#1499: Apple’s record Q1 2020 profit; Google Voice as protection from spearfishing; iOS 13.3.1, iPadOS 13.3.1, macOS 10.15.3, watchOS 6.1.2, and tvOS 13.3.1
Apple has posted record-setting financial results for Q1 2020, with nearly $92 billion in revenue and over $22 billion in profit, thanks to the resurgent iPhone 11 and its popular wearables. The company also updated all of its operating systems last week, releasing iOS 13.3.1, iPadOS 13.3.1, macOS 10.15.3 Catalina, watchOS 6.1.2, and tvOS 13.3.1—read on for details and our update advice. Last but not least, Apple consultant Ivan Drucker joins us to explain how to use Google Voice as the centerpiece of a two-factor authentication scheme that addresses some of the problems with two-factor authentication apps. Notable Mac app releases this week include Security Update 2020-001 (Mojave and High Sierra), Safari 13.0.5, DEVONthink 3.0.4, URL Manager Pro 5.0, and Fantastical 3.0.
In Apple’s Q1 2020, iPhone Rebounds and Wearables Soar
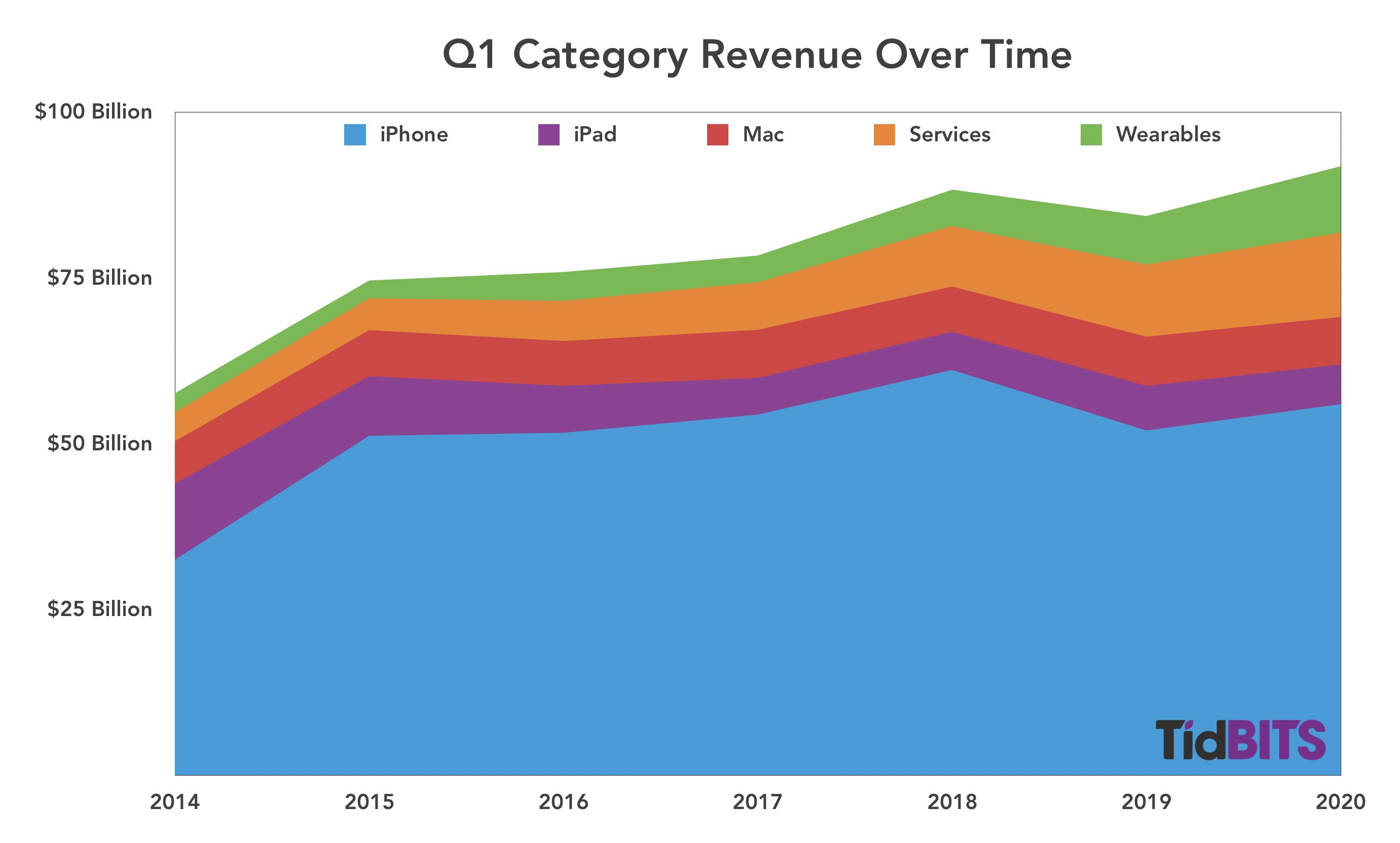
Reporting on its first-quarter 2020 financial results, Apple has announced net profits of $22.2 billion ($4.99 per diluted share) on revenues of $91.8 billion. The company’s gross revenues are up 9% compared to the year-ago quarter and net revenues are up by 11% (see Apple’s Q1 2019 Results: iPhone Bad, the Rest Good, 29 January 2019).
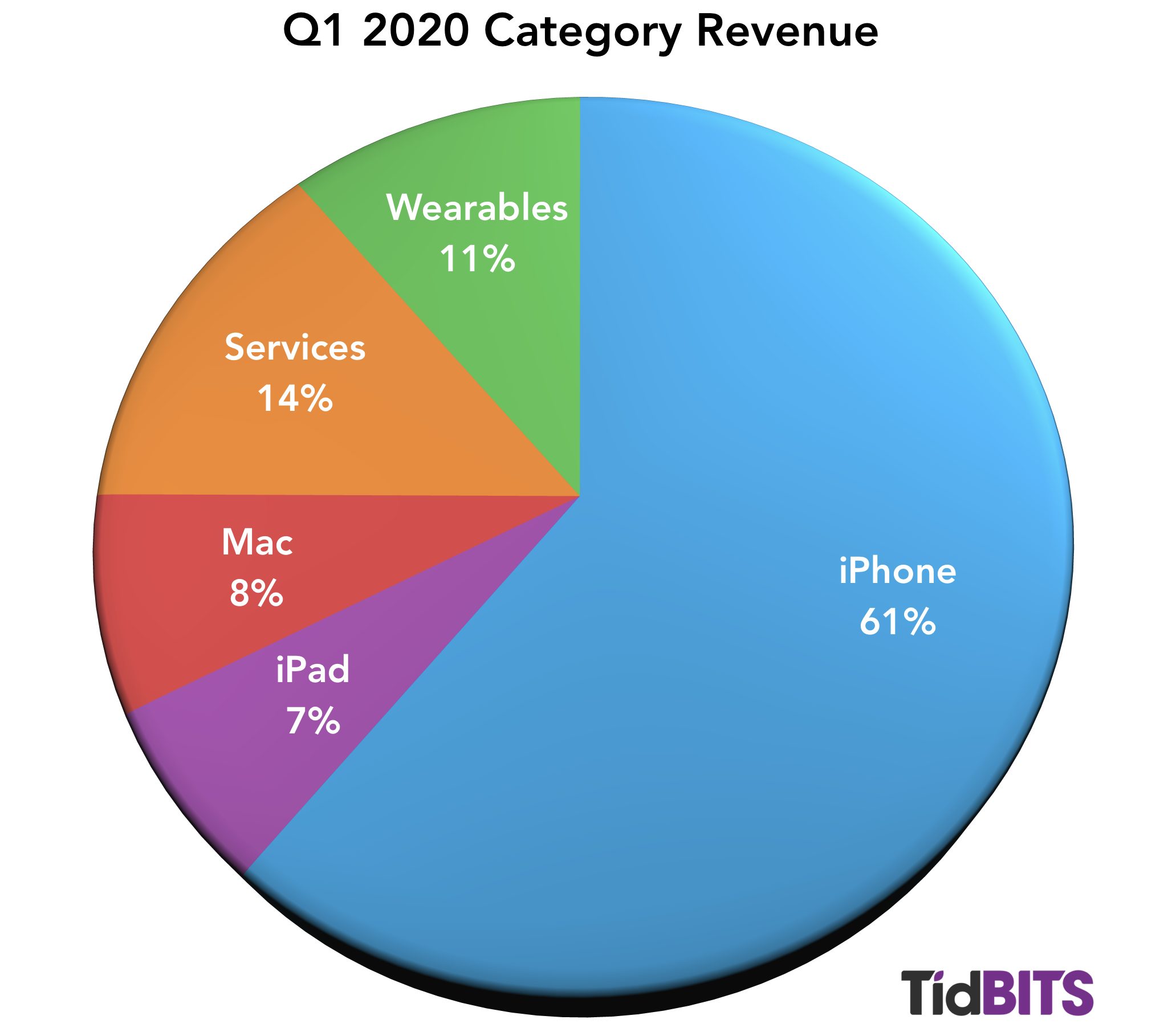
Although Apple’s overall results are very good—record-breaking, in fact—a look at the individual product categories reveals a more nuanced story, with income up for iPhone, Wearables, and Services, whereas both iPad and Mac sales were down in comparison to the year-ago quarter.
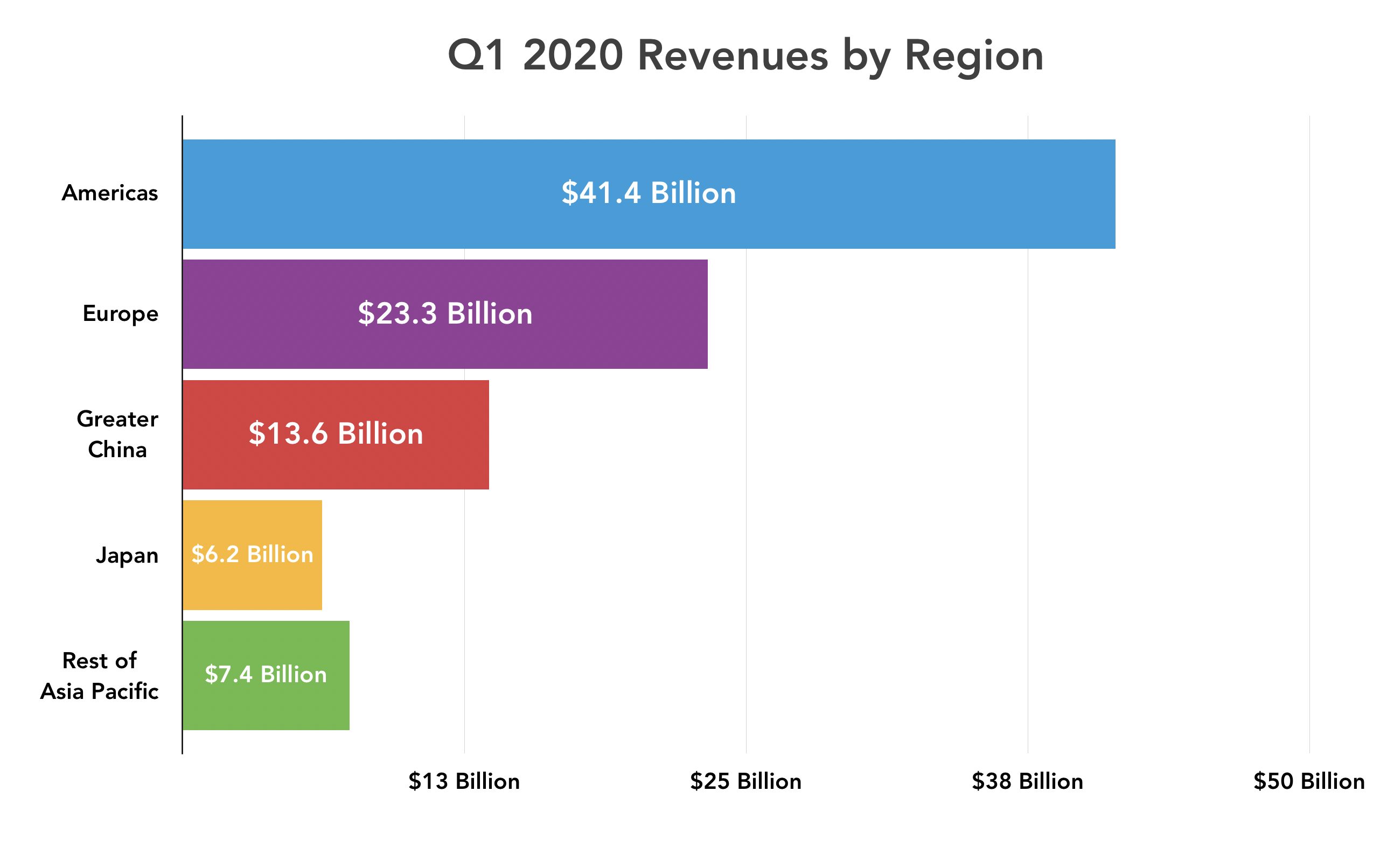
Apple saw double-digit sales growth in the Americas and Europe, but only modest gains of 6.5% in Asia Pacific and 3.1% in Greater China, as well as a 9.9% decline in Japan. However, the China revenue growth, though low, is a cause for optimism, as it reverses that geographic sector’s revenue declines in recent quarters. In Europe, Apple brought in $23.3 billion, and sales in the Americas hit $41.4 billion.
Apple faces a unique virus threat for the current quarter. Not a computer virus, but coronavirus, which was a topic in the quarterly investor call. CEO Tim Cook confirmed that Apple does have some suppliers in the Wuhan region, which is the epicenter of the outbreak, and that their facilities would be closed until at least 10 February 2020 at the recommendation of the Chinese government. Apple has closed all of its stores and offices in mainland China until 9 Feburary 2020. Apple has also halted all non-essential employee travel to China for now, and while the company is taking reasonable precautions, such as cleaning stores, it’s a factor ultimately beyond Apple’s control.
iPhone
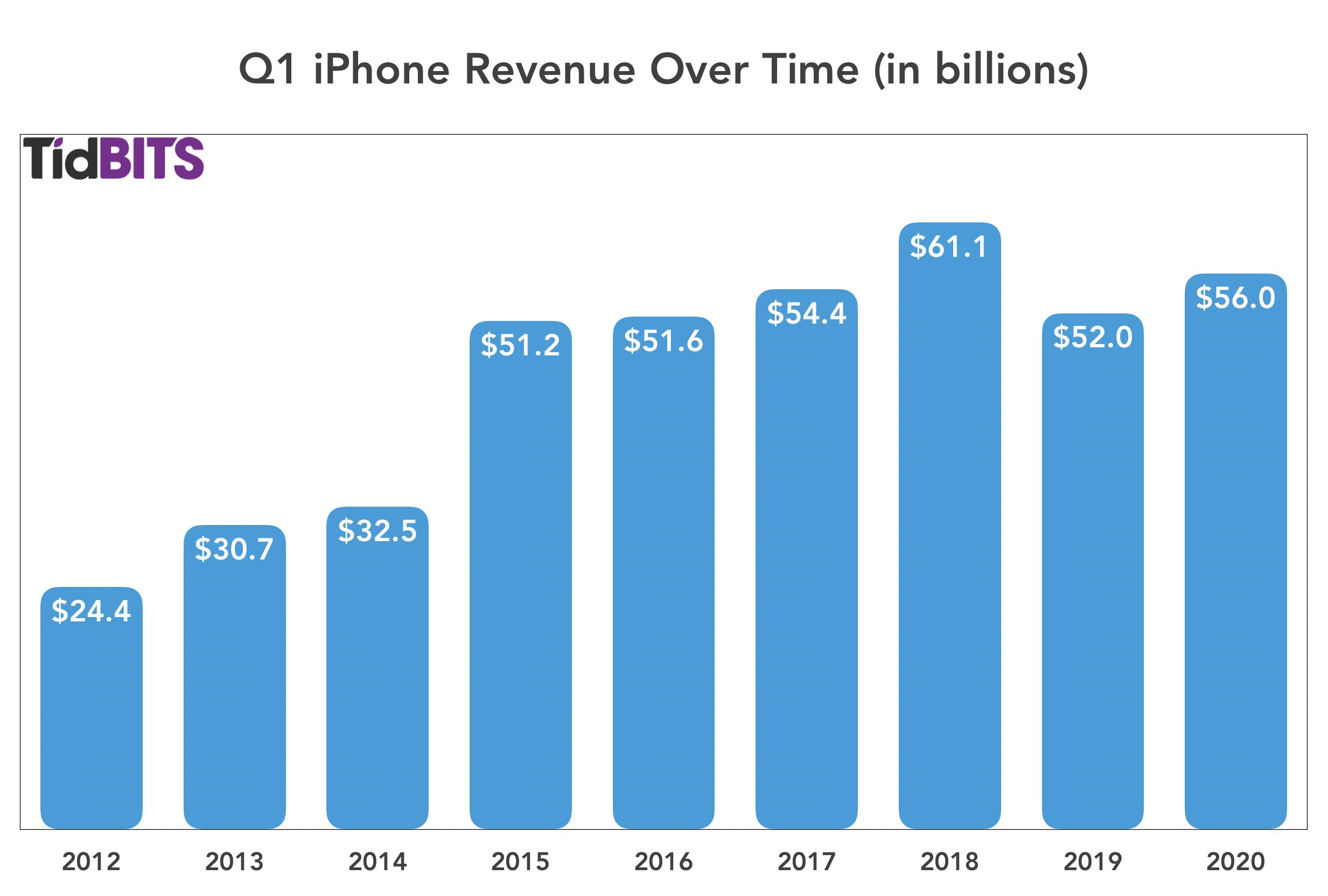
After a drop in Q1 2019, iPhone sales were up by 7.6% in Q1 2020, rebounding from $51.9 billion to $55.9 billion year over year. Cook said that the iPhone 11 was Apple’s top-selling model every week in the quarter. Cook credited the iPhone 11’s success in part due to the new payment plan available for Apple Card holders, showing the value of the credit card to Apple besides just interest and transaction fees.
iPad
The iPad had a disappointing quarter, with sales dropping from $6.73 billion in Q1 2019 to $5.98 billion in Q1 2010, a double-digit drop of 11.2%. Cook, however, called out iPad sales growth in emerging markets such as Mexico and India. CFO Luca Maestri said that the decline can largely be explained by the release of the iPad Pro during last year’s first fiscal quarter with no such release this year. That does make sense, given that Q1 2020 is otherwise in line with the first quarters of 2017 and 2018.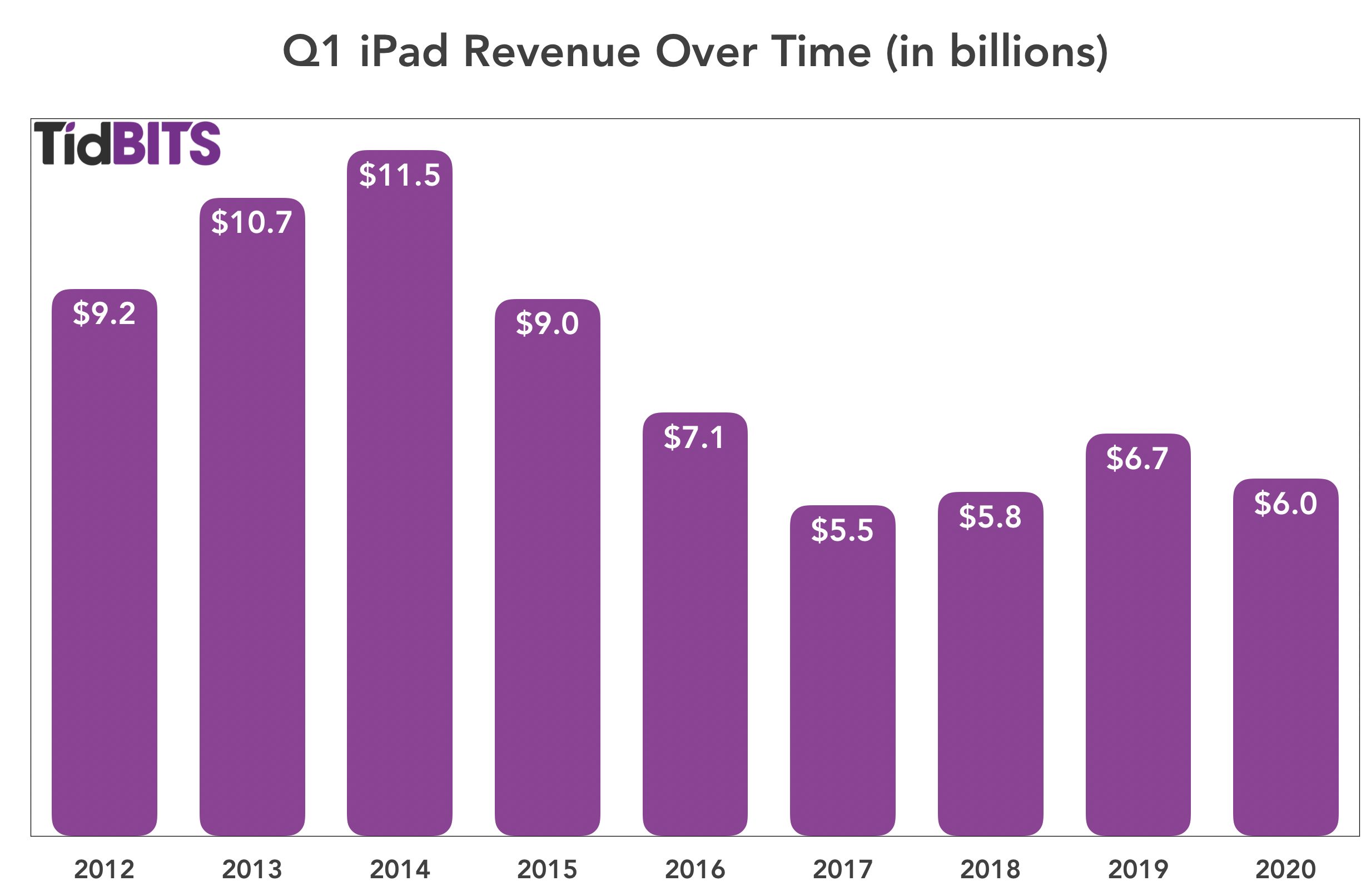
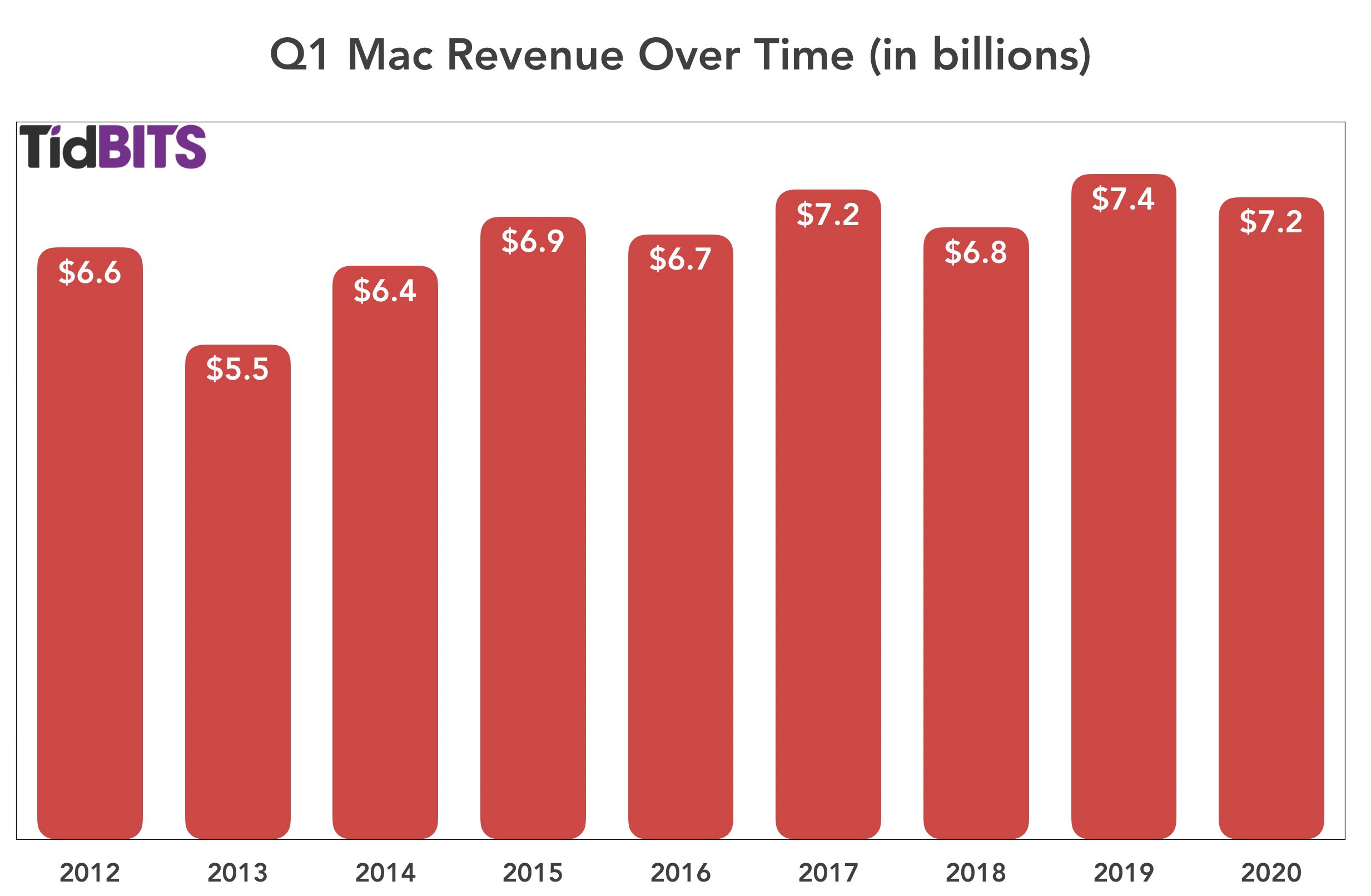
Mac
Mac sales were also somewhat disappointing, with a year-over-year decline of 3.5%. Apple sold $7.16 billion of Macs in Q1 2020, as opposed to $7.46 billion in Q1 2019. Although the Mac did see new models during the quarter, the release of the 16-inch MacBook Pro and the long-awaited Mac Pro may have come too late (or been too high-end) to make the kind of difference that last year’s release of the latest MacBook Air and refreshed Mac mini made.
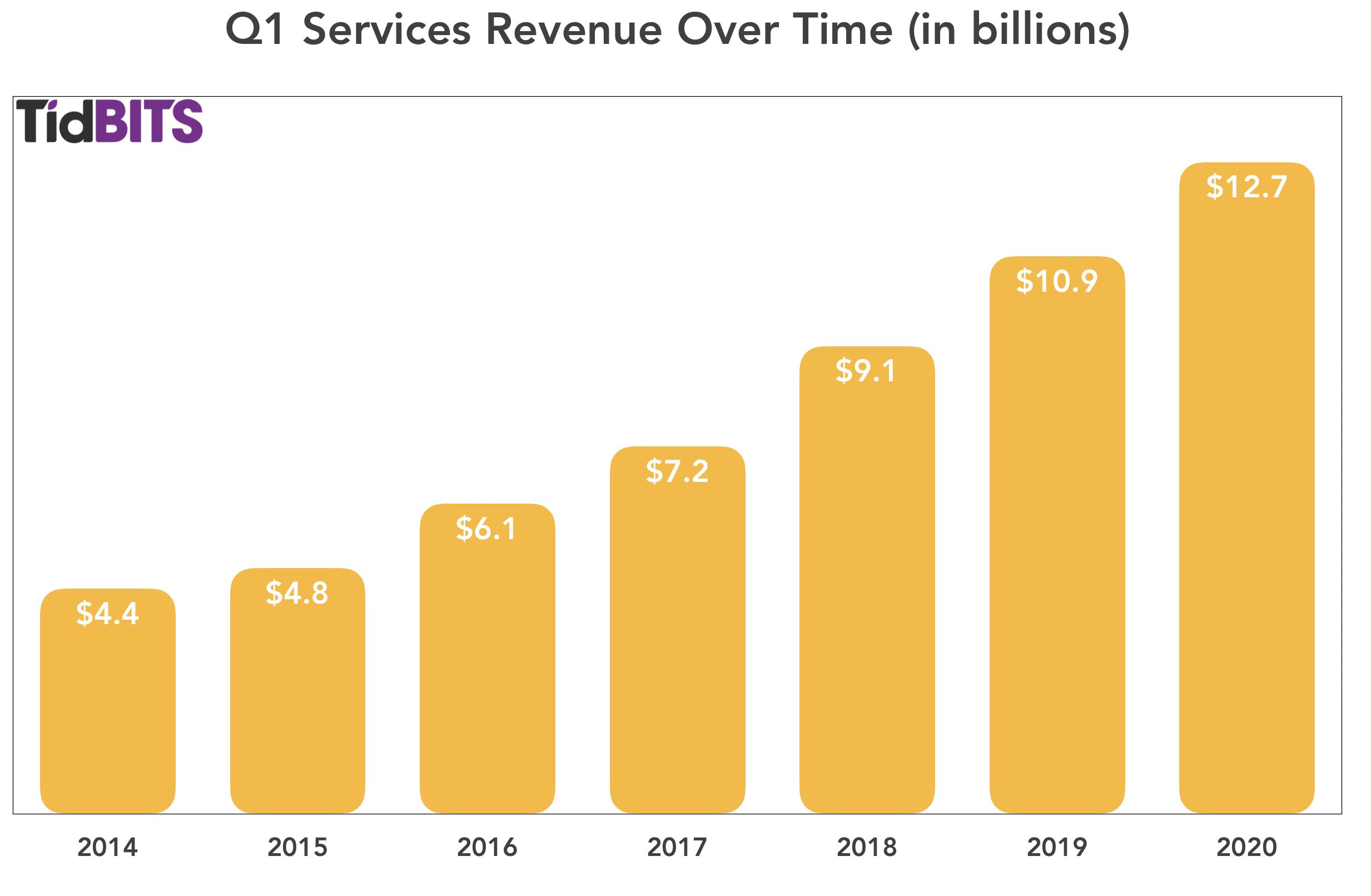
Services
As has been the recent trend, Services saw tremendous year-over-year growth, up 16.9%, from $10.9 billion in the year-ago quarter to $12.7 billion in Q1 2020. “Apple TV+ is off to a rousing start,” Cook said, although we have to assume that most Apple TV+ subscribers received it for free with the purchase of Apple hardware. Services achieved double-digit growth in all of its geographic sectors, and Maestri reported that Apple now has 480 million subscribers to the company’s paid service offerings. Apple expects that number to reach 600 million by the end of this calendar year.
Wearables
The Wearables category knocked it out of the park in Q1 2020 (Cook called it a “blowout quarter”), with an eye-watering 37% increase in revenue from last year, climbing from $7.31 billion in Q1 2019 to $10 billion last quarter. While Cook remains cagey with the real numbers, he said that the Apple Watch set an all-time revenue record in the quarter and that the Wearables category alone is now the size of a Fortune 150 company, largely thanks to the success of the AirPods. The AirPods revenues would have been even higher had the intense demand not created product shortages.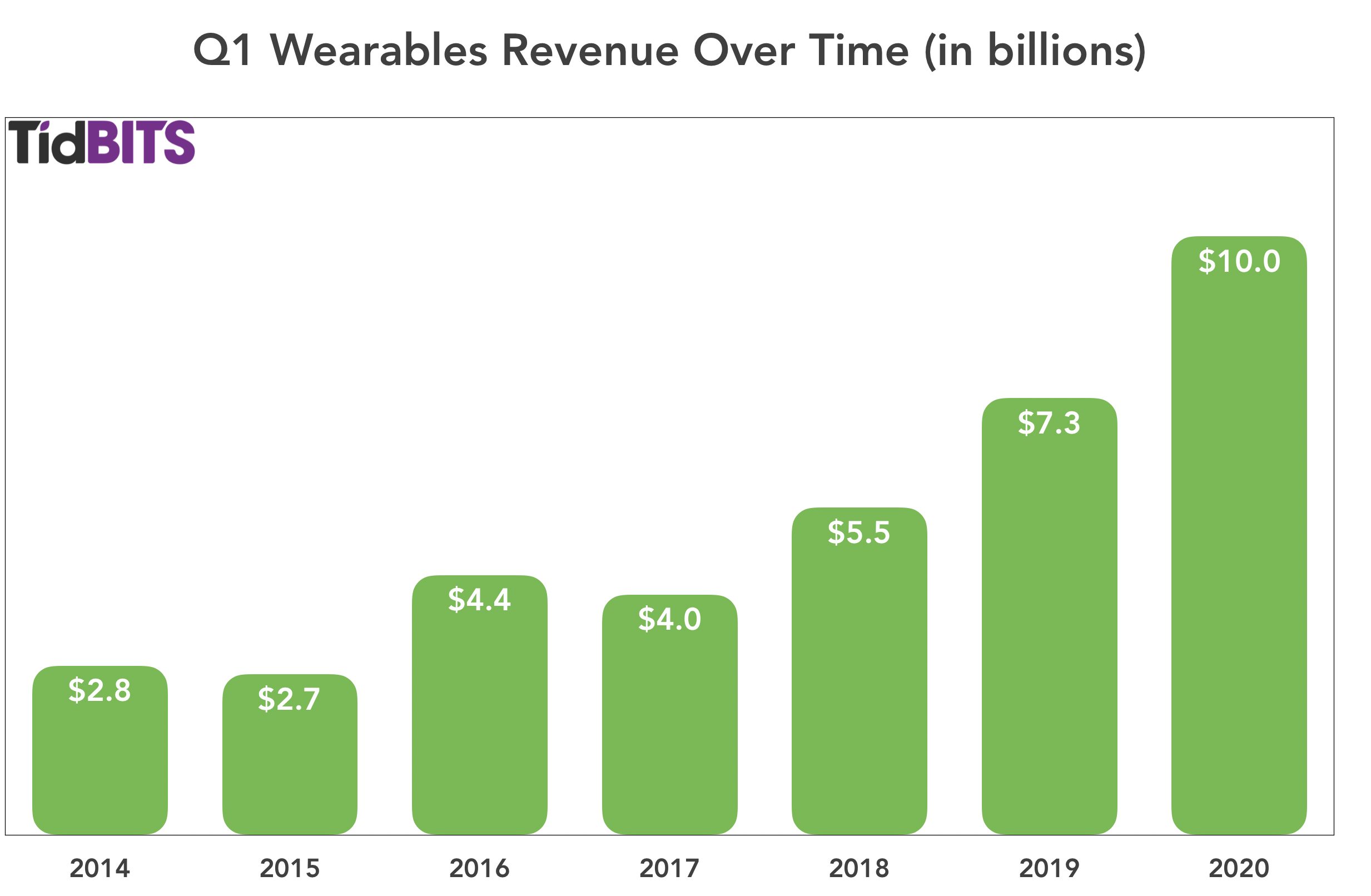
Overall
Apple’s revenues grow more complicated to track and forecast every year: for example, figuring out how Apple TV+ subscriptions contribute to overall Services revenue is complicated by the complimentary subscriptions Apple offers to new hardware buyers and by variable costs of producing Apple TV+ content—show business is like no business anyone knows!
In addition, Apple’s global supply chain and sales are always dependent on unexpected outside factors, such as the current coronavirus epidemic and political climate. Nonetheless, Apple looks to be on a roll, with its new products and services paying off and with more in the pipeline. You don’t need AR-enhanced glasses to see Apple’s near-term future as rosy.
Apple Releases iOS 13.3.1, iPadOS 13.3.1, macOS 10.15.3, watchOS 6.1.2, and tvOS 13.3.1
With its engineers back on the job after the end-of-year holiday, Apple has released updates for all its major operating systems, though without any particular theme. iOS 13 gains a new privacy setting, iOS and iPadOS receive a fix for an easily circumvented parental control, and macOS tweaks performance for recent Apple hardware. Once again, watchOS and tvOS don’t merit detailed release notes.
iOS 13.3.1 and iPadOS 13.3.1
iOS 13.3.1 and iPadOS 13.3.1 offer a grab bag of fixes and one privacy-related improvement. In general, we see no reason to delay upgrading for more than a week or so to make sure there aren’t unexpected problems lurking in the updated code.
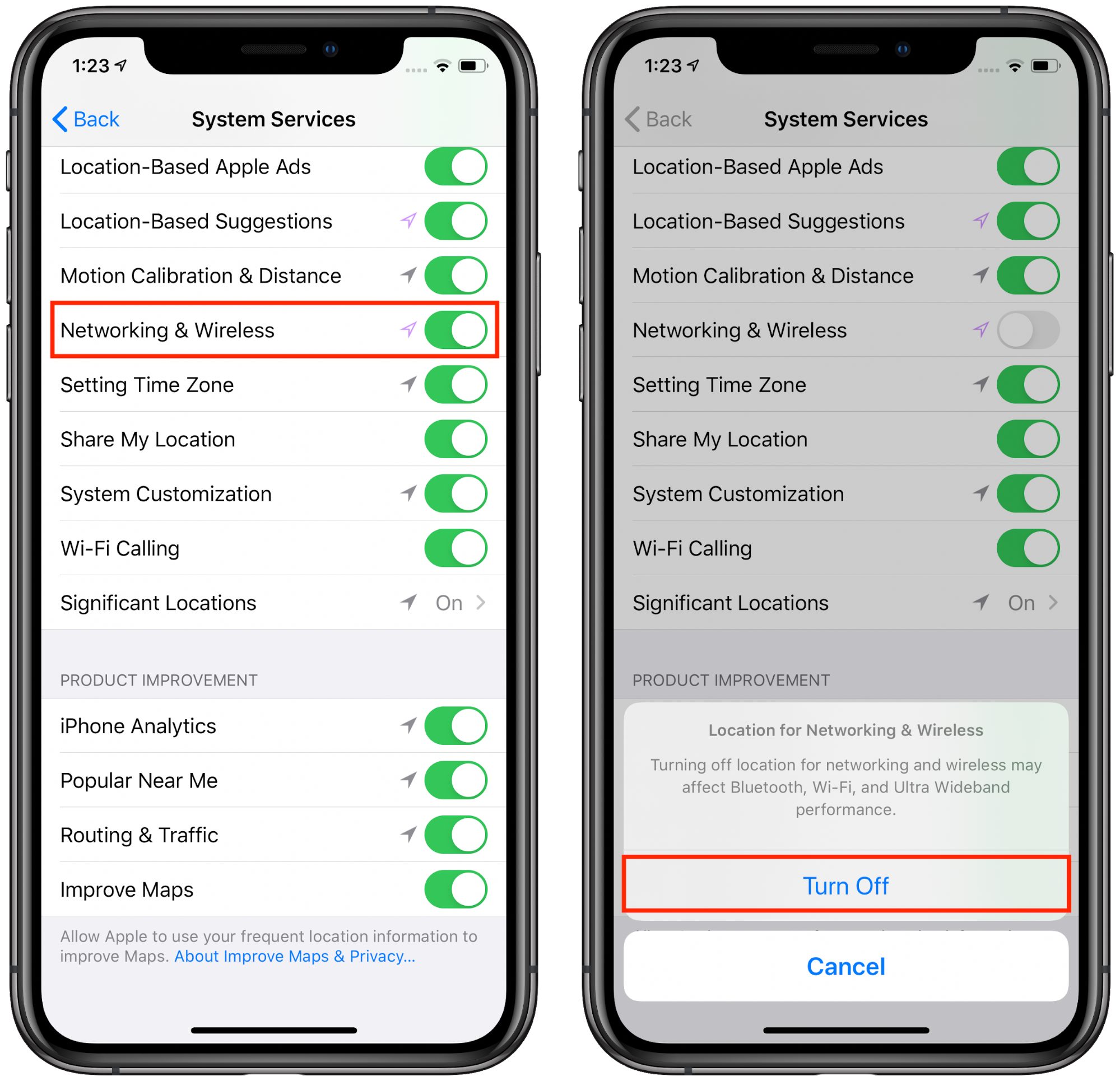
After privacy concerns surfaced about the ultra-wideband technology in the iPhone 11, Apple has added a feature to turn it off entirely in iOS 13.3.1. Just go to Settings > Privacy > Location Services > System Services and turn off Networking & Wireless.
Almost immediately after iOS 13.3 and iPadOS 13.3 introduced the long-delayed capability for parents to limit who their children can contact via calls, FaceTime, and iMessage (see “Apple Pushes Out iOS 13.3, iPadOS 13.3, iOS 13.3 for HomePod, macOS 10.15.2 Catalina, watchOS 6.1.1, and tvOS 13.3,” 10 December 2019), kids found a way around it. iOS 13.3.1 claims to fix that.
Other changes include:
- Both iOS 13.3.1 and iPadOS 13.3.1 resolve a mistake in Mail that could cause remote images to load even when the Load Remote Images setting is disabled.
- Both iOS and iPadOS fix a bug that could cause multiple undo dialogs to appear in Mail.
- Both operating systems address a bug that prevented push notifications from being delivered over Wi-Fi.
- iOS 13.3.1 eliminates a momentary delay before editing a Deep Fusion photo taken on an iPhone 11 or iPhone 11 Pro.
- iOS addresses an issue where FaceTime could use the rear-facing ultra-wide camera instead of the wide camera.
- iOS addresses a CarPlay bug that could cause distorted sound when making phone calls in certain vehicles.
Our Watchlist contributor, Agen Schmitz, tells us that iPadOS 13 on his iPad Air 2 ran slowly and stuttered frequently, but the iPadOS 13.3.1 update has restored its snappiness.
The iOS 13.3.1 update includes 21 security fixes.
You can install the iOS 13.3.1 update—278.8 MB on an iPhone 11 Pro—and the iPadOS 13.3.1 update—180.6 MB on a 10.5-inch iPad Pro—from Settings > General > Software Update, in the Finder in macOS 10.15 Catalina, or using iTunes in earlier versions of macOS.
For older devices that can’t upgrade to iOS 13, Apple also released iOS 12.4.5 with “important security updates” but did not publish any CVE entries.
iOS 13.3.1 for HomePod
The 117.3 MB iOS 13.3.1 update for HomePod introduces an Indian English Siri voice, along with general fixes.
You can change your HomePod Siri voice by opening the Home app, touching and holding the HomePod tile, tapping the gear icon in the lower-right corner, and then selecting Siri Voice.
To update the HomePod manually (it should update itself soon enough), open the Home app, touch and hold the HomePod’s tile, tap the gear icon to bring up HomePod settings, and then tap Install.
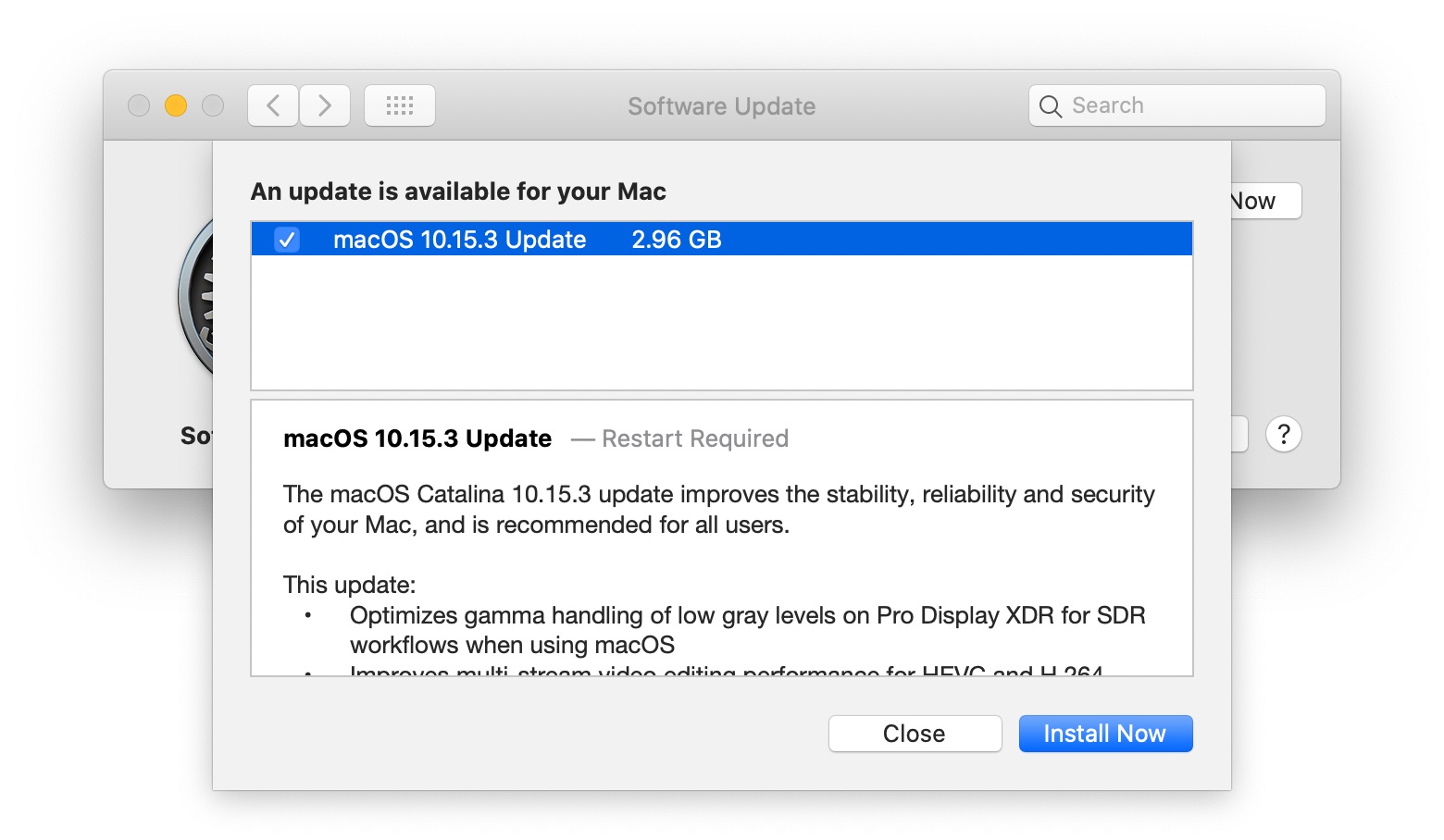
macOS 10.15.3 Catalina
The 2.96 GB macOS 10.15.3 Catalina update offers 27 security fixes and a pair of highly specific improvements for recently released Apple hardware:
- Optimizes gamma handling of low gray levels on Pro Display XDR for SDR workflows when using macOS
- Improves multi-stream video editing performance for HEVC and H.264-encoded 4K video on the 16-inch MacBook Pro
Apple made no mention of the Mail data loss bugs that we’ve been hearing about (see “Beware Mail Data Loss in Catalina,” 11 October 2019), but our own Michael Cohen reports that after installing the update, macOS informed him that it was updating his Mail database. Let us know if you experience any data loss problems with Mail in 10.15.3.
Michael Tsai, who has been tracking this issue, wrote:
There’s nothing about it in Apple’s release notes, but from what I’ve heard macOS 10.15.3 fixes the bug where large numbers of messages stored “On My Mac” could be deleted when updating to Catalina or rebuilding Mail’s database. It does not fix the bugs where moving messages between mailboxes (via drag and drop, rules, or AppleScript) can delete them, duplicate them, or simply not move them at all.
You can install the macOS 10.15.3 update from System Preferences > Software Update. If you’re editing video on a 16-inch MacBook Pro or using a Pro Display XDR, you probably should install it soon. Otherwise, assuming you’re already running Catalina, it’s worth waiting to install it for a few days to make sure the community doesn’t report new problems. For those who haven’t yet upgraded from Mojave, and especially for those who move messages in Mail frequently, there’s still no harm in sitting tight for now.
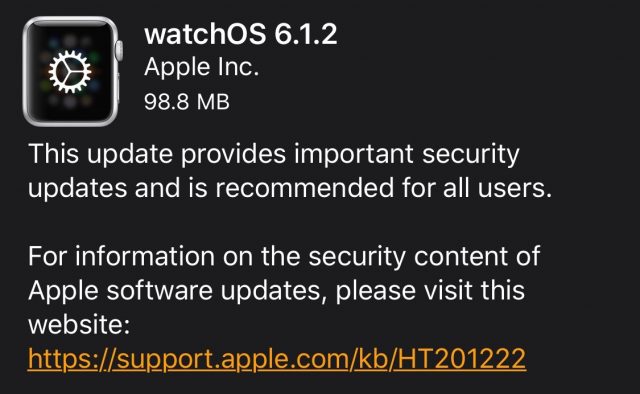
watchOS 6.1.2
The watchOS 6.1.2 update “provides important security updates and is recommended for all users.” You can install the update, which weighs in at 98.8 MB on an Apple Watch Series 4, from the iPhone’s Watch app: go to Watch > General > Software Update.
There’s no reason to avoid this update, but it’s hard to get excited about installing it quickly. Do it some night when your Apple Watch is charging anyway.
tvOS 13.3.1
As usual, the tvOS 13.3 update notes are sparse, promising only “general performance and stability improvements.” The update includes 13 security updates, largely shared with the other operating systems. If automatic updates aren’t on, you can update your Apple TV HD or Apple TV 4K by going to Settings > System > Software Updates. We just let ours update automatically when they get around to it. Let us know if you notice any changes.
Alternative Ways to Protect Yourself from Being Spearfished
If you, or people you know, have a public presence, high net worth, or something desirable to online thieves, conventional security best practices may not be sufficient. Increasingly, online thieves are targeting individuals directly via a technique called “spearfishing,” which relies on the shocking ease of stealing a cell phone number and then using it to reset passwords (see “SMS Text Message Login Codes Autofill in iOS 12 and Mojave, but Remain Insecure,” 4 October 2018). Authenticator apps are the generally accepted solution to this problem, but they can be problematic for a number of reasons, including being too difficult to use for non-technical users.
My partner Caroline Green and I co-own a Mac consulting firm in Manhattan. This year, we’ve seen two cases of spearfishing and heard of several others. In the cases we worked on, several critical accounts were stolen, such as email, domain hosting, and social media sites. While we were able to recover most of them eventually, there’s no guarantee that we could do so successfully in other situations. Further, the accounts were inaccessible for days, and reputation damage could have easily occurred via abuse of the accounts.
We worry that spearfishing will become more common as the tools and techniques of malicious actors become more sophisticated and widespread. The challenge for us as consultants and tech experts is to be able to offer our clients—especially those with high profiles or high net worth—comprehensive online security in a way that is easy for them to manage.
We came up with a technique that uses Google Voice text messages as an alternative to authenticator apps—although it requires a bit more setup, we think it’s easier to use and understand, plus it acknowledges some people have to allow trusted assistants or consultants access to their accounts. Our goal in sharing this technique is twofold. First, we hope that it might help other people looking for a similar solution, and second, we’re hoping outside scrutiny will reveal any potential weaknesses or vulnerabilities.
Where Are You Exposed?
First, let’s review some basics about keeping online accounts secure.
- Prioritize Your Accounts: Not every account, such as your average retail or content site, needs bulletproof security. But others do. These include your email account, Apple ID, Google account, Microsoft account, social media sites, financial sites, domain registrar, DNS host, Web host, Web site content management system, online business applications, cloud storage, cloud backup, and photo sharing sites. In short, you should put more effort into protecting any account that contains something you wouldn’t want to lose, wouldn’t want to be revealed to others, or wouldn’t want to misrepresent you if an attacker were to use it.
- Use Strong, Unique Passwords: We’ve all heard this advice, but it bears repeating. Do not try to memorize every password. Doing so means reusing the same passwords, or variants of a similar password. The risk is that if any one site suffers from a security breach, a depressingly regular occurrence, thieves now have access to all of your accounts. Every online account needs a unique, computer-generated password, remembered by a password manager, such as 1Password, Dashlane, LastPass, or at least the simpler ones built into current versions of Web browsers. I know only three of my passwords: the administrator password for logging into my Mac, my 1Password master password, and the password for my Apple ID. 1Password knows the rest.
- Use Two-Factor Authentication: Two-factor authentication (2FA) is when you enter your password and then get a separate code or prompt, via text message, onscreen dialog, or authentication app, to verify that it’s really you, and not just someone who knows your password. Most Apple users see this when signing in with their Apple ID on a new device. You should enable 2FA for any important site that supports it. There are several flavors of 2FA that I’ll discuss more below.
- Provide Fake Answers to Security Questions: In general, if you have 2FA enabled, you shouldn’t have or need security questions. But some sites require them, and in those cases, operate under the assumption that there are unseen, nefarious databases about all of us that correlate all kinds of information we might assume to be separate and private (the best-known are called “Facebook” and “Google”). Imagine that anyone can learn everything about you with a few quick searches. One way to thwart attackers from hacking your security questions is to make up nonsense answers—different for every site, of course—and keep them in the notes area of your password manager. What was the name of your first pet? “Macatma Gandhi.” What’s your birthdate? Pick a random date like “1/9/1919.”.
- Think You’re Important: It’s normal to think that good security is for other people because you’re too insignificant to warrant a thief’s attention. Alas, it’s 2020, and we’re all a lot more visible and important than we may believe we are. The phone number theft I’m about to tell you about was motivated simply because its owner also held a two-letter Instagram name—highly valuable on the Dark Web black market, as it turned out.
Your Cell Phone Number Is the Weak Link
Even if you do all of the above, you may not be safe. One of the two account thefts we saw involved a sophisticated attack in which the victim—who used strong passwords and a password manager—had thieves port his cell phone number from his SIM card to theirs. Once they had a phone with his phone number, it was trivial to gain access to his accounts by requesting password resets, since the confirmation codes were sent by text message.
You’re probably wondering how this could have happened. The thief used social engineering to persuade someone at the victim’s cellular provider to transfer the number. Lest you think that’s an unlikely scenario, consider it from this angle: anyone from anywhere in the world can call your carrier’s customer service, and every single employee who answers the phone has the capability of putting your number on another SIM card! That’s a lot of exposure. Most carriers offer a transfer lock, passcode, or PIN that they’ll require before porting a number.
I called my carrier and activated a PIN, and I keep it in my password manager. I strongly advise that you do the same—here are informational links for AT&T, Sprint, T-Mobile, and Verizon. However, I don’t want to rely solely on a carrier transfer lock. I don’t know how well they are implemented, and I assume that some thieves are really good at what they do and may be able to talk their way around it.
The Problem With Authenticator Apps
Security experts usually recommend that, rather than receiving a text message for two-factor authentication, you instead use an authentication app, such as Authy (see “Authy Protects Your Two-Factor Authentication Tokens,” 6 November 2014), Google Authenticator, or Duo Mobile. The app provides, on its own, a code that changes every 30 seconds. Some password managers, such as 1Password, can operate as an authenticator app as well. We agree that authenticator apps are a very secure method of getting a 2FA code.
The problem that we’ve found with standalone authenticator apps is that they’re not especially well designed. Our clients have difficulty setting up new accounts in them, and the apps are difficult to use even once set up. They’re serviceable for you and me, but I’m thinking about people who don’t read TidBITS. Even people who are already using a password manager that has authenticator app capabilities would have to scan QR codes and absorb concepts like “time-based one-time password” in order to set up 2FA.
Furthermore, for people like you and me, standalone authenticator apps have liabilities:
- If an assistant, colleague, or consultant needs to access an account, both people have to configure the authenticator app for the account at the same moment, with the same seed.
- Sometimes the account name shown within the app is obscured, causing confusion if the user has multiple accounts at the same site.
- Support for authenticator apps on a desktop computer may be limited, hard to use, or nonexistent.
- There is some risk of losing the 2FA codes after a device switch (we’ve seen this with Google Authenticator).
- The user isn’t told exactly what to do during login—they need to remember to look at the correct authenticator app and find the single correct code from among the many listed.
- Many sites don’t support authenticator apps at all and instead require that you be able to receive an SMS text message for 2FA.
1Password (and perhaps other password managers) elegantly addresses many of these concerns, such as by putting the security code on the clipboard during autofill, and notifying that it has done so. But building 2FA support into a password manager is not without its own issues:
- Having both the password and the one-time code in the same app creates a risk of being permanently locked out of accounts if you lose access to the password manager due to a lost master password or data corruption.
- Similarly, if there were some sort of breach of your password manager, a thief would have easy access to all accounts, despite 2FA being enabled.
- Giving a colleague or other trusted party access to an account still requires either simultaneous setup, or a more expensive “Teams” plan that adds complexity by having a secondary shared vault.
- Again, many sites don’t support 2FA via authenticator apps, instead requiring that you receive an SMS text message.
We went looking for another solution.
Google Voice as an Alternative to Authenticator Apps and Cell Phone Numbers
Google Voice is a free service that gives you a phone number suitable for both calls and text messages. You can access it via the Google Voice iOS app or a Web browser, and both can provide notifications.
The Google Voice service is attractive because it solves a lot of the problems we discussed with real cell phone numbers and authenticator apps:
- The phone number can’t be ported without login access to the associated Google account—there’s no one to fall prey to social engineering.
- Text messages are easily accessed from any browser or phone, making it easy for an assistant, colleague, or consultant to receive a code.
- Users get a notification on their phone as they would with any text message, so there’s no change in user experience.
- It’s easy for our clients to set it up for new accounts—all they have to do is provide an alternative phone number, rather than fuss with an authenticator app and a QR code.
Our approach is to create a new Gmail account—with no real, identifying information in the email address, first name, last name, or birth date fields—to host this Google Voice number. Then we add the Google Voice app to the user’s iPhone (and iPad if necessary) and sign them in. Because the account email address in no way identifies them and is used for nothing other than hosting the Google Voice number, a thief should never come across it. And, even if one did, they wouldn’t know to whom it belongs. (If you do try this Google Voice approach, be sure to remove your real cell phone number from your account, which is added by default during setup. If you don’t, an attacker stealing your cell phone number would still get the Google Voice text message codes. Also disable the default forwarding of text messages to your email address.)
With a strong password, the Google Voice account is secure. What if those credentials were lost? This may be overkill, but for account recovery of the Google Voice account, should it be needed, we use another non-identifying email alias associated with the user’s iCloud address. The actual, non-identifying iCloud account behind the alias can either be checked directly or forwarded to our client’s actual email. So, if a thief were to discover the recovery address for the Google Voice account, they couldn’t log into anything with it. We also record the account creation date and fake birthday, as Google may ask for them during account recovery.
By using the Google Voice phone number, our clients can easily set up two-factor authentication on any account simply by using an alternate phone number. When a code is needed, they are actively notified via text message notification. An assistant, colleague, or consultant can access the code as well. And the alternate phone number can’t be moved to a thief’s SIM card without login access to the Google Voice account.
Downsides to Google Voice for Two-Factor Authentication
The most significant disadvantage that we can see to this Google Voice approach is that if you don’t send a text message or make a phone call every six months or so, the number expires. Google warns you about this, of course, but it is best to be proactive, as we are for our clients. It’s a good idea to forward all mail sent to the Google Voice account’s Gmail address to an actively checked account, so that any warnings sent by Google are seen. It would also be smart to set a biannual reminder on a calendar as well.
Some Web sites may reject a Google Voice number or may not accept text messaging as a primary means of 2FA. I have seen this in a handful of cases. For example, Facebook will not accept a Google Voice number unless it is the first number you add to the account. CrashPlan supports authenticator apps, but not SMS. For these kinds of accounts, you would need to make a strategic decision whether to use an authenticator app (or a password manager that acts as one), enter the real cell phone number, or do without 2FA. Also, some prominent Web sites don’t support 2FA at all (I’m looking at you, Spotify).
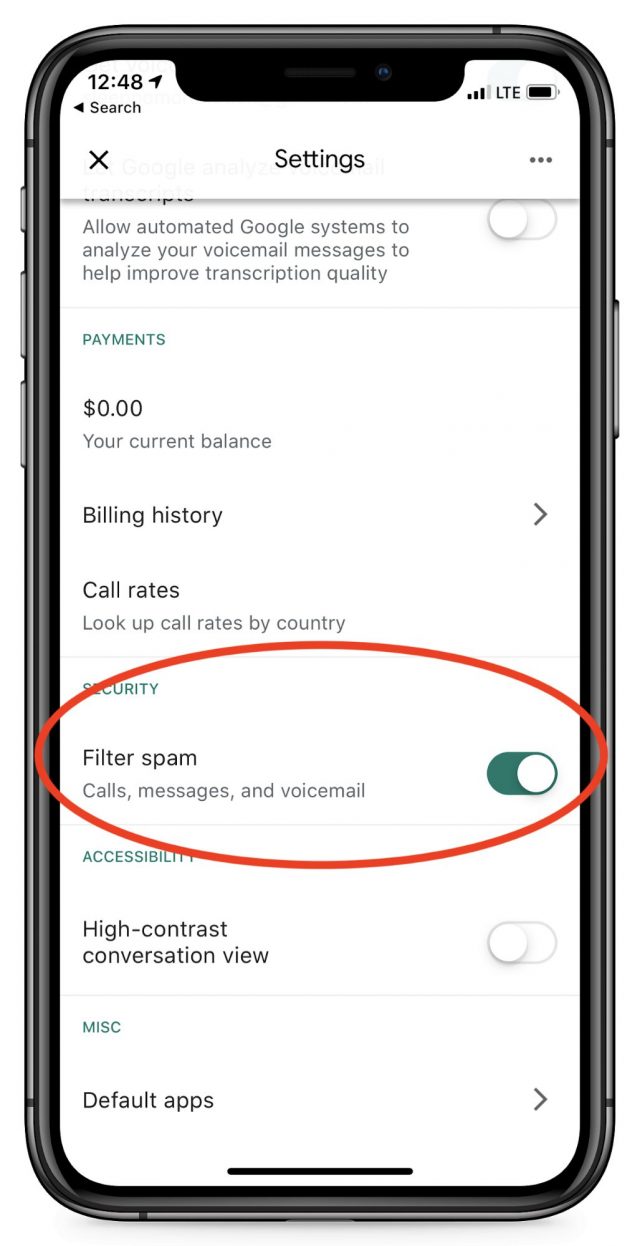 Adam Engst suggested another possible downside, which is the possibility of the Google Voice number receiving spam calls. We need to advise our clients to ignore all calls and voicemails in the Google Voice app. Better still, in the Settings area of the app, you can disable incoming calls, as well as filter possible spam, although this creates the risk of missing an important code if Google misidentifies it.
Adam Engst suggested another possible downside, which is the possibility of the Google Voice number receiving spam calls. We need to advise our clients to ignore all calls and voicemails in the Google Voice app. Better still, in the Settings area of the app, you can disable incoming calls, as well as filter possible spam, although this creates the risk of missing an important code if Google misidentifies it.
Finally, Google Voice is one of Google’s more peripheral products, so who knows if the company might drop it one day. Nonetheless, Google would likely provide sufficient warning for users to make alternate plans.
What Do You Think?
I’m not a professional security expert, but this system seems like it strikes the right balance between being safe enough and usable enough for our clients with high profiles or high net worth, or for those with an extra level of security consciousness. Do you see any glaring flaws or risks? Let us know in the comments.
Ivan Drucker is the founder and CEO of IvanExpert Mac Support in New York City. He is a former software quality engineer for Apple and began using his first Apple II in 1978, at the age of eight.



 Agen Schmitz
9
comments
Agen Schmitz
9
comments