll. ($199.99 new in the Mac App Store, free update, 1.05 GB, release notes, 10.9+)
Read/post comments about Logic Pro X 10.1.1.
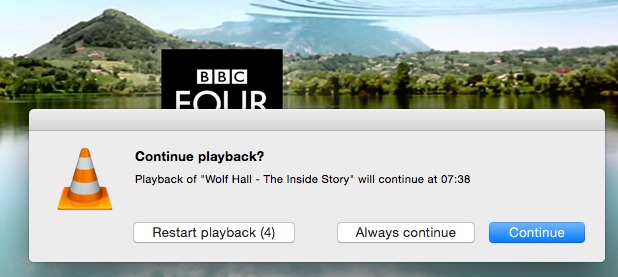
VLC Media Player 2.2.0 — VideoLAN has released VLC 2.2.0 (nicknamed WeatherWax after the Granny Weatherwax character from Terry Pratchett’s “Discworld” novels) with automatic rotation of vertically oriented videos captured by mobile devices (supported for MP4/MOV, MKV, and raw H.264 formats) and the addition of a playback resumption feature that returns you to the point last played when the file was closed (a feature that has been available in all mobile editions of VLC for some time). When you open a previously played video, you can restart from the beginning,
continue from the left-off point, or choose to always continue playback (these options can be adjusted in Preferences > Interface).
The open-source media player also improves support for UltraHD video codecs like VP9 and H.265, adds a subtitle downloading extension (using OpenSubtitles), and updates the user interface to be more in line with OS X 10.10 Yosemite. (Free, 33.5 MB, release notes)
Read/post comments about VLC Media Player 2.2.0.
ExtraBITS for 2 March 2015
In this week’s collection of ExtraBITS, Managing Editor Josh Centers made a couple of podcast appearances and Google teamed up with carriers for mobile payments.
Josh Centers Talks Patents, Apple Watch on The Mac Show — Managing Editor Josh Centers joined The Mac Show panel to discuss patent reform, the Apple Watch, the possibility of a new Apple TV, how much gold Apple is using for the Apple Watch Edition, public iOS betas, what’s coming in iOS 9, and the viability of Final Cut Pro X.
Josh Centers Goes Gold on The Dan Benjamin Hour — Managing Editor Josh Centers joined host Dan Benjamin on The Dan Benjamin Hour to discuss how much gold Apple may be using to produce Apple Watch Edition units.
Google Teaming Up with Carriers on Payments — Google has agreed to a deal with AT&T, T-Mobile, and Verizon that will make Google Wallet more competitive with Apple Pay. All three carriers will pre-install the Google Wallet app on Android phones, and Google will gain intellectual property from the carrier-owned payment service Softcard. Google beat Apple to mobile payments by several years, but in many cases, the carriers prevented Google Wallet from accessing the necessary NFC chip in Android phones.