OpenDNS Blocks Flashback and Other Threats
Malicious Web sites install code without our knowledge, or rely on our gullibility, in order to hijack our computers. Anti-malware software can help by blocking known attacks, but does little or nothing about new vectors. Some software, like McAfee’s security package, can show whether a site linked via a search engine is known to be safe or malicious. But OpenDNS can go a step further.
OpenDNS promoted itself as a way to avoid being exploited by the Flashback malware last month, but it takes a little unpacking of that claim to understand how the service can help. Flashback attacked Macs by using an exploit in Java triggered when a user visited a Web site hosting the necessary malicious code (see “How to Detect and Protect Against Updated Flashback Malware,” 5 April 2012). Once the malware was installed, Flashback attempted to contact command-and-control servers at obscured domain names built into the code. (Security firms and anti-virus companies ferreted out these domains
and registered those that weren’t already controlled, while those already registered were blocked by ISPs and other parties.) When successful, Flashback’s goal was to infect network applications and steal identity and financial information, transmitting it back to those command-and-control servers.
You could thus be protected from infection if your computer were deterred from visiting compromised and malicious sites that have all manner of code that could cause you trouble. And you could reduce the liability of being infected if Flashback were blocked from connecting to its command-and-control sites. OpenDNS provides both those benefits by controlling DNS lookups.
DNS (Domain Name System) is as complex as any other bit of Internet plumbing, but simple to explain at its highest level. It converts a name of a host and domain, like www.tidbits.com, into an Internet Protocol (IP) number, like 173.255.250.214. DNS enables users to initiate connections to remote servers by using human-readable names instead of the numeric IP addresses that operating systems rely on.
When you switch your Mac or router to use OpenDNS instead of your ISP’s DNS servers, OpenDNS can intercept a DNS request and respond based on what it knows about the destination IP address. This is used for simple but useful purposes, such as fixing a typo like .cmo to .com. (Basic OpenDNS features are free; the firm offers a $20 per year account with additional reporting, support, and controls, and more expensive business and academic institution accounts.)
But it can do more. OpenDNS built a system called PhishTank that accepts reports of “phishing,” or schemes in which spam email messages lure unwary recipients to counterfeit Web sites designed to steal passwords, credit card numbers, or other personal information. PhishTank relies on community reporting and review, letting users examine reports and vote on whether a given Web site should be categorized as one that’s associated with phishing.
Here’s the key for how OpenDNS can protect you from malware. When you’re using OpenDNS, if you visit a Web site identified as being involved in phishing scams, the site is blocked, and OpenDNS displays a message warning you about the site. Other network applications that try to connect to a PhishTank-listed IP address are simply blocked. OpenDNS also maintains a list of servers that are used to control zombified computers, and blocks access to those as well. Finally, OpenDNS can optionally keep DNS from resolving to private address ranges, the ones reserved for use only on local networks (like the 192.168.0.0–192.168.255.255 set) that would never be used for publicly reachable domain names. That might seem unnecessary, but malware
can try to rewrite DNS to point to other compromised machines on the same network or to load a Web site from the computer on which it’s running.
I’ve been using OpenDNS for years, and I also recommend it as something you could set up for friends, family, and colleagues who may not be sophisticated enough to avoid phishing attacks, or who ask you for help in protecting their computers. Adam and Tonya Engst point out that kids — notably young teenagers — are also a prime audience for protection via OpenDNS, since the teens that they’ve observed often click seemingly randomly on Web pages (and in program interfaces in general), exercising little or no discretion as to whether a risk is involved.
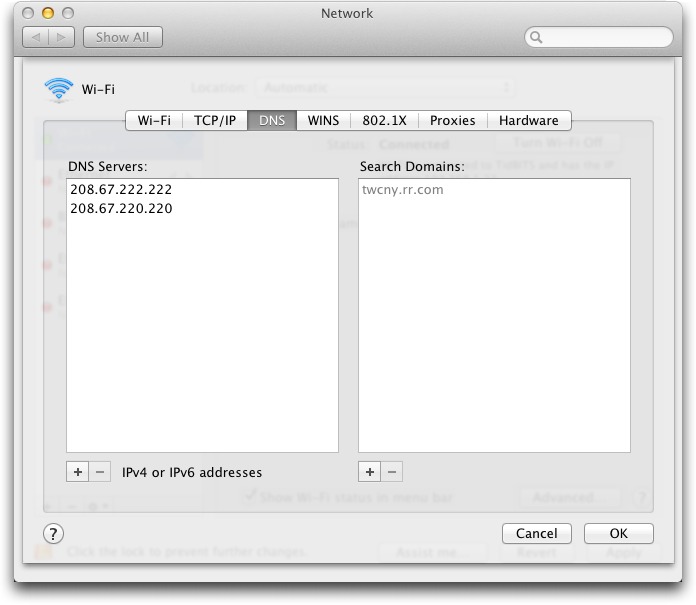
You can use OpenDNS at either the level of a single computer, or, more effectively, at your router, so it protects your entire network. (In fact, for laptops, it’s worth doing both, so you’re protected even when you’re away from your home or office network.) For a single Mac, manually enter OpenDNS’s two DNS server IP addresses (208.67.222.222 and 208.67.220.220) into the DNS view of the appropriate network adapter’s Advanced dialog.
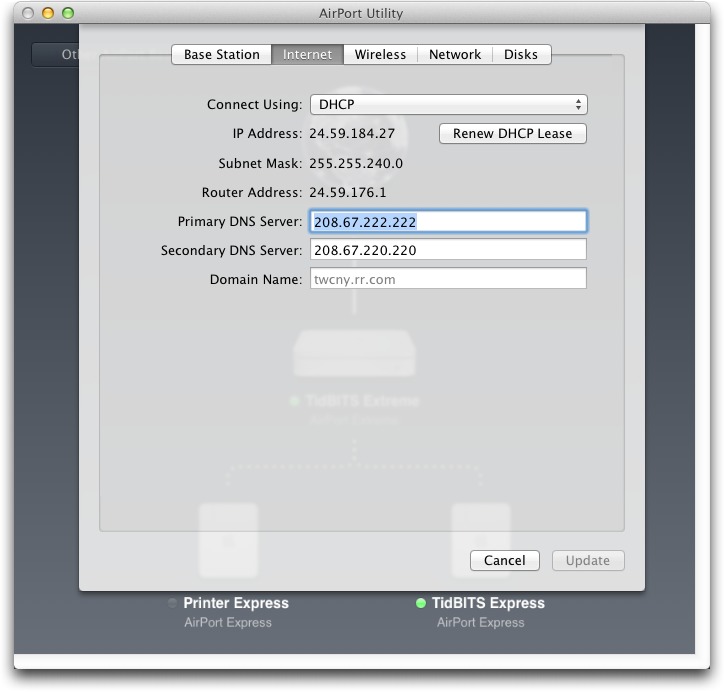
For an AirPort base station, run AirPort Utility, edit your base station’s configuration, and in the Internet view, enter 208.67.222.222 in the Primary DNS Server field and 208.67.220.220 into the Secondary DNS Server field.
A final option for advanced users is to use OpenDNS’s DNSCrypt software, currently in beta. DNSCrypt encrypts DNS lookups, which can prevent malicious redirection on public networks or in subverted nations. I wrote more about DNSCrypt at Macworld.
OpenDNS certainly can’t prevent malware attacks or even protect against unknown malicious Web sites. But by using DNS as part of an Internet-wide reporting and deterrence approach, and requiring that you install no software to take advantage of the benefits, OpenDNS can play a useful role in your overall security strategy.
This is really interesting, the only problem I'm having is my Mac is now having trouble with my hosted exchange account through OS X mail, I'm on 10.7.4 and my hosted exchange account is with GoDaddy - anyone have any suggestions? I've tried allowing a certificate exception but this isn't working.
Can't imagine this has a connection with DNS. If you're making a connection, and have a certificate problem, this likely has something to do with how GoDaddy has created its certificates.
I have intermittent issues with my GoDaddy hosted email account most often affecting SMTP.
This is a recent problem, as in the last few months — I've been both an OpenDNS and GoDaddy hosted mail user for years.
Thanks guys, I went through the hoops with GoDaddy about this and they claim it's an ISP issue, but when I changed my DNS settings back to my ISP's from OpenDNS everything worked fine, just as it always has. GoDaddy say they have no issues with OpenDNS but I don't see how this could be so if my Hosted Exchange doesn't work with OpenDNS but does with my ISP. Am I being a bit thick about this or is GoDaddy giving me the run around?
Mystifies me! You should contact OpenDNS to see if they know about this issue.
The only issue with OpenDNS is that they redirect users to their domain
[user@myhost ~]$ nslookup supermandoesnotexist.com 8.8.8.8
Server: 8.8.8.8
Address: 8.8.8.8#53
** server can't find supermandoesnotexist.com: NXDOMAIN
[user@myhost ~]$ nslookup supermandoesnotexist.com 208.67.222.222
Server: 208.67.222.222
Address: 208.67.222.222#53
Non-authoritative answer:
Name: supermandoesnotexist.com
Address: 67.215.65.132
so, what you are seeing is the result of bad resolution/non-existing domain
I don't see why this is an issue, since you're opting into this behavior. The notion is that OpenDNS solves the problem of a non-existent domain by providing information. In its case, that's a Google search result that OpenDNS receives revenue from.
But it's opt in, and no one is obliged to use OpenDNS. So it's part of their business model and user approach. I know some people hate this because they want definitive answers, but if so, OpenDNS isn't a service they should use.
@Glenn: I agree. I think the problem the user (accessing hosted mail) is facing could have been due to this issue.
If you are primarily a web user, using OpenDNS, it would be easy to understand if there is an issue. But when using it with mail/SSH/ or other services, using OpenDNS could cause some confusion.
True, but it's weird that GoDaddy's public DNS would vary and be a problem based on DNS provider.
Is there anything to know about when using a VPN (either X's built-in client or OpenVPN)? I ain't no networking wizard but it seems like if you have a VPN on then all your traffic is going to the remote server first, then using the VPN server's DNS for the final destination (so it wouldn't matter what you set locally). Or is the local DNS used even when a VPN is on?
It's actually a feature. You don't want to use local DNS, as it could be subverted. You can override this by setting your DNS values for the VPN connection, as OS X treats a VPN like a network interface. Click Advanced, DNS, and override.
But you usually want to use the VPN-based DNS to avoid any local poisoning if you're already concerned enough to use a VPN.
I'm no DNS geek, either! So, why would OpenDNS have better/faster discovery and blocking than any other large DNS provider (Google, OpenDNS, etc.)?
Why would OpenDNS be better than OpenDNS? Or did you mean another firm?
Google Public DNS blocks hostile DNS behavior, but it doesn't block phishing sites, etc. (there's no configuration nor account).
OpenDNS can be set up to work directly with your current IP or a fixed IP range and lets you set particular behaviors you want, such as blocking, warning, filtering, etc.
Great article I had changed over to Open DNS earlier.
I have a question about the Search Domain box shown in the Network panel. Mine shows my ISP. Does anything have to be there at all? Does it matter?
Doesn't matter. It's an obscure setting which tells the DNS resolver in your Mac to append that domain name when you enter a host name (the part before a domain name) that doesn't end in a period.
If you type in tidbits.com in a Web browser, it will try tidbits.com.thing.in.box first to see if there's a match. Used for company/academic networks, and still there for that reason.
(The trailing . isn't required in DNS, but it's part of the spec. So anything without a trailing . is thought of as a host name, not a fully qualified domain name! In practice, this rarely causes a problem.)
Thanks again
Very good suggestion. However, when I try to change the primary and secondary DNS servers in Airport Utility, they and the Domain Name are greyed out and cannot be changed. I don't see any way to unlock them. Am I missing something?
When you say they are grayed out, have you tried typing in the field?
Yes. Nothing happens.
Peculiar. I can't replicate, so I don't have a solution for that yet.
One other person mentioned this in email, but it was equally inexplicable. Can you think of anything unusual about your account or AirPort setup (non-admin user, older base station) that might give us a hint?
"into the DNS view of the appropriate network adapter’s Advanced dialog."
What does "appropriate network adapter" mean?
On the left side of the Network preference pane, you see a list of network adapters, like Ethernet, Wi-Fi, etc. Click the adapter, and then click the Advanced button.
What about using OpenDNS outside of the US?
http://apcmag.com/why-using-google-dns-opendns-is-a-bad-idea.htm
OpenDNS has servers worldwide, but there's an issue in how public DNS works currently that conflicts with content-distribution networks (CDNs). CDNs are used to cache media (images, video, animations) and Web pages in servers that are inside or close to popular networks — fewer hops and thus faster and less latency and less general Internet bandwidth wasted.
CDNs work by providing a lookup for the numeric address of a caching server closest to your IP address (in Internet topology terms). When OpenDNS sends a query, however, the CDN doesn't know from whence the query originates, and may send the wrong response.
OpenDNS and others have proposed a way to pass along a little information in the DNS query to a CDN that would provide a hint (but not the full IP address) of the original requester, and thus give a better answer.
I've found sometimes that with OpenDNS set, my Apple downloads take 20 times longer than when I switch to Comcast. That's because of the CDN issue. The moment I switch, a new lookup happens, and the caching server is so much closer (maybe even inside Comcast's network).
This will be true in the U.S. and around the globe with OpenDNS, Google Public DNS, and others.