How to Detect and Protect Against Updated Flashback Malware
Apple has released updates to its Java libraries for users of Mac OS X 10.7 Lion and 10.6 Snow Leopard (see “Java for OS X Lion 2012-001 and Java for Mac OS X 10.6 Update 7,” 3 April 2012). The updates bring the Java runtime engine up to version 1.6.0_31 and fix multiple vulnerabilities in Java version 1.6.0_29, “the most serious of which may allow an untrusted Java applet to execute arbitrary code outside the Java sandbox.” What those release notes aren’t saying is that the vulnerabilities in question were being exploited in the wild by a new variant of the Flashback malware (see “Beware
the Morphing Flashback Malware,” 27 February 2012).
[Update: On 12 April 2012, Apple released updates for Lion and Snow Leopard that remove Flashback. Installing the Lion update disables Java on Web pages unless you specifically re-enable Java. Apple also made available a separate Flashback removal tool for Lion users who haven’t installed Java. For more information, see “Apple Releases Flashback Malware Updates,” 12 April 2012.]
Significant Infection Rates — A Russian antivirus developer, Doctor Web, says their research shows more than 550,000 Macs have been infected after users visited compromised Web sites that contain JavaScript code to activate a malicious Java applet. Sorokin Ivan of Doctor Web later raised that estimate to over 600,000 in a tweet. [Update: A week after Flashback hit the news, its infection level had dropped to below 300,000.]
Although we haven’t seen anything from Doctor Web before, the question of who they are came up on TidBITS Talk, where security analyst Brian McNett said:
The first I heard of Doctor Web was when they were referenced, and when Sorokin Ivan later responded via Twitter to Mikko Hypponen, Chief Research Officer of F-Secure. I know and trust Mikko. He uses reliable sources. Doctor Web appears to be a Russian outfit, with largely Russian clientele, so it wouldn’t be unusual for their reputation to be unknown elsewhere. Their key discovery is that Flashback uses the MAC address of the infected machine as the User-Agent when connecting to its command-and-control server. This is a unique pattern that allowed them to track infections before anyone else. That they shared this finding publicly, along with their data, adds to their credibility.
Mikko Hypponen said in a tweet that F-Secure has spoken with Doctor Web and that the infection numbers look real. And Kaspersky Labs has now provided independent confirmation that Doctor Web’s numbers are reasonable and are in fact Macs.
According to Mac security firm Intego, Flashback-infected Macs show no symptoms at all, other than communication with Flashback’s command-and-control servers that could be detected by network monitoring tools. Although we haven’t seen confirmation of this with recent Flashback variants, earlier versions of Flashback tried to capture user names and passwords by injecting code into Web browsers and other network applications, like Skype. In such cases, the affected programs tended to crash frequently. Security firm Sophos says that along with stealing passwords, Flashback can also poison search engine results to perform
advertising fraud (by fraudulently increasing click-through rate) or to direct victims to further malicious content (though that seems unnecessary, if the Mac is already compromised).
More concerning is that Intego says it has seen dozens of variants of Flashback in the past weeks, indicating that the programmers behind Flashback are modifying it quickly to avoid detection and to take advantage of newfound vulnerabilities. That may render obsolete any advice for preventing, detecting, and removing Flashback. On a side note, Intego also says that it has evidence that Flashback was created by the same people who created MacDefender in 2011 (see “Beware Fake
MACDefender Antivirus Software ,” 2 May 2011 and “Apple Responds to Increasingly Serious MacDefender Situation,” 25 May 2011).
Detect Flashback Infection — So how can you tell if you’re infected? Security firm F-Secure posted instructions for detecting current Flashback infections; the instructions also include removal steps that we would dissuade anyone but advanced users from attempting.
That said, detection comes down to issuing the following defaults read commands in Terminal (F-Secure suggests only the first and last; the others extend the technique from Safari to Google Chrome, Firefox, and iCab). In each case, if you see “does not exist” at the end of the response from each command, you are not infected. (The defaults read command is entirely safe — it’s just attempting to determine whether some data exists in the Info.plist file within each application package.)
defaults read /Applications/Safari.app/Contents/Info LSEnvironment
defaults read /Applications/Google\ Chrome.app/Contents/Info LSEnvironment
defaults read /Applications/Firefox.app/Contents/Info LSEnvironment
defaults read /Applications/iCab\ 4/iCab.app/Contents/Info LSEnvironment
defaults read ~/.MacOSX/environment DYLD_INSERT_LIBRARIES
For a simpler approach, Marc Zeedar, publisher of Real Studio Developer magazine, has written a simple Test4Flashback application that encapsulates the defaults read checks and presents a dialog telling you whether or not you’re infected. It doesn’t attempt to do any removal at all.
Protect Yourself Against Flashback — In the meantime, if you are using 10.7 Lion and have not yet installed Java, hold off unless you need it. If you have installed Java in Lion or are using 10.6 Snow Leopard, immediately install Apple’s Java updates via Software Update to prevent infection from this particular variant of Flashback. And although uninstalling Java is difficult, you can disable it, either system-wide or in individual Web browsers (Flashback relies entirely on Web-based attacks, as far as we’re aware).
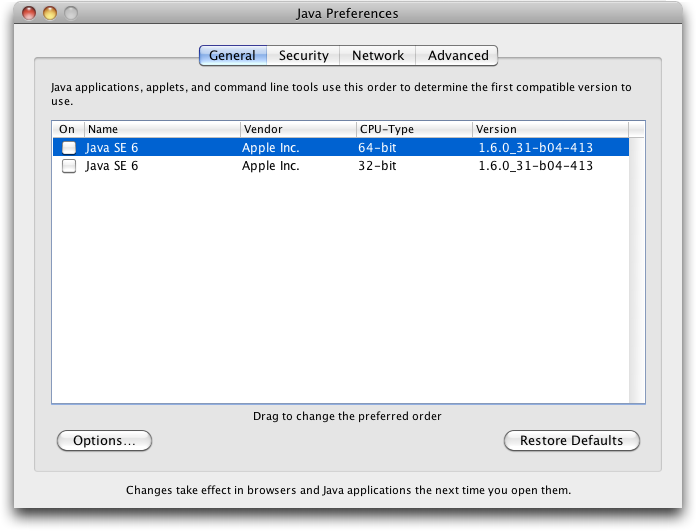
- To disable Java entirely on your Mac, open the Java Preferences utility in
/Applications/Utilitiesand uncheck the checkboxes. Don’t do this if you use CrashPlan or any other Java-based software, including some Adobe applications! -
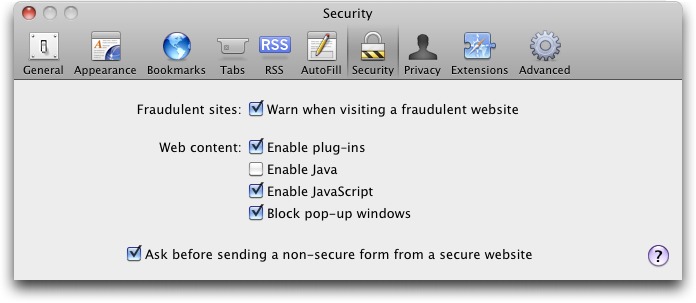
To disable Java in Safari, choose Safari > Preferences, and turn off Java in the Security pane.
-
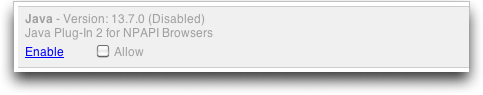
To turn off Java in Google Chrome, type
about:pluginsin the address bar, scroll down, and click the Disable link for Java Plug-In 2 for NPAPI Browsers. -
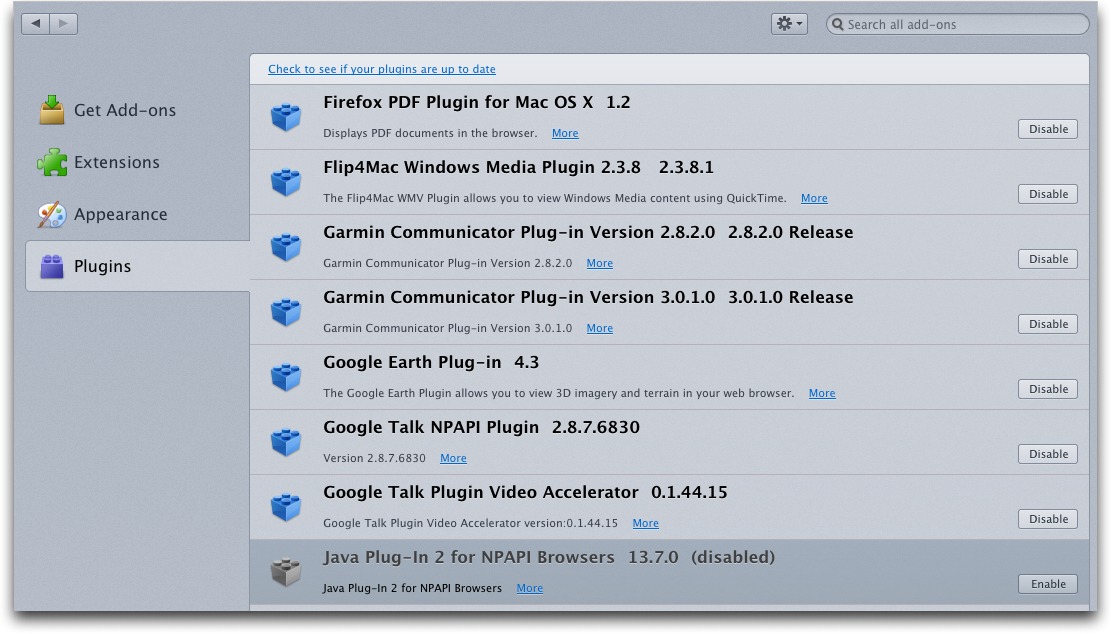
To turn off Java in Firefox, choose Tools > Add-ons, click the Plugins tab, and disable the Java Plug-In 2 for NPAPI Browsers.
If you need to use Java only occasionally, consider leaving it enabled in a browser that you seldom use, and rely on that browser for those specific sites — like Web conferencing tools — that require Java.
Installing antivirus software like Intego’s VirusBarrier will also provide protection, both from the software’s base functionality and because the Flashback malware doesn’t install itself if it detects certain antivirus programs.
Lastly, it’s worth noting that some variants of Flashback worm their way onto Macs not through exploiting Java vulnerabilities, but by fooling users into entering an administrator password. The only way you can protect yourself against such trickery is by being suspicious of any password request that doesn’t come in direct response to an action that you’ve just taken, such as installing a new piece of software that you downloaded intentionally.
Be careful out there.
How about the following?
defaults read /Applications/iCab\ 4/iCab.app/Contents/Info DYLD_INSERT_LIBRARIES
(Note that this one also needs the backslash character in the pathname.)
iCab does _both_ list "Java plug-in for Cocoa" in the 'Plugins' Preferences tab, _and_ provide an option "Run Java applets" in the 'Java' Preferences tab. (Oh, this is under Tiger.)
Wouldn't it be heavenly nice if Apple's Java Update removed/destroyed the malware (if found) at the same time? Would be equally cool if other OS/iOS software developers did the same specific to major threats (via fixes/Updates), if possible.
Here's a *screening* shell snippet that will tell you about any apps in /Applications that have the rather suspect DYLD_INSERT_LIBRARIES key:
for x in /Applications/*; do defaults read "$x/Contents/Info" DYLD_INSERT_LIBRARIES 2>&- && echo "$x loads extra libs\!"; done
(Make that one line or replace the semicolons with line breaks)
If it doesn't emit anything, none of those apps has been compromised by Flashback. Note that the key is for a legitimate OS feature which is not widely used. Its presence isn't necessary a sign of Flashback, but it is arguably a sign of sloppy development practices.
Ignore that shell snippet. It was based on Adam's defaults commands, which are, well, wrong. Really.
See the F-Secure page for the right ones.
Bah - sorry about that, folks. I copied those lines from another site that was referencing F-Secure and didn't compare carefully to make sure they'd gotten it right.
The check for DYLD_INSERT_LIBRARIES in Mac OS X in general is correct, but the Web browser checks should be for LSEnvironment according to the F-Secure page. I've updated the lines above.
> defaults read commands in Terminal (F-Secure suggests only the first two;
but "the first two" should read "the first and the last", I guess.
Fixed, along with some other associated bits.
I don't know if this snippet can be made to work usefully when looking for LSEnvironment, since I find a number of innocuous apps with that set.
Which is why I said ignore it rather than trying to fix it. I have written a more robust shell script for doing the right thing but it is unsuited to a comment :)
The DYLD_INSERT_LIBRARIES key inside the LSEnvironment dictionary is the telltale sign, and it shouldn't exist in a released app, as it is a debugging/testing hook. So far I've seen it in only one app's Info.plist, in a disabled section, in a beta release. See 'man dyld' for details on what it is for.
Is Flashback a threat to older Macs? I'm thinking of PowePC-macs running whatever version of OSX they might be running or Intel-Macs that still use OSX 10.5 or older?
Honestly, I don't know, but I'd be a little surprised - exploits tend to require fairly specific conditions, and older systems may be quite different.
The active code itself wouldn't be able to run on PPC Macs, but the attack vector via Java exists in older versions. Java is CPU-neutral.
If F-Secure is accurate, having Xcode or Little Snitch or any of a handful of AV programs installed scares off Flashback at an early point, so if you have older Intel Macs that can't go to 10.6, you can immunize against Flashback easily.
Both Little Snitch and ClamXav still work on PPC Macs as well as on Intel, back to OS X 10.4.8. Either one will scare off this particular version of Flashback. However, we have no way of knowing if future iterations will be as cautious. The advantage of a security app like ClamXav is that it can be set to quarantine infected files which would, in effect, remove them. However, I don't have an infected Mac to test this on so feedback from anyone who has actually used a security app to deal with this infection would be appreciated.
Does this mean that Marc Zeedar's Test4Flashback app mentioned in the article is not useful?
Marc has kept updating it to keep pace with what we've figured out about the default read commands, so I think it's fine, though you might want to grab a new version if you got it right after this article was published.
This is the best article about this threat. Thank you Tidbits. Specially for explaining why Dr. Web (what a ridiculous name) is trustable.
Thank you! I was perturbed that I hadn't heard of them before, which is why I took a few more steps to find out what others thought.
Your research is particularly useful in light of how riled up some blog contributors have been over the fact that no one else had heard of Dr. Web either. Some have even used this as an excuse to deny the importance of the Flashback trojan.
Indeed, there is a lot of denial going on out there, which I take to be the first stage of grief over the loss of the Mac's storied reputation for being almost entirely malware free. If we take Dr. Web's claimed infection rate at face value (now over 650,000) that reputation is certainly bruised, if not entirely broken.
Sadly, Apple has decided to shoot the messenger, trying to shut down the web server Dr. Web is using to monitor Flashback infections. This is a poor substitute for taking their fair share of responsibility for the infections. After all, Apple was very late in patching the Java vulnerability - two months after if had been patched on Windows. Apple's careless behavior in delaying the patch provided the window of opportunity the malware developers needed to launch their exploit.
I think the Mac press is in denial, as well. While reporting on the Flashback trojan they seem reluctant to apportion responsibility where it clearly belongs. If not exactly a cover up, it certainly smacks of a whitewash.
Macworld has an excellent article about Flashback now too, written by our own Rich Mogull:
http://www.macworld.com/article/1166254/
I'm a dufus. I couldn't get the ":plugins" in the address bar to work in Chrome (18.0.1025.151).
how to check?
You have to type "about:plugins", not just ":plugins" for it to work. Try that. You can also navigate to that page in Chrome's preferences, but it's involved.
Any ideas as to how to remove Flashback from OS 10.5 and 10.4? All I've seen is for 10.6 and 10.7. I'm not a geek so pls keep it simple as to next steps.
Do you know that you're infected? I haven't seen any instructions for those versions of Mac OS X either, and I imagine that the security companies are having a hard time infecting Macs of that age so they could figure out how to remove the infection, especially given how Flashback's infection servers seem to be offline now.
Honestly, if you're not a geek, I strongly recommend you get and install some antivirus software.
Why 10.5.8 very likely not vulnerable: On 10.5 with all updates "java -version" says 1.5.0_30-161 and it seems hole is in java 1.6.0_x (x<31). A google for "vulnerable 1.5.0_30" finds no known holes in it. So I guess the hole in 1.6.0_x is not in 1.5.0_30. And apple never provided any 1.6 for 10.5 and earlier, only for 10.6 and newer.
Still should disable java (but not javascript) in all browsers in 10.5. If using g4/g5 try firefox-port tenfourfox.com which disables all plugins by default, so no flash, no java, etc.
For 10.6+ you could also use the guest account for sites that need java instead of keeping a java-enabled browser around. Unless you disable java for all users similar to http://derflounder.wordpress.com/2011/08/31/activate-java-web-plug-ins-setting-in-10-7-from-the-command-line/
Finally, to get www.mozilla.org/en-US/plugincheck/ to see updated plugins, must delete pluginreg.dat in Firefox/Profiles due to bug: https://bugzilla.mozilla.org/show_bug.cgi?id=313700
May be hard to find anti-virus for non-intel mac. Try first the newest ClamXav 2.2.4 which runs on 10.5 powerbookg4. I would make full backup before installing it, and generally disable on-access checking as it will really slow down older macs. Be sure to keep copy of the ClamAV Enging REMOVER.app just in case. Apple used to include ClamAV on it's older macosx-servers but mostly for filtering out windows viruses in emails. It is hard to find a mac anti-virus product that actually provides an explicit list of the macintosh-malware it can detect. Apple's own (10.6 and up) is looking for about 40 signatures currently.
Is the program Little Snitch necessary if I have disabled and unchecked as required and also downloaded Sophos and ClamXav?
Little Snitch reports on apps making secret network connections; it's very different from ClamXav and Sophos, which are more traditional antivirus apps. Intego's VirusBarrier has Little Snitch-like capabilities, so I wouldn't install both of those, but coupling Little Snitch with any other antivirus app seems reasonable.
I think one of these has to be repeated for every user account on the machine:
defaults read ~/.MacOSX/environment DYLD_INSERT_LIBRARIES
Yes, I think that's true - thanks!
Disabling Java in a browser seems to have unintended consequences, such as perhaps printing or saving pages as pdf files - both of which cause Safari to crash after I disabled Java.
I'd appreciate a more thorough explanation of what Java allows a browser to do, other than visit websites. I'm concerned that without it, Safari is crashing consistently.
...I use Sophos, so perhaps that should be enough to keep me from being as paranoid as this article advises in its final graphs...
It seems unlikely that a plug-in like Java would be required for basic browser functionality, but stranger things have happened.
If you're running antivirus software, you're probably fine. Just make sure to keep it up to date, and be careful about admin-level password prompts no matter what.
Some versions of Safari 5.1 had a problem saving PDFs that had nothing to do with Java. This bug was fixed in the latest Safari update, version 5.1.5, one each for Lion and Snow Leopard.
It should be noted that keeping your software up-to-date is another useful strategy in keeping your Mac secure. This goes for your web browsers - all of which have regular security updates - as well as the Flash plugin (which now has auto-update capability) and Adobe Reader. Some people have sworn off Adobe, but this seems to me to be cutting off your nose to spite your face. But to each his own.
Thanks to your articles, I detected and removed it. It seems my iMac was infected from 4/5 to 4/10. I'm concerned about it getting my passwords. Do you know what it actually does? Do I have to change all the passwords of all the web pages I visited? that's a lot. Other personal information? I've found a lot of information about detection and removal, but nothing about what to do to try to control any damage it might have done.
Unfortunately, there's no way, short of having a full log of your network traffic, to know what might have been stolen. :-(
I would STRONGLY recommend that you change any passwords to important sites (banking, email, etc) or any passwords that you might use on multiple sites visited during that time.
You might also look through your history to see what site might have been the cause of the infection and try to stay away from similar places in the future, if possible.
Thanks, Adam. I was afraid of that.
I re-ran the method described by F-secure just yesterday, ran the new removal tool this morning and was told it removed an infection.
Here is a tool to check for Flashback on OS 10.5
https://github.com/jils/FlashbackChecker/wiki