How to Help a Friend Whose Email Has Been Hacked to Send Scams
Beware of an email-based scam that’s making the rounds this year! Since January, I’ve been targeted three times, and I wanted to share the story—both to help you avoid falling prey to the scam and so you can better alert any friends or acquaintances whose email accounts have been hacked.
First, let me bang the drum one more time: None of these people would have had problems if their email passwords had been strong and unique. If you reuse your email password anywhere, or if it’s short and obvious, stop reading right now and go change it.
Your new email password can be at least 13 truly random characters (something like iR82dGlQf3&@C) or at least 28 characters of common words separated by hyphens (like the classic correct-battery-horse-staple), or you could generate it through some combination of numbers (like dates) and letters (such as initials) that make sense to you. Whatever you choose, it must be strong and unique. And if you’re not using a password manager, you’re wasting your time and likely being insecure.
How the Scam Progresses
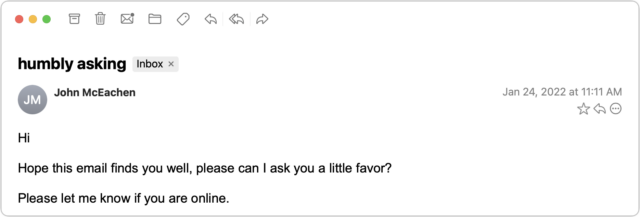
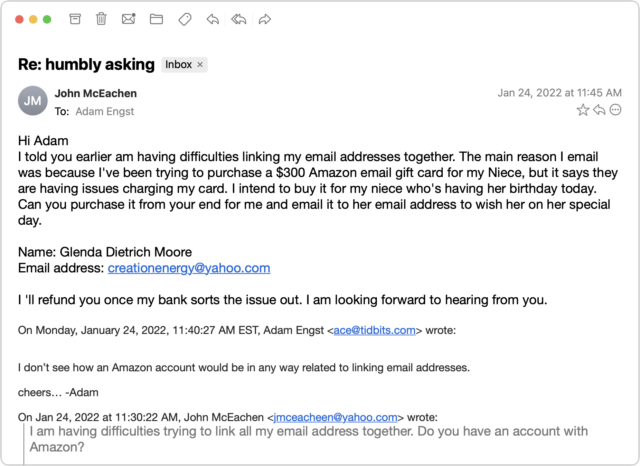
The email scam message I received came from someone I know quite tangentially—John is a runner from a nearby city who had participated in some of the track meets that I organize. Since I assign bib numbers and announce all the races, his name was sufficiently familiar that I wasn’t surprised to receive email from him—we had corresponded once in 2021 about an upcoming track meet. But with only one prior conversation, I had no sense of his email style, so his first message didn’t raise any alarm bells in my head.
I replied generally to the first message—there were various reasons an upstate New York runner might contact me—but those alarm bells went off instantly upon receiving the next message.
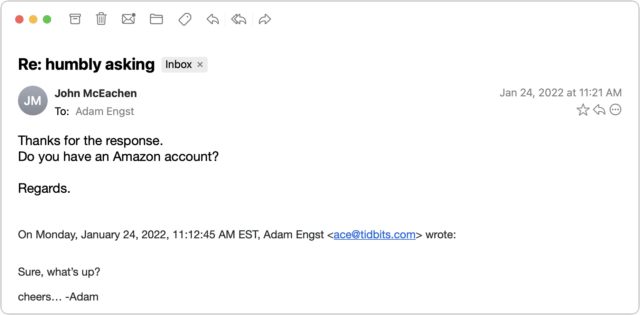
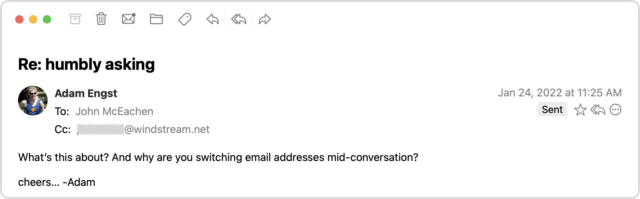
I couldn’t see any reason why a person I barely knew would ask if I had an Amazon account, and besides, at this point, who doesn’t? I switched into investigation mode. What you can’t tell from the message above is that although the sender’s name remained the same, the email address had changed from windstream.net to yahoo.com. Combined with the strange request about an Amazon account, I was now nearly certain I was talking to a scammer who was using the email address switch to get me into their own account in case John locked them out by changing his password. I decided to keep the scammer talking and see what I could learn.
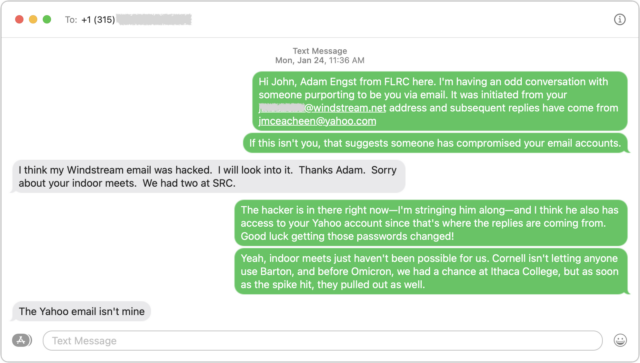
After sending that message, I looked up John’s phone number in his most recent track meet registration and texted him. Luckily, I was able to provide sufficient context in my initial text that he knew who I was. As I expected, he knew nothing about what was happening and confirmed that the Yahoo account wasn’t his.
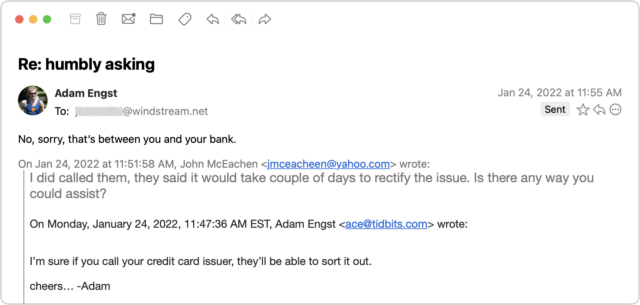
By now, I was curious what the scam would be, so I kept pretending that I was skeptical but still going along with it all. After another message or two, it became clear—the scammer wanted me to buy a $300 Amazon gift card for which they would reimburse me later. Yeah, right.
Throughout all this, I made sure to send only to the windstream.net account in part to see if the scammer would lose access. I was simultaneously keeping up the text backchannel with John, who said that he saw none of these messages in his Sent mailbox nor messages from me in his Inbox, which suggested that the scammer was somehow deleting them instantly to cover their tracks. I assume that John changed his password, but if so, that apparently didn’t kick the scammer out because I kept getting replies to the messages I sent to windstream.net.
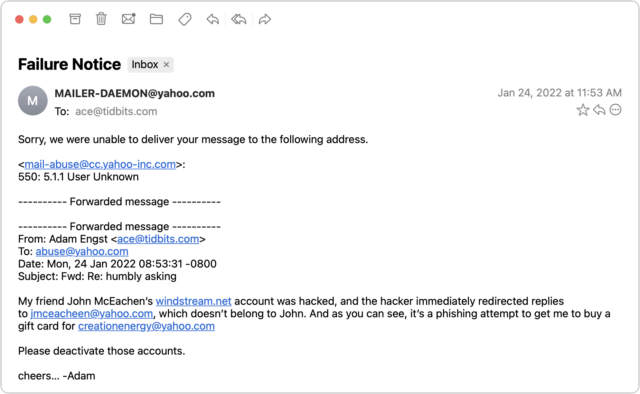
I entertained a faint hope that Yahoo would be interested in shutting down both the scammer’s address and the address they wanted me to use for the Amazon gift card. But no, my attempt to alert [email protected] failed. I subsequently tried to contact Yahoo via a recommended Web form after I mentioned the issue in “Yahoo-Backed POP Connections Cause TidBITS Formatting Error” (26 January 2022), but that was equally unsuccessful.
By this time, I had traded a few more messages with the scammer to keep the conversation going, but they eventually gave up on me. I never heard back again after this message.
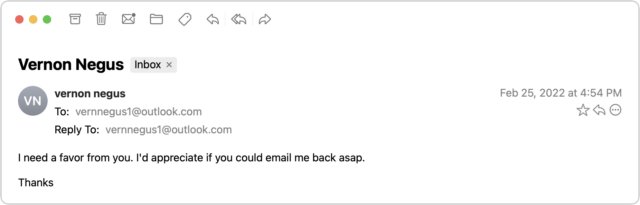
I didn’t get around to writing up this story right away and quickly forgot about it. But a month later, it happened again! Vern isn’t someone with whom I’ve ever exchanged email, but he runs an excellent U-Pick blueberry farm in my nearby hometown, and I had left my email address in his visitor book the last time I picked berries there. Luckily, I had an in for contacting him—my father used to be the mail carrier, and he still knows most people in town. Dad was able to call him and let him know about the problem, and Vern changed his password and alerted all his email contacts not to reply to the scam messages. Amusingly, this time, Vern’s real email address was at Yahoo, and the scammer was trying to redirect replies to a fake Outlook account.
Two months later, the scam reappeared in my email, with the scammer victimizing an older runner in the area. In this case, I’d been talking about Tom with another friend who worked with him regularly just the day before, so I recruited my friend to encourage Tom to change his password.
How to Help Your Friends
Let’s assume that you get one of these messages. They’re so weirdly generic that you’ll realize it’s a scam right away if they come from someone you know well. Or, as in the case of my second example, you’ll know the person so slightly that the scam will be obvious purely because a stranger would never ask such questions. The awkward middle occurs if the message is like my first and third examples, where I knew the people just well enough that I wasn’t surprised to get email from them but not well enough to be certain that the message was fake.
Nevertheless, if you’re unsure, there’s no harm in replying—just don’t get sucked in! If you notice that your reply (or any subsequent one) is going to an address other than where the first one originated, that’s another clue that you’re in the middle of a con. Once you realize what’s going on, here’s what I recommend doing… and not doing:
- Do recommend a password change: By calling, texting, or emailing a secondary address, tell the person whose account has been hacked to change their email account password immediately and recommend that they create a strong, unique password using a password manager. You must assume that the scammer has full control over the victim’s primary email account and will delete all warnings and evidence of wrongdoing.
- Do encourage alerting of other contacts: Although the person whose account was hacked probably won’t be able to tell who received the scam message, encourage them to alert all their contacts that the previous message was fake and should be ignored. Also, suggest that they encourage their contacts to check their passwords—might the acquaintances of people whose passwords were so weak as to be compromised be likely to have weak passwords as well?
- Don’t fall for the scam: Never buy an Amazon or other gift card for someone you don’t know just because they ask. (If you want to give someone money, become a TidBITS member.)
- Don’t mark it as spam: Don’t mark the initial message from the scammer as spam or report it as phishing. Remember, it’s essentially legitimate email, having been sent from the compromised account, so marking it as spam could cause future real messages from that person to be filtered too.
- Don’t bother reporting the scammer: Sadly, I don’t recommend trying to report the scammer to whatever email service they’re using. The goal is good, but it’s all too likely to be a waste of your time.
To make it easier to alert victims, here’s a sample message you can text them or use as a script when talking to them:
It looks like your email account has been hacked and used to send scam messages to contacts like me. I’d encourage you to change your email password immediately, making the new password strong and unique, ideally using a password manager app. Also, it would be good to alert your contacts to ignore the scam message and encourage them to make sure their own passwords are secure.
Finally, if you have friends who aren’t Internet-savvy, share these stories so they have a better chance of avoiding being scammed or having their accounts compromised.
I got one of these a month ago from an aunt I haven’t communicated with in years. She has a Yahoo email address, but the reply-to address on the original email was a slightly altered version of her username, at gmail (think [email protected] vs. [email protected]).
I wrote her separately and she confirmed she was aware she’d been hacked. Another relative helped her change her password, but she also spent about an hour and a half on the phone with Yahoo support. I’m not sure what she did with them.
I will add I first saw the email on my iPhone. It got me wondering, but other than the Amazon reference it was entirely plausible that she was reaching out to me - so I left it until I could open it on my computer and examine it more closely. That’s when I saw the reply-to change. If I’d just hit “reply” on the original, I believe I would have seen her first and last name in the “To:” field, and therefore no opportunity to notice the redirection.
We’ve found that the scammer will often setup a rule in the hacked mail account to redirect the email from the person they are scamming - which would explain why your friend couldn’t see the messages. They may also keep them in another folder in the hacked account. So along with password changes, we recommend people log into their accounts via webmail and look for rules that might also keep the scam alive even after a pw change.
Thanks, Adam. Good illustration of the scam, and these are fun to read at least.
You mentioned a scammer seemingly continuing to have access after a password change. I wonder if it’s helpful to suggest folks try to cancel current sessions along with changing the password? For example, Google/gmail has a “Your Devices” section where you can “log out” of specific devices or note if they are unrecognized. This increases the complexity of responding to a scam/hack, and may not be that helpful, but I would try it if I thought someone has gained password access. Thoughts?
I dislike that Apple makes it complicated to see senders’ real address on the iPhone, but it is possible.
Excellent advice!
I think it’s a good idea, but it strikes me as quite difficult to explain to someone who’s likely non-technical enough to get hacked. Especially because it will be different for every provider. I figured that windstream.net, whoever they are, may not have even had that feature, such that when my friend changed his password (which I think he did, but don’t really know), it didn’t kick the hacker out.
Yes, of course! But the sneaky part was that the “From” address was her legitimate address. It was the “Reply To” address that was different. If you hit reply and then look at the “To” address, you can see that.
But at the time I didn’t know if it was legitimately from her (hacked) account or if it had somehow been spoofed so I set it aside to look at the headers on my computer. I saw it had come from her address through Yahoo’s servers.
Because I know enough and I was wondering what the scam was, I looked at the reply-to header and caught the difference.
i mainly posted this as a cautionary tale to be extra careful if something tingles your Spidey senses.
A friend of mine got hacked and I (and many others) got a similar email purporting to be from her and asking for a favour. However, this case is a little more interesting, in that she is known for using a particular phrase in her email sign-off. That phrase appeared in the first message I received, which made it seem like it really might have come from her … but I quickly realized that it was not legitimate.
It’s also worthwhile investigating whether or not their email service supports application passwords that bypass two-factor authentication (and future password changes.) I just helped someone clean up after an email compromise on AOL (I know…) and was equally surprised to find that AOL had instituted app passwords, given their demographic, and unsurprised that the scammer had taken advantage of this to give themselves a nearly invisible back door to the account.
Great article, and god advice from all… I use Mail as my email program, and the suggestion to “email all your contacts” struck me as, well, difficult. I haven’t done it before, and a have a LOT of email contacts… Any tutorial to make it easier, before I ask https://duckduckgo.com to help me out?
I was encouraged to see that our local Walgreens had a large sign in the gift card section that warned people not to buy cards under dubious circumstances.
Our church gets targeted regularly. Someone creates an email in our preacher’s name and contacts members, asking for gift cards. One woman fell for it, but we caught her in time and Walmart refunded her money.
Sounds like it might be something she had coded into an automatic signature, such that the scammer’s message picked it up automatically.
You noticed the hand-waving there? :-) My hope is that the sort of people who tend to have their email accounts compromised due to weak passwords aren’t prolific users of email, such that they would have relatively few contacts. When Vern, my second example, sent that email to his contacts, I noted that there were 139 of them. So a lot, but not an insane number.
Hacked emails using mailing lists ?
Indirectly related to Adam’s case, I have had several cases with mailing lists recently, e.g. from scientific journals that send out announcements of newly published articles. The weird thing is that the links embedded in announcements didn’t link to the publisher’s web site as usual but to some advertisements completely unrelated to the topic. So I am not sure if someone hacked the publishers site or something else happened. For instance, this title
Recent mitochondrial lineage extinction in the critically endangered Javan rhinoceros.
linked to
Email Marketing Software…
which redirected to
https://unemploymentbenefitsguide.com/[relayAttr…
(both links shortened). The correct link is this (found on the website):
https://academic.oup.com/zoolinnean/article/190/1/372/5802322
I don’t even know how this would benefit a scammer as these journals are rather esoteric and won’t generate much traffic. But mailing lists could target much larger numbers of people, obviously.
I have heard that scientists and academics are often targeted with scams that promise to get them published in respected journals, or promising an opportunity to get published in a brand new journal that will be published by a respected academic institution. But this one clearly wasn’t targeted correctly. It doesn’t cost the scammer anything to send stuff to a target, and the more shots they fire increases the chance they will eventually hit some bulls’ eyes. Publications are a plus for many employed in scientific fields.
My 2 cents:
First, it IS possible your friend’s email account HAS been compromised, it’s also extremely rare: generally speaking, the “sender’s” email has NOT been “hacked” and changing passwords won’t do anything to stop this nonsense (altho there’s nothing wrong with making that change.) Email addresses are “harvested” (usually by robot/crawlers) and the “From” address is taken from the lists of these addresses, which are sold on the dark-web. Setting an email to appear to be from someone else is trivial, and fully-sutomated.
What’s interesting in most of these emails is how the additional “reality” details are harvested. Such details are often harvested from social media accounts. Another way is to hit the reply button. That reply lets the crook know you are “on the hook” and sends along additional useful email information (including your sig.) That is why you should NEVER reply to an email unless you KNOW it’s legit.
Tons of personal information about all of us is already freely available on the internet. Billions of bytes have come from banks, credit agencies, stores that HAVE been hacked. If one of those released your social security number to the dark web, you’re in a LOT of trouble. In fact, on the “light web” visit a “reputation” site. The will sell anyone more detail about you than you can imagine: your family members names, ages, occupations, schooling, workplace; the names of all your neighbors within a 1/2 mile radius, names of other relatives and your friends; whether you or they have financial problems or criminal complaints. Whether you have a mortgage or rent, how much is owed, all about your car and car loan; where you last lived… the list goes on and on.
Then, whether acquired legitimately, or via the dark web, using that information to provide a lot of “reality” details for what is called “spear phishing” emails. That seems to be what’s actually being discussed here. It’s very effective. I’ve gotten emails from people I have not seen in decades, with lots of personal information that made the email credible to me… but his email account was NOT hacked. The info was assembled by using bits paid for from the above, and a bit of social engineering.
Please note that I’m NOT saying your friends email account -wasn’t- hacked. It’s possible… it’s just not very likely. There are easier, less time-consuming and more profitable ways for the crooks to assemble the needed data.
What is really going on out there in the wild-west of the internet is non-trivial.
Here’s a link to a good starter explanation: https://blog.privacyguard.com/post/how-do-scammers-get-your-personal-information
And to check your own email and passwords are compromised:
https://haveibeenpwned.com/
(One of the best uses of haveibeenpwned is that it’s integrated into 1Password ! Good thinking, that…)
hth
A good point, @tracy, and I should have checked that fact while writing the article. I just went back and looked at the headers of each of the three messages, and I can confirm that all three were sent using the mailservers of the accounts in question (Windstream and Yahoo). That doesn’t necessarily mean that the accounts were hacked, but it’s certainly suggestive of that fact.
My understanding is that spoofing mail in such a way that evades all the SPF/DKIM sort of technologies is reasonably hard these days. I haven’t tried doing it in many years (I still fondly remember an April Fools prank that involved spoofing email from a friend to a running club mailing list we were both on), but even then, I couldn’t do it as completely as was possible back in the day.
I’m one of the the techie-ist in a group of 300 people mostly in their 70s to 90s. We see these hacks a lot, and in my experience usually their account HAS been hacked. For instance, in an AOL account, a rule has been created to move all incoming mail to deleted mail. Or the last access to the account was from Nigeria. It is important to check these things, and to check for any authorized apps or devices and delete those points of access.
We’re also associated with CUNY and required to have CUNY email accounts. CUNY requires a password reset every three months (which is silly). But even worse, their directory must be publicly accessible, because there are frequent phishing efforts through phony emails stating that it is time to reset your password and giving a bogus link.
You say none of your friends would have had trouble if their passwords were strong and unique. But in most of the cases I see, the user responded to scam text message or email about fixing a problem of some kind and basically handed their password to the scammer. In one case of my neighbor (age 90) responded to a pop up on his computer offering to help him fix a problem he didn’t know he had. After an hour together with the guy in his system, he’d even signed into his investment account. Luckily we were able to fix things in time.
Ouch. Yeah, if the user is going to hand the password over to the hacker, the strength of the password won’t make any difference at all. 2FA might help, but even then, if the user is facilitating entry by the hacker, all bets are off.
The internet is a big place and sending scam messages costs next to nothing. All it takes is one person to fall for the scam and the bad guy made money. Sending to a small list with a high click rate - thats just easy ROI.