
Image by Gerd Altmann from Pixabay
Was Your Data Included in Recent Security Breaches?
So far in 2019, I’ve received four email notifications from the Have I Been Pwned service, each one alerting me that I was one of tens or hundreds of millions of people whose data was stolen in a security breach. In fact, if I add up all the people whose data was compromised just in those four breaches, the total comes to 1,588,640,494. That’s right—over 1.5 billion records of data, including names, email addresses, passwords, dates of birth, employers, genders, geographic locations, IP addresses, job titles, phone numbers, and physical addresses.
Such laxity and malfeasance are incredibly distressing, but these breaches are all in the past, and there’s absolutely nothing you or I or anyone else can do about that exposed data now. However, any of that data—particularly passwords—could be used against you, so it’s essential to make sure that you’re as protected as possible from such attacks.
The best thing to do is to make sure that you’re using a password manager like 1Password (TidBITS members get six months free!) or LastPass to create a strong, unique password for every Web site. That way, even if one site is compromised, as seems to happen every other week now, your accounts on other sites won’t be vulnerable (and yes, this happens; it’s called credential stuffing). According to one 2017 survey, as many as 25% of users reuse the same password across a majority of their accounts, and over 80% of people have reused the same password across two or more sites.
If you fall into that 25%, or someone close to you does, I strongly recommend Joe Kissell’s recently updated Take Control of Your Passwords, Third Edition. It’s one of Take Control’s best-selling books because it explains everything you need to know about making your online accounts more secure and simultaneously easier to access. And if you or someone you know has ever said, “But I don’t have anything to hide,” read Joe’s Take Control of Your Online Privacy, Fourth Edition, which he just updated with essential advice on dealing with all the latest threats. (It explains what you do have to hide.) Each book costs $14.99, but you can buy both together for just $20.
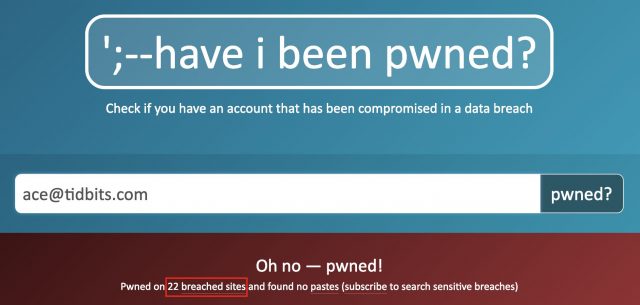
One last thing: Take a minute and search for your email address on the Have I Been Pwned site. It will tell you how many breached sites contained your address. (Don’t worry, the site is safe to use; the email address is never stored.) My address, which I’ve used broadly and consistently for many years, has been caught up in 22 breaches; if you can beat that, let me know in the comments.

Credit Karma also has a similar monitoring service, and they seem to catch breaches that Have I Been Pwned doesn’t, as I’m subscribed to both and get notifications of some breaches from Credit Karma that I don’t from Have I Been Pwned.
Discover Card also monitors for my social security number and new financial accounts in my name, but not for other things that Credit Karma and Have I Been Pwned do.
Credit Karma is free, although you do have to sign up and give them some personal information. I don’t know if you have to have a Discover Card to use Discover’s service, I’d guess you do, although I already had one when they started offering the service.
Obviously giving your personal information to additional services increases your risk because those services could be hacked, so it’s a balance, but in my opinion worthwhile to use at least Have I Been Pwned and Credit Karma.
This question is only tangentially related, and doesn’t apply if someone reuses passwords. Why don’t programmers build a delay into accepting passwords after the first incorrect password? I envision the host allowing me to enter a password incorrectly, then allowing me to try again, but then introducing short delay (say, one second) before accepting the next password attempt. After another small number of incorrect attempts (perhaps one, perhaps two or three), the delay becomes longer. After still more attempts, the delay becomes longer still.
It seems like this would slow down a brute force attack. To make it a bit fancier, restart the timer or at least reduce the delay if a different IP address attempts to connect. This would allow the user to get in even if a bad actor was actively trying to hack the account. (I assume the bad actor could switch IP addresses, but from within a limited pool.)
To me, this seems simple and obvious. Is there something I’m missing?
On a different note, I recently read about a bank that detected an intruder in one of its user’s accounts by the way the intruder moved the mouse. The intruder had actually gotten into the user’s account, but was thwarted by behavior (mouse movement!) while in the account. (Obviously, the bank had been monitoring the user’s behavior, and presumably all users’ behaviors, prior to the incident.)
My suspicion is that many sites do in fact have delays before accepting multiple login attempts on the same account, but if you have automation software that distributes thousands of login attempts across hundreds of sites, it’s easy to avoid such obstacles.
Here’s an article that explains more about how credential stuffing works:
That’s what I was missing: I was forgetting about botnets. If there are many hundreds of sites, my idea is not as good as I had originally thought. And you’re right that the sites might already do this; there is no reason they would let me know.
Just in terms of security, how does using a third party password manager like 1Password compare to the Apple KeyChain? Both appear to be strong/vulnerable in the same ways. Is there an article, or at some point could there be, comparing approaches? Thanks.
Take Control of Your Passwords compares all the major password managers, including iCloud Keychain, in a fair amount of detail. I’m not sure if Apple publishes details about the encryption, so I don’t know if it can be compared purely on security.
Joe says:
The inflexible password generation would be a problem for me—some sites require only 16 character passwords or don’t like certain character types. I fairly often have to adjust LastPass’s settings to generate an acceptable password.
Somewhat off-topic here; my question is about buying Take Control books. I understand that discounts cannot be combined, but does that apply to the entire order or to individual (or combinations of) books? In the current situation, if I want to buy the two books named in the link plus another title or two, should that be one order to get the quoted discount on the linked titles and another order to get the TidBITS member discount on the other titles? Thanks.
Here’s what @joe says:
The limitation is one coupon per order. So, for example, you could have a coupon that gives you a discount on one or two specific books, and then add other books besides those to your order (which would not be discounted).
The TidBITS member discount uses a coupon code, which applies to your entire order and can’t be combined with any other coupons (back to the one-coupon-per-order rule).
So, if you wanted to use the link to buy those two books together for $20 (which is a greater than 30% discount), you can’t also use your TidBITS member discount for other books in the same order. You’d need to place two separate orders.
We understand this is a hassle. The limitation of one coupon per order comes from eSellerate, our payment processor. It so happens eSellerate is shutting down in a couple of months, and we’re in the process of rebuilding our website to use both a different payment processor and different logic to deal with coupons and other discounts. In the new world order, it will be possible, for example, to do things like have two coupons in a single order (one that gives you a discount on book A and one that gives you a different discount on book B). We want to make all this stuff way easier and less fiddly. One thing we won’t do, however (even though it would be technically possible) is permit coupons to be stacked—as in, save 50% due to some promotion and then save another 30% on top of that with your TidBITS member discount. That seems incompatible with staying in business :-).
Thanks for the detailed response.
That’s fine. I want you to stay in business.
The Passwords and Accounts function of iOS Settings now includes a caution about the use of the same password on multiple websites. A triangle with ! appears next to each case. Tapping on the triangle brings up an option to “Change Password on Website”.
Looking at my list I have some work to do…
It is a pity that macOS KeyChain Access does not have the same feature.
Adam, you mentioned that your email showed up in 22 data breaches; I just checked the email address that I’ve had since the late 80s and … I beat you at 23! Believe me, I’m not happy at all about that.
While I am a big fan of 1Password — it was the first article I wrote when I was the Tech Daddy on the Huffington Post — it is dismaying that even though I’ve spent several hours a day over the last week dealing with the list 1P is showing me of my Compromised, Vulnerable, Reused and Weak passwords, there are still literally HUNDREDS of them that still need attention. Of course, a certain amount of these are for websites that are no longer in existence, but that still leaves weeks more of work to do.
How many people will have the wherewithal to do this? At what point will the big tech companies and corporate America start taking responsibility? I may never get the answer to those questions but I can’t stop asking them …
One of my breaches was MyFitnessPal - except I’ve never used that program! I delete just about any app that makes me set up an account. But obviously I use something owned by them.
I had 7 breaches on my main email. Off to check the others.
Diane
Your phrasing makes it sound like you’re blaming 1Password for something but isn’t it just the messenger?
There are a number of MapMy… apps that are also owned now by Under Armor. There’s also an app marketplace that lists a few dozen other apps that must as least give the option of being connected to one’s MyFitnessPal account.
And there it is - mapmyride. I signed up for that years ago so I could map out longer rides and import them into my GPS. Thanks!
Diane
You’re the leader so far, Ken!
It is distressing, and I have much the same problem. The only real consolation is that none of those accounts are at all important, so it’s unlikely that a bad guy breaking into several of them could actually do much damage.
Diane, I envy you
As for MyFitnessPal, many years ago it was purchased by UnderArmour and merged with their suite of websites, so if you ever used any of the other associated sites that’s probably what happened. Which is a whole other topic, isn’t it? The way companies absorb other companies and in the process acquire their users’ logins and personal info. Some companies require you to create a new account, while others don’t.
And don’t get me started (oops! too late) on the process of creating a login password itself, and how so many websites don’t tell you what their password requirements are until AFTER you try to create one and then it tells you “not accepted!” and what they expected you to do. sigh
I was not blaming 1P for anything; I apologize for my lack of rigor in writing that. One of the reasons I use and recommend 1Password is precisely because it tells you what passwords are compromised, weak, vulnerable or reused.
Here’s a real-world example of people suffering from credential stuffing.
https://www.washingtonpost.com/technology/2019/04/23/how-nest-designed-keep-intruders-out-peoples-homes-effectively-allowed-hackers-get/
The reason I used MyFitnessPal was the digital divide between Withings and Garmin Connect. For a while the only way to get weight from a Withings scale to automatically be sent to Garmin Connect was MyFitnessPal. It stopped working a couple of weeks ago (which end is responsible I’m not sure) so I looked into alternatives and found smartscalesync.com, which I signed up and paid for. Weights are now automatically flowing again. I never bothered trying to keep track of calories with MFP, because I don’t trust either the input or the output numbers various devices/sites give, so what’s the point. I trust my scale so far as my weight goes.
Of course, there’s another digital divide that I have problems with, the split between 1Password on my Sierra MacPro (upgrading to High Sierra when it came out failed, and I need the machine too much right now to try upgrading to Mojave) and my Mojave MacBookPro. I went to login to smartscalesync on my MacPro and neither 1Password or Sierra have any record of the password I set up. Fortunately, 1Password on my iPhone does, so I simply read it off the phone and typed it into Safari on my MacPro (and now I hope it remembers it).
In addition to periodically checking Watchtower in 1 Password, I use Identity Leak Checker https://sec.hpi.uni-potsdam.de/ilc/?
I did MapMyRide close to 10 years ago, and had no idea that UA now owns them!
Diane
Oh I HATE that! I also wish that when you use the wrong password, it comes back with a hint of how many characters etc. I’ve seen sites do that and it’s usually enough to trigger me.
I did find a couple of breaches on 2-3 of my other accounts but I think I am still under - or close to - 12 total. Ticketfly got me on 2 emails.
Diane
I wanted a scale that would talk to the health app, but they all required a login, so I just went with another old fashioned Tanita.
Diane
What do folks think about PassWord Wallet, which does not use the cloud, it encrypts the datafile with a Master Password of your choosing. Easy to learn, logical interface, one time $20, iOS version $4.99 and you can import the data file you created on your Mac.
I used to use it…but switched over to 1Password for Secure Notes, auto entry of credentials, cloud storage, and much easier sync. My wife still uses it even though I’ve got a family 1Password account…can’t convince her to switch. PW has improved in the years since I switched but it’s still not as good as 1PW in features or sync…not to mention cloud sync. Although I have a 1PW family account…my main vault lives on DropBox.
I love it. It was one of the first. I have been using it since TidBITS recommended it some 20 odd years ago. At that time I mostly stored registration data for software I had purchased, like GraphicConverter and Passwordwallet. Later I tried 1Password but didn’t like it. Eventually, I stored the PW file in my Dropbox folder so it would be available on all my computers bypassing the syncing altogether.
Later I tried 1Password but didn’t like it. Eventually, I stored the PW file in my Dropbox folder so it would be available on all my computers bypassing the syncing altogether.
Yes! Did the programmers think only mind readers (byte readers?) would use their web sites?
That has always been a very annoying ‘pet peeve’ of mine. It would seem that it would not be all that difficult to tell you up front what they actually need or accept. I suppose they don’t because it makes it easier for someone trying a brute force approach.
I always thought it would be nice if they would pass the requirement to the browser or password manager through some defined protocol. Then when you as for example, use 1Password to generate a password it could automatically generate the password to fit the requirements.
I think the idea of not showing password complexity requirements until one is entered that doesn’t meet them is to not clutter the interface showing users information they don’t need until they need it. Some number of users won’t need to be shown the password requirements because the password they chose the first time meets them (perhaps because they let a password manager generate it for them). Only when one enters a password that doesn’t meet the requirements do they need to be displayed (all the requirements, I’ve seen ones that only show the individual requirements you failed to meet e.g. “password1” “Error: password must include a symbol” “password#” “Error: password must include a number”).
If their requirements include not permitting certain characters, (&, ;, >, etc.), they may not show them until they’re used in a password out of embarrassment. If their system can’t handle certain characters in passwords, someone has done a bad job.
But I have a set policy in my password manager to generate passwords as words rather than some random variation on must have numerals, upper case, punctuation and lower case or whatever that do not actually add any useful entropy to my default settings of three words and ~14 characters…
Especially when they have a limit of <14 characters…
It is just bad UX to not explain what you expect.
You can.
In Safari on Mac, open Prefs > Passwords tab (login via TouchID or password). Then you can see the Yellow triangles, click on them to see the other sites sharing the same password. Et voila!
The problem is, like 1Password, some sites are run by the same company and you cannot dismiss the warnings (though 1Password say they’re working on a solution that’ll work across all the platforms they operate on).
For example, I’m on amazon.co.uk / amazon.com / amazon.co.jp / and other sites of their’s, even though each site has their own separate login screens, they share the same password.
Same for bbc.co.uk / bbc.com + ebay.co.uk / ebay.com + wikipedia.org / wikimedia.org to name but a few.
I know I’ve seen some that don’t allow a few special characters. “!” seems to be one of them.
Diane
In 1Password, you can manage one account that’s used on multiple domain names by having a single 1Password record with multiple websites saved.
I’m not arguing in favor of any password requirements, I’m just explaining why sites that have them might not display them up-front. If they’re displayed first, everyone has to get past them but only some need the information. If they aren’t, some won’t need the information because they met the requirements anyway and others will be shown the requirements after the first attempt. If the percentage of people who don’t meet the requirements the first time and feel frustrated is small, that could be a reasonable trade-off benefiting the majority. My guess is in practice the percentage who fail to meet the requirements and are perturbed is not small for most sites. Of course, just because the requirements are displayed first does not mean they are read, understood, and followed.
A password manager’s job is to create, remember, and fill in passwords for you. I don’t know why it would be advantageous to have it routinely choose mnemonic ones that you know will run afoul of some password complexity requirements when it’s just as easy to have it create equally strong passwords that won’t. I have 1Password choose long passwords that include digits and symbols (there’s a 50/50 chance of each letter being upper or lower case so for long passwords it’s very unlikely they’ll be all one or the other, 1Password may even put its thumb on the scale to make sure there’s at least one of each). By including symbols, that means on rare occasions I have to intervene in the password selection when it’s a bad site that can’t take some symbols. It’s more common to intervene because of a maximum password length but that affects passphrases as well. I’m not going to weaken my passwords for better sites by setting a default that satisfies some lowest common denominator site.
I support Curtis’ comments. And will slightly modify my 1PSW password generation Default to similar guidance.
Based upon my experience with “Touch ID” on my iPhone 7 and 8, I’m not enthusiastic about a future that is biometric based.
Sorry yeah, you’re absolutely right. My examples were the wrong ones.
I should have said ones that need separate entries in 1Password (for whatever reason), so still get flagged as “Reused Passwords”.
The issue still remains with Apple Keychain though, as each URL entry is separate by its very nature in Apple Keychain. So when you, say, open the Safari > Prefs > Passwords, you cannot turn-off the yellow warning triangles for all the Amazon’s, Ebay’s, BBC’s, Wiki’s, etc.
For those looking for something simpler than 1Password that doesn’t rely on a subscription fee, Alco Blom has just updated his Web Confidential to be 64-bit savvy.
https://www.web-confidential.com/notes50.html