Zoom Repairs Flaws and Improves Privacy
The Zoom videoconferencing service has faced unprecedented scrutiny amid massive growth, largely from consumer and school users relying on its free service tier. At the beginning of April, TidBITS published my extensive list of every Zoom security, privacy, and encryption flaw, design mistake, and judgment error (see “Every Zoom Security and Privacy Flaw So Far, and What You Can Do to Protect Yourself,” 3 April 2020).
Even during the writing and editing of that article, new exploits and problems emerged while Zoom was simultaneously addressing all the concerns it could. The company’s all-hands-on-deck efforts continued in the following days, but have finally slowed down as it has gotten ahead of urgent changes. Let’s look at the now-solved issues, new disclosures, and Zoom’s update on its roadmap.
Heightened Safety Controls
The company’s biggest problem was one that arises from toxic Internet culture, but the firm and its users were caught in the crossfire. “Zoombombing” entered the lexicon to describe trolls and bigots leaping into meetings to stream pornography, post anti-Semitic remarks, or scream racial epithets, among other forms of unacceptable behavior.
This happens on other systems, too: my kids’ public-school system standardized on Microsoft Teams, and a teacher sent an email last week about what one could call “Teamsbombing.” But Zoom has seen the most growth by far and ostensibly had the weakest safeguards.
Zoom had published a set of best practices to help hosts avoid unwanted participants or bad behavior by people in both publicly announced and private meetings. That proved insufficient, and on 4 April 2020, the company began a series of measures that have transformed the safety profile of using its service, albeit with additional overhead for hosts and people joining meetings. On 8 April 2020, Zoom’s CEO, Eric Yuan, told NPR, “When it comes to a conflict between usability and privacy and security, privacy and security [are] more important–even at the cost of multiple clicks.”
Some of these changes made it into the last article, but most are new. They include:
- Passwords required: All free-tier accounts, free upgraded education accounts, and single-host paid accounts now require a password. It’s generated automatically and may be changed but cannot be removed. This blocks access by those who obtain the meeting ID but not the password, and it prevents access through bots trying to join randomly generated meeting IDs in the reasonable hope of connecting to a password-free session.
- Meeting ID hidden: The meeting ID no longer appears in the title bar of Zoom apps to prevent it from appearing in screen captures posted on social media or elsewhere.
- Waiting Room enabled: By default, the Waiting Room feature is now enabled for all accounts, even those that previously had the option turned off. The Waiting Room puts participants who attempt to join the meeting into a holding position. The host must admit them. It’s fussy, and if it’s unnecessary in your environment, you can override the default on a per-meeting or per-host basis.
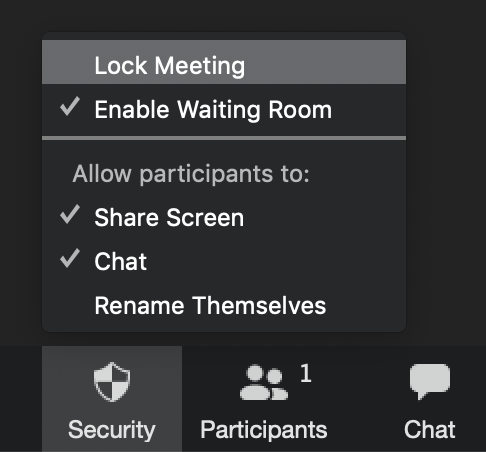
- Centralized security settings: A new Security button in Zoom apps centralizes all privacy and safety settings, including locking participants out of the chat and preventing them from sharing their screen.
- Meeting locks: With a click of the Security button, hosts can lock a meeting at any point to prevent new participants from being added to the Waiting Room or joining directly. Another click unlocks the meeting.
- Name change prevention: Hosts can prevent participants from changing the name that appears when they join or request to join a meeting. Some people—both unwanted visitors and juveniles who thought it was funny—were changing their names to derogatory or abusive forms during meetings.
A less obvious anti-troll change involves requiring a Zoom account sign-in for those using Zoom’s Web app, available across all major browsers. Reportedly, malicious conference joiners could script the Web app to let them continuously re-join a meeting with a new name each time. Hosts can disable that requirement if it’s undesirable to require everyone to sign in with a Zoom account. However, for recurring meetings among an affinity group, like an addiction-support group that has moved online, it’s likely to help deter abuse.
Other Security and Privacy Fixes
Zoom has also repaired other security and privacy problems:
- Domain contacts visibility: Zoom no longer treats every user with the same domain in their email address as belonging to the same organization. Previously, anyone with a given address could view account information or add everyone to their contacts who had the same domain, excluding some major ISPs and mail hosts, like Gmail and iCloud. That feature is now disabled for free tier and paid single-host accounts, and must be enabled on higher-tier paid accounts.
- Waiting Room vulnerability: Citizen Lab discovered a security problem with the Waiting Room feature that it didn’t include in its 3 April 2020 report in order to give Zoom a chance to fix it. That bug, later disclosed on 8 April 2020 after Zoom updated server software, would have let someone with a little technical expertise be restricted to a meeting’s Waiting Room and yet still be able to extract the session’s encryption key and video stream.
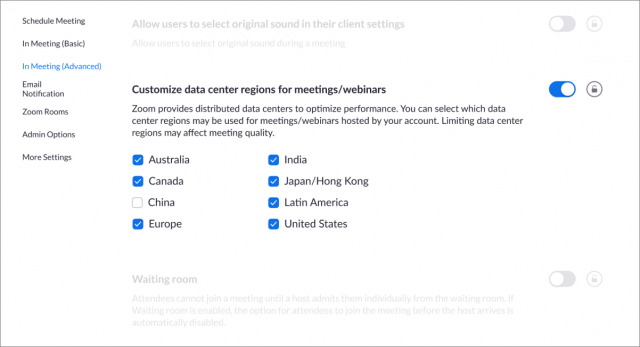
- Traffic routed through China: The paths that data travels is a political, regulatory, and business question, not just a technical one. Citizen Lab’s report revealed that Zoom was routing some traffic that didn’t involve any participants in China through servers in that country. Zoom explained that it was an error in load balancing, which seemed plausible given the quick scaling of operations it needed to have. The company said it made permanent changes to prevent data passing through Chinese servers from outside the country. A new feature for paid users starts 18 April 2020, and those users will be able to select which of several regions data may pass through. Free users are locked to data centers in the region from which they subscribed. Apart from concerns about China, some people outside the United States don’t trust the National Security Agency or other US intelligence groups.
Zoom has also announced that it has formed a council of chief information security officers (CISOs) to advise the company. In addition, it contracted with former Facebook chief security officer Alex Stamos to work as a paid advisor.
While Facebook has faced extreme criticism and government investigations into its security and privacy practices, Stamos had reportedly become a thorn in the side of Mark Zuckerberg and other executives for stressing the danger of Russian misinformation on the platform. In 2018, Stamos left the company to pursue academic research and engage in paid consulting.
Is Continued Progress Enough for You?
Zoom continues to squash bugs while making good on its promises of the last few weeks to respond rapidly. To regain the trust of those who have been troubled, to put it mildly, about Zoom’s past lapses, the company will have to continue down this path of improved security and privacy and increased transparency, while maintaining the high levels of quality and performance that have made it one of the most popular options for videoconferencing during the pandemic.
We suspect that Zoom will never be able to recover from its mistakes in the eyes of some people. For those who aren’t as adamantly opposed to the company, however, it does seem that the company is both saying the right things and working hard to move in the right direction. For a recent TidBITS staff call, we tried Skype for about 5 minutes and were plagued with audio dropouts and other issues. When we switched to Zoom, the audio and video were rock-solid for the remainder of the hour-long call. We’ll continue to test other options, but Zoom has set the bar high.
I’m writing a book about Zoom for Take Control Books and would welcome your tips and input in the comments. I would also encourage you to download a free copy of Take Control of Working from Home Temporarily, a book I wrote to help people with the sudden adjustment in their working lives. It contains a number of videoconferencing tips, among many others provided by Take Control authors, TidBITS editors and contributors, and others who donated their experiences and insights.
They have really been saying and doing the right things since the wave of criticism hit. Obviously, this needs to continue, but I’ve been impressed so far.
Thank you, Glenn. Great news.
I like Zoom’s quality and ease of use (I do hope they eventually fix their broken GUI* though). If it can get its act together on governance and security/privacy I’d be very happy.The UC system uses them even though we are usually a Google shop these days and I personally hope we can continue to use Zoom. These changes sound like they could help make that happen.
[* things like forcing the pref window to float, no return/esc keyboard equivalent for OK/cancel buttons, non-Mac standard GUI behavior, etc. ]
It also looks like they fixed the installation procedure for the Mac app. Previously, the app installed in the pre-flight phase of the procedure, bypassing several checks and installation options for the user. When I installed the current update, I got several windows letting me know the progress of the installation, allowing me to respecify the location where the app should be installed, and whether I wanted to install the app for the current user or all users on the machine.
The only minor annoyance is that after the updated app starts, it covers the window letting you know the the installation has been completed, so that you end up not seeing the notification that the installation is complete until you quit the app.
I’m afraid this is consistent with the rest of the app’s GUI approach to floating panels. Same with prefs for example. It’s annoying and un-Mac-like.
Yes, that was fixed within a few days of it being noted on Twitter. The CEO responded to the original poster on Twitter, even! It’s noted in our article from last week, as the fix was in before we published.
Where I live, we have a saying ‘Trust comes on foot and goes by horse’, so I think it is going to take quite some time. The company I work for has forbidden us to use Zoom. We’ll see when they change that directive. For now we can use Teams and Skype.
I wondered about installing it in a separate user in macOS. Is that significantly more snoop resistant to the kinds of things Zoom has done? I’ve been using it in iOS for that reason, but the small screen is a disadvantage.
In its latest update, Zoom said it’s adding an abuse-reporting feature.
I’ve been quite impressed with Jitsi as an alternative solution to zoom, due to its (zoom’s) shoddy security and privacy (which they are fixing, but by bandaids rather than surgery).
Jitsi is open source, free, and has almost all of the features of zoom. I stress tested it against zoom on a multi-party call and found it to be more resilient than zoom in terms of handling network congestion. It has a neat YouTube video sharing feature too.
Downsides are it doesn’t behave well in safari (but works fine in Chrome), lacks the breakout rooms that zoom has, and scheduling meetings is a little fiddly (but a Chrome extension has fixed that).
Despite the work they have done, I won’t be going back to zoom.
My company’s IT people, a defense contractor, have instructed us to NOT participate in any Zoom calls. We have technical data that needs to be controlled and have been told Zoom doesn’t cut it for us.
Rich
This is totally fair. As I note in the original article, anyone with heightened security concerns needs to avoid Zoom, because it doesn’t have a model that’s robust enough to ensure protection. That is, it is very likely perfectly private to use, but it’s not effectively guaranteed to be 100% private. For personal and education users and most businesses, the difference isn’t meaningful. Steven Bellovin’s examination of the likelihood of interception and decryption is a good read on this.
But if you are in an industry in which there’s a mandate for government-grade security and protection, as you are, or in legal, financial, or medical fields, I don’t think Zoom meets the bar for that. It might be fine, but it hasn’t proven it well enough. As they fix their flaws and overhaul encryption, I expect they will then go through independent audit and certification, which will let them provide the sort of outside assurances needed for fields that require it.
I don’t think there’s a risk on that side of things. There were flaws in previous versions (particularly the one fixed mid-2019) that created a risk to your device. More recently, the flaws are largely about meetings, servers, and stuff that happens within an app, as opposed to operating system related flaws. (The Windows link issue was an app thing that allowed a file exploit, so it was serious, but it required someone being able to chat with you or join a meeting; it didn’t leave a Windows machine vulnerable generally.)
Hi Glenn: Yes, it was your original article that flagged me to this. I would say that anyone who wants a secure connection, should probably bypass zoom for now. For us, it means BIG fines and penalties, so we really need to avoid Zoom.
The hospital I work at is using VidyoConnect for seeing patients during the COVID pandemic. Some doctors here use Doximity, but I am hesitant to it as it seemed to have grown out of LinkedIn. Also, when I was signing up to verify my identity (after giving only my name and birthdate), it asked me the year of my car on the verification info. That seemed a bit too creepy to me. wasn’t sure how my financial info could be pulled from basic data, but caused me to back out of the sign up.
Not sure how secure they are, though they state they are HIPAA compliant.
Thank you Glenn. I was thinking about Zoom grabbing email info, but maybe that was another app.
Zoom has now posted a report on its security progress after 90 days.