With a Stolen iCloud Password, Your Mac Can Be Held Hostage
Apple designed macOS’s Find My Mac feature to help those who have lost a Mac or had one stolen recover their machines while simultaneously rendering the computers inaccessible. Unfortunately, Find My Mac has recently been subverted by extortionists relying on usernames and weak passwords leaked from account breaches at major sites like Yahoo and LinkedIn — not iCloud itself.
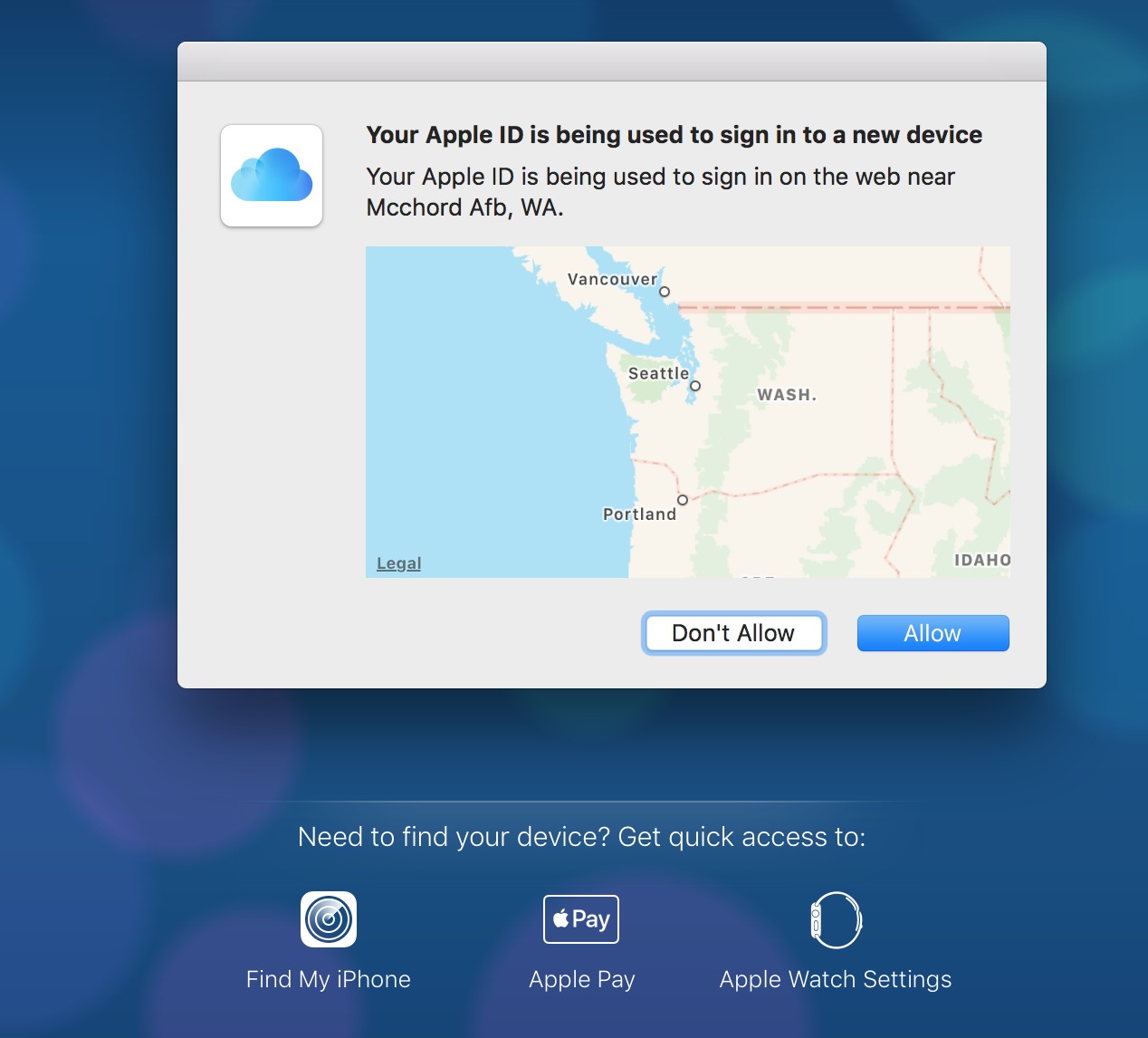
These criminals log in to iCloud.com with a leaked username and password, lock your Mac via Find My Mac with a secret code, and then post a message on the screen telling you where to send Bitcoin to receive the numbers to unlock your Mac.
If you have fallen victim to this attack, do not pay the ransom! Instead, go to an Apple Store or independent Apple Authorized Service Provider and — according to Apple’s FAQ — with proof of purchase in hand, Apple can unlock your Mac. But change your iCloud password first.
You would think that Apple’s two-factor authentication (2FA) would block this attack, but it doesn’t, for the simple reason that Apple lets certain iCloud activities take place without a 2FA code. That’s an intentional security decision that Apple made to allow people to lock lost devices even if they couldn’t gain access to a trusted device or phone number — imagine that your Mac and iPhone are both stolen. But given how extortionists have subverted Find My Mac, Apple needs to rethink this feature immediately.
If you use the same password for iCloud and other sites or if you haven’t changed your iCloud password in years, change it immediately. Some pundits are recommending that you disable Find My Mac, but doing that removes a valuable tool for data protection and device recovery. The password is the issue, not the Find My Mac service.
To see if your credentials may have been exposed in one of these major account breaches, you should also consult Have I Been Pwned?, a trustworthy site run by Australian security expert Troy Hunt that compiles public account breaches.
This attack doesn’t work against iPhones and iPads that already have a passcode in place because iOS’s Lost Mode relies on the passcode to unlock the device. But if your iOS device lacks a passcode or if you have a Mac, the Lock (Mac) and Lost Mode (iOS) in iCloud.com’s Find My iPhone screen allow an attacker to enter a code only they know and display a custom message telling you how to pay up.
In addition to online reports and our testing, we have a direct report of this attack. A graduate student at Cornell (whose mother is a TidBITS reader and got in touch with us) fell prey to this attack this week. Both of the student’s MacBooks were locked, and a dialog appeared on her screens with an email address intended to appear as though it belonged to Apple.
Luckily, she had both Time Machine and Carbon Copy Cloner backups. Instead of responding to the email address, she called Apple and was told to take her MacBooks to the nearest Apple Store. (It’s an hour away, and they couldn’t fit her in for three days; just because Apple can help doesn’t mean it will be convenient.) Upon doing so, and proving ownership with receipts, the Apple Store employees were able to unlock both computers. And the student’s mother managed to refrain from admonishing her daughter for ignoring parental advice to use strong passwords and not reuse them across sites.
That’s all you need to know. However, if you want to understand why these attacks are happening now, read on.
A Feature Becomes a Bludgeon — To be crystal clear, iCloud has not suffered a major breach. Rather, this attack was made possible thanks to breaches at other sites that revealed usernames and passwords. The problem stems from people using the same password on both iCloud and a site that was breached. Since nearly five billion accounts have been exposed in breaches over the years, it’s entirely likely that the bad guys have your credentials from those snapshots.
You would think an attack relying on reused passwords would already have happened to iCloud, and it has: many iCloud users had problems a few years ago when weak passwords in early breaches were cracked. The thing is, crackers are still churning away at stronger passwords from those exfiltrated databases using ever more powerful computational engines. Thus, passwords that might have withstood cracking in the past are falling to this continued effort. Plus, because Apple now actively encourages two-factor authentication, some people still rely on relatively weak passwords due to the belief that 2FA will protect them. That’s actually a reasonable assumption — except in this one terrible case!
2FA does prevent someone with just your password from gaining full access to your iCloud. What criminals have realized more recently is that they can still wreak havoc on accounts that have crackable passwords, regardless of 2FA.
At iCloud.com, a login attempt for a 2FA-protected account begins with a request for the username and password. Next, on all 2FA-enrolled computers and devices, a prompt appears that asks the user to Allow or Don’t Allow the login attempt. But here’s the hole. Without dismissing that dialog, iCloud.com allows someone to access Find My iPhone, Apple Pay, and Apple Watch Settings, and from the Find My iPhone screen, lock a Mac or put an iOS device in Lost Mode. Apple should address this vulnerability immediately.
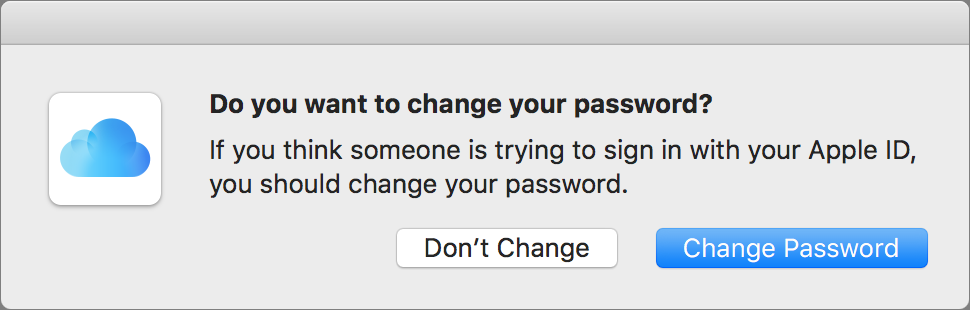
(Pay attention if you ever get an unexpected 2FA login request because it could indicate that someone has obtained your password. Whenever you receive an unexpected request, immediately disable Find My Mac on your Macs, change your iCloud password, and then re-enable Find My Mac. Also note that Apple recently changed what happens when you click Don’t Allow. Formerly, nothing happened. Now, on the device from which you clicked Don’t Allow, you receive a warning that someone might
be trying to access your account and suggesting that you change your password.)
The other reason these attacks are happening now is that the spread of ransomware has popularized the notion of locking someone’s files in exchange for payment. Such payments can be difficult to track to their recipients, thanks to Bitcoin, a largely anonymous cryptocurrency that can be readily used internationally and is the coin of the realm for illegal and dubious transactions. (Yes, Bitcoin is used for plenty of legitimate transactions, too, but it’s the preferred medium for online black markets.) And before you ask, yes, Apple
could track the IP addresses from which the Find My iPhone locking requests originate, but with VPNs, Internet cafés, and other ways to obfuscate origin, that wouldn’t help.
We believe that attackers won’t be able to erase your Mac or iOS device if you have 2FA enabled because erasure requires your second factor. We tested this with iOS but weren’t able to confirm the final steps with macOS, not having a Mac we could erase on hand. Nonetheless, the same process appears to be followed. (Apple doesn’t document these erasure steps to that degree of granularity, which would help.)
Improve Your iCloud and General Password Security — The summary of our best advice for your iCloud password and security, and for password hygiene in general, is as follows:
- Use a password manager. We use 1Password and LastPass around TidBITS. You can also use iCloud Keychain more extensively in iOS 11, which allows third-party apps to tap into an iCloud Keychain password store.
- Create a unique password for each site. With a password manager, this is trivial, both for creating them and filling them in.
-
For services like iCloud, Google, and Netflix where you may need to type your password instead of using a password manager, use long passwords that are easy to type. The old advice — which many sites enforce, unfortunately — of using short passwords (often just 8 to 12 characters) with a mix of letters, numbers, and punctuation is outdated. The latest recommendations, including those promulgated by the National Institute of Standards and Technology, say longer, memorable, and easy to type is better. Password managers can create those for you, too.
-
Enable 2FA everywhere you can, including iCloud. While this attack exploits a loophole in Apple’s use of 2FA, 2FA retains its advantages everywhere else.
For more advice on password selection, using password managers, and general account security, consult Joe Kissell’s excellent “Take Control of Your Passwords.”
Thanks to high-profile breaches, many sites have dramatically increased their password-encryption security. Any intelligently run company has shifted to using better algorithms and approaches for encrypting passwords. Many sites now choose an algorithm that has a scaling factor — over time, the site can keep dialing a number up to keep stored passwords infeasible to crack despite increases in computing power. 1Password, LastPass, and others already use this technique to protect their vault passwords. In 2015, LastPass suffered a severe breach, but there were no reports of cracked accounts because of the computational burden to
break through even a single password.
What we don’t know is whether users are now regularly choosing better passwords and not reusing them across sites. The popularity of 1Password and LastPass would point toward some improvements there, but I’d argue that the outdated password requirements presented by many sites have kept less-savvy users from increasing password strength. Sites need to get with the times, follow best practices, and give users the best modern advice (which is coincidentally less frustrating, too).
Apple Needs To Rethink This Loophole — Letting someone with just an iCloud password lock a Mac with a secret code seems like a bad idea. Perhaps Apple could change macOS’s behavior to mimic that of iOS, which lets you unlock a device with the passcode. What if you could regain access to a Mac locked via Find My Mac using one of its macOS administrator passwords?
Apple could adapt a feature already used with FileVault 2 to enable such a capability while still allowing Mac owners who had just lost all their 2FA-enrolled hardware to lock their devices.
With FileVault, Apple uses the Recovery partition to store account information for all macOS logins that have FileVault access. When you turn on or restart a FileVault-protected Mac, macOS actually boots into Recovery. Entering your password unlocks the full-disk encryption key used for your main boot partition and allows the startup sequence to proceed normally.
Right now, however, if you don’t have FileVault enabled, the Recovery partition has no account credentials that it could compare against when unlocking a Mac. That’s likely why Apple lets the person locking a Mac choose the secret unlock code. If Apple updated macOS to store encrypted credentials for an administrator account in the Recovery partition, it would become possible to unlock a locked Mac with just the administrator password, just as in iOS, where the passcode disables Lost Mode.
With such an update, Mac users wouldn’t have to worry about being extorted through iCloud password reuse, social engineering, or any other lost password scenario. We hope Apple is working to make this change or something similar.
Why is or why would ipassword or lastpass be any more secure than making up and remembering your own passwords? What's to stop someone hacking into ipassword /lastpass and accessing millions of passwords? And equally if not more important why should anyone be required to pay a third party such as ipassword /lastpass when really the issue around security of device is the resoinsibility of the hardware and software provider?
1Password and LastPass use an approach where they retain zero knowledge of the vault passwords for users. They also use a technique that requires a vast amount of work to attempt each password crack for a vault, meaning that to test a million passwords might take on the order of 12 days. So even weak password would survive cracking attempts.
That's a separate issue from whether or not Apple has rolled this out in a good way, which we argue they have not.
The main reason to use a password manager is that you can't possibly remember unique passwords to every site at which you might have an account. I have over 600 sites stored in LastPass, for instance.
As Glenn noted, they are architected to be extremely secure, to the point where even if there was a breach (as LastPass suffered) the passwords cannot be decrypted.
You can use iCloud Keychain with Apple devices for free. Historically, it hasn't been nearly as good as 1Password and LastPass, particularly with non-Apple browsers and apps, but Apple integrated into iOS 11 in a good way.
Oh, no, Adam! I'm a Tidbits member and love all the good advice, but I'm horrified. Please, nothing is "architected," they were designed!
(And also, just for the record, "exponentially" has a real meaning, it doesn't just mean "a lot" as people today seem to think.)
Language evolves.
Language evolves, but those who desire to retain the clarity and specificity of a language element have the right, even the duty, to oppose, critique, or just not use neologisms and reinterpretations.
I, for one, will never use the verb "to author" in any form or conjugation.
English has developed to verbify nouns and nounify verbs, and I use some of those constructs regularly, but carefully and selectively.
Author was first used in English as a verb in the 1500s and through the 1600s, hit an odd gap, and then began use again in that form in the early 1900s.
Here's an interesting discussion.
http://english.stackexchange.com/questions/8699/is-architect-a-verb-and-a-noun
It's not terribly new, starting around 1920 and picking up speed in 1980.
http://goo.gl/BU1MmH
I have two iCloud account, one of which I dont use very often. However I do have to keep it as some of the softwre I use is associated to the old account.
Anyway the other day I went into the account to make sure everything was ok (it got mixed up once a wile ago) I put in the correct apple ID but instead of letting me in it insisted that I change my password. No reason was given and after I answered the appropiate security questions I was given no option but to change my password. As my old password was only 8 letters and all in lower case I am assuming that Apple has deployed software to force users to update what it considers to be unsafe passwords.
Yes, Apple has upgraded what it requires, so you might be told to create a new one. However, its rules still allow the creation of weak password that its approach judges as strong.
Are there password managers that allow me to use the same password database on my various Macs and my iOS devices without using "the cloud"? Is there any way for my devices to sync their password databases directly (and conveniently) without involving a third party?
So far what's kept me from using such a password manager is that I'd want to sync all my Macs and iOS devices, but I also refuse to hand over my passwords (hash, encrypted, or in any other fashion) to anybody else.
You can choose to use 1Password in a way that your vault and passwords never leave your own devices. I believe this is covered in Joe’s book. You don't have to use 1Password-dot-com and you don't have sync via Dropbox or iCloud.
While I see your concerns about syncing, my issues are only if another party controls or possesses, even temporarily, any of the keys required for decryption. The 1Password design in which you sync via Dropbox means that Dropbox has a strongly encrypted vault and never has your password and AgileBits never has your password to begin with.
But even if you'd have complete faith in Dropbox, you still require it to be up, right? I assume if Dropbox goes down, your syncing via Dropbox is broken until it comes back online.
Dropbox syncs locally, so if it breaks, you still have the latest version of your databases stored locally. You could then shift to manual syncing among devices. Dropbox has something like 99.99% uptime.
Thanks, Glenn.
To put things in perspective, that's an hour of downtime a year. Now that's not much at all, but with my luck (Murphy and all) that means they'll be unavailable exactly when I'd really need them to be up. ;)
I’m estimating. It might be 99.9999%. And, again, it doesn't affect local copies.
If DropBox were down, the only feature you would not have for the down period is changes made on one device finding their way to your other devices. It's not passwords being unavailable. And the changes catch up when DropBox recovers.
And one more question, am I forced to subscribe to 1Password or can I buy it?
I believe you can buy the last standalone release. It’s slightly hidden on the site. However, you can subscribe and never use the cloud features, too.
I really dislike how they appear to be hiding the non-subscription version.
But assuming I can the find the version for purchase on their site, does that include a license for the iOS app?
The iOS app is free, although you can pay in-app to unlock some features that most users probably don’t need. You only pay to use either a desktop standalone app or the subscription service, which includes all desktop software and unlocks the premium mobile features.
An even better tip is to not use your Apple-ID e-mail address on other sites for registration purposes. Get a second or third address to use instead.
Until those sites decide to just ban major long-time email domains. That has happened to me with my permanent email address that I've had for almost 30 years.
Quote:
Use a password manager. We use 1Password and LastPass around TidBITS. You can also use iCloud Keychain more extensively in iOS 11, which allows third-party apps to tap into an iCloud Keychain password store.
Create a unique password for each site. With a password manager, this is trivial, both for creating them and filling them in.
End Quote
1Password has a random password generator built-in, but I can't use it because most my sites have very restrictive password requirements and randomly generated passwords frequently don't pass the restrictions.
1 Password has a number of ways to configure password generation to various requirements. Of course I don't know what web sites you use, but I have never encountered a site for which I could not generate an acceptable password. Also it's possible to type in a unique password of your choice if you wish.
I don't need iCloud to "Find My Mac", (all I have to do is walk into my office room, and there they are: Intel iMac i5, iMac G5, iMac G4, PowerBook G4, MacBook Air) so I don't have it activated.
Glenn:
You say "Apple uses the Recovery partition to store account information for all macOS logins that have FileVault access."
That makes perfect sense, but how did you learn that fact?
Apple does not make it easy to find, but they have a PDF with all the details in it for IT people: http://training.apple.com/pdf/WP_FileVault2.pdf
Forgive me Glenn for pointing out that fake Mac ransoming via 'Find My Mac' was first discovered in March of 2016. Here is the discovery article by Thomas Reed at Malwarebytes:
https://blog.malwarebytes.com/cybercrime/2016/03/an-icloud-scam-that-may-be-worse-than-ransomware/
The problem keeps cropping up. Therefore, repeated attention is brought to the problem. I'd like to see Apple provide better, real and solid (vs flaky) two and three factor authentication in order to help avoid this happening.
Also in 2014, before two-factor and before ransomware was as big a problem (the 2014 attackers asked for PayPal).
However, the point of this article is that people wrongly assumed that 2FA would protect against all aspects of password-based account hacking. Unfortunately, it doesn't, thus the advocacy here to urge people to immediately change their iCloud passwords if they're any doubt about their re-use or strength.
Related, people who thought because they weren't hacked before, or were unaware of the billions of passwords leaked, are now at risk as password cracking of old exfiltrated data persists.
I find these security articles very informative and useful - keep them coming!
I would be interested in a discussion/article about Mac and IOS users who do not use iCloud - do not have an iCloud account. How feasible is it to not have an iCloud account in an Apple environment?
Honestly, not very. You can do it, but if you have multiple Apple devices, avoiding iCloud will make your life significantly harder and your Apple experience significantly worse. For instance, if you turned off Find My Mac, thinking that it would protect you from this attack (whereas a better password is the real solution), you would be creating a situation where you stood no chance of finding a lost or stolen Mac. Plus, you wouldn’t be able to lock it remotely, which could increase the likelihood of data on that Mac being exposed (though FileVault and a strong login password would likely solve that issue).
People have been trying to work counter to the way Mac OS X is designed since its release, and while you can usually do so, it’s always more work and often comes with unanticipated problems.
That last sentence seems somewhat odd to me. When OS X launched there was no iCloud. Macs and OS X ran just fine without any "cloud features". OS X was not "designed to work with the cloud". It was only after Apple had launched iOS and iCloud and determined that everybody's life would be better if they used iCloud, that they started designing workflows based on the premise that everybody uses iCloud.
I think the core of what you were saying is right, but it's not related specifically to OS X. It's just Apple. In the Apple world you should work the way they want you to work. Sure you can try otherwise, but it will be difficult and often unpleasant.
The big thing that people stumbled over with Mac OS X was its insistence on using specific folders and a particular folder hierarchy. People really didn’t like that and tried to work around it for years, which always caused headaches in the end.
Working against iCloud is the modern-day version of that. You can avoid iCloud, but you will lose functionality and probably end up stumbling over assumptions that macOS makes.
You bring up a very interesting point there, Adam. I'd say third-party app developers won that one. Instead of sticking to the folder hierarchy Apple foresaw in OS X, they chose to rely on installers that stashed stuff away all over the place. Sometimes going so far as to create their own folder structure and installing in locations not intended for that purpose. IMHO it's a shame Apple didn't win that battle. I remember initially things used to be so easy to find. Now, just go and try to cleanly remove let's say an Adobe app without any kind of uninstaller. ;)