Apple Adds Lockdown Mode to Protect Activists and Government Targets
Apple has announced that a new Lockdown Mode will be coming to iOS, iPadOS, and macOS later this year to deflect attempts by government-level spyware to infiltrate the devices of targeted activists, protestors, journalists, and politicians. It’s the latest measure taken by Apple in its significant efforts to protect its users’ devices from being compromised and data taken without their knowledge or consent.
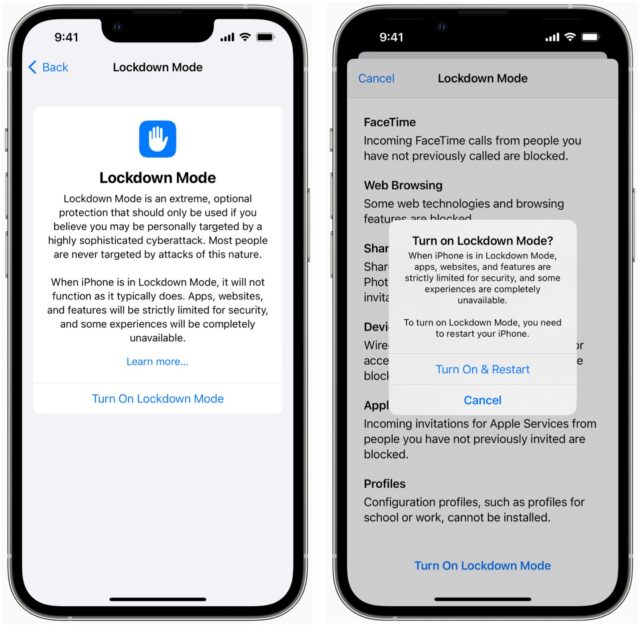
Lockdown Mode targets key points of weakness on always-connected devices that can connect to arbitrary servers around the world and be reached through Apple services, like Messages and FaceTime.
With Lockdown Mode enabled, you won’t be able to receive anything but images and text via iMessage and MMS; all other document types will be blocked. Messages also won’t preview links, among other not-yet-disclosed clampdowns. Plus, FaceTime and other Apple services that can receive arbitrary inbound invitations and requests will block everyone with whom you haven’t previously initiated a call or request. (The block doesn’t appear to cover anyone you’ve talked with before, only your outbound connections. Otherwise, someone who idly contacted you in the past as cover for a future hack would be permitted, among other scenarios.)
Those changes would have protected against the most recent severe exploit for Apple devices—a zero-day flaw, one that was exploited in the wild before Apple knew about it—which came through maliciously formed PDFs that bypassed Apple’s 2020 addition of sandbox security to Messages (see “BlastDoor Hardens iMessage Against Malware Assaults,” 4 February 2021).
Apple said that Lockdown Mode also prevents browsers from executing certain “complex web technologies,” a reaction to past exploits and concerns about likely future vectors. Users can opt to add sites to a trusted list. In Lockdown Mode, wired connections are blocked whenever an iPhone is locked; Apple didn’t mention iPads.
Lockdown Mode also blocks the installation of configuration profiles, which some attackers have exploited to intercept all data entering and leaving a device. Nor can devices in Lockdown Mode be enrolled into mobile device management, eliminating another known worry.
Apple has focused Lockdown Mode on users facing a known risk because it will limit some of what you can do on your devices. Even by that measure, tens of millions of Apple users worldwide could potentially benefit from enabling Lockdown Mode.
Consider, for instance, Russia’s aggressive arrests of any resident insufficiently patriotic regarding its unprovoked invasion of Ukraine. Suddenly, many people in a nation of nearly 150 million might have reason to worry about state-sponsored spyware. Likewise, in America, the Supreme Court’s recent decision overturning Roe v. Wade, coupled with law enforcement’s behavior in past abortion-related cases, has privacy advocates concerned that police may seize the text messages and digital activity of pregnant people seeking medical care.
Alongside Lockdown Mode, Apple also announced a $10 million grant to the Dignity and Justice Fund, a grant-making organization formed within the Ford Foundation’s New Venture Fund. Awards from this pool of money will fund “approaches to help expose mercenary spyware and protect potential targets.” This could include outreach and awareness, bolstering the security of human-rights organizations, and directing research into spyware. Apple said the fund will be advised by a committee of human-rights-oriented technologists drawn from groups like Amnesty International and Citizen Lab. Ivan Krstić, Apple’s head of security engineering and architecture, will also serve on the committee.
Lockdown Mode marks both an evolution and an escalation in Apple’s battle to balance compliance with legal government actions with illegal, extrajudicial, and criminal efforts to penetrate iPhone, iPad, and Mac security. Last year, Apple sued a major global government spyware supplier, NSO Group, for its alleged role in exploiting Apple products and services (see “Apple Lawsuit Goes After Spyware Firm NSO Group,” 24 November 2021).
Not all potential uses of spyware are inappropriate. NSO Group and similar companies consistently claim that the primary use of their products is to combat terrorism and human trafficking. Yet there’s no evidence of what Apple calls “mercenary spyware” aiding in such, while NSO Group’s Pegasus has allegedly been used to target journalists in Mexico, politicians in the Catalonia region of Spain, and human-rights activists in the United Arab Emirates, among others.
When Apple announced its lawsuit against NSO Group last year, the company said it would give $10 million to Citizen Lab and Amnesty Tech, part of Amnesty International, along with any damages it received if the company prevailed in its lawsuit. This new announcement doesn’t reference that grant, even though it notes the same sum and says damages from the lawsuit will be part of the pot it donates to the New Venture Fund. Apple should provide more clarity here—are these separate initiatives, or did the previous grant get folded into this new approach?
Lockdown Mode arrives in iOS 16, iPadOS 16, and macOS 13 Ventura later this year. Enabling it appears to require just a tap, a confirmation, and a restart. You can turn it off with the same simplicity.
Should you enable Lockdown Mode even if you’re unlikely to be targeted by state-sponsored actors? We suspect it will be overkill for nearly everyone and quickly become frustrating if you’re not worried about your personal safety. But as far as we can tell, there’s no harm in enabling it as a test or for temporary protection.
We’ll see how effective Lockdown Mode ends up being in the real world, but based on the early description, Apple has set a new high-water mark in its commitment to security in the unequal battle between governments and individuals.
A very interesting addition. I realize its present implementation is geared towards people who are at high risk or already under attack.
I wonder though, if by allowing for a more granular approach (say, allow only text and images to arrive in my messages inbox), this could be opened up to a larger crowd who knows they individually do not need their devices quite as open as perhaps others. More granular control I’m pretty sure could make certain parts of this far more accessible to ‘regular’ users such as myself.
Glenn - I recently heard a NY-Times (The Daily) story about NSO/Pegasus.
My question is: Isn’t possible for Apple to detect presence of this NSO spyware (and/or other similar spyware), and disable, and/or remove this software? If it is possible, why do they not offer this removing service?
Apple has taken steps in the past to patch vulnerabilities that NSO and others have used to infect iPhones, but NSO just finds a new vulnerability to use. Detecting and removing an already infected device is much more difficult using a software update and AFAIK has never been attempted. The only solution that I have seen is a Device Firmware Update (DFU), basically a factory reset.
Thanks for the note. It still seems strange to me that Apple appears to be unable to develop a more satisfying solution.
Rootkits by their nature are rather difficult/impossible to remove. I assume that Apple does do emergency patch releases to eradicate them as soon as they are aware of their existence and the vulnerabilities they exploit (these days there are often a chain of several vulnerabilities that are exploited).