Apple Alerts Developers about Xcode Downloads
The XcodeGhost hack, which enabled malware to worm its way into iOS apps by way of modified versions of Xcode that Chinese developers downloaded from unofficial sources, has been one of the more successful breaches of Apple’s security systems (see “XcodeGhost Exploits the Security Economics of Apple’s Ecosystem,” 21 September 2015). Although Apple has neither addressed either the root cause of the problem (China’s bandwidth restrictions to foreign servers) nor enabled digital certificate pinning and better app signing within Xcode, the company has now alerted all Apple developers to the problem via email.
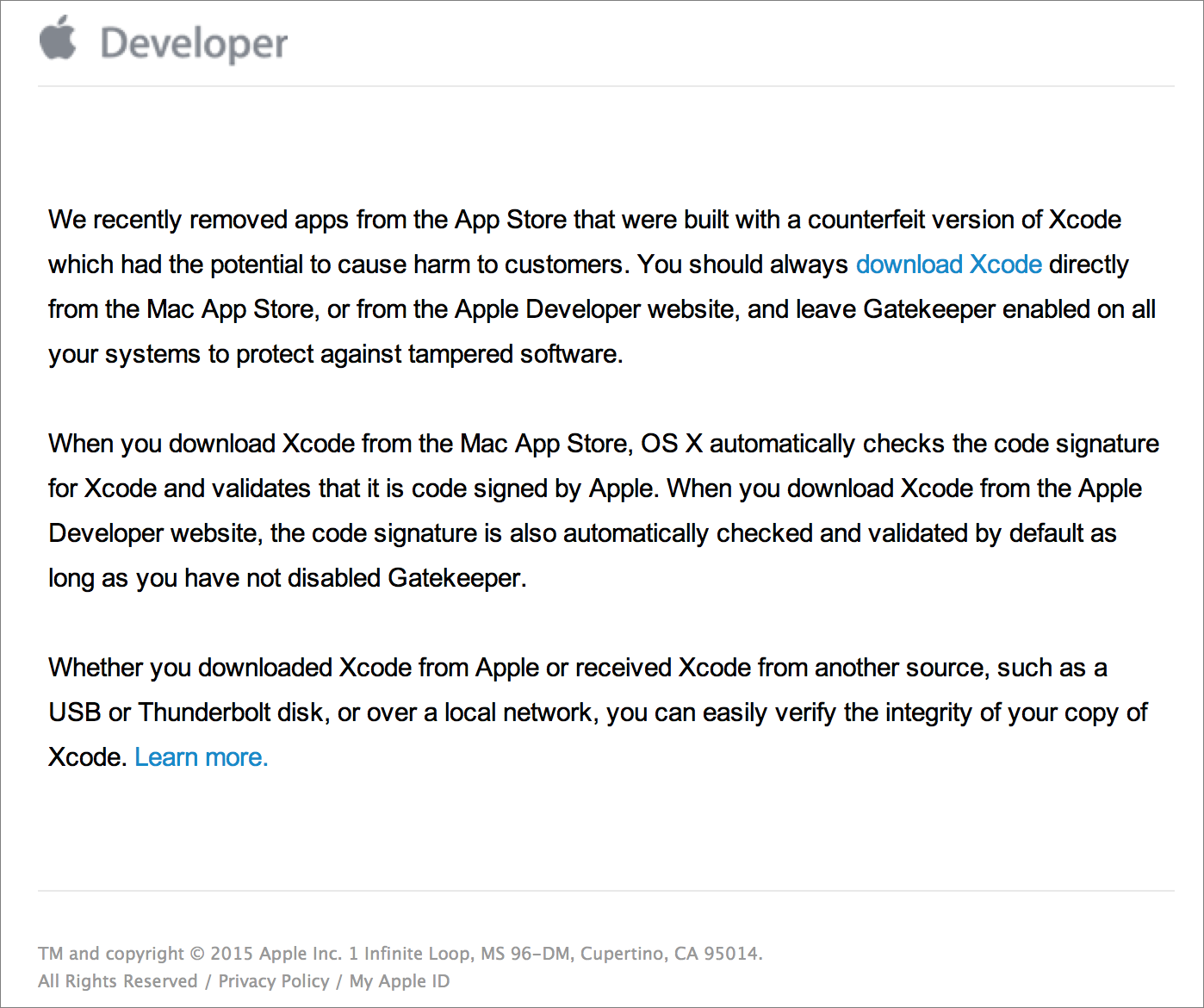
The message exhorts developers to download Xcode directly from the Mac App Store, or from the Apple Developer Web site, since both of those channels allow OS X to check and validate the code signature for Xcode. In an acknowledgement that not all copies of Xcode will come from one of those two sources, though, Apple’s expanded developer news posting provides instructions on how developers can verify the identity of a copy of Xcode acquired via USB thumb
drive, external hard drive, or LAN fileserver.
Apple has also now posted an XcodeGhost Q&A page on the Chinese version of the company’s Web site explaining the situation. It’s in Chinese, of course, but there’s an English version at the bottom. Apple’s Q&A lists the 25 most popular apps that were affected, which is interesting in its own right, even if for the names alone — my favorites are Carrot Fantasy (will there be a spinoff called Daikon Dreams?), Miraculous Warmth (which I have to assume drains your battery awfully quickly), and Flush (which is, amusingly, a stock-tracking app).
Again, there’s nothing we normal users need to do — or can do — about this situation, since Apple’s security lapses in allowing modified versions of Xcode to function and letting malware-infested apps into the App Store are simply outside our control.
Re:"...enable ... better app signing within Xcode":
Xcode's own signature was broken by the hack and OS X correctly refuses to run that _unless_ GateKeeper was turned off.
Xcode could refuse to run with GateKeeper off, or the system would run GateKeeper anyway on Apple-signed apps - that might be the best solution.
Re: "...since both of those channels allow OS X to check and validate the code signature for Xcode.": I think that's only true for the Mac App Store, not for downloads from the developer page, which uses quarantine+GateKeeper.
RB App Checker Lite 1.1.3, which tests for the current exploit, is in review and should be out Real Soon Now.
With regard to downloads from the Developer site, Apple claims:
"When you download Xcode from the Apple Developer website, the code signature is also automatically checked and validated by default as long as you have not disabled Gatekeeper."
But I agree, running Gatekeeper on Xcode (and probably on all Apple apps) instead of honoring the user's setting is probably the easiest approach for now.
For anyone who wants to check out Rainer's app, once updated, it's at:
https://itunes.apple.com/us/app/rb-app-checker-lite/id519421117?mt=12
Yes, we're saying the same thing here: website downloads are checked by GateKeeper (via the Quarantine attribute).
Thanks for the link, there'll also be a DeveloperID-signed version available at http://brockerhoff.net/RB/AppCheckerLite/ — and the app _does_ check itself, which is much faster for such a small app. Xcode is burdened by its huge/complex SDKs.
It's out now, just saying... ;-)