Caller ID Authentication May Tame the Scourge of Spam Calls
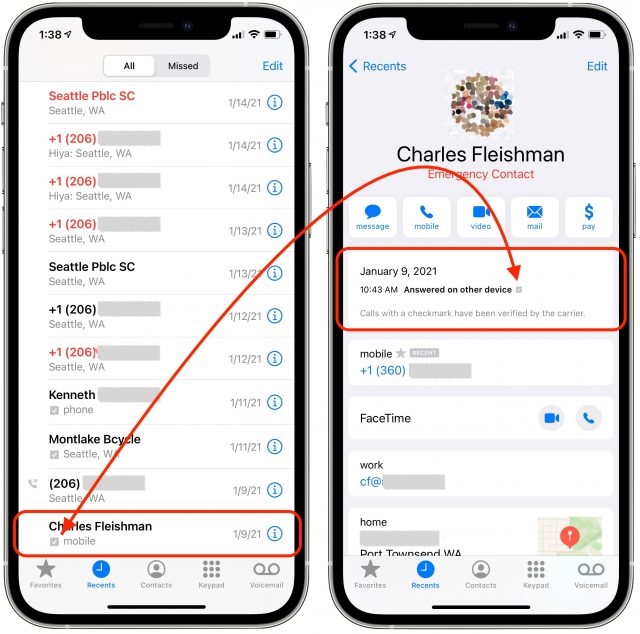
This morning, my iPhone rang five times. Because I pay Hiya for reverse Caller ID lookups, each number lit up with a name I didn’t know, along with the originating city and state: three from Florida and two from Connecticut. I didn’t answer any of the calls because I didn’t recognize any of the names. When I checked later, I found they lacked a relatively new indicator that I watch out for: a tell-tale checkmark. While tiny, it’s a harbinger of better things to come, particularly with a looming deadline in June 2021 for major phone carriers and Internet telephony providers.
You may not even notice this checkmark—it’s truly very tiny—but it appears in the Recents list in the Phone app on an iPhone and in call details. On some Android phones, a verified indicator appears on the incoming call screen, and telephone carriers have asked Apple to add it there on iPhones, too. Only in the call detail do you get an explanation from Apple: “Calls with a checkmark have been verified by the carrier.”
What Are Those Tiny Checkmarks?
These marks started to appear in iOS 13 in the third quarter of 2019, but usage has accelerated as carriers want to block spam calls from ever reaching their customers. Spam calls cause huge headaches for those who run phone networks. They consume network resources, don’t produce revenue (spammers don’t pay a receiving phone network for the calls they place), and irritate the heck out of a carrier’s customers. Those customers, in turn, spend a lot of time complaining to customer-service operators, on forums, and to the US Federal Communications Commission and Federal Trade Commission.
Those two federal agencies have targeted these spam calls, as they want to reduce the number of people who lose money to scams. These calls might waste a moment of your time, but scammers can exploit vulnerable people in cognitive decline or those with too much trust in others to the tune of hundreds or even tens of thousands of dollars. It’s a rare regulatory initiative that started under the previous hands-off presidential administration.
These tiny checkmarks appear on calls that pass through a new standard implemented on major telephone networks starting in 2019 and gradually being rolled out by smaller ones since. The standard, known as SHAKEN, is an amusingly named expansion of an earlier plan called STIR, and the two are often spoken of together as STIR/SHAKEN. (Best said with a James Bond intonation.) What they do is establish a cryptographic chain of trust for the originating number that you see as a Caller ID message. (If you want to know what they stand for, take a deep breath: STIR is Secure Telephony Identity Revisited; SHAKEN is quite absurdly squeezed into its acronym from Signature-based Handling of Asserted Information Using toKENs.)
Larger companies involved in plain old telephone service (POTS), a loose term for the network that handles phone numbers for calling, must implement STIR/SHAKEN by 30 June 2021. There are a lot of exceptions, as noted in this industry briefing article, but any carrier with 100,000 or more lines has to be ready to go by then. (Smaller carriers have until 30 June 2023.) As we approach that date, we should see a few effects at varying levels:
- Fewer spam and scam calls: Pundits often predict this desirable result whenever there’s a major enforcement action or carriers make changes. But in the past, fraudsters just adapted because call-based financial crimes are low-hanging fruit with little risk. STIR/SHAKEN will bump up the cost of doing business, so crime won’t pay as well.
- More checkmarks: We can train ourselves and vulnerable members of our families, friends, and colleagues to identify recent calls with no checkmark. Apple might not yet put the mark on the incoming call screen, but we can check in the Recents list before treating the source as eventually legitimate. About one-third of my regular incoming calls already have a checkmark.
- Better automated call-blocking: With STIR/SHAKEN as a signal, carrier software—like T-Mobile’s free tier of ScamShield—and third-party apps could more accurately predict unwanted calls. Carriers normally are required to pass all calls placed through to a recipient, but the FCC made clear a few years ago that as long as a telco is appropriately looking for spam signals, they can block these. STIR/SHAKEN provides even more data for that purpose. (Verizon claims it has blocked nine billion unwanted calls as of December 2020 through various techniques that include STIR/SHAKEN.)
- Greater accountability: Because STIR/SHAKEN will force spammers who keep plying their trade to rely more heavily on legitimate originating phone numbers, it will make them (or their providers) a lot more vulnerable, trackable, and arrestable. It could help authorities shut down boiler-room operations much more quickly, too.
How STIR/SHAKEN Will Help
STIR/SHAKEN essentially rectifies a historical failure that resulted from extending phone system technology that assumed few participants who trusted one another, much like email. It’s harder to forge Caller ID than the return address on an email, but Caller ID has been spoofable for decades. You probably already knew that, because you’ve received so many illegitimate calls. In recent years, scammers would even engage in “prefix spam,” calling your number with a fake Caller ID number that used the same three-digit prefix that follows the area code. (That prefix remains tied to local phone exchanges with wireline numbers and regional assignments with wireless carriers.)
Originally, businesses and other institutions could set Caller ID via a PBX (corporate phone exchange), which made sense first when companies were managing oodles of internal lines and later when they started using Voice over IP (VoIP). Back in the late 1990s and early 2000s, when I freelanced for the New York Times, I knew I was getting a call from an editor there when Caller ID reported 1 (111) 111-1111, the number the Times spoofed to protect their internal phone numbers. (The Times changed that a decade ago.)
VoIP carriers have long had the broader capability to set a unique phone number for any outgoing call because their calls don’t originate in the plain old telephone system, and carriers had to offer that flexibility to allow Caller ID to work for VoIP calls at all. While hundreds of millions of VoIP-based calls made with correct identification occur every day, spammers also make a reported 100 million-plus illegitimate calls daily. How do you avoid throwing the baby out with the bathwater?
A call may need to make multiple hops across different carrier and third-party networks from the caller to the person answering. STIR and SHAKEN—the latter technically an implementable and broader version of the former—use public-key cryptography to identify which phone numbers are assigned to which originating parts of the phone network. When a call is placed, it has to pass cryptographic tests that are checked at each hop and that can validate that the number identified from Caller ID originated from the right point in the phone system. (For more technical details, see my 2019 Fast Company article on the early stages of STIR/SHAKEN.)
While STIR/SHAKEN should allow carriers to block the passage of calls that lie about their originating numbers, questions remain unanswered about other elements of the system. How will it affect calls that aren’t properly tagged? How should carriers and smartphone manufacturers present such calls to the dialing public? Although Apple’s display is tremendously subtle right now, I expect more prominent marking and signaling over time, including adding a verified message to the incoming call screen. Validated Caller ID should eventually help legitimate calls evade blocking techniques that snag the unproven.
How long will this take? We can probably draw a lesson from the Web’s fairly rapid switchover from mostly non-secured HTTP sites to nearly all HTTPS-secured ones. While the transition started slowly, once browser makers decided on schedules, they began to identify sites without HTTPS with increasingly aggressive labeling that warned of the lack of security. That changeover was combined with significantly easier and cheaper systems for creating and managing the necessary security certificates, like Let’s Encrypt. Having both the carrot of easy upgrades and the stick of browser warnings prompted site owners to upgrade their security.
Ultimately, companies and carriers will find their calls dropped or blocked unless they fully embrace STIR/SHAKEN as it’s adopted by mobile phone operating systems and the rest of the phone network. For those who have built businesses on unethical practices, we hope STIR/SHAKEN will spell the end for them. Good riddance, and we look forward to the day when we can once again answer the phone without worrying that we’re being targeted by a scammer.
If anything, our rate of spam has gone UP significantly the last couple of months. And the Caller ID values are usually forged. So it would be A Good Thing if this was actually fully implemented and working as proposed, but you can’t prove that by me.
What carrier? And do you ever see the little checkmark? Verizon and T-Mobile may be out ahead on this. Intra-carrier compatibility has to be in place by June, but it doesn’t seem to be there (or fully there) now.
I’m on Verizon and have had an increase in calls the past few weeks. Same with spam emails on my Comcast account.
Most of them seem to be the “your car warranty has expired”. One day I was expecting a call, answered it and put it on speaker. My hands were full so I let it go through its spiel and finally a person came on the phone. They asked for my car info and I told them I assumed they’d know it since they knew my warranty had expired (I haven’t had a car warranty since 1992). He insisted he needed it. I called him a scammer. He was completely offended.
(I never answer “hello”, I just pick up and let them say something. Sometimes it’s actually someone I need to talk to!)
Oh - I have the Verizon call block and a free version of HiYa. I also have apps set to offload due to lack of space on the phone, and now and then I discover they’ve both uninstalled. But spam does get through them at times.
Diane
Fwiw, I’m on Verizon Wireless and my wife and I get hardly any spam calls. Maybe one every two months each (and I have my phone set to reject unknown callers so i really never notice.)
And our home landline service (Spectrum) is way better than it used to be, though lately we are getting quite a few more same exchange fake caller ID calls than we used to. Nomorobo captures much of the spam calls.
T-Mobile on the cell, and Consolidated Communications on the land-line. Many more calls on the landline, most of them marked as in-state/same-area-code. I have not seen the checkmark on T-Mobile.
T-Mobile user. I’ve actually noticed spam calls have been much less recently. I use to get ten or so per day. Now it might be one every other day. I do have Spam Likely calls silenced (dial #622#).
I checked my recent calls, and only about 10% have checks.
How do I know if my VoIP carrier will use STIR/SHAKEN? I understand that VoIP carriers might not be part of it.
I wonder whether this is deployed, or even deployable, outside the USA. Oh, yes. Wikipedia says that it’s deployable Internationally, and deployed in Canada. No ticks here from my UK mobile carrier.
I did a unscientific survey of friends on Facebook. 13 reported “more calls the last couple of months”, vs 4 who said “fewer”.
Same here. Used to get several a week, now almost none in a month. I’ve always given out my phone number very sparingly. Same with email. I often resort to Mailinator. I wish there were Mailinator for phones. ;)
STIR/SHAKEN are extensions to industry-standard protocols (SIP for VoIP calls and SS7 for traditional calls), which are used world-wide. So it’s really just a matter of if/when the various telcos around the world decide (or are forced by law) to deploy them.
I’m on ATT and I scrolled down my recent calls, to find a very few with the Check Mark. And those are known callers in my contacts, and on same carrier.
One thing that makes this frustrating is that CLECs (Competitive Local Exchange Carrier) might be able to get reciprocal income from calls coming into phone numbers they “own” and “terminate” to their own customers. So by authenticating calls and marking/blocking spam/fraudulent/spoofed number means they might lose income from others. (yes, CLEC and other lines/ISP/VOIP providers still pay/receive carrier fees). A good read on CLECs…
Absolutely. There’s some settlement involved, but the spammers don’t generate income per se for the carriers who handle the vast majority of the volume of those calls.
The industry document I link in the article says carriers with 100,000 lines or more will have to have STIR/SHAKEN in place by 30 June 2021. I would expect there are smaller VoIP providers who have less oversight and are a bigger part of the problem who won’t be subject until 30 June 2023 per that document.
But what this says to me is that a) the vast majority of unique originating calls will be covered by June. b) VoIP providers who aren’t covered by the mandate and haven’t updated will stand out more strongly making it easier for carriers to identify and pursue technical and legal action against them or their subscribers.
I should have noted in passing in the article that the visual presentation of Caller ID verification isn’t the only measure that it’s happening. Carriers and calls could be fully or mostly verified behind the scenes, and the carrier isn’t passing the signal to a phone that causes the verification message to display. So if 8 of 9 hops are verified, the carrier might use that for its internal management of whether it’s a spam call or not, but doesn’t pass through a 100% verified checkmark. I expect that is going to improve, too, though.
Verizon user. Yesterday I had my first call with a checkmark
I signed up for Verizon Call filter but today when I checked the app I was not subccribed and there was no way to do so
I get lots of spam. One tactic is to answer but make no sound for a while, then answer. Many spammers seem to have robots voice activated
Well, it is a brute force approach but I have every call not in my contacts go directly to voice mail. The spam calls almost never leave a message (the car warranty people do) and occasionally I miss talking to someone directly but going to voice mail isn’t a big issue for me. And, I am careful to make sure the people I want to talk to are in my contacts. If I am expecting an important call from someone where I don’t know their phone number, I turn this off temporarily. (iPhone, T-Mobile)
David
GREAT article Hope it continues to gain support
While most comments seem to be Cell Phone based I want to report that my Comcast VOIP “wired phone” service is showing an occasional (v) indication
I need to use this feature to get a bigger screen TV set since Comcast shows Caller ID information on the display
But I’m afraid even a $225 million dollar fine won’t be enough. They need to get the DoJ to file criminal charges against them and their customers, seeking a shutdown of their business, confiscation of all assets, and jail time for their employees.
Nothing less than that will be enough to send the message that spam doesn’t pay.
silent.m4r is my ringtone. If someone calls me who is in my contacts and has ever called m, they have a ringtone assigned. If someone calls who is not in my contacts they have to leave a message and a number I can call them back on., If not, they do not get to talk to me.
Might not work for everyone, but it works very well for me, and I doubt I will change this even if there are never any more robocalls or spam calls. Phon calls are an interruption that I do not want and I’ve trained most everyone to send me an iMessage or SMS instead if they want me to see it.
And I am sure no rules will prevent the fake policemen calling for donations to possibly fake police charities while implying that it’s you’re obligation to support the police, or any other charity hucksters. If I could buy an iPhone with no ability to install a phone app, I would do it.
Maybe a cellular-connected iPad mini?
Learned something new. On vzw. Checked my recent call list. Only two people, who happen to be on vzw have the checkmark. No other legitimate user from another mobile operator or any other business appears to have said checkmark. So, I certainly could not filter that way, if said filter existed.
We all get multiple spam calls per day, some blocked by youmail free, some labeled scam likely, some with a spoofed number where the first three or even six match our numbers.
It was a home number, that has been on do not call since that launched. What a joke that has been.
AT&T mobile, Frontier landline. On the iPhone, of the ~200 calls in my recent list, there are four checkmarks, and two of those were from unknown (not in Contacts) callers. The odd example is a (I presume) spammer whose caller id had the checkmark on the first attempt, and then one minute later from the same caller id, the checkmark is missing.
This leads me to ask: How granular is the chain of authentication? In other words, if I spoof a number with a valid area code, and a valid prefix within that area code, is that sufficient to pass? Or does the authentication go all the way down to the actual number?
The whole number gets signed, including area code, but it’s not so much the number as the chain of trust and validity. Each call within the system passes a signature that proves the number is valid.
There’s a Silent unknown callers setting on the iPhone.
So I have 2 phones, one a 6s (that very rarely gets used, it’s only for emergencies when I am out and about) and a VOIP line on specdribble. The VOIP gets NOMOROBO service. I use the “silence other calls” on the cell, but there is a downside in that sometimes you need to open it up for calls you WANT to get that may come from unknown numbers (like a car service for example). I get a TON of spam calls on the cell… out of habit I have been blocking those numbers, but now I think why bother as I have the “silence all” active most of the time. OTOH, blocking may spare me a call or two when I DO have to turn that setting off. Of course, remembering to turn it off is also an issue.
On the VOPI, I only answer if I know or am expecting a call. Which a lot of time means I can’t include everyone I may want to speak to, so I simply don’t answer. BUT it gets really annoying as it goes through 4 “rings” (because at times I am far away from the phone and don’t move as fast as I use to). If it’s something actually important, they will leave a message and there have been times that the start of the message tells me I want this call so I just pick it up.
NOMOROBO is an effort but not that good of one. Their schtick is numbers I have reported to them get one ring then no more, indicating it was blocked.Thing is I RARELY have one of those… maybe once or twice in a month. I don’t know if the blocks they make are based ONLY on what I report, or from all reports (it should be from all reports). More and more I am feeling that the whole reporting a number is a huge waste of time. AND that just maybe I am very much alone in dutifully reporting numbers.
Recently a new wrinkle has started up. Phone rings 4 times BUT the called ID is “SPAM RISK.” Yes the phone on my VOIP announces he caller id. But STILL I have to listen to it, which many times can really screw with my concentration (trust me, at my age that is an issue!).
There is NO QUESTION in my mind the telcos (anyone that provides any kind of phone service) are responsible for all this. I believe we have more than enough technology to stop this scourge.I REALLY want to stop doing business with them, but that is kinda impractical!
One of the biggest issues of the Silence unknown callers switch is that there’s no way to create a shortcut to turn it on and off. Plus, the only way to see if it’s on or off is to look at the setting.
Silence Unknown Callers is a lot more sophisticated than most people realize. It allows through all calls based upon your contacts and whom you’ve previously called and whom you’ve texted and based upon Siri Suggestions from numbers found in your email and text messages. I’ll text someone or write an email to myself with a phone number I don’t want blocked just to prevent Silence all callers from blocking that call without having to create an entire address entry for that number.
Still, it’d be nice to easily turn this on and off.
Is this on your iPhone? T-Mobile has a Spam Likely Caller ID when it suspects it’s spam. The nice thing is that T-Mobile lets you silence any call that’s marked as Spam Likely. If you have AT&T Wireless, you can download their Call Protect app, and automatically send those SPAM RISK calls off to voicemail without your phone ringing.
I’ve worked with several of these wireless carriers. It is really out of their hands. If you want to blame a particular company, blame AT&T when it created Caller ID back in 1984. AT&T never provided a means to verify that the Caller ID was accurate. Anyone with a switchboard equipment could set it to say whatever they want. Of course, back in 1984, it was AT&T with all the switchboards. It’s not like there were thousands of scammy companies out there connecting phone calls.
Like email, it was originally setup with the idea that everyone who was on the backend could be trusted. And like with email, we’re now paying the price. There’s absolutely no security. Anyone with a few thousands of dollars can create a VoIP phone company. And that means anyone can set that Caller ID to whatever they want.
Your local phone carrier has no idea who is behind a particular call when its outside of their network, and all of these spam calls are. The dialer is usually located somewhere in the Caribbean out of reach of United States law enforcement. The voice recording is usually from another company based in the Caribbean. When you press 1 to talk to a representative, the call is routed not to a call center, but to individuals working from home reading off a script. These representatives can be working for multiple scammers.
STIR/SHAKEN is an attempt to add proven identity behind Caller ID. AT&T and T-Mobile have both implemented it. I think Verizon and Qwest will have it in place by June. That’s all of the Incumbent Carriers and the major cellphone companies. However, that doesn’t handle all the various VoIP phone companies that many people now use. That’s the issue.
According to the regulations all CIN (companies that actually have the power to dole out phone numbers) must have STIR/SHAKEN installed by June. However, many carriers get numbers from other companies (or via porting). They can’t set the Caller ID via STIR/SHAKEN because they can’t produce the security certificates needed.
There are literally tens of thousands of companies out there passing out phone numbers, providing phone service, and switchboard operations. It’s a big mess that no one controls. STIR/SHAKEN will take a while to work. You’ll probably start by seeing some sort of number verification next to the phone call. Later, you’ll be able to block out people whose number isn’t verified like you can do with the current Silence all callers.
Of course, once everything is working, spammers will probably find another way around the entire process. That’s what happened to services like Nomorobo. They used phone numbers as a means of blocking spammers, so spammers simply use random phone numbers that aren’t blocked.
This is a lot of great insight. I would add that I am rarely sympathetic to carriers, but here, the regulatory framework has made it dicey for them to block calls, because they are obliged to carry all calls except in limited circumstances. One of the only sensible things the former FCC Chair did was to provide more explicit permission for carriers to engage in call blocking across their network if they adhered to certain standards. The other thing is that all these spam-detection apps from carriers appeared—mostly free—because carriers are allowed to block when customers request it, and then they can use those signals on calls that members are blocking for better network filtering.
It’s true, but the point is always removing low-hanging fruit. On 1 July 2021, all the major carriers and VoIP providers will have to have STIR/SHAKEN in place, but there are a ton of exceptions, mostly relating to smaller carriers and infrastructure providers. Spammers will certainly move there—but because these companies are smaller, they will lack the technical and legal resources when the carriers target them as spam sources.
To some extent this happened in web hosting, where big hosts got smarter about not allowing spammers to sign up, forcing spammers into worse and worse places, until they’re more easily blacklisted and blocked. It’s didn’t stop phishing pages and the like, but the transition into ransomware is one outcome of it being harder to scam people via web pages. (That’s my theory at least! There are a lot of reasons ransomware thrives, but it all comes down to “the currently easiest way to get people’s money without their understanding or permission.”)
How does this apply to MVNOs? In my case, I pay Boost, which Wikipedia tells me is owned by Dish, and I understand my calls were routed on Sprint which is now T-Mobile. Does Boost need to have 100,000 lines to be required to have STIR/SHAKEN or would it piggyback on T-Mobile?
For what it’s worth, I silence unknown callers, I have not seen the checkmark indicating a valid caller ID (but I get very few valid calls), and I have seen “Scam Likely” in place of the phone number on many occasions.
Does the prevalence of spam calls vary by where you live? Reading the comments here, people seem to get far more spam calls than anyone I know. I get maybe one or two a year. I don’t know if I’m just lucky or if there are dynamics that make some countries more susceptible to spam calls than others?
The STIR/SHAKEN protocol requires heavy processing and thus suffers scalability challenges. Especially if it ever extends beyond the network boundaries of the US telephony carriers. Considering the low value/revenue per call it may come to a point where the cost of processing a call through the STIR/SHAKEN protocol is too close to the value of the call itself.
I get more unwanted calls on my landline than on my iPhone. I tamed the landline by move it to Anveo and then setting up a workflow so only calls from people in my address book can reach me. I am now giving out my landline number more often.
My biggest problem on my iPhone is Marriott Hotel and auto warrantees but fewer than once a day. I get occasional notes from Verizon about blocking various calls as potential spam, the phone didn’t even ring.
But anything that improves the situation without requiring more work by the phone owner are welcome.
Maybe it won’t. I’ve lived and worked in several European countries. And in some of those spam calls are essentially non-existent. So I’d wager at the end of the day this is a regulation issue, not a technical problem. If I’m a country that has well regulated telcos and no spam problems, why would I go through the trouble of incorporating a tool that does nothing for me and comes from a place that’s spam hell compared to my paradise. I’d laugh them out of the room and tell them to go look up “regulation” in a dictionary.
What drives me up the wall is our office phone (which is from 8x8). Nearly every single call I get on it is spam, and because of working from home it either forwards to my cell or the 8x8 app handles it on my laptop (and the spam features on it re terrible). And as it’s a work phone you have to answer it. It’s got to the point I never say my name on the phone just in case they are trying to record it to get into my back account.
I also use 8x8 but it hasn’t been so painful. Normally, if callerID doesn’t show up I don’t answer. In my case most unwelcome calls are people trying to sell me something. If I was a salesperson or a job dealing with the public then I would feel obliged to answer every call.
Why don’t you have the 8x8 app installed on your cell phone? One advantage is that the button/slide associated with 8x8 incoming calls are blue so I know it is a work related call before I answer.
Yeah, so spam tools beyond making it easy to block phone numbers. Which is handy for me, some day I will block every phone number associated with Compare Business Solutions.
I have it on the cell too, but it’s not a particularly good product (try getting rid of the text spam). As I work for a physics magazine though we sort of have to answer all the calls, even if we think it’s dodgy. I still remember one Nobel Prize Winner who got irritated that I put him on voicemail…
Do be clear about 8x8 it’s supposed to have spam filtering it just doesn’t seem to do a very good job at it.
I will have to ask, 8x8 never mentioned spam filtering to me. Nor did any of the other competing office phone products. I will ask my communications agency about this issue since they are better at putting pressure on 8x8 than me.
A few months after getting 8x8 we started getting a few spam messages and I thought here we go. But it is rare for us and we have everyone’s contact info on our web site.
I don’t think STIR/SHAKEN will extend beyond the network boundaries of the USA.
In Europe spam is regulated, though it still exists. I’m currently involved in an interesting attempt to mitigate fraudulent calls between European carriers using blockchain and ZKP to meet GDPR requirements.
As part of my job I am also carrying a Hong-Kong cell phone (eSIM as a second number on my iPhone) and I was getting hit every night by spam calls on that number. No matter if I put my device on DND, they will call twice so it rings on the second call. I ended up using an app that simply adds all the HKG spam calls to the “blocked numbers” list on my phone. The database is updated almost every day and as a token of appreciation for my uninterrupted sleep I have paid for the app (well worth the few bucks) and even got rid of the ads. So this is a specific country solution by a third party.
T-Mobile just announced that it’s on board…
We are peculiar here in the US in how we don’t protect people, but we allow scams to flourish. Email is the global exception, for sure. But with the phone industry, we have had both the common-carrier exception (carriers aren’t allowed to differentiate calls on their network) and the supremacy of the free market (companies will be responsive to their customers because they would lose the business…missing the idea of monopolies, combines, and so forth).
Interesting to me, T-Mobile broke the wireless market by refusing to play by the rules under their previous CEO, and his actions and aggressive pricing broke a bunch of different elements: costs fell, data limits rose, and features rose, as well as networks becoming faster.
Here in Norway we have been targeted by a lot of different spam calls. In periods it has been a nuisance. Just recently Telenor (Norways biggest telecom operator) made a statement that they had made it more difficult for the spammers. In my translation they write: “Simply explained, the new system uses network information to find out if the Norwegian mobile number that is calling belongs to a mobile that is actually located in Norway. If it does, and the calls still come in from abroad, the call is considered spoofed. It will then be turned into a hidden call, regardless of whether it is spoofing or wangiri.” No mention of STIR/SHAKEN. I can confirm that now I only get the local unwanted calls from real Norwegian business selling insurance, telecom, electrical power and so on. I use Silence unknown callers to handle them. After searching Google I found this: Telenor Norway Deploys Hiya to Stop New Wave of Fraud Calls Targeting Norwegians | Business Wire Do you know what this Hiya solution is @glennf?
The problem with Telenor’s simple approach is that there are perfectly legitimate reasons for this “spoofing” as well.
For instance, a previous employer of mine used VoIP software on a laptop PC to implement employee phone numbers. A call to my number would ring the software no matter where in the world I was at the time. And calls I place from that software would show my number on caller ID, no matter where in the world I was at the time. There were many many occasions where I was in a foreign country on a business trip making and receiving calls via that software - all of which originating/terminating with my (US) phone number.
More recently, I was on vacation in Italy. I enabled Verizon’s Wi-Fi calling feature on my iPhone to avoid roaming charges. All calls I placed had my phone number, even though I was physically located in another country.
None of the above calls were spam, none should have been blocked, but they were all “spoofed” by Telenor’s standards, since the country/area code of the caller ID did not in any way correspond to the location where the call is terminated.
Yes! Hiya has been working with carriers for several years, and powers multiple carriers’ engines for blocking and marking calls before they reach customers. Hiya also has an app that has a free and paid version for iPhones. I finally ponied up after years for the subscription version because it provides reverse number lookups on the incoming call screen. See Hiya.com.
Telenor has a app called “Se Hvem” it translates to “See Who”, guess that is powerwed by Hiya engine.
Nice coverage of STIR/SHAKEN!
I’m actually involved with implementing STIR/SHAKEN at the carrier where I’m employed. Let me just add a few notes that might be helpful.
(Haven’t read all the comments, so apologies if this was already mentioned).
I think of STIR/SHAKEN for spam calls as being a lot like Domain Keys for spam email. DK places a responsibility on the carrier originating the email to cryptographically sign the body and headers of emails going out, including the From header, so you can trust the email came from who it says. Then the receiving mail carrier can use a public key to check to make sure the email is authentic (including not tampered with) before dropping it into your mailbox. And they can stamp it with some type of indicator header to that effect.
STIR/SHAKEN basically does the same for phone calls.
This leads me to my second point.
Just knowing a caller is who they say they are doesn’t block the call or really help you much at all unless they really did spoof a CallerID that you know. I find those calls to be a tiny fraction of spam calls.
So to help add some real value, some carriers are implementing features that go above and beyond what is required by the STIR/SHAKEN mandate by offering Robocall Mitigation and Reputation Scoring. These extra features check the CalledID against a (typically shared) database of statistically bad offenders and so give the call a reputation score. They can then use this score to replace the Calling Name that displays on your receiving device with something like “Spam Risk”. Or they may block the call completely if the reputation is super low. This is, again, very similar to the Real-time Blackhole List (RBL) that many ISPs like us subscribed to 20 years ago to block spam email.
This is when you’re really reaping the benefit of STIR/SHAKEN. But you can see that Robocall mitigation and Reputation Scoring are useless to try to implement if someone can pretend they’re someone else, and therefore steal their reputation. That’s why getting a system that allows us to trust CallerID, as STIR/SHAKEN does, is foundational for all these other cool features.
Very excited to possibly be moving towards a more trustworthy phone network!
Sure, this has been true for decades not only of CLECs but also ILECs (incumbents like Verizon) and IXCs (inter-exchange carriers like AT&T). This isn’t fraud. It’s how carriers compensate each other. Remember, traditionally you only got billed for outgoing calls. But it takes just as many resources (in some ways more, for determining Calling Name) to terminate the call. So the carrier that terminates the call for you is allowed to ask your phone company for tiny per-minute $.
You’re right that traffic pumping, as it’s called, has been used by some rogue carriers to generate tons of reciprocal-compensation income. We have seen it :-). But I don’t think the major carriers we’re all talking about here are likely to be driven by those goals.
It is called an iPod Touch:
So cell and VOIP phones are covered by this, correct? What about plain old landlines?
All US phone lines. The emphasis is on wireless, because that’s where the growth is and the majority of lines now; VoIP is called out, because some providers are the source of the problem; and landlines used to be somewhat left out of Caller ID (highly variable), but they’re a key component of it too. It’s just landlines are…fixed! So it’s easier to identify a landline as a verifiable component: it comes from a particular wirebase run by a particular carrier.
I haven’t seen ANY form of verification on my landlines whether AT&T in CA or CenturyLink in AZ. Also Robocallers start their speel as soon as my answering message begins even though the first part is the “Disconnected Number” SITs.
Fortunately after several years of my anti-telemarketing message, spam callers are greatly reduced; mainly they are the robocallers and the RNCC.
Uh, no. I wanted to be sure with enough examples before I answered this. (T-Mobile, more ‘extended warranty’ spam calls.)
The biggest problem is that carriers have no idea where VoIP calls originate. There are laws against calling cellphone numbers for unsolicited commercial purposes or for calling someone on the Do Not Call registry. Unfortunately, with spammers hiding behind fake numbers, there is just no way to prosecute these callers.
However, once STIR/SHAKEN happens, phone companies will know the calling party or the company that gave out the number (since they’re the ones who must verify the call). These bad actors can be sued and blocked.
I imagine once we have 80% of all calls verified via STIR/SHAKEN, the phone companies can offer spam blocking services. For example, T-Mobile allows me to block all calls T-Mobile has determined to be Spam Likely. I don’t have to. It’s up to me.
I can imagine the phone companies giving you the option to block all unverified calls, and maybe let me block calls that rate a certain chance of being spam. Maybe rate calls on a scale of 1 to 5 of dependability, and I can choose to block all calls that rate less than a certain number.
This is probably exactly where regulation fails here in the US. The law can require carriers to complete every call, even those coming from some untrusted VOIP source. Such law can make sense since we don’t want carriers determining if they should complete a call depending on how much the source of that call is willing to pay them. But at the same time it makes no sense to say that a call from each and every VOIP source has to be completed because that will certainly be exploited by bad actors, especially if they are far outside the regulator’s reach. But I submit that there is room for a reasonable middle ground here. A regulator could essentially have a list of “trusted” VOIP sources for which carriers are required to complete calls. Regulators then have a stick to use against shady operators and their enablers, especially those abroad for which the FCC here has no direct legal recourse. If they can threaten taking somebody off the list for which calls have to be completed, that should get most actors to fall in line rather quickly. At the same time it requires domestic VOIP operators to get their house in order. If you allow bad customers to use your service for spam, you are putting your good customers at risk of getting cut off too.
In the current environment, the carrier has no idea who the source is and whether they’re trusted or not. All they get is that a call is coming through and that they have a Caller ID.
STIR/SHAKEN will verify the Caller ID. The carrier could still put an unverified call through, but with enough carriers using STIR/SHAKEN, they could let users know the call isn’t verified. T-Mobile does this now. I get a tiny check mark by verified phone calls. Once all the major carriers are on board, T-Mobile told me they’ll switch from marking verified calls to unverified ones, and make it more obvious.
Right now, if T-Mobile determines a call is spam, it displays Spam Likely on my Caller ID. I can then reject the call if I do desire. And I can configure my service to automatically reject all such calls, so I never hear my phone ring. I imagine they could offer a similar configuration for unverified Caller IDs or calls from a service that is known as a spam source.
The carrier is still putting the calls through and giving me the option on how I’d like to handle the calls. My choice is to tell T-Mobile to ignore them.
Once enough carriers use STIR/SHAKEN, it’ll get smaller Voip players to also use it. I had an email service that ended up on a spam list. When I found too many of my emails getting rejected, and my service didn’t want to do anything about it, I switched servers. I imagine a small voip carrier will face a similar dilemma. Either implement STIR/SHAKEN or lose customers.
I agree with everything you said!
Yes, for prosecution, STIR/SHAKEN definitely helps. I guess my point is that for every spam call that heads towards prosecution, there will probably be 10,000 that will be nothing but annoying. The fact that the CallerID is trustworthy for those calls doesn’t mitigate you being annoyed ;-) But when carriers implement Robocall Mitigation and Reputation Scoring, then we really benefit as users. Kinda like the Junk Folder in Gmail, as you also said.
And this is the way it should be. Some people may want to receive these calls. Maybe they’re pedantic about answering every call or maybe they don’t trust the verification system, but they should always have the option to receive their spam if they want to.
Additionally, completely blocking calls (of any kind) without giving the customer a choice may cause a service provider to lose “common carrier” status. This could open them up to all kinds of legal nightmares, like being legally responsible for the content of every call carried on their network.
Off-topic. When I read this thread, I get a cookie from T-Mobile. Why is that? I don’t click or even hover on any links, but a cookie from T-Mobile shows up.
There is a reference to an article earlier in the thread that loads a T-Mobile image. They are likely tracking that. Gotcha!
Same way Facebook, Twitter, etc track you even if you don’t have an account. Your browser fingerprint combined with data from other similar more cooperative sources identifies and tracks you precisely.
Thanks. I learn something new every day.
I was going to say I had no check marks at all, but after scrolling down 5 pages worth I finally saw some. Only from 3 people, all known contacts, but one is a family member so maybe it’s AT&T only authenticating AT&T at this point? With silence unknown callers on at this point most of the calls that come in are through my Google Voice or Vonage Home numbers anyway…
Interesting thread. I have both a VOIP “landline” and a mobile iPhone. The mobile is rarely used.Silence iunknown seems to do a good job of cutting off spam, FORTUNATELY I am NOT being charged minutes (very economical plan for very little use!). Frequency is may 3-4 per month.
It’s my main VOIP phone that can ring up to 4 times PER DAY. Sure, if I do NOT know who is calling, I just let it ring. BUT that also means I get to listen to maybe 20 rings every day.
Now for the life Ime I can NOT imagine ANY entity needing such a HUGE volume of outgoing calling for any legitimate reason. What business needs to make 400 outgoing calls every minute (that’s a wild assed guess!)? First question is whatever carrier they are connecting to KNOWS this customer is using a FAR larger than normal amount of outgoing calling. THEY whould be raining this in… but due to $$$ my guess is there is no incentive to prevent this affront to their end customers. So laws and regulations… BUT I WOULD love to have you folks poke holes in my speculation.
The FCC moved the date up for STIR/SHAKEN for smaller VoIP providers due to abuse by spammers. Maybe this will cut down on robocalls…
FCC says it closed a loophole that many robocallers used to evade blocking
Starting today, small carriers must use STIR/SHAKEN Caller ID authentication tech.
Apparently what the FCC does has little effect because DOJ doesn’t pursue enforcement.
FCC Robocall Enforcement A Feckless Mess, Experts Once Again Tell Congress
We’ve long noted how absurd it is that scammers, debt collectors, and greedy telemarketers have ruined our voice communications networks. We’ve also noted how a big reason our robocall …
Enforcement depends on what will make the best return in actual revenue (a.k.a “fines”) or the better political headlines.
Hmm well I’m not sure lack of enforcement is a problem here.
I’ve been personally involved in implementing STIR/SHAKEN at the carrier where I work. And you don’t mess with the FCC. They can put you out of business (unless maybe you’re Verizon or AT&T who can throw their weight around). Fear of an audit is enough reason to make sure you’re compliant.
Plus, I’m not surprised there hasn’t been much enforcement yet because authentication is new. Without the new tech, carriers didn’t have the needed tools anyway. It was like having an entire class of 30 rowdy kids: you can’t send them all to the principals office.
But now we have tech that can clamp this down and requirements governing it. The next year or two should start shifting call spam problems.