TidBITS#1308/15-Feb-2016
Many Apple professionals depend on the Microsoft Office for Mac and iOS Accredited Support Professional program, but it appears to be in limbo, without any scheduled events and no word from Microsoft as to its future. Apple users have lately been plagued by a pair of problems: a security vulnerability associated with the popular Sparkle update framework in OS X and the mysterious Error 53 that has locked out iPhone users. Josh Centers and Adam Engst explain what to do about both, before turning their attention to another OS X hidden treasure: Quick Look, which turns out to be far deeper than even they had imagined. Notable software releases this week include PopChar X 7.4, Piezo 1.5, Hazel 3.3.7, and 1Password 6.0.2.
Microsoft Mum on Office Accreditation Program Future
Here’s one for those of you who are Apple consultants or IT professionals. For the past few years, Microsoft has offered the Microsoft Office for Mac and iOS Accredited Support Professional program, consisting of a half day of training and evaluation, and culminating in an accreditation for those who passed the exam.
The program was popular with technical folks who found it useful for reviewing Office features and capabilities, learning key troubleshooting tactics, and getting a chance to talk directly with Microsoft reps. The accreditation is well-regarded as a tool for self-promotion too, since it has helped consultants demonstrate Office expertise to clients, and gave enterprise IT support engineers a leg up when applying for a raise or promotion.
Historically, the program has been offered in advance of the MacTech events that take place around the country, but when the schedule for the MacTech Pro 2016 series was announced (see “MacTech Pro 2016 Dates and Locations Announced,” 29 January 2016), Microsoft made no mention of the accreditation program.
I reached out to Microsoft and was given this statement a week later:
Microsoft remains committed to IT Pros on the Mac platform and we recognize that the Accreditation Program has historically proved an important venue. We’re in the process of evaluating options for 2016, but don’t have anything to share at this time. We will keep you posted as we learn more.
Simultaneous with my January 29th article about MacTech Pro, concerned users started a thread on Microsoft’s community forums to praise the program and ask what was happening with it in the future. As with Apple’s community forums, there’s no way to know if anyone from Microsoft actually reads them, and no Microsoft representative has weighed in there.
When I pressed Microsoft’s PR reps for a timeline on when more details might be forthcoming, I was told simply that there was nothing additional to share and that I would be notified if there were. Frankly, it sounds like Microsoft is suffering from some internal confusion about what’s going on.
It would make no sense for Microsoft to choose this year to pull back on this program, given that we’ve now seen releases of Office for the iPad (“Office for iPad: A Deep Look,” 3 April 2014), iPhone (“Microsoft Office Comes to the iPhone, and It’s Free,” 7 November 2014), and Mac (“Microsoft Releases Public Preview of Office 2016 for Mac,” 6 March 2015). Dropping the program would send the message that Microsoft may make Mac and iOS software, but it’s not committed to the larger Apple community.
Should anything change, we’ll be sure to let you know.
Sparkle Vulnerability Real, but Exploits Highly Unlikely
While numerous readers love our regular TidBITS Watchlist feature, in which we track notable updates for key Mac software, many apps no longer require you to go hunting for the latest versions as they’re released. Instead, these apps use an open source framework called Sparkle to check for, download, and install updates automatically.
Unfortunately, some developers haven’t been careful enough with their implementations of Sparkle, and that could put your Mac at risk of attack. Researcher Radosław Karpowicz found that many developers use unencrypted HTTP connections to their servers, which makes man-in-the-middle attacks possible. So, a bad guy could sniff out your network connection, insert malicious code, and hijack your Mac via the compromised app without triggering Apple’s Gatekeeper security feature.
Sparkle itself isn’t really doing much wrong, since using unencrypted HTTP connections violates this recommendation in its documentation: “We strongly encourage you to use HTTPS URLs for the AppCast.” Regardless, the Sparkle team has already updated Sparkle to address the vulnerability. The only problem is that getting an updated app with the new Sparkle code requires, well, getting an update, which could expose you to the vulnerability.
But don’t panic! To exploit this vulnerability, an attacker would need to be on the same network as your Mac. So if you’re safely in the confines of your home or office with an Ethernet or secure Wi-Fi connection, you have nothing to fear. Just keep letting your apps update when they want, and as long as you’re on a private network, you’ll be fine.
However, if you often use public Wi-Fi networks without also employing a VPN to secure all your network traffic, you could be at risk if there was a sufficiently capable hacker at the next table. That risk would apply for any affected app that has automatic update checking enabled and is running. However, using a VPN will keep you safe and should be standard operating procedure when using networks outside your home or office. If a VPN isn’t an option, you can also disable automatic update checking in any apps that use Sparkle, and when an update arrives, download and install it manually. Since taking advantage of this vulnerability would require a targeted attack, it’s highly unlikely that it would be used indiscriminately against
people who aren’t high-profile government or corporate officials.
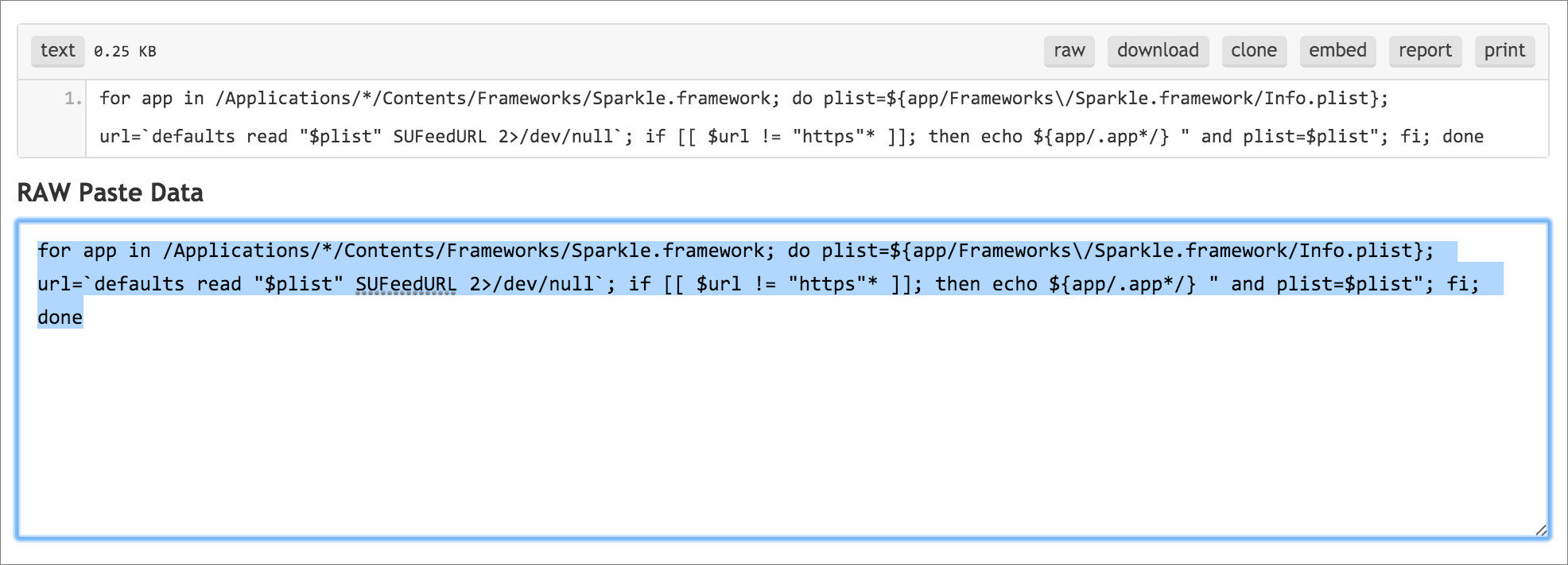
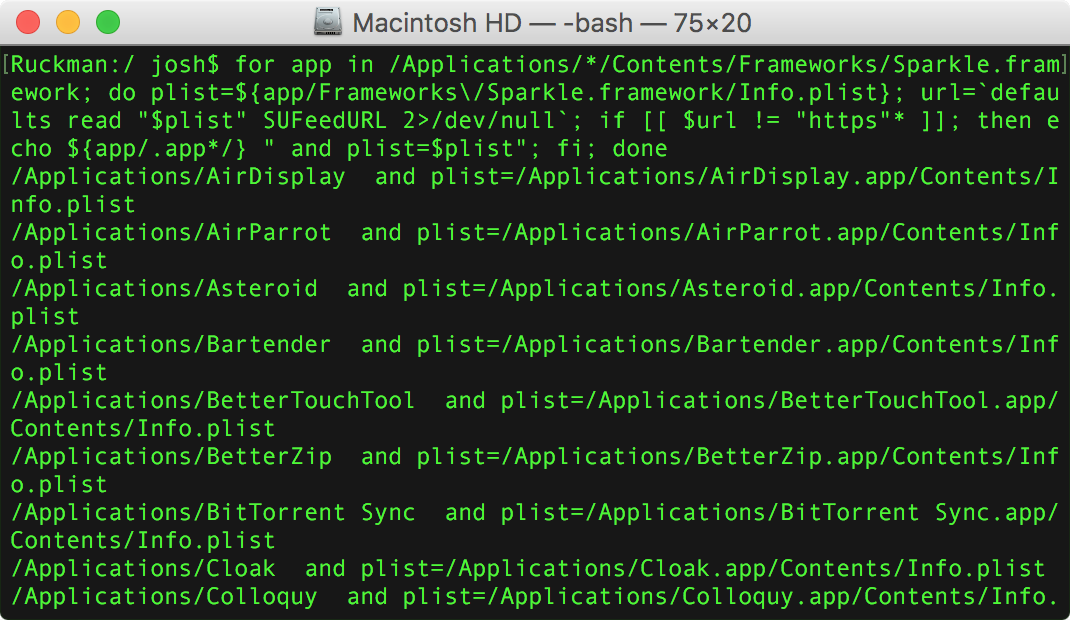
If you are still worried, how do you figure out which apps are vulnerable? People have offered all sorts of Terminal commands to suss out vulnerable apps, but the best one I’ve found comes from RussW, a commenter on Mac Kung Fu. His solution checks to see if the app uses both Sparkle and an insecure HTTP connection, and then it prints out a list of those apps in a fairly readable format.
Unfortunately, there are smart quotes in RussW’s text that partially break the command (thanks to reader Joe for pointing that out), so I’ve created a Pastebin link with the properly formatted command. Follow that link, copy the command under RAW Paste Data, paste the command in the Terminal window, and press Return. Terminal will list the vulnerable apps in your Applications folder.
The list may be long, but those who use public Wi-Fi networks can use it to figure out for which apps automatic updates should be disabled until a new version is available. At that point, either update manually or re-enable automatic updating only when on a
trusted network. Again, this is necessary only if you’re paranoid or are concerned about using untrusted networks. And as Security Editor Rich Mogull likes to remind us, if you’re in China or are being pursued by the NSA, your data is probably already compromised.
What “Error 53” Means for the Future of Apple Repairs
In “Error 53 Will Kill Your iPhone and No One Knows Why,” (23 April 2015), I reported on the mysterious Error 53, which makes iPhones unusable, with no explanation from Apple. The good news is the community has now pinpointed the cause of Error 53, and it’s easy to avoid. The bad news is that the explanation makes the future of repairing your own Apple devices or using less expensive independent repair services even more dim.
The cause of Error 53 is a failure within the Touch ID sensor in the Home button of new iPhones. When you restore or update to iOS 9, it verifies that the Touch ID sensor is properly paired with the processor’s secure enclave. If iOS detects that the pairing has failed, which it might even if only the screen was replaced, Touch ID is disabled to protect the security of Apple Pay, and additional security checks display Error 53 and prevent further access.
Pairing the Touch ID hardware with the secure enclave is a clever security measure that ensures no one can access your fingerprint data or Apple Pay details by messing with Touch ID. The problem is that if an unauthorized repair center replaces your iPhone’s Home button, or even an associated part such as the screen, updating or restoring iOS 9 at some later date will render the iPhone useless. If you run into this situation, Apple says to “contact Apple Support about pricing information for out-of-warranty repairs.”
As Daring Fireball’s John Gruber pointed out, Apple could have handled Error 53 better. Instead of bricking the iPhone, iOS 9 should just disable Touch ID and Apple Pay, and explain to the user why it did so. In short, there’s no reason to throw the baby out with the bathwater.
We reached out to an Apple Authorized Service Provider who is familiar with the matter. While he confirmed that Apple’s requirement is a security feature, he also sees it as Apple pushing several agendas: selling AppleCare+, pushing customers into buying new phones after AppleCare+ expires, shutting out non-authorized repairers and suppliers, and shutting out fake devices built from knock-off parts. It turns out that all iPhone screen repairs have to go back to Apple for screen replacements; Apple has a machine that restores the pairing between the Touch ID sensor and the secure enclave.
We also spoke with a technician at a local independent repair shop, who was outraged that Apple was doing this to customers, particularly without warning. He said that his shop is now telling customers that they can either take iPhones that require this sort of repair to Apple or avoid updating to a new version of iOS 9. The tech was in fact performing just such a repair during the conversation, and the waiting customer said that he wouldn’t have updated the iPhone anyway, so that limitation didn’t bother him.
Apple’s handling of the situation has prompted the Seattle law firm PVCA to file a class action suit against Apple; if you’ve experienced Error 53, consider getting in touch with them.
The Bigger Repair Picture — Apple’s discouragement of tinkerers is nothing new. The original Macs were notoriously hard to work on, requiring a long Torx screwdriver to open, and after Steve Jobs returned to Apple in 1997, the company’s hardware became ever more difficult for outsiders to service.
A key example is Apple’s choice to switch from standard #00 Phillips screws to proprietary pentalobe screws during the iPhone 4’s lifecycle. In fact, if you brought an iPhone 4 with Phillips screws to an Apple Store for repairs, Apple would replace them with pentalobe screws.
The funky screws didn’t dissuade most DIYers, and it wasn’t hard to replace the battery in the iPhone 4, but Apple continued down the path of making future iPhones even harder to repair, as Adam Engst and I documented in “Replace a Dying iPhone 5 Battery” (5 March 2014) and “How to Replace a Cracked iPhone 5c Screen with Screasy” (24 July 2015).
Because of these difficulties, our advice since the release of the iPhone 5 has been to leave repairs to the professionals, even if you think you know what you’re doing. Unfortunately, even when going directly to Apple for repairs, things don’t always go smoothly, as I detailed in “Replace a Dying iPhone 5 Battery: Take Two” (28 August 2014). A couple of weeks after having my iPhone 5 battery replaced by Apple, the rear camera stopped working — I suspect due to a bad connection. Thankfully, it was time to upgrade anyway, so I never bothered trying to fix it.
So what’s the takeaway? Sadly, it seems that the era of repairing your own Apple devices continues to wane; if you can repair an Apple device yourself, it’s likely either because it’s an older model or a design accident. And as Apple struggles to maintain its revenue growth in the face of slowing sales, the company will try to extract money wherever it can, with repairs and service plans as another means to that goal (ask any auto dealer).
Here’s our advice for your future iPhone repair needs:
- Whenever possible, have your Apple products serviced at an Apple Store or an Apple Authorized Service Provider.
- If you’re at all hard on devices, and particularly for portable devices, think about buying AppleCare coverage to extend your warranty.
-
Consider the iPhone Upgrade Program (see “Comparing U.S. iPhone Plan Costs in a Contract-Free World,” 11 September 2015) for your next iPhone purchase, as it includes AppleCare+ and it lets you replace your iPhone every year.
-
If a non-authorized repair is unavoidable or vastly less expensive, be sure to keep your original parts in case there’s a problem. Historically, Apple won’t even talk to you if you have third-party parts installed in your iPhone. And if you do need an independent repair that might cause Error 53, well, avoid updating to iOS 9 or a newer version of iOS 9. Small bug fixes and security risks are better than a dead iPhone.
However, it’s not all bad news. In order to deal with unauthorized repairs, Apple has drastically reduced the price for out-of-warranty screen repairs. Without AppleCare+, the company now charges between $109 to $149 for a screen replacement, which isn’t much more than what you’d pay with AppleCare+. However, if you have AppleCare+, Apple will give you a loaner phone and likely move your repair up in its priority list.
OS X Hidden Treasures: Quick Look
OS X is full of useful little features that are easy to miss or forget about, such as services, which we covered in “OS X Hidden Treasures: Services” (5 February 2016). Another easily overlooked feature in OS X is Quick Look, introduced in Mac OS X 10.5 Leopard back in 2009.
Quick Look offers a fast preview of what’s inside a file, most notably in the Finder and third-party file transfer apps. It works with many common file types, such as text files, images, audio, video, PDFs, Microsoft Office files, and even fonts (here’s a larger list of supported file types).
We’ll explain how to use Quick Look, in which apps you can use it, and how to use it from the command line (which is also helpful for troubleshooting). Then we’ll share some of our favorite Quick Look plug-ins to extend Quick Look’s capabilities and make it even more useful.
(One quick internal note. If you’re reading this on our Web site, click any image to zoom it to a better size; click it again to shrink it down. It’s not Quick Look, but it’s not far off, and some reader comments have indicated that people don’t realize this is how our site works.)
Basic Quick Look Usage
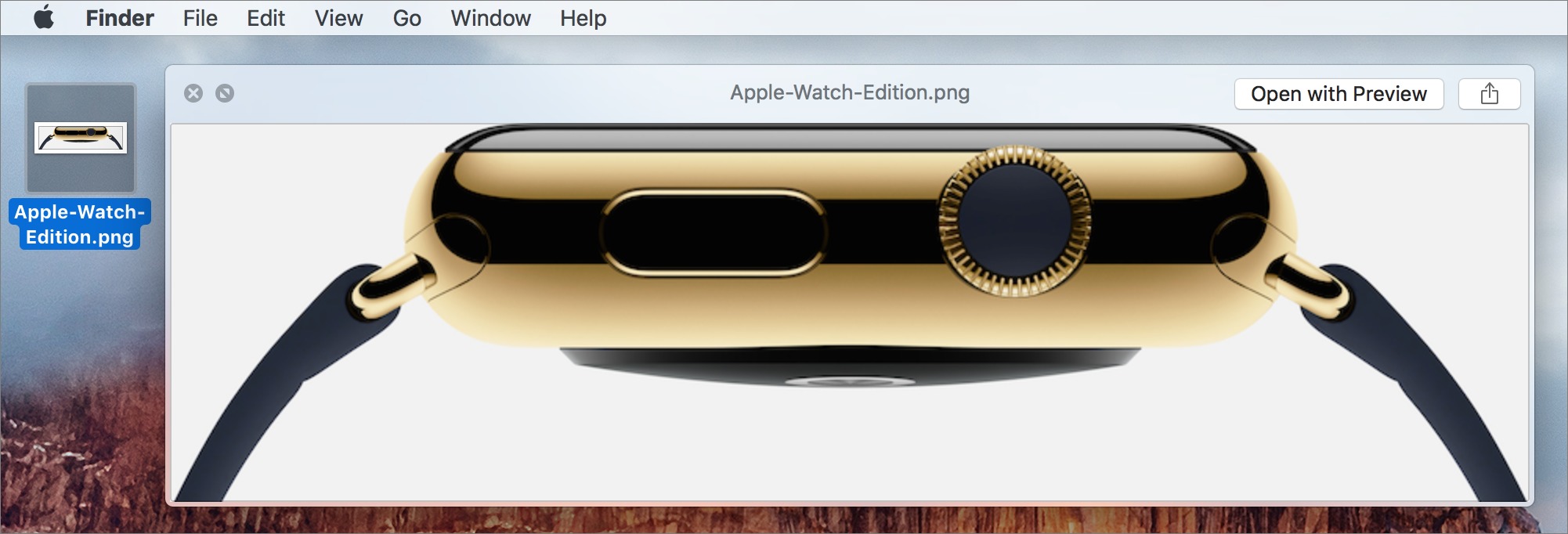
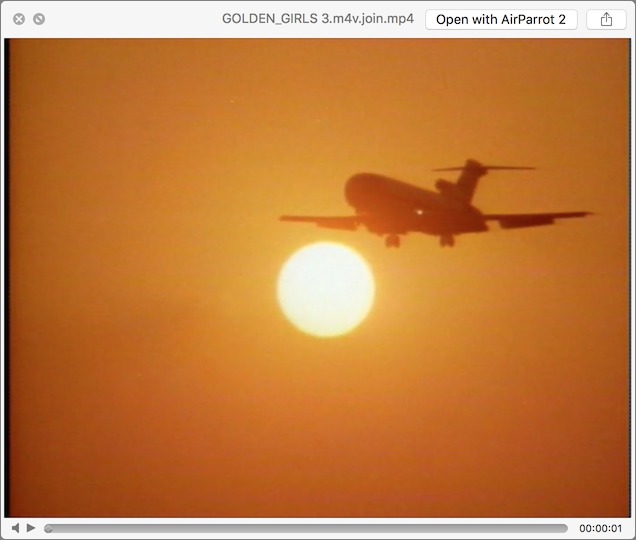
To invoke Quick Look in the Finder, select a file and choose File > Quick Look “filename” (Command-Y). Better yet, just click a file and press the Space bar. The screenshot below shows Quick Look displaying a picture of an Apple Watch Edition.
With Quick Look open, you can click Open with App to open the file in its default app. You can also click the Share button in the upper right to send the file to another app or service without fully opening it. If the file you’re previewing with Quick Look has multiple pages, you’ll see thumbnails on the right that you can scroll through using your mouse or trackpad, or by using the Page Up/Page Down keys (on a laptop, use Fn-Up Arrow and Fn-Down Arrow). Although Quick Look windows generally open to a useful size,
you can resize the window by dragging any edge. To close Quick Look, press the Space bar or Command-Y again, press Escape, or click the window’s close button in the upper left.
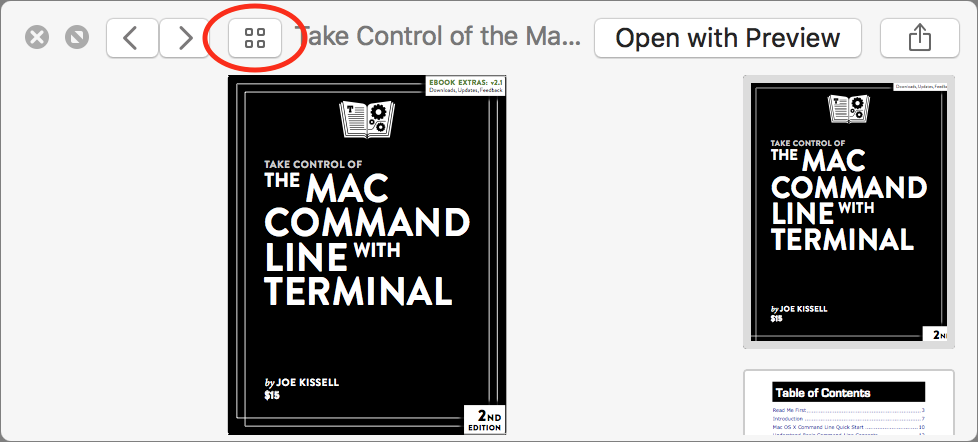
If you select multiple files before invoking Quick Look, you can use the Left and Right arrow keys to cycle through your selections; there are also forward and back buttons that appear in the top left of the Quick Look window. Next to those buttons is a thumbnail button that displays the selected files in a grid of thumbnails. Click any thumbnail to focus on just that item.
You can also use Quick Look to scan through the contents of a folder. While Quick Look is open, use the arrow keys to display other files in the same folder — how you navigate among the files depends on the Finder window’s view. Using Quick Look and the Up and Down arrow keys can be a
great way to browse pictures in a folder in List view. You can continue to interact with the Finder while using Quick Look, which means you can delete an unwanted file by pressing Command-Delete while previewing it.
One interesting use of this capability is that you can use Quick Look to examine files in the Trash, which can’t otherwise be opened while they remain in the Trash. So if you want to recover a particular image among a bunch that you’ve trashed, Quick Look is a fast way to figure out which one to pull out. Similarly, you can use Quick Look within Time Machine to preview file versions before restoring them.
Certain file types offer special controls. If you open an image that’s larger than the Quick Look window, press the Option key to expand the image to its original size and use the mouse to pan around in the expanded image. Plus, when using Quick Look to preview video and audio files, you see mute and play/pause buttons, along with a scrubbable timeline.
Want to focus on an image without the distraction of your desktop? Select a file and press Option-Space (or Command-Option-Y) to open the Quick Look view in full-screen view. You can also enter full-screen view by clicking the zoom button in the upper left (to the right of the close button) while viewing a file in a regular Quick Look window.
One final tip. Quick Look also works in Open dialogs, so you can select any file and press the Space bar to see the preview. You can even select multiple files and preview them just as though you had selected them in the Finder. The only caveat is that the Open with App button does not appear.
Quick Look Outside the Finder
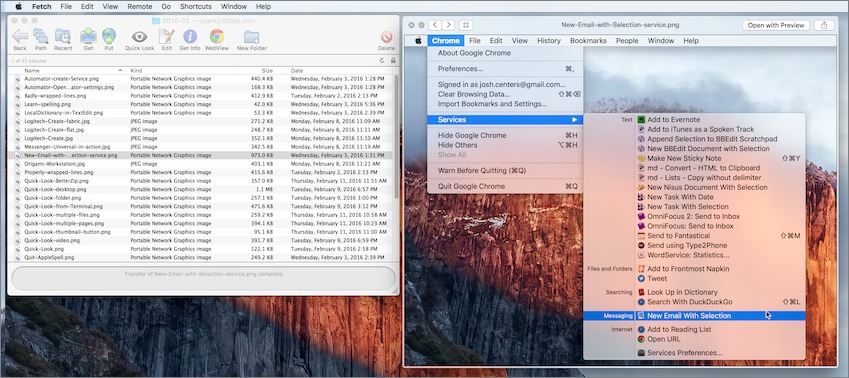
Quick Look isn’t limited to the Finder. The main additional place you’ll find it is in file transfer apps like Fetch, Transmit, and Cyberduck. In those apps, Quick Look is usually invoked in exactly the same way as in the Finder, with a click to select a file and then a press of the Space bar.
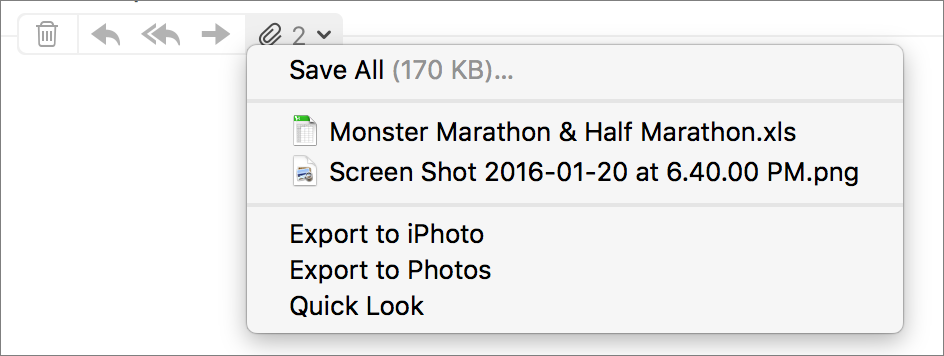
However, various other OS X apps, including Mail and Messages, take advantage of Quick Look as well. In Mail, you can use Quick Look on attachments by clicking the paperclip button (which appears when you move the cursor to the message header area) and choosing Quick Look. In Messages, you can view all the attachments in a conversation by choosing File > Quick Look — it’s like previewing multiple files in the Finder with Quick Look, so you can navigate through them with arrow keys. Alternatively, double-click an attachment,
select it and press the Space bar, or use a three-finger trackpad tap.
Safari, Mail, and Messages also let you summon a preview of a Web link with a three-finger tap on the trackpad (sorry, mouse users!). This may not be Quick Look behind the scenes, but it’s conceptually similar. If it doesn’t work for you, enable Look Up & Data Detectors in System Preferences > Trackpad > Point & Click.
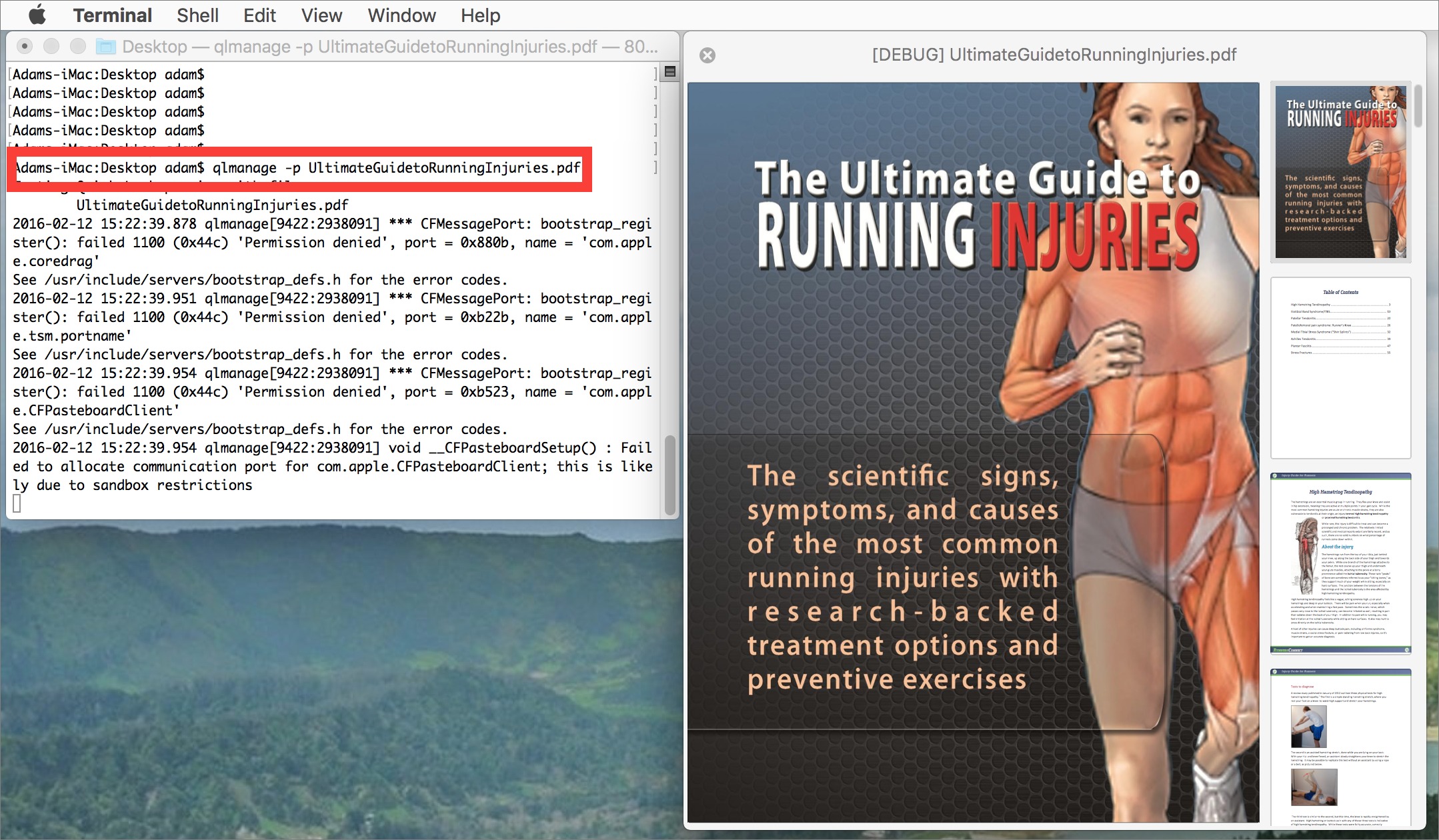
Quick Look from the Command Line
If you prefer the command line for browsing, you can use Quick Look from Terminal with the command qlmanage -p filename. That’s handy for a quick glance into any file that’s not straight text and thus not viewable with the likes of less and tail. It’s a little fussy — it displays a bunch of debug messages and you have to close the Quick Look preview or press Control-C to quit the process — but it’s handy if you don’t want to switch back out to the Finder to look inside a file.
The qlmanage -m command is also useful, since it displays all the loaded Quick Look plug-ins and may alert you to the existence of Quick Look support in apps you hadn’t realized supported Quick Look (DEVONthink! Evernote!). Since Quick Look plug-ins can conflict with one another (we haven’t yet figured out what determines loading order), qlmanage -m can help you determine which app has precedence. To suss out who was managing EPUB support in Quick Look (see below), we used qlmanage -m | grep epub, which filtered just the EPUB-related lines out of the full report.
Another reason to use the qlmanage command is for paranoid security reasons. Whenever Quick Look is invoked, OS X creates a cache of the thumbnail data for future use, even if the file previewed was on an external drive. To prevent an attacker (with physical access, of course) from spelunking through the thumbnail cache, you can reset it with the command qlmanage -r cache. It’s not a concern for most people, but secret agents should take note.
There’s a bug in Quick Look that fails to release previewed files right away. So if you preview a file with Quick Look, send it to the Trash, and immediately try to empty the Trash, the Finder won’t delete that file, claiming that it’s “in use.” The solution is either to wait a while for Quick Look to let go of the file, or to reset Quick Look with qlmanage -r and try again.
Finally, if you’re using a version of OS X prior to OS X 10.11 El Capitan, you can use the following Terminal command to enable copying text from the Quick Look window. Unfortunately, Apple decided to disable this option in El Capitan. Boo!
defaults write com.apple.finder QLEnableTextSelection -bool TRUE; killall Finder
Extend Quick Look with Plug-ins
Quick Look supports a number of file types out of the box, but far from all of them. Thankfully, Apple created a plug-in interface for Quick Look so that developers could expand its capabilities, even without a companion app.
We’ve found a number of useful Quick Look plug-ins, but before we share that list, you need to know how to install them. All standalone Quick Look plug-ins are .qlgenerator files that need to live in /Library/QuickLook (if you want the plug-in to be accessible to all users on your Mac) or in ~/Library/QuickLook (if only your user needs to be able to use it). Some Quick Look plug-ins are distributed as package files that you double-click to install in one of those locations. But most are just bare .qlgenerator files that need to be moved to a Library folder manually. To install them in your user Library folder, in the Finder, press Option and choose Go > Library.
Then open the QuickLook folder (create it if necessary, noting that the folder name doesn’t have a space between the two words). Drag .qlgenerator files into this folder.
After installing a new Quick Look plug-in, OS X should notice and load it automatically, but if the plug-in doesn’t seem to work, you may need to refresh the Quick Look engine. A restart is easy, but you can instead either log out and back in or Control-Option-click the Finder icon in the Dock and choose Relaunch. Or, if you’re in Terminal, type qlmanage -r and press Return.
With that out of the way, here are some of our favorite Quick Look plug-ins:
- Art View: One of only two commercial Quick Look plug-ins on this list, the $49.95 Art View helps graphic designers by both previewing Adobe InDesign and Illustrator files and providing additional information about embedded fonts and linked images. There’s a 15-day free trial if you want to give it a try.
- BetterZip: BetterZip lets you peer inside a wide variety of compressed archives and even disk images! Just download the app, extract it from the .zip archive, drag it to your Applications folder, and restart your Mac. After that, when you use Quick Look on compressed archives and disk images, you’ll see a preview of their contents.

- HetimaClipping: If you select text and drag it to the Finder, you’ll get a text clipping, and you can insert that text into other apps by dragging it into the right location. Text clippings aren’t terribly useful, but part of the reason is that without this Quick Look plug-in, you can’t easily preview them. It also works with picture clipping files.
- Murasaki: Although iBooks has a Quick Look plug-in, all it does is display the cover of the book, which isn’t much of a preview. For those who want to crack the covers on an EPUB, the best option we know of is the EPUB reader Murasaki, which includes a Quick Look plug-in that lets you scroll through the entire book. (Even better would be the Quick Look plug-in from the EPUB reader Scarlett, which shows the table of contents and theoretically lets you navigate within the book that way; sadly, it doesn’t display the text of the book at all.)
Murasaki costs $7.99 from the Mac App Store, but it may be worthwhile for those who use EPUBs a lot or who would prefer a scrolling EPUB reader instead of the page-by-page approach of iBooks.
- qlcolorcode: If you work with source code regularly, you probably appreciate how much more readable it is when individual elements are denoted with colored text. The qlcolorcode plug-in does just that, making source code files in Quick Look that much more parsable.
- qlImageSize: The simple qlImageSize plug-in displays the dimensions and file size of images in the Quick Look title bar. It also enables Quick Look to show previews for a few otherwise unsupported graphic formats. It’s distributed as a package installer; Control-click it and choose Open from the contextual menu to launch the installer and install into
/Library/QuickLook. - QLMarkdown: This plug-in enables Quick Look to display fully rendered Markdown files (see “Enable Quick Look for Markdown Files,” 17 January 2013).
- QLStephen: At last, you can view all of your favorite Stephens in Quick Look! Just kidding. The QLStephen plug-in lets you view text files without extensions in Quick Look. For instance, many downloaded packages include a README file that lacks a .txt extension in the filename and without this plug-in, Quick Look can’t display them.
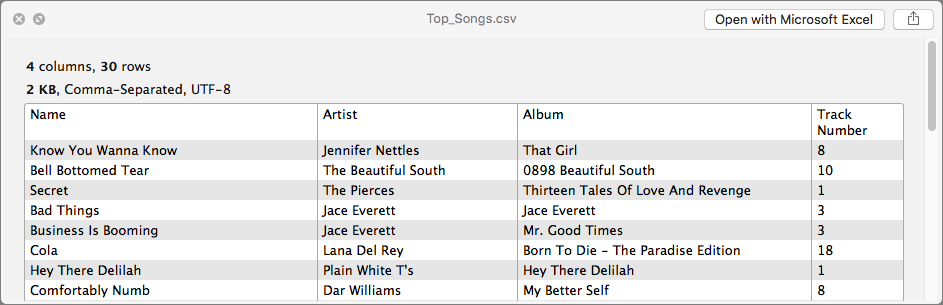
- QuickLookCSV: By default, Quick Look shows you previews of Numbers spreadsheets, but not comma separated values (CSV) files, which are often used to distribute spreadsheets. The QuickLookCSV plug-in displays these files, split into rows and columns.
- Quicklook Video: The Quicklook Video plug-in adds support for more video formats than Apple offers out of the box.
For even more Quick Look goodness, check out the QuickLook Plugins List, which is the best centralized repository of Quick Look plug-ins.
Quick Look is easy to master, and once you get in the habit of using it, you’ll be all the more productive on your Mac. Let us know in the comments if you have any other Quick Look tricks or plug-ins that you find useful!
TidBITS Watchlist: Notable Software Updates for 15 February 2016
PopChar X 7.4 — Ergonis Software has issued PopChar X 7.4 with support for displaying all the color flags that are available in Apple Color Emoji. You can also search for country names (rather than use combinations of so-called “regional indicator symbols,” such as “CK” for the Cook Islands flag), and this functionality requires OS X 10.10.3 Yosemite or later (with an extended flag set available in 10.11 El Capitan).
The character discovery utility also improves metrics adjustments for certain fonts (such as handwriting fonts), fixes a a minor cosmetic issue with the group pop-up button on Retina displays, and improves the app’s clipboard-based insertion technique. (€29.99 new with a 25 percent discount for TidBITS members, free update, 4.5 MB, release notes, 10.6+)
Read/post comments about PopChar X 7.4.
Piezo 1.5 — Rogue Amoeba has released Piezo 1.5 with the addition of the Instant On component (also found in other Rogue Amoeba titles such as Audio Hijack and Airfoil), which enables the minimalist audio recording app to capture audio from already-running applications. Additionally, Rogue Amoeba has pulled Piezo from the Mac App Store due to Apple’s sandboxing limitations, which made Piezo less and less effective over time. (For more details on Piezo, see “Piezo Makes Audio
Recording Dead Simple,” 8 December 2011.)
If you previously purchased Piezo from the Mac App Store, you can download it directly from the Rogue Amoeba Web site. The app will recognize Mac App Store buyers and will lead them through a brief, one-time migration process that provides a complimentary license key (make sure to get your license key before recording with Piezo). See this Rogue Amoeba blog post for license migration instructions, as well as more background on Rogue Amoeba’s decision to leave the Mac App Store.
Piezo 1.5 also improves VU meter animation and ensures that the Sparkle-powered software update mechanism runs securely over HTTPS. ($19 new, free update, 8.4 MB, release notes, 10.9+)
Read/post comments about Piezo 1.5.
Hazel 3.3.7 — Noodlesoft has released Hazel 3.3.7, a maintenance update that offers a few fixes for the file cleanup utility. The new version fixes a couple of instances of rules not triggering (where “date last matched” is used and when using “did change”), resolves an issue with events being filtered out in cases where a nested condition used a “sub-file…” target with the file event in a subfolder, and fixes a problem with conditions using “this week/this month/this year…” matching randomly when they shouldn’t. ($29 new, free update, 9.0 MB, release notes, 10.8+)
Read/post comments about Hazel 3.3.7.
1Password 6.0.2 — After releasing 1Password 6.0 (and subsequently version 6.0.1; see “1Password 6 for Mac Adds Teams, Expands Sync Options,” 18 January 2016), AgileBits has now followed up with 1Password 6.0.2, which adds a preference that enables you to control which vault opens when you unlock the password manager. The update also improves the autosave feature to better understand which sites to avoid, renames the Everyone and Your Vault vaults in 1Password for Teams to Shared and Personal to avoid confusion, fixes a bug that prevented 1Password mini from showing
logins for certain site variations (such as showing on amazon.com, but not amazon.co.uk), resolves an issue that caused the Option key to not reveal passwords in 1Password mini, and ensures that anchored 1Password mini windows retain their contents after unlocking.
1Password 6.0.2 is a free update for owners of 1Password versions 4 and 5 (upgrade prices for version 3 and older vary). As of this writing, the Mac App Store version of 1Password remains stalled at version 6.0.1. ($49.99 new from AgileBits and the Mac App Store with a 25 percent discount for TidBITS members when purchased from AgileBits, free update, 43.8 MB, release notes, 10.10+)
Read/post comments about 1Password 6.0.2.
ExtraBITS for 15 February 2016
In this week’s ExtraBITS collection, Google is shutting down its Picasa photo service, a serious (but now fixed) bug in Adobe Creative Cloud’s Mac software deletes files, Bob “Dr. Mac” LeVitus sets his criticisms of iTunes to music, Apple Music works with Sonos audio systems, and the Apple Store is installing Belkin screen protectors on iPhones.
Google to Shut Down Picasa in Favor of Google Photos — Google has announced that it will shut down its Picasa photo service on 1 May 2016. The company advises Picasa users to log in to Google Photos to access their Picasa photos, which should already be transferred. Google also said that it will provide a way for Picasa users to access their photos without Google Photos. As for the Picasa desktop app, Google will stop supporting it on 15 March 2016. We can’t say that we’re surprised by this move, since Google has shifted heavily toward Google Photos, but we will miss Picasa’s Mac
app, as it was one of only a handful of alternatives to Apple’s Photos on the Mac.
Adobe Creative Cloud App Deletes Contents of Hidden Folders — The folks at cloud-backup service Backblaze discovered a troubling behavior in Adobe Creative Cloud: an update to Adobe’s Mac software was deleting the contents of the first hidden folder it saw, in alphabetical order, at the root of users’ disks. (Hidden folders aren’t displayed in the Finder, but often contain important settings or other data.) Backblaze users noticed the bug because the Backblaze app depends on a hidden folder called .bzvol, which is often alphabetically the first hidden folder on Backblaze users’ drives.
For other Mac users, the first folder would likely have been .DocumentRevisions-V100, which stores data required for OS X’s Auto Save and Versions features — deleting that data could be problematic. Adobe acknowledged the bug and replaced the update quickly, so make sure to let Creative Cloud update itself.
iTunes Must Die: The Song (and Petition) — Over the years, we’ve shared numerous lamentations about the myriad problems with iTunes. The latest person to lend his voice — literally — to the cause is well-known author and musician Bob “Dr. Mac” LeVitus, who has recorded the song “iTunes Must Die” in conjunction with an “iTunes Must Die” petition. You can preview it for free on CD Baby, and if you want your own copy, it’s available for $0.99 from Amazon, CD Baby, and Google Play, though not yet from the iTunes Store. Hmm…
Apple Music Arrives on Sonos — If you’re a fan of both Sonos wireless audio systems and Apple Music, we have good news: they now work together! To stream songs from Apple Music on your Sonos system, choose Add Music Services in any Sonos controller app, tap the Apple Music button, and log in.
Apple Stores Installing Belkin iPhone Screen Protectors — Although iPhone screens are generally quite durable, particularly if guarded by a case, some people like to add a screen protector too. But installing a screen protector can be a finicky and error-prone process that suffers from problems with alignment, air bubbles, and trapped dust. Apple and Belkin are trying to address these frustrations in Apple retail stores, where Apple employees will install screen protectors using Belkin’s proprietary ScreenCare+ Application System — a machine designed to perform perfect installations. The system works with
the iPhone 6, 6 Plus, 6s, and 6s Plus, and offers two screen protector options: InvisiGlass and Anti-Glare.