Beware Fake MACDefender Antivirus Software
While the news of the Weyland-Yutani crimekit (see “Macs Targeted by New “Crimekit”,” 2 May 2011) is more concerning for the Mac platform as a whole, security software firm Intego has identified a new piece of malware that masquerades as an antivirus program called MACDefender. (This MACDefender isn’t in any way associated with a German company that runs the MacDefender.org Web site and writes geocaching and other GPS-related software.)
A rather specific combination of actions needs to occur for MACDefender to be downloaded and installed, including visiting a poisoned Web site, allowing the Web browser to open files after the file downloads itself, and then entering an admin password in the installer. But if all that happens, MACDefender adds itself to the login items, displays a menu bar icon, and looks like a real antivirus program. See the Intego security memo for screenshots of what it looks like.
MACDefender’s goal appears to be to scam users into paying for the program, and to that end, it claims to find viruses and also opens porn sites in the user’s browser every few minutes in an attempt to make the user think they’re infected. After paying, the warnings disappear. Of course, it’s entirely likely that the purchase process is designed as much to steal credit card numbers as to make money from purchases, given that the charges can be reversed if the user discovers the scam.
MACDefender is an example of “scareware,” an increasingly popular type of malware that attempts to trick users into thinking they are infected with viruses in order to extort money (and credit card numbers).
Intego’s VirusBarrier X5 and X6 with updated malware definitions do protect against MACDefender, but MACDefender isn’t sufficiently subtle for us to recommend that you run antivirus software (see “Should Mac Users Run Antivirus Software?,” 18 March 2008). Just avoid iffy Web sites, and for goodness sake, if you’re ever asked for your administrator password by a software installer that you didn’t explicitly download and run, don’t enter that password!
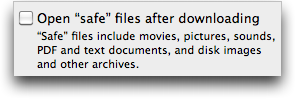
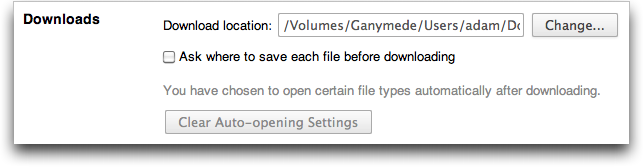
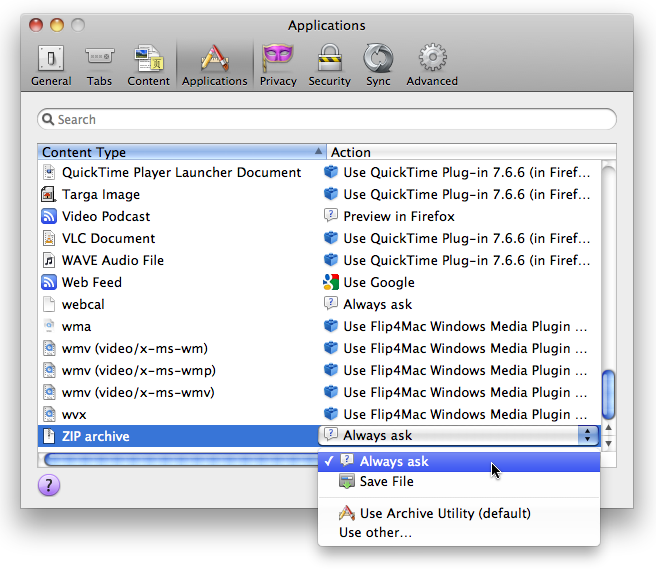
It’s also a good idea to uncheck Safari’s “Open ‘safe’ files after downloading” checkbox in its General preferences. I believe Google Chrome and Firefox always ask for permission when you first encounter a new type of download, and you can clear previously granted auto-opening permissions in Chrome’s Under the Hood preferences (choose Chrome > Preferences > Under the Hood > Downloads) and in Firefox’s Applications preferences (set the desired file type, such as Zip, to Always Ask).
If you've been unlucky enough to end up with MACDefender installed, here's how to remove it.
http://www.securemac.com/MAC-Defender-Rouge-Anti-Virus-Analysis-Removal.php
Adam, in the fourth paragraph, you write:
> MacDefender is an example of "scareware,"
which is wrong. That should have been MACDefender.
(already corrected in the Japanese translation :)
Drat! Rich added that paragraph in editing, and I missed the incorrect capitalization. Fixed now.
Not that I really care in this instance, but the bozos behind MACDefender were somewhat inconsistent in their naming in the screenshots shown by Intego. We went with MACDefender but MAC Defender would also be "correct."
MACDefender reminds me of an old French joke making fun of the Belgians: "This a Belgian virus. Since we are not good at programming, please open a command line and type the following for us: "format c:"
:-))
I'm so glad I heard you talk about this just today listening to last week's MacBreak - my mom got hit by this or something like it calling itself "Apple Security Center." She didn't fall for it but it's starting.
Yes, I just learned yesterday that the 10-year-old son of a friend got hit with it too - he was prompted for the admin password but just asked his mother to enter it for him, which she did without any question or comment. Sigh....
I've now heard of variants called MacSecurity.app and MacProtector.app. :-( Same thing, just a different name.
There's a fast and easy program that kills all the MacDefender strains on Macupdate.com: http://www.macupdate.com/app/mac/38520/macdefenderkiller Works great for a lab environment when you have hundreds of CPU's that are infected. It even patches the pref in Safari to not allow safe files to run.
My next door neighbor, who is eighty-one, had this on his white unibody macbook. Today I helped him. At first I looked for ways to resolve it myself, but didn't see good information, or simple and understandable enough for my use. I ended up bringing it in and my next door neighbor wrote a check for $60 for the technicians to remove it. And I returned the macbook to my neighbor, sans MacDefender.
I am just so surprised, that this could happen so close to home.
Here's a simple set of steps...
http://blogs.pcmag.com/securitywatch/2011/05/how_to_remove_macdefender.php