LittleBITS: TidBITS Formatting Bug, Ransomware Protections, More OCR in Images
I’ve recently been trying to track down a curious formatting problem in TidBITS issues and could use your help. This installment of LittleBITS also gives me a chance to explain why I haven’t written more about ransomware (while sharing two useful tools for protecting against it if you are worried) and loop back to an article I wrote about utilities that go beyond Live Text in offering OCR for text in images.
Have You Seen the One-Character Column Bug?
Here’s a quirky bug. Now and then, we get a report from a reader whose TidBITS issue has an entire article formatted as a column of text that’s a single character wide. I could tell what happened in at least two cases, but I’m utterly stumped as to what might be causing it. The problem doesn’t appear to originate on our end.
In one report where the reader forwarded the badly formatted issue to us, the problem stemmed from CSS corruption. The CSS styling for TidBITS email issues uses style="padding: 0.25em" repeatedly, but in one munged article, that had been changed to style="padding:25em". In other words, the characters : 0. were deleted for that article, turning 0.25em into 25em and transforming a slight indent into a massive one. In another example, just the period was deleted, resulting in style="padding: 025em", which was also interpreted as 25em. In both cases, I confirmed that everything was correct in the version I received.
How could such a thing happen? If it were a one-off problem, I’d chalk it up to a communications error somewhere along the way. But we’ve had several reports of it in the last two weeks from different people. One of them said he’d seen it before as well, each time in macOS 10.13 High Sierra and its version of Mail. Another said he saw the same problem with the issue on his iPhone and iPad. It’s hard to imagine a Mail bug affecting so few people, but it’s similarly difficult to imagine cosmic rays zapping that particular CSS attribute more than once.
If you’ve seen this problem, please forward me a corrupted issue and let me know what operating system versions you use, if you rely on Mail or another email client, and who your email service provider is so we can do some tech sleuthing together. Thanks!
RansomWhere and Retrospect Protect against Ransomware
There have been a bunch of high-profile ransomware attacks in 2021, most notably Colonial Pipeline. I have long been thinking about writing more about the trend but couldn’t motivate myself to do a big article for two reasons. First, although ransomware isn’t unknown on the Mac, it’s not a real-world threat to Mac users at this point, with most examples being incomplete or badly coded. It’s easy to say that ransomware attacks could escalate on the Mac (and many publications do) because there’s nowhere to go but up, but I don’t like to encourage paranoia. Second, most ransomware attacks have targeted businesses, not the individuals who comprise the bulk of the TidBITS audience. In other words, why write much of anything in TidBITS about issues important primarily to Windows enterprise users? That said, two Mac apps are doing interesting things in this area.
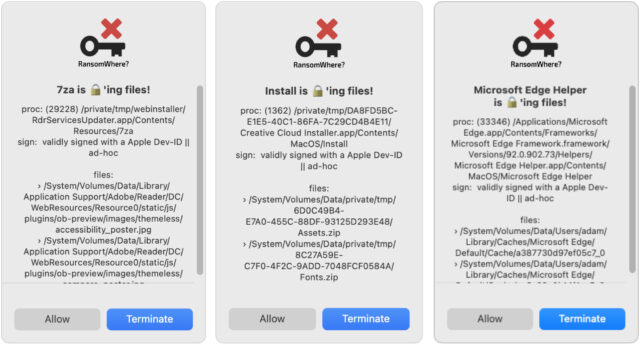
First is Patrick Wardle’s free RansomWhere, which takes a mathematical approach to thwart possible future instances of Mac-specific ransomware. Most ransomware works by encrypting your files silently in the background and then demanding that you pay up sometime later. In an effort to detect such behavior, RansomWhere monitors for untrusted processes that start quickly creating files that appear to be encrypted. When it detects one, it displays a dialog and lets you terminate the offending process or allow it to continue if it’s a false alarm. Since I installed it in May 2021, it has flagged some concerning processes, but all were clearly legitimate when I looked at the names and paths reported: Adobe Acrobat, Adobe Creative Cloud, Adobe Reader, Backblaze, Google Chrome, Microsoft Edge, and SuperDuper. RansomWhere is sufficiently unobtrusive that I’m happy to keep it running, even knowing that future Mac ransomware could explicitly avoid its checks.
Second is the long-standing Retrospect backup app. Backups are the solution to many problems, and ransomware is one of them—if you fall prey to a ransomware attack but can just restore from backup, you won’t need to pay up. To block that approach, ransomware works silently in the background for quite some time to ensure that your backups are full of useless encrypted data. It also often attacks backups directly to prevent restoration.
To protect its backed-up data, Retrospect 18 added support for a cloud storage feature called Cloud Object Lock, informally known as immutable storage. It replicates a type of physical storage called WORM (write once read many)—think CD-R and DVD-R drives. With Cloud Object Lock enabled for Retrospect backups on a compatible cloud storage provider (Amazon S3, Backblaze B2, Google Cloud Storage, Microsoft Azure Blob Storage, MinIO, and Wasabi), you can set a retention policy that specifies for how long a particular backup is locked against changes by any user, including ransomware that may have acquired root-level privileges. Even if ransomware does encrypt your working data and renders backups from that point on useless, the historical backups cannot be deleted, overwritten, or corrupted in any way.
More Text in Image Recognition Utilities
A few months ago, I wrote “Work with Text in Images with TextSniper and Photos Search” (23 August 2021) about a couple of apps that played in the space that was soon to be occupied by Apple’s Live Text feature (which we later covered in “Digitize Any Text with Live Text in iOS 15 and iPadOS 15,” 4 October 2021). TextSniper lets you copy text from images on the Mac, and Photos Search enables you to search for text detected in photos in iOS, iPadOS, and macOS. What I hadn’t internalized when I wrote that article is what Bob Stern noted in the comments—that these features were due to Apple making its OCR engine available to developers last year in the Text Recognition part of the Vision framework. Thanks to that support, quite a few other apps have added OCR features, including these:
- LiveScan: This Mac and iOS app from Gentleman Coders, the company behind the RAW Power photo editing utility for RAW images, lets you capture text from anywhere on your screen, much like TextSniper. It comes with 14 actions, and you can add plug-ins for custom workflows. It’s $9.99 for lifetime access, or you can subscribe for $0.99 per month or $5.99 per year. As with TextSniper, the big win with LiveScan is being able to capture text from any app at any time, such as with slides in videoconferencing. And, of course, it runs in macOS 11 Big Sur, whereas Live Text is limited to macOS 12 Monterey.
- Orga: As you’d expect from its inclusion in this list, the free Orga can identify text in images for copying and pasting, and it lets you search for text in images. However, it’s more generally billed as a “private photo vault” because its AI image recognition goes beyond text to nudity, letting users employ “customizable nudity detection sensitivity” when scrubbing NSFW images from the Photos app and moving them into Orga. Orga may be fully encrypted and password-protected, but I’d still suggest that public figures refrain from engaging in career-limiting photographic predilections.
- CleanShot X: While TextSniper and LiveScan are focused on text identification, CleanShot X is a powerful tool for capturing screenshots and videos that recently added text capture as well. Just invoke it, drag a rectangle around the text, and CleanShot X copies it to the clipboard. I’m embarrassed that I failed to notice this feature earlier since CleanShot X is my preferred screenshot utility these days, thanks to its plethora of options and annotation capabilities. It’s $29 and is also available in Setapp.
- Nisus Writer Pro: One thing I miss about writing and editing Take Control books is the opportunity to use the feature-laden Nisus Writer Pro word processor. To make it even more powerful, an update last year added the capability to perform OCR on imported images. It works much like the other utilities, and it’s particularly convenient to clean up the captured text right in Nisus Writer Pro, with its full-featured PowerFind Pro regular expression searches.
- TextBuddy: Speaking of cleaning up text, if you’re intimidated by regular expressions in Nisus Writer Pro or BBEdit, the TextBuddy utility encapsulates over 100 common text-manipulation actions. Alongside those actions is the capability to extract text from images or capture text in the viewfinder of your iPhone’s camera. More unusual is a feature that detects text content in audio files—it has to “play” the file internally, so it’s not quick, but it might be a good way to get started on a transcript without subscribing to the impressive but pricey Otter.ai. TextBuddy is free but has optional licenses.
That’s it for this week, and I’ll keep collecting little bits worth sharing.
Re: Ransomware Protections
You mentioned Colonial Pipeline as a high profile ransomware attack. I understand the attack was due to an employee who re-used a password on another service that was hacked and not requiring 2 factor authentication to access a Colonial Pipeline administrator account.
Passwords are notoriously insecure. They can stolen, phished, intercepted, and all too often guessed. While 2-factor-authentication is an improvement, the user experience is awful and using SMS messaging to send a confirmation code is still insecure. Even authenticator apps still rely on entering a secret that can be phished or compromised.
The future is passwordless. You authenticate to your smartphone (something you have and something you are Face-ID or Touch-ID), and your smartphone authenticates to the “Relying Party” using modern cryptography such that no secrets are exchanged.
Apple recently joined the FIDO Alliance elevating it to a de-facto industry standard. The next step is mass adoption which users can encourage by letting service providers know they want passwordless authentication. Details of course matter like what if you lose your phone and need to re-enroll?
The vision is simple: navigate to a service and click a button to approve logging in from your smartphone. No password to enter or remember.
Any mail server passed through could be rewriting the CSS causing the formatting problem. You should ask for a copy of the email including all headers from those experiencing the problem. (An easy way to explain that to Mac Mail users might be to say to send the message with “Forward as attachment”.)
I find it interesting that all those Adobe apps are setting off the RansomWhere alarm. I’ve found that Adobe always have several processes running in the background even if I have none of their apps open. This is the why I’ve avoided using Adobe-anything if there is an alternative I can live with.
Re: More OCR in Images
For my extremely meager OCR needs, an unlikely solution turns out to be Google Docs. Open a picture file in Google Docs, and if any text in there is relatively straight and in focus, you will get a file with usable (?) text.
Google Docs doesn’t do a thing to preserve text styles, and don’t think you can throw multi-column text at it. But if you need some text that you can work with in another app, give it a try.
Apple Mail does this when you have it set to forward mail to another address. It inserts breaks in the message HTML, which depending on where they are, can break the mail formatting.
first thanks for this extremely helpful article. I’ve started to use RansomWhere based on this article and will look into Retrospect (I am currently a CCC user, with time machine; and coincidentally am experiencing problems with some files, which though not due to malware are a vivid reminder of the importance of file hygiene; I’m a super diligent “backer upper”, but there’s always room for improvement ).
).
Now my question: Does anyone know of a utility that lists all modified change files? Does one of the two utilities mentioned actually list the changed files (conveniently)? Or does it just use that info in its processes? I’d rather not have to wade through a super long output; I’d like to focus specifically on daily “changed file” logs.
Rationale:
I’d be willing to use regular expressions to parse the software’s output into something like that.
Coincidentally, on Nov 14 (day before the article here) , CBC Radio aired Diagnosing healthcare’s cyber hygiene problem | CBC Radio. This included interviews with
both mentioned limitations of signatures, and need for AI in Ransomware detection.
BTW: I am super impressed by the quality and relevance of information on TidBits. I subscribe to few newsletters, but I do read my TidBit round emails on Mondays with interest.
Now my third reply for the day… (each different angles on this) :
anyone care to share an opinion regarding Malwarebytes re ransomware protection? Is it purely signature based? I think they have an organizational product, but I’m looking for something local. (My own main organization CogSci Apps Corp. is distributed.)
Re: Ransomware
I have been learning to use ChronoSync. It occurred to me that I could install ChronoSync on an old MacMini and ChronoAgent on our main computer and have ChronoSync maintain an archive with several versions of our files. If ransomware did get onto our main computer somehow, it wouldn’t have access to the MacMini to encrypt the backups. Does anyone see any holes in this idea?
Currently Malwarebytes is almost entirely signature or filename+location based, so would only be effective against known, current ransomware and since all of the known Mac ransomware is extinct, I doubt there are any such signatures in the current database. I’m confident that if a new ransomware 0day threat emerges, Malwarebytes will have distributed appropriate signatures within a few hours of obtaining a sample, as it did with previous exploits.
I would guess that probably would not prevent new ransomware from from accessing the MacMini since it has write access to those files, but it would have to be designed to recognize a ChronoSync file as one that it would bother encrypting. Ransomware only encrypts certain files that it deems critical to the user in order to finish quickly while doing the most damage.
Re: More Text in Image Recognition Utilities
Always worth mentioning that Shortcuts combined to the Live-Text feature of Monterey let you build your own (free) screen text/ locked PDF text extraction tool. Look at the explanation provided by Gary Rosenzweig from macmost.
The problem is that there’s no way of knowing what a hypothetical ransomware app could do. If the Macs are both on the same network, the ransomware could theoretically hop from one to another, for instance. The only thing that’s truly safe is some sort of WORM method that guarantees that nothing can mess with the backups.
But as I said in the article, I really don’t think protecting against ransomware is worth much effort for individual Mac users at this point. There’s just no credible threat. RansomWhere is easy to run and worth having as a small bit of insurance, and a good backup strategy is likely to be sufficient to recover even if there is a new piece of ransomware that targets Macs in the future, given how weak they’ve been so far.
Obviously, should a new and aggressive form of ransomware for Macs appear, all that advice would have to change.
It’s like protecting your house from meteor strikes. They’re not inconceivable now, but they’re so infrequent that there’s no reason to live in an underground bunker just in case. But if something happened such that parts of the moon started breaking off and hitting the Earth, we’d all be adjusting our housing preference.
I’ve not used this, but FSMonitor claims to do it and has a trial version.
https://fsmonitor.com/
And there’s this StackExchange discussion about how to do it on the command line.
That’s how I’d think most Unix-thinking people would solve the problem—there has to be some command-line incantation that just does this.
The problem that I think you’ll run into is that a LOT of things change on a Mac daily, and it may be difficult to narrow it to just things that you care about.
This is one of the reason why off-line (if not off-site) backups are an important part of any backup strategy.
In addition to automatically scheduled backups (e.g. Time Machine, Chronosync, etc.), you should also perform periodic manual backups to external storage (e.g. a USB hard drive) that is powered-off or disconnected when not actively being used (to backup or restore files).
This way, if you get some malware (ransom or otherwise) that starts trashing connected backup media, it won’t be able to get those disconnected backups.
If your backup software makes snapshots (e.g. as CCC does), then even if your current data got corrupted, you will probably have a backup (if not the most recent one, then a previous one) with the good data. Not quite as robust as the Retrospect solution, but probably good enough for individual/home users. (Of course malware could actively seek out and delete snapshots - that’s why it’s not a perfect solution - but I don’t think we’ve seen this happen yet.)
Fully agree. Offline/off-site backups are as simple as clones to an external HDD that then gets removed and dumped into a closet at work/vacation home/brother’s house.
HDDs are super cheap these days, even large capacity. USB-SATA docks cost next to nothing. SuperDuper has a free mode that will do a simple straightforward clone with literally two clicks.
I have a rotating set that sees one of these disks updated about monthly. If a ransomware attack were to occur, the worst I’d lose is the not cloud-backed up stuff from the last month. That’s very little, and none of it is really important. I feel what I’m doing is neither expensive, time consuming (cloning takes place over night), nor complicated. And the added peace of mind is more than worth the little effort.
quickly glancing I couldn’t tell whether they encrypt the backups – and in a way that only can be decrypted by myself. I wouldn’t want my data residing unencrypted on someone else’s server. I guess I could do the encryption myself and only send the encrypted files up to the server. That of course complicates matters (as encrypting a drive complicates recovery).
unfortunately, the interview I quoted above (perhaps it was the Microsoft person saying this; they have a bigger problem) said that current RW modifies its own “signature” i.e., does not have a signature.
Yes, Retrospect 18 offers encryption:
Retrospect supports a variety of encryption algorithms, including AES-256, for both at-rest and in-transit security options
Definitely, though it’s important that those drives not be connected to the machine before the ransomware is removed, or they could be encrypted or damaged as well at that point. That’s an advantage of Internet backup as long as there’s versioning in place so you can always roll back to before the ransomware-encrypted data started to be backed up.
The real problem with ransomware is that there’s sufficiently big money involved that the crazy hypotheticals have to be considered seriously. For instance, Backblaze has versioning so it would seem to provide protection. But there are ways that Backblaze backups can be deleted by the user, so if the ransomware could simulate those actions, it could prevent Backblaze from being a possible restoration option. That’s why the way Retrospect uses Cloud Object Lock to create immutable backups is important—there’s no theoretical attack that can affect its data. (Short of a massive infiltration of an entire cloud service provider and the assumption that there’s some possible way of disabling Cloud Object Lock as a result of that infiltration.)
I’m intrigued by TextBuddy, cited under “More Text in Image Recognition Utilities.”
I’m looking for an app like this for iOS. Can anyone recommend something?
macOS makes the encryption easy. Simply create an encrypted drive, then back up to it.
(If for some reason you don’t want to encrypt the drive, then make an encrypted sparse bundle disk image and back up to it. That will add some small complications. The whole disk method is as simple as pie. Simpler than pie. Do it once. If you like, CCC will remember the password for you in a keychain.)
I have two 2.5" hard drives and rotate them through the trunk of my car. Many cars have obscure places in the trunk to stash things where car burglars are not likely to look. Even if stolen, or burned in a crash, I have the previous backup in the house.
THanks, @tidbits44 . I’ve been using encrypted disk images since around the time they were introduced, and yes I do encrypt all my numerous b/u drives.
My encryption questions were re Retrospect WORM SaaS , per Adam’s answer.
Regarding file history, the kind folks at Mac Backup Software | Carbon Copy Cloner | Bombich Software told me in email:
what the above means is that I can use Spotlight regularly to manually keep an eye on files that have changed, and CCC to detect/deal with changed files that have same date stamp, and RansomWhere too. So now I have a lot more peace of mind than before I read the original article. So : thank you everyone!
I’ve updated to Carbon Copy Cloner 6 and am pleased as always .