#1396: Emergency macOS updates, iOS 11.2, net neutrality, iOS backups, Amazon Prime Video
They say no news is good news, and we’re sorry to say that this week’s issue of TidBITS is chock full of the bad kind. Apple had to push out two emergency updates to macOS to close a massive security vulnerability, and the company released iOS 11.2 ahead of schedule to eliminate an infinite reboot bug. While Apple had an awful week, the entire Internet may have had a worse one, as Ajit Pai’s FCC is set to eliminate Obama-era net neutrality protections. On top of everything else, Rich Mogull explains how iOS 11 makes your encrypted backups via iTunes less secure, albeit with the silver lining of making it harder to lock yourself out of them. There is one bit of unalloyed good news this week: Amazon says its Prime Video app for the Apple TV will ship this month. Notable software releases this week include Keyboard Maestro 8.0.4, BBEdit 12.0.2, BusyCal 3.2.5 and BusyContacts 1.2.6, LaunchBar 6.9.3, and Default Folder X 5.1.9.
Apple Pushes Updates to Block the Root Vulnerability Bug
[Editor’s Note: This article is a significant update to “Update Immediately to Block the Root Vulnerability Bug” (29 November 2017), since so much information changed since we first published that piece. This article supplants the previous one. -Adam]
If this is the first you’re hearing about the root vulnerability bug that was discovered and patched last week, you can read “High Sierra Bug Provides Full Root Access” (28 November 2017) for details about how it allowed anyone to gain admin access to your Mac without a password. As I predicted in that article, Apple quickly released Security Update 2017-001 to fix the bug. I have installed the update and confirmed that it works as advertised.
On 29 November 2017, Apple initially made Security Update 2017-001 available as a regular download via Software Update, but later that day, the company started using the automatic update mechanism built into macOS to push the update to all Macs running High Sierra, both versions 10.13.0 and 10.13.1.
No restart is necessary, so Apple can install the update without requiring interaction from the user. We believe that a Mac must be awake for the automatic update to install since we’ve seen it appear on a MacBook Pro that was awake, but not on a MacBook Air that was sleeping all day (lazybones!).
If your Mac has been asleep since Apple released Security Update 2017-001, you’ll see it in the Updates tab in the App Store app, and you can still install it manually. We usually recommend caution when it comes to installing updates, but this vulnerability is so severe that the fix is more important than any trouble it could conceivably cause.
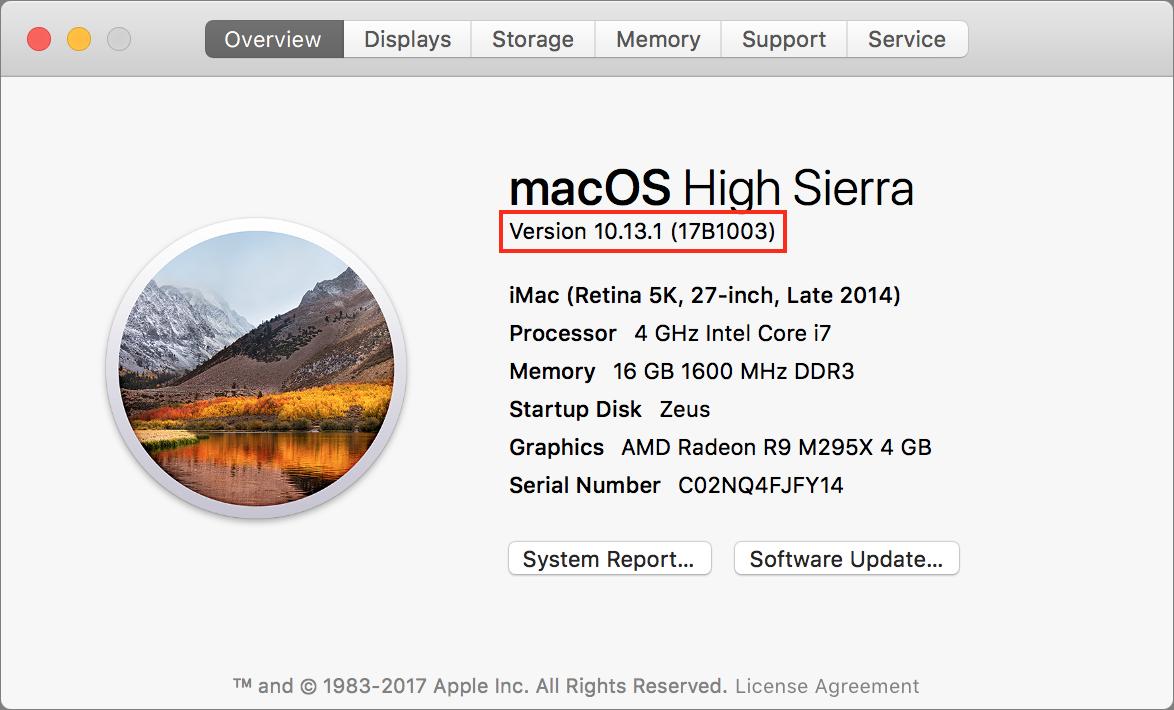
In fact, it did cause problems. Apple released two versions of Security Update 2017-001 last week. The first updated High Sierra to build 17B1002, and the second to build 17B1003. (To verify that number, choose > About This Mac and click the Version 10.13.1 line.) The second version was necessary because the first broke authentication for file sharing. We didn’t test file sharing after installing the first version of the update because the original bug didn’t affect file sharing.
If you installed Security Update 2017-001, and your build number is 17B1002, Software Update should offer you the update again; install it manually to fix the file sharing bug and move to build 17B1003. On my iMac with build 17B1002, no automatic update took place before I updated again manually, but other users received the automatic update after installing the first update manually.
For those who need a standalone installer for Security Update 2017-001, Apple has made downloads available for both 10.13.0 and 10.13.1.
If you have a legitimate use for the root user account on your Mac, you’ll need to re-enable it and change its password in Directory Utility after installing the update. Hardly anyone should have to do this.
Why all this fuss? Although the Mac community identified the primary attack vectors on 28 November 2017 when the vulnerability was first publicized, it’s possible that there are others that are not blocked by changing the root password or disabling remote access. We have to assume that black hat hackers are probing every possible area where this bug could provide access. That’s why it’s entirely reasonable for Apple to push the security update to all systems.
In an early statement to John Gruber of Daring Fireball, Apple said:
Security is a top priority for every Apple product, and regrettably we stumbled with this release of macOS.
When our security engineers became aware of the issue Tuesday afternoon, we immediately began working on an update that closes the security hole. This morning, as of 8:00 a.m., the update is available for download, and starting later today it will be automatically installed on all systems running the latest version (10.13.1) of macOS High Sierra.
We greatly regret this error and we apologize to all Mac users, both for releasing with this vulnerability and for the concern it has caused. Our customers deserve better. We are auditing our development processes to help prevent this from happening again.
Apple deserves credit for releasing this security update in less than 24 hours after the bug was publicized on Twitter. That quick reaction time is reassuring, much as I’m sure many developers, testers, and deployment teams at Apple had a truly awful day.
But the fact that Apple could introduce a security hole the size of a truck into High Sierra is appalling. Ensuring that unauthorized users can’t act as the root user in a Unix system is basic security, because anyone who can become root can do anything they want. That the vulnerability escaped notice in Apple’s security testing is almost worse than the bug itself, and the initial release of Security Update 2017-001 breaking file sharing authentication is also distressing.
And yes, if you’ve been waiting to upgrade to High Sierra, pat yourself on the back. 10.12 Sierra and earlier versions of OS X don’t suffer from this bug.
Surprise! Apple Releases iOS 11.2 to Combat Reset Loop Bug
As I write this, it is Saturday morning, 2 December 2017. The sun has yet to rise. I have yet to put on pants. Nonetheless, I’m staring at the release notes for iOS 11.2, a significant update of iOS that Apple released overnight. Despite the company’s penchant for opening pre-orders at the absurd hour of midnight Pacific time, Apple usually releases software updates, at least for those of us in the United States, on a weekday, while it’s light out.
What gives?
Just before I fell asleep last night, news broke of a terrible bug affecting Australian users. As the clock struck midnight and the date changed to 2 December 2017 down under, Australian iPhones started rebooting. And rebooting. Every few seconds or minutes, affected iPhones rebooted again.
Reddit users in /r/iphone caught on to the problem and quickly began suggesting solutions. The obvious solution, rolling back the clock, broke so many apps that it was not advised. The best alternative was to turn off third-party notifications. But the real fix is to install iOS 11.2.
You can download the iOS 11.2 update either in Settings > General > Software Update or via iTunes — it’s about 430 MB on an iPhone X. We usually advise a waiting period before installing such large updates, but given Apple’s software quality problems this week, the better part of valor would seem to be to install it right away. We hope the iOS 11 quality assurance team did a better job on the 11.2 release than the High Sierra team did with the root vulnerability bug update.
As for you, gentle iOS user, if your device is stuck in a terrible reboot loop, your best bet, per iMore’s Rene Ritchie, is to navigate to Settings > Notifications and disable all third-party notifications. That should stop the reboot loop.
iOS 11.2 also fixes another glaring glitch that caused error-inducing lag in the built-in Calculator app (see “iOS 11 Calculator Lags Cause Errors,” 9 November 2017). Unofficially, it reportedly fixes the lesser known bug that autocorrected the word “it” into the abbreviation “I.T.”
Besides preventing your iPhone from entering an infinite loop of reboot doom or turning your 24 into a 6, iOS 11.2 finally brings us Apple Pay Cash, the now-official name for Apple’s person-to-person Apple Pay feature. Well, it sort of does. It wasn’t available at release, and as of 4 December 2017, there is (sometimes) a switch to enable it in Settings > Wallet & Apple Pay, though it doesn’t seem to be functional yet.
Apple Pay Cash would undoubtedly be the top story if not for this reboot bug. Our condolences to the Apple Pay Cash team for having their feature release overshadowed by a bug fix. We plan to have in-depth coverage once Apple enables it.
iOS 11.2 also adds support for faster Qi “wireless” charging for the iPhone 8, 8 Plus, and X, if you have a compatible charger. These devices push out 7.5 watts of power, as opposed to the typical 5 watts.
The update also adds three new live wallpapers for the iPhone X. You can find them in Settings > Wallpaper > Choose a New Wallpaper.
In the Podcasts app, you can now swipe up while playing an episode to see a sleep timer, episode description, chapters, episode notes, and Up Next.
On the accessibility front, iOS 11.2 adds support for real-time-text phone calls for the deaf and hard of hearing.
Closing out the list of new features, HealthKit now supports downhill snow sports.
Also, iOS 11.2 improves video camera stabilization. Right now, it’s great to see Apple improving any sort of stability. Sorry, couldn’t resist.
The rest of the changes are bug fixes for less severe problems. The iOS 11.2 update:
- Fixes an issue that could cause Mail to appear to be checking for new messages even when a download is complete
- Fixes an issue that could cause cleared Mail notifications from Exchange accounts to reappear
- Improves Calendar stability (look, more stability!)
- Resolves an issue where Settings could open to a blank screen
- Fixes an issue that could prevent swiping to Today View or Camera from the Lock screen
- Addresses an issue that could prevent Music controls from displaying on the Lock screen
- Fixes an issue that could cause app icons to be arranged incorrectly on the Home screen
- Addresses an issue that could prevent users from deleting recent photos when iCloud storage is exceeded
- Addresses an issue where Find My iPhone sometimes wouldn’t display a map
- Fixes an issue in Messages where the keyboard could overlap the most recent message
- Addresses an issue where the keyboard could respond slowly
- Improves VoiceOver stability in Messages, Settings, App Store, and Music (stability is good!)
- Resolves an issue that prevented VoiceOver from announcing incoming Notifications
Apple hasn’t yet published a list of security updates for iOS 11.2, although they should appear soon on the Apple Security Updates page. That team must have had the weekend off.
Kudos to Apple for moving up iOS 11.2 release schedule to help affected users, but this is yet another nasty bug that Apple’s testing should have caught and fixed sooner. It doesn’t help that it reared its ugly head the same week as a security hole the size of Texas was found in macOS 10.13 High Sierra, and the first update to fix that problem broke file sharing (see “Apple Pushes Updates to Block the Root Vulnerability Bug,” 30 November 2017). And it hasn’t even been a month since the iOS bug that autocorrected the letter “i” to the letter “A” followed by a question mark in a box (see “Me, Myself, and A⍰,” 7 November
2017).
Something is clearly rotten in the state of Denmark, by which I mean Apple’s quality assurance department. Many long-time TidBITS readers have been complaining for years about Apple’s declining software quality. Major missteps like these give Apple a black eye and, when they affect tens or even hundreds of millions of users, cause a significant waste of the world’s time.
Amazon Still Promising Prime Video App for Apple TV in 2017
The Apple TV often feels like a forgotten middle child. Apple’s most exciting announcement for it this year wasn’t a new feature, but an app: Amazon Prime Video, which would let customers view movies and shows purchased from Amazon and stream titles — including Amazon’s original programming — included for free with Amazon Prime subscriptions.
Amazon’s video app is nearly as widespread as Netflix. It’s available on my Sony TV, my Amazon Fire Stick, my PlayStation 4, and even my Nintendo Wii U. Outside of my toaster, it seems that the only device in my house that can’t stream video from Amazon is my Apple TV. (And inside a toaster, it’s awfully hot.)
At this year’s Worldwide Developers Conference, Apple and Amazon finally announced that we would be able to watch Amazon video natively on the Apple TV by the end of the year (see “Apple TV to Get Amazon Prime Video and More Later in 2017,” 5 June 2017). TidBITS readers are champing at the bit for this app! Every time I write anything about the Apple TV, readers ask where the Amazon Prime Video app is.
But it’s December, and Amazon Prime Video for the Apple TV remains vaporware. Is it still due in 2017? Surprisingly, yes. Amazon public relations told me, “Thanks for checking in. Yes, you can expect the launch this year.”
So there you have it — at least Amazon PR is on the record as promising the Amazon Prime Video app before 2018. Keep your eyes peeled for it becoming available any day now for your fourth-generation Apple TV or Apple TV 4K.
That said, the cynic in me could imagine Amazon shipping the app late in the month to avoid cutting into holiday sales of Amazon Fire TV devices.
FCC to End Net Neutrality
Earlier this year we noted that the U.S. Federal Communications Commission (FCC), under Trump-appointed chairman Ajit Pai, was preparing to roll back Obama-era regulations that classified Internet service providers as common carriers and mandated “net neutrality.” (See “FCC and Congress Work to Roll Back Net Neutrality,” 05 May 2017.) Well, now is the time the hammer meets the nail: the FCC is expected to vote on the proposal to undo net neutrality on 14 December 2017.
The full 210-page proposal (PDF) is available to the public, but it boils down to:
- The FCC will reclassify Internet service providers as “information services” rather than more-regulated common carriers like utilities and telephone companies.
-
Mobile Internet service will be reclassified as a “private” service subject to little regulation rather than “commercial” service, on the basis of some hairsplitting about connecting to the public switched telephone network.
-
In the spirit of transparency, network operators will have to publish (or disclose to the FCC) some information about their network operations and commercial offerings that is “sufficient to enable consumers to make informed choices.” This would include information about blocking, throttling, or prioritizing of some services or apps at the expense of others. However, providers would essentially be able to take any action they like under the aegis of “network management” without disclosure.
-
States and localities will be prevented from drawing up their own broadband consumer protections.
Under this new framework, the FCC is essentially forfeiting its authority to regulate the broadband Internet market. This means responsibility for keeping network operators on the up-and-up falls to the Federal Trade Commission. The FTC has never had anything to do with net neutrality and cannot impose regulations on network operators, but it can investigate anti-competitive behavior.
Commissioner Pai has consistently characterized net neutrality as a solution looking for a problem. Generally, Pai sees net neutrality regulations as an unneeded burden because the Internet did not devolve into a dystopia of slow lanes, fast lanes, and paid prioritization before 2015. Pai also feels the FCC is unnecessary to keep network providers in line: in the handful of instances where anticompetitive behavior did crop up, most were handled by the industry without the FCC’s intervention. Further, Pai claims that eliminating net neutrality regulations — or, rather, “restoring Internet freedom” — is essential to spur investment in America’s broadband infrastructure. Pai cites studies claiming broadband investment fell in the two years since the Obama-era FCC enacted net neutrality regulations.
All these claims are dubious. Where the FCC says broadband investment has fallen since 2015, ISPs have consistently told their investors (via legally-binding financial disclosures) that net neutrality regulations were not impeding them. Almost every major network operator — from Comcast and Verizon to Time-Warner, Sprint, and T-Mobile — has engaged in or is actively engaging in some form of blocking, paid prioritization, or (particularly) throttling with little or no disclosure to customers. And network operators didn’t set up fast lanes in the “light-touch” regulatory era before 2015
because they were waiting to see how a number of court challenges to FCC authority were going to turn out.
Public opinion also does not agree with Commissioner Pai. Surveys sponsored by both the cable industry and Mozilla — arguably on opposite sides of the issue — find the American public remains overwhelmingly in favor of net neutrality.
In this light, Commissioner Pai’s view on the value of public opinion is interesting. When proposing to undo net neutrality, Pai promised a “far more transparent” process than that used by the FCC in 2015. Yet the process the FCC implemented this time around apparently gave no thought to filtering out automated spam and trolling of the comment process, leading to the FCC claiming that it was just too burdensome on them to, you know, actually process the comments. Also too burdensome? Publishing the comments, or responding to inquiries about the comment process. In the words of Commissioner Mignon Clyburn, the process completely ignored “thousands of consumer complaints and millions of individual comments that ask the FCC to save net neutrality and uphold the principles that all traffic should be created equal.”
The FCC’s proposal states that the “disinfectant of public scrutiny and market pressure” is far more effective at controlling the broadband industry than any government regulation. Yet, under Pai’s leadership, the FCC has found a way to disregard public comment and craft a regulatory framework that relies on network providers voluntarily disclosing whether they’re violating any rules. And market pressure works only if there is a market: according to the FCC’s own proposal, at the end of 2016 some 48.9 percent of Americans had access just a single broadband provider capable of meeting the FCC’s definition of “modern broadband” (25 Mbps downstream and 3 Mbps upstream) or no access at all. If you don’t like your ISP,
it’s hard to take your business elsewhere when there is no other ISP. So much for market pressure.
Although many consumer rights groups continue to protest the FCC’s proposal (and the EFF has created a service enabling citizens to directly lobby their congressional representatives on the issue), the fix is in: it’s very unlikely any public action will delay or fend off the FCC’s action.
It’s difficult to say how all this will play out for network operators, Internet companies, and consumers. Network operators all give lip service to wanting a free and open Internet, and they claim they have no interest in blocking services or restricting access. But these are the same companies that feel Internet heavy-hitters like Apple, Amazon, Facebook, Google, and Netflix have made billions off the “free lunch” of network neutrality requirements, and the only leverage network providers have is limiting access to consumers. So, there is absolutely no question network operators will want more money from Internet companies — as fast as they
can get it. Similarly, Internet companies will pay up if there’s no alternative, and they’ll almost certainly pass those costs on to consumers. So, consumers can expect charges and fees to increase, along with having virtually no recourse if their ISP blocks or degrades Internet services they want or need.
iOS 11 Encrypted Backup Change Reduces Security, Boosts Data Safety
Digital forensics firm Elcomsoft revealed this week that Apple has changed how encrypted iOS backups are protected, reducing security to improve the overall user experience.
Elcomsoft’s discovery kicked off a vigorous debate on Hacker News and Twitter, but does this change represent a real risk to the average Apple user? The answer is yes, but that answer has to be understood in the proper context. In absolute terms, Apple’s change is a step backward for iOS security, but the nuances of real-world usage suggest that Apple believes it’s a net improvement for protecting user data from loss.
While I wish that Apple hadn’t made this change, and I do consider it a hit to my personal security, I can see where Apple is coming from and how the company may see it as enhancing the safety of user data. Let me explain.
The Difference between iCloud and iTunes Backups — By default, iOS devices try to back up to iCloud. Apple encrypts those backups in storage, but they aren’t protected with a separate user-defined password or encryption key. That’s why Apple can access customer data if required by law enforcement; Apple controls the encryption key and can recover the data without the customer’s knowledge or permission.
Before you call this a massive security flaw, keep in mind that my sources tell me that Apple has seriously looked at encrypting these backups with customer-managed encryption. However, allowing users to control encryption keys creates a massive usability problem. If someone were to lose their device and couldn’t remember their iCloud credentials, which happens all the time, they would lose access to all their data forever. Yes, it’s possible to regain access if you have more than one device, but many millions of Apple’s customers own just a single iPhone.
I would love to see Apple make customer-managed encryption for iCloud backups an option, but I see no viable path for it to become the default. Too many users lose access to their iCloud accounts — and thus to irretrievable family photos — for Apple to implement something that would unilaterally prevent data recovery. And too few journalists and security professionals either understand or want to admit the complexity of Apple’s situation, which leads to oversimplified suggestions that “Apple could just…”
Apple does try to minimize customer risk by limiting what is backed up. Most notably, your keychain passwords are not backed up to iCloud unless you separately enable iCloud Keychain, which has a different passcode that follows an entirely different security and restore mechanism. Apps can also control what data goes into an iCloud backup, ensuring that really sensitive information isn’t exposed.
Encrypted iTunes backups are a completely different beast. Rely on iTunes for backing up your iOS device and effectively all your data, including your entire keychain, is backed up locally (although I believe app programmers can still block the transfer of some keychain items in their code). The security assumption is these local backups are protected by a separate password and strong encryption, Apple never sees them, and no one but the device owner can access them. I’ve glossed over a few details, but that’s essentially how encrypted iTunes backups work.
That’s why, when you upgrade to a new iPhone or iPad, you should always restore from an encrypted iTunes backup or an iCloud backup that has iCloud Keychain enabled. You won’t have to log back into everything as most of your keychain items will be restored, plus a lot of other ephemeral data.
How Encrypted iTunes Backups Changed — In iOS 8, 9, and 10, if you made an encrypted iTunes backup to your local machine, the password protecting the backup was owned by the iOS device. Although you set the password on your computer, the device itself would then protect all future backups to any computer using that password. The host computer itself wouldn’t have access to the backup password, although you could store it in the keychain.
In other words, when you make an encrypted iTunes backup, your iOS device does the encryption, not your computer. This approach materially improved the security of iOS backups, since the computer itself couldn’t access the data without the encryption key. It also prevented someone who had gained physical possession of the device from performing an encrypted backup with a new password and then using that to unlock and snoop the data.
This backup password was different from your computer’s login password or device’s passcode. If you lost your backup password, you could never restore from those backups ever again, as you would want to do when buying a new iPhone. Since there was no way to set a new backup password without knowing the old password, no one, including Apple, could help you. Worse, according to Elcomsoft, you could never again make another encrypted backup that you could restore in the future without factory-resetting your device.
(Conceivably, if you still controlled the device, you could switch to iCloud backups, reset the device, and restore from iCloud to reset the iTunes backup password, although I haven’t tested that.)
This previous iTunes approach was secure, but not very user-friendly; just the opposite of how iCloud backups are user-friendly, but not as secure as they could be.
Here’s what’s new and controversial. In iOS 11, Apple lets you reset the encrypted local backup password if you know the device’s login passcode.
Using the device passcode as a second password reduces security because if an attacker can get the passcode, they can then reset the encrypted backup password and perform arbitrary backups with a weak passcode that tools from companies like Elcomsoft can crack.
“So what?” you say. “The attacker has the iPhone and the passcode anyway.” True, but iOS devices employ a fair number of protections even if you have local access. Tools that can read full device backups can access much more information. For example, they can pull passwords out of your keychain that are not accessible when using iOS. Your iPhone may use your email password to log into your email account, but it never displays that password. By hacking into a backup, an attacker can read it and log into your account or change your password and lock you out. And that’s just the tip of the iceberg — all other passwords stored in the keychain would be accessible as well.
Before this change, there was no way an attacker could hack into your iTunes backups without the backup password. Now, if the attacker can get your passcode, everything in the iPhone is fair game.
Risks Have Nuance — I’m a bit surprised Elcomsoft publicized this change in iOS 11 because it’s a boon to forensics firms. Elcomsoft often hypes up their ability to access iOS devices, but when you read between the lines, you see that their access pretty much always depends on having a passphrase or some other circumvention first. Security firms often use these kinds of discoveries as a marketing tool, so you should always take them with a grain of salt.
Let’s take a step back and look at this change within the context of the Apple ecosystem.
There are over a billion iOS devices out there, with many hundreds of millions of users. In recent years, Apple has had an exceptional track record on security and privacy in the iOS world. Elcomsoft hints they believe Apple made this change at the behest of law enforcement, but doing so would be antithetical to Apple’s current culture. Apple is the company that faced down the FBI.
Here’s how I see it. What percentage of iOS users use encrypted iTunes backups? What percentage of those people lose their backup password and then have to reset their device — possibly with a complete loss of data — if they ever want to make or restore from an encrypted backup again?
On the other side of the equation, what percentage of users with encrypted backups lose their device (even temporarily) and the passcode, thus allowing an attacker to change the encrypted backup password, perform a backup, and crawl through their data?
Only Apple, via support requests, knows those numbers, and thus we have to assume that Apple believes that fewer people will suffer from inherently reduced security than will benefit from a second chance at recovering data from a backup.
There is no question that allowing the iOS device passcode to act as a secondary backup password reduces the security of encrypted iTunes backups on an individual level. As a professional paranoid I really wish Apple hadn’t made this change.
But there is also a legitimate case to be made that Apple improved the overall iOS experience for a much larger percentage of its customer base by making it less likely that average users could lose access to their encrypted iTunes backups entirely.
As an Apple customer who once had to factory-reset one of my children’s iPads because I had forgotten the backup password, hadn’t backed up to iCloud to save space, and couldn’t recover it from the Mac keychain where I… had failed to store it, I can certainly see Apple’s point of view.
TidBITS Watchlist: Notable Software Updates for 4 December 2017
Keyboard Maestro 8.0.4 — Peter Lewis of Stairways Software has issued Keyboard Maestro 8.0.4 with improvements for the recently updated automation and clipboard utility (see “Keyboard Maestro 8 Automates Even More of Your Mac Life,” 9 October 2017). The release adds “increases” and “decreases” options to the MIDI controller change trigger, adds more clipboard flavor exclusions for Microsoft Word to avoid a longstanding bookmark link issue, ensures that the Clipboard Switcher Info button setting is remembered, fixes a bug that prevented some fields from being edited in
disabled actions, and fixes the Command-K action to toggle the Action Selector. Keyboard Maestro 8 costs $36, and upgrades from previous versions are $25. Anyone who purchased after 1 March 2017 is eligible for a free upgrade. ($36 new with a 20 percent discount for TidBITS members, free update, 22.3 MB, release notes, 10.10+)
Read/post comments about Keyboard Maestro 8.0.4.
BBEdit 12.0.2 — Bare Bones Software has issued BBEdit 12.0.2 with a lengthy list of 90 improvements and bug fixes for the long-standing text editor (see “Modernized BBEdit 12 Manipulates Columnar Data and More,” 14 October 2017). BBEdit no longer submits recently opened items to the system-wide Recent Items list that appears on the Apple and Dock menus to avoid a crash, resolves several issues with FTP/SFTP, patches several memory leaks, fixes a bug that disabled menu items found by searching in the Help search field, and restores heading level indicators for
entries in the function menu for Markdown documents.
You can upgrade from BBEdit 11 for $29.99 or from an earlier version for $39.99 (upgrades for purchases made after 1 March 2017 are free). Upgrade prices apply to copies purchased from the Mac App Store as well. ($49.99, $29.99 or $39.99 upgrade, free update from version 12, 13.5 MB, release notes, 10.11.6+)
Read/post comments about BBEdit 12.0.2.
BusyCal 3.2.5 and BusyContacts 1.2.6 — BusyMac has released BusyCal 3.2.5 and BusyContacts 1.2.6, with both apps fixing persistent login prompts. BusyCal 3.2.5 also addresses a date/time formatting issue introduced in version 3.2.4 (released the day before 3.2.5), adds a faded month name to additional cells in the Month view, resolves a bug that occurred when dragging an event to the To Do list and sorting by title, and fixes time zone menu updating in the toolbar. BusyContacts 1.2.6 can now display contact photos in a circular mask and ensures that checking an address book
in the source list selects it. ($49.99 new for BusyCal from BusyMac or the Mac App Store, free update, 11.8 MB, release notes, 10.11+; $49.99 new for BusyContacts from BusyMac or the Mac App Store, free update, 5.6 MB, release notes, 10.9+)
Read/post comments about BusyCal 3.2.5 and BusyContacts 1.2.6.
LaunchBar 6.9.3 — Objective Development has released LaunchBar 6.9.3 to address a few bugs in the just-released version 6.9.2, which in turn fixed a bug that prevented Recent Documents of apps not updating in macOS 10.13 High Sierra and improved 1Password info browsing to allow opening of URLs. The keyboard-based launcher adds support for the subscription, non-subscription, and Setapp versions of Ulysses; enables LaunchBar Actions to use images stored in an app’s asset catalog; resolves an issue with emoji icons being cut off in 10.12 Sierra; fixes missing contact images for
contacts that are stored in multiple accounts; and adds support for sending selected text to macOS Sharing Actions that normally support only sending files. ($29 new with a 20 percent discount for TidBITS members, free update, 14.5 MB, release notes, 10.9+)
Read/post comments about LaunchBar 6.9.3.
Default Folder X 5.1.9 — St. Clair Software has released Default Folder X 5.1.9, adding a new Recently Closed submenu to the Finder’s Window menu. The Open/Save dialog enhancement utility properly hides file extensions when the Hide Extension checkbox is selected in a Save dialog, provides better workarounds for a bug in macOS 10.13 High Sierra that prevented Default Folder X from knowing which item was selected in a file dialog, correctly handles Desktop and Documents folders on iCloud, fixes a potential crash that could occur when Default Folder X relaunched the Finder, and adds an option to make Default Folder
X use color icons in its toolbar (via a Terminal command). ($34.95 new, TidBITS members save $10 on new copies and $5 on upgrades, 7.0 MB, release notes, 10.10+)
Read/post comments about Default Folder X 5.1.9.
ExtraBITS for 4 December 2017
In ExtraBITS this week, developer Marco Arment offers some suggestions for how Apple could improve the MacBook Pro, and Bloomberg’s Mark Gurman reveals the messy development history of Apple’s forthcoming HomePod.
Marco Arment: How Apple Could Fix the MacBook Pro — Developer Marco Arment has some ideas for how Apple could restore the current MacBook Pro to the glory of the 2015 model. If nothing else, Arment suggests that Apple return to scissor key switches, since the butterfly switches in the current keyboards are disliked by many, unreliable, and expensive to repair. He also proposes removing the Touch Bar, a return to “inverted-T” arrow keys, more ports to reduce dongle dependency, better and more affordable first-party USB-C hubs, and chargers that bring back the charging LED and cable management arms. We
agree with Arment, though it’s impossible to know if Apple is open to hearing and responding to such criticisms from the community.
Why the HomePod Faces an Uphill Battle — Apple has officially delayed the HomePod until next year, and many reports indicate that, unlike the standalone Amazon Echo, it will depend on a connected iPhone for most of its smarts. Bloomberg’s Mark Gurman has gathered the inside story: the HomePod has been in development for over five years, was originally conceived of as a modern iPod Hi-Fi, and its designers were blindsided by the Amazon Echo. But despite the Echo’s success, Apple focused on sound quality and not voice assistant capabilities, which
may prove problematic in the market. Regardless, the HomePod will have a hard time competing on audio quality alone, since you can buy several Amazon Echoes for the price of one HomePod.