TidBITS#1242/29-Sep-2014
After a botched iOS 8.0.1 update that disabled cellular connectivity and Touch ID for many iPhone users, Apple quickly released iOS 8.0.2 to fix those issues, along with other iOS 8.0 problems. But that wasn’t the end of Apple’s software concerns for the week: a long-standing vulnerability in the ubiquitous Bash shell could leave some systems exposed, as Rich Mogull explains. In a Jeff/Geoff op-ed trifecta, Jeff Carlson explains why Apple kept 16 GB iPhones in the lineup and dropped 32 GB models, Jeff Porten expounds on why he’s not impressed with Apple’s latest offerings, and Geoff Duncan investigates Apple’s new commitment to privacy. Finally, in FunBITS this week, Josh Centers tours Epic Zen Garden, which isn’t so much a game as a visually stunning demonstration of the iPhone 6’s power. Notable software releases this week include OS X Server 3.2.1, Evernote 5.6, SpamSieve 2.9.16, Sandvox 2.9, PopChar X 6.7, and Typinator 6.2.
Apple Releases iOS 8.0.2, Gets It Right This Time
After a botched iOS 8.0.1 update that disabled cellular connectivity and Touch ID for tens of thousands of iPhone users (see “Apple Releases 8.0.1, but Don’t Update Yet!,” 24 September 2014), Apple seems to have gotten it right with iOS 8.0.2, a 73.1 MB download you can obtain in Settings > General > Software Update. We’re seeing no reports of problems from those who have installed iOS 8.0.2.
Though Apple pulled the iOS 8.0.1 update quickly, some unfortunate users got stuck with the update package on their devices, which may confuse the upgrade path. You can delete the bum update in Settings > General > Usage > Manage Storage > iOS 8.0.1 (it will likely be either 1.1 GB and thus near the top of the list, or 73.1 MB, and much further down). iOS 8.0.2 should download automatically after that.
In addition to fixing the aforementioned cellular and Touch ID issues introduced by iOS 8.0.1, iOS 8.0.2 brings back HealthKit, which was pulled just prior to iOS 8’s release due to a bug. Developers can now release apps that take advantage of HealthKit to integrate with the built-in Health app, introduced in iOS 8.
Another frequent annoyance fixed in iOS 8.0.2 is an issue that caused third-party keyboards to be deselected when entering a password. We aren’t yet sure if this fixes the frequently reported “disappearing keyboard” issue, but we can hope.
iOS 8.0.2 also reportedly makes the new Reachability feature in the iPhone 6 more reliable. Reachability is a workaround for the larger screened iPhones, enabling you to move the top of the screen down by double-touching (not pressing) the Home button. In iOS 8.0, it was often difficult to trigger. In my testing of iOS 8.0.2, it doesn’t seem to be any more or less reliable.
Other issues fixed in iOS 8.0.2 include bugs that prevented some apps from accessing Photo Library photos, that could have caused unexpected cellular data usage when receiving text messages, that prevented ringtones from being restored from iCloud backups, and that prevented photo and video uploads in Safari. Plus, iOS 8.0.2 promises to improve support for the Ask to Buy feature of Family Sharing for in-app purchases.
Macs Mostly Safe from Bash Vulnerability, but Be Ready to Patch
No one is ever excited when a new software vulnerability is revealed, but the disclosure this week of a major bug in a common Unix tool set off an earthquake in the security community. Not only is nearly every version of Unix vulnerable, including Linux and OS X, but most of the initial patches are not completely effective at blocking the hole. It’s a near-worst-case scenario where we have a piece of software on nearly every non-Windows server on the Internet — and plenty of personal computers thanks to Apple’s market growth — that is vulnerable to multiple
kinds of remote attacks, all capable of completely taking over the system, with no way to stop it completely.
Despite the severity, a combination of Apple’s design decisions and how we use Macs dramatically reduces your risk, but you still need to be careful and be ready to install Apple’s next security update.
Shellshock — Bash is one of the most fundamental tools on Unix-based systems, including Linux and BSD, a version of which is at the heart of OS X. By default, when you launch Terminal, Bash is the program that provides the command-line interface. It has been around for decades and is by far the most popular interactive shell.
You don’t need to know the gory details (read Troy Hunt’s write-up if you want them), but in short, a researcher discovered a vulnerability in Bash that enables an attacker to do pretty much whatever he wants. It involves manipulating environment variables sent to the shell when it opens a session. This is clearly a problem if someone gains direct or remote access to your computer, but Bash is so deeply embedded into Unix systems that the vulnerability has some unusual effects.
Many programs hook into a Unix system’s default shell to issue command-line instructions because it’s a convenient way to interact with the computer. It isn’t the safest approach, so those commands are often limited to a low-privilege user account or use some other safety mechanism. Unfortunately, that mechanism rarely involves sanitizing commands sent for bad data, something programmers know they should do, but which can be hard to get right.
Thus we find that many installations of the Apache Web server are vulnerable, as is the DHCP software many Unix systems use to obtain their IP addresses. And those two merely scratch the surface. Passing commands through Bash is such a common technique that we don’t know all the ways it could be exploited, or how easy the exploitation might be. In the DHCP example, simply connecting to a hostile network (wired or wireless) could give an attacker control of your computer. And worst of all, this particular exploit is insanely easy to use — all an attacker needs to do is send a bit of the right text to a receptive app.
For example, security researcher (and friend) Rob Graham ran a partial scan of the Internet and determined Shellshock could be used to create a new Internet worm.
Once Bash is fully patched, the vulnerability should be blocked, but it is also possible there are strange variations that haven’t been found yet. Worse, the sheer number of computers that need to be patched is nearly incomprehensible. Bash is even found in odd places like network devices, appliances, industrial control system components (think your power company), and home automation. On the positive side, not everything is exploitable. It takes a combination of the vulnerable version of Bash and some way to send it arbitrary commands that can be executed in an interesting way. But, to bring you back down again, we don’t know what all those combinations are.
We will be dealing with Shellshock for years.
Why Most Macs Are Safe — As I noted before, all recent versions of OS X have Bash installed as the default shell, and are just as vulnerable as any other Unix-based operating system. However, the default configurations of most Macs appear to block the highest-risk methods of exploiting the Shellshock bug. Unless you set up your Mac as a Web server, or enable some other remote software that could link to Bash, you should be safe. That said, anyone running a Mac server should look into recompiling Bash.
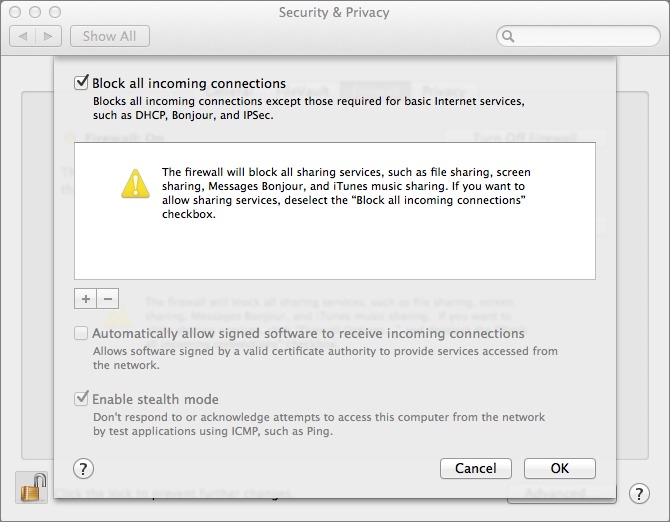
When you’re on your home network, behind NAT (in which your router gets a single IP address from your ISP, and then distributes multiple internal IP addresses to all the devices that connect to it), you’re likely safe. However, when you’re out and about on networks of unknown safety, I recommend turning on OS X’s built-in firewall (System Preferences > Security & Privacy > Firewall > Turn On Firewall). Then click the Firewall Options button and select Block All Incoming Connections. That might be overkill, but it probably won’t affect anything negatively as you use your Mac (it’s how my MacBook Pro is always configured), and it’s easily toggled off and on.
The main vector I was extremely worried about was an attack via DHCP, which could expose your Mac if all you did was connect to a network. To test this concern, I set up my own hostile DHCP server and tried the attack, but to no avail. I couldn’t compromise my Mac, and after asking on Twitter, I found out that Apple uses its own DHCP client, which is safer.
Since we don’t yet understand the full implications of the Bash vulnerability, keep your eyes out for a security update from Apple rather than attempting to patch Bash willy-nilly. (If you run older versions of OS X that no longer receive security updates, you’ll want to recompile your version of Bash, since this vulnerability dates back decades.) But the rest of us should wait for an official update, since the risk to everyday Mac users is low. Apple has already notified the media (including us) that they are working on the problem, and since most of the other fixes are
incomplete, I’m okay waiting a little longer.
Why Apple Kept the 16 GB iPhone in Favor of 32 GB
Perhaps the biggest surprise of the iPhone 6 and iPhone 6 Plus introduction was not the larger screen sizes, but the storage levels among the models. The most expensive configurations now include a roomy 128 GB, but the low-end models ship with only 16 GB. The sole option in the middle is 64 GB.
Unfortunately, 16 GB of free space disappears quickly, as many people have discovered when upgrading to iOS; they need to clear nearly 6 GB off their phones just to download and apply the update. (Connecting the iPhone to iTunes and updating from there bypasses the restriction.)
In the past, Apple has offered evenly doubled capacities. The original iPhone in 2007 was available in 4 GB and 8 GB capacities. And last year’s iPhone 5s and iPhone 5c came in 16 GB, 32 GB, and 64 GB models; they’re still available for purchase, but in only 16 GB and 32 GB sizes for the iPhone 5s and a laughable 8 GB for the iPhone 5c.
So why didn’t Apple stick to its pattern and release the iPhone 6 in 32/64/128 GB tiers?
The answer, of course, is profit — but profit mixed with a little marketing psychology.
It’s All About the Benjamins — Apple has offered 16 GB configurations of the iPhone, iPad, and iPod touch since a revision of the original iPhone in 2008. Even taking into account that the speed of those memory chips has no doubt improved over the years (and would presumably be more expensive than in 2008), Apple’s volume purchasing power — it’s equipping millions of devices — means the company is surely paying very little for each one.
IHS estimates the 16 GB memory in the iPhone 6 costs $15, based on their teardown of the device. That also includes 1 GB of LPDDR3 active memory, but in an article for Re/code, Andrew Rassweiler, the IHS analyst who supervised the teardown, is quoted as estimating that Apple is paying about $0.42 per gigabyte for flash storage. That implies that 16 GB costs Apple $6.72. The IHS figures don’t break out a price for the 64 GB RAM module, but using the same cost-per-gigabyte estimate, 64 GB would cost
Apple $26.88.
Apple claims that the 16 GB model enables the company to maintain a low $199 (carrier subsidized) introductory price for the iPhone 6. Being the least expensive option, the 16 GB no doubt sells well to those who don’t store much media, which means Apple makes a decent profit on each 16 GB iPhone sold.
If Apple were to offer the $199 model at 32 GB, however, the company would make a slightly lower profit at that tier, since that amount of storage would cost $13.44 instead of $6.72. At the scale of iPhone sales — 10 million in the first weekend — the loss of $6.72 per sale would add up fast (if we assume 4 million of those sales were the low-end model, Apple would have left $26.9 million on the table). Apple would still be happy. But there’s opportunity for even greater reward.
Psychology — I suspect the more compelling reason for bypassing the 32 GB tier is related to an Apple briefing I (and other TidBITS editors) had when the company released the iPod nano back in 2005 (see “New iPod nano Replaces iPod mini,” 12 September 2005).
In an unexpected move, Apple discontinued its best-selling iPod mini in favor of the smaller iPod nano, which used solid state memory for storage instead of a tiny hard disk. The iPod nano was available in three configurations: 1 GB for $149, 2 GB for $199, and 4 GB for $249. However, Apple also sold its full-sized fifth-generation iPod, which still had a hard disk inside, alongside the iPod nano in a 30 GB configuration for $299 (and a 60 GB model for $399).
In our briefing with Phil Schiller, Apple’s senior vice president of worldwide marketing, we brought up the question a lot of people were asking: Why offer a 4 GB iPod nano for $249 when a customer could get 30 GB of storage for just $50 more?
Schiller’s eyes lit up as he answered (I’m paraphrasing) that Apple was more than happy to sell the higher-priced product. (Ever the consummate marketer, he then went back on message to praise the benefits of the iPod nano’s smaller size and cutting-edge design.)
I’ve watched this same marketing psychology at work since the iPhone 6 was announced. The general advice given by folks like me who tend to care about electronics is to avoid the 16 GB model because it’s just not enough storage for many people to run iOS 8 and to store apps, music, photos, and videos without constant management.
But I suspect the more influential factor at work is this thought: “For only $100 more, I can get four times as much storage!”
“Only $100 more” is an enormously powerful marketing strategy that Apple has used successfully for years.
It also plays into what’s called “price bracketing,” by which a company offers products at three different price points. In this case, consumers may see (or listen to us pundits say!) that the 16 GB model is too small, the 128 GB model is too big, and therefore the 64 GB model is just right. Goldilocks would be right at home in an Apple Store, and anecdotal data from a local AT&T store suggests that the 128 GB model is the least desirable of the three.
But Apple’s happy no matter what you buy. The 16 GB model costs them less than a 32 GB model would have at the low end. More important, working from the $200.10 cost of materials and manufacturing for the 16 GB model estimated by IHS and the cost-per-gigabyte estimated above, we can see that when you pay $100 more for the 64 GB model, Apple earns roughly $80 more in profit on each sale. And while the 128 GB model may not sell as well, Apple still pockets nearly $75 more than it would if you bought a 64 GB model.
Everybody wins. The customer is happy to get more storage than they likely had before, at what seems like an entirely reasonable cost, and Apple racks up still more profit.
Apple Goes Public on Privacy
Last week Apple published an Open Letter on Privacy, in which CEO Tim Cook emphasized how Apple products are designed with customer privacy as a top priority. The letter and accompanying site detail some of Apple’s privacy-related practices and technologies, as well as the policies that the company mandates and follows with advertisers, partners, and governments. Apple also posted the same content to its various international sites. It’s worth a look.
In part, the site and the letter are a public relations move. Apple has taken a flogging in recent weeks in the wake of attackers accessing several celebrities’ iCloud photos. (Apple claims the attacks are due to compromised passwords and security questions, not inherent security flaws, see “iCloud Flaw Not Source of Celebrity Photo Theft,” 2 September 2014.) As a result, Apple is currently trying to reposition itself as a company worthy of consumers’ trust. Of course, the site also highlights new privacy-related technologies in iOS 8: it’s no coincidence this open letter was published alongside a
massive Apple product launch.
At one level, the site shows how Apple is in the same boat as other technology companies: Apple is constantly storing and processing sensitive data for hundreds of millions of people, and must comply with lawful government orders to hand over information. However, Apple’s privacy pages also highlight how it is different from other technology giants, primarily because Apple earns most of its money selling products, rather than by selling advertisers access to its customers.
Do these differences matter to you? The answer depends on how you (and those you know) use technology and online services.
Apple’s Main Privacy Points — Apple’s new privacy site details how individual Apple technologies (like iCloud, Maps, Siri, FaceTime, Messages, Apple Pay, HealthKit, and more) manage and store personal information. Equally important, Apple also details how users can control how their personal information is stored and shared, and offers some basic advice on safeguarding privacy and avoiding phishing scams. Notably, the site uses accessible English rather than technospeak or legalese, even in the still-dense privacy policy.
A few key points emerge:
- Apple believes users should control how their information is collected and used. One way this manifests in iOS is requiring explicit permission before Apple (or anyone else) can collect data — and users can later revoke those permissions. The stance is a bit risky: pesky prompting is a bad user experience and people quickly learn to click (or tap) through alerts without reading them. (Think: when did you last read the iTunes End User License Agreement?) However, at least users can review permissions granted to iOS apps and revoke them if they like. Not comfortable with a Twitter client tapping into your photos? Deny it access in Settings. Same if you
don’t want Siri knowing your location. - Apple collects only information it believes it needs for a good user experience, anonymizes it when it can, and retains as little of that information as possible. If user data must be stored, where possible Apple encrypts it (say, on iCloud) and does not associate it with Apple IDs (for instance, Siri). If Apple no longer needs the information to provide services, it deletes the data. Apple also repeatedly emphasizes that it does not (and, in many cases, cannot) scan messages, photos, email, or documents on its services for any purpose, including compiling marketing profiles, mapping social or business connections, or selling products.
-
Apple tries to limit ways nefarious (or merely unscrupulous) app makers and third parties can abuse its products and services. For instance, Apple contractually prohibits app makers from collecting iOS device Advertising IDs from users who limit ad tracking. (Further, iOS users can reset their Advertising ID at any time.) While Apple cannot police the practices of every third-party developer, other things are within the company’s control. In iOS 8, Apple is randomizing the internal identifiers used by Wi-Fi hardware. Why? Those identifiers are disclosed every time a device connects to a Wi-Fi network (or even scans for available networks); marketers, hotspot operators, and even governments have used those identifiers to track individuals without consent.
-
If users set a passcode, iOS devices encrypt most user information they store. Apple introduced hardware encryption back in 2009 on the iPhone 3GS: all users had to do was set a passcode. Although that initial effort had severe shortcomings (see “iPhone 3GS Hardware Encryption Easy to Circumvent,” 7 August 2009), Apple has continued to improve on-device data protection. With iOS 8, Apple claims it is “not technically feasible” even for Apple to retrieve much information stored on a device protected with a passcode. This capability shouldn’t be viewed as a privacy panacea — attackers (and governments) can still brute-force
passcodes to access data if they can get their hands on your iOS device. However, it does take Apple out of the business of extracting data from iOS 8 devices if law enforcement goes to the company with a warrant and someone’s iPhone. This device encryption has already raised concerns amongst law enforcement agencies. Inaccessible on-device encryption makes mobile technology more appealing to criminals, and the encryption could also impede time-sensitive investigations like abductions. -
Apple says it does not allow any government agency from any country to access its servers “and never will.” Leaving aside whether agencies like the NSA already have clandestine access, the claim is precarious since the company operates in many countries — including the United States — that can legally compel such access. Apple just opened an iCloud data center in mainland China, subcontracting through state-controlled China Telecom. “Never” is a strong word: it will be interesting to see how Apple responds to any government demands for access to its servers. After all, not even Google will build data centers in
China.
How Apple Compares — Apple seeks to differentiate its products and services from companies like Google and Microsoft on one primary point: selling access to advertisers. Google algorithmically monitors its users’ email, Web searches, contacts, and other online activity to compile information for advertisers. (Yahoo and Microsoft do much the same, although Microsoft no longer scans email.) Google users can tailor their ad preferences for a bit of control over what ads they see, but cannot opt out of Google scanning their data, doing everything possible to determine their location, and compiling those profiles which Google users cannot view, correct, or delete. Many of Google’s products and services may be free to users, but as Tim Cook noted in his open letter, “When an online service is free, you’re not the customer. You’re the product.” Google’s customers are advertisers. During the first half of 2014, 90 percent of Google’s revenue came from advertising.
This isn’t to say Google wants Android or its services to be insecure. Google has always made security a high priority, and has redoubled its efforts in recent years following cyberattacks and mass surveillance revelations. Android has offered user-data encryption on devices as an option since 2011, and Google will be making device encryption a default setting in Android L, due out in a few months.
The distinction is that while Google, Yahoo, Microsoft, Amazon, Facebook, and others want your data to be secure, they don’t want it to be private. They need to know as many specific things about their users as possible to feed their business models. Conversely, Apple claims to access only data it needs for specific features and services, use it only with users’ consent, and (where possible) extends that stance to data that can be collected by third parties. If you don’t have a problem with an app (or a company) tracking your every move, that can be done on an iOS device as easily as an Android phone. But that’s not how Apple’s apps and services behave by default.
To be fair, since Apple designs and markets products for the masses, little that Apple might learn about individual customers could help them sell more products. While there’s no reason to suspect Apple’s public commitment to user privacy is insincere, the company is certainly spinning this basic business model fact into marketing gold.
Of Courts and Canaries — Last year, Apple published its first transparency report on government information requests, which included a so-called “warrant canary:” “Apple has never received an order under Section 215 of the USA Patriot Act.” The untested idea is that while Apple can be barred from disclosing whether it has received an order to disclose information from the mostly secret Foreign Intelligence Surveillance Court (FISC), it cannot be compelled to lie about having not received such an order. If the language were to vanish from an updated version of a document, the reader would be free to infer Apple had received at least such one secret court
order.
Some hay has been made of this warrant canary going missing in Apple’s transparency report covering the first half of 2014; in fact, Apple dropped it in the latter half of 2013 following changes that Google, Microsoft, Facebook, Apple, and other companies worked out with the U.S. government that enable aggregate reporting on both FISA requests and National Security Letters (NSLs). In its place, Apple now says “To date, Apple has not received any orders for bulk data.”
The implication is that while Apple may well have received FISC orders to disclose information, any such orders have not involved the kind of massive handover or continual monitoring implied by things like the NSA’s PRISM program. If this language disappears in the future, readers could infer Apple has been ordered to hand over data en masse.
Does a Privacy Policy Matter? Although Apple’s revamped privacy information site is high-profile, it is basically a statement of intent rather than a set of legal commitments. If any part turns out to be inaccurate or untrue, the worst Apple could face is a civil suit for misrepresentation. (Few U.S. laws apply to privacy: the one most relevant to Apple is the Children’s Online Privacy Protection Act (COPPA).) Apple can change any of its practices at any time, with no warning, and plans to update the site once a year or when there are “significant” changes to its policies. There’s no word on how Apple plans to let people know about changes.
Nonetheless, if any part of this highly public privacy site and policy proves to be untrue, the damage to Apple’s brand and reputation would be immense — Apple is putting its neck on the line.
Another thing is clear: Apple now considers privacy consciousness a feature of its product ecosystem, just like high-quality displays, good cameras, speedy graphics, and elegant design. Apple doesn’t think the Googles, Facebooks, Microsofts, and Amazons of the world can compete.
After September, Still Apple Watching and Waiting
As a veteran Apple observer and enthusiast, I look forward to every Apple keynote presentation with interest, and when possible, an optimistically cleared-off portion of my calendar so I can watch the live stream. I’ve rarely been disappointed, iPod socks aside. But this time around, even after the stream became watchable, I spent most of the time scratching my head, saying (metaphorically), “Huh? I don’t get it.”
Ironically, Apple started the iPhone 6 and Apple Watch keynote with a video celebrating people who “see things differently.” I don’t think my reaction is what they had in mind. Naturally, I don’t expect to be the perfect target for everything that Apple does, so here’s what I expect to get eventually, and what I think will continue to befuddle me.
Venti, Vidi, Vici? — Oddly, one-third of the big news from the event was definitely big and not particularly news, as predictions of supersized iPhones littered the Internet prior to the event. I come not to bury the iPhone 6, but to praise and eulogize the iPhone 5.
“Eulogize? Aren’t you jumping ahead, Porten? The 5s and 5c are still available in the Apple Store.” Yes, that’s true; as is usual with new iPhone releases, the older models have dropped into the “free or cheap with contract” bargain bin. But that’s also the place where old models go to die. With the exception of the iPhone 5 sort of being resurrected as the iPhone 5c, I can’t think of an example when Apple has spiffed up an older iPhone — and the iPhone 5 was the top model prior to the release of the 5s.
Meanwhile, I have extensive pre-release experience with an ersatz 4.7-inch iPhone, thanks to an ongoing dispute with A Titanic & Terrible carrier that holds the lock on my iPhone 5. When I switched to T-Mobile in early 2013, it seemed silly to own two iPhones, so I picked up an HTC One; this phone, coincidentally, has the physical form factor of an iPhone 6, and the pixel resolution of an iPhone 6 Plus. I regularly carry both phones, using the HTC One as a tethered hotspot to give my iPhone an always-on Internet experience. (And thanks to Google Voice, I can pick up a call on either phone.)
My experience using both phones is that the iPhone normally rides in my pants pocket and is my go-to device, while the HTC One stays in my backpack performing hotspot duties. That’s partially because I prefer iOS to Android, but more due to the physical form factor. Although Jeff Carlson says both iPhone 6 models fit in a pants pocket (see “Apple Announces iPhone 6 and iPhone 6 Plus with Larger Screens”, 9 Sep 2014), he also apparently lives in a future cashless world with biometric locks. Where I live, I carry metal keys and coins, which rule out my front pockets for phone toting lest I scratch my gizmos. My HTC
One sticks out of my back pocket, the better for it to be pickpocketed or accidentally slide into someone else’s comfy chair; it fills me with dread even before I do something as risky as sit down. The iPhone 5, meanwhile, gets safely covered with fabric in a back pocket, and even has space to squoosh out of the way when I sit down. [Editor’s Note: TidBITS editor-in-chief Tonya Engst, who has to put up with the impractical pockets in women’s clothing, wasn’t pleased about the size change from the iPhone 4S to the taller iPhone 5s; she’s even less amused about what the iPhone 6s might look like next year when it’s her turn to upgrade. -Adam]
Don’t get me wrong; more screen real estate is nifty, and I’m sure both Apple and third-party developers will put it to good use. Clearly, at least ten million people disagree with me. But I can’t tell the difference between true 1080p video and other HD content on my HTC One 1080p screen, and I doubt that will be different with the iPhone 6 Plus 5.5-inch display. By all means, Apple should be giving larger screens a try; I’m just surprised and miffed (of the “I don’t get it” variety) to see the svelte iPhone 5 apparently deprecated. Unless Apple pulls a first-time reach into the bargain bin next year for
an internal update to the old form factor, will we smaller phone aficionados have to permanently do without an A8 chip, voice over LTE, and higher-quality slo-mo videos, let alone the upgrades of 2015?
Granted, other iPhone 6 features, such as optical stabilization and higher resolutions, probably won’t fit in the iPhone 5 form factor. Nor is Reachability strictly necessary (despite my continually wanting to call it Reacharound), although it does solve one-handed problems I have with both my iPhone and my HTC One.
Watching the Clock for an Apple Watch — Now that I’ve wedged my head firmly into my back pocket, I’ll take it out and look wristward. Keep in mind, I’ve reviewed several competitors in the smartwatch market (see “Four Smartwatches Reviewed: Cookoo, Martian, MetaWatch, i’m Watch”, 31 Jul 2014). Again, I’m clearly in the minority with my lack of “getting it” regarding the Apple Watch; witness the standing ovation Tim Cook received when he announced it, even before any details were shared. He claims that Apple will “redefine what people expect from this category,” and I agree with him — the Apple Watch
will definitely be the bar that any smartwatch over $300 will have to hurdle. (While leaving space in the market for Pebbles, Metawatches, and Martians in the roughly $150 category.)
Apple hits it out of the park on the three primary factors I previously identified: “glanceable” information, two new control surfaces, and functionality as a plain old watch. But what surprises me about the Apple Watch is that it’s so damn fiddly. Take the process for launching a new app: Press to go to the home screen. Rotate the “digital crown” to zoom out to see your app icons. Slide around to the region where your app lives, then rotate the crown to zoom in, then slide around a little more until your app is front and center, where hopefully you’ll tap in the right location and not launch the app next door. I think this is probably the best possible way to present a hundred app icons on a tiny screen; I also think that
this is going to require some hand-eye coordination to get it right the first time.
Likewise, what happens when those hundred apps pummel your Apple Watch with notifications? I wrote that I wanted to see “an app store of [watch] widgets to give me better ideas” of what could be done with a smartwatch; it only now occurs to me that the Apple Watch may be too much of a good thing. The announcement of WatchKit ensures that there will be hundreds to thousands of apps available for the Apple Watch soon after release. Trust my experience with other watches: you’re going to want to limit incoming notifications to those that are “wrist worthy,” which means tons of fiddling with either Apple Watch or iPhone host applications to narrow down the number of haptic taps
on your wrist for attention. (Although if Apple provides a way to modify the taps you receive based on the type of notification, I’ll call that a sheer genius interface.)
Finally, I’m interested to know what limitations of the Apple Watch appear when it’s not being used within range of a required iPhone. There are situations when you want a watch to replace, not augment, an iPhone, so what will an Apple Watch be able to do all by its lonesome? Likewise, see my earlier comments about bigger iPhones; although I’m glad that the iPhone 5 is supported by the Apple Watch, I wonder what iPhone 6 users are expected to do when out for a run without a requisitely sized pocket in their spandex. (Or as Geoff Duncan asks, will overalls make a hipster comeback?)
Quis Custodiet Ipsos Apple Watch? — Pardon my Latin again, but I’d like to segue here to what I think the Apple Watch might have gotten right, or at least, what I’ll be looking for in launch day reviews.
I’m heartened that Apple agreed with me on having built-in Siri, and I’m hoping that this means less fiddling: “Hey, Siri, launch Activity” (so I don’t have to search for it on my home screen) is much easier and faster. The question here is whether key Siri functionality will be fast enough to improve on a touch user interface; I assume some of what Siri does is built into the Apple Watch, while the rest of it will be shipped off to the required nearby iPhone. In my review of the Martian, I was less than excited about its Siri functionality (due to handoff delays), and I was generally down on having a two-way wrist microphone in my smartwatch; here I’ll want the watch-Siri experience to be seamless — by which I mean,
“damned near instantaneous” — in order to make it something that’s better than reaching for an iPhone and possibly improves on the fiddliness required by tapping and rotating.
I’m fascinated by Apple’s unstated promise about the Apple Watch: that it’s literally going to make you into a better person. At least, that to me is the subtext of the entire health-and-fitness genre of included Apple Watch apps, let alone what will be available from third parties. When a smartwatch is keeping track of how often you stand up and how much time you spend at your desk, it effectively gamifies every minute of your life. Even we Philadelphians (diet: hoagies and cheesesteaks) who don’t exercise regularly will be provided with manageable and simple reminders to make minor changes that add up to a healthier lifestyle. Fitness apps have previously targeted the fitness-as-lifestyle folks; these are apps for the rest of
us. I wonder if we’re ready for them.
I’ll also be watching — no pun intended — to see whether the Apple Watch literally changes the social norms by which we all interact. Apple decided to make the Apple Watch’s notifications invisible to other people — not the case for many other smartwatches, where the vibrator may create a public buzzing noise — which raises a question I asked in 2013 (see “Pondering the Social Future of Wearable Computing”, 29 May 2013):
In the parlance of anthropologists, the culture surrounding mobile phones is “thick”: a set of rules and norms that vary depending upon who you are, whom you’re with, where you are, and dozens of other factors that are all instantaneously processed and coded…. The amazing thing is that we’ve developed such a thick set of rules for handheld Internet computers after only five years.
Your dinner companion glances at his watch — to check the time? Check a Facebook update? Read a text message? … You [don’t] know if your companion is choosing to do this or responding to an alert. Does that make a difference? Does the content of the alert make a difference?
With the Apple Watch, Apple is betting that we’ll learn a new set of rules surrounding the meaning of “glancing at my watch,” which in these pre-Apple Watch days is generally taken to mean “I’m bored” or “I’m waiting for something more important than, uh, you.” In this case, Apple may have outsmarted itself; the feature that turns on the screen when you lift and turn your wrist also makes it more difficult to check your watch covertly. The question is how this will be interpreted by everyone else — and that’s likely to change over time depending on how quickly all smartwatches are adopted by the general public.
This is the primary meaning I’m assigning to my deprecating assessment of the Apple Watch as “too fiddly,” because I think it will be socially acceptable to glance at your watch occasionally, and much less so to fiddle with it. The Apple Watch demos beautifully, but the question of how acceptable it’s going to be will come down to how often it requires no interaction aside from a glance. My prediction: better than any smartwatch before it, but poorly enough that we’re going to have to come up with new rules for what’s socially “wrist-acceptable.”
Apple Paying the Piper — This brings us to the third part of Apple’s announcement which left me confused: Apple Pay. To be clearer, Rich Mogull and Adam Engst already discussed the sordid cesspit that is our current credit card system (see “Apple Pay Aims to Disrupt Payment Industry”, 09 Sep 2014), which basically functions on the principle that the vast majority of people who see your credit card are decent human beings, the vast majority of the time. It is instantly obvious why Apple Pay should succeed, on its security provisions alone.
The issue comes with using Apple Pay, especially in its early adoption. Cook cited 220,000 points-of-sale, which sounds impressive until you think of the 30 million businesses that exist in the United States. You can leave your wallet at home and still buy a bottled water while out for a run, but only if you stop at a Walgreens or McDonald’s. For the time being, Apple Pay faces the same problem that bedevils other payment methods like PayPal and LevelUp: needing to remember the limited list of businesses where the thing will work.
Let’s be generous and assume that by mid-2015, Apple Pay is accepted at some number of businesses that we can call non-anomalous. You’re at a point-of-sale, and you can pay with either Apple Pay or a credit card. If you’re wearing an Apple Watch, it’s pretty much a done deal — there’s nothing more convenient than waving your hand like you’re Mandrake the Magician.
But if you’re still in the Watchless community, Apple’s supposition is that it’s easier to take an iPhone out of your pocket than it is to reach for a credit card. Unfortunately:
- That iPhone 6 is closer to the size of a checkbook.
- If I drop my credit card, it won’t shatter.
A credit card is valuable, but cheap to replace. Apple Pay flips this equation exactly: an iPhone 6 and an Apple Watch are worthless for accessing your bank accounts, but expensive to replace. Cook suggested that you could use your iPhone 6 to pay at a drive-through; I’d be leery of that for the same reason that I’m not going to repeat the demo and take optically stabilized movies with an iPhone 6 Plus from a moving bicycle.
It’s not that tapping an iPhone to a payment platform is a particularly dangerous thing to do. It’s that it’s a slightly dangerous thing to do one-handed when you’re distracted by something else, and that describes the experience of shopping. Multiply that by the two hundred times a year you buy something, or by the millions of times Apple Pay will be used: we’re going to hear, on day three of Apple Pay or sooner, about some poor schmo who broke his iPhone and Apple wouldn’t replace it. That means Apple Pay isn’t a free service any longer, because I wouldn’t use it without signing up first for AppleCare+.
Credit cards as we know them deserve to die. And the fact is, they’re going to, as the United States finally catches up on the chip-and-PIN technology that makes the system more secure in Europe. As I understand it (and thanks to Rich and Adam again for that), Apple Pay is better than chip-and-PIN for a half-dozen different reasons; it’s just that with Apple Pay, a new credit card will cost you $200 or more if you break the one you’re using.
What to Watch For — That sums up why I’m unlikely to be an Apple upgrader in 2015. But I’ll be looking with anticipation (and some trepidation) at the September 2015 iPhone rollout to see if iPhone 5-sized phones are included in the upgrade, or if they’re doomed to be the next iPod classic: a long lifetime with no love. (My prediction is that this is exactly what will happen. What would you call one? The iPhone 6s Minus? The iPhone 6s mini? The iPhone 6s nano?)
I also believe the Apple Watch will be a success, selling primarily to the kind of people who signed up for a Pebble when it was a Kickstarter project — particularly those who are that kind of person but who didn’t actually get a Pebble. I’m off this upgrade path primarily because I’m off the iPhone upgrade path — if there were a compelling iPhone 6 option that didn’t have the size drawbacks of my HTC One, I’d consider it. And while the Apple Watch is compatible with the iPhone 5, I’ll be looking to see if it works with my (admittedly bizarre) situation of having my iPhone off-contract but online. Even if it is — at that point, I’m making a decision to live in an Apple ecosystem, whereas I’ve spent the last two
years switching between iPhone and Android. (This decision point is also created by the purchase of an Android Wear watch; however, I expect the Apple Watch to be much more successful in terms of mindshare and sales than any Wear watch.)
As for Apple Pay, I think it will work great in the few places it’s offered, but I doubt we’re going to see the takeover of the American financial system. Where Apple Pay could make serious inroads is in two categories: Apple Watch owners, because it’s so damned easy, and online payment, about which Apple Pay details remain slim.
So for those of you keeping score: I seriously doubt any of these rollouts will be a failure. I just think that, if you’re not already using your iPhone 6 and squirrelling money away for an Apple Watch, more caution is warranted for 2015 than is usually the case with Apple rollouts. And that having been said, I’ll certainly come back to TidBITS to eat my claim chowder if I end up sporting any of these devices next year.
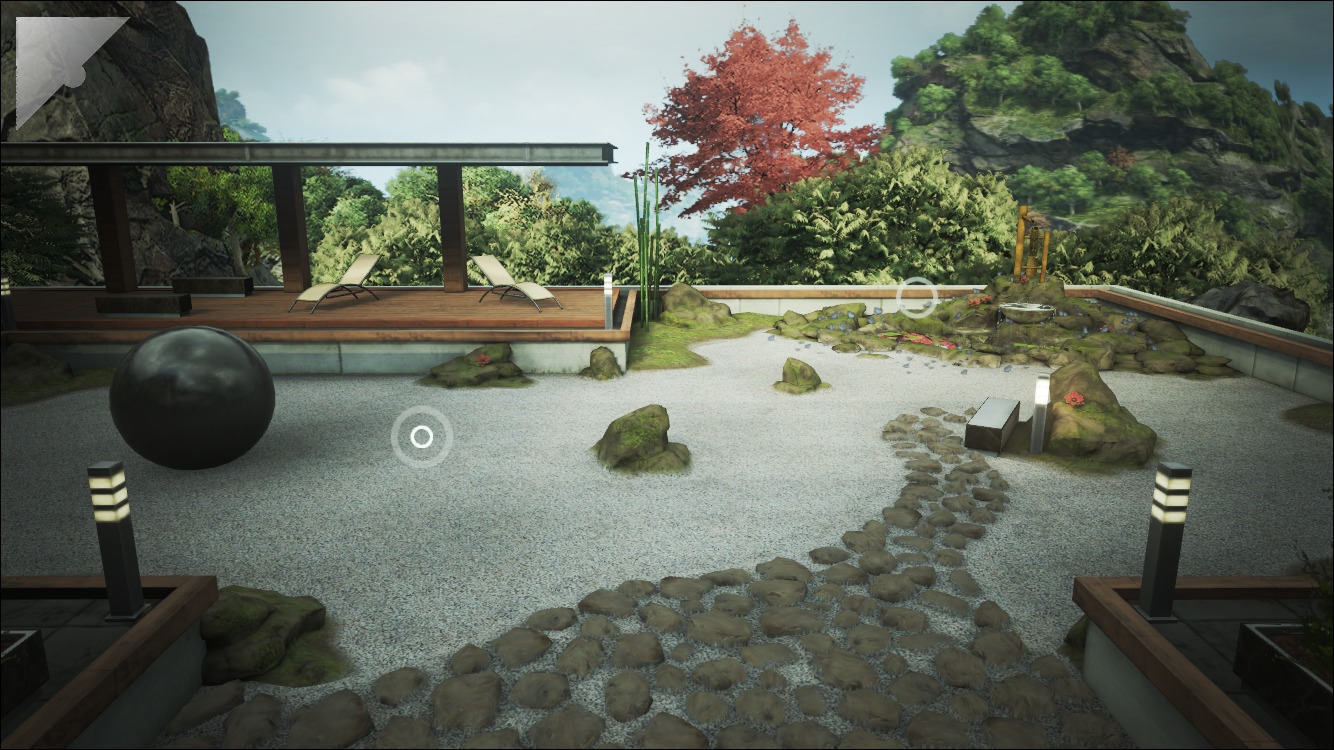
FunBITS: Epic Zen Garden Shows off Your New iPhone
If you watched Apple’s 2014 WWDC keynote, you might recall Tim Sweeney of Epic Games being brought on stage to show off his company’s Zen Garden demo, which demonstrated the power of the new Metal API in iOS 8. His demonstration displayed amazing advances in shaders, artificial intelligence, and particle effects.
Now that tech demo, Epic Zen Garden, is available for free in the App Store. It requires iOS 8.0 or later on an iPhone 5s, iPad Air, or iPad mini with Retina display or later, and is a 232 MB download.
In terms of gameplay, Epic Zen Garden doesn’t offer much, but if you just purchased a new iPhone 6 or iPhone 6 Plus, it’s probably the flashiest way you can show off your new toy to friends.
Epic Zen Garden begins on the outside of a house, with three tappable targets, denoted by white circles. Each target opens a different activity (all screenshots were taken on an iPhone 6):
- Chair: Tapping the chair zooms you out to view the floating island that your house was built on. There’s nothing you can do here other than watch birds fly by, but it’s pretty! Tap the white arrow in the upper left to return.
-
Tree: Tapping the tree takes you to what appears to be a dead tree. But hold your finger over its withered branches, and flowers will bloom. Touch the flowers to make the petals fall, which is a neat demo of Metal’s particle effects. Tap the side arrows to rotate around the tree, the circle in the upper right to reset the tree, or the arrow in the upper left to return to the main view.
-
Pool: Tapping the pool zooms in on the water, showing a large school of koi. Dragging your finger across the water will cause ripple effects that the koi will follow. From the pool, you can also see three more locations in the distance:
-
Courtyard: The middle option takes you into a courtyard, where you can visit the Zen garden or the fountain.
-
Zen Garden: Tapping the sand brings you into the Zen garden. Drag your finger along the sand to rake it.
-
Fountain: Finally, there’s the fountain. Tap the bamboo to release a swarm of butterflies. Touch the screen to have the butterflies gather at that point.
That’s it. Despite the name, there’s nothing particularly epic here, other than the lush visuals and the promise of things to come. You may remember the open-world Epic Citadel, which demonstrated the prowess of the iPhone 4 and which later evolved into the more constrained, but incredibly popular Infinity Blade (for my review of the
third installment, see “FunBITS: Show Off Your New iPad with Infinity Blade III,” 8 November 2013).
Much as the “gameplay” of Epic Citadel was very different than its final commercial release, I don’t expect that whatever the fleshed-out Epic Zen Garden becomes will bear much resemblance to the “gameplay” of its tech demo. But it will be exciting to see what Epic does with the newfound power of Apple’s Metal API.
TidBITS Watchlist: Notable Software Updates for 29 September 2014
OS X Server 3.2.1 — Apple has released OS X Server 3.2.1, which adds Profile Manager support for several new features in iOS 8 and OS X Yosemite. You can now use Mobile Device Management (MDM) to install PDF, EPUB, and iBooks Author files on iOS, install OS X enterprise apps, and rename Mac and iOS devices. In iOS 8, OS X Server 3.2.1 can also prevent managed apps from storing data in iCloud as well as restrict cellular data usage, Handoff, syncing, managed books and Spotlight search. The update can also configure managed Web domains on iOS 8 and mail domains on iOS 8 and OS X
Yosemite. ($19.99 new, free update, 185 MB, 10.9.5+)
TidBITS members can learn more about OS X Server via streamed “chapticles” of Charles Edge’s “Take Control of OS X Server,” due for full ebook publication soon. The first two chapters — “Take Control of OS X Server, Chapter 1: Introducing OS X Server” and “Take Control of OS X Server, Chapter 2: Choosing Server Hardware” — can be read by everyone, and TidBITS members enjoy full access to the subsequent chapticles. The TidBITS membership program also includes a 30 percent discount on all Take Control books and discounts on leading Mac apps, a full-text RSS feed, and a
banner-free version of the TidBITS Web site.
Read/post comments about OS X Server 3.2.1.
Evernote 5.6 — While Evernote 5.6 might not look that different at first glance, the information management app overhauls its engine to improve overall speed, synchronization, and editing. The release offers more options for creating and editing notes, enables you to resize images within a note (without changing the size of the original image), redesigns checkboxes within notes, adds a new table editor, and improves sync times for Evernote Business users and those with a large number of shared notebooks. Evernote 5.6 also improves searching notes with search results displayed in order of relevance, and adds support for using
Spotlight to search within your Evernote account. Note that Evernote is still stuck at version 5.5.1 in the Mac App Store as of this writing. (Free from Evernote or the Mac App Store, 55.9 MB, release notes, 10.6.6+)
Read/post comments about Evernote 5.6.
SpamSieve 2.9.16 — Michael Tsai of C-Command Software has released SpamSieve 2.9.16 with support for OS X 10.9.5 Mavericks and improvements to SpamSieve’s filtering accuracy. The release also updates Outlook and Entourage scripts for compatibility with 10.10 Yosemite, as well as several Apple Mail scripts with a workaround for a bug in Yosemite. Additionally, SpamSieve 2.9.16 offers a new method of hiding SpamSieve’s Dock icon (that doesn’t rely on editing an Info.plist file), improves repairing folder ownership and permissions, works around a hang at launch if MailTags was installed, and removes spurious warnings about
extra Apple Mail preferences files. ($30 new with a 20 percent discount for TidBITS members, free update, 13.3 MB, release notes, 10.5+)
Read/post comments about SpamSieve 2.9.16.
Sandvox 2.9 — Karelia has released Sandvox 2.9 with improved publishing performance, support for SSL security for FTP and WebDAV, and a new Vimeo object that makes it easy to display videos hosted on Vimeo.com. The Web site authoring tool also improves reporting of errors during publishing, enables a currently uploading file to finish if publishing is stopped, reuses SFTP and FTP connections when possible for better performance, allows published video and MP3 audio to play natively on Internet Explorer 9 (rather than having to rely on Flash), improves favicon compatibility with Google Chrome, disables smart-quote substitution
in the Raw HTML editing and Code Injection windows, and fixes the Dock progress indicator for publishing. ($79.99 new, free update from Karelia or the Mac App Store, 38 MB, release notes, 10.6.6+)
Read/post comments about Sandvox 2.9.
PopChar X 6.7 — Ergonis Software has released PopChar X 6.7 with several speed improvements to the character discovery utility, including faster refresh for recently used fonts, quicker refresh of the font table when a search for characters is active, and zippier computation of available characters and layouts. The update also fixes an issue that resulted in invisible characters on Macs with PowerPC processors, provides a workaround for a problem with automatic selection of the Find field on OS X 10.10 Yosemite, and improves handling of low-level issues in library components to avoid crashes in some system
configurations. (€29.99 new with a 25 percent discount for TidBITS members, free update, 3.8 MB, release notes, 10.5.8+)
Read/post comments about PopChar X 6.7.
Typinator 6.2 — Building on the utility’s capability to create expansions based on regular expressions, Ergonis has released Typinator 6.2 with several new built-in functions — Count, List, Any, and Index — that enable you to extract and analyze pieces of text in longer text fragments. The text expansion tool also displays input fields in a scrollable list if there are too many to fit on the screen, improves handling of spelling corrections, suppresses expansions in the input field of LaunchBar, correctly disables itself when Microsoft Remote Desktop is active, and improves handling of low-level issues in
library components to avoid crashes in some system configurations. (€24.99 new with a 25 percent discount for TidBITS members, 7.3 MB, release notes, 10.5.8+)
Read/post comments about Typinator 6.2.
ExtraBITS for 29 September 2014
In this week’s collection of ExtraBITS links, we look at the viability of Mac OS 9 in 2014, why old security vulnerabilities just won’t die, and Apple’s iPhone stress-testing process.
Using Mac OS 9 in 2014 — Andrew Cunningham of Ars Technica was challenged by his coworkers to use Mac OS 9 for a few days. Armed with a 2002 PowerBook G4, Cunningham set out to do his job with the now 12-year-old Mac OS 9.2.2… and found that he could get nothing done. However, he discovered that it was a nice setup for classic games that no longer run on modern Apple devices.
Why Security Vulnerabilities Aren’t Going Away — Old security vulnerabilities never seem to go away. Our own Glenn Fleishman, writing for Boing Boing, explores the reasons why, which boil down to companies not deactivating old software and there being no money in maintaining it.
The Place iPhones Go to Die — In response to claims that the iPhone 6 bends in pants pockets, Apple gave The Verge a rare look at the facility where it stress tests new iPhone models. Apple tested 30,000 iPhones before release, including a special test that simulates pressure inside a pants pocket. Apple claims that out of over 10 million iPhone 6 and iPhone 6 Plus models sold so far, there have only been nine complaints about bent phones.