Add Two-Factor Codes to Password Entries in iOS 15, iPadOS 15, and Safari 15
Raise your hand if you’ve avoided enabling two-factor authentication for websites that offer it because it’s too much of a hassle to launch an app, find the appropriate site entry, copy a six-digit code and paste it in whenever the site requires that you validate yourself beyond your password. Apple feels your pain, and the company has a new streamlined way to reduce the friction in entering these short-lived codes.
Two-factor authentication significantly increases Internet security because it prevents attackers from easily hijacking online accounts. Even if you use a password manager to create strong, unique passwords for every site, passwords are still vulnerable to theft or interception. When a website’s login process requires a second factor—something you own or control, like a smartphone, tablet, phone number, or computer—you don’t have to worry about a stolen or intercepted password being sufficient to compromise the accounts.
Many sites want to use an SMS message (or a phone call) as a second factor, either defaulting to it or offering it as a secondary option. The problem is that a texted or spoken code doesn’t provide the assurance that the recipient is the party that has access—only that they have a phone number. It’s far too easy to hijack a phone number. It can be done via social engineering (talking a rep at a telecom firm into switching the number), flaws in how telecoms manage numbers, and hardware-level exploits across the telephone system.
While text and voice calls are better than not using two-factor authentication, they are relatively weak. Even as services are increasingly also supporting authentication apps or proprietary systems—like Apple’s two-factor authentication approach—many still fall back to weak SMS and voice calls.
A much better form of two-factor authentication is a shared-secret method called a Time-based One-Time Password (TOTP). Most sites that support two-factor authentication don’t require a TOTP but let you add it to an existing account. During the enrollment process, the site creates a seeding secret using its TOTP software, which it stores for your account and then shares with you. This seeding secret is typically displayed as a QR code for easy scanning, though some sites also show it as a hexadecimal-encoded number.
Setting up your side of two-factor authentication via TOTP is usually harder than enrolling at a site. You can add a TOTP secret and generate TOTPs with a standalone app like Google Authenticator (which doesn’t sync between platforms) or Authy (which does, securely), or as part of a password management tool, like 1Password. But given that only a small percentage of users rely on third-party tools, built-in TOTP support in Apple’s operating systems could drive much higher usage.
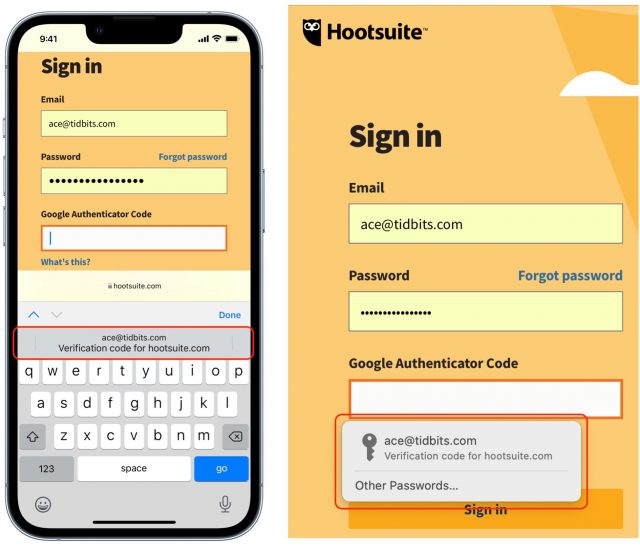
With iOS 15, iPadOS 15, and Safari 15 in macOS, that support is now in place. The updated Passwords interface bakes in the basics of password management for everyone. You work with passwords and TOTPs in Settings > Passwords in iOS 15 and iPadOS 15 and in Safari > Preferences > Passwords in Safari 15 for macOS. (Passwords won’t become a first-class macOS citizen until macOS 12 Monterey ships, at which point you’ll be able to access it in System Preferences > Passwords.) When a site or app prompts for a code later, it appears in the iOS/iPadOS QuickType bar or as an auto-fill prompt in Safari.
The ease of adding these second-factor codes and then generating them as needed should help increase usage and decrease frustration. It also makes it far easier for you to teach others how to use two-factor authentication with a minimum of fuss.
Add a TOTP
In iOS 15/iPadOS 15 and Safari 15 for macOS, once you’ve stored a password in Passwords, the easiest way to add a TOTP is with a QR code presented during enrollment:
- Go to the website or service for which you want to add TOTP verification and run through the process until you reach the QR code. (For instance, with Google, once logged in, click your image in the upper-right corner of a Web page, click Manage Your Google Account, click Security, and click 2-Step Verification. Enroll in authentication and select iPhone. You can also practice using this article, which has a non-functional but legitimate TOTP QR code.)
- In iOS or iPadOS, touch and hold the QR code to bring up a menu of options and tap Add Verification Code in Passwords. In Safari for macOS, Control-click the QR Code and choose Set Up Verification Code.
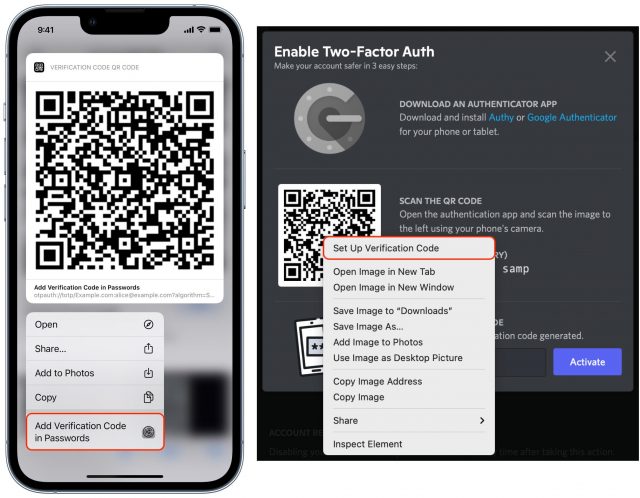
- Depending on what logins you already have stored in Passwords, you’ll be presented with one of three choices:
- A single matching account is shown, and you’re prompted to add a code to that.
- If multiple domains match, you’re asked to select or search for the correct entry.
- If no match can be found, you can search your stored passwords.
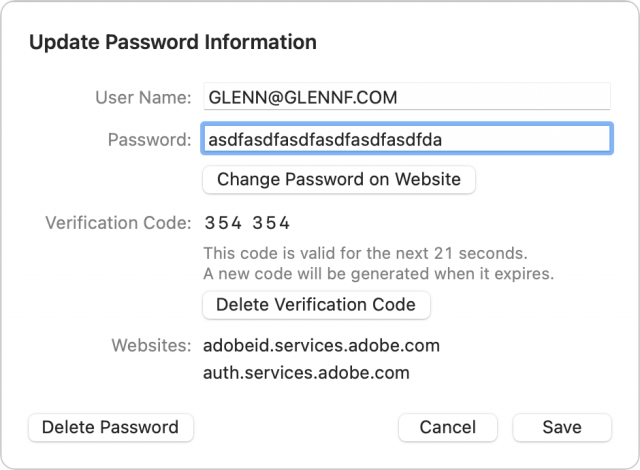
A code now appears in the Verification Code area.
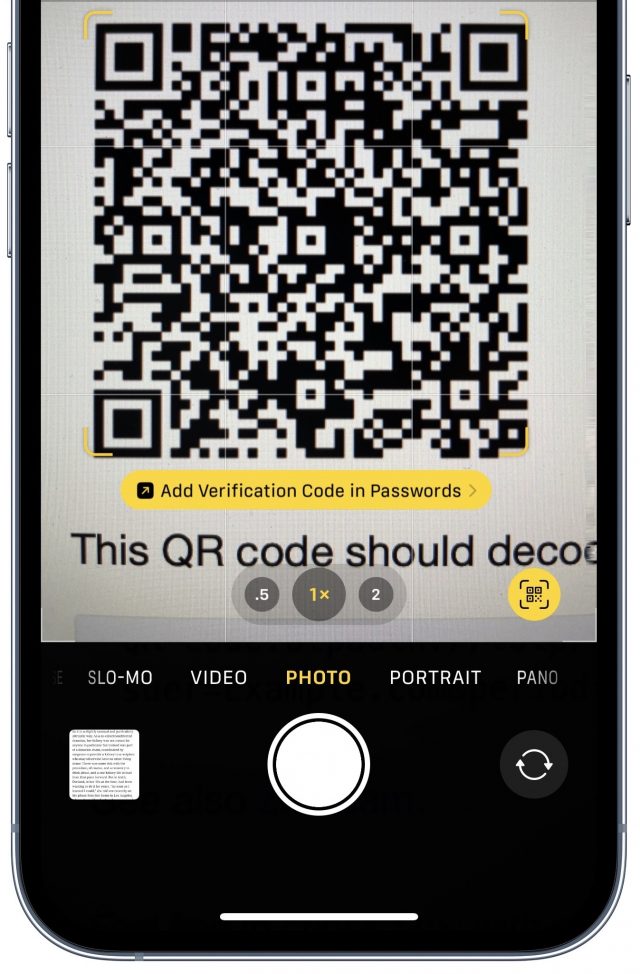
If you can’t load the QR code directly within Safari in iOS/iPadOS, you can instead scan it with the Camera app, which recognizes the type of QR code and offers the same prompt as in Step 2 above.
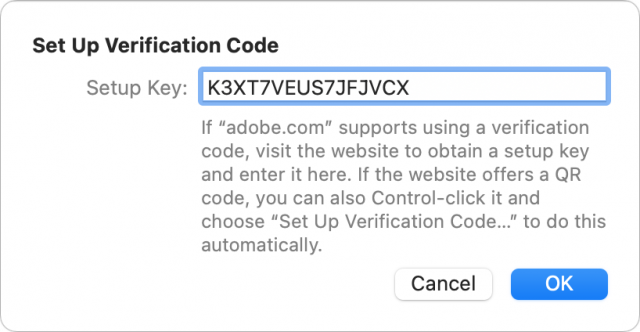
You can also set up a TOTP through other methods. Go to Settings > Passwords in iOS/iPadOS or open Safari > Preferences > Passwords in Safari for macOS. The path bifurcates here, but in both cases, you can use a TOTP’s secret if it appears on the enrollment page.
In iOS or iPadOS:
- Select a password entry.
- Tap Set Up Verification Code.
- Choose either Enter Setup Key to enter the shared secret or Scan QR Code to point at the QR Code as above.
In Safari for macOS:
After adding a TOTP, you will likely have to verify that you possess the correct code to finish enrollment.
These codes sync with the rest of a password entry’s details across your devices if you have iCloud Keychain enabled.
Unfortunately, you can’t migrate TOTPs from another app or ecosystem to Apple’s: authentication apps and systems don’t allow exporting the seed codes. Authy’s support documentation says, “In order to maintain security for our users, the Authy application does not allow importing or exporting 2FA account tokens.” Most sites also don’t let you re-display the TOTP enrollment process.
Thus, to switch from whatever you’re using now to Apple’s system, you’ll have to disable and re-enable two-factor authentication for each site or, if the site supports it, regenerate the seeding secret.
What if you want to try Apple’s system but maintain whatever app you’re using now? In that case, after you disable and re-enable two-factor authentication, you can scan the QR code or enter the setup key manually in multiple systems, one after another. Just add the QR code to Apple’s system, and then, while it remains onscreen, scan it with Authy or 1Password or whatever. You could even take a screenshot of the QR code for later addition into another app, but be sure to delete it permanently afterward, as retaining it in that unprotected form may increase your security risk.
Enter Your TOTP Code
After you enter the correct username and password for an account protected by two-factor authentication using TOTP, Apple’s software automatically recognizes the field and gives you another way to enter the automatically:
- In iOS and iPadOS, Apple automatically presents a verification code option in the QuickType bar when you tap in a field requesting the TOTP code. Simply tap the item in the QuickType bar to fill the field with the six-digit code.
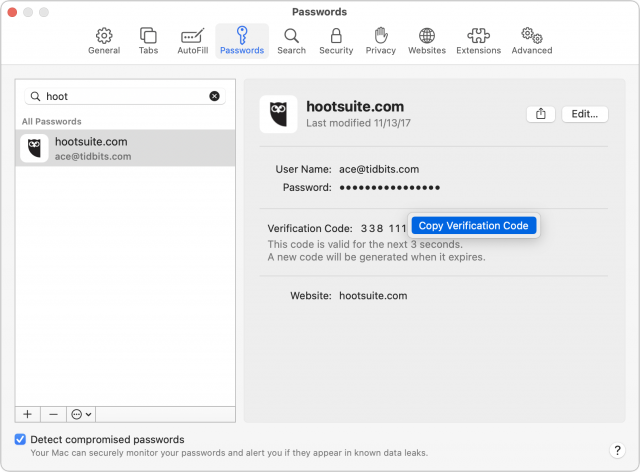
- In Safari for macOS, the app may automatically select the field and offer the verification code option as a button you can click, or you may need to click the field to get that auto-fill option to appear. In either case, click it to proceed.
If neither of those automated options happens, open Safari > Preferences > Passwords, find the password entry, and click the username, password, or verification code to copy them for manual pasting into the login form. Some sites make it hard to log in.
TOTPs Are Tops
TOTPs are a robust way to validate your identity as the only person who should be allowed access to an account because you’re sending a cryptographically generated code that requires possession of a secret and that doesn’t pass in a useful form through any other communication systems. The only way for an attacker to acquire a TOTP would be to hijack it from someone who can generate it and then enter the code within a minute or so—a high bar—or steal and unlock one of their devices.
Don’t make the mistake of thinking you’re not important enough to have your accounts hacked. With the seemingly constant breaches of major sites revealing millions of usernames and passwords, attackers are automating how they test which accounts they can compromise. Two-factor authentication ensures that protected accounts remain safe from this kind of wholesale attack and from many targeted ones. If you can avoid phone-based codes and rely on TOTP with Passwords in iOS 15, iPadOS 15, and Safari 15 for macOS, you’ll have the best combination of security and ease of use.
To learn more about securing your iPhone and iPad and preserving your privacy, check out the latest edition of my book, Take Control of iOS & iPadOS Privacy and Security, now updated for iOS 15 and iPadOS 15.
I assume this syncs across platforms (MacOS, iPadOS and IOS) for all devices logged into the same Apple ID? I don’t think that was made clear in the article (though I may have missed it).
It syncs via iCloud Keychain like all other passwords and associated details if you have iCloud Keychain enabled. But we did not mention that!
…and now we’ve updated the article. Thanks for the catch!
I’m surprised apple would do something like this. Doesn’t this completely defeats the purpose of having 2 factors? When they are both stored together and autocompleted by the same system?
It’s not obvious, but it doesn’t violate the principle: something you know and something you have:
The Apple verification code in Passwords is much more reliable than an SMS as a result. You have to have an iPhone, iPad, or Mac, be able to unlock it, and be able to validate your access to the code with password, Touch ID, or Face ID as well.
But if somebody has your password, they can use it both as the password and also to get the token, right? Isn’t the problem that Apple is putting the token beind the same system that also safeguards your other password? In that sense the two are no longer independent. Sure, initially the secret was exchanged and linked to you. But if now in the meantime your password has become compromised and somebody else claims to be you, how does this system stop them? I realize SMS can be a problem (if you cannot protect yourself from SIM hijacking), but at least there it appears the two systems used for authentication are entirely independent. A phone number and an iCloud account. Same goes for the little code generator fobs. But having your password locked by the same system that is locking your second token? Not sure how that can be considered 2 independent factors.
No, because the items stored by Apple in a local keychain are only accessible on the device and only with an administrative password on a Mac (or in some cases, Touch ID), or the device password, Touch ID, or Face ID (depending on circumstances) in iOS and IPadOS.
If iCloud Keychain is enabled, there is no access to password entries, including the stored secrets for TOTPs, except on validated end-point devices: any of your iPhones, iPads, or Macs. To add a device to iCloud and have it gain access to iCloud Keychain or enable iCloud Keychain on a device already logged into iCloud, you have to go through a validation process that requires entering the device password of another device in the set in order to receive appropriate encryption keys.
So the only way someone can access a stored verification code:
So I don’t see how someone can gain access to both the password on your device and the TOTP without the conditions above, which means that someone has heavily compromised you already. An additional safeguard would be not using Apple’s system, but a third-party one, like 1Password, and relying on a separate strong password to unlock the 1Password vault. But if someone has managed to obtain all your other keys and secrets, I can’t imagine that however you stored the 1Password secret (unless memorized), it wouldn’t be obtainable too.
Well with this system, yes.
But if you didn’t get your token from that same system, but instead from something independent like SMS or a code fob, you’d still have a fighting chance. When push comes to shove, I don’t know how much time I’ll need to set up new iCloud password, block accounts, or lock my stolen device. But I’d like to know I have given myself at least some, and not nothing at all.
I guess I just don’t like the idea of putting all eggs in one basket, even if that basket is very convenient. Personally, I’d prefer focusing on what fixes the other basket (so, for example, ensuring SMS tokens are safe because SIM jacking has been prevented) than getting rid of the second basket altogether. To that extent, in the US (where I suppose this problem is most prevalent) customers can ask T-Mobile to secure their SIM/phone number from transferral. I’d expect other carriers have similar systems in place. In two countries I worked in Europe I already knew nothing would happen to my SIM/number without me showing up with government photo ID in their store first. IMHO the way it should be.
There is nothing forcing you to add 2FA codes to iCloud Keychain, so, don’t. Use another method instead. Probably the safest for you is a fob or device such as a Yubikey. But Glenn’s response is correct. In order for somebody to gain access to your iCloud Keychain, there are a lot of hoops to jump through, and the iCloud Keychain is end to end encrypted; Apple even cannot access without the passphrase to one of your trusted devices.
I have one or two accounts with 2FA in my 1Password vault, just for convenience, but they are accounts I really don’t care about all that much. Most of my totp 2FA codes are stored in another way.
To answer this part, though all US carriers allow customers to add some sort of PIN to their account to prevent sim-jacking, there are reports of thieves who are able to sim-jack simply by bribing customer service agents when they call. So it’s not a perfect solution.
One of the nice things about using a password manager without 2FA is allowing someone take over your identity in an emergency or death.
In the case of LastPass, for example, you designate your executor as “trusted” in Emergency Access and specify how long you have to deny an access request. Then, when the time comes, all the executor needs to do is request access to your password vault and wait the specified time. (Obviously, the denial period has to be long enough that in normal situations you are confident that you’d get the request in time to deny it. The assumption is that if haven’t denied the request within this period, you must be incapacitated.)
For a better explanation, see:
How can you give your executor your digital legacy with 2FA turned on?
I have used TOTP authentication for many years now. At first it was just a few sites. When 1Password implemented it I moved over from Google Authenticator. As soon as a new site offers TOTP I add it to 1Password. I do not use apple key-chain except for wifi passwords. I wonder if the user interface with Apples password management is working better than 1Passwords. Is this a reason for me to move over TOTP sites to Apple’s password management?
One other thing. I guess Apple’s password management only works for Safari?
FWIW I’m now using this implementation to access 1Password.com itself
Smart, thanks for the tip!
Is the TOTP information included in password-protected iOS backups?
Great question. Password items are only included in encrypted local backups made via iTunes (pre-Catalina) or the Finder; they are not included in unencrypted local backups, nor in iCloud backups.
Keychain entries are only synced among devices using end-to-end encryption, so they’re not available in an Apple-encrypted form (only a device-encrypted one) on iCloud.com.
Oh, interesting. That makes sense—you need them backed up if you back up to the Mac and don’t use iCloud at all. But if you do use iCloud, as long as you turn on iCloud Keychain, they’re essentially backed up there, even if you have only one device.
Still too much work needed to use two-factor authentication for it to be worthwhile using. (But may change my mind if I get fully hacked – had to change passwords a few times, including Apple forcing me at one time for one account, and they had partly guessed a password in a phishing message, but nothing serious for the last 30 years – worst has been Yahoo refusing me to gain access to my own account, but no serious people has used them lately anyway …).
After the fact, accounts and ToTP managers do not give you ready access to the secret (which is encoded in the QR code). That’s because it’s highly risky to do so. However, I have several ToTP programs, some more convenient in some situations than others, and some don’t share across devices and OSes. And if a particular app ceases being supported, I want a fall-back. So recognizing that this is risky, I save the QR codes (or secrets) to print, and add them to all my ToTP apps. I store the printouts in a safe place.
It’s been quite a while since this article was written, but here’s some information that is new since it was written:
Google Authenticator now gives you the option to synchronize devices via your Google account. I keep it turned off, but you can do it.
Google Authenticator lets you export TOTP seeds. You select the ones you want to export and it generates a QR code, which you can scan from another device. This makes it possible to migrate codes to new phones/devices without needing to sync them through Google’s cloud servers.
You can also screen-shot that QR code if you want to archive a copy of your seeds. Of course, keep this image very secure, since it will grant an attacker access to any accounts secured by those TOTP codes. I keep a printed copy in a locked file cabinet for emergency use only. You could also use this to migrate from Google Authenticator to Apple’s system, should you not be able to import the code directly.