Kernel Vulnerability Causes Apple to Update All Operating Systems
If you’ve ever wondered if all of Apple’s operating systems—macOS, iOS, iPadOS, watchOS, and tvOS—are really based on the same code, today’s updates should show just how true that is.
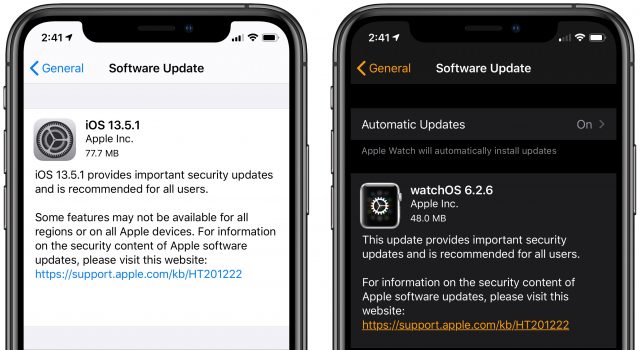
Apple just pushed out macOS Catalina Supplemental Update (1.2 GB), iOS 13.5.1 (77.7 MB) and iPadOS 13.5.1 (284.8 MB), watchOS 6.2.6 (48 MB), and tvOS 13.4.6, along with what we presume is an updated version of Security Update 2020-03 for High Sierra. The only change listed for each of these releases is along the lines of “This update provides important security updates and is recommended for all users.” The security note pages linked above all say, “A memory consumption issue was addressed with improved memory handling,” and note that the fix addresses CVE-2020-9859. Details of that vulnerability are still being held; perhaps they’ll reveal more than “An application may be able to execute arbitrary code with kernel privileges.”
We suspect this vulnerability is an ugly one. Anything that could give apps the capability to execute code with kernel privileges is concerning—it could do anything it wanted on the device from installing a keylogger to surreptitiously recording the user to erasing all local storage. It’s also possible that the vulnerability is fairly easily exploited, which would put hundreds of millions of Apple users at risk.
9to5Mac suggests that these releases are to address the vulnerability used in a new jailbreak for devices running iOS 13.5, given that Apple credits jailbreak maker unc0ver in the security notes. It’s unclear why unc0ver would have reported the vulnerability it relied on for its jailbreak; perhaps the vulnerability was simply too dangerous given that it affects all of Apple’s operating systems.
Oddly, Security Update 2020-03 for macOS 10.14 Mojave was not mentioned in the macOS security notes. It seems strange that the bug could affect High Sierra and Catalina, but not the intervening Mojave. Perhaps a Mojave update is still coming, or maybe a fix that Apple put in place in Mojave was somehow reverted.
While it’s inconvenient for Apple to update all of its operating systems at once, the company deserves kudos for dropping everything during a particularly stressful time to fix this bug.
We tend to recommend a conservative approach to updates, but given the likely severity of the vulnerability and its applicability to all of Apple’s operating systems, we suggest that updating as soon as you can is the safest course of action. If you need a refresher on how to do that:
- macOS: System Preferences > Software Update
- iOS and iPadOS: Settings > General > Software Update
- watchOS: Watch app > General > Software Update
- tvOS: Settings > System > Software Updates > Update Software
I don’t see an update for my macOS 10.14.6 Mojave MacBook Pro. If it’s an oversight, it’s not just in Apple’s notes.
Yeah, I’ve now seen a suggestion that the bug was in High Sierra, Apple fixed it in Mojave, and that it was somehow reverted in Catalina. Feels odd, but then again, the entire thing is unusual.
Ditto - no update posted in Software Update for my MBP with 10.14.6 Mojave.
But then, I’m in Canada. It could be that the Ice Wall is preventing immigrant bits from traveling north across the border.
Thanks for the tip, Adam. I’ll keep checking back in Sys Prefs.
(I’ll have to keep checking manually, since the idiot design of the System Preferences dock icon and the Software Update icon are constantly badged to try and trick me into upgrading to Catalina…)
Seems iOS 12 isn’t getting an update for this issue. I wonder why?
In general, Apple doesn’t release fixes for older versions of iOS. However, the theory that Apple actually had fixed this bug in the kernel for Mojave would suggest that it was also fixed in iOS 12. iOS 11 might be still be vulnerable, given that it was parallel to High Sierra.
One of the security updates for iOS 13.5.1 specifically lists the kernel vulnerability that was exploited by the recent unc0ver jailbreak method (“ CVE-2020-9859: unc0ver”). The unc0ver people listed some versions of iOS 12.x that were not vulnerable, and, while 12.4.7 was not one of them, it may be that Apple wasn’t able to verify that this patch worked with iOS 12, so perhaps an update for iOS 12.4.7 is still coming for iPhone 6/6+ and iPhone 5s (and I believe some iPads are still getting those iOS 12 updates.)
There’s also an HomePod update.
My Apple TV was set to receive Beta Updates and claimed to be up to date with 10.13.5. However, when I turned off the Beta update switch, it was able to download 10.13.6, I turned on Beta updating again and was informed everything was up to date.
One thing to note about the 10.15.5 update, it seems to be resetting the host name and any custom network settings to default on some machines.
Needless to say, this is a problem for many Mac Admins.
Then the article title “Kernel Vulnerability Causes Apple to Update All Operating Systems” is misleading. Based on it I figured fixes were available for all iOS, all Watch OS, all TV OS, and all Mac OS X versions.
Regarding the OS 13 update, does it fix the problems that were caused by the iOS 13.5 update? These problems seem to be generating major concern based on reports in Apple Discussions.
Thankfully I’ve never updated my iPhone 10 to iOS 13 and I won’t be updating my iPad Mini 4 & 5 past iOS 13.1. Of course my iPhone 6 is safe as it can’t be updated to buggy 13.
“All Operating Systems” “All Versions of All Operating Systems."
I’ve always presumed that Apple sees the jailbreak, deconstructs it, then “credits” the jailbreakers for finding the exploit, as kind of a backhanded compliment.
I’m very disappointed this update didn’t address the problem “a very small number of phones are seeing” in iOs 13.5
I have an iphone SE first generation and an iPhone 11. On the first i amd trying to change the apple ID on the second I want to set it up with the same ID. In both it is not possible to conclude this because when you get updating Apple services they both hang. Apple senior technicians informed me on both accounts.
At this time I have two bricks. I can call and message, but no family sharing, no app purchase sharing which is the principal reason I am doing all of this. I do not expect to call and message from both phones
I installed the 10.13.6 update and now I’m having two issues:
Adam, you write: " If you need a refresher on how to do that:
macOS: System Preferences > Software Update"
I don’t see that in High Sierra. Did you mean System Preferences> App Store?
(I certainly won’t be surprised if Apple decided to change that in a later version.)
Please remove this comment if off base, or after making any needed change in the article. Thanks.
Is this true of 10.15.5 in particular? I thought I saw something about how this started with an earlier version of 10.15?
Oh, come on. That’s just ridiculous and you know it. I was just trying to figure out a way to be clear without listing every one of Apple’s current operating systems, along with High Sierra.
I was just trying to figure out a way to be clear without listing every one of Apple’s current operating systems, along with High Sierra.
There’s only one fix listed, and 13.5 just came out, so I’d be surprised.
Hah! That would be a Steve Jobs thing to do. Since Apple referenced a CVE entry, I assumed that the unc0ver team had submitted it, but there’s still no information revealed in the CVE.
I started the update on my iMac prior to my 1 hour morning walk. When I started work everything seemed normal until I tried to open Mail. Several seconds of the icon “hopping”, then freeze, then reboot. This process repeated over and over, so I had to use the recovery option to reinstall macOS 10.15.5. It’s working now, but will not try to update again until I have a bootable backup. Next try will be using the combo update, which I should have done this time. So far no issues with iOS.
Oh, foo. Now you’re just being silly. Obviously it means current operating systems.
And you forgot A/UX.
Yes. Apple changed it in Mojave.
@ace I believe this started with the 10.15.4 supplemental update. The discovery of the network settings reset came later than the linked article, but I can confirm it. On my test machine that had the issue, our proxy settings had disappeared. Luckily I was still able to remote in via IP and fix it since no proxy means no https traffic which means I could not use Jamf to remediate.
Here is the article:
I’ve heard on the MacAdmins Slack that Apple does not plan to fix this until 10.16. This seems insane to me as I really don’t want my entire fleet to lose their ability to reach the Web. If you know anyone at Apple please ask them to run this up the chain. Their OS updates lately have become very sloppy.
Anyway that was just my initial thought but then I mentally substituted “current” in the title. Perhaps it could have read “… All Current Operating Systems plus High Sierra”?
So I won’t be looking for an update to Newton 2.1 or ProDOS 8.
Oops!
Good God. We have the hot mess that is Catalina on our hands, but here we are over a dozen posts deep debating the grammatical nuances and purported insufficiencies of the title @ace chose for his article. C’mon folks.
Well, we have to find some way to combat boredom during “shelter-in-place/quarantine/curfew/etc”.
I have a Mac mini which was running 10.15.4. I installed 10.15.5 just now, expecting to find the Catalina Supplemental Update offered after that. It installed ok, but System Preferences > Software Update now says “Your Mac is up to date - macOS Catalina 10.15.5”, and there is no mention of the Supplemental Update. I have plenty of experience with High Sierra and earlier, but I don’t know Catalina well yet. What have I misunderstood? Has the Supplemental Update been rolled in to the 10.15.5 update I just applied? How can I check that the Supplemental Update has been installed? (System Information.app > Software > Installations has no mention of it.) Can I download the Supplemental Update as a file and install it? Thanks for any help.
Interesting. I installed the suppl update after the 10.15.5 update on my new MBP. What’s your build? I’m at 19F101.
I wonder if Apple might have bundled the supplemental update into the 10.15.5 update and re-released it for those who hadn’t already installed.
My build (click the version number in About This Mac) is also 19F101 after installing 10.15.5 and then the supplemental update separately.
Again, I thank you for providing the How To hints. Even stuff I know, I forget occasionally.
It would be interesting if anyone noted the build number before and after installing the supplemental update. Might the supplemental update change the build number?
I’ve just installed a fat (1.4 GB) security upgrade to my iMac running Mojave (10.14.6) here in UK. Afterwards t looked as though it was no longer blocking a Catalina upgrade and when I put the locking instruction into via Terminal, there was a statement in Terminal that the ability to block future upgrades would itself be blocked. Boo! Anyone know of a way to defeat that?
Thanks all.
From this discussion:
So, yes, I think so.
My Mac mini shows Version 10.15.5 (19F101). So it does seem to have the Supplemental Update installed, although I thought I was installing “just 10.15.5”. Now I think the point here is which 10.15.5…
I dug a little more, trying to find a record of what 10.15.5 build was installed, rather than just relying on what is there now.
The following show that 10.15.5 was installed, but they don’t show a build number:
softwareupdate --history,system_profiler SPApplicationsDataType,/Library/Receipts/InstallHistory.plist.But (mentioned in the discussion I linked to above),
/System/Library/Receipts/has a filecom.apple.pkg.update.os.10.15.5.19F101.plist. So I think @ace is correct:I think this may be what Jeff Johnson wrote about here: Software Update changes in the latest macOS releases
It’s exactly what I’m seeing. Very many thanks for that. I’ve never enabled automatic installations of OSX updates so you should be safe. The red badge is a good reminder to stick another pin in my Catalina voodoo doll!
As someone who upgraded from OS 9.7.3 to 10.3.3 in one step, I’m in no rush to leave Mojave.
Oh, ugh. Seriously?
How long until updates are simply automatic and mandatory?
I’m dreading that. That feels even more MS than MS set it up on Windows 10. ;)
Yes, Apple did bundle the supplemental update into the 10.15.5 update and re-released it. The original 10.15.5 was build 19F96.
The only way anybody has been able to defeat it is through the use of an application blocking software such as santa or Jamf’s Restricted Software to prevent the Install macOS Catalina.app from launching. The prompt will still occur, no matter what you try.
It also seems to be bundled into the latest version of the 10.15.5 installer. I did a fresh install a on VM yesterday using a full 10.15.5 installer that I downloaded on June 9. The resulting build number was 19F101.