TidBITS#1068/21-Mar-2011
If you’re using a passcode on your iOS device, you probably think your data is encrypted. Rich Mogull has discovered a common scenario that prevents encryption from happening, but luckily it’s easy to fix. In other news, Joe Kissell is tweeting his entire “Take Control of Your Paperless Office” book, Glenn Fleishman explains the impact of AT&T buying T-Mobile, and Michael Cohen looks at Time Warner’s iPad app for watching live TV. This issue also marks the kickoff of Adam’s four-part series about how he switched from Eudora to Gmail. Notable software releases this week include Mac OS X 10.6.7, Security Update 2011-001 (Leopard), Bento 4.0.2, DEVONthink and DEVONnote 2.0.9, and Yojimbo 3.0.2.
Make Sure Your iOS Device is Really Encrypted
Encrypting your data on your iPad or iPhone is a great way to protect yourself on the off chance you lose your device. Even if someone plugs your device into a computer, they ideally won’t be able to steal all of your data. On current iOS devices, encrypting is as simple as setting a passcode.
Encryption in iOS 3 and iOS 4 — I say “ideally” because it turns out to be a little more complicated than simply setting a passcode. Apple first dipped their toes into the encryption waters by including hardware encryption on the iPhone 3GS using iOS 3. That version was deeply flawed, since merely jailbreaking the phone enabled bad guys to bypass the encryption.
That’s because authorized access to the device would allow decryption of the data — something that happened automatically when moving data onto or off of the iPhone. All an attacker needed to do to compromise data was to jailbreak the device, after which the passcode could be avoided and disabled. After that, all access was seen as authorized and all the data was conveniently decrypted by the nifty new hardware chip. I first wrote about this in “iPhone 3GS Hardware Encryption Easy to Circumvent” (7 August 2009).
Apple fixed much of this with the release of iOS 4. In that version, some of your data is encrypted using your device passcode. Even if an attacker bypasses the passcode by jailbreaking, he can’t access protected data without knowing the passcode.
“Protected data” includes all of your email (and attachments) and data in any apps that link into Apple’s encryption. Other data on your device still isn’t encrypted with your passcode, so that might still be at risk (again, it depends on the app), but you probably don’t care if someone steals your Angry Birds high scores.
Just as in iOS 3, encryption is automatically enabled by default if you set a passcode on any iPhone 3GS or later device with iOS 4 or above. You enable this in Settings > General > Passcode Lock.
The iOS 4 Upgrade Encryption Loophole — Unfortunately there’s one case where you might have a passcode set, but your device still isn’t encrypted. I used to think this case was rare, but a show of hands at my Macworld 2011 iOS security session revealed that a fair number of attendees weren’t protected, and that’s a small sample of relatively technical users, suggesting that the general population might be even more at risk.
The problem can occur if you had a passcode set on an iOS device that shipped with iOS 3, and then upgraded your device from iOS 3 to 4, which is a common scenario.
To see if encryption is actually enabled on your iOS device, on the Passcode Lock settings screen, look at the bottom. If you see “Data protection is enabled” you are all set. If not, you need to make a small change that’s easy, if a bit time consuming (it depends on how much data you have on your device). Follow these steps:
- Disable your passcode in Settings > General > Passcode Lock.
- Back up your device by connecting it to your computer and, in iTunes, Control-clicking it and choosing Back Up.
-
Restore your device by clicking the Restore button in the Summary screen in iTunes. Note that several commenters have said that Control-clicking your device in iTunes and choosing Restore from Backup does not work in the same way.
-
Enable your passcode again, which turns on encryption.
Apple provides a nice support article with all the steps.
I always recommend that people set passcodes on their smartphone or tablet no matter who manufactures it. Since setting a passcode in iOS also encrypts the sensitive data on the device, we might as well take advantage of that extra encryption hardware chip.
The Impact of AT&T Buying T-Mobile
A giant corporation in a mildly competitive industry buying a smaller but significant firm never bodes well for prices. AT&T’s plan to purchase T-Mobile still must pass hurdles at the Justice Department (due to antitrust and other issues), the Federal Trade Commission, and the Federal Communications Commission. But assuming it goes through, we can expect higher prices — and better phone and data service.
From a technical and business standpoint, the acquisition makes sense. T-Mobile has lagged as the fourth player in the market for years, behind Verizon, AT&T, and Sprint Nextel, before and after Sprint acquired Nextel. Although its push into HSPA+ (a super-fast 3G flavor being advertised meaninglessly as 4G) put it ahead of the curve for a while, T-Mobile lacks sufficient spectrum and resources to compete on the same footing as the big boys.
AT&T and T-Mobile both use GSM technology for 2G, 3G, and 3G+ (HSPA+) networks, and AT&T has already spent billions to buy new spectrum for a closer-to-real-4G network that will use LTE. From a business standpoint, neither AT&T nor T-Mobile has any peculiarities, like the old networks and unusual technologies that still drag down Verizon and Sprint. (Those two companies use CDMA. Verizon is moving to GSM with its 4G LTE network. Sprint also runs another standard, iDEN, for its Nextel customers, and put its money into WiMax for 4G, which is proving to be the wrong horse to have bet on.)
With the merger, AT&T and Verizon Wireless would even more clearly rank as the giants of the U.S. mobile landscape. Sprint Nextel has many liabilities that prevent it from being nearly as competitive on price or services as T-Mobile is (or was), and it will have a smaller voice and 3G footprint than either a combined AT&T/T-Mobile or Verizon as well. There’s plenty of speculation that Verizon might buy Sprint, but Sprint doesn’t bring enough value to Verizon.
As a customer, you’re not likely to see any price benefit from the AT&T acquisition. T-Mobile has some of the cheapest national pricing for voice, data, and texting plans in any combination, sometimes $20 to $30 less each month than the cheapest competing plan. AT&T’s pricing tends to be in line with Verizon’s, and we’ll likely see most T-Mobile plans age out and new users or purchasers of newer phones be required to switch to higher-priced offerings.
That stinks, because as we already know, carriers charge a mix of reasonable prices for infrastructure-intensive services, like carrying voice and data, and egregious prices that are nearly pure profit for things like texting (which costs as close to zero as one may calculate), and mobile hotspots, which have no additional cost on metered or tiered plans. (Verizon may have a point in charging for a mobile hotspot on the iPhone because it offers unlimited service only on its phone-based data plan, and allots a separate data pool for tethering and mobile hotspot.)
The good news is that AT&T and T-Mobile customers will see an immediate and notable improvement in call quality and coverage area once the merger is approved. Both companies keep users on home networks as much as possible in areas where they provide service. Roaming happens only when one carrier lacks coverage, as was the case with AT&T in large parts of the Midwest and Northeast, among other areas. (In 2009, AT&T spent billions to buy spectrum in rural areas that Verizon was obliged to sell when it bought the number five carrier at that time, Alltel.)
T-Mobile’s 3G network rollouts were accompanied by a lot of high-capacity backhaul to the towers. The company most likely has a far greater percentage of its 3G-and-beyond network with the bandwidth necessary to handle the amount of traffic that’s possible. AT&T had lagged, and is still working incrementally to increase its backhaul capacity. Leaning on T-Mobile’s network will mean faster service for existing AT&T customers.
The two companies promise 95-percent coverage for 4G, which is far more than AT&T’s initial plans (or license requirements) for LTE deployment, scheduled to start in mid-2011. Verizon had already signaled its intent to reach into the hinterlands, bringing 5 to 12 Mbps downstream rates to people in fairly small towns and rural areas as well as the country’s metropolitan areas. Oddly, the greatest competition could be outside urban areas, where small wireless service providers, satellite Internet operators, and AT&T and Verizon would contend for customers.
The bottom line is that this merger will put more money in the pockets of cellular companies as a whole. If you already pay AT&T or Verizon Wireless prices, you likely won’t see a difference in the foreseeable future. But it also makes AT&T into a stronger competitive force against Verizon, which has used its larger network footprint to counter the faster speeds of both AT&T and T-Mobile’s smaller networks.
The acquisition could have an unintended consequence — but AT&T is pushing this message, so it may be wishful thinking. It could cause an increase in competition from regional mobile providers like Cricket, Leap, MetroPCS, and US Cellular, among others. These firms often have cheap prices and advanced features that work only in a limited number of urban areas. Roaming is expensive, if available. Still, many people may prefer the cheaper price as a tradeoff if they aren’t often outside of a home service area. The big providers became behemoths by providing everything to everyone. Niches emerge when the dinosaurs ignore the incoming meteor while furry mammals scurry around their feet.
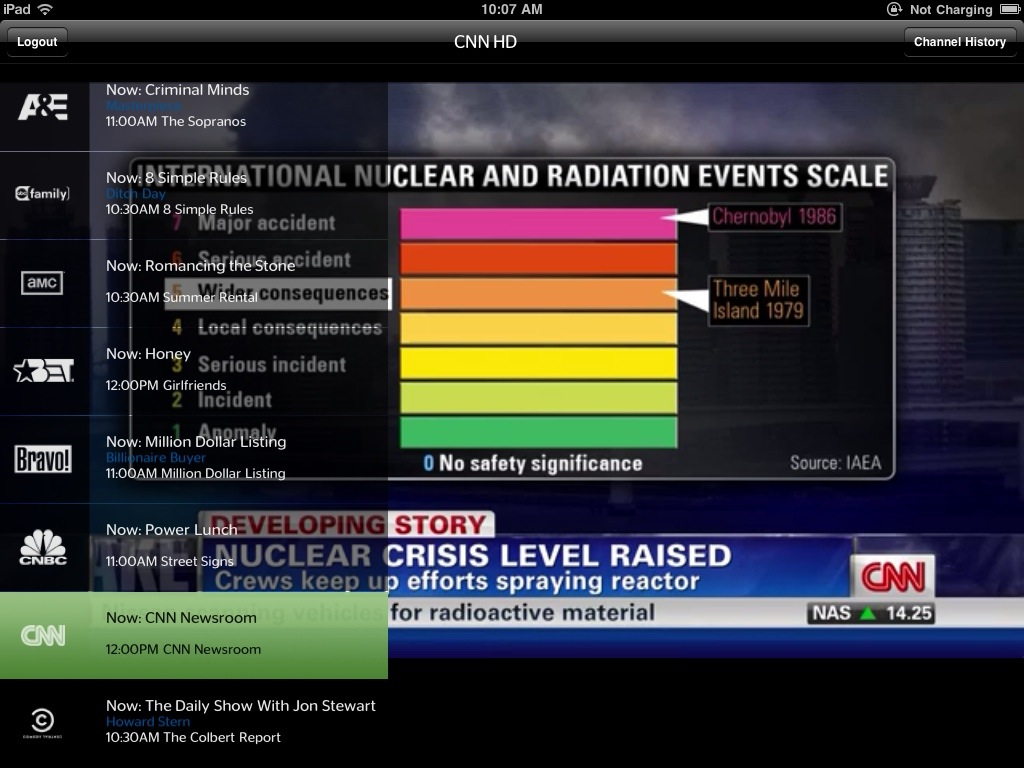
Time Warner Sprinkles Cable TV on the iPad
Obscured by the smoke and sparkles of the iPad 2 release, media giant Time Warner released a free iPad app, TWCable TV, aimed at current Time Warner cable subscribers. Compatible with both the original iPad and its sleek younger sibling, the app brings a bunch of Time Warner cable channels to the magic tablet’s oleophobic screen. That’s right, it’s live cable TV for your iPad.
The App in Operation — The app is designed to be as easy to use as a cable TV, or maybe even easier. Once the app is configured, just launch it, tap a channel, and watch. The channel selection palette appears along the left side of the display (which always appears in landscape orientation). You can easily reveal and hide the channel palette with a tap anywhere on the screen. If you want to play the channel-swap game as you would with a TV remote control’s Back or Jump button, tap the app’s Channel History button to reveal a list of the channels you’ve most recently watched and then tap a channel on the list to switch to that channel. If you close the app and later
reopen it, it starts streaming the channel you were watching when you closed the app, just like a TV.
That’s it in terms of app features. It doesn’t do anything other than play live TV and let you change channels.
Set Up Issues — The simplicity offered by the app is unfortunately not mirrored in the initial configuration steps you must follow to get it working. First, you must be both a Time Warner cable subscriber and a Time Warner Internet Service subscriber. You also have to have your Time Warner Internet service available via Wi-Fi. If your cable TV and Internet service meet these criteria, you’re good to go.
To sign up, you need to enter your Time Warner Cable user name and password into the app. If you don’t have a Time Warner Cable user name and password (I didn’t, even though I’ve been using the company’s Internet service for several years), you have to create them.
To create these essential credentials, the app takes you to the Time Warner site, where you have to choose a user name (an email address that you currently use) and a password that is at least eight characters long and that has at least one numeral in it, configure a couple of security questions to which you know the answers (such as “What is your mother’s father’s first name?”), enter a user code from your most recent cable bill and the last balance you paid, and verify the user name by responding to an email that Time Warner sends you.
In my case, the signup process was flakier than a well-made croissant, and nowhere near as tasty. To start, the Time Warner site repeatedly rejected a password I entered that met all of the stated criteria. After I had filled out all the required information, the verification email I received contained a link I had to click to confirm the signup: that link brought me to an error page. On that error page was an instruction to “Click below” for assistance, but there was no link to click! However, the verification error page was itself apparently in error because I was able to get the app to work with the user name and password that I had supplied.
My problems might be attributed to the fact that I tried to set things up on the app’s very first day of release. Apparently, the app was so popular that it brought Time Warner’s site to its knees on the first day, and also forced the company to scale back the number of channels offered temporarily from the promised thirty to about half that number. However, as I write this, I see twenty-eight channels listed.
Limitations — The app, now that I have configured it, works very well. But it does have its limits.
Aside from the lack of any viewing controls other than channel switching (for example, no pause capability, no AirPlay capability, no on-screen volume controls, no parental controls), the channel selection is constrained: the channels offered are basic cable channels only. You can’t view any of the premium services to which you subscribe, nor can you view any of the local broadcast stations that your cable subscription includes. These limits, I understand, are due in part to the licensing agreements that Time Warner has with its partners.
Furthermore, the app works only over Wi-Fi, and only within your own home. Were I to go on the road, I wouldn’t be able to use the app unless I were in a location with both Time Warner cable and Internet service, and I happened to have the login credentials for that location. The chances of that, of course, are rather small.
Musings — This app is certainly not The End of TV as We Know It. The limitations it imposes are major, and the functionality it offers is low. All it really provides is a portable TV screen you can carry around your home so that you can watch a fraction of the TV channels to which you have subscribed. Time Warner has worked hard to come up with the bare minimum of a cable TV app.
On the one hand, I feel rather disappointed and insulted: I pay quite a bit of money to Time Warner for my cable and Internet service, and the limits that the app imposes makes it feel less like a bonus from my service subscription and more like a begrudged handful of pennies tossed my way from a wealthy but miserly uncle.
On the other hand, I rather like having a very portable TV with a high-quality screen at hand any time. Like any TV, I often have it on while I’m busy doing something else (such as, for example, writing this article), and the channels it does offer usually have something worth watching at any given time.
As I implied above, there’s a lot more that I would appreciate in a live cable TV app:
- More of the channels to which I subscribe, including, especially, my local TV channels.
- Some basic playback controls: although this app is not a DVR (and I can accept that), it does do some buffering, and I would like at least a 30-second jump-back control and a pause button that could let me pause for a minute or two.
-
Parental controls: while I don’t have kids, my extensive research leads me to believe that other Time Warner subscribers do, and some of those subscribers even have children with iPads (shocking, but true).
-
More schedule information beyond the current show and the next show for each supplied channel.
-
The actual names of the cable channels, rather than just their current logos (the Comedy Central logo, for example, looks like a copyright symbol, and I had to tap it to see what channel it actually was).
Even though TWCable TV is the barest of a bare-bones cable-TV app, it may be enough. For now. I’d like more, and maybe, someday, I’ll get it. But I’m not going to hold my breath as I wait.
Joe Kissell Shreds an Ebook into Twitter
If you read TidBITS regularly, you’re probably aware of my ebook “Take Control of Your Paperless Office,” which was published in November 2010. Among the things I explain in the ebook is how you can scan paper documents and then recycle or shred the originals. But how do you shred an ebook? It’s easy: rip it into 140-character strips and feed it to Twitter! And so, I’m doing exactly that.
Adam and Tonya and I came up with this idea a few weeks ago during a conversation about how to have some fun spreading the word about the Take Control ebooks. Even though this experiment amounts to giving away the entire text of the book for free (if you really want to read the whole thing on Twitter), we figured that most people who become interested in the ebook because of this project would opt to buy a copy, thus getting the vastly improved readability of a proper book layout — not to mention access
to future upgrades. To sweeten the deal, Take Control is offering a 30 percent discount on the book to everyone who follows it on Twitter!
So, it works like this: Starting at 9 AM Pacific/12 PM Eastern on 21 March 2011, the book is being tweeted, 140 characters (or so) at a time on the account @zapmypaper. I decided on a frequency of one tweet every 15 minutes, at which rate it’ll take 17 days to tweet the entire 118-page book. From time to time, I’ll intersperse reminders about how to purchase the full ebook, suggestions to follow me on Twitter (@joekissell), and other tips. Interstitial messages that aren’t part of the book’s text will start with ==. For example:
== Tip: Support author Joe Kissell’s baguette and cheese habit. Buy this ebook at http://bit.ly/h2mPrl
Ideally, I’d like to refrain from sending manual tweets, @replies, and retweets from the @zapmypaper account during the period that the book is being tweeted, simply because that’ll keep the stream cleaner and make it easier to follow. However, if I do need to insert any special announcements or other tweets, I’ll use the same == convention at the start so you can tell they’re not part of the book itself.
After the entire book has been tweeted, my intention is to continue using the @zapmypaper account for news, suggestions, and questions about maintaining a paperless office, so those who follow that feed can get ongoing support for their paperless habit.
Tweeting with Style — If I were tweeting a novel or some other book that contained only plain text to begin with, the process would have been much simpler. But this being a how-to book on a somewhat technical topic, it included lots of elements that don’t directly translate into text. My goal was to preserve as much of the structure of the book as I reasonably could, striking a balance between faithfulness to the original and readability within Twitter.
I think I did a reasonably good job at that, although the conversion was slightly lossy — that is, one could reassemble the tweets into a rough approximation of the original book, but a few elements (and a tiny bit of text) wouldn’t come through. For those who are curious, as well as for the geeks who will inevitably write scripts to recreate the book despite my disclaimers, here’s what I did.
- Headings: The ebook uses different font sizes, weights, and colors to indicate various heading levels. In Twitter, I’ve converted them as follows:
- Heading 1:
**HEADING TEXT**(all caps, two asterisks on each side) - Heading 2:
*HEADING TEXT*(all caps, one asterisk on each side) - Heading 3:
HEADING TEXT(all caps) - Heading 4 and below:
_Heading Text_(title case, underscores on each side)
- Heading 1:
- Sidebars: I enclosed the contents of the sidebar, including its title, in double square brackets, like so:
[[sidebar text]] - Tips, Notes, Warnings, etc.: I enclosed the contents in single square brackets, like so:
[tip text](and note that the Twitter version doesn’t distinguish between the different visual styles we used for tips/notes and those we used for “emphatic” paragraphs). -
Paragraph breaks: I debated whether to do anything at all to represent paragraph breaks and if so, how. After careful deliberation and testing, I settled on using the paragraph symbol (
¶) to denote the beginning of each new paragraph. I decided against using actual line feeds because some Twitter clients don’t display them, and neither does the Twitter Web site — so some readers wouldn’t have been able to tell where new paragraphs began. (And, when you’re reading an entire book, I think that’s pretty important!) -
Graphics: The book contained a handful of screenshots; I’ve uploaded these separately and embedded links in the text.
-
URLs: I converted nearly all the external links in the book (except for a few very short ones) to bit.ly URLs for compactness.
-
Footnotes: The book had only two footnotes, and for the purpose of this project I relocated their contents into the main body of the text.
-
Character styles: Boldface, italics, colors, special fonts, and other modified character styles are simply gone.
-
Tweet length: Obviously every tweet must fit within 140 characters, but I went a bit further to ensure that tweets always break at word boundaries, and never end with, for example, a paragraph mark or bullet character. Also, I discovered that the Python script I use to send the tweets incorrectly counts certain symbols (such as
•,¶, and—) as more than one character, and rather than spend a lot of time trying to rework the script, I opted to simply leave a few extra characters free to accommodate these symbols on lines that contain them. The result is that some of the tweets will appear to be shorter
than they strictly need to be.
Beyond character styles, several other portions of the text didn’t make the transition to Twitter at all:
- The table of contents (because suggesting that you jump to the text on Thursday, March 31st at 4 PM EDT is just silly)
-
Portions of the front and back matter that make sense only in the original ebook form
-
Inline graphics (there were just a few of these)
-
Captions for the screenshots
-
Bookmarks and internal navigational links
How I Did All This — I don’t imagine a whole lot of people are going to want to go out and start tweeting their own books, but in case you’re curious how I pulled this off, here’s a quick overview.
I began by taking the Word file containing the complete text of the book and adapting it, using a series of Find and Replace operations to convert things like headings and sidebars into a format that would make sense in plain text (as described above). Once I’d gotten to the point where the file no longer had any data that was dependent on text styles, I moved it over to BBEdit, whose much more powerful grep-based Find and Replace feature, along with Text Factories that combine multiple text-manipulation actions into a single command, enabled me to do all the remaining conversion. I converted real paragraph breaks to ¶ characters, making the whole book one long line. I then set the window to wrap
at 140 characters and did a quick visual scan to look for any line-break issues my automated procedure missed (and there were a number of these). Once I had everything the way I wanted it, I used the Text > Add Line Breaks command to put hard returns back at the end of each line. The result: the entire book as a single text file, formatted to be tweet-friendly, with each line corresponding to a single tweet. As a final step, I stuck in some announcements at appropriate intervals.
To send the tweets, I installed the Python Twitter wrapper and its various dependencies on my Mac, and then found a simple tweet_textfile script contributed by user “cydeweys” to go through a text file line by line, sending each line out sequentially as a tweet at the interval of my choice (which happened to be every 15 minutes). Actually, the tweet_textfile script was a bit old, and used an obsolete Twitter API, so I had to update it to use OAuth, but the basic logic of the script remained unchanged.
During a test run of the script, I woke up one morning to discover that the tweeting had stalled overnight. Apparently, due to a fleeting outage on Twitter’s side, one post wasn’t acknowledged the way the script expected, and even though it had some built-in error checking, the precise timing of the glitch produced no actual error message (which would have prompted the script to try again in a couple of minutes) and instead resulted in the script hanging indefinitely. I didn’t have the time to think through all the ways the API interactions could fail and update the script to be as robust as it could be, so instead I cheated a bit, by using launchd to poke the Python script periodically. It’s not elegant, but it works.
Of course, there was more to it than that; I’m yadda-yadda’ing a bunch of steps such as registering a Twitter application, getting the necessary API keys and whatnot, and loads of testing and bug fixing. But essentially it boiled down to converting the document to plain text, splitting it into 140-character lines, and using a Python script to send out the tweets. Easy. Or at least fun, in a tremendously geeky way.
Note: Much of this article was taken from a post on my Web site that describes the project and serves as a landing page for those who want to know more about it but may not already be familiar with the book, or with the Take Control series in general.
Zen and the Art of Gmail, Part 1: Why I Switched
For the record, it has now been some time since I used Eudora 6.2.4 as my everyday email program, and I have instead switched to Google’s Gmail. I realize that may come as a surprise, considering that I wrote the “Eudora Visual QuickStart Guide” back in 1997 and was long a vocal supporter of the program. But Eudora had started crashing more frequently and corrupting mailboxes in the process. I could fix the damaged mailboxes (see “How to Fix Corrupt Eudora Mailboxes,” 4 April 2008), but doing so had become an annoying interruption when I just wanted to move forward with the day’s work.
I held onto Eudora as long as I could because I liked the way the program worked. I liked the fact that it was tweaky and customizable, that it reported clearly what it was doing, and that it was entirely straightforward. I’ve used and written about most other Mac email programs over the years, and if I was forced to generalize, I’d say that they all feel to me as though they’re starting from the same conceptual base as Eudora, but with a different set of priorities. Since I had become utterly familiar with Eudora’s mindset, all these other programs simply felt like awkward take-offs.
That’s why, when it came time to choose a new email program a while back, I picked Google’s Gmail. Alone among my choices at the time, Gmail’s engineers decided to rethink the entire concept of email, throwing out many basic assumptions and designing from scratch. I felt that if I were going to make a major leap (and since email is my primary communication medium, it truly is a huge leap for me), I wanted to develop a new and better way of working, not merely adjust my old habits to a new program that lacked the parts of Eudora I liked.
The classic email program, Eudora included, takes its architectural cues from the stereotypical 1950s office environment, where incoming mail arrives in a single location, is routed according to various rules, and ends up in a single destination where, after being read and potentially replied to, it will be filed away in a hierarchical filing system or deleted. This approach is functional, but many of the advances in email programs over the last few years have been aimed at making it easier to deal with a large influx of mail, easier to file messages, and easier to find them after they’ve been filed. In other words, these changes are simply trying to build robots into the 1950s office environment so everything moves faster. Meanwhile, the world has moved on from those days of secretaries taking dictation from snazzily suited executives.
Gmail’s engineers instead focused their efforts on search, a far more modern concept. After all, Google’s skyrocketing fortunes gave some indication that search was a winning idea. With search at its core and Google’s unimaginably massive server farms backing it up, Gmail could do some seemingly simple things that standalone email programs have been either unable or unwilling to do, most notably trading the old “folder” concept for a modern “label” approach and generating every collection of messages via a search.
As an aside, I’m quite depressed that only Google has been able to do this successfully. I see no reason that a modern Mac couldn’t offer the same level of functionality, and the fact that Gmail can be made to work offline via Google Gears shows that it should be possible. That said, I don’t use Gears; it was flaky last I tested it, and if I don’t have Internet access, there’s not much I can do anyway, since most of my work requires more than just the capability to read and write email.
The other reason I chose Gmail was that, although I wanted to use its Web-based interface, since that’s where all the innovation is, I also appreciate the fact that it provides access to my email via IMAP, for a local backup and in case I want to switch to some other email program in the future. (For some people, the capability to access Gmail from any computer with a Web browser is a big deal. Since I seldom use any computers but my own, this isn’t a significant advantage for me.)
Giving even more weight to my decision was the fact that, although I have my own mail server, I’d rather forward mail to Gmail and let Google’s engineers deal with keeping things running. Acting as my own email admin hasn’t been fun for years, between dealing with spam and the stress of being responsible for the email accounts of a number of local users.
So here’s my new philosophy of email, which has proven significantly less stressful than the last few years of using Eudora:
- I forced myself to let go of the need to file obsessively, via either filters or manual operations. I’m a professional, not the clerical help. I don’t even approve of the concept of clerical help — technology should eliminate the need for obsessive filing, and I’m letting Gmail do that for me now. This reduced a lot of stress, and after two years of usage, I haven’t yet missed my old filing system. Similarly, I’ve given up on managing an address book, which is possible because Gmail’s auto-fill of previously used addresses, both in the address fields and the search field, is wonderfully instant and accurate.
- Email is a constant stream, and while I want to be able to ignore it for a weekend, while I’m working, I want the option of seeing and responding to messages quickly and concisely. By eliminating the concept of checking mail, Gmail allowed me to escape the check/send cycle. Mail is either present in Gmail or it’s not; there’s no intermediate server where it could be. (In fact, because I still use Postini for server-side spam filtering for some tidbits.com addresses, this isn’t quite true.)
- While I don’t want to file messages, email should naturally collect into appropriate groups. Gmail does this brilliantly, automatically collecting messages with the same Subject lines into conversations, and making it trivial — far more so than in traditional programs — to collect messages associated with specific individuals or groups via a search.
Gmail Limitations — Though I’m currently a big fan of Gmail, I think it’s important to acknowledge Gmail’s limitations up front. None of these are more than a minor irritation for me, but not everyone will agree.
First, some common concerns: privacy, security, and advertising. Although Google has a privacy policy that claims it won’t share information in unreasonable ways, the fact remains that Google stores all your email (as does any IMAP email provider). Since I’ve long subscribed to my mother’s advice not to say anything in email that I wouldn’t want on the front page of the New York Times, I’m not particularly concerned about Google having theoretical access to my email. Nor am I worried about Google somehow selling access to my mail; if such a thing ever happened and became known (and it would, given the scrutiny Google is under), it would cause irreparable damage to Google.
Also, with all your email online, all that protects it is your password (so pick a good one!). If that’s not sufficient for you, Gmail recently added two-step verification that requires a level of security beyond your password when your account is accessed from a new device. Lifehacker has a good explanation and tutorial, but beware that two-step verification can be a pain to use if you use other desktop or Web applications that access Gmail or other Google services and aren’t yet updated for two-step verification.
And the ads? Gmail analyzes every email message and displays contextual ads at the right edge of the message, ranging from the ridiculous to the occasionally creepy. Honestly, I seldom even noticed them, and now that I’ve installed the Rapportive plug-in, they don’t appear at all (see “Rapportive Plug-in Replaces Gmail Ads with Sender Info,” 27 March 2010). Similarly, Gmail’s distracting Web Clips, which display news items in a little box at the top of the Inbox, can contain ads; I just turn them off in the Web Clips screen of Gmail’s Settings (to access them, click the gear icon at the top of Gmail’s Web interface page and click Mail Settings in the menu that appears).
While Gmail’s Web interface is extremely good overall, there are certain areas where it falls down. Most notably, Gmail is occasionally slow to send a message or load a new one, showing a small progress message while I sit and stew. Most of the time it’s not an issue, which makes it all the more annoying on those occasions when it takes five to ten seconds to send a message or open a new one. Those are the only times I wish for a desktop application.
That’s not quite true. Gmail’s Web interface is designed for a single window, which is generally fine, since most email either doesn’t require reference to other messages or requires only checking back in the same conversation. But on those occasions when I need to refer back to a message in a separate conversation, it’s clumsy to pop an in-progress message into its own window so I can get back to the main Gmail window, perform a quick search, and refer to the older message while writing the new one. Gmail does offer both on-screen controls and keyboard shortcuts for generating separate windows, but it’s clearly of secondary importance and harder than it would be in a desktop application.
And of course, while you can download a local copy of your email via Apple Mail or any other IMAP client, you do have to do that if you want a backup of your mail. There’s no reason to believe Google would lose your mail permanently, but it’s always best to have a backup you control as well.
Most of the rest of Gmail’s problems are part and parcel with its innovations. For instance, as fabulous as conversations are the vast majority of the time, they sometimes get in the way. As an example, when we send out email about a new Take Control book, Tonya receives a number of email messages that all need individual attention. But because people often reply to incoming mail as a way of generating a new message, she’s often faced with a multi-message conversation where each message is actually an independent unit that’s harder to work with in the conversation than it would be on its own. (You can turn off conversation view entirely in Gmail’s Settings screen, but that’s overkill.)
Similarly, threads in mailing lists sort into conversations too, which is almost always a help. But if there’s private mail with participants of the thread, it can occasionally be confusing to have the private messages mixed in with the public ones. It would be nice if Gmail enabled us to explode any given conversation into its component messages.
There are a few areas where Gmail doesn’t compete with traditional email programs. For instance, when building spam-catching filters, it’s nice to have access to grep capabilities so you can match patterns of text. Gmail can’t do that, and in fact, all searches are word-based, so you can’t even do partial-word searches. Also frustrating is that you can’t search on arbitrary header lines, which can be useful for eliminating foreign language spam, for instance. Gmail does support searching on From, To, Cc, Bcc, Subject, and Delivered-To, along with dates and attachments, and realistically, I haven’t felt hampered by Gmail’s search limitations.
If you receive a ton of email, with lots of large attachments, it’s possible that the 7.5 GB of free space you get with a Gmail account might not be enough. However, at $5 per year for 20 GB (up to 16 TB), it’s hard to be too concerned about this.
Lastly, it’s not particularly easy to import old local email messages into Gmail. There is a Google Email Uploader for Mac, but it works only with Gmail within Google Apps, not with standalone Gmail accounts. The alternative is to connect your old email client to Gmail via IMAP (or import your old mail into Apple Mail or Thunderbird, which talk fairly well to Gmail via IMAP) and then copy messages manually, mailbox by mailbox. When I tried this with Eudora, I lost original dates on the imported messages, rendering it useless, and I’ve heard that it’s difficult to import significant quantities of mail at once, with the actions timing out and messages failing to transfer.
After considering the situation, I decided there was no significant win in importing my old Eudora mail. Eudora still launches and runs fine on my Mac Pro under Mac OS X 10.6.6 Snow Leopard, so when I need to find a really old message, it’s all still there. If Rosetta really does disappear in Mac OS X Lion, I may have to import all those messages into another program. Starting from scratch required some visits to my Eudora archive for the first month or two, and it took Gmail a short while to learn the email addresses of my most frequent correspondents. But the switch was otherwise entirely painless.
If nothing else, Gmail is free, offers excellent spam filtering, can accept mail forwarded from another account, and provides access to all your mail via POP and IMAP, so it’s easy to test.
In the next article in this series, I’ll explain in some detail how Gmail’s search-centric approach to email enables an entirely different technique of reading email (see “Zen and the Art of Gmail, Part 2: Labels & Filters”). Then, in “Zen and the Art of Gmail, Part 3: Gmail Labs,” I’ll delve into the many ways to extend and improve Gmail via Gmail Labs, and in “Zen and the Art of Gmail, Part 4: Mailplane,” I’ll look at the Mac program that makes using Gmail far more palatable than just having it in a Web browser tab.
TidBITS Watchlist: Notable Software Updates for 21 March 2011
Mac OS X 10.6.7 — Apple has released Mac OS X 10.6.7 to fix a variety of bugs in Snow Leopard and Snow Leopard Server. Most notably, it’s aimed at improving the reliability of Back to My Mac, resolving problems with transferring files to certain SMB servers, and addressing various minor Mac App Store bugs. If you’ve missed earlier updates to Mac OS X 10.6, they’re included as well, along with Safari 5.0.4 and the latest raw image compatibility updates.
Also included are security fixes for numerous system components, including AirPort, Apache, AppleScript, bzip2, Carbon, ClamAV, font handling, HFS, image handling, Installer, Kerberos, the kernel, Mailman, PHP, Quick Look, QuickTime, Ruby, Samba, Subversion, and Terminal.
Finally, a number of highly specific bugs are also fixed, including a window resizing issue with X-Plane 9 on Macs with ATI graphics, improved brightness on external displays and projectors, problems opening afp:// URLs, and more. See Apple’s release notes for the full list.
As usual, Mac OS X 10.6.7 comes in a variety of forms, including one specific to the recently released MacBook Pro. They include:
- Mac OS X 10.6.7 Update: 475 MB
- Mac OS X 10.6.7 Update for early 2011 MacBook Pro: 368.21 MB
-
Mac OS X 10.6.7 Update Combo: 1.12 GB
-
Mac OS X Server 10.6.7 Update: 541.21 MB
-
Mac OS X Server 10.6.7 Update Combo: 1.15 GB
-
Server Admin Tools 10.6.7: 241.32 MB
It’s probably most important to install this update for the security fixes, unless you’ve been troubled by one of the now-fixed bugs. That said, it may be worth waiting briefly to make sure the update doesn’t cause additional problems.
Read/post comments about Mac OS X 10.6.7.
Security Update 2011-001 (Leopard) — Bringing the security content of Mac OS X 10.6.7 to Mac OS X 10.5, Apple has released Security Update 2011-001 for both Leopard and Leopard Server. It addresses fewer items than are in Mac OS X 10.6.7 and focuses largely on open source components of the operating system, including Apache, bzip2, ClamAV, image handling, Kerberos, Libinfo, libxml, Mailman, PHP, Quick Look, Ruby, and X11. (Free, 241.35 MB/473.23 MB)
Read/post comments about Security Update 2011-001 (Leopard).
Bento 4.0.2 — FileMaker has upgraded its human-friendly Mac database software Bento. New in version 4 is the capability to print mailing labels, inventory tags, name badges, and other labels from within the software. Other printing options make an appearance, too — you now get finer-grained printing controls, and new printer-friendly themes. Also new is the capability to export templates with data (so that you can share pre-populated databases with others), Location Data support (so that you can note the exact location where data is entered), and easy date searching. Full release notes are available at FileMaker’s Web site, and quick 4.0.1 and 4.0.2 releases squash a few bugs. ($49 new, $29 upgrade)
Read/post comments about Bento 4.0.2.
DEVONthink and DEVONnote 2.0.9 — DEVONtechnologies has released another set of minor updates for all editions of its information assistant programs, DEVONthink and DEVONnote. The latest versions of DEVONthink and DEVONnote now offer much improved email archiving and faster downloading of OCR resources. The software also now includes the capability to rename and move databases, even when they’re open. Sorting, classifying, and searching are all improved, too. Also new is an option to install widgets from the Install Add-Ons window.
(DEVONthink Pro Office, $149.95 new, free update; DEVONthink Professional, $79.95 new, free update; DEVONthink Personal, $49.95 new, free update; DEVONnote, $24.95 new, free update)
Read/post comments about DEVONthink and DEVONnote 2.0.9.
Yojimbo 3.0.2 — Bare Bones Software has released a small update to its information organization tool Yojimbo that contains no new features, but does pack in a few fixes. A crash that could occur when retrieving the Sidekick export location preference — even if you didn’t use Sidekick — has been corrected, as have multiple issues with iPad syncing. Note that iPad synchronization now requires version 1.0.3 of Yojimbo for iPad, which is available in the App Store. ($38.99 new, free update for owners of Yojimbo 2.0 and later, 7.2 MB)
Read/post comments about Yojimbo 3.0.2.
ExtraBITS for 21 March 2011
Lots of stuff was going on last week, with many Apple developers donating some profits to relief efforts in Japan, along with stellar behavior on the part of Apple Store employees there. We have links to more reading on those topics, as well as an article about Sprint integrating Google Voice, a Will It Blend? video about the iPad 2 (ouch!), a warning about a Flash vulnerability transmitted via Excel files, and an option to secure Twitter connections.
Apple Developers Donate Profits to Japan Relief Efforts — Kudos to the developers who are donating a portion of their profits to support the relief efforts in Japan following the recent earthquake and tsunami. Macworld has collected a list of the donations, many of which are extremely time-limited and require quick action.
Sprint Thinks Different by Integrating Google Voice — Rob Pegoraro at The Washington Post has the news that cellular carrier Sprint will be integrating the free Google Voice service into nearly all their accounts. Sprint users will get all the benefits of Google Voice, such as automated call screening, rule-based call forwarding, voicemail transcription, and more.
iPad 2: Will It Blend? — Come on, you know the answer to this one. But it’s still always fun to see the Will It Blend? folks shove whatever Apple comes up with into their blender.
Beware Excel Files Bearing Flash Vulnerabilities — Adobe has issued a security advisory about a vulnerability in current and past versions of Adobe Flash Player for all platforms that could enable an attacker to take control of an affected system. The vulnerability is reportedly being exploited in the wild via a Flash (.swf) file embedded in a Microsoft Excel (.xls) document delivered as an email attachment. Adobe expects to release a fix this week, but until then, be very careful of Excel files in email.
Stellar Apple Behavior During the Japanese Earthquake — This is a blog post from an Apple Store employee in Tokyo about the role the Apple Store has played, being one of the few places in Japan with free Wi-Fi, and how Apple has supported its employees and their families. Apple as a company seldom comments on or reacts to events like this, but it’s great to see Apple employees at all levels going beyond the call of duty.
Twitter Adds Always Secure Option — Twitter has joined Facebook in adding a profile configuration to always use a secured HTTPS connection for routine tweeting and reading after you log in to the company’s Web site; the login was already secure. Using HTTPS protects you against sidejacking in a public location where someone with Firesheep or other software could hijack your identity by sniffing a Twitter token without needing to know your account name and password. Log in, click your name at the upper right, select Settings, and scroll down to enable the option.