
Featured Image Credit: Apple Inc.
What Does the T2 Chip Mean for Mac Usage?
Beginning with the iMac Pro in December 2017—and continuing with Mac mini, MacBook Air, and MacBook Pro models introduced in 2018 and onwards—Apple has packed Macs with its own homegrown T2 chip. Like its predecessor, the T1, the T2 is designed to shift responsibility for security-critical aspects of Mac hardware out of the hands of the Mac CPU and traditional computing components—where they can be subject to hacks and malfeasance—into a “secure enclave,” a separate environment inaccessible to hacks, malware, and even hardware-based security risks. Even if macOS were somehow completely “pwned” by a security flaw or attacker, the critical functions and data handled by the T2 would be completely unaffected.
These days, it’s safe to say most technology users are interested in more security, rather than less, so the benefits of the T2 seem clear, if decidedly nerdy. But that doesn’t mean a T2-equipped Mac is the right choice for every Mac user right now—even those who want to be as secure as possible.
Why Does Apple Need Security Chips?
It’s no secret Apple’s hardware group has been on a roll for the last several years: it currently makes five processor lines (the A, H, S, T and W chips) that power everything from iPhones and iPads to the Apple Watch and AirPods. So it’s not surprising Apple would bring its own silicon to the Mac to enable Apple-exclusive features.
The company introduced the T1 in late 2016 to handle the fingerprint processing for Touch ID sensors in the first Touch Bar-equipped MacBook Pros, and it also helped lock down sensitive components like the built-in microphones and cameras. Further, the T1 took over the System Management Controller (SMC), which is responsible for heat and power management, battery charging, and sleeping and waking the Mac. Finally, the T1 determines if macOS is running on actual Apple hardware.
The T2 picks up from there, with four major capabilities:
- It takes over all access to built-in solid-state drives, enabling real-time encryption and decryption so your data is never stored in the clear
- It provides the processing power that lets you invoke Siri with “Hey Siri”
- It offers image enhancement for built-in FaceTime HD cameras
- It can optionally lock down a Mac’s boot process—so if someone were to steal your Mac, they wouldn’t be able to start it up using an external drive and steal your data
The T1 and T2 can do all these things because they’re basically separate computers with their own isolated memory and storage: they’re ARM chips running Apple’s bridgeOS. The T2 is based on the A10 processor that shipped in the iPhone 7, and bridgeOS derives from Apple’s watchOS. In some ways, the T1 and T2 act as independent co-processors, enhancing performance by handling common tasks for the Mac and enabling the CPU to focus on other things. But in other ways, they significantly beef up security, since they offer a fully independent system that remains secure even if macOS is compromised.
What Does The T2 Do For You?
Apple has published an overview of the T2 chip spelling out some of its technical details, but here are the main points:
- Secure Boot: The T2 ensures all components of the startup process—including firmware, the kernel, any kernel extensions, and bootloaders—can be cryptographically verified as trusted by Apple before booting. The idea is to prevent the Mac from being started up on compromised low-level software, thereby exposing users’ data. Secure Boot also covers Recovery Mode, Diagnostics mode, and Internet Recovery mode. By default, Secure Boot trusts only software signed by Apple or—get this—signed by a Microsoft certificate to authenticate Microsoft bootloaders. That means Boot Camp installations of Windows 10 on the internal SSD have all the benefits of Secure Boot, but anything else—like Linux—is currently out in the cold.
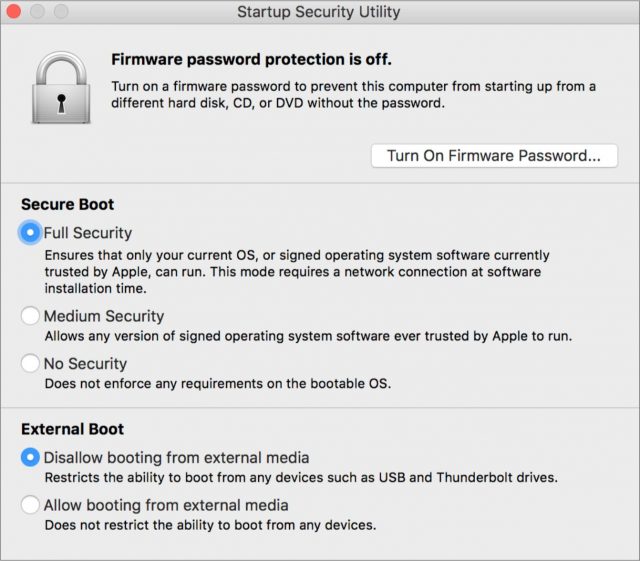
Macs with T2 chips also have the Startup Security Utility available in Recovery Mode. Users (with a valid admin password!) can set a firmware password and/or downgrade some Secure Boot functionality. However, the No Security setting doesn’t necessarily enable untrusted operating systems to start up using the internal SSD, since they’d have to support the T2 as a storage controller (sorry, Linux). Using other operating systems seems to be possible only from external drives, and they gain virtually none of the benefits of the T2, including fingerprint authentication. - Encrypted Storage: The T2 enables on-the-fly encryption and decryption of data on a Mac’s built-in solid-state drive. The encryption uses the same technology as FileVault and requires a valid password to boot up. Because the T2 is a separate system, it can enforce delays on failed password attempts: there’s a limit of 30 password attempts on the Login window or in Target Disk Mode, with a 1-minute delay on each after 14 failures. More attempts are available in Recovery Mode and FileVault recovery (including iCloud recovery), but the delay can grow to as much as an hour between allowed password attempts. This sort of delay makes brute-force password attacks impractical. However, don’t expect to see the T2’s on-the-fly encryption on anything but internal SSDs: Macs with traditional hard drives (some new iMacs still have them!) will probably never see this benefit. External drives don’t gain this protection, either.
- Touch ID: On the MacBook Pro and MacBook Air, Touch ID works much as it does on iOS devices: you get five tries to match a fingerprint, and the odds of any random fingerprint matching one stored in Touch ID are about 1 in 50,000. (So if you set up 5 fingerprints, roughly 1 in 10,000 will unlock your Mac. That’s a lot of grubby hands on your Mac.) The Mac will still require a password at startup if it hasn’t been used in 2 days, or if no password has been used in roughly a week. (The real criteria are that a password hasn’t unlocked the Mac in 6.5 days and no fingerprint has unlocked it in 4 hours.)
- Hush, Now: All T2-equipped MacBook Pro and MacBook Air models have a hardware disconnect for the built-in microphone whenever the lid is closed. That means even if some malware were able to take control of your microphone and surreptitiously listen or record through it, the microphone is essentially physically unplugged from the Mac when you close the lid. The same can’t be said of headsets, external microphones, or other audio gear, though. There’s no hardware disconnect for the FaceTime HD cameras: closing the lid blocks them effectively.
Downsides of the T2
For most Mac users, the benefits of the T2 are clear, particularly for notebook users who take their Macs with them wherever they go. If your new MacBook Air is stolen, the T2 offers decent assurance that sensitive data—like email, passwords, credit card numbers, social media accounts, super-secret projects, or those pictures—won’t fall into the wrong hands.
The T2 isn’t without trade-offs, however:
- Less Repairability: The T2 chip requires technicians to run a proprietary diagnostic tool to replace certain components like flash storage, the Touch ID sensor, and the main logic board, which means repairs or replacement of those components can only be done at Apple Stores or by Apple Authorized Service Providers. Most Mac users will never need to replace those components, but it’s yet another way Macs are becoming less repairable.
- Goodbye, NetBoot: T2-equipped Macs can’t boot from network volumes, which could be a serious issue for organizations and schools that still rely on the now-deprecated NetBoot. If you need NetBoot, take note: Apple’s recently refreshed iMac line does not have the T2 chip (see “Apple Boosts iMac Performance with Faster Multi-Core CPUs,” 19 March 2019).
- Data Recovery As-Good-As Impossible: That on-the-fly encryption and decryption the T2 chip provides for the SSD means the T2 is the only way to get data off the internal drive. If the T2 is damaged or becomes inoperable, your data is inaccessible, even to top data forensics experts, so have a solid backup strategy in place—check out Take Control of Backing Up Your Mac, Third Edition for all you need to know in that department.
- Linux & Older Windows Boot Issues: Lots of software developers—particularly Web developers—prefer to work in Linux or other operating systems, even if they own a Mac. T2-equipped Macs can only boot Linux or versions of Windows prior to Windows 10 from external drives after disabling the T2’s Secure Boot feature. If you need to run one of these operating systems, get used to doing it in a virtual machine. If you must run one of these systems on “bare metal,” a T2 Mac is not for you.
So What’s With These Audio Problems?
Since the introduction of the iMac Pro—and continuing with newer T2-equipped Macs—users have reported occasional audio glitches: little clicks, pops, or bursts of noise that seem to happen at irregular intervals. They occur with both audio playback and audio recording, and can happen using any app, whether listening to Apple Music, watching a video on YouTube, playing a game, or—uh oh!—playing a hot DJ set at a party or recording a live symphony orchestra.
The problem seems most common with USB-connected audio devices—whether consumer-grade headsets, podcaster-level microphones, or professional audio gear—but the glitches also happen with built-in speakers and microphones as well as audio devices connected via Thunderbolt. How often do they happen? Hard to say. Some users see a few every hour, others maybe only one per day.
Many Mac users won’t care. If there’s a little pop while streaming “Baby Shark” for the thirty-first time, it’s not the end of the world, am I right? OK, maybe I’m right?
However, for others, these glitches are literally showstoppers. If you’re using your Mac to process live audio—maybe you’re a DJ, or a musician using your Mac to run software instruments with programs like Ableton Live or Apple’s MainStage—blasting your audience with random pops, clicks, and bursts of sound is a Very Bad Thing. If you are recording music—whether in your bedroom using GarageBand or burning through hundreds of dollars per hour in a professional studio—those glitches will inevitably happen during critical moments, often destroying your recording. Imagine telling a legendary performer: “Hey, that was great, but the Mac glitched. Let’s go again, maybe it’ll record OK this time!” It’s a quick way to end a career. For musicians and audio professionals, this problem makes T2 Macs unreliable and untrustworthy—an irony, since many of these people use Macs to avoid the famous undependability of audio setups under Windows.
For professional recording studios, the T2 chip isn’t yet much of a problem. (No joke: plenty of Mac-based recording studios are still using decade-old Mac Pro towers.) But a tremendous amount of amateur, enthusiast, and professional audio work—whether music, podcasts, mixing, or DJing—doesn’t happen in professional studios: it happens on notebooks and in small Mac-based project studios. Plenty of musicians take their Macs on stage with them to perform in real time. The T2 is spreading across ever-greater swaths of Apple’s Mac lineup, which makes choosing a new Mac difficult.
What to do? The T2 audio problems have been known for well over a year, and Apple has been utterly silent about them save for a vague claim that macOS Mojave 10.14.4 “improves the reliability” of USB audio devices used with T2-equipped Macs. Some audio developers (like Germany’s RME) have reported improvements with USB audio, but my limited testing with a T2-equipped MacBook Pro found no discernible improvement using 10.14.4 with USB or Thunderbolt audio devices.
Some T2 users have been able to reduce the frequency of glitches by killing the built-in timed process (which synchronizes the Mac clock with a time server) and/or locationd (which tries to determine a Mac’s location for Location Services). Some folks have had good luck with these workarounds; others still experience problems. Unfortunately, stopping these background processes is non-trivial and requires disabling macOS’s System Integrity Protection. In other words, not recommended.
Is A T2 Mac Right For You?
For most Mac users, the T2 chip offers clear benefits: not only does it power spiffy fingerprint detection on the MacBook Pro and MacBook Air, but it also provides fully encrypted storage and hardens the Mac against a range of sophisticated attacks—including the sorts of things that a government might carry out if one were to seize a computer.
But the T2 also highlights how fragile the Mac world can be. Users who don’t have easy access to an Apple Store or authorized repair shop may encounter real problems getting a T2 Mac fixed. Users who don’t have a good backup strategy probably won’t be able to recover any data at all if the T2 chip fails—even if they turn to data recovery experts. And developers who want to run anything but macOS or Windows 10 natively are basically out of luck. So if your Mac has a T2 chip, figure out in advance where you’ll get it repaired if necessary, make sure you’re backing up regularly to multiple locations, and stick with virtualization for guest operating systems.
All that said, if you rely on your Mac for audio—whether recording podcasts, DJing parties, or as a professional engineer or musician—I recommend avoiding T2-equipped Macs until audio issues have been verifiably resolved for quite some time. If you need a new Mac before that happens, consider one of the few remaining models without a T2 chip, or perhaps an older pre-T2 Mac—sometimes Apple offers a good deal on refurbished and clearance models.
I’ve received a few questions about the audio testing methodology I used in this article, so here are the “off into the weeds” details.
I do a fair bit of pro audio work (mostly recording music), but I don’t have a T2 Mac myself because the T2 Macs have been fairly infamous in audio circles since the introduction of the iMac Pro. So I tested using other people’s systems as I had access to them: these included iMac Pros, as well as more-recent MacBook Pros and Mac minis, in environments ranging from professional recording and production studios (Seattle and New Orleans) to amateur musicians and podcasters just doing stuff in at home.
When Adam assigned the article (I think in January) I thought I would make a couple template projects in Pro Tools, Logic, Reason, etc., and carry those around on a USB stick so I could quickly fire them up on T2 Macs and test. That turned out not to work so well: audio setups vary too widely, and I almost always made test projects from scratch (sometimes in GarageBand, because most people had it). The T2 problems are also unpredictable enough that it took me a long time to gather what I felt was solid data: I did 42 tests of varying duration (ranging from 30 mins to over four hours) on 15 machines over a span of about two and a half months. I also spoke to several audio interface makers on background.
For the testing, I borrowed an NTi Digirator DR2. It’s basically a signal generator: totally overkill for what I was doing, but it’s reliable. The idea behind all the tests was the same: record as many channels of sine wave input as I could for as long as possible, then go back through the audio and look for anomalies. Testing used Avid (Pro Tools), UA, MOTU, Presonus, Focusrite, Apogee interfaces connected using USB and Thunderbolt, depending, along with “consumer level” USB interfaces like a Blue Yeti mic and “guitar” inputs from iRig and Line6. No plugins or onboard preprocessing: just straight in.
The “glitch” screenshot screenshot shows Logic Pro X 10.4.4 on a 10-core iMac Pro running High Sierra 10.14.3 on a rig with Thunderbolt UA Apollo interfaces (two x16s and an x8p, I think) recording at 24-bit/48KHz (nothing stressful). It’s recording eight tracks of sine wave input from the Digirator; I did the signal bussing for the Digirator on the studio’s physical console (old school!), so the UA/iMac was just blindly recording eight tracks of audio—as un-fancy as I could make it. I got to run that test about 90 minutes; there’s another glitch later in the same session. I picked that particular glitch because it happened just four minutes into the test - so I knew I could find it again fast - and it was on eight tracks simultaneously.
Now, if Adam would finally approve article pitches on unity gain, avoiding single-coil hum from LCD displays and other noise sources, how to change acoustic guitar strings using just hose-clamp pliers…I could do that all in-house.
Man, that hose-clamp pliers tip sounds hot.
Just to further confuse the issue, there’s an article on Appleinsider today that concludes Macs with T2 chips can encode video much faster.
https://iphone.appleinsider.com/articles/19/04/09/apples-t2-chip-makes-a-giant-difference-in-video-encoding-for-most-users
I like their testing methodology. I’m not a video person, but I can see that helping out consumers and hobbyist video people who (I’m just making this up) use iMovie or Adobe Premier Elements(?) or similar things. (Do people actually do that? I know no one who uses these programs, but I’m obviously more audio-focused.) I imagine most pros/semi-pros would prefer to render with “real” graphics processors. I have no idea how widespread third-party support for Video Toolbox might be, or the degree to which Video Toolbox supports third-party graphics hardware.
For what Handbrake is doing, converting video files from one format to each other, GPU is not important. VideoToolbox provides software access to available hardware that exists to encode or decode specific video formats, like H.265. These chips are common, everybody’s smartphone has them because without them, watching or creating a video would kill their battery life, if it was possible at all. iPhones, GoPros, etc. can shoot 4K video because of chips do nothing but encode video to the format they support. A discrete video card could have such chips on its board in addition to its main GPU and I would expect them to be available through VideoToolbox; since VideoToolbox is a part of macOS’s core graphics library, it would be weird to make a video card and drivers for Macs that didn’t use it.
In the AppleInsider testing, the 4K iMac they used has a “real” discrete video card, a Radeon Pro 555X, it didn’t help. They have another graph that shows encode times didn’t change when an eGPU was attached to a 2018 Mac mini or MacBook Pro.
Good GPUs matter earlier in the production process; rendering 3D graphics, applying filters, doing color correction, etc. When it comes to encoding the final product, a good GPU only helps if those effects need to be re-applied before the actual encode (e.g. when editing using proxy files). In the absence of dedicated hardware for encoding the final video format, encoding is handled by the computer’s CPU.
I think that’s quite in line with what we see in the AI benchmarks linked to above. The 4K iMac had a dedicated GPU and hardly did any better than the Core i3 mini with only Intel on-board graphics and T2 deactivated.
The real game changer according to those benchmarks appears to have been enabling the mini’s T2. With the T2 coming from the iOS world where Apple has had the greatest interest in integrated encoding/decoding circuitry this perhaps it not a big surprise.
What I do wonder about is where the modest gains of the iMac compared to the mini with T2 disabled did come from. The AI testers explicitly checked to make sure it was unrelated to disk. Both Macs use the same i3 and memory bus. The difference in transcoding time was on the 20% level so more than I’d expect to chalk up to measurement accuracy/repeatability. Is the GPU is contributing in some other fashion?
Thanks for posting this, Curtis: makes sense to me and a video editor I’m in a Messages chat with (although he doesn’t have a T2 Mac).
There is another downside to the T2 chip, especially if you use Carbon Copy Cloner: bootable backups. I have 2 TB HDDs that I use for making clones, and only clones. I have to format them as APFS, and not HFS+, so that I can later run FileVault and encrypt the HDDs (of course, after allowing booting from external media in the Startup Security Utility). Performance is slow for magnetic media drives running APFS, but there appears to be no other choice.
That’s a great point, although so long as Recovery Mode is still accessible startup security can be disabled via the Startup Security Utility. Not all drive failures leave Recovery Mode accessible, though.
As much as I love the idea of bootable backups, I’m going to run slightly counter to the usual TidBITS mindset and claim they’re something of a red herring. In my experience, the most important part of “bootable backup” is “backup”—making bootable backups on a Mac has been an exclusively nerdy activity for many years. A great deal of external storage devices (particularly USB hard drives) cannot be used to start up Macs anyway, so I’ve essentially stopped trying to convince the backup-adverse they need to make bootable backups in the simple hope they’ll get some form of storage and perform some sort of regular backup, bootable or not. Mostly, they don’t.
Bootable backups, in my case SuperDuper made, have saved my bacon on more than one occasion.
I have to agree with both you and Geoff. Bootable backups are kind of “nerdy” things, and getting someone to have any kind of backup is the first priority (and often seemingly an insurmountable task ). That being said though, they’ve saved my bacon a number of times as well, and I would hate to be without (at least) one.
). That being said though, they’ve saved my bacon a number of times as well, and I would hate to be without (at least) one.
Totally. It is no longer 2010. Making bootable backups is going against Apple’s design and development directions. More so with each OS release.
For when it can work and I need it I have a flash drive that can boot multiple versions of the OS. AFPS has made it so I now use 2 of them.
Yep. I still personally do bootable backups as part of my backup strategy, but I can count on the toes of one hand the number of other people I’ve convinced to make that leap. I, have, however, gotten a few to be pretty rigorous about using Time Machine and whatnot.
I agree bootable backups are great, and I really wish they were easier to make and perform. But they’re not, they’ve been difficult for years, and they’re getting more difficult all the time.
Just curious, is something going on that is making this harder now or will make it harder in the future? I have been doing the same thing for at least 15 years, which is open SuperDuper, click the backup and let it do its thing. Every so often I boot from one of them to make sure it’s working. I only just updated to Mojave and haven’t made a bootable of the new OS. Is that going to cause issues for SuperDuper?
What’s changed is Macs with the T2 chip will not boot from external media by default. As Geoff mentioned, it can be enabled by booting from the Recovery partition and changing a setting in the Startup Security Utility. If you don’t make that change in advance of needing it and the Mac has experienced a total drive failure, there’s still Internet Recovery but I’ve never checked to see if it includes all the utilities, including Startup Security Utility.
Without starting a deep discussion about the why of it, Apple SEEMS to feel that booting one machine from an image made on another machine is not something that is desirable going forward.
In my pure speculation I can see a time when you might have a perfect clone of a boot disk, but it will only (if even that) be able to boot the system serial # it was cloned from. For those of us who deal with management of systems, image
copying is a fail and we have been told that for years. So, most of us in such jobs have just moved on from bootable imaging. Those that haven’t are having a hard time keeping their old imaging/cloning processes working. A very hard time.
For those who have a system that works now great. Will it work with the next release of the macOS or the next computer they buy? Maybe? But at some point, I expect not.
Like jaclay I have been using Superduper for some time and it is very simple to use. Recently I accidentally erased the contents of my iBooks. I tried to do a recovery using TM but it refused to do it for me. I was able to go into my Superduper backup and recover the missing data quite easily. It will be disappointing if this is not possible in the future.
There’s no concern that bootable duplicates will go away; what people are talking about is how they’re a bit more of a stretch to make for less-experienced users and how Apple is discouraging about booting one Mac from another’s duplicate (it’s related to the fact that firmware updates won’t get installed unless the installer is used).
I suspect you are underestimating Apple’s plans.
But this is speculation on my part.
What you are doing is NOT using a clone to boot a system. You are using a clone of your disk to extract a few files. Not the same thing at all.
Ah, but I did extract the data I needed by booting the system using Superduper backup on my external HD.
I have to argue in strong favor of bootable clone backups. If a Mac dies screaming at a point where downtime is inexcusable (doing work on a workstation on deadline, or pretty much any server), if the fault is the drive you can be back up and running in under 10 minutes if your clone is up-to-date. A little bit longer if your clone is older and you need to restore recent file changes from Time Machine. If the fault is the other hardware, the external drive lets you swap in a different Mac on the same schedule.
Of course, the key thing to understand is that the instant you do this, your clone backup is no longer a backup. So ideally, you have two rotating clone backup drives, and the first thing you do is boot off the newer one and update the older one so there’s always one clone backup.
I’m happy to have Time Machine capturing files I edited 20 minutes ago, and Backblaze if my house burns down—but both mean at least a day of downtime. For $30-50 for software and ~$200 for a drive, very few people wouldn’t benefit from a clone.
Agreed on all counts, Jeff. The main issues I run into with end users are:
Acquiring external drives that can successfully boot a Mac from a clone. Harder than it seems. I have never (repeat NEVER) known a user new to the bootable clone game getting a drive that can be used for a bootable clone on their Mac on their first try. I always have to recommend drives that are known to work—and sometimes drive models that worked get revised and…stop working. (Think this is an issue only for old Macs or old drives? You’re wrong.) Dongleland — er, Apple’s decision to go with USB C — makes the situation for USB drives even worse. And sometimes the only way to get USB C drives to work is — yep — to use a USB 2 cable. That’ll help with recovery, but for many people that’s no longer a hot-swappable/get-back-to-work solution.
For best results you have to use Thunderbolt drives or (cough) Firewire, not USB. (Yes I still have clients using Firewire Macs.) Thunderbolt drives are pretty pricey per GB (about $250/500GB compared to say $65/2TB for USB drives). Good luck finding Firewire drives. (You can! But you probably want to make your own.)
Once all those hurdles are cleared (usually takes quite a lot of time), then the user has to be disciplined about making bootable clones. Disciplined forever.
Now, some people do handle this with aplomb, and Jeff’s points are all valid. But the pain threshold is high, especially for non-technical folks, home users, students, etc.
Firewire is spectacularly good and reliable technology and unlike when it was introduced very affordable. What’s with this silly geek snobbery about ThunderBolt?
The best machines Apple has ever made are the Silver Towers 4,1 and 5,1. The 1,1 though 3,1 are still not too shabby for very old machines. They fall down on high end gaming or video work but can still do almost anything else.
Apple is anti-environment, controlling company who look out only for the shareholders (Steve Jobs ran Apple for himself and for Apple users). All this lockdown stuff is very scary. Remember how Microsoft would not let you move your license/OS/startup drive from one computer to another for decades?
It looks like I will be an ex-Apple user within four or five years. I’m hanging on by my fingernails now, despite at least ten thousand dollars invested in third party software (for myself, another ten thousand or more for my business). The Apple brand was supposed to be about freedom and creativity, not locking users in a cubicle with bars, even if it is rainbow-coloured.
I just ran into my first set of issues with the T2 chip and after a trip to the local Apple Store came away a bit dismayed at their lack of support for my problem making Bootable Backups. As I read through these comments, I took note of one critical issue which wasn’t discussed. It has to do with the fact that until the T2 chip came on the scene, because the Mac can be booted from an external drive, it is the only computer on the market that gives users a shot at dealing with Ransomware, which has attacked six student’s computers at McGill University, here in Montreal, Quebec. Canada. The Macs that had Bootable Backups simple booted up on their external drives, erased the internal and CCC’d the cleaned up drive back to life.
Any thoughts?
I perfectly understand where you’re coming from.
I have always considered the fact that any Mac can easily be booted from an external clone a key troubleshooting advantage of the platform. I don’t know how many times that has saved my bacon, not to mention how easy it makes testing a new OS version or an update. You can always role back fairly quickly. It’s bad enough that Apple screwed around so much in DiskUtility (related [solely?] to APFS) it’s now at a point where making a simple clone of your internal drive has become such a hassle so that instead of using the free built-in tool, most people (especially those less experienced) will be better off using a commercial 3rd party tool like SuperDuper.
Once I get a T2 Mac for myself I will certainly change the default setting so I retain the capability to boot from external drives. The added recovery security easily outweighs the added risk in my case.
“… I will certainly change the default setting so I retain the capability to boot from external drives.”
Sorry, Simon, but as far as I can find out, no matter what you do, there is no way you can get a T2 chipped Mac to boot from an external drive. And, since most people just plug in TM and leave it running – thinking that they are covered – they will possibly find out that they are just as vulnerable to Ransomware since it locks up the attached TM drive, too. Couldn’t we just have a separate password for our external drives?
While Apple seems to think that they are boxing in one solution, they are actually opening up other problems by not thoroughly field testing. For example, Disk Warrior hasn’t been able to get a functioning disk map from Apple since macOS 10.12.6. They seemingly have decided on mandating annual upgrades, whether they are justified or not.
Yes there is. Boot from the Mac’s Recovery partition, run Startup Security Utility, choose “Allow booting from external media.” Ransomware shouldn’t be able to prevent booting any partition on the Mac so “Allow booting” doesn’t have to be enabled before an attack. It’s also not in their interests, they need victims to be able to read their ransom note.
To recover from ransomware, following the 3-2-1 backup rule is more helpful than merely having a bootable external drive. The “1” doesn’t even have to be offsite, having a copy of your data that’s not mounted when the ransomware strikes is what’s critical.
I like the option to use an external boot drive, I don’t think everyone has to have one.
Excellent point, Curtis. The setting can be left off until you actually need to boot from an external. Best of both worlds. :)
Have you guys actually done this process? I have and it didn’t work. Took it down to my local Genius Bar and neither of the two “Apple Geniuses” that worked on it could get it to boot the external drive … and it wasn’t one of those flakey WD drives, either. The best that they could do was send in a report to Apple Engineering.
In fact, here is a copy of the report:
Genius Bar Work Authorization
Repair No: RXXXXXXXX
Customer Information ### Product Information
Terry Sneller Warranty Status: In Warranty (W)
Canada Model: MacBook Air (Retina, 13-inch, 2019)
Date of Purchase: 10-Jul-2019
Serial No: XXXXXXXXXXX
Problem Description/Diagnosis
Issue: Customer came to Genius Bar with a new MacBook Air and two external hard drives. Customer had used carbon copy to copy the internal hard drive of an older Mac to an external hard drive and then to a second external hard drive. Customer wanted to use the external hard drives as a bootable backup for his clients computers if they were infected with ransomware. Attempted to boot to external drives using his new MacBook Air, which has a T2 chip. We removed secure boot and allowed booting from external sources. After the setting was changed, the copied drives appeared in startup manager, but booted to a prohibitory sign. Tested external drive with our floater MacBook Air, not a T2 system, and it booted normally.
Proposed Resolution: Was unable to find any Apple articles referencing creating external bootable Mojave disk or how to make it work with T2 system, only an external installer. Recommended to customer to have his customers use time machine as it is is supported for all systems to back up user data. Customer pushed back as his customers leave their external hard drives connected and it would back up ransomeware as well if it happened. Advised customer to advise his customers that it may be better to connect hard drives only when they intend to create a backup to avoid that possibility. Also advised customer to contact carbon copy to see if they have any options as their software is what created the bootable disks that were not working for the customer.
Proposed Resolution: Application used by customer to create clones has a support article referencing prohibitory sign on startup.
Thank you, Terry Sneller, for your contribution.
I am especially, um, intrigued by the advice to disconnect Time Machine disks from the computer, apparently negating what I thought was supposed to be a primary advantage of Time Machine. I was also gratified by this recommendation, as it is something I have been doing with one of my Time Machine disks for many months, all the while wondering if I was crazy.
And, unless I’m misreading it, that “Proposed Resolution” is a complete abdication of responsibility for creating a problem, and not a resolution in any sense.
I have no definitive information on how Ransomware works, other than it suddenly encrypts all the data on your computer and you have to use Bitcoin to buy a key and hopefully “unencrypt” your computer. I don’t know if Ransomware is activated as soon as it is installed, or if it is time activated. Regardless, what I’ve been advocating – on the assumption that it activates upon installation – is to keep TM inactive and the external drive “unplugged” until you want to make a backup. At that time, simple turn off access to wifi while doing the backup and then, when the backup is complete, unplug the external drive and turn wifi back on.
Any thoughts from you Wizards out there?
There have only been a couple of actual Mac ransomware attacks and they were short lived, so there isn’t much data available to pass on. A rash of fake attacks have been showing up that claim to be on hold, to be implemented if payment is not made, but none of those have turned out to be true.
It’s my understanding that the encryption starts immediately after the malware is installed and triggered, but takes an extended amount of time to complete its task, which may only include selected types of files.
In a number of cases with PC ransomware, it’s been possible for experts to figure out and publish the key to users so they don’t need to pay.
If by “this process” you mean booted a T2 Mac from an external drive, yes I have, it was an iMac Pro last fall. It was not a drive created from cloning the internal drive, I definitely booted from a flash drive made using macOS’s
createinstallmediacommand but I might have also booted it from another drive running a full macOS that had been previously installed directly, not created by cloning.I haven’t looking for the actual information but the last comment from Apple Support makes it sound like a known issue with Carbon Copy Cloner.
I’m not aware of Time Machine backups having any protection against ransomware or other malware that could alter or delete their contents, unmounting the drive is all you can do. It’s probably not that hard for Apple to keep users from changing files in Time Machine backups but users need to be able to selectively delete backup contents and to be able to format drives. Ransomware could achieve its goal of having the keys to the sole copy of one’s data by encrypting the user files on the internal drive and reformatting any attached external drives.
Rather than only leaving a Time Machine volume connected long enough to complete a backup, the safer option would be to have two Time Machine drives that are regularly swapped so only one is exposed to the risk at a time.
Thanks, Curtis, for the tip on the createinstallmedia command! I already have several uses in mind for a bit of future Terminal action.
I’m going to quiz the CCC folks about this whole issue.
I also assume ransomware runs as soon as it can. The longer it lies in wait, the greater the chance of being discovered. Waiting, or silently working over a long period of time is more the realm of state-on-state attacks (e.g. Stuxnet) or other targeted attacks, where there’s knowledge of the specific victim’s systems and/or the goal is to cause harm rather than make money. this is “Mr. Robot” Season 1 stuff.
Turning off the wifi for the duration of the backup seems a little extreme but is simpler to follow than “avoid doing risky things while you’re running a backup.” Ransomware is almost always going to be initiated by tricking someone into downloading and opening a file, reading email is fine (don’t open attachments or click links), directly visiting major sites is fine, maybe avoid media sites that are heavy with ads.
I think regularly rotating two backup drives is easier to do and doesn’t require changing other behavior.
I think there have been a few cases of really sloppy ransomware but it’s also been revealed that a number of businesses that offer decryption to ransomware victims were secretly paying ransom.
Ransomware writers have become more clever to make it difficult to recover on your own. They may try to encrypt backups first before encrypting a server. Or encrypt files in an order to make it less likely that you will notice.
I have seen Apple reference the T2 makes HEVC encoding on the Mac Mini faster, but for no other Mac with a T2 chip is this claim made. Does anyone have any confirmation from Apple or real world experience that HEVC hardware encoding has been turn on in the iMac Pro?
This article includes a video encoding comparison between three different Macs with T2 chips, a Mac mini, an iMac Pro, and a 13" MacBook Pro: The 2018 Mac Mini. Naturally, the iMac Pro was the fastest when encoding using the CPU but the HEVC hardware encoder in all the T2s was dramatically faster and identical on all models. Here’s another article that compared a T2 Mac mini with an iMac without a T2 that includes more detail for how they configured the software for testing: Apple’s T2 chip makes a giant difference in video encoding for most users.
As the this TidBITS article notes, the T2 is based on the A10 ARM processor found in the iPhone 7. It makes sense it contains such video hardware acceleration since a phone would need such dedicated hardware to record and playback such videos, to save battery life and keep the phone from melting in your hands