TidBITS#1040/16-Aug-2010
iOS security reigns in this issue, with Glenn Fleishman covering Apple’s security-related iOS updates, describing how using encrypted iOS backups actually reduces security slightly, and explaining how to update a changed Wi-Fi network password in an iOS device. Beyond that, security editor Rich Mogull runs down the security challenges that Apple faces with iOS and the advantages that the company enjoys. For a change of pace, Lex Friedman looks at some essential Safari Extensions, we announce the release of Sharon Zardetto’s authoritative “Take Control of Fonts in Snow Leopard” ebook, and Adam describes how we’ve moved some legacy services. Notable software releases this week include VMware Fusion 3.1.1, Things 1.3.5, and Office 2004/2008 Security Updates.
iOS Security Fixes Released for Serious Vulnerabilities
Fixes for two serious holes in iOS are now available in the form of iOS 3.2.2 for iPad and iOS 4.0.2 for 2008 and later models of iPhone and iPod touch. Attach your iOS device (or devices) to the computer with which you sync using iTunes, and use iTunes to download and install the upgrade.
One flaw lies in TrueType handling within Apple’s iOS PDF display software. A PDF with fonts crafted in a particular way could allow a malicious party to run any code on an iOS device simply by getting you to view the PDF file. That flaw is paired with a second in IOSurface, a framework for buffering or holding images in memory. The IOSurface flaw allows the code to be executed in a way that gives the attack full system privileges.
At that point, an attacker could enable remote access, copy or delete all your data, or install background monitoring or call-interception software.
The flaws were revealed as part of the first successful iPhone 4 jailbreak in iOS 4, which required only that you visited a particular Web page. The escalation of privileges enabled the jailbreak software to crack Apple’s protection against installing software other than that which the company allows.
Apple apparently no longer provides security upgrades for the iPhone 3.1 software branch, which is unfortunate as some iPhone 3G users were forced to revert from iOS 4 to 3.1.3 due to significant performance problems that Apple has said it is investigating.
Even with iOS 4 being a free upgrade, Apple should provide security fixes for known, significant problems in the previous widely used OS release. Further, original iPhone and iPod touch users will likely also be subject to these flaws, and cannot upgrade to iOS 4.
Wrangle Your Fonts with “Take Control of Fonts in Snow Leopard”
Managing fonts in Mac OS X is all too often like herding cats (all those Fonts folders!), but you can now corral your serif and sans-serif felines with our new “Take Control of Fonts in Snow Leopard.” Written by Sharon Zardetto, this 225-page ebook covers not only everything you need to know about fonts in Mac OS X 10.6 Snow Leopard and 10.5 Leopard, but also special font situations in software such as Adobe CS4 and CS5, Microsoft Office 2004 and 2008, iLife, and iWork.
Important topics covered include:
- Where your fonts reside, in what order they load, and what – if anything – you should do about it
- The ins and outs of different font installation methods
-
Using Font Book to manage, validate, and organize fonts
-
Making the most of character-rich Unicode fonts
-
Using Apple’s Character Palette/Viewer and Keyboard Viewer to insert and explore special characters
-
The quirks of fonts from Microsoft Office 2004 and 2008, and which ones you should keep around
-
Organizing fonts from Adobe CS2, CS3, CS4, and CS5 so they are available where you need them
The ebook costs $15 and includes a coupon worth 20 percent off on any purchase from Ergonis Software, makers of the font utility PopChar X and other software.
Recover from Changed Wi-Fi Network Passwords in iOS
When you connect to a password-protected Wi-Fi network using an iOS device – iPad, iPhone, or iPod touch – your gadget stores that password for use the next time you connect. Makes sense.
But what if the WEP, WPA, or WPA2 password for the Wi-Fi network in question is changed? Your device may try to connect and then tell you it can’t, or in the case of an iPhone or 3G-capable iPad, just silently drop back to 3G data service, with the only indication being the 3G status icon appearing at the top of the screen when the Wi-Fi status icon should be there.
The solution is enforced amnesia; I only recently figured out that this would resolve some problems I had suffered from in the past.
To work around to the now-incorrect password being stored, make sure you’re in range of the network that has had its password changed and follow these steps:
- In the Settings app, tap General > Network > Wi-Fi.
- Tap the blue details arrow to the right of the network name in the Wi-Fi Networks list.
If the password is stored, you’ll see a Forget This Network button at the top.
-
Tap it, and confirm the action.
-
Return to the Wi-Fi Networks list, and tap the network name (not the details arrow).
iOS prompts you for the network password, which you can now enter to reconnect to the network.
Useful as this trick is, Apple should update iOS to prompt the user when a stored password for a remembered network no longer works.
Secured iOS Backups Reduce Security, but Not by Much
At first, I thought Elcomsoft had discovered a major flaw in the way that iOS allows iTunes to back up the data of an iPhone, iPad, or iPod touch. The Russian security firm creates software designed to test the quality of passwords for many different software packages and systems by trying to crack them; it also markets its software for forensic use.
Elcomsoft offers iPhone Password Breaker software ($79 or $199, depending on features) to crack the password for an iTunes backup of an iOS device. Version 1.2 adds the capability to view the contents of an iOS device’s keychain if a password is cracked. The iOS keychain, much like (or perhaps identical to) the one in Mac OS X, stores network, email, and other system passwords, as well as passwords from third-party apps that took Apple’s advice to use the keychain.
Andrey Belenko of Elcomsoft explained how this new feature came about. Prior to iOS 4, iOS devices with a hardware encryption key always used that key to encrypt the keychain. So far, it has been impossible to recover the hardware encryption key from a device, and the key is strong enough to resist cracking. (Hardware encryption is found in all iOS devices released from 2009 on: all iPads, the iPhone 3GS and iPhone 4, and third-generation iPod touch models.)
The hardware key continues to be used in iOS 4 backups in iTunes, with an important exception. If you enable Encrypt iPhone Backup (or whatever iOS device is plugged in), iOS 4 switches from using the hardware key to a key derived from the password you enter for your backup.
The reason, Belenko explains, is that iOS 4 then allows the transfer of the keychain to a device being restored from a backup. If your iPhone is lost, stolen, or destroyed, or if you upgrade from one iPhone to another, you can restore your last backup onto your new iPhone. Before iOS 4, the passwords weren’t passed along. (Elcomsoft offers an extensive FAQ explaining this even further.)
It’s a strange notion, that encrypting your backup might actually make your data less secure. But it’s not really a security hole, nor does Elcomsoft see it that way.
In order to extract passwords from your iPhone keychain, a ne’er-do-well has to gain access to your computer in some fashion, physically or through a remote exploit. With that kind of access, a keystroke sniffer could be installed, and then all the keys to the kingdom would be available.
Further, if you’ve picked a good, strong password, the Elcomsoft breaker won’t help. It’s a brute-force method, and the company doesn’t oversell the difficulty of recovering a password. Its FAQ has this amusing dialog:
(end of one question): …Only relatively short and simple passwords can be recovered in a reasonable time.
Q: What do you mean by “time consuming” and “reasonable time”?
A: A lifetime? Seriously, with protection as good as that, it may take centuries to recover a long password.
And Elcomsoft goes on to note, “The iPhone backup encryption is good enough. Well, it is near perfect by our standards. That’s to say, it’s really secure.”
Apparently, Apple was able to add flexibility without compromising security so long as you take care to create a reasonably long and strong password. Apple’s one mistake? Not including the Password Assistant that’s used in the Keychain Access program and a few other places in Mac OS X to assist you in creating the best password for your iOS backups.
(Thanks to TidBITS security editor Rich Mogull for his input on this article.)
Legacy TidBITS Issue Formats Moved
We’ve been doing this Internet thing for a very long time, which leads at times to awkward situations where readers have become accustomed to some service that we started providing back in the mid-1990s, but which no longer makes much sense in today’s Internet.
Two of those services came up for review recently after the hardware that ran one of them – an ancient machine hosted at our old ISP Northwest Nexus – needed some hands-on care to bring the ftp.tidbits.com archive back online. The computer in question, an elderly Pentium-based PC running Linux, needs rebooting or fussing with every few years, and while that’s an impressive reliability record, we decided that it’s time to put it out to pasture and move its files to a server we control.
The files in question are the setext-formatted versions of our weekly issues, which some people still like to collect for archival purposes. We also distribute TidBITS in an HTML edition via email, and those static HTML files have also long been archived, should anyone want to revisit an issue. The HTML files live on our older PowerPC-based Xserve, from which we’re gradually removing services as well.
All this is by way of explaining that we are now providing static setext- and HTML-formatted files of our weekly issues in a new location on our tidbits.com machine. Should you want them, you can find them at:
Just for nostalgia’s sake, we’ve left our old TidBITS logo graphic in place on those pages, so you feel you’re back in the mid-1990s when you’re browsing the archives.
Note that these static files aren’t the primary way we provide back issues. That’s all done from our database-driven Web site now. If you visit the Back Issues page (linked at the bottom of the Weekly Issues section of the navigation bar), you can see a reverse-chronological list of back issues, complete with their abstracts.
Click one, and the issue loads, displaying all the articles and their summaries; you can instantly show the full text of all the articles in that issue, show the full text of any individual article, or jump directly to an article’s own page. Since these issues are built dynamically, not from static text files, you can click through to listen to the audio version, access the print view, and read any comments.
Why might you want the static setext- and HTML-formatted versions of our issues? We’ve heard from people who like to download back issues for offline reading in Internet-barren locations. Also, a few programmers have created tools – often for personal use – that depend on these formats.
There are undoubtedly other reasons as well, so as long as we can create these files easily, we’ll continue to keep them available as yet another way you can read TidBITS, alongside getting it via email, subscribing to our RSS feed, using the TidBITS News iPhone app, and just reading it on the Web.
Five Essential Safari Extensions
Web browsers like Firefox, Chrome, and even Internet Explorer have offered support for add-ons and extras since soon after their respective releases. Apple’s own Safari browser, however, took seven and a half years to gain support for extensions, which arrived with the recently released Safari 5.
Apple launched its own directory of Safari extensions last month; before then, Jonas Wisser’s Safari Extensions blog was the easiest place to find new extensions – but both sites can feel a bit overwhelming. There are hundreds of Safari Extensions, with more arriving every day, so it can be hard to find the signal in the noise. I’ve already dug up several extensions that vastly improve my own daily Internet surfing – perhaps they can help you, too.
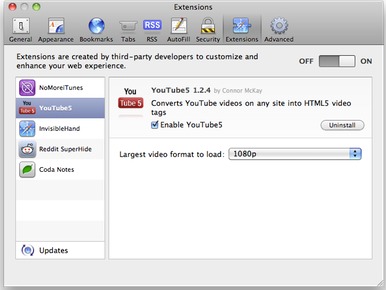
YouTube5 — Connor McKay’s YouTube5 is one of my favorite Safari Extensions – but don’t judge the extension by the creator’s Web site. Enabling this extension dramatically reduces the number of Flash videos you’ll encounter on the Web. YouTube videos, whether on YouTube itself or embedded elsewhere, will no longer use Flash; rather, they will leverage the magic of HTML5, which should mean much lower processor demands (and thus less power consumption) for your Mac.
The YouTube5 extension includes a single preference: you can choose the largest video format the extension should load when available: 360p, 720p, or full high-definition 1080p.
InvisibleHand — Created by the eponymous shopping site, the InvisibleHand extension makes me happy because I love saving money. Before I make a purchase online, I spend considerable time searching to make sure I’m getting the best deal possible. Or, at least, I used to.
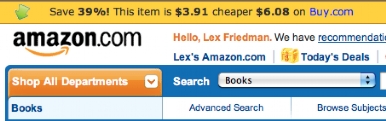
With InvisibleHand installed, you see a small yellow bar across the top of some shopping sites. That bar tells you how much you could save if you instead purchase that product from another source (it also tells you if you’re already at the retailer with the best price). For example, when I looked at the iPod touch on Amazon.com, InvisibleHand suggested that I could buy it elsewhere for $37 less – a savings of more than 20 percent.
When InvisibleHand works, it’s awesome, and can save you some serious coin. Unfortunately, the extension does have a few weaknesses: You can’t configure which other online retailers it should search, so if you’d prefer not to see, say, eBay price comparisons, you’re out of luck.
NoMoreiTunes — Another Safari extension that works to eliminate one major Web-browsing annoyance goes by the catchy name of NoMoreiTunes. Whether you’re clicking on an iPhone or iPad app link, or an iTunes song or movie, you always know what to expect: After the Apple-hosted preview page loads, then iTunes opens, and it (slowly) loads the content you were after.
Well, that’s what happened in the era before NoMoreiTunes. Now, when I click those links, I see Apple’s preview page for the given content (like this one) – and iTunes remains undisturbed. It’s delightfully refreshing. It would be nice if Apple would code its iTunes Preview Web site so it doesn’t pop open iTunes anyway, but until Cupertino comes to its senses, NoMoreiTunes makes a great sanity restorer.
[Editor’s note: It appears that Apple has indeed come to its senses and changed this behavior on the iTunes Web site after the initial publication of this article, so there’s no need for NoMoreiTunes any more. -Adam]
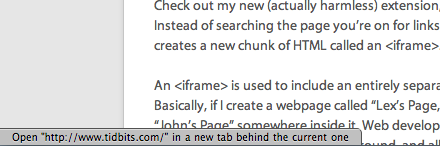
Ultimate Status Bar — Safari’s status bar – the strip at the bottom edge of your browser window that displays a URL when you hover the cursor over a hyperlink – is off by default, but once you turn it on, it’s always there. In some browsers, like Google Chrome, the status bar appears only when necessary when you move your cursor over a link.
Ultimate Status Bar emulates that behavior, freeing a few precious vertical pixels to show you more of your Web pages. On top of that, the extension offers numerous benefits over Safari’s default status bar. For one thing, you can change its appearance; the extension includes ten themes, from the subtle Classic to the technicolor, unicorn-laden Sparkle. Beyond that, it shows the destination URL’s favicon and even expands shortened URLs like those you’d find on Twitter, so you can know where you’re going before you click. And the extension can even show the size of a linked file to download.
A promising competitor called Gentle Status Bar offers similar functionality, but hews much more closely to Safari’s own design aesthetic, with the added benefit of reflecting when you’re holding down keys that will make the clicked link open in a new window or tab. But it lacks some of Ultimate Status Bar’s niceties, like revealing the favicon or file size for the link in
question.
AutoPagerize — Many Web sites break their articles into separate pages, to encourage extra page views (which lead to extra ad impressions). AutoPagerize magically makes that extra clicking (and waiting for pages to load) go away. Subsequent pages of the article you’re reading simply load right into the page, waiting for you to scroll down and read them. The Japanese developer’s Web site is a bit tough to parse, but I needed only to install the extension to start using it successfully.
But Wait, There’s More — While those five extensions are the ones that most regularly impact my daily Web surfing, there are plenty of others. John Siracusa’s standalone Reload Button, an unofficial Instapaper button called Instafari, the Reddit-improving extension Reddit SuperHide, and Panic Software’s Coda Notes all provide handy features and are worth trying out. Apple’s own directory includes new extensions from big partners like Twitter, The New York Times, and Major League Baseball; those are certainly worth a look, too.
In another, not-too-distant life, I was a Web developer. Since Safari Extensions just use familiar bits of Web code – like HTML, CSS, and JavaScript – I realized that I could create some for my own purposes. To date, I’ve built two. The first, Facebook Improved, removes considerable amounts of cruft from that social networking site – invasive ads, unnecessary elements
(that ever-present callout to create an event), and the like. It also changes the site’s font to Helvetica, and makes subtle changes to the placeholder text on certain fields to ensure you never get confused about whether you’re posting on someone else’s Wall or your own.
My other extension, Affiliatizer for Safari, automatically rewrites Amazon links across the Web so that they include the Amazon affiliate code of your choosing. The extension, which affects only links that don’t already include affiliate codes of their own, accepts up to three affiliate codes, and picks one at random on each page view. It’s a nice way to reward yourself, or a friend who has an affiliate code. By default, the app includes my affiliate code and those of our friends John Gruber and Jason Snell, until you save your own preferences instead.
But ounce for ounce, no extensions benefit my day-to-day Web surfing as much as YouTube5, InvisibleHand, NoMoreiTunes, Ultimate Status Bar, and AutoPagerize. Try them out, and you’ll see for yourself how handy these tools are when you’re on Safari. And of course, if you decide you don’t like what a particular extension does for you, just visit the Extension pane in Safari’s Preferences window to uninstall it.
Apple’s iOS Security Challenges and Advantages
One of the most controversial debates in the security world has long been the role of market share. Are Macs safer because there are fewer users, making them less attractive to serious cyber-criminals? Although Mac market share continues to increase slowly, the answer remains elusive. But it’s more likely that we’ll see the answer in our pockets, not on our desktops.
The iPhone is arguably the most popular phone series on the face of the planet. Include the other iOS devices – the iPad and iPod touch – and Apple becomes one of the most powerful mobile device manufacturers, with over 100 million devices sold so far. Since there are vastly more mobile phones in the world than computers, and since that disparity continues to grow, iOS devices become far more significant in the big security picture than Macs.
As reported in this CNET article, the iPhone (and by extension, other iOS devices) is already seeing greater scrutiny by the security research community. I can personally attest to the fact that many of my security research associates are gaining interest in mobile devices of all types, but especially iOS- and Android-based devices. And if the number of mobile banking and retail apps in the App Store is any indication, there is now broad use of these devices for significant financial transactions (beyond teenagers’ massive texting bills).
Smartphones Change the Security Game — While mobile phones may never have been the most secure gadgets, their security issues were limited until wide adoption of smartphones. The worst you had to worry about was someone cloning your phone and running up your bill with international calls. Even early smartphones were fairly limited due to their clunky interfaces, terrible browsers, minimal penetration outside of the enterprise, and lack of consistency. But the iPhone ushered in a new age of popular and extensible smartphones. The combination of popularity and functionality changes the mobile security landscape in a number of fundamental ways:
- iOS devices are based on a general-purpose operating system with a larger attack surface than less-sophisticated “feature” phones.
- iOS is widely deployed in three major product lines. While the operating system versions aren’t fully aligned, they are extremely close, rely on the same code base, and are likely to converge more soon.
-
Consumers increasingly use their mobile phones for sensitive transactions – mobile banking, shopping, and confidential communications. Bad guys accessing a device have far more to gain than in the past, when the worst they could do was steal your contacts and make phone calls.
-
Email and Web browsing are the top two vectors for attacking personal computers… and they are also the two most popular non-phone functions on iOS devices.
The good news is that although Apple faces new security challenges with their mobile devices, they have already laid a strong security foundation with the potential for far greater security than we will ever see on general-purpose computing platforms like the Mac.
Since I prefer to end on a high note, let’s start with some of Apple’s security challenges, and close with the company’s potential advantages.
Apple’s Mobile Security Challenges — The primary problems Apple faces with the iPhone aren’t the hardware, or even the software, but their internal processes and the difficulties of maintaining security on multiple platforms (mobile or otherwise) with a common code base.
First, Apple is historically slow to offer patches for known vulnerabilities fixed in the open source components used in OS X. For example, one of the first exploits used to enable jailbreaking was a known flaw in a common software library used for displaying TIFF images. Since this flaw was patched for other platforms long before the iPhone, it provided attackers a direct road map into the iPhone. While Apple has skated by with these sorts of exposures in Mac OS X (including flaws for the Apache Web server, Samba for Windows-compatible file sharing, and the MDNS service that underpins Bonjour), the increasing scrutiny on the iPhone shortens the time between when a component is patched for other platforms, and when an iOS user is at
risk.
Second, Apple also patches their own software flaws on different schedules for different platforms, potentially exposing users to more risks. For example, Apple sometimes patches security flaws for the Mac version of Safari before fixing the same flaws for Mobile Safari. iOS is a version of OS X, and thus it’s only to be expected that some security flaws will carry through to both platforms. Apple has even patched the open source version of the WebKit code that underlies Safari (which they manage) before bringing the same fixes back into Safari itself.
These process-related issues likely represent the single greatest combined security risk for iOS devices. Every time some vulnerability is patched on another platform, either an open source component or a piece of Apple’s proprietary software, it may give attackers another way to exploit iOS devices.
Apple faces several additional security challenges. Most notably, since jailbreaking relies on the exploitation of security vulnerabilities, any time a new jailbreak is released, it may provide attackers with yet another way to attack iOS devices.
In some cases this isn’t a major concern, since jailbreaking relies on physical control of the device. But as the jailbreakme.com site shows, these exploits can sometimes be activated simply by browsing a Web page. Think of it this way – even if cyber-criminals aren’t willing to put in the hard work to break into iOS devices, jailbreakers are. And once a jailbreak is released, the bad guys are free to turn it into an offensive weapon. (And yes, for the record, every jailbreak is a security exploit.)
Finally, while iOS has significantly better security than Mac OS X, there is still major room for improvement, especially in the sandboxing of some of the native Apple applications, such as Safari. Of all the iOS security risks, these are the easiest for Apple to address.
Apple’s iOS Security Advantages — Although the security of iOS devices is under greater scrutiny than that of nearly any other mobile device (the possible exception being RIM’s BlackBerry, and with Google’s Android undoubtedly receiving an increasing amount of attention), iOS devices also come with some significant security advantages:
- No other mobile device is as easy to patch and update. Before the iPhone, the only way to patch the majority of phones on the market was to take the device into a retail store and beg for an update, or hack it yourself through a Byzantine process that frequently involved illegally downloading carrier software. For the first time we have a popular, widely deployed, mobile device that is as easy to update as any other software on your computer.
-
iOS devices are difficult to hack. Apple has combined the hardware and software to lock down the platform in ways that aren’t possible on a general purpose computer without severely restricting the user experience. While some users complain about Apple’s rigid control, it does provide some extremely important security advantages. For instance, all applications are cryptographically signed with digital certificates tied to the device’s hardware, making it extremely difficult to install malicious software. Yes, we’ve seen exploits that circumvent these controls, but creating such exploits tends to require a high degree of skill.
-
The iOS is a closed system. All apps are vetted and distributed by Apple, with the exception of enterprise-specific apps that are managed by internal IT departments and that have limited distribution. Although we are sure to see malicious apps sneak through the App Store eventually, Apple can quickly remove these when identified. This has already happened on the open Android Marketplace, where a malicious wallpaper app was downloaded by millions before being identified and removed. We’re trading a closed system and some freedom for increased security (something I worry about in society in general, but I’m
okay with when it comes to a phone… as long as they don’t listen to my calls). -
Greater market share and public scrutiny means that Apple faces considerable public pressure to keep the platform secure. As Microsoft learned in the late 1990s, security failures directly translate to material market risk when you’re the big dog in the industry. When a minor antenna problem appears on the front page of every major newspaper, it’s clear that a major security breach could cause much worse problems for Apple.
Security Wins, For Now — In the overall calculation of security challenges versus advantages, Apple’s iOS devices are in a strong position. The fundamental security of the platform is well designed, even if there is room for improvement. The skill level required to create significant exploits for the platform is much higher than that needed to attack the Mac, even though there is more motivation for the bad guys.
Although there have been some calls to open up the platform to additional security software like antivirus tools (mostly from antivirus vendors), I’d rather see Apple continue to tighten down the screws and rely more on a closed system, faster patching rate, and more sandboxing. Their greatest opportunities for improvement lie in increased awareness, faster response processes, and greater realization of the potential implications of security exposures.
And even if Apple doesn’t get the message now, they certainly will the first time there is a widespread attack.
TidBITS Watchlist: Notable Software Updates for 16 August 2010
VMware Fusion 3.1.1 — VMware Fusion, which lets you run Windows and other operating systems on your Intel-powered Mac, has been updated to version 3.1.1. The maintenance-focused update now supports VMware vSphere 4.1 as a guest operating system, enabling you to run ESX without needing spare hardware – though this feature is currently labeled as experimental and the company warns against using it in production environments. The update also addresses an issue with some iSight cameras, removes an incorrect disk error message after a host crash, and corrects an issue where audio recording worked only at 44.1 kHz. VMware Fusion requires Mac OS X
10.4.11 or higher, and of course a copy of Windows if you plan to install that operating system. The download is accessible from within VMware Fusion itself, or from the VMware Web site. ($79.95 new, free upgrade, 434 MB)
Read/post comments about VMware Fusion 3.1.1.
Things 1.3.5 — Cultured Code has rolled out a series of fixes to its flagship task management app Things. The 1.3.5 update resolves several crashing bugs, including crashes when rescheduling to-dos in the Today view. Other improvements include fixes for an issue with iCal calendars not being visible when using Custom iCal Sync, an issue where double-clicking a to-do could open the wrong item in certain views, and an issue with resorting to-dos when filtering by tag. Rounding out the detailed release notes are other fixes addressing localization quirks, toolbar icons, Daylight
Saving Time, project tags, and miscellaneous user interface issues. ($49.95 new, free upgrade, 8.0 MB)
Read/post comments about Things 1.3.5.
Office 2004/2008 Security Updates — Microsoft has released a trio of software updates addressing various security issues in its Office suites. The updates – Microsoft Office 2008 for Mac 12.2.6 Update, Microsoft Office 2004 for Mac 11.6.0 Update, and the Open XML File Format Converter for Mac 1.1.6 – patch an issue where maliciously crafted files opened in Excel or Word could enable an attacker to execute code on your Mac. The Office 2008 update also updates Microsoft Entourage’s time zone information and fixes some Excel crashes that could occur on launch, when sorting merged cells, or editing cells. The updates are free, and Microsoft recommends Office users install them as quickly as possible. Be sure not to cancel or interrupt the installation process, or your Office installation may be left in a non-functional state (if this has already happened, reinstall from your original media and then install all necessary updates before using
Office again).
Read/post comments about Office 2004/2008 Security Updates.
ExtraBITS for 16 August 2010
Just two quick bits for you this week – a hearty congratulations to the inimitable Nitrozac and Snaggy for the 10th anniversary of their Joy of Tech comic and a link to an academic paper showing that smartphone passwords could be hacked by virtue of screen smudges.
Joy of Tech Comic Celebrates 10th Anniversary — Congratulations to Nitrozac and Snaggy for 10 years of their technology-focused Joy of Tech comic, which has long been a regular stop for all of us here at TidBITS. If you’re not reading it, you’re missing out on one of the top sources of technology humor, often with a wry emphasis on the world of Apple.
Smartphones Susceptible to Smudge Hacking (PDF) — Don’t get too paranoid about this, but security researchers at the University of Pennsylvania have shown than Android graphical passwords can be recovered by photographing the screen of a smartphone and analyzing the smudge patterns. There isn’t much likelihood of this attack being used widely, because its utility requires either gaining control of the smartphone or the same password being used elsewhere, and the screen can easily be cleaned. But it’s still interesting just where security vulnerabilities will be found.