#1524: ScanSnap Manager for Catalina, Camo turns an iPhone into a webcam, Apple Security Researcher Device, Micro Snitch warns of webcam/mic spying
This week’s surprise news is that—a year after Fujitsu announced it wouldn’t support older ScanSnap scanners in Catalina—the company has reversed course and released ScanSnap Manager V7 for macOS 10.15 Catalina. The rest of our issue revolves around security and webcams. First, on the security front, Apple has started a program that gives specially modified iPhones to security researchers to aid in their investigations. More immediately useful for those concerned about webcam spying is Micro Snitch, a utility that warns you when apps activate your Mac’s webcam or microphone. And if you’ve been unable to get a better webcam for your Mac, Glenn Fleishman provides a look at Camo, a system that lets you press your iPhone into service as a Mac webcam. Notable Mac app releases this week include Fantastical 3.1.2 and Carbon Copy Cloner 5.1.20.
Feeling Paranoid? Micro Snitch Tells You If Your Mac Is Spying on You
Our reporting on Apple’s warning against closing a MacBook with a webcam cover installed (see “Don’t Close Your MacBook with a Webcam Cover Attached,” 14 July 2020) sparked an interesting TidBITS Talk discussion about Mac webcam security.
In theory, malware can’t activate your Mac’s webcam without your knowledge, because the indicator light is wired in series to the webcam. That means the webcam cannot receive power without turning on the light. An earlier webcam implementation in pre-2008 Apple laptops was vulnerable to a firmware exploit, but a lengthy treatise by John Gruber of Daring Fireball quotes an unnamed Apple engineer as saying that this exploit is now impossible, because the connection is direct. No malware can bypass basic electrical connections.
Nothing’s Perfect
Or so we think. The problem with any sort of “unbreakable” security scheme is that there are a lot of bad guys out there, and security breaches have real monetary value to organized crime and government surveillance agencies. One TidBITS Talk reader pointed out that a clever attacker could use the webcam to take quick still images, flashing the indicator light so quickly that you might not even notice it.
Even if Apple’s webcam security is foolproof, what about third-party webcams? Built-in Mac webcams aren’t very high-quality (see “The 2020 MacBook Air’s FaceTime HD Camera Is Still Lousy,” 8 April 2020), so many people who rely on videoconferencing (a number that has skyrocketed during the COVID-19 pandemic) have a third-party camera attached.
The reality is that you probably don’t have much to fear from your webcam, because even years ago it would have taken a targeted attack to access it. But there’s something about having an electronic eye pointed at you all day long that can make you feel like you’re being watched…
Micro Snitch to the Rescue
If you’d like a little extra peace of mind, consider installing Micro Snitch from Objective Development, makers of LaunchBar and the famous Little Snitch network monitoring utility. Micro Snitch costs $3.99 either directly from Objective Development or in the Mac App Store, and Objective Development makes a free trial available.
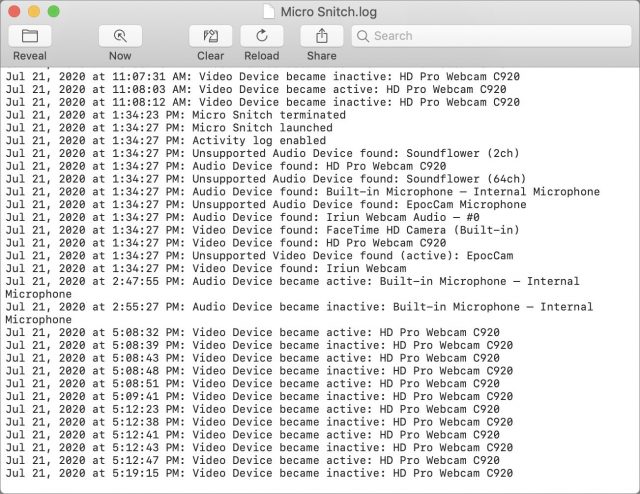
Micro Snitch lives in your Mac’s menu bar. Whenever an app accesses your webcam or microphone, a large, square icon of a hat and glasses appears in the center of your screen and then moves to the lower-right corner. You also receive a notification. The hat and glasses icon doesn’t go away until you close it or the activity stops.
Afraid that you somehow missed the little spy guy? Choose Open Activity Log from Micro Snitch’s menu bar icon to see a log of every time either the camera or the microphone has been accessed.
The only downside I can find is that Micro Snitch can’t monitor some of the odd software devices I have installed, like Soundflower (which lets me reroute audio on my Mac) and the EpocCam driver that promised to let me use my iPhone as a webcam—I was planning a review, but recent security changes to Zoom and Skype prevented it from working. I recommend being careful about installing such drivers, and I’ve now uninstalled EpocCam. Soundflower, on the other hand, is now open source.
If your webcam causes you any anxiety, $3.99 for Micro Snitch is a small investment for additional peace of mind. Give it a try, and let us know if it reveals any unexpected behavior on your Mac!
Surprise! Fujitsu Releases 64-Bit ScanSnap Manager for Older Scanners
Many of you have been following our coverage of Fujitsu’s decision to effectively drop support for some of its older but still popular ScanSnap scanners by not updating the ScanSnap Manager software to 64-bit so it could run in macOS 10.15 Catalina. To keep those scanners off the trash heap, we evaluated and reported on some third-party solutions that will keep them running under Catalina, including VueScan (see “VueScan: Not the ScanSnap Replacement You’re Looking For,” 2 December 2019) and ExactScan (see “ExactScan Might Be the ScanSnap Replacement You Need,” 6 May 2020). Neither was perfect, but they got the job done.
A Stunning Announcement
A few weeks back, TidBITS reader Stephen Miller shared the shocking observation that Fujitsu had updated ScanSnap Manager to V7, with the company saying “We’ll soon be making ScanSnap Manager available for the new iX1500, as well as for earlier models.”
A quick check of the specifications in Fujitsu’s announcement showed that ScanSnap Manager V7 works in macOS 10.12.4 Sierra and later, including Catalina, and the “earlier models” include the S1500, S1500M, and the S1300 that I’ve been using for many years.
ScanSnap Manager V7 Test Drive
Still in a state of shock, I went to the ScanSnap Manager V7 download page and fetched a copy for my S1300 to see if it really did work under Catalina in the same way it did in prior macOS versions.
Amazingly, it does work. And it’s almost indistinguishable from its previous 32-bit incarnation. But let me share a few observations:
- ScanSnap Manager V7 remembered only two of my profiles, and reset their destination folders back to Pictures. I set the folder and changed the application to None (Scan to File), and it’s back to working as expected. Why it forgot the destination folders and remembered only two of the eight profiles I defined is a mystery.
- Scan to Photos worked instantly, as expected, as did Scan to Email and Scan to Print.
- The pretty icons in the Dock pop-up menu for profile selection that were present in the 32-bit app are gone, so now you have a plainer look.

ScanSnap Manager Dock pop-up menu in Mojave (left) and Catalina (right)
On the download page, Fujitsu added a comment about a few features in the 6.x (32-bit) versions that are not yet in the V7 (64-bit) version:
Cloud linkage (*1), ScanSnap Page Merger, or [sic] Searchable PDF Converter, which are available with ScanSnap Manager V6.3 or earlier, are not available with ScanSnap Manager V7.0L20 for Mac. (They will be available in a later update.)
(*1) Cloud linkage functions: Scan to Dropbox, Scan to Evernote (Document), Scan to Evernote (Note), Scan to Google Drive, Scan to Salesforce Chatter, Scan to SugarSync
I’m not sure what the Searchable PDF Converter is, but it must not be the essential Convert to Searchable PDF feature that still has a checkbox in V7. I tested the latter just now in V7 and confirmed that Spotlight finds the document by searching for some of its content.
Although I haven’t done a comprehensive analysis, my takeaway is that all my key workflows still work, and all the features I remember seeing in ScanSnap Manager still appear to be there. It seems too good to be true, but it is.
Why Did Fujitsu Change Its Mind?
To me, this is the big question. Fujitsu announced it wouldn’t support Catalina well over a year ago, and many ScanSnap owners have already gone through the Five Stages of Grief and resolved to buy either a new scanner or one of the third-party software solutions I previously mentioned. In all likelihood, many have already done so.
One possible explanation is that the series of TidBITS articles on this topic and those from elsewhere on the Web may have resulted in enough negative press to get Fujitsu’s attention.
But another factor may have weighed more heavily in the decision. Lots of people have been complaining about ScanSnap Home, the 64-bit software that replaced ScanSnap Manager. Complaints center around its lack of features in comparison to the older ScanSnap Manager. Fujitsu has been saying that it would gradually update ScanSnap Home with the features that people missed from ScanSnap Manager. Perhaps that effort was later determined to be greater than just porting ScanSnap Manager to 64-bit.
I contacted Fujitsu to ask why the company made this move, and I received the following explanation (which I reproduce faithfully, errors and all):
Dear Valued Customer,
Thank you for contacting Fujitsu. The newly release ScanSnap Manager software was released for those customer who upgraded to the new iX1500 as well as customers who did not want to use ScanSnap Home but rather wanted use ScanSnap Manager again for scanning. We do not guarantee previous model scanners will work with the newly release ScanSnap Manager as well as there is no support for scanners not supported officially under OS Catalina.
Kind Regards,
Coreena, C.
Fujitsu Computer Products of America
The reply does provide some insight, suggesting that providing a solid software solution for the company’s new, higher-end iX1500 model may also have been a driving force behind exhuming ScanSnap Manager from its 32-bit grave. Support for older ScanSnap models, like my S1300, may have been a secondary motivation, or just a welcome side-effect of that process.
Curious about the comment that “there is no support for scanners not supported officially under OS Catalina,” I checked the S1300’s compatibility status, and sure enough, the S1300 is now listed as compatible with Catalina.
Interestingly, a TidBITS reader found that ScanSnap Manager V7 worked with his older ScanSnap S300M though it’s not listed as being compatible. So it’s worth giving the new ScanSnap Manager a try even if your older ScanSnap scanner isn’t explicitly included in the compatibility list.
All’s Well That Ends Well?
This is fantastic news for ScanSnap owners, especially those who have not already purchased a new scanner or new software. I have copies of VueScan and ExactScan, but I’m just going to use ScanSnap Manager V7 under Catalina. I do miss the scan-on-insert feature those third-party products offered but not enough to switch from the familiar, seamless experience provided by Fujitsu’s native solution.
If you have a previously orphaned ScanSnap scanner, please try ScanSnap Manager V7 out for yourself and report back if anything doesn’t work as you expect it should!
Apple Releases Dedicated Security Research Device
Apple has announced that it is releasing a special version of the iPhone to approved security researchers as part of a new Apple Security Research Device Program (SRD). The SRD, which was originally announced during last year’s Black Hat information security conference, is a standard iPhone with key security controls disabled to allow security researchers to run their own tools. Apple will provide SRDs on one-year renewable loans to researchers who are accepted into the program.
In a private briefing, Apple provided additional details about and background on the SRD program.
Who Can Get an SRD
Apple said that anyone with a track record of “systems security” research is encouraged to apply, even if they have little to no experience with iOS. The program has two key goals: to open up opportunities for those with experience on other platforms by lowering the bar for iOS research and to make security research more efficient for existing researchers.
Until now, researchers were largely limited to two options. They could use standard, secure devices and attack them almost blindly, which was inefficient at best. Or they could rely on jailbroken devices that were often limited to earlier versions of hardware and software because every jailbreak is a severe security vulnerability that Apple tends to patch swiftly.
What Makes an SRD Different from a Regular iPhone
The SRD lacks code execution and containment capabilities on multiple levels of the hardware and software to allow researchers to run their own toolchains, including common research tools (which we assume need to be compiled for the platform). As an example, the SRD ships with a terminal shell out of the box, so the researchers can employ a wide range of debugging tools and access low-level logs that are normally inaccessible. A researcher could, for example, deploy a full network monitor onto the device.
Researchers can also run their tools with arbitrary entitlements, including Apple’s own entitlements that are never available to developers. Entitlements are the key sandboxing control on iOS to restrict what applications can do.
Although the SRD will support iOS 14, it needs to run special Apple-provided versions of iOS since regular consumer builds have all the security controls enabled.
How the SRD Will Be Useful to Researchers
One of the interesting aspects of the SRD program is how it will enable research on the Apple iOS ecosystem beyond traditional device security. For example, in 2019, the Citizen Lab discovered that Tibetan groups were being targeted with government-sponsored mobile malware, including attacks on iOS devices.
An SRD could help researchers run security tooling to better identify and research these kinds of attacks. When asked if Apple would support this general kind of research, which differs from traditional vulnerability hunting, company reps responded, “They are supporting the security of our users… that would likely qualify as strong research.”
Additional Details
A few other interesting points came up in our discussion:
- The SRD is based on “the latest hardware.” Apple did not specify a particular model but said that it’s important to keep the hardware up to date so it reflects what customers use. On the off-chance Apple releases new iPhones in the future, it’s likely that the company will update the SRDs.
- Researchers are required to report vulnerabilities to Apple and withhold disclosure until fixes are available. This applies only to vulnerabilities discovered using the SRD and not anything discovered independently. Researchers who have policies to disclose vulnerabilities on a preset timeline won’t be able to participate in the program without changing that practice.
- Researchers will need to comply with the terms and conditions of any App Store apps they install on the device; Apple is not adding its own restrictions. If they do discover a vulnerability, the researchers are expected to report it to both the vendor and Apple.
- Aside from basic access to the device, Apple is also supporting the program with a dedicated forum that includes Apple security engineers. Apple security leadership is also available for program feedback.
- Apple has not determined how many SRDs will be produced, and the initial run of devices is not representative of the overall program. The company plans to continue to evaluate and expand based on how things go. My assumption (which could be incorrect) is that the program will initially be relatively small and will grow over time.
Constructive Progress, but with Risks
Overall, I see this is as a highly positive move for Apple. It can be incredibly difficult to build a toolchain for a device as locked-down as the iPhone since you are effectively flying blind until you crack the security deeply enough to install some instrumentation. Assuming the SRD works as described, it will remove many of the major roadblocks to iOS security research and could result in discoveries that provide better security for us all.
On the whole, Apple’s program requirements and restrictions appear reasonable, and I look forward to seeing how they work in practice. However, there is some risk that the program restrictions will muzzle some researchers while Apple sits on vulnerabilities. Apple’s track record for fixing issues has been pretty good in recent years, but we can’t dismiss this concern out of hand.
As Michael Tsai notes, this restriction could inhibit program members from releasing other iOS vulnerability information discovered independently. Researchers might lack solid records defending the origin of an independent discovery and thus feel constrained by Apple’s restrictions.
One final note: I don’t expect Apple’s highly gated access to the program to change in the future. An opportunity like this is ripe for abuse by malicious governments and private organizations that already pay large bounties for iOS vulnerabilities. The SRD reduces barriers for research that contributes to Apple’s ecosystem security without lowering the boundaries for malicious actors.
Turn Your iPhone into a Powerful Webcam with Camo
Some of us have been living in videoconferencing sessions for months, which has presented many challenges. (“Kids, can you stop singing ‘Baby Shark’? I’m in a meeting” “Bill, can you grab the cat?”) One of them is the revelation of just how poor the video is that’s produced by the FaceTime HD camera on Mac laptops and iMacs. Apple has stuck with a low-quality, outdated 720p webcam through its very latest MacBook Air released this year (see “The 2020 MacBook Air’s FaceTime HD Camera Is Still Lousy,” 8 April 2020).
Meanwhile, Apple continuously improves the front and back cameras found in iPhones and iPads. The front-facing selfie camera in the iPhone 11 and iPhone 11 Pro records 4K video at up to 60 frames per second.
What if you could put your iPhone’s peanut butter in your Mac’s chocolate? The result is Reincubate’s Camo, a virtual-camera system that lets you treat the front- or rear-facing camera on your iPhone, iPad, or iPod touch as a full-fledged video source for many Mac videoconferencing, streaming, and video-editing apps. For dozens of compatible apps, Camo appears just like any camera built-in or attached to your Mac.
Unfortunately, it doesn’t work with FaceTime or Safari! However, compared to competing apps, like Kinomi’s EpocCam, which has been blocked by some Mac videoconferencing services, Camo has much wider support.
Why Camo Turns Your iPhone into a Great Webcam
Camo scratches an acute pandemic-era itch for Mac owners, particularly given the shortages of high-quality 1080p and higher-resolution USB-connected webcams, including several popular models from Logitech. Why not use the best camera you already own?
Many people with DSLR and mirrorless cameras are using virtual-camera software that lets them rely on those devices’ superior optics and lenses. However, the necessary software isn’t available from every camera maker or for every model, and the best solution, Ecamm Live, is priced for professionals at tiers of $15 and $25 per month. And if you don’t already have one, those cameras aren’t cheap! (If you do own one and the software doesn’t exist for your model, look into an HDMI-to-USB adapter; some electronics maker is pumping out an excellent generic adapter sold under many names, like this one for about $33.)
Camo comprises two parts: an iOS app for iOS 12 and later and Camo Studio for macOS 10.13 High Sierra or later. To ensure optimal video throughput and control, Camo Studio requires that you plug your device in via USB. (Connectivity via Wi-Fi and a Windows version of Camo Studio are both on Reincubate’s roadmap.)
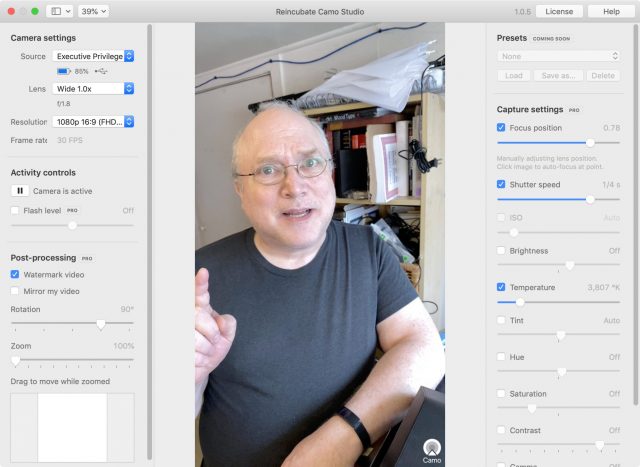
Camo’s mobile app has no features: it merely provides a connection to Camo Studio, which has all the controls. You can choose among multiple connected devices, pick lenses (front or any rear lens), select resolutions up to 1080p (for now), and enable the built-in flash to add fill lighting. You can also rotate the image, zoom (and pan within the zoom), and control an array of video stream corrections and effects.
These settings include a critical feature that’s difficult to manage with both the Mac’s FaceTime HD camera and the iPhone and iPad: setting focus and keeping it there. The iOS Camera app lets you press to create an auto-lock, but it doesn’t offer a manual setting, as found in many third-party camera and video apps. In Camo Studio, select the Focus Position checkbox, and then you can adjust focus and lock it in place, which avoids the camera picking a point you don’t want or moving in and out of focus as you move around or other people come into view.
Tips for Using Your iPhone as a Webcam
Camo works best with a way to elevate and stabilize your iPhone or iPad so the camera is level with your head and you can look directly at or just below it, as you would with a standard webcam.
That can be tricky: you may need a stable monopod-like stand, a small tripod, or some kind of swing arm. Although it seems logical to want to mount your iPhone above a laptop or iMac display, all mounting hardware I’ve found—like the Mountie and Mountie Plus—works only as a side mount, probably for reasons of stability and center of gravity.
Reincubate published a lengthy article in which the writer tested a staggering array of tripods, arms, magnetic mounts, gimbals, and other ways to hold an iPhone or iPad into place.
In some of my presentations over Zoom, I use a camera or my iPhone to point at places where I’m demoing something, such as a laser cutter in a recent letterpress/laser-cutting workshop I taught online. I mounted a camera swing-arm on the wall near the laser cutter for overhead shots while it’s in action. I can use the laser cutter as an ersatz document stand, too, by placing a piece of foam core on top.
However, to use my iPhone in that way and control it from my Mac, instead of running Zoom on the iPhone, I use Zoom’s screen-sharing feature. In macOS, Zoom lets you tap into an iPhone or iPad that’s connected via USB or sharing its display to Zoom via AirPlay. But in that mode, Zoom just streams what’s on the iPhone or iPad’s screen—including any interface elements in, say, the Camera app—and puts the Zoom session into screen-sharing mode for you and everyone watching. That’s useful for software demonstrations, like a walkthrough, or playing a video or showing images, but it’s not great when you want to treat the mobile device as an additional camera for input. (I could launch Zoom and join the meeting from my iPhone, but some Zoom options are available only by directly interacting with the interface on that device, and other features can be used only from Zoom’s desktop apps.)
With Camo, I can simply use my iPhone as another standard camera input to Zoom, control how it appears, and use Zoom’s Video pop-up menu to switch between Camo and my iMac’s built-in front-facing camera. For other videoconferencing software that doesn’t allow bringing in mobile camera feeds via screen sharing or other methods, Camo is an even more useful upgrade.
What Camo Works With
You can use Camo with nearly all videoconferencing apps, though some require an extra step. Out of the box, you can use BlueJeans, Google Meet, GoToMeeting, Houseparty, Jitsi, and the big gorilla, Zoom (5.0.5 or later required). Firefox, Google Chrome, and Microsoft Edge are also directly supported, so Web apps that rely on video components in those browsers should also work without a hitch. People who stream on Twitch or record with ScreenFlow or QuickTime Player can use Camo directly as well. (Reincubate has an annotated list of supported apps.)
Some other meeting apps, like Amazon Chime, Cisco WebEx, and Microsoft Skype and Teams; collaborative team discussion software, such as Discord and Slack; and several other packages require Camo to strip a security setting from the app. Specifically, Camo has to remove the app’s signature designed to let macOS know if the app has been modified. Once you grant your permission and enter an administrative password, Camo makes a modification in how the app handles video that allows the use of its virtual camera.
Camo also integrates well with OBS (Open Broadcaster Software). OBS is an open-source video-stream mixer that lets you bring in different sources to create a single output that is itself a virtual camera you can use in other software and with live streams at Twitch, YouTube Live, and elsewhere. The mmhmm video-mixing/presentation software currently in beta testing also works natively with Camo.
The Downsides of Camo
If you use an app that Camo needs to modify to patch into, you do create a small security hole: once Camo has stripped the app’s signature, malware could modify it, but that malware would have to get on your machine, too. Reincubate is open about such drawbacks and other updating issues with its approach.
What’s Camo still missing? The company is frank about what it lacks, publishing a roadmap of features it hopes to add after version 1.0. You can’t stream 4K video yet, although that seems to be a priority. While the background-blurring “bokeh” Portrait mode in Apple’s Camera app only works for still images, Reincubate has that feature on its list of video options; Apple makes the depth data necessary to isolate foreground and background available to developers. (Reincubate is also looking at supporting Wi-Fi connections, but it’s understandable that the company started with the reliability and throughput of USB.
Camo also lacks green-screen or “chroma key” removal, where software replaces a solid-color backdrop with an image or other video. Zoom and other software include green-screen removal, and Camo’s virtual camera doesn’t prevent that. But if Reincubate built it in, the option would become available in any supported app.
The free version of Camo offers fairly little: just 720p resolution, video mirroring, rotation, and zoom, and it requires a watermark. Pay $39.99 per year to unlock Camo Pro, and all features become available, including removing the Camo watermark. The free tier is useful for testing out how Camo works with your setup and apps, however, so you know if it’s a good fit. Zoom also currently limits video to 720p in most cases, making higher resolutions less useful, though Camo’s other camera features are significant enhancements over the Mac’s standard FaceTime HD camera.
While I own a Logitech C920 1080p webcam that I use with my iMac, it’s not as versatile as my iPhone and has just a single lens. I find Camo a great addition to my video arsenal, which is a great thing to expand, given the indefinite future of remote business meetings, workshops, and presentations ahead of us.