TidBITS#1118/19-Mar-2012
We don’t focus on financial news much, but Adam found some fascinating details in Apple’s announcement that it would start using some of its cash to pay quarterly dividends and to repurchase stock. Other articles in this wide-ranging issue include Jeff Carlson’s explanation of how to use iTunes Match to get higher-quality, DRM-free copies of your music; Adam’s review of the CloudPull utility for backing up your Google Docs, Gmail, and other Google data locally; and Glenn Fleishman’s analysis of a recent Elcomsoft white paper criticizing the security of iOS password-keeping apps. Finally, we’re pleased to welcome as a long-term sponsor Fujitsu, makers of the ScanSnap family of document scanners. Notable software releases this week include Aperture 3.2.3, Sandvox 2.5.3, and Firefox 11.0.
Apple to Pay Quarterly Dividends and Repurchase Stock
The longstanding question of just what Apple would do with its tens of billions of dollars in cash gained at least two answers today, in an Apple conference call with press and analysts. CEO Tim Cook and CFO Peter Oppenheimer announced that Apple will start paying a quarterly $2.65 per share dividend, starting in the September quarter (which, if I’m doing the math right, would be Apple’s fiscal fourth quarter of 2012). That will reportedly make Apple one of the largest dividend payers in the United States. Plus, starting in
the December quarter (Apple’s fiscal Q1 2013), the company will start to repurchase Apple stock to limit the future dilution of share ownership from employee stock grants and the employee stock purchase program. All told, over the next three years, Apple anticipates spending $45 billion on these programs. (Of course, as our friend Marshall Clow pointed out, this level of expenditure won’t reduce Apple’s cash hoard but will only make it grow more slowly.)
Tim Cook took pains to emphasize that innovation remains Apple’s most important objective, given that the decision to start paying dividends generally indicates that a company feels it can no longer increase profits by rolling money back into the business. For instance, Cook said that although Apple sold 37 million iPhones in the last quarter, that represented less than 9 percent of the handsets sold overall. The worldwide cell phone market is expected to grow from 1.6 billion units in 2011 to over 2 billion by 2015, with all handsets becoming smartphones eventually, which Apple takes as indication that iPhone sales won’t be slowing any time soon. Add to that Apple’s 55 million iPads sold at the end of the most recent quarter,
viewed against Gartner’s estimate that the tablet market will reach 325 million units by 2015 and Apple’s belief that the tablet market will eventually surpass the PC market, and you can see how Apple doesn’t believe its growth will be leveling out in the near future.
It’s hard to argue — Apple has been generating cash at an unprecedented rate over the last few years, even while investing money into R&D, acquisition, retail stores, strategic prepayments and capital expenditures in the supply chain, and infrastructure. Also mentioned as an investment, interestingly, was a direct enterprise sales force — Apple may not be designing products explicitly for the enterprise, but the company is apparently working to sell into that market. Apple will continue to do all these things, and retain a war chest for unanticipated opportunities and contingencies, but Apple’s Scrooge McDuck money pit is still overflowing.
So what to do with the excess? Start returning some of it to shareholders in the form of a quarterly $2.65 per share dividend. That will, Cook said, not only provide income to current investors, but will also make Apple stock more attractive to a different class of investor. That last statement is certainly true, but it’s hard to know why Apple would care. My best guess is that dividend-oriented investors tend to buy and hold, so an increase in that class of investor could reduce some level of volatility in Apple’s stock price. Although Apple will include past and future unvested employee stock in the dividend program, Peter Oppenheimer said that Tim Cook asked that his unvested shares not be included in the dividend program.
The other half of the announcement is a stock repurchase program, under which Apple will buy back company stock in order to reissue it to employees, either in the form of grants or through the employee stock purchase plan. Presumably, Apple anticipates distributing enough stock to employees — likely an ever-increasing number — that the repurchase is deemed necessary to avoid the need to issue new stock, thus diluting the price.
During the Q&A session, in which analysts largely asked questions that Cook and Oppenheimer had said they wouldn’t answer and then didn’t, the topic of a stock split came up. Apparently, Apple has considered splitting the stock, which would reduce the price (currently about $600 per share) and increase the number of outstanding shares, but Cook and Oppenheimer said that while there was little evidence that a split would help Apple in any way, they were continuing to evaluate it.
Interestingly, all the cash that will be used for the quarterly dividends and the stock repurchase will come from cash held within the United States. Although Apple could end up with nearly $100 billion (by one analyst’s off-the-cuff estimate) in cash holdings abroad by the end of the year, current U.S. tax law makes repatriating foreign cash expensive. Though we don’t hear about Apple lobbying the government much, Cook said about this situation, “We have expressed our views with Congress and the administration.”
ScanSnap Sponsoring TidBITS
We’re pleased to welcome as our latest long-term TidBITS sponsor Fujitsu, makers of the ScanSnap family of document scanners for home and small business use. They have been stalwarts in the Macintosh world for years, and it’s not an exaggeration to say that the ScanSnap was a key piece in Joe Kissell’s efforts to eliminate (or at least significantly reduce) paper in his life, leading to the publication of “Take Control of Your Paperless Office.”
The ScanSnap line starts with the $199 ScanSnap S1100, a diminutive portable scanner powered by a USB cable and capable of single-sided scanning at 8 pages per minute (ppm). For double-sided scanning, a 10-sheet automatic document feeder, and faster performance in a slightly larger and heavier package, there’s the $295 S1300, which is what Tonya chose last year when she finally buckled under the barrage of school papers and forms (see “Dragging School Papers into the 21st Century with a ScanSnap,” 30 September 2011). And for heavier-duty use
there’s the $495 S1500M, a full-fledged desktop scanner that has a 50-sheet automatic document feeder, scans in duplex at 20 ppm, and has the most complete software bundle of the three.
Speaking of software, all three scanners come with ScanSnap Manager and Cardiris 3.6 for scanning business cards and ABBYY FineReader for ScanSnap for optical character recognition, and the S1500M adds Adobe Acrobat 9 Professional.
Thanks to their longstanding presence, the ScanSnap scanners have broad third-party software support, so you can scan directly into Evernote, SugarSync, Salesforce Chatter, and Google Docs. The ScanSnap scanners can’t yet communicate directly with an iOS device; to accomplish this task, Fujitsu has released the free ScanSnap Connect iOS app that enables you to move scanned documents and images from a Mac or PC to an iOS device.
Thanks to Fujitsu for their support of TidBITS and the Apple community!
iTunes Match Improves Sonos Music Selection
I wasn’t initially excited about iTunes Match, Apple’s service for accessing music you’ve purchased via iCloud, but I signed up for it anyway because I knew I’d need to write about it for TidBITS and my books about the iPad. My purchase of a Sonos stereo system, however, has more than made the $24.99 annual fee for iTunes Match worth it.
Until recently, if we wanted to listen to music in our living room, we had to do it through our HDTV by way of an Apple TV (we didn’t have a functional stereo). It wasn’t a terrible setup — the room isn’t large — but I hated having to power the entire TV just to listen to music. I decided to buy the Sonos Play:5, a $399 single unit that features five speakers and a wireless network connection. (For more about the Sonos system, see “Audio Bliss: Sonos Digital Music System,” 23 January 2006.)
It’s a great solution. With the addition of the Sonos Bridge, a wireless device that connects to my AirPort Extreme via Ethernet and routes music to the Play:5, I can access the music library stored on a Mac mini in my office. I control playback using the free Sonos Controller app for the iPad or iPhone/iPod touch.
However, there’s a problem — a problem that’s fading into the past, but still a problem. The Sonos system, as well as other devices that can play iTunes content, can’t play older FairPlay-protected tracks. Apple stopped wrapping purchased music in annoying DRM in 2009 (see “iTunes Drops DRM from Music, Initiates Tiered Pricing,” 7 April 2009), but I never bothered to update my tracks (which cost $0.30 each); the songs played fine on my computer and iOS devices, so there was no urgent need.
Unfortunately, those songs are invisible to the Sonos. I could convert them to another format, but iTunes Match provides an easier and higher quality solution. Plus, I don’t have to pay anything more than that initial $24.99 fee; I can keep the upgraded tracks even if I choose not to renew my iTunes Match service.
Here’s what I did to locate and convert the files, and to make them available to the Sonos. As a bonus, this process gave me higher quality versions of songs I ripped at bit rates below the 256 Kbps rate of tracks in iTunes Match.
Warning! You need to be an iTunes Match subscriber and have iTunes Match completely updated before doing any of the following. But you don’t need a Sonos or other device to take advantage of this technique of getting higher quality, DRM-free copies of your music.
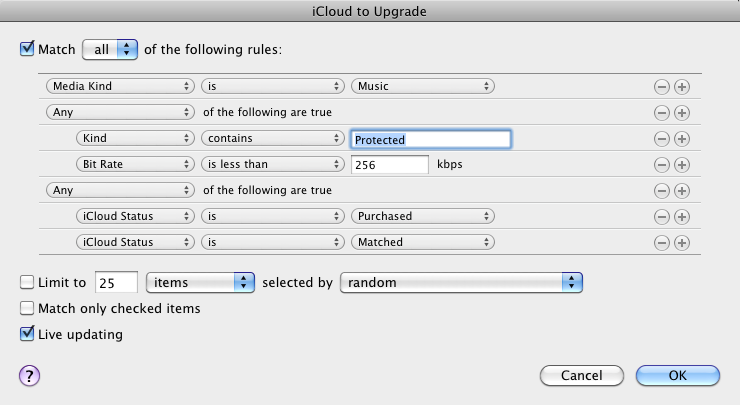
Create a Smart Playlist — First, to locate the DRM-shackled songs, create a new smart playlist in iTunes by choosing File > New Smart Playlist and set it up with the following attributes.
- Media Kind is Music
(Nest the following two conditions by Option-clicking the plus-sign (+) button to the right of the previous attribute, and change All to Any from the “of the following are true” pop-up menu.)
- Kind contains Protected
- Bit Rate is less than 256 kbps
(Nest these two as well, also as Any instead of All.)
- iCloud Status is Purchased
- iCloud Status is Matched
Lastly, click OK to create the playlist. It appears in the iTunes sidebar ready to be named.
This smart playlist goes above and beyond finding protected tracks by identifying any whose bit rates are less than 256 Kbps. If you’re going to sweep through your library to replace protected tracks, you might as well replace low quality tracks in the same pass.
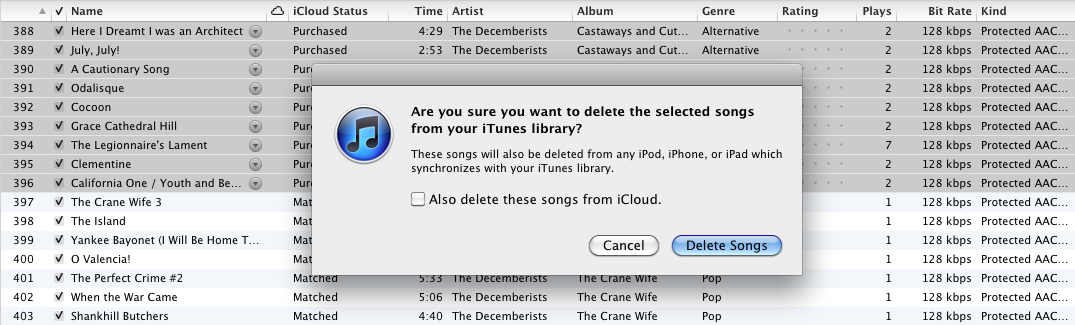
Delete Local Files — The next step is to delete the local files. That seems like a drastic action, but remember, all music matched by iTunes Match exists on iCloud, either in the form of a copy already stored by Apple or a copy uploaded for any of your files that are missing from the iTunes Match database. (That said, I always recommend having a backup before deleting anything.)
Select a group of songs (or all of them), hold Option, and press the Delete key (Option-Delete enables you to delete tracks from within a playlist, even a smart playlist that doesn’t normally allow manual editing). When iTunes asks for confirmation, make sure the option to delete files from iCloud is not checked.
In the next dialog that appears, click the Move to Trash button to remove the old files from your hard disk. The songs remain in your library, but their iCloud Download status is set to Not Downloaded.
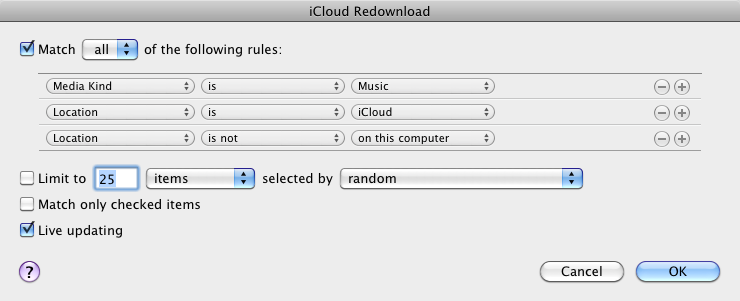
Locate and Re-download Songs — Deleting the files removes them from the smart playlist, so another one is required to make them visible again. Create a new smart playlist with the following attributes.
- Media Kind is Music
- Location is iCloud
- Location is not on this computer
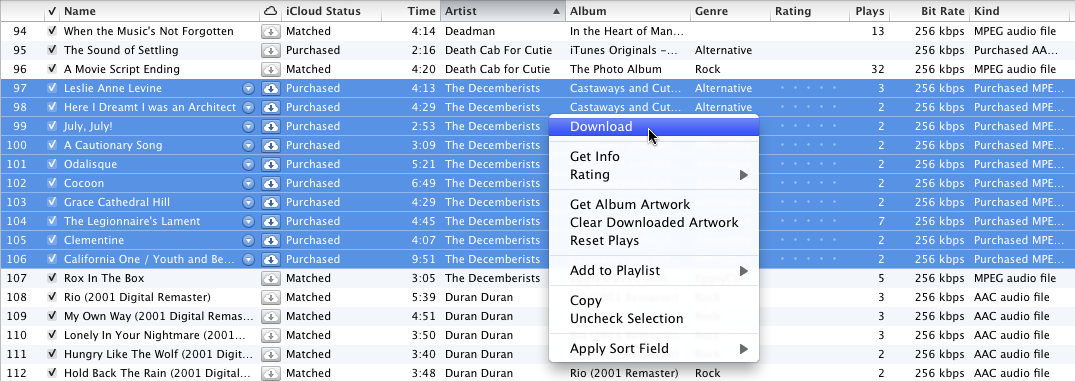
Next, select the songs you want to re-download. Control-click (or right-click) one of them to bring up the contextual menu and choose Download to get high-quality, DRM-free copies.
Or, to download everything listed (which could involve multiple gigabytes of data and might best be done overnight), click the iCloud button to the right of the smart playlist’s name in the sidebar when the playlist is selected.
Update the Sonos Database — The last step in my situation was to make the Sonos speaker recognize the new files — if you’re just following along to get higher-quality, DRM-free copies of your songs and you don’t have a Sonos, you’re done.
Otherwise, in the Sonos Desktop Controller software, choose Music > Update Music Now to re-index the music library. You could also do this from the Sonos Controller iOS app: tap the Music button, then go to Settings > Manage Music Library > Update Music Index Now.
After the Sonos software finishes indexing, the previously unavailable songs will be ready to play.
Back Up Your Google Data with CloudPull
Do you trust Google? Let me rephrase that. Assuming that you trust Google sufficiently to use their services — Gmail, Google Docs, Google Calendar, Google Contacts, and Google Reader — do you trust Google not to lose your data? It’s a legitimate question to ask of any cloud-based service, and it’s especially important to ask of those services that are free and lack official support.
As with any discussion of backup, it’s important to consider all possible sources of problems. Personally, I don’t worry much about my data at Google — I believe that Google is exercising all due diligence to ensure that nothing disappears due to hardware or software failure. But all that data is protected by nothing more than a password, and it could be stolen or cracked by some nefarious character. James Fallows wrote movingly about his wife’s Gmail account being taken over; the attacker deleted six years’ worth of correspondence — over 4 GB of stored messages and attachments that wasn’t backed up (Google was able to recover it in the
end).
Don’t discount human error, too, either your own or programmer error. It’s not inconceivable that you could become confused and accidentally delete a calendar or document, either directly or within some utility software that provides access to your data on Google.
Backing Up the Cloud — For peace of mind, therefore, a backup is necessary. But traditional backup programs protect the data on your hard disk, not data hosted in Google’s data centers. You can sync certain types of cloud data, such as email, calendars, and contacts, by pointing Apple Mail at Gmail, iCal at Google Calendar, and Address Book at Google Contacts. But for other types of data — most notably documents in Google Docs — none of Apple’s programs can help. Plus, as noted just above, synchronization can be dangerous, since actions on your Mac can result in data being deleted on Google.
The solution is CloudPull 2.0, from Golden Hill Software, which does exactly what you’d want from a Google-focused cloud backup program, downloading all your data from Google using read-only APIs over a secure https connection. The 1.x version of CloudPull supports Google Docs, Google Calendar, Google Contacts, and Google Reader, and the just-released 2.0 version adds support for Gmail. (The 2.0 version has a few other welcome features too, but since it works only with Mac OS X 10.7 Lion, Golden Hill Software will be maintaining and continuing to sell CloudPull 1.5 for those who need to use it under 10.6 Snow Leopard.)
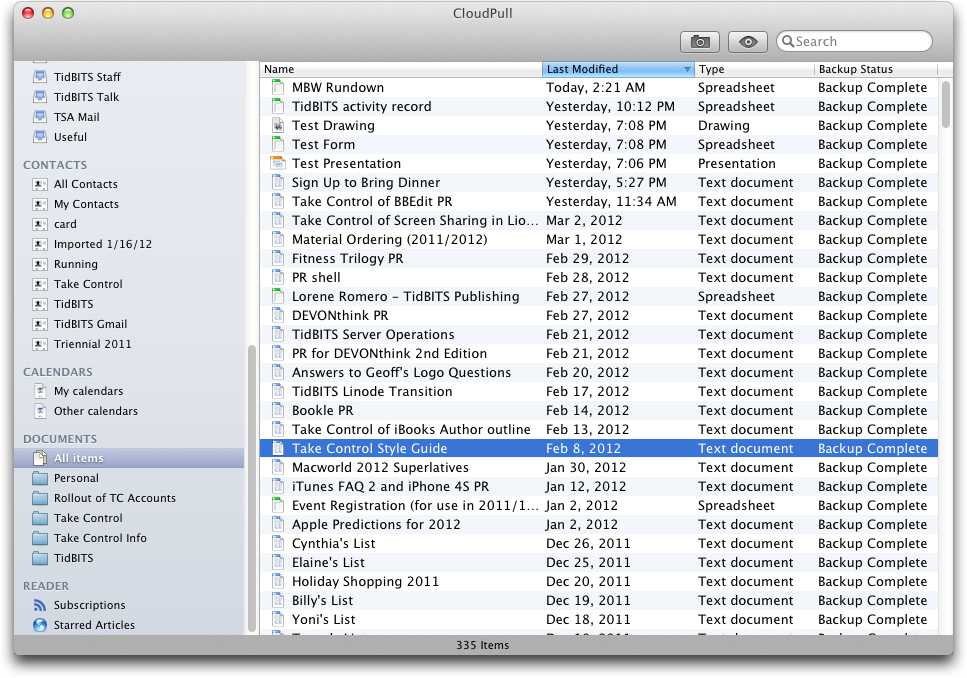
CloudPull stores backed-up data in common, easily readable formats, which means the following:
- Gmail: Email messages are stored in .emlx format, suitable for importing into Apple Mail. CloudPull maintains Gmail labels, which can be dragged from CloudPull’s sidebar to the Desktop for export, and later imported into Apple Mail as mailboxes.
- Google Calendar: Calendars are stored as .ics files and can be imported into iCal if necessary. (Individual events aren’t accessible on their own.)
-
Google Contacts: Contacts are stored as .vcf files that you can add to Address Book. Groups are maintained within CloudPull but can’t be exported in their entirety.
-
Google Docs: CloudPull converts documents into appropriate Microsoft Office formats, so word processing documents become Word documents, spreadsheets and forms become Excel documents, and presentations become PowerPoint documents. Drawings turn into .png files and documents of other types in Google Docs retain their original formats.
-
Google Reader: Subscriptions and starred articles are retained as .inetloc bookmark files that open in Safari.
What’s more, for document types (everything in Google Docs, calendars, and contacts) that can be changed online, CloudPull downloads and maintains multiple versions as independent documents so you can always go back to an earlier state of a document.
Using CloudPull — Setting up and using CloudPull is simple. A pair of first launch dialogs collect your Google account credentials and let you specify which Gmail labels you want to include in your backup. Before you configure this second dialog, make sure your Gmail IMAP settings are correct.
In the second dialog, it’s easiest to select all labels, but it might be worth thinking about whether there are certain labels, such as those associated with mailing lists you no longer read, that you really don’t need to back up. And remember, since messages in Gmail can have multiple labels, just because you deselect a particular label doesn’t mean that the message won’t be matched by some other label.
With that configuration out of the way, CloudPull connects to Google and starts downloading your data. This will take some time — perhaps a number of days, depending on how much email you have stored in Gmail. (Luckily, other types of data aren’t blocked by the slow initial email download, and, to my mind, the Google Docs backup is the most important.) Once that’s started, take a few minutes to check out CloudPull’s preferences.
You can change your Google account settings (double-click your email address to work through the two first launch dialogs again) or add another account. I’ll probably back up Tristan’s Google account onto my Mac with CloudPull, along with my own, since it would be a very bad thing if something were to happen to his homework files in Google Docs at the wrong time.
Another interesting option is how long to keep snapshots and outdated backups — 30 days, 90 days, 1 year, or indefinitely. You can choose whether to show deleted files, and if CloudPull should run as a background app to get it out of the Dock and application switcher; its menu bar icon then becomes the primary interface. It’s also possible to set how often CloudPull backs up (from every hour to once per day) and where it stores backups (in ~/Library/Application Support/CloudPull/backups by default). Finally, exclusion rules enable you to exclude specific items from your backup based on name and kind.
Once CloudPull has completed its initial backup, it watches your Google account for changes on the schedule you’ve set, bringing down new and changed data as necessary. Most people will just leave CloudPull running in the background at that point. It launches at startup by default, and you’ll want to let it do that in most situations.
Backups are useful only if you can restore data from them, though, and that’s where you’ll eventually interact with CloudPull. It offers a single iTunes-like window with a sidebar containing collections for each type of backed-up data; the items in each collection appear as a list in the main pane of the window. In CloudPull 1.x, a right-hand pane showed the history of the file; in CloudPull 2.0, the history is available as a popover that you call up by Control-clicking the item and choosing History of… from the contextual menu. The new approach is a bit clumsier, but realistically, it’s so unlikely that you’ll need to use it that burying it in the interface makes sense.
Quick Look (available by pressing the Space bar or clicking the Quick Look button in the toolbar) lets you preview items in CloudPull’s window, and you can double-click them to open them in the associated program (see the bullet list above for details).
Opening items shouldn’t be done willy-nilly. For data types that import, like email, calendars, and contacts, CloudPull hands the data off instantly, which may add data to iCloud or Address Book in undesirable ways. For document data types, CloudPull opens the file in the associated program, but read-only, so you can’t make changes without first saving a copy. A better approach is to drag items out of CloudPull’s window to the Desktop, which “restores” them in a more controlled fashion, after which you can import or
open the item as you wish.
Although you will most likely want to restore the latest version of backed-up items, or an older version of a particular item, the new snapshot feature in CloudPull 2.0 shows the state of your Google-based data at a particular point in time. It seems mostly useful if there’s a data corruption event that you don’t notice right away, such that you want to restore data other than the latest version.
Frankly, CloudPull does exactly what it promises, and provides a welcome local backup of Google-hosted cloud data. My main criticism is that it’s very slow to download the initial set of email, much slower than IMAP-savvy email programs I’ve used (the speed improved some in version 2.0.2). It could take days to complete the initial download, and the only progress indicator appears when you stop the backup from CloudPull’s menu bar icon’s menu, and then look at that menu again once stopped. Golden Hill Software is aware of these issues and is working on them for an update. Otherwise, I prefer the more-colorful sidebar in the 1.5 version in Snow Leopard to the near-monochromatic look in the 2.0 version in Lion, but that’s minor.
I would like to see CloudPull support other cloud services in the future, such as those from Yahoo and Microsoft, but perhaps Golden Hill Software is planning that for CloudPull 3.0.
CloudPull 2.0.2 is available at an introductory price for $24.99, either from Golden Hill Software directly or from the Mac App Store (TidBITS members save 20 percent on direct orders, dropping the price to $19.99). If you use Google Docs heavily, or don’t currently have a good IMAP-based backup of your Gmail account, I encourage you to buy a copy right away. But a 30-day demo is available, so if you’re at all on the fence, you can give CloudPull a try and get at least a month of snapshots locally.
Elcomsoft Criticism of iOS Password Apps Overblown
Major password-keeping apps for iOS use encryption techniques that, depending on the strength of the master password, can be easily overcome in under a day, revealing all of the ostensibly secured passwords, security firm Elcomsoft said in a security conference presentation in the Netherlands. Short passwords and numeric PIN-style passwords are allowed in such software, although it’s unclear how many users might opt for such weak choices. A full explanation is in an associated white paper (PDF) that provides mathematical and encryption details. You may see this reported breathlessly as “Password Safes Unlocked!” The reality is nowhere near that worrying, but the
report is worth examining.
The list of examined apps includes 1Password Pro, LastPass Premium, and mSecure, three of the most popular iOS password keepers available. However, the risk is quite low even without considering the issue of short (six or fewer characters, including letters, numbers, and punctuation) or solely numeric passwords. For starters, access to the app’s data store is required — either via an iTunes backup or an iOS device containing the app and its data — and any iOS security controls must be bypassed first. The flaws that Elcomsoft has identified cannot be exploited (as far as is currently
known) over the Internet, which further limits exposure.
The Risk Scenario — Elcomsoft analyzed 14 apps for iOS and 3 for BlackBerry OS. Of those, 7 had inadequate protections allowing instant recovery of a master key no matter the password’s composition because, the firm said, data is stored with no encryption, protected only with a static password built into the software, or protected by a key derived from flawed cryptography. (The white paper provides app-by-app details, so you can read about any app you may use.) In all cases, the researchers needed access to the app’s data store, which means first circumventing any iOS security protections, also discussed in the white paper.
In order to extract information from one of these iOS apps, a cracker needs physical access to the device and the ability to bypass certain security protections, or access to either an iTunes backup of the device or an image of the device’s storage. App data can be extracted from a local iTunes backup if the backup is unencrypted, or if the backup is encrypted and a cracker knows or can guess the backup password.
If you use iCloud for backups or have a strong, secret iTunes backup password, your device backups aren’t vulnerable. There is more risk if the cracker obtains access to your actual device, but that person must have significant forensic skills and software, and extracting the app data might take an inordinately long time. Such extraction may not be possible at all on the latest iOS hardware when it’s properly protected with a passcode that’s not easily guessed (don’t pick “1234” or “4444”, for instance). If locked, the passcodes used by the iPad 2, third-generation iPad, and iPhone 4S are entirely secure unless the device was jailbroken before being locked.
In short, although it’s extremely distressing to hear that so many iOS apps aren’t doing as good a job protecting your data as would be ideal, the risk for any given person is very low — and nearly zero if you use a strong password. Where that risk becomes higher is if you rely on a cryptographically weak password and a particular individual who has or can hire the necessary skills targets you specifically. If you’re going through a messy divorce, work on secure and private matters (governmental, rebel, legal, banking, or other), or express unpopular opinions widely in public, I recommend that you immediately change your app’s master password to one that’s stronger, encrypt any local iTunes backups, and set at least a
four-digit iOS passcode. You should also delete old iTunes backups that are not encrypted (see “Deleting a Backup,” in this Apple support note).
All the flaws relate to how the apps protect their stored password data locally. In the case of 1Password, mSecure, and LastPass, stored data cannot be cracked immediately, but Elcomsoft estimates that for those three (and seven others on both iOS and BlackBerry), it would take a cracker less than a day to crack a relatively long, but solely numeric, password, or a short password that’s a jumble of characters.
With 1Password and LastPass, a numeric master password can be broken in under a day if it is 12 digits or fewer in length, and 10 or fewer digits for mSecure. Passwords of half that length (6 and 5 characters) can also be broken in under a day even if they use a random mix of letters, numbers, and punctuation.
Plus, 1Password allows the use of a short PIN code instead of or in addition to a longer password. I use the PIN code to lock all access with 1Password for iOS. After it’s entered, I can view items by name but not passwords, which requires the additional entry of the master password. If 1Password’s PIN code is used exclusively to unlock its data in iOS then computation time drops to hours.
The Encryption Background — Each additional digit in a numeric password increases the time it takes to crack by a factor of 10, but each extra character in a mixed password multiplies the complexity by 95 (the number of legitimate printable ASCII characters). These numbers assume using a computer with a high-end graphics card that together cost well under $3,000; more expensive systems can crack faster. (Comparatively, a mixed-text password requires 85 to the Nth power more attempts than a numeric one where N is the number of characters in the password.)
While all three apps use robust security mechanisms to protect the data, the weak link is always the password that, when entered, unlocks the actual, long encryption key used to encrypt the data. mSecure quotes a review of its product in IT Business Net, which states that mSecure “uses 256-bit data encryption, which is basically impenetrable.” That’s essentially true of the actual encrypted data; decryption without the long encryption key might be impossible without years or even centuries of effort by any means currently known. However, if the password protecting that long encryption key is weak, the protected data is vulnerable with only minimal computational effort.
The three apps we know best, 1Password, LastPass, and mSecure, store password data in other places as well, a topic not addressed by Elcomsoft. 1Password stores its password data on a local volume or in a Dropbox folder, although it doesn’t provide a PIN-style interface on the desktop and advises that you pick a good password when you set it up. (Dropbox has seen various security failures in the past, though none recently.) LastPass caches password data on your desktop computer and mobile devices, but maintains the master copy on its servers for syncing, securing the data with your password, which the firm doesn’t retain. mSecure stores data in desktop and mobile data stores, and can sync between the two.
Any of these data stores could potentially be vulnerable, although the same issue applies: the cracker must obtain remote access to the data files, or gain physical access to a system from which data can be copied. Other password keepers with syncing capabilities undoubtedly suffer from similar theoretical vulnerabilities. And again, the concern largely disappears as long as you have a strong password.
Updating your app’s master password to a mix of letters, numbers, and punctuation (or even a few memorable words) of 10 characters or more will provide the greatest assurance of protection, although at the cost of reduced usability. In iOS, think about how you switch back and forth between keyboards to access numbers and punctuation; it makes sense to create a strong password that doesn’t require unnecessary keyboard flipping.
The white paper’s authors note that the lack of physical keyboards on touch-based smartphones and tablets contributes to people choosing shorter passwords. That’s in part why Windows 8 offers gestural passwords overlaid on personal photos.
For protection beyond a longer app password, you should either store your device backups in iCloud or, if you’re storing them locally, encrypt them with a strong password. Also, using iOS’s optional four-digit passcode significantly increases the security of your data. For even more security, you can set a strong passcode for your iOS device instead of the four-digit one; just turn off Simple Password in Settings > General > Passcode Lock, and enter a stronger passcode.
And if all this seems like too much trouble, consider whether it’s worth having access to all your passwords on your iOS device — it might be best simply to delete the password-keeping app and all its data.
The Response from Software Makers — After this story was first published and we contacted the three software makers discussed above, we received a response from LastPass’s Joe Siegrist, who says Elcomsoft is in error about the way in which LastPass currently protects a master password. As of four months ago, LastPass started using a substantially stronger method of obscuring a password, as noted in this blog post. That brings recovery difficulty far beyond 1Password and mSecure, according to Siegrist. Further, LastPass allows an increase in difficulty that makes weaker passwords
harder to break as well. New accounts and password changes made since this security update went into effect get the additional protection. You can change your password in LastPass (even to the same current password) to ensure that the more-secure process is applied if you’re not sure.
AgileBits also responded, pointing us to a new blog entry which illustrates the time to crack passwords of various lengths, and explaining its current approach, which the firm believes is adequate, but already had plans to improve upon. These plans include dropping PIN-only protection in the iOS version, and, alongside an associated switch to requiring iOS 5, adding a technique that slows down attackers. These moves should make shorter and numeric passwords safer as well as improving overall security.
Lastly, we heard from mSevenSoftware, makers of mSecure, which generally agrees with the conclusions of this article about password strength and will work to provide better feedback to users about the strength of chosen passwords. The firm noted that its Dropbox sync option requires a 12- to 30-character password that is stored only locally.
I was concerned to learn from Elcomsoft that the companies mentioned in the white paper were not made aware of these vulnerabilities in advance of the white paper being released. That’s common practice in the security world, to give firms a chance to address the vulnerabilities before the information becomes widely known.
An Elcomsoft spokesperson told me that too many companies were involved and the flaws were too fundamental to pre-disclose. That seems like a somewhat weak excuse (“it was too much work to contact each of them”), but since physical access to the apps’ data stores is necessary and the quick decryption relies on weak numeric passwords, the release of this information doesn’t create a “zero-day” exploit scenario in which crackers can immediately use the information to exploit vulnerable systems in a widespread fashion.
A Positive Outcome — In the long run, we’re glad to see all these firms — Elcomsoft and the makers of the various password-keeping apps — taking the issue of smartphone data security seriously.
TidBITS Watchlist: Notable Software Updates for 19 March 2012
Aperture 3.2.3 — Apple has released Aperture 3.2.3, a small maintenance update to its professional photo organizer and editor. Like the recent update to iPhoto (see “iPhoto ’11 9.2.2,” 8 March 2012), this release enables you to delete individual photos from your iCloud Photo Stream. It also addresses unnamed “minor issues related to performance and stability.” ($79.99 new, free update, 635.54 MB, release notes)
Read/post comments about Aperture 3.2.3.
Sandvox 2.5.3 — Karelia has updated its Sandvox Web site creation software to version 2.5.3 with numerous small improvements and fixes. On the publishing front, the update improves stability during publishing and error handling with SFTP upload failures, fixes an issue with Facebook Comments administration, and fixes an issue that created incorrect HTML paths when exporting a site for the first time. The release also provides several media-related fixes, including audio and video compatibility with Internet Explorer 9 and 10, and ensuring raw Flash files will preview correctly within Sandvox. Other changes include the capability to add custom banners to Quick Look
previews, and the immediate appearance of an object’s border in the Web view when toggled. For a full rundown of the update’s fixes and improvements, be sure to check out the release notes. ($79.99 new from Karelia or the Mac App Store, free update, 28.2 MB)
Read/post comments about Sandvox 2.5.3.
Firefox 11.0 — Mozilla continues its relentlessly hurtling climb to a triple-digit version number with Firefox 11 (a.k.a. the Nigel Tufnel Special Edition), which is light on new features that you’ll actually notice (though developers get a couple of new toys). The new Add-on Sync feature enables you to keep your add-ons copacetic across multiple computers (go to the Sync tab in Preferences to opt into this), and you can now migrate bookmarks, history, and cookies from Google Chrome. Also, users of Growl 1.3 and later will get a welcome return of notifications. On the developer side, the update adds the Style Editor tool
for editing CSS stylesheets in a text editor and the Page Inspector 3D View, a WebGL-based visualization tool that provides a three-dimensional view of the HTML elements on your page (see this Mozilla blog entry for a video demonstration). Firefox 11 also provides support for the outerHTML and CSS text-size-adjust properties, and includes redesigned media controls for HTML5 video. The update is rounded out by a variety of security fixes. (Free, 32 MB, release notes)
Read/post comments about Firefox 11.0.
ExtraBITS for 19 March 2012
We have a lovely collection of ExtraBITS links for you this week, including a hint that we may someday see more lenient electronics usage policies on airplanes, Glenn Fleishman’s thoughts on the Mike Daisey controversy, answers to oodles of iPad questions via a MUG meeting on MacVoicesTV, and a cool demonstration of the scale of the universe.
FAA to Review Electronics Use on Planes — Nick Bilton of the New York Times stumbled on this story by calling to pester the Federal Aviation Administration about its antiquated rules surrounding the use of electronic devices during taxi, takeoff, and landing (and our perennial favorite, sitting on the runway for hours). Instead of giving him the runaround, the FAA unexpectedly changed its tune, saying that it has decided to take a fresh look at the use of personal electronics on planes.
Mike Daisey Revelations Don’t Surprise — This American Life, a public-radio show that tells stories about people, retracted their episode that was largely a reduced form of Mike Daisey’s monologue, “The Agony and the Ecstasy of Steve Jobs.” Daisey didn’t meet the people or see the things he said he did. Glenn Fleishman explains at Macworld how this didn’t surprise him because of his acquaintance with Daisey and his methods.
TidBITS Staffers Answer MUG iOS Questions on MacVoicesTV — Speaking remotely to a packed house at the Apple iCloud sub-group of the Villages Mac Users Group, Joe Kissell and Adam Engst fielded numerous iOS questions from the audience in this MUG meeting recorded by Chuck Joiner for MacVoicesTV. If you’re relatively new to iOS, you’ll pick up a wide variety of usage tips, including a Car Talk-inspired solution involving electrical tape.
Interactive Demonstration of the Scale of the Universe — Apologies in advance to iOS users for pointing to a Flash-only resource, but Cary and Michael Huang’s “The Scale of the Universe” interactive page on NASA’s Astronomy Picture of the Day site is a fascinating update to the classic “Powers of Ten” video created in the 1960s by designers Charles and Ray Eames. We were particularly amused to see Boeing’s Everett, Washington aircraft plant (on the scale of Vatican City) and the virtual Minecraft world (larger than Neptune).