What Are Rapid Security Responses and Why Are They Important?
One of Apple’s promised features for iOS 16, iPadOS 16, and macOS 13 Ventura was a new type of update, the Rapid Security Response. The first of these updates have now shipped, so you can update to iOS 16.4.1 (a), iPadOS 16.4.1 (a), and macOS 13.3.1 (a) in Software Update. Apple hasn’t said what security vulnerabilities these updates address on either the Apple Security Updates page or the release note pages for iOS 16, iPadOS 16, and macOS 13, but realistically, the vast majority of users don’t care about such tweaky technical details. I’ve updated all three operating systems with no problems, and I encourage you to update as well.
So what’s a Rapid Security Response, and why are we seeing them now? Apple’s goal is to distribute important security fixes to users more quickly and encourage faster adoption, particularly when a vulnerability is being exploited in the wild. Although only Apple knows how long it takes for its user base to install security updates, it’s undoubtedly slowed by three factors:
- Download size: Although high-speed Internet connections are commonplace, many people still have slower connections that cause them to delay large updates.
- Installation time: More problematic is the downtime associated with installing an operating system update. We all schedule updates for when life circumstances permit.
- Update hesitancy: Some updates have introduced new problems, causing cautious users to delay updating until early adopters have reported success.
The first two factors stem from Apple’s move to the read-only Signed System Volume in macOS 11 Big Sur. As the inimitable Howard Oakley explains, changing the contents of the Signed System Volume requires installing the update on the System volume, making a cryptographically sealed snapshot, and restarting from that snapshot. Because of the many files that require updating for even minor changes, updates require large downloads and lengthy installation times.
Apple’s solution is to move components likely to need updating—Safari and its underlying WebKit foremost among them—outside of the Signed System Volume. That makes them easier to update but also more vulnerable. To maintain security for such external components, Apple introduced special disk images called cryptexes (cryptographically signed extensions). There’s almost no documentation of cryptexes apart from Howard Oakley’s exploration, where he says they’re stored on the Preboot volume and loaded early in the boot process, when they’re grafted into the parent file system such that their contents effectively become part of the system.
Rapid Security Response updates are also cryptexes, which theoretically allows them to be a fraction of the size of traditional security updates, and they should install in vastly less time, addressing the first two factors that delay update adoption.
Installing Rapid Security Responses
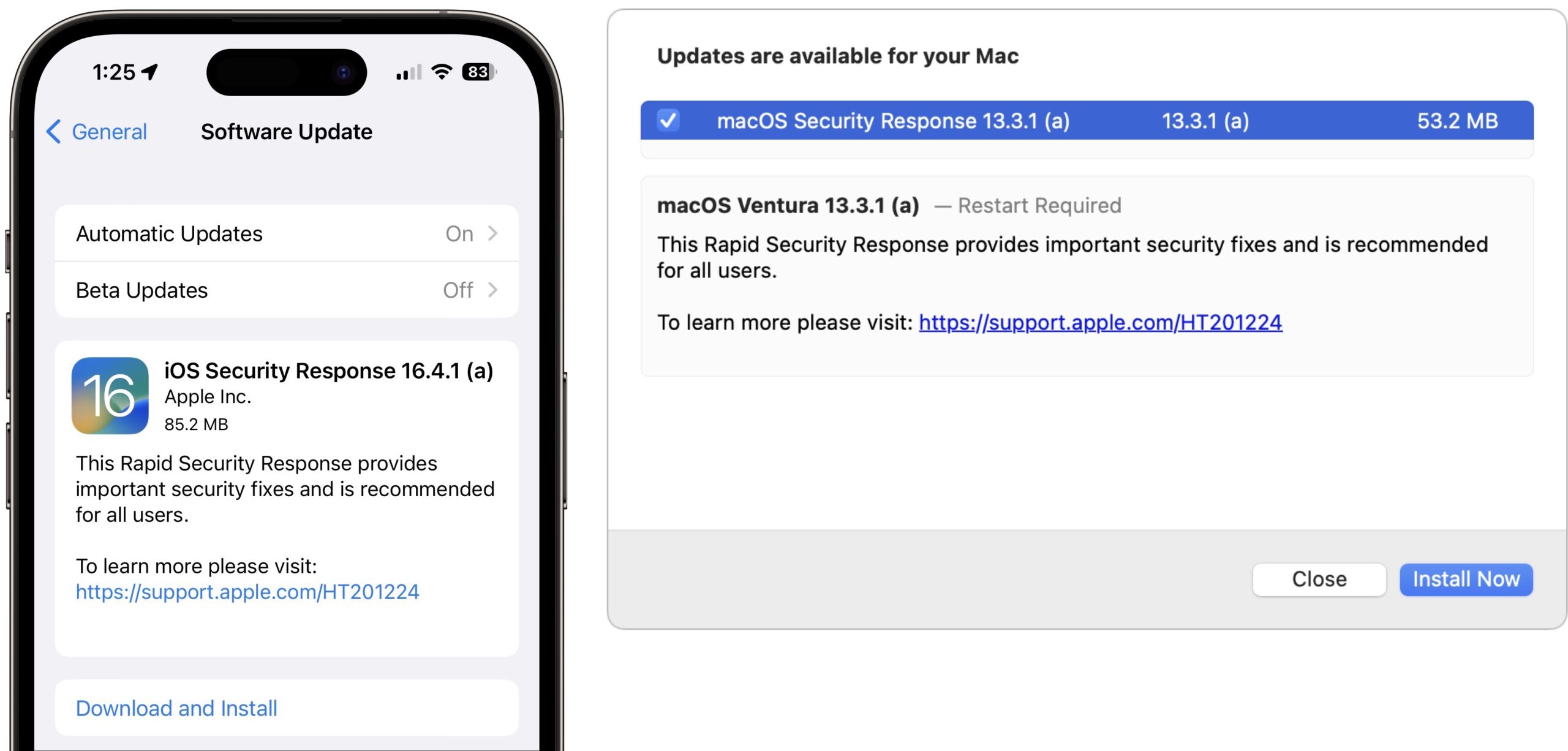
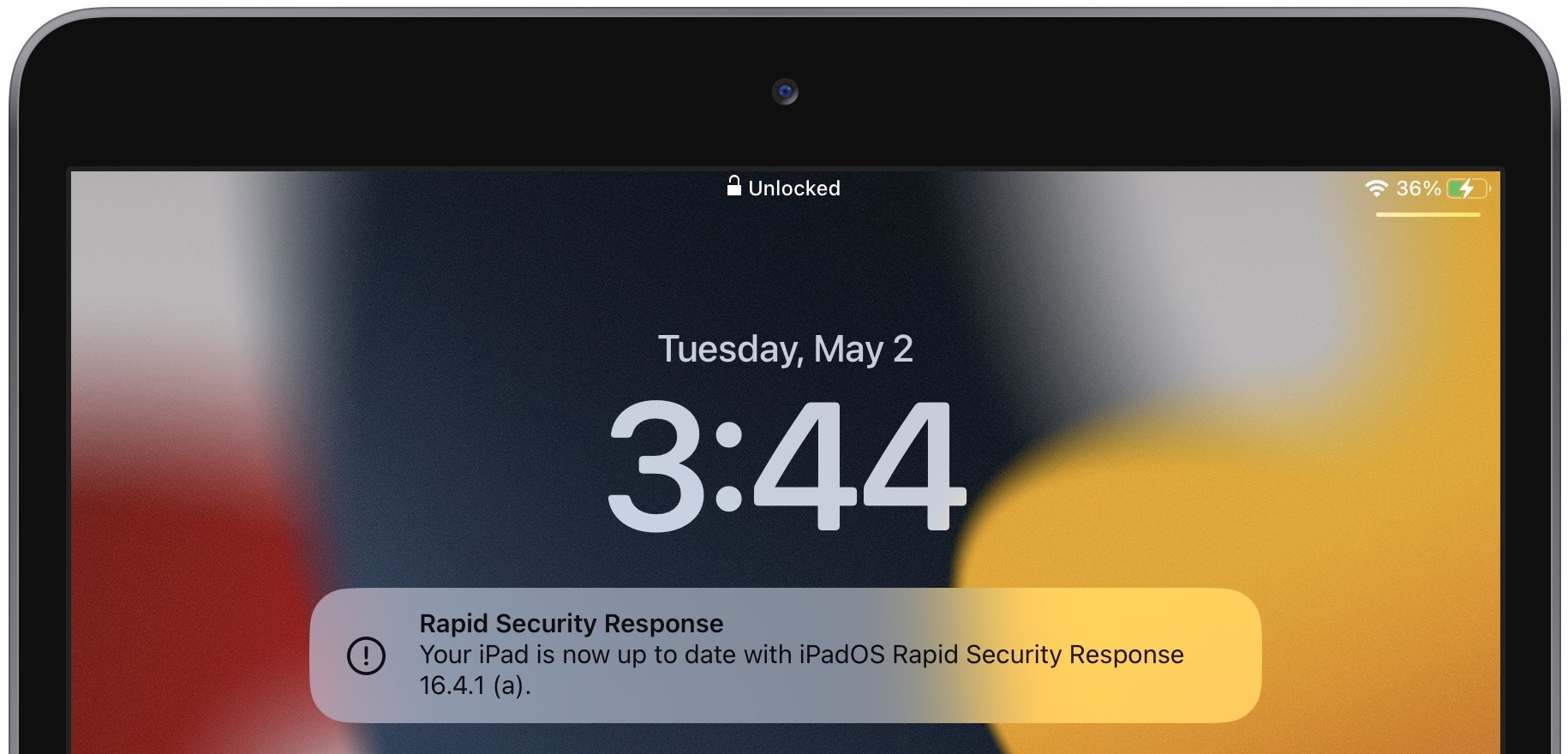
By default, all iPhones, iPads, and Macs running the latest operating systems allow Rapid Security Responses to be applied automatically. Theoretically, you shouldn’t notice them being installed unless a restart is required, which was true of all three of these updates. After restarting, iOS and iPadOS—but not macOS—posted a notification alerting the user to the update. I suspect Rapid Security Responses that don’t warrant restarts will also generate such notifications.
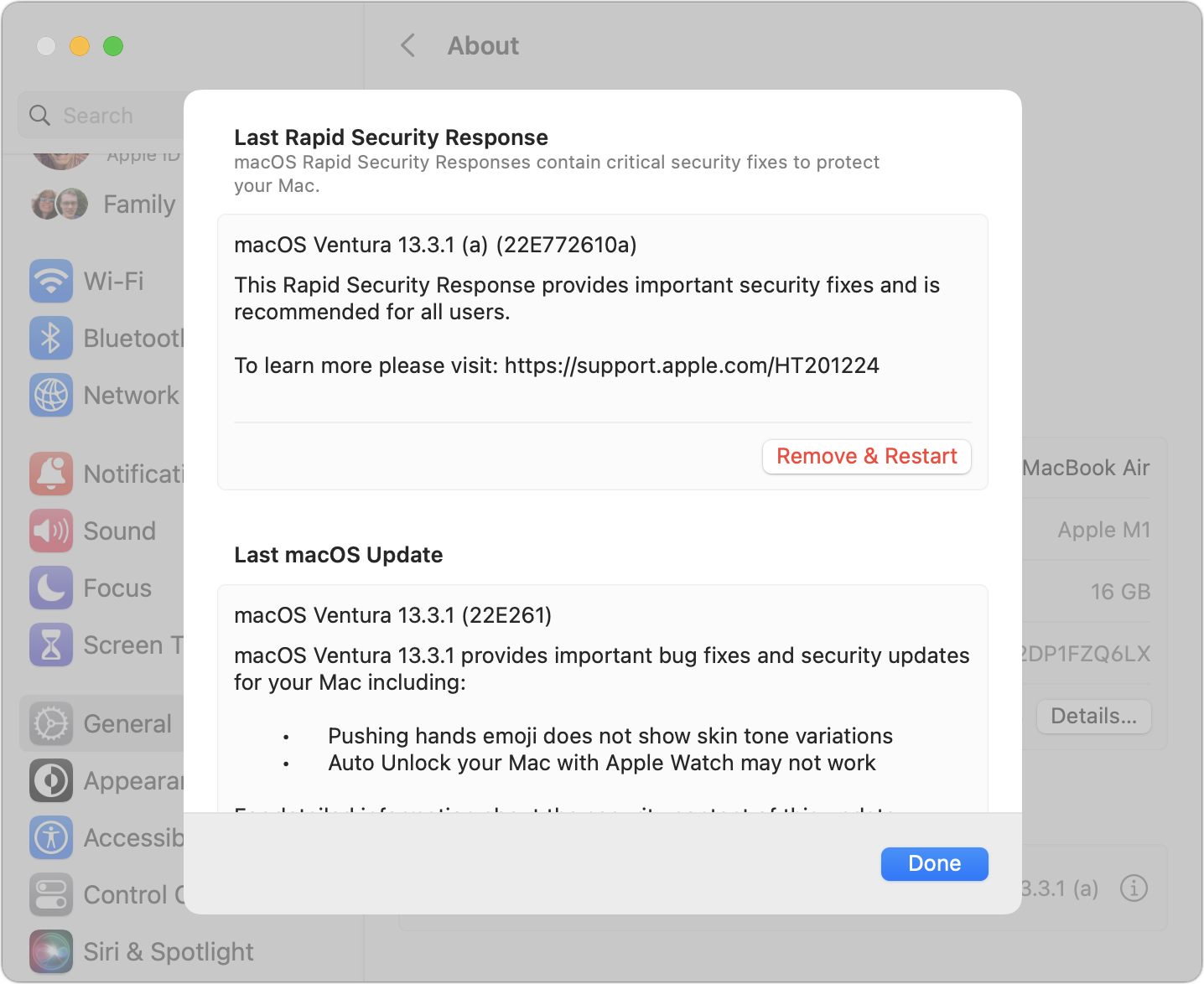
You can always tell if a Rapid Security Response has been installed because the version number in Settings > General > About or About This Mac will include a letter, as in iOS 16.4.1 (a). I presume Apple will increment the letter if multiple Rapid Security Responses ship before the next operating system update.
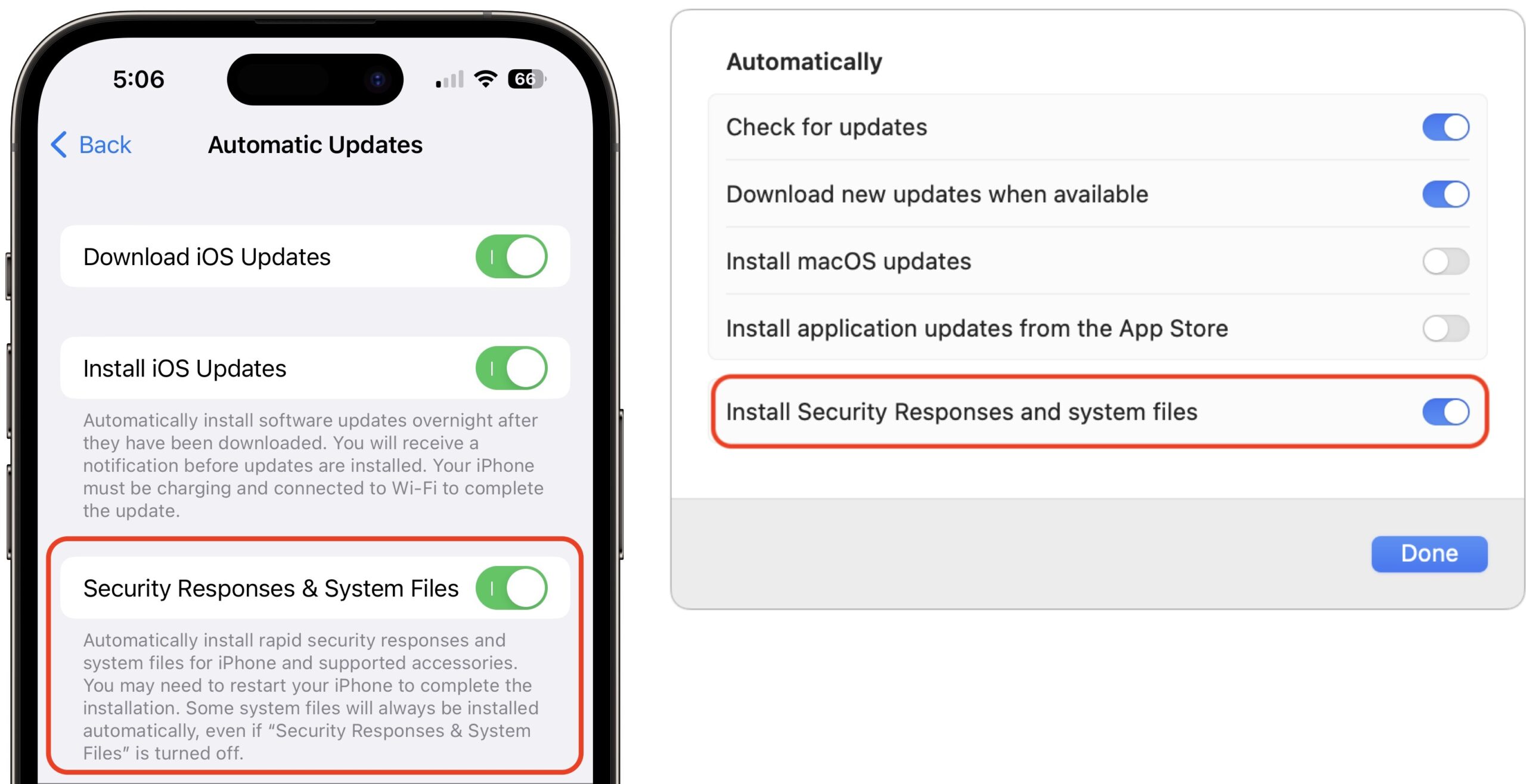
You can check to make sure Rapid Security Responses are set to be installed in:
- iOS/iPadOS: Go to Settings > General > Software Update > Automatic Updates, and look at “Security Responses & System Files.”
- macOS: Go to System Settings > General > Software Update, and click the ⓘ next to Automatic Updates. Then look at “Install Security Responses and system files.”
If you turn off automatic updates or avoid installing Rapid Security Responses when they become available, you’ll automatically get all the included fixes with the next operating system update. I plan to allow mine to install automatically, and I encourage most other people to do so, too. If you want full manual control, that’s fine, but then it’s your responsibility to check for and install updates. Given the small downloads, quick installation, and ease of reverting, I think it’s worth letting Apple work to protect our devices against attack as it sees fit.
On my devices, the updates ranged in size from 53.2 MB to 309.8 MB, and the installation time was commensurate with the update size and power of the machine. Apple has clearly solved the size and time problems.
| Device | Update Size | Installation Time |
| iPhone 14 Pro | 85.2 MB | 4 minutes |
| 10.5-inch iPad Pro | 86.2 MB | 13 minutes |
| 27-inch iMac | 53.2 MB | 1.5 minutes |
| M1 MacBook Air | 309.8 MB | 4 minutes |
What about update hesitancy? Since the entire point of Rapid Security Responses is that Apple can push them out quickly, presumably with less testing time than a full operating system update would require, it’s more likely that they could have unanticipated side effects. But since cryptexes are atomic—they’re standalone disk images whose contents are grafted into the system at boot—it’s easy for Apple to provide a mechanism for removing them. So if you experience apps crashing or other significant problems immediately after installing a Rapid Security Response, you can remove it and revert to the previous version of the operating system. That’s a huge win and something that’s never before been possible.
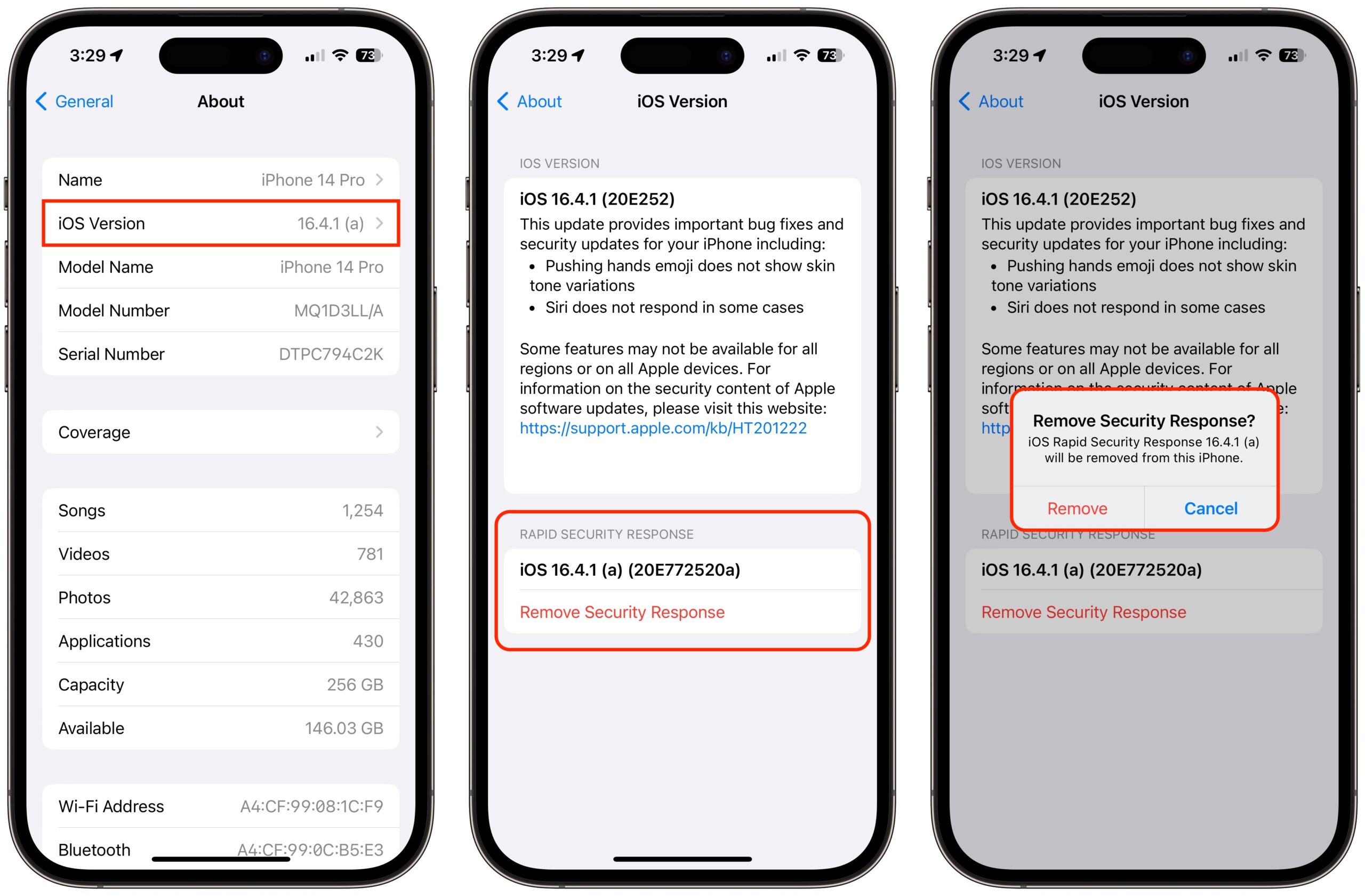
Removing Rapid Security Responses
In iOS and iPadOS, you remove a Rapid Security Response by going to Settings > General > About > iOS/iPadOS Version, tapping Remove Security Response, and confirming the action. Removing the Rapid Security Response from the iPad Pro was roughly the same speed as installing—about 14 minutes—but after it restarted, the update was available to install again, as it should be.
On the Mac, removing a Rapid Security Response requires going to System Settings > General > About, clicking the ⓘ next to the macOS version, clicking Remove & Restart, and confirming the action. The process took about 2.5 minutes. On the first boot after removing, Software Update wouldn’t show me the Rapid Security Response, claiming that macOS 13.3.1 was up to date. After another restart, it came back, and I was able to reinstall it.
Note that the release notes of the previous operating system update also appeared on these screens. That’s a small but welcome addition.
Ultimately, it’s good to see Apple finally utilizing the long-promised Rapid Security Response update mechanism. I’ll admit that I had somewhat come to dread operating system updates, particularly on the Mac, where you can end up staring at a black screen for far longer than is comfortable. Rapid Security Responses won’t fix that problem for actual operating system updates, but I hope Apple can use them to reduce the number of full updates that are necessary.
The MacOS RSR required restarts on both my M1 Macs.
Mine requires restart too, updating from macOS 13.3.1.
Why do you think it took a whopping 13 minutes on the 10.5-inch iPad Pro? That seems rather unusual.
Apple has a goal of not requiring RSR’s to require a restart, but if the patches involve a process that loads during boot or login, then a restart is required.
Since most security vulnerabilities do involve such background processes, I expect the majority of RSRs will continue to require restart.
Since this is the first RSR delivered to the public, and first to require a restart, I find it difficult to judge whether 13 minutes is unusual or not.
I’m guessing that this sentence in the article triggered your comment, @aforkosh.
What I was trying to point out was that although all operating systems had to restart, the notification appeared only in iOS and iPadOS. I’ll recast that sentence for clarity.
My assumption is that it’s a much, much slower device than my iPhone 14 Pro, and I suspect there’s some serious CPU work involved with all the cryptographic details. All the other machines were 4 minutes or less.
My MBP installed the update and then restarted without prompting – or if a prompt was supplied, it apparently restarted after a timeout period had expired. Is that normal? If so, I’m not a fan … and it has me seriously considering disabling the automatic installation of security responses.
Automatic restarting after any macOS installation that requires it always takes place. Future RSRs may or may not require a restart, depending on whether running background processes get patched or not.
I’m unaware of a separate choice to only automatically install RSRs
Interesting; thanks. Then I guess I’m confused by why macOS updates are being automatically installed. I had been used to simply being informed that updates are available … and then manually installing them. Software Update > Automatic update > “Install macOS updates” is enabled. I wonder if Ventura or a subsequent update enabled that. In any case, it’s now disabled.
Coincidentally, I was going to start a separate thread about what might be causing my MBP to unexpectedly restart. It’s done so, seemingly with increasing frequency, a few times over the past few months, well prior to the release of last week’s RSR. I figured there was something amiss on my system and was/is wondering how to troubleshoot it. Perhaps reinstall the OS … or even perform a factory reset and then restore from backup – something I have no experience with on macOS.
On the Software Update > Automatic update window, there is an option to “Install Security Responses and system files”. I’ve disabled it, for the time being. I monitor macOS news daily, from many sources, so will know when the next one is released – and can plan accordingly.
Sorry, but since I haven’t tried Ventura yet, I didn’t realize those preference options had changed.
I will caution that the same option does control the installation of System files, which can only be accomplished in the background once every 24 hours. That includes XProtect Payloads files (XProtect Remediator) and other database updates that aren’t announced by Apple nor widely publicizedd on rumor sites. You won’t be able to install those updates without using a Terminal command or a utility like SilentKnight/LockRattler to trigger background update checks since they don’t ever show up in Software Updates.
You’re in luck… TidBITS comes through as usual!
Did this setting change? Does this mean if I want XPR installs to happen over night I also need to allow RSR to install automatically? I want the former, but definitely not the latter.
I’ve been curious since this part of the discussion started. Since XPR’s are considered to address a problem that is considered too severe to wait for a background update (e.g. XProtect), why would you not want such an update to install without your approval. It’s rumored that an XPR involves a vulnerability that is being actively exploited, whereas a routine update of XProtect/XProtect Remediator may not.
Learned a lot as always from Adam but I was most struck by the level of patience required to watch and update of indeterminate length until completion in order to time it. Four times.
Also, “Why does iOS use title case while macOS uses sentence case?”