DropKey Makes Exchanging Encrypted Files a Snap
I know what you’re thinking: you need more encryption in your life. Of course, you’re not really thinking that. No one but security wonks like me and TidBITS Security Editor Rich Mogull has any interest in the stuff that makes transactions and communications safe from snoopers. Rather, you know you want privacy and security, but you likely don’t care about the details.
A new software product, DropKey 1.0 from WellRedApps, should therefore merit your attention, at least if you’re running Mac OS X 10.7 Lion, which it requires. It’s a dead simple way to exchange encrypted files with other people without a lot of overhead or fuss in making the exchange work securely. DropKey is also secure and powerful enough that security wonks will like it, too. (Note: I offered the developers free advice while beta testing DropKey, especially about key verification, but received no compensation and have no financial or other interest in the success of the application.)
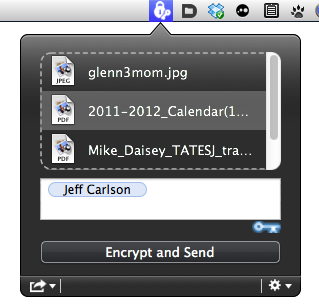
DropKey and Public Key Crypto Basics — After you install and launch DropKey, it appears as an icon in your menu bar. Click it, and a dialog reveals a drag-and-drop area into which you can put files and a space to enter recipients, who are matched from your Address Book. Other controls include a share button (the iOS-like arrow coming out of a box) for handing out your public key in various ways, and a gear icon that provides access to preferences, a key manager for viewing and verifying other people’s public keys, online help, and the Quit command.
DropKey uses public-key cryptography, which starts with a process that creates both a public key that you can share and a private key to which only you have access. DropKey stores your private key in your system keychain, and you never need to manage this at all. When someone wants to send you a file, they encrypt it with your public key, and you decrypt it with your private key. Since only you have your private key, no one else can snoop on the contents of the file. Similarly, when you send someone a
file, you encrypt it with their public key, and they decrypt it with their private key.
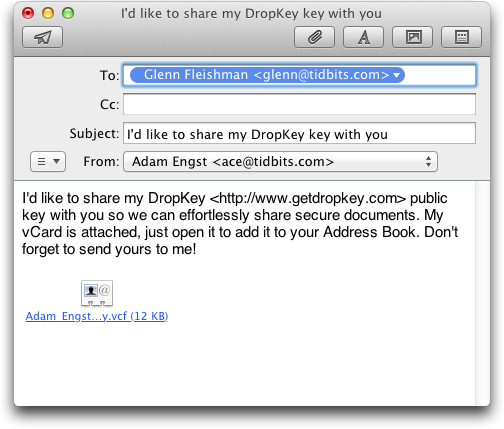
For other people to be able to send you encrypted files, they need to have your public key. DropKey stores your public key as a custom field in your personal contact record in Address Book, and it shares your public key with recipients within a vCard (.vcf) file attached to an email message created in Apple Mail. (vCard is the standard for encoding contacts for export and import; it’s what you get when you share a contact from Address Book on the Mac or Contacts in iOS.) A recipient can import your vCard (via a menu or by dragging) into Address Book, where either a new record is created, or the program prompts to merge the imported vCard with an existing entry. You likewise need the DropKey public keys from those to whom you wish to
send files. It’s a one-time hassle to exchange keys.
(A privacy warning about your personal Address Book entry: if you store data in there that you don’t want shared, you should disable the export of those private fields. In Address Book, click Edit for your entry, and then uncheck the boxes to the right of the fields you want to keep private. In general, I recommend against storing private data in your Address Book entry, but you might also consider not sharing your birthdate or partner’s name.)
If exchanging public keys is too much trouble for some reason, DropKey also offers a less-secure password mode. To use it, click the skeleton key icon in DropKey’s dialog; you’ll have to share the password with the recipient in some other fashion. The password mode also works with an unregistered copy of DropKey even after the 30-day-trial ends.
DropKey compresses the files you’ve dropped into its dialog into a Zip archive and then encrypts the archive. It can create a message in Apple Mail (click the Encrypt and Send button below the file list) in a single step, or you can set its preferences to encrypt only (or hold down Option, which changes Encrypt and Send to just Encrypt). That lets you save the encrypted archive to your hard drive, after which you can attach it to a message in any other email program, transfer it via iChat, sync it via a shared Dropbox folder, share it via Dropbox’s Public folder, or use some other means to hand it off.
DropKey Verification to Prevent Man-in-the-Middle Attacks — It’s worth pausing briefly here to note exactly what DropKey is good for, and what it’s not good for. DropKey is not a local encryption solution — while you certainly could encrypt a file locally and delete the original securely, such that the encrypted version was all that existed on your hard disk (and your recipient could do so as well), that’s not the point of the program. Instead, DropKey is designed to protect files in transit between you and a recipient, along the entire path of networks to which you’re connected and servers that might handle your message. (Using SSL/TLS in your email
program is good, but protects the communication only between your computer and your SMTP server, leaving attachments vulnerable to snoopers along the way and at the recipient’s email provider.)
Nevertheless, public-key cryptography can still be subject to “man-in-the-middle attacks,” in which a bad guy eavesdrops on your communications and sends you his public key instead of the one that your recipient would send, presumably forging the email such that you aren’t aware of the substitution. To foil this attack, you use an “out-of-band” method to verify your recipient’s public key. For example, after you send someone your DropKey public key via email, you then make sure it’s the right key using the telephone or secure chat or even an in-person conversation — any method other than email that you feel assured is free of interception or compromise. To make this verification easier, encryption software can create a
so-called “fingerprint” that uniquely identifies a very long key with a small number of bytes. Unfortunately, fingerprint verification is rather tedious in practice.
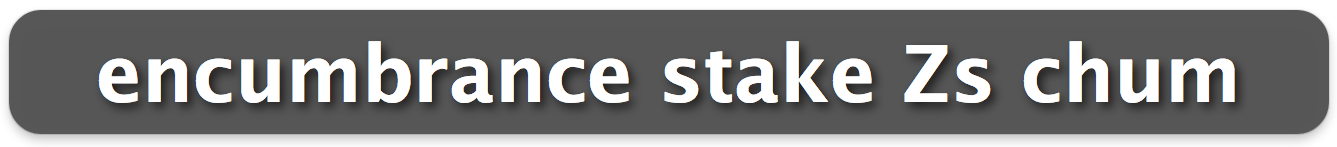
DropKey can help here, too. WellRedApps has created a small dictionary of words that DropKey uses to let you verify just four bytes of the fingerprint. It turns those four bytes into four words that you can use for verification using any other out-of-band method, like Messages, Skype, or a normal telephone call. I confess to suggesting this idea to the developers, and it makes saying “My key verification is ‘encumbrance stake Zs chum’” rather hilarious.
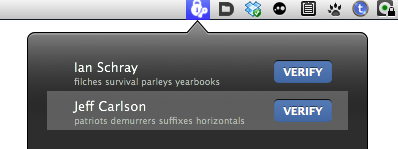
In DropKey’s Key Manager, you view the entry for a person whose key you’ve received, make sure the words they tell you match, and click Verify. This is almost perfect. (You can have perfect verification only if you confirm the entire fingerprint, but while the odds of a man-in-the-middle being able to compromise this system are not zero, they are infinitesimal.)
The Key to the Future? — DropKey is a strong product, but it’s also a version 1.0. Its biggest weakness out of the gate — apart from requiring Lion in a world where many Mac users are still using Snow Leopard — is that the private key that it generates for you at launch is stored in a system keychain, and can’t easily be synced to multiple Macs. If you send and receive email on multiple machines and install DropKey on each, you will confuse senders (as they would need multiple keys for you) and be able to decrypt received files on only the machine that matches the particular key that the sender used. WellRedApps says that it is working on a better approach to
this issue. (I don’t know how many people use multiple machines for email. I use two: a desktop and a laptop.)
I also experienced some minor problems with verifying keys and decrypting files on first launch. After quitting and re-launching DropKey, these problems went away, although a few cosmetic issues with the program persist. I’ve submitted bug reports to the company, and based on past performance, I expect they will be addressed soon.
For strong encryption without burdensome management of keys, DropKey is a solid solution, and anyone who needs to share encrypted files will appreciate its ease of use — in particular, I can imagine lawyers relying on it heavily to ensure confidentiality when trading drafts of legal documents back and forth with clients, so long as they’re all Lion users.
DropKey will retail for $29.99, but WellRedApps is offering a $19.99 introductory offer for a limited (but unspecified) time, both directly and from the Mac App Store. There’s also a free 30-day trial version that you can get from WellRedApps (since Apple refuses to allow trial versions in the Mac App Store). In a particularly welcome move, when you purchase a copy of DropKey directly from WellRedApps, you also get a coupon for a free second license, since it’s impossible to use DropKey without someone with whom you can exchange files. Those who purchase from the Mac App Store can contact WellRedApps at support@wellredapps.com to receive the coupon for the free second license.
Time for an article on how to use the free GPGTools to accomplish the same thing. It comes with a Mail plug-in for sending secure mail, and its ease of use has improved.
I'll second that! However, it must be noted that the Mail plug-in is still in beta for Lion (it works for me, for the most part). Apple needs to make the details of its Mail plug-in architecture available to developers, and ideally not keep changing them with each release of the application.
Yeah a little pricy for what really accounts for a widget, not really a fully thought out product. Seems like a pain in the arse really, I prefer to just use Dropbox to share files.
It's a complete system, designed for people who want encryption and no fuss, not particularly a widget, as it's end to end.
Dropbox lacks end-to-end security, you know. It's fine for what it does (we use it constantly), but can't provide assurance.
So are some of these encryption applications compatible with pgp? Do these applications merely use the encryption tech in OS X? Is a stronger key possible?
"OSX 10.7, which it requires." I quit reading right there.
What is wrong with this dev that they can't support an active OS that even Apple still supports?
Small firm, they go with where the audience is moving to, not where it was.
If my understanding of Dropkey is correct ( just based on this article, so maybe I'm incorrect ) my email recipients must all have Macs to use Dropkey? Most emails I send that need to be secure are to Windows users.
Yes, this isn't a broad solution, like GPG (versions of which are available for everything), but a specific one (just for Mac OS X users with Lion).
I expect the developers could expand the reach or even work toward interoperability if demand were great enough, but there are many millions of Lion users, and that might be enough of a market for them to pursue.
I would tend to agree that this is of limited use for me as I have many people who are, unfortunately, still using Windows. I really think there would be much greater sales if we did have some interoperability. It is really much too limited at this point, but simplicity is a good idea.
WellRedApps is having a very limited time promotion for DropKey - it's free through 20 May 2012 (three days). If you want a copy, act fast!
http://tid.bl.it/JlvV9b
I just installed it as I read on TUAW it was free. Although I encountered a few bugs already, it looks promising but I'm missing one major feature: signing.
Right now anyone can send me an encrypted file provided my public key is used. That's fine. But I cannot be sure if the file did come from the person it seemed to be originated from. This will only be possible if the sender includes a signature encrypted with his own private key. I can then verify this by decrypting this with his public key: that's the only key being able to decrypt the signature ensuring the file did really come from that person (provided he kept his private key secret).
That's the basic approach for PGP / GPG secure communication. Just encrypting with a public key is not strong enough in many cases. I will leave a note on their site.
That's a good point. The software doesn't provide signing, but it's unlikely random people will have your key, which reduces the probability of random transmissions.
For what it's worth, DropKey does offer a second-factor authentication system. Basically, DropKey grabs four random words from a dictionary that you can use to verify the authenticity of the public key. Simply open your Key Manager (from DropKey's lower-right menu), find the recipient, and use an out-of-band method (call them, for example) to determine that the words match up. This was designed to validate the authenticity of the public keys you receive.
This has nothing to do with signing. It's just the two-factor authentication system so you can ensure the public key really belongs to the one you think it belongs to.
Signing has to do with ensuring a received file indeed came from the person where it seemed to be coming from.
I contacted the software developoers of DropKey and they confirmed the concept of signing is fully supported. When a signature doesn't match, the recipient is warned. So, that's good.
DropKey could become the killer encryption app as soon as it supports PGP, runs on Windows and when it becomes possible to do in-place encryption of text.
Yes, Ian, what Rembert says: you all could add automatic signing in a future release, which would be cool, as I would think most people using DropKey for simple encryption would only want to receive files from verified other people. (Or get a warning and advice if the file wasn't signed.)
And, of course, we'd be happy to help you with any issues you're having in using DropKey. Please email us at [email protected]
Thanks!!