
Photo by denvit on Pixabay.
USB Group Moves to Validate USB-C Devices for Safety and Security
The industry group that manages USB 3.0 has launched an authentication program for USB-C in an effort to block inadequate cables and malicious devices from connecting to computers and mobile devices that support the compact, reversible connector. This group’s leadership includes Apple, Intel, and Microsoft, making it likely the standard will receive wide adoption.
Some inexpensive cables that don’t meet the USB-C spec for carrying high-wattage power have started fires or destroyed computers. Less dramatically, some subset of cables and adapters from little-known suppliers don’t perform as promised, can’t carry high data rates or power, or fail to work consistently.
Malicious USB hacks abound as well, and flaws in the USB “stack,” or the low-level software that manages USB on host hardware, has revealed the potential for exploits that can exfiltrate data or compromise a computer, phone, or tablet. Simply plugging in a USB cable or connecting to a USB charger could enable a malicious device embedded in the cable or charger to hijack data or take over a device.
The proposed solution is a cryptographically backed system, called the “USB Type-C Authentication Program,” which allows manufacturers of host hardware—a smartphone, tablet, or computer—to use a handshake process to confirm that a connected device is legitimately certified and licensed by the organization that manages the entire USB standard, the USB Implementers Forum (USB-IF). If it’s not, the host device could lock down the port entirely or reduce the features available to the attached cable or peripheral.
There’s a reasonable concern that limiting connections to devices that support a paid, proprietary, and closed system could hurt competition and increase costs to buyers. But because the program is voluntary, and host device makers (from Apple to ZTE) will have a choice about how they enforce authentication, it seems more likely to be a benefit.
USB-C: Universal Confusion
The USB-C standard was supposed to make everything easier. A single connector type would carry USB 3, Thunderbolt 3, DisplayPort, and other standards, and it didn’t have to be inserted the “right way,” as it works in either orientation. USB-C would even make good on the promise of earlier USB flavors to offer a reliable way to carry laptop-scale power—up to 100 watts in some implementations.
In reality, USB-C has been a bit of a mess, though not necessarily as bad as some predicted or still claim it to be. Those with older peripherals had to add adapters or upgrade devices. Confusion still reigns about the difference between USB 3.1 and Thunderbolt 3: Thunderbolt 3 uses USB-C as a connection standard, but many non-Apple computers and phones with USB-C don’t support Thunderbolt 3. (For more about these differences, read “Explaining Thunderbolt 3, USB-C, and Everything In Between,” 3 November 2016.)
This confusion, coupled with initially scarce supplies of the necessary chips for each plug and high manufacturing costs to get them just right, opened the door for low-quality cable and adapter makers to flood the market with shoddy hardware.
While the USB-IF acts as a central organization for standards, testing, and certification, a massive amount of gear ships labeled “USB” that the group has never evaluated. In particular, quite a lot of “USB” and “USB Type-C” equipment on Amazon hasn’t passed through outside testing. For a standard as complex as USB-C, those aren’t great decisions, but they reduce costs and time to market.
The maker of one USB-C 100 watt/5 amp cable (which can pass enough power to fry any device if something goes wrong) answered a question about certification with this response:
Dear customer, we only do USB-IF certification on some of the cables, not all, but all with the same quality, please rest assured to purchase. Thanks!
Half of that product’s reviews are 1 to 3 stars, and the 3-star reviews aren’t very positive. The company can assert its quality, and certification doesn’t mean products are perfect, but it shows the gap.
It’s this mess that the USB-IF’s authentication program tries to address.
Authentication: Lock Out or Lock In?
It’s entirely reasonable to worry that a system that has a central organization assigning encryption credentials that can block unapproved devices from connecting to equipment you own could have been designed in part to reduce competition.
We’re all familiar with the arguments against digital-rights management for media and games. Being locked into an organization’s ecosystem means that you are subject to any demand it places, can only use equipment it approves, and will likely pay inflated prices.
However, I don’t think the USB-IF and its USB-C authentication program fall into that trap. The authentication program will increase costs slightly, but I believe the tradeoffs are worth it. The standard is more akin to the security offered by Web browsers for an HTTPS connection than the security imposed by Apple for video or Amazon for Kindle books. In other words, it’s security that skews toward protecting your interests, rather than holding you hostage to an organization’s profit goals.
The USB-IF has picked DigiCert to provide a root of trust using public-key cryptography, much as public-key cryptography is used to protect Web sites. Everyone in the USB-C ecosystem will obtain certificates from DigiCert, just like a Web site operator applies to a certificate authority.
A cable, adapter, or peripheral with an integral USB-C plug will use its certificate to sign and validate information provided about capabilities. Because the USB-IF is part of the process, only equipment that has been tested and certified by the trade group will be able to provide cryptographic proof in the plug itself.
That could help identify uncertified cables and prevent them from causing damage to a host device, even if the manufacturer tries to claim it passed USB-IF testing.
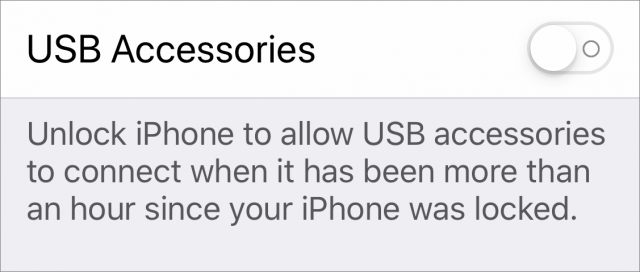
But this authentication approach could also prevent malicious USB attacks, by blocking data from unauthorized plugs. Apple has effectively implemented a tangential version of this with its USB Restricted Mode, which locks out data (and sometimes power) when your iOS device hasn’t been unlocked in the last hour. It has the same effect as USB-C authentication, although it requires the user to authenticate a connection instead of relying on a cryptography infrastructure. (See “USB Restricted Mode Can Block iOS Device Charging,” 6 August 2018.)
The key part of this process will happen with a host device, like a Mac or iPad Pro. With a future MacBook Pro, say, that supports USB-C authentication, the question will be how macOS presents choices to you.
When you insert a certified plug, macOS will likely work exactly as it does now: a connection is silently negotiated, validated, and started, including access to power flows the plug says it can handle, and to data paths.
But when you insert a non-certified plug, what will macOS do? Will Apple:
- Maintain a list of “rogue” cables, adapters, and other hardware, and tell you a device might damage your computer, as with XProtect and known malware? That’s not a bad idea, but it seems unlikely given the unending work to identify such rogues and maintain the list.
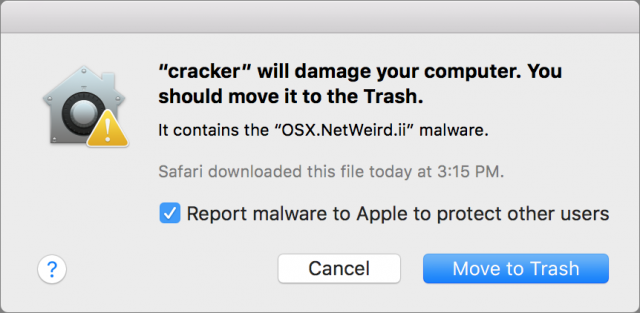
- Explain that an otherwise innocuous inserted device can’t be validated and give you a chance to proceed at your own risk—perhaps even offering to disable Power Delivery features or not? This would be similar to the message you see with uncertified Lightning cables.
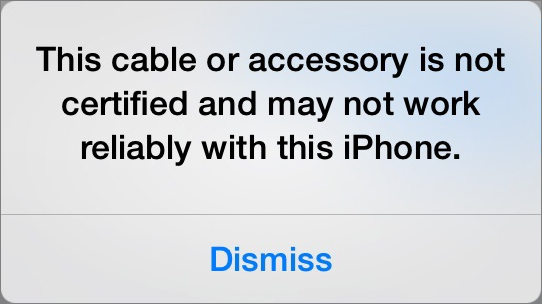
- Reject the device outright, with a warning that it was rejected because it might damage your computer?
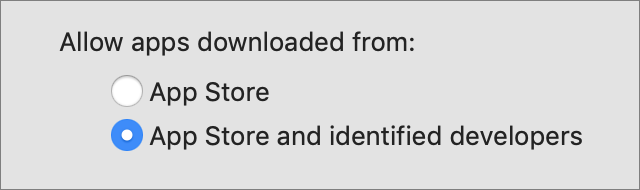
- Offer an advanced option you can configure that controls all of the above? It could work like the “Allow apps downloaded from” options in System Preferences > Security & Privacy > General.
The only certainty is that whatever choice Apple and other operating system makers pick, it won’t come any time soon.
A Market Too Big To Block
With companies like Monoprice that compete heavily on price and volume in the cable and adapter space, and that also are part of standards and certification processes, it seems unlikely USB-C authentication will be used as a cudgel to reject devices that don’t meet the approval of OS makers. They can do that today because USB devices already identify themselves and have certain characteristics—those details just remain unvalidated.
This standard is just now being rolled out, after which it needs to find its way into the USB and Thunderbolt 3 controller hardware that manages USB-C connections in computers and mobile devices. That will take time, and no company will adopt an “authenticated devices only” approach soon, given the hundreds of millions of USB-C devices, cables, adapters, and miscellany without authentication already on the market.
We’re hearing fewer horror stories about USB-C meltdowns as reputable companies have shipped more equipment and dropped prices. But there’s still a strong case to be made for improving the safety and security of USB-C through this authentication program.
Hopefully this will make consumers lives easier when buying even simple products like USB-C cables.
Does this mean that brands will display a logo or text identifying what the cable is certified to do?
Much like how currently Apple MFi certified cables/devices can either claim Apple MFi Certified ® and/or display one of the Apple MiFi logos:
Wouldn’t that be nice! I’d love to see it, but it’s not part of this specification. The USB-IF and the Thunderbolt 3 group (i.e., Intel) does have standard iconography and wording for gross compatibility. USB 3.0 and 3.1 cables are supposed to have a particular “SS” logo (probably ill-advised given history). The “10” in the logo is for USB 3.1 (of course) and the battery symbol indicates Power Delivery 2.0 (but not what wattage).
B&H has a great little write up of this with some amazing illustrations.