TidBITS#1337/12-Sep-2016
We have huge news for you this week, as Apple has announced the iPhone 7 and iPhone 7 Plus, as well as the Apple Watch Series 2. But that’s not all: Apple also unveiled the AirPods, new Bluetooth wireless earbuds powered by a proprietary W1 chip. Apple’s September 7th event boasted other surprises as well, including new commitments to education, real-time collaboration features in iWork, and a Super Mario Bros. game for the iPhone. And if that weren’t enough, Apple that day also published the release date for macOS 10.12 Sierra and tweaked its iPad lineup. In other news, Dropbox is removing the capability to host Web pages with its service. Finally, Jeff Porten takes a deep look at how foreign hackers could affect the 2016 U.S. presidential election. Be sure to read ExtraBITS right away for news of a spectacular one-day sale on iTunes Movies! We have no TidBITS Watchlist for you this week, as most developers delayed releases to avoid being overshadowed by Apple’s announcements.
Apple’s iPhone Event: Education, Karaoke, Mario, and More
Apple opened its September event with a special edition of James Corden’s “Carpool Karaoke,” featuring Tim Cook, Pharrell Williams, and Corden singing “Sweet Home Alabama” as the car pulled up to the stage door entrance so Tim could walk in and begin the show. Even when he did, the presentation remained an exercise in delayed gratification, as Cook held back on the big, anticipated announcements so that he could do a bit of updating on current Apple initiatives.
If you don’t have time to watch the entire event, Apple has posted a very quick, very loud summary video to YouTube.
Cook began his on-stage stint with an Apple Music update, noting that the service now has 17 million subscribers, and he briefly described the new interface coming to Apple Music in iOS 10, which he described as “simple and intuitive.” He finished that segment of the presentation by promoting the upcoming Apple Music Festival (formerly known as the iTunes Music Festival) to be held at the Roundhouse in London from September 18th through 30th.
From music, Cook turned to the App Store. Noting that the App Store has now tallied more than 140 billion apps downloaded since its debut, he announced that the store had generated twice the revenue of its closest competitors in the previous two months and had experienced 106 percent year-over-year growth. These statistics seemed designed to mollify investors harboring worries over the company’s recent decline in profits (see “Apple Beats Expectations in Q3 2016, but Slump Continues,” 26 July 2016).
One of the factors behind the App Store’s recent growth is games — can you say Pokémon Go, which has been downloaded over 500 million times? The App Store currently carries more than 500,000 games, and Cook used that statistic as an opportunity to bring out Nintendo’s Shigeru Miyamoto, creator of the Super Mario Bros. and Legend of Zelda franchises — he’s essentially the Walt Disney of video games. With the help of a translator, Miyamoto gave a demonstration of his company’s forthcoming Super Mario Run — Nintendo’s first full iOS game, and the iconic character’s iOS debut (our 2014 April Fools article
notwithstanding). In an App Store first, you can sign up to hear when Super Mario Run becomes available to purchase, which Nintendo expects to be during the 2016 holiday shopping season. Super Mario stickers will also be available in Messages with the rollout of iOS 10.
Speaking of Pokémon Go, developer Niantic announced an Apple Watch version of the game that will let players perform many common actions without having to pull out their iPhones.
But it wasn’t all fun and games in the prelude that led up to Apple’s big announcements. Apple has long been interested in education, and Cook took the opportunity to share what Apple is doing in the White House’s ConnectED program. Under this program, which provides funding, equipment, and support to “under-served” schools around the country, Apple will supply 114 schools with Macs, iPads, and Apple TVs: 4500 teachers will receive iPads and Macs, Apple TVs will be installed in every classroom in the participating schools, and more than 50,000 students will receive iPads. (This is great, and we’re not criticizing, but to give a sense of scale, there are nearly 100,000 K-12 schools in the United States and almost 55 million students, meaning that Apple’s contribution to ConnectED will affect 0.1 percent of the country’s schools and students.)
What will those students and teachers be running on that equipment? Among other things, Swift Playgrounds, a learning environment for coding that ships with iOS 10 and that is augmented with teaching guides and instructional tips.
Along with Swift Playgrounds, students will be able to use updated versions of Apple’s iWork apps. Cook ceded the stage to Susan Prescott, senior vice president of product marketing, who demonstrated the newest feature in iWork: real-time collaboration. Although iWork has long allowed document sharing on both Mac and iOS devices, real-time collaboration capabilities previously had been limited to the browser-hosted versions of the apps.
The new iWork apps, however, now support real-time collaboration natively on all devices, which Prescott illustrated by building a Keynote presentation with animations and graphics supplied by both her and collaborators. Because teaching students to work collaboratively has become an integral part of many curricula, this addition to the iWork suite promises to make the apps a more compelling option for educators, including those who are not part of the ConnectED initiative. However, collaboration is something Apple has struggled with numerous times in the past (see “iWork for iCloud Beta Recalls iWork.com,” 10 June 2013), so we’re curious to see if these new features will, in fact,
prove useful to educators, or anyone else.
Following that demonstration, Cook and his compatriots took the stage to present new watches, new phones, new cameras, new earbuds, and more. You can read about those announcements in the following articles:
- “iPhone 7 and 7 Plus Say “Hit the Road, Jack.”,” 7 September 2016
- “Apple Watch Series 2 Offers GPS, Water Resistance, and More Power,” 7 September 2016
-
“W1-powered AirPods Usher in a New Era of Wireless,” 7 September 2016
Finally, although Apple made no mention of the Mac or iPad during the presentation, later that day, the company published the release date for macOS 10.12 Sierra (it will debut on 20 September 2016) and adjusted the iPad lineup slightly (see “Apple Tweaks iPad Configs and Pricing,” 12 September 2016).
Dropbox to Discontinue HTML Rendering, Breaking Hosted Sites
For many years, if you needed to throw up a quick Web site, one of the easiest ways to do it was to put HTML-formatted text files and linked graphics in your Dropbox folder’s Public folder. Control-click the index.html file for your site in the Finder, choose Copy Public Link to get the URL to the page, and you had a fully functional site to share. This worked because Dropbox allowed HTML files to be rendered by the browser instead of forcing them to be treated as downloads. Dropbox hasn’t been enthused about this feature for years, but the company let it continue (see “Dropbox Public Folder Leaves and Returns,” 14 July 2012).
Unfortunately, as of 3 October 2016, Dropbox says it will no longer allow HTML files loaded in a Web browser to be rendered. The files themselves remain safe in Dropbox, but Dropbox will presumably give those who click the links the options of downloading the file or adding it to their own Dropbox folder, just as happens with non-Web file types now. Thanks to reader Vic Case for alerting us to this development; although Dropbox informed some users, neither I nor Joe Kissell, author of “Take Control of Dropbox, Second Edition” received any such notification.
So, if you’re hosting a simple Web site via Dropbox, you have a few weeks to find an alternative host and update any links to your site. You might think that you could just switch to Google Drive, which also provided this sort of service, but Google Drive also discontinued hosting of Web pages as of 31 August 2016.
Alternatives abound, but finding one that is equivalently simple (and cheap, if you were using a free Dropbox account) could require some research. A year ago, Scott Murray, then an Assistant Professor of Design at the University of San Francisco, published a rundown of services that offer cheap or free hosting of static Web sites to help graduating seniors keep their sites alive after their student accounts were deleted. It’s now somewhat dated, with Dropbox and Google Drive gone, and some resources are appropriate only for students, but it’s still a good start.
I don’t want to make any recommendations in this area since I have no experience with any of the choices. Instead, I’ll open it up to readers — if you’re hosting a simple static Web site, where are you doing it, how much does it cost, and how happy are you with the service?
iPhone 7 and 7 Plus Say “Hit the Road, Jack.”
Yes, the rumors are true: the next generation of iPhone — the iPhone 7 and the iPhone 7 Plus — get rid of the nearly universal headphone jack. Why? Apple’s Senior Vice President of Worldwide Marketing Phil Schiller summed it up in a word: “Courage.” Yes, “courage,” hearkening back to Apple’s prior decisions to abandon floppy disks, optical drives, and legacy ports. Or how Apple plans to deal with the inevitable criticism.
After we stopped giggling at this pronouncement of courage, we tried to focus on how Apple made up for the missing analog jack. Every new iPhone will ship with a Lightning-to-headphone adapter so you can still plug in your existing devices. Also, the new iPhones will be bundled with Lightning-connected EarPods. Sadly, neither the adaptor nor the new EarPods allow the iPhone to be charged when they’re plugged in — we expect third-party vendors will fill in that gap. Fortunately, extra Lightning to 3.5mm Headphone Jack Adapters will cost only $9 from Apple.
However, Apple said the future is wireless, which begs the question of why the company doesn’t have the courage to go whole hog and include its new wireless AirPods in the box (the price of courage would then be $159, in case you were wondering). The good news is that Apple isn’t leaving you at the mercy of stock Bluetooth audio: the new AirPods introduce Apple’s proprietary W1 chip, which enhances the Bluetooth experience for the AirPods and other headphones from Apple subsidiary Beats (see “W1-powered AirPods Usher in a New Era of Wireless,” 7 September 2016).
How big of a deal is the lack of a headphone jack? It wasn’t popular, with a post-announcement survey of 1140 American consumers by Toluna Quicksurveys revealing that Apple’s move ranks among the least favorite changes in the iPhone 7. However, Toluna Quicksurveys added a couple of exclusive questions at our request. Of the respondents, 74 percent said that the lack of a headphone jack wouldn’t affect their purchase decision, and 56 percent of respondents went further, saying that it wouldn’t even require them to change their habits, presumably because they already rely on wireless audio or the iPhone’s built-in speakers.
Speaking of speakers, you may not need to plug in as much for audio, since the new iPhone will be the first to feature stereo speakers: one on the top and one on the bottom. Apple also said that the new iPhone 7 models produce twice the volume of the iPhone 6s units.
What else do you get in exchange for losing that headphone jack? Water and dust resistance. Apple claims the new iPhones are IP67 compliant, which means they are completely protected against dust and protected against immersion in up to 1 meter of water. IP67 is the highest level of dust protection and the third-highest level of water protection. Realistically, your iPhone 7 should be fine if you accidentally drop it in the tub, but losing it overboard in anything but shallow water may still kill it. Apple still warns that the iPhone warranty doesn’t cover liquid damage, so for safety, we
recommend assuming that the iPhone 7 is no different than previous models. Concerning dust, we hope the Lightning port doesn’t collect pocket lint like the ports in earlier models did — a blast of compressed air is often the solution to odd charging problems.
Apple has redesigned the Home button. Like the Force Touch trackpad, the Home button is now a “force sensitive” software button that Apple claims is more responsive and more reliable. Apple integrated the Home button with a new generation of the Taptic Engine, which comes with an API — we’re curious to see how developers take advantage of the new hardware. Perhaps an iPhone 7 will be able to give you text messages in Morse code?
The biggest improvements to the iPhone 7 are its cameras. Yes, cameras, because while the iPhone 7 includes one dramatically improved rear-facing camera, the iPhone 7 Plus features two cameras on the back of the case.
The camera in the iPhone 7 includes a 12-megapixel high-speed sensor with an ƒ/1.8 aperture six-element lens that Apple claims is 60 percent faster and 30 percent more energy efficient than the camera in the iPhone 6s. The flash now features four LEDs, which Apple says offer 50 percent more light, plus a flicker sensor to help the software correct for artificial lighting. Optical image stabilization, formerly exclusive to the Plus model, is now standard on the iPhone 7.
As noted, the iPhone 7 Plus features two 12-megapixel sensors: one with a wide-angle lens and the other with a telephoto lens with an ƒ/2.8 aperture. Putting these together enables two new features: 2x optical zoom (up to 10x in software) and a new depth of field effect, which produces photos in which people in the foreground are in focus while the background is blurred. While Schiller was quick to admit that the iPhone 7 Plus’s camera isn’t up to DSLR quality, it’s a big step closer. The depth of field effect, which you’ll access via a new camera mode labeled Portrait, will not be available at launch, but will instead arrive in a free iOS update “later this year.”
Both iPhone models can also capture raw images with wide-gamut color, and offer stabilization and editing for Live Photos. Apple is also releasing capture and editing APIs for Live Photos, so developers can create tools to work with them. Last but not least, the front-facing FaceTime HD Camera now offers 7-megapixel resolution, body and face detection, and automatic image stabilization.
Complementing the improved cameras is a new Retina HD display that’s 25 percent bright and offers cinematic color and built-in color management. That should be welcome news for photographers. Instagram demoed new effects and filters that take advantage of the expanded color gamut.
Under the hood, the new iPhones feature a new A-series processor, the quad-core A10 Fusion with an embedded M10 motion coprocessor. Interestingly, two of the four cores are dedicated to high performance, while the other two are optimized for power efficiency, using 20 percent of the power of the other cores. A new Apple performance controller automatically switches between the two sets, depending on what’s needed.
The A10 Fusion processor includes a new Apple-designed image signal processor, which applies over 100 billion operations (we assume this is a generous definition of “operation”) and machine learning to every photo you take. It also allows for faster focus, improved local tone mapping, and better white balance.
Relatively little changes regarding networking, but the iPhone 7 and 7 Plus support 25 LTE bands, with theoretical speeds of up to 450 Mbps. We doubt you’ll see such throughput anytime soon.
Apart from the cameras, the form factors of the iPhone 7 and 7 Plus are the same as the iPhone 6s and 6s Plus, but the color options are slightly different. The new iPhones will feature the now-standard gold, silver, and rose gold finishes, but Apple swapped space gray for two shades of black: a shiny “jet black” finish and a matte finish, that Apple calls “black.” Apple cautions buyers that the jet black finish can scratch, but reports from those who have held it indicate that it’s less slippery than the other finishes. The new models are 5 and 4 grams lighter than the previous models, respectively.
Finally, Japanese models of the iPhone 7 and 7 Plus (and the Apple Watch Series 2; see “Apple Watch Series 2 Offers GPS, Water Resistance, and More Power,” 7 September 2016) will include FeliCa contactless technology, enabling Apple Pay to work in Japan (for more on this, see “Around The World With Apple Pay,” 13 May 2015). In other news for Japanese users, Apple said that transit directions for locations in Japan should become available in Maps in October.
Pricing of the iPhone 7 and 7 Plus remains the same as for previous models, but the storage amounts double, so:
- 32 GB iPhone 7: $649 / iPhone 7 Plus: $769
- 128 GB iPhone 7: $749 / iPhone 7 Plus: $869
- 256 GB iPhone 7: $849 / iPhone 7 Plus: $969
Oddly, the jet black color is available only in 128 GB and 256 GB sizes.
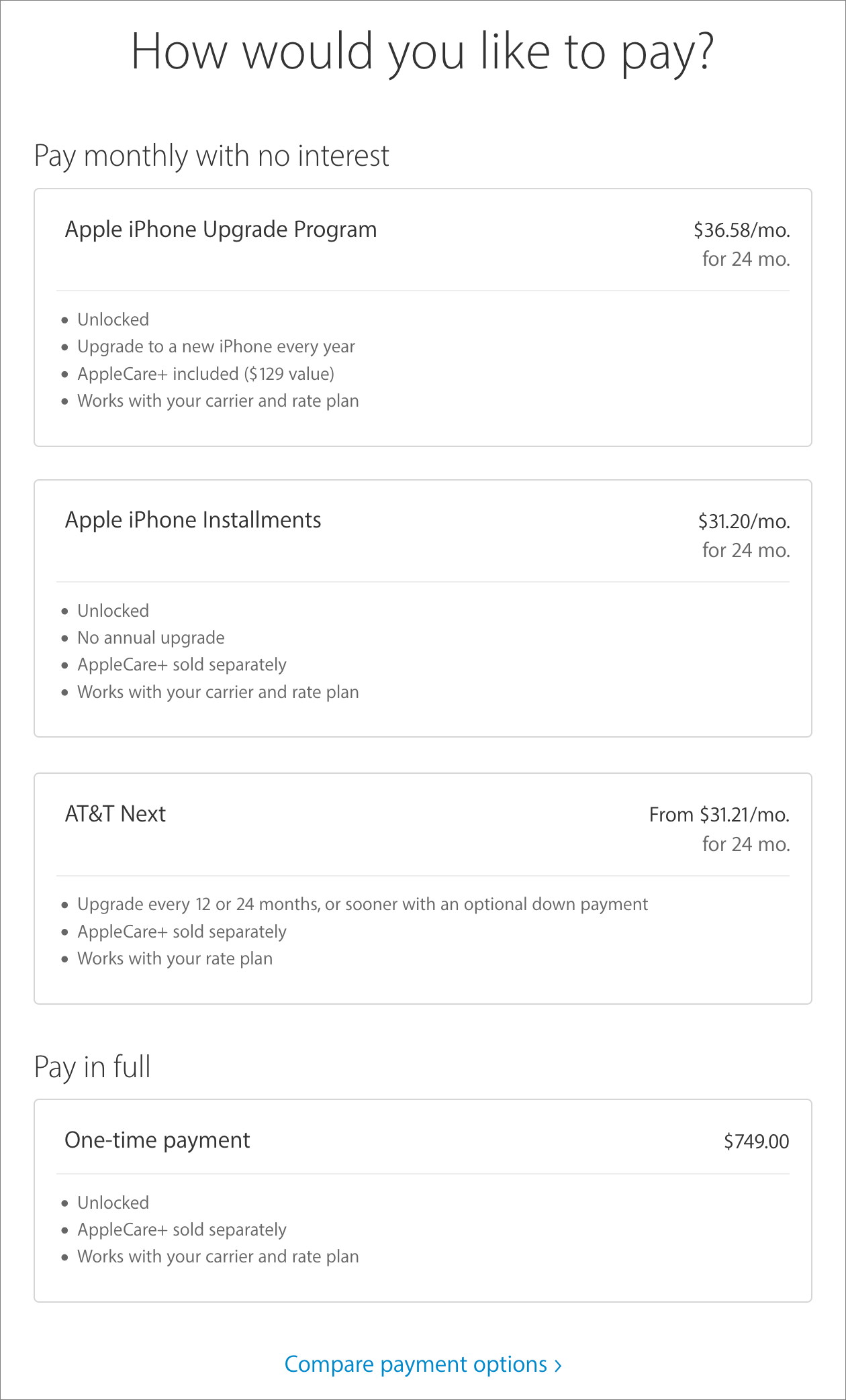
If the upfront cost is too much for you, you can instead choose the iPhone Upgrade Program’s payments of $32 to $46 per month for 2 years, depending on which model you want. iPhone preorders started on 9 September 2016, with availability promised for 16 September 2016. In fact, depending on your carrier, you may have multiple purchasing options, and after you’ve configured an iPhone in Apple’s online store, you’re shown those options. Clicking a Compare Payment Options at the bottom displays an informative table of all the possibilities.
As is common for Apple, previous models remain available, so you can still buy an iPhone 6s or 6s Plus, but in doubled 32 GB and 128 GB capacities at reduced prices. The iPhone SE stays on the price list too, in 16 GB and 64 GB capacities.
As Apple always says, these are the best iPhones the company has ever made. This statement, while banal, is always true too, although we can imagine some people delaying an upgrade or purchase until they’ve had a chance to think through the implications of losing the headphone jack. Photography lovers, at least those with small hands or pockets, will also have to weigh the appeal of the dual-camera iPhone 7 Plus against its larger size. But if you’re ready for a new iPhone, the iPhone 7 and 7 Plus are tremendously appealing.
Apple Watch Series 2 Offers GPS, Water Resistance, and More Power
The original Apple Watch, though groundbreaking in numerous ways, disappointed many when Apple trotted it out last year. It garnered criticism for being bulky and underpowered while lacking certain important features, such as a GPS chip and water resistance. Its screen was sometimes hard to make out in bright sunlight, too.
Apple has now announced the Apple Watch Series 2, which is the same size as the original. So much for fantasies about a thinner, less obtrusive watch. However, Apple did check off vital items on Apple Watch users’ wish lists: water resistance, more horsepower, a brighter display, and most important, a built-in GPS chip.
Apple also announced a handful of specialty models – notably a new and supposedly extra-durable white ceramic Apple Watch Edition Series 2, which replaces the gaudy gold Apple Watch Edition. Apple is also keeping the original watch model around at a lower price along with a processor upgrade and a new moniker: Apple Watch Series 1.
Let’s Go for a Run — Runners and other athletes have long been irked that the Apple Watch lacked a GPS chip, making it necessary to carry a bulky iPhone during a run in order to track the route and get performance stats. That necessity should be a thing of the past courtesy of the Apple Watch Series 2’s integrated – and, crucially, iPhone-independent – GPS chip. It enables the Apple Watch to record precise distance, pace, and speed during outdoor workouts such as walking, running, or bicycling – no iPhone required (cue singing angels and a happier publisher; see Adam Engst’s “Exercising with the Apple Watch: The
Hardware,” 15 May 2015).
At the start of a workout, according to Apple, a Series 2 watch uses a blend of Wi-Fi, GPS, and locally stockpiled satellite data to pinpoint a user’s location quickly. Upon completion of a workout, a route map with speed data appears in the watch’s Activity app. This all counts towards filling in those Stand, Move, and Exercise rings, naturally. We expect to see third-party apps from the likes of Strava and Runkeeper take advantage of the new GPS capabilities as well.
Though GPS is a genuinely welcome improvement, note that the Series 2 still lacks cellular connectivity — found in some rival timepieces — that allows for phone-independent voice calling and data transfers when away from Wi-Fi. Perhaps we’ll see that in the Series 3 in 2018.
Let’s Go Swimming — Brave owners of the original Apple Watch have been known to take their wearables into the shower or pouring rain with no consequences. Although they were rated at IPX7, Apple said that the original devices were “splash and water resistant, but not waterproof,” and recommended against submersion.
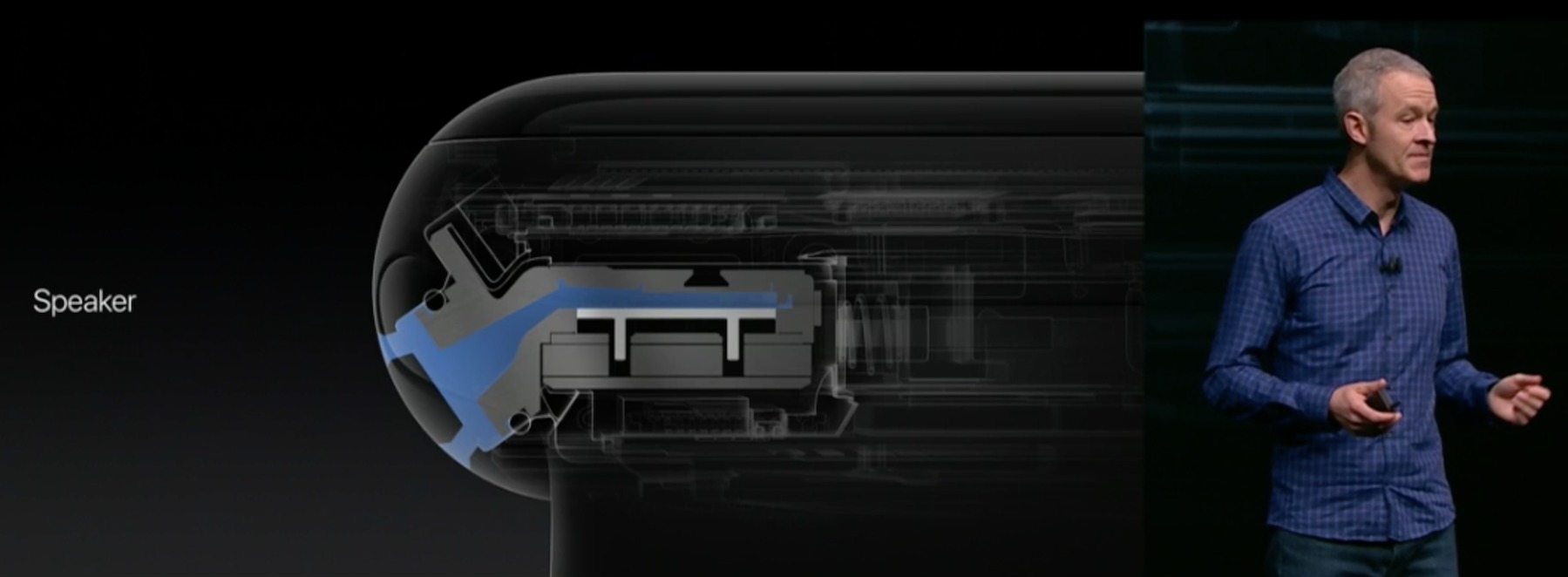
Apple is touting the Series 2 models as vastly more resistant to water, certifying them for dunks in a pool or open water at a depth of up to 50 meters (164 feet). Apple said it accomplished this by aggressively plugging up all the ingress points – with the exception of the speaker, which must be open in order to work as intended. Apple claims to have resolved that problem with a new speaker that can actively eject water (insert your own jokes here).
With the Series 2 watches now positioned as thoroughly aquatic contraptions, Apple has rolled out two new Workout options called Pool and Open Water that will enable swimmers to count laps, track average lap pace, and detect stroke styles in order to measure burned calories accurately. But you still shouldn’t take calorie counts seriously — apart from “burning more is better,” the specifics aren’t particularly useful (see “Exercising with the Apple
Watch: The Software,” 2 June 2015).
More Power! — The original Apple Watch was woefully slow, causing users no end of frustration. Some of its sluggishness was due to inefficiencies in watchOS 1 and watchOS 2, due to be corrected in watchOS 3, but the hardware deserved major blame too.
Apple says that its new second-generation dual-core S2 System in Package (SiP) in the Series 2 watch will take performance “to a new level,” and make the Apple Watch 50 percent faster. The S2 SiP also sports a new GPU that promises significantly improved graphics performance, to the point where it can even run video at 60 frames per second.
The upgraded innards will also drive a brighter display. At 1000 nits, it’s more than twice as bright as the original Apple Watch’s screen, and it has the distinction of being the brightest display Apple has ever shipped on any device. The new screen should be much more readable in bright sunlight, a distinct problem with the original model.
The dual-core S2 chip is going into the lower-cost Series 1 watches, too, so even budget-conscious Apple Watch buyers will get zippier performance.
The Fancier Options — Apple’s original version of the fancy Apple Watch Edition was made out of gold. Now, maybe fearing bored yawns among its monied clientele or perhaps chagrined at slow sales of expensive watches whose prices topped out at $17,000, Apple has shifted direction.
The new Apple Watch Edition Series 2 is made out of ceramic. This might conjure up images of plates or ashtrays falling to the floor and shattering – but Apple said it’s not that kind of ceramic. Far from it, Apple claims its zirconia ceramic is four times tougher than stainless steel with “a beautiful, white, pearl-like finish” that is “extremely scratch-resistant.”
The ceramic Apple Watch Edition looks to be tricky to track down since, like its precursor, it will be sold only at a limited number of Apple stores and Apple-authorized resellers.
Apple also announced two other specialty Apple Watch options. The Apple Watch Nike+ Series 2, offered in a partnership with the footwear manufacturer, is basically a stock Series 2 watch with Nike-like aesthetics – including Swiss cheese-like, sports bands in a choice of four black and gray designs. Two of these bands have bright yellow accents (a color that Apple flaunted on-screen with a custom watch face). The watch includes the Nike+ Run Club app, too.
For those who fancy Hermès luxury products, Apple also will sell you an Apple Watch Hermès Series 2 with your choice of redesigned Hermès leather bands.
Model Breakdown — All Apple Watch models are available in the same two case sizes as before, 38mm and 42mm. Series 2 and Series 1 watches are all available in aluminum and stainless steel with gold, rose gold, silver, or space gray coloring – no surprises there.
Cost is one crucial differentiator. Series 2 watches, including the Nike+ model, start at $369 while Series 1 models now start at $269. Dropping that price is a welcome move since the Apple Watch has been regarded by many as pricey. The starting prices are for 38mm models and increase with the 42mm model and with certain bands.
On the high end, the ceramic Apple Watch Edition Series 2 begins at $1249, and the Hermès-branded model starts at $1149.
Availability — Like the iPhone 7, the Apple Watch Series 1 and Series 2 versions, along with the Apple Watch Edition Series 2, became available for preorder in the United States on 9 September 2016. They will hit U.S. stores on 16 September 2016.
You can also preorder the Nike+ version on 9 September 2016, but it won’t become available until October. The Apple Watch Hermès Series 2 goes on sale 23 September 2016.
Internationally, Apple is releasing the new models in stages. See Apple’s press release for details.
W1-powered AirPods Usher in a New Era of Wireless Audio
Like it or not, Apple is moving away from the nigh-universal headphone jack, at least on the iPhone line. The just-announced iPhone 7 and 7 Plus, as expected, lack an analog 3.5mm headphone plug (see “iPhone 7 and 7 Plus Say “Hit the Road, Jack.”,” 7 September 2016). But the good news is that Apple understands that existing wireless audio solutions are lacking; Bluetooth sound quality is mediocre, and more importantly, it’s difficult to use Bluetooth headphones with multiple devices. AirPlay switches easily between devices, but its dependency on Wi-Fi means that the power draw is too high for mobile devices.
To counter those problems, Apple has introduced the new W1 chip, which will power the company’s upcoming flagship AirPod wireless headphones, as well as new Beats headphones. The $159 AirPods are expected in late October 2016. Apple is also incorporating the W1 chip into its new $299.95 Beats Solo3 Wireless headphones, plus the forthcoming $199.95 Powerbeats3 Wireless workout earphones, and the $149.95 Beatsx earphones.
The proprietary W1 chip brings several advantages: up to 5 hours of battery life, support for various sensors, purportedly superior audio quality, and most important, easy connections. You’ll be able to pair a W1 device merely by placing it close to an iOS device. Once connected, settings are synced to an Apple Watch, if you have one, and over iCloud to any of your other Apple devices (although Apple didn’t mention the Apple TV). You can simultaneously connect to your iOS devices, Macs, and Apple Watches and, according to Apple, switch seamlessly between them.
The W1’s technology is based on Bluetooth, so you can use W1 headphones with unsupported devices, but you will have to pair them just as you would any other Bluetooth device.
Apple’s AirPods are the flagship W1 device. They have a futuristic look, reminiscent of the omnipresent headsets featured in the movie “Her,” and are similar to the existing EarPods, with elongated microphone stems that extend from your ears.
Like the EarPods, AirPods include a microphone — two microphones, actually. To activate Siri, double-tap either AirPod. Special sensors detect where your voice is coming from and focus the microphones appropriately. The AirPods also include optical sensors that detect when the AirPods enter or exit your ears — the AirPods pause audio when you remove them and you can configure them to play audio when you insert them. You can even use just one AirPod at a time if you wish, which is a good idea at times for safety reasons.
Because they’re so small and have so little room for batteries, a fully charged AirPod runs for only 5 hours, but Apple has a few special tricks to improve the situation. The AirPods come with a special charging case that can provide a 3-hour charge in just 15 minutes. Apple provided few details about the case but claims it extends AirPod battery life up to 24 hours. You charge the case itself via a Lightning connector.
TidBITS Security Editor Rich Mogull was on site at the Apple announcement and had a chance to try the new AirPods. He verified that they fit similarly to EarPods, so if you dislike that fit, don’t waste your money on the AirPods. However, Rich said that they’re overall more comfortable, because there’s no cable drag. Even so, he wasn’t sure that he would use them for running.
The AirPods and the W1 chip offer legitimate advantages over existing wireless technologies, but be aware of the additional platform lock-in, since these devices will require compatible Apple hardware for full functionality.
On Hacking During the U.S. Presidential Campaign
Technology has been front and center of this year’s presidential campaign, and not in a good way. We argued endlessly about Hillary Clinton’s implementation of email while she was Secretary of State, we learned about the hack of the Democratic National Committee and other Democratic campaign
organizations, and we were treated to the spectacle of a presidential nominee requesting a foreign government to release more stolen documents. Whether or not that request was sarcastic, it pretty much ensured that subsequent discussion would be devoid of technical detail in favor of campaign optics. I hope to rectify that situation somewhat.
I won’t address the issues with Clinton’s email server here for reasons of brevity, but also because the technical detail necessary to analyze the situation is not public. More information is available to evaluate the security considerations resulting from other hacks that have come to light.
The Three Circles of Computer Hackers — As a technology professional, I’ve been frustrated by the news focus on scandal versus actual security issues. Clinton’s email server is endlessly debated and will likely be a topic of discussion long after the election if she wins. Meanwhile, few people are even aware that the State Department’s email was definitely hacked, which certainly included far more email messages than were on her private server.
The Office of Personnel Management, the Internal Revenue Service, and potentially dozens of other government networks were also compromised, but these have been at best two-day stories in the mainstream press, followed by debate only in techie circles. When a hack has staying power in the mainstream media, such as the one suffered at the DNC, it’s because it feeds partisan debate, and the technical issues are ignored.
Before we get into the details of the hacks, it’s worthwhile to discuss who these hackers are. I classify them into one of three groups: script kiddies, lone hackers and criminal networks, and state actors.
- Script Kiddies: Most of the time, when you hear about a powerful hacker in the press, that person is actually a “script kiddie.” Once a security flaw is discovered, and a corresponding hacking tool is developed, said tool has commercial value in the more disreputable corners of the Internet. “Script kiddie” was coined to describe the hypothetical 12-year-old who, with little knowledge of actual hacking, downloads such a tool and unleashes it from their home computer.
This is not a new phenomenon — I had a friend in high school who was visited by the FBI in 1985 and politely asked not to touch any computers for a few years. What is new is that these people can easily congregate on the dark web, enabling a security vulnerability to go from recently-discovered to worldwide-attack-vector in hours.
Script kiddies use existing tools and known vulnerabilities; their target is the user who ignores security updates. (Don’t be that person.) As such, script kiddies are easily defended against. However, they’re also useful as political fodder when it’s in the interest of an agency to report they were attacked over 70,000 times. It’s not the quantity we should worry about, it’s the quality.
- Lone Hackers and Criminal Networks: The real concern to most people are the hackers who discover new vulnerabilities and the criminal networks that exploit those vulnerabilities.
It’s important to note that “hacking” itself is not a bad thing: it’s just a kind of computer forensics and programming. “Black hat” hackers are the bad guys; “white hat” hackers are hired by businesses and governments to protect you. Black hat hackers often crop up in places where highly skilled technical people tend to be underemployed. Thanks to the Internet, it’s trivial for these people to organize or be recruited by criminal organizations; when you hear about a hospital paying a $17,000 ransom to get its files back, that’s whom they’re paying.
Hackers are portrayed in movies as near-magicians, able to access just about any digital file on the planet. In reality, their abilities are much more limited but still pretty scary. The best defense against them, as with the script kiddies, is keeping up-to-date with security updates — you’re relying on the computer industry to learn about potential vulnerabilities before the bad guys do. The Internet and many computer resources were built during a much more trusting era, and have evolved into an astonishingly complex system. As a result, the whack-a-mole process of “find a vulnerability and patch it” is what we’ll have to live with for decades to come.
The Achilles heel of the black hat hackers and the criminal organizations that employ them is that they need to monetize their hacks: information, once discovered, has to be sold or exploited. This need provides an opportunity for law enforcement both to discover the hack and to trace its source. The best friend of these hackers is secrecy: corporations that cover up data breaches for fear of public embarrassment, technology companies that keep their source code secret (and unavailable for review by outside experts), and government agencies that don’t publicize attacks for fear of exposing their vulnerabilities.
-
State Actors: Here is where we really need to draw a distinction in hacking organizations. There are state-run hacking groups and everyone else. The technology that state-sponsored hackers have access to is secret, but we can guess several things. First, they have budgets larger than any available to all but the biggest criminal networks. Second, they have access to classified hardware and software that likely outstrips what’s available on the mass market. Third, when they find a vulnerability, they can sit on it for years, harvesting exposed information without publicity. And fourth, they can work with friendly companies and old-fashioned spies to build backdoors and other vulnerabilities into the technology
that’s sold to the public and to other governments.It’s that last reason that helps make the scariest techies on Earth not “Chinese hackers” or “Russian hackers,” but “American hackers.” It’s nearly certain that the most sophisticated and powerful cyberwarfare capabilities are those deployed by American agencies. Some of these technologies are defensive — as with anthrax, sometimes you need to possess a weapon in order to understand how to defend against it — but since a cyberweapon is covert in the way that a guided missile very much isn’t, it’s anyone’s guess just what the U.S. government is doing with its cyberwarfare capabilities.
We do know that other governments are doing their best to catch up. The Chinese and Russian governments have dominated the headlines when it comes to recent attacks on American entities, but any country with a significant military capacity has a cyberwar component running alongside it. As the dominant nation when it comes to building new consumer-level computer hardware and software, it’s likely we have an equivalent lead in covert military uses of similar technology.
The distinctions between these hacker types become important when you start asking the question of whether you personally are being targeted.
Script kiddies and individual hackers use scattershot methods to attack vast numbers of devices on the Internet; ergo, to stay safe, we should all employ basic security tools and practices (even if they’re just built into our hardware, software, and services).
You’re in more danger if you’re targeted by a capable black-hat hacker or criminal network; they might hit you with attacks designed to penetrate your organization’s defenses. Unless you’re a high-level employee in a major company or someone with access to confidential systems, it’s unlikely that you’d be targeted personally. However, individuals have been targeted for angering the wrong people, and hackers can be hired by a personal enemy. Most people are generally safe from personal attack, but there are exceptions.
If you’re the target of a state-run hacking organization, all bets are off: it’s impossible to know what tools state-sponsored hackers might use to penetrate your systems, but the story behind Apple’s recent iOS and Mac updates can give you an idea of what’s possible (see “iOS 9.3.5 Blocks Remote Jailbreak,” 25 August 2016). Governments may be interested in your activities for legitimate or political reasons; if so, constant vigilance on top of excellent security practices would be necessary.
Our Democracy Has Been Hacked — This brings us to the Russian attack on Democratic campaign organizations. That statement has already been politicized, as some people have tried to obfuscate who masterminded the attack.
Here’s the evidence pointing to the Russian government: the Romanian hacker who claimed credit for the hack doesn’t seem to be a native Romanian speaker; the series of events following the attack follows the pattern of Russian disinformation campaigns; and the signatures of the hack identified the perpetrators as two organizations known to work with and for the Russian government.
There are two ways in which this hack affects the election:
First, the last time foreign security agencies were interested, or actively involved, in influencing U.S. elections was when we were in an openly confrontational situation. Such activity is historically documented on both sides of the Cold War, but certain lines haven’t been publicly known to be crossed since. Yes, other countries have tried to support American domestic political movements in the hopes of generating a friendlier government (to them). But as far as we know, they’ve rarely tried to support or torpedo specific candidates; the last time the Russians tried (unsuccessfully), they were called “Soviets” and we were locked in the Cold War.
Second, it means that literally thousands of political entities are now potentially being targeted by foreign agencies with significant capabilities. Your reaction to hearing of an attack on a national Democratic organization may have been horror or schadenfreude depending on your voting plans, but consider who really runs politics in America: a number of nationwide organizations, a hundred statewide entities (and a hundred more during a presidential campaign), and literally thousands of county and city groups involved in local politics.
Most of these people are volunteers who likely have average technical skills. What these volunteers don’t have is access to computer security resources and training, unless they’re provided by the national political organizations. And to the extent that security advice has been provided, we can presume that it was done with an eye toward preventing hacks by political opponents, rather than sophisticated state agencies.
I’m not trying to describe a conspiracy to subvert all elections, but the dangerously close ones are vulnerable. If Clinton’s lead over Trump is substantial, it’s unlikely that foreign influence would be enough to tip the election. But if it were to get closer, things could change. Most of us remember an election 16 years ago that was decided by 537 votes in Florida. In a close election (or even just in close states), outside tampering with the political process could be a deciding factor. I live in Philadelphia; if the local Democratic organization’s computers were crashed here on Election Day, Clinton could have a substantial lead in Pennsylvania and still lose to Trump on a failed get-out-the-vote effort.
The Election Hack — Unfortunately, the attack on Democratic organizations isn’t even the most recent in the news. Voter registration systems in Illinois and Arizona were targeted and penetrated to varying extents. It’s important to note that it’s unknown (or at least, not public) who is behind these hacks; we can’t assume the Russians are also targeting our election systems. But somebody is.
The motive behind these hacks is also unclear. No registration data was changed in either case; in Illinois, 90,000 voter registration files were downloaded, so it could have been a matter of simple identity theft. Malware was installed on the Arizona server, but officials haven’t reported what it was attempting to do. It’s entirely possible that the intent of these hacks was purely criminal, not political.
That shouldn’t make us relax, however. These hacks show that our election systems are vulnerable, and future hacks may try to sway elections. Not to put too fine a point on it, but our political system is not designed to defend against such threats. Elections are run by the fifty states, and implemented by thousands of city and county election boards. You might think that most Americans have an interest in, say, the integrity of elections in Georgia, which has 2 senators and 16 electoral votes; the state of Georgia, though, thinks you should mind your own business.
Beyond that, we’re vulnerable because we have heavily politicized the debate over election integrity. Republicans routinely claim that voter fraud is rampant (despite evidence to the contrary), and Trump claims that fraud would be the only explanation were he to lose Pennsylvania. Democrats argue that this concern amounts to crocodile tears to provide political cover for disenfranchising groups who happen to vote Democratic.
I have my own opinions about which side is correct, but one thing is certain: the debate is so politicized that it was impossible to choose links that everyone would agree came from credible sources. I cited the Brennan Center because it’s the first result in Google (after signing out and anonymizing my browser); for all I know, a significant percentage of my readers might have been told that the Brennan Center is unreliable by news sources they trust.
It’s easy to be disappointed when your candidate isn’t doing well in the polls or has lost a given state. It’s a lot harder to give credence to claims of fraud and hacking attacks on elections when opening that can of worms might overturn a win by a candidate you support. For that reason, I expect post-election arguments about possible hacks to be driven entirely by partisan reaction, and to have nearly nothing to do with factual information. Even finding facts will be made more difficult amid the noise made by partisan bickering.
How the Thoughtful Voter Should React — Full disclosure: I’m a partisan Democrat. Like many of my political persuasion, I chortled mightily when I read about the impact of a failed computer system on the Romney campaign in 2012. But that was a self-inflicted wound. I would feel differently if that damage had been caused by outside agents, even if they were Democratic actors on “my side” attacking the system. I can’t support winning an election by corrupting it. I would feel even more strongly that way if the hacking were done by a foreign
government.
As a democracy, we need a reasonable expectation that our elections are, for the most part, the will of the populace.
And as with most threats to democracy, the best defense is a more informed voter. If you’re an American, you’re most likely a partisan or have partisan leanings; you’re more likely to respond positively to news that helps your candidate or harms their opponent, even when it involves foreign tampering. Resist that impulse. It’s appropriate only within the realm of partisan politics; it’s inappropriate and dangerous when we’re talking about attacks that transcend the political realm.
Part of this can be laid at the feet of the media that drives much of our political discussion. The national security threat of a known hack of State Department networks is orders of magnitude larger than that of a hack on the Secretary of State’s email server. A political debate driven by national security policy would give far more weight to the former. A political debate driven by scandal favors the latter.
This problem is driven by the fact that news organizations respond to the appetites of their audiences; the quality of political media is often no better than the quality of those appetites. It’s one thing for us to consume editorial and opinion pieces that agree with our political views; when we decide to filter reporting of national events with the same prejudices, we make it impossible to hold a rational debate with people who disagree with us.
My personal strategy is to deliberately expand my media diet with plenty of international sources, especially the BBC. Perhaps these sources have political bias when covering their own countries, but they’re unlikely to fall prey to American political influences. I avoid partisan news outlets on both sides not because I disagree with them, but because I find them non-credible sources, both for what they select as newsworthy and their actual coverage. I sometimes listen to Rachel Maddow, but that’s part of my entertainment diet in addition to my regular news diet, not in lieu of it.
Likewise, resist attempts by the media and political organizations to normalize hacked documents by citing them as unbiased sources. The National Republican Congressional Committee cited hacked documents from the DNC in a campaign ad in Florida; political newspaper The Hill ran with a story about DNC manipulation of primary races in Pennsylvania. (The Hill at least points out that the intentions of the leaker are “interesting” but then drops the topic for the rest of the story.) Both actions presume that using the documents in
question is legitimate; both also inherently assert that the documents are true and accurate. The former is up for debate; the latter is entirely uncertain. Hacks are done for a reason, public releases are done for a reason, and electronic documents can be modified easily; all of these should contribute to a healthy dose of skepticism when you’re evaluating such news. (This is not to suggest that the leaked DNC documents were falsified; the resignations of three DNC
officials thereafter implies they were basically sound. However, if I were going to design a disinformation campaign, I’d start with true documents and then follow up with false ones.)
If you’re involved in politics, it’s time to up your information security game; if you’re not involved but have technological chops, now is an excellent opportunity to make your skills known to community organizations who might need you. It’s too late this election cycle to walk into a campaign and volunteer to see their most valuable data, but anyone who gets involved in 2016 becomes a known resource in 2018 and later.
This is a nonpartisan prescription: we know that Democrat organizations have been targeted, but there’s no reason to think that Republican groups have better security. I can think of a dozen reasons why foreign governments would be just as interested in Republican data, so until further information is available, I’m assuming that it’s more accurate to say the Republicans “are not known to be hacked” than “were not hacked.”
As Jefferson (supposedly) said, vigilance is the price of liberty. He didn’t have computer networks in mind, but this is one of those times when it’s even more important than usual.
ExtraBITS for 12 September 2016
In ExtraBITS this week, Apple is having a spectacular one-day sale on iTunes Movies, Google Photos now works with Live Photos, Apple has tweaked the iPad lineup, and you can read a thorough explanation for why Apple removed the iPhone headphone jack.
September 12th Only: 10-Movie iTunes Bundles for $10 — To celebrate 10 years of iTunes Movies, Apple is offering six 10-movie bundles that you can buy for $10 each. The sale runs for just one day: 12 September 2016, so act fast. Even if a bundle contains only a few films that pique your interest, the price makes taking a chance on the rest worthwhile. (Thanks to Zac Cichy for alerting us to this sale.)
Google Photos Now Improves Live Photos — The Google Photos app for iOS can now apply effects to Apple’s proprietary Harry Potter-like Live Photos and export them as videos or animated GIFs that others can play on any platform. You can also use Google Photos to smooth out shaky video in Live Photos or to create cinematic pans. Other tweaks in the Google Photos app include better album sorting options and the capability to choose a new thumbnail for faces in the People album. Live Photos can be taken only with the iPhone 6s and 6s Plus, the iPhone SE, 9.7-inch iPad Pro, and with the soon-to-be-released
iPhone 7 models.
Apple Tweaks iPad Configs and Pricing — Even while focusing on the iPhone 7 and Apple Watch Series 2, Apple found time to tweak the iPad lineup’s configuration and pricing. The standard iPads — the iPad Air 2, iPad mini 4, and iPad mini 2 — just became better deals. Prices remain the same, but for each price point, Apple doubled the base storage. You can now buy the iPad Air 2 or iPad mini 4 with either 32 GB ($399 for Wi-Fi or $529 for Wi-Fi plus cellular) or 128 GB ($499/$629), and the iPad mini 2 in just a 32 GB configuration
($269/$399). On the iPad Pro front, the storage options are unchanged for both the 9.7-inch and 12.9-inch models, but the 128 GB configurations dropped in price by $50, and the 256 GB configurations are now $100 cheaper. Our question is if this minor adjustment will be the only change to the iPad lineup that we’ll see for the rest of the year, or if Apple has new models up its sleeve.
Why Apple Removed the iPhone Headphone Jack — Many people were angered by Apple removing the standard 3.5mm headphone jack from the iPhone 7, assuming that it was an intentional plan to increase wireless headphone sales for Apple subsidiary Beats. That fact may have played a role in the decision, but BuzzFeed’s John Paczkowski offers a thorough and compelling narrative behind Apple’s decision: the company just ran out of space for it.
“We’ve got this 50-year-old connector — just a hole filled with air — and it’s just sitting there taking up space, really valuable space,” said Dan Riccio, Apple’s senior vice president of hardware engineering. “It was holding us back from a number of things we wanted to put into the iPhone. It was fighting for space with camera technologies and processors and battery life.”
The camera systems in the iPhone 7 models are much larger than in previous models, and Apple engineers found that the easiest way to cram all the parts in was to remove the headphone jack. Removing it also helped with water resistance and allowed for larger batteries. Ultimately, it wasn’t Apple that killed the headphone jack, but simple math, and we’re willing to bet that most other smartphone manufacturers eventually follow suit.