Using Apple’s iCloud Passwords Outside Safari
We regularly recommend using a password manager like 1Password, and for good reason. Passkeys may eventually take over—and I hope to explore them soon—but until that time, we’re stuck with passwords, and managing them manually is less secure and vastly more work. For many years, solutions like 1Password, BitWarden, Dashlane, and LastPass (which I no longer recommend—see “LastPass Publishes More Details about Its Data Breaches,” 3 March 2023) fell into the must-have category.
Apple’s Keychain Access utility has long provided basic password management capabilities in macOS but has never been particularly convenient to use. With macOS 12 Monterey, iOS 15, and iPadOS 15, Apple gave passwords a better user-facing interface in System Preferences and Safari on the Mac and the Settings app on the iPhone and iPad. Although the settings screens are labeled Passwords and the iCloud-based password syncing feature is called iCloud Keychain, Apple doesn’t seem to have a formal name for the totality of these password management features, making it hard to talk about them in the same sentence as something like 1Password. For this article, I will use the name iCloud Passwords for reasons that will soon become obvious.
Although iCloud Passwords didn’t—and still doesn’t—have full feature parity with third-party password managers, it was pretty good. It offered all the basics, such as auto-fill, editing, searching, and even syncing through iCloud Keychain. Over time, Apple added support for one-time passwords, password sharing, and more. Importantly, it’s also completely free.
Despite these improvements, iCloud Passwords suffered in one significant way: it worked only in Safari. On the iPhone and iPad, that wasn’t a problem because other Web browsers relied on the same WebKit engine as Safari. (Apple also allowed Safari to treat third-party password managers as first-class alternatives.) But Mac users who wanted to use Chromium-based browsers like Arc, Brave, Google Chrome, Microsoft Edge, Opera, and Vivaldi, or Mozilla’s Firefox couldn’t take advantage of iCloud Passwords.
In 2021, Apple released the iCloud Passwords extension for Google Chrome, but only for Windows. In July 2023, Apple updated it to version 2.0, adding support for Mac versions of Google Chrome running in macOS 14 Sonoma. Although I’m happy with 1Password, I’ve been using iCloud Passwords for the past month in Arc to see if I could recommend iCloud Passwords for those who don’t rely on Safari. While I miss features from 1Password, the answer is yes: iCloud Passwords works fine. At least that’s true for me—I see reviews on the Chrome Web Store page that claim it doesn’t work or broke after some update, but I’ve been using it long enough that I’m comfortable saying it’s functional.
Although Apple released iCloud Passwords only for Chromium browsers—and it seems to work equally well in all the variants I’ve tried—the company has done nothing for Firefox users. However, an independent developer named Aurélien recently published a Firefox add-on also called iCloud Passwords, so that’s an option for those running Sonoma or recent versions of Windows—it doesn’t work for earlier versions of macOS. It’s not yet well-known, with only 716 users last I checked (versus 2 million for the iCloud Passwords Chrome extension), but I’ve installed it and verified that it works. Although I’m a little hesitant to recommend an independent add-on that interacts with a system-wide password store, it’s open source, and anyone can view its code on GitHub.
Passwords Settings
Before we get to the specifics of using iCloud Passwords in a Chromium browser, I want to review the basics of password management in macOS. You access your passwords in System Settings > Passwords or Safari > Settings > Passwords—they show the same set of passwords—and you must authenticate every time you go there. Touch ID or Apple Watch authentication makes that a lot easier.
Let’s look at all the options from the top:
- Search field: Use this to find logins in the list below by searching for the site name or username. Unlike 1Password, you can’t search for strings contained in your passwords.
- + menu: Choose New Password or New Shared Group as desired. Most of the time, you’ll create new logins while setting up an account on a website—iCloud Passwords offers to remember the login information for you. More on shared groups shortly.
- ••• menu: Apple puts the Import and Export commands in this unhelpfully labeled menu. The import/export format is CSV, and Apple warns that exported passwords will be stored unencrypted. (As an aside, I think using + and ••• to label menus is borderline criminal interface design, but it’s just one of many decisions in System Settings that will make its designers first up against the wall when the revolution comes.)
- Security Recommendations: If the switch here is enabled, Apple will check your passwords against those from known breaches and warn you if they may have been compromised. The company doesn’t say explicitly, but I imagine it uses Have I Been Pwned, much like 1Password does for its Watchtower feature. Apple also points out logins that have weak passwords.
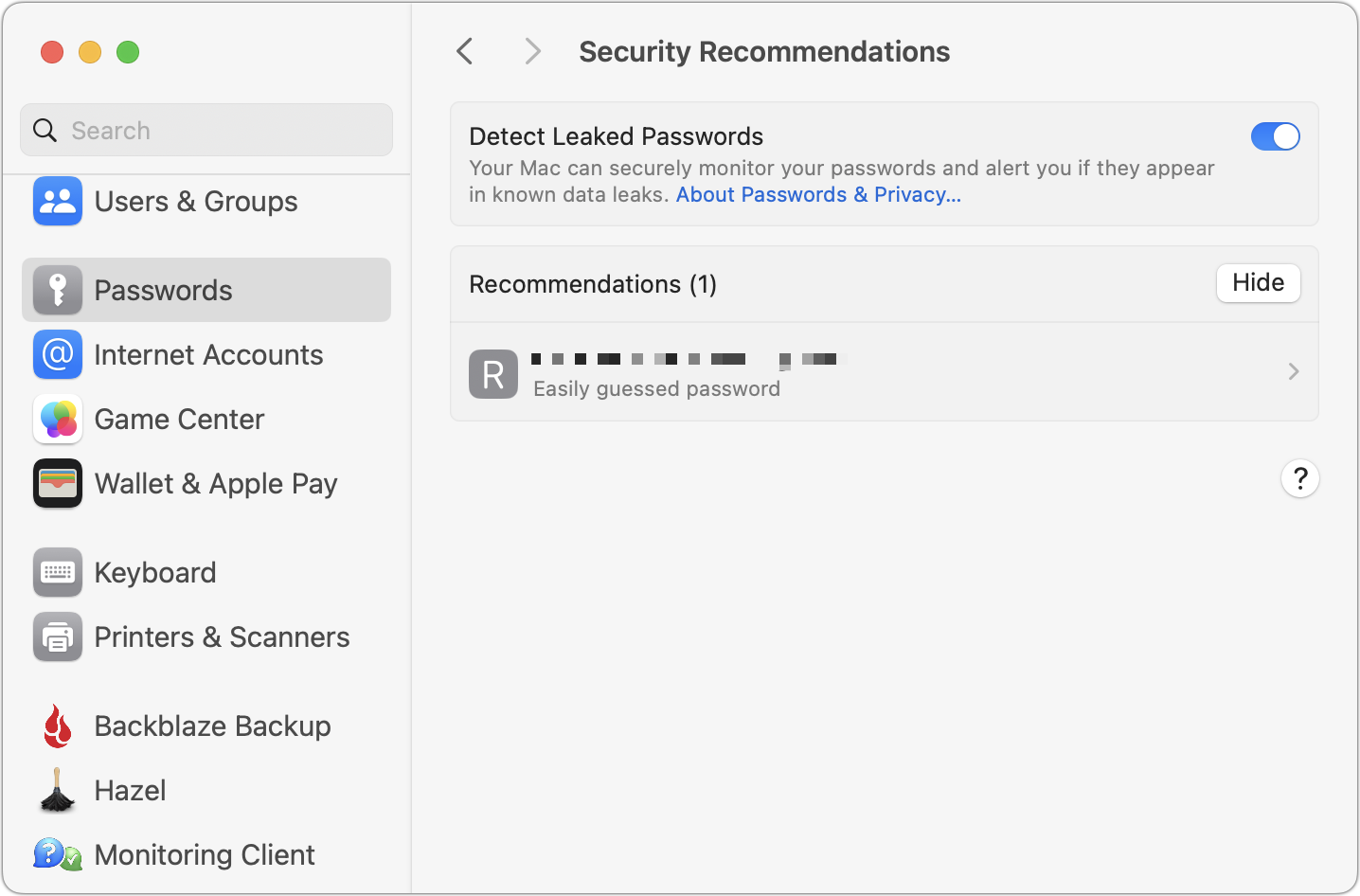
- Password Options: I see no reason to turn off autofill or the option to clean up verification codes automatically, but I’m intrigued by the “Use passwords and passkeys from” section. iCloud Keychain is the only option here, but this setting parallels the iOS Settings > Passwords > Password Options screen that lets you use third-party password managers. Perhaps Apple will open up macOS to others in the future.
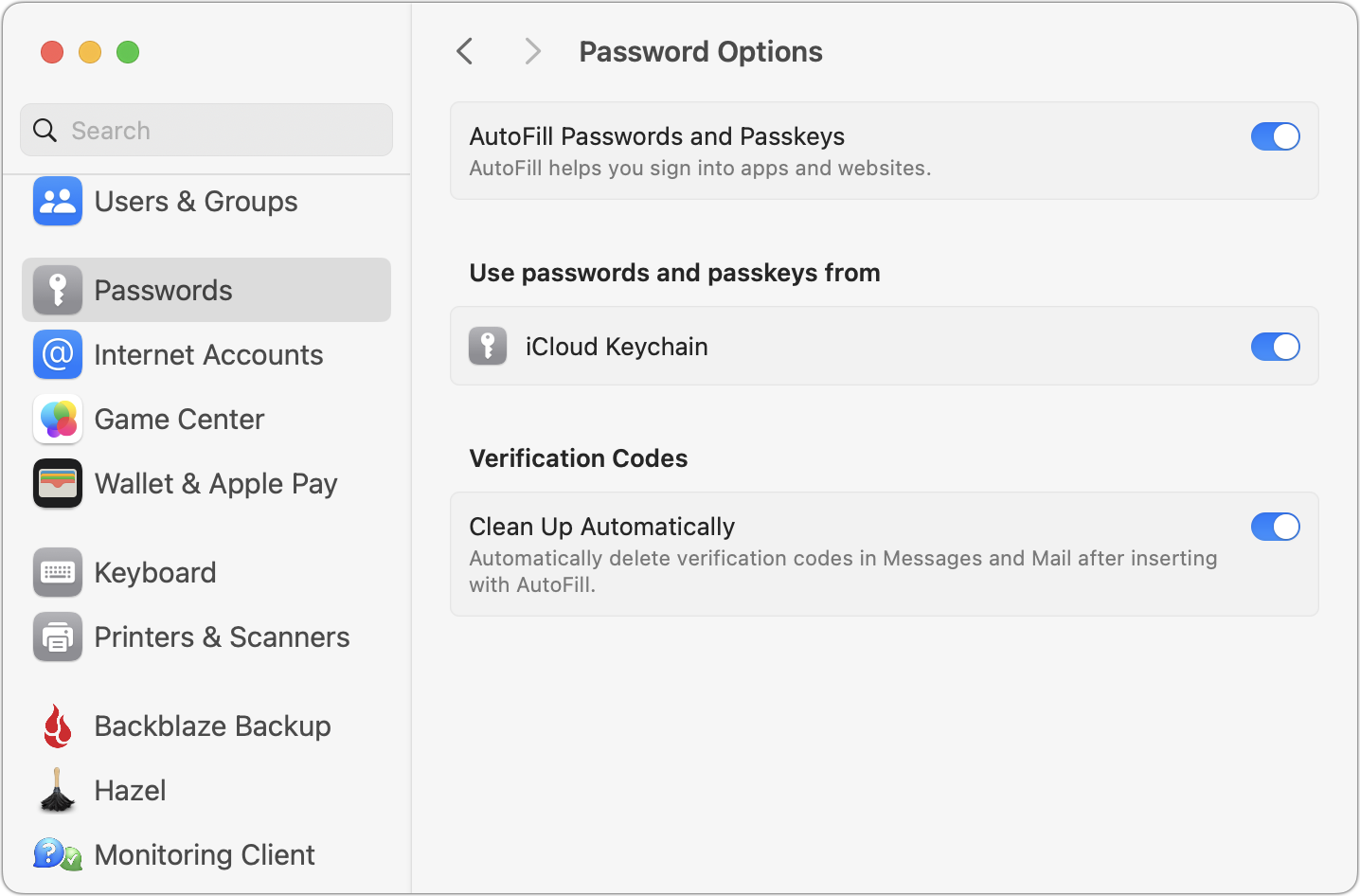
- Share Passwords with Family: This option triggers an assistant that walks you through creating a Family Passwords shared group, adding family members, and moving passwords from your personal set to the shared set. It’s simple and well done. You can also share passwords with any other group; choose New Shared Group from the + menu at the top.
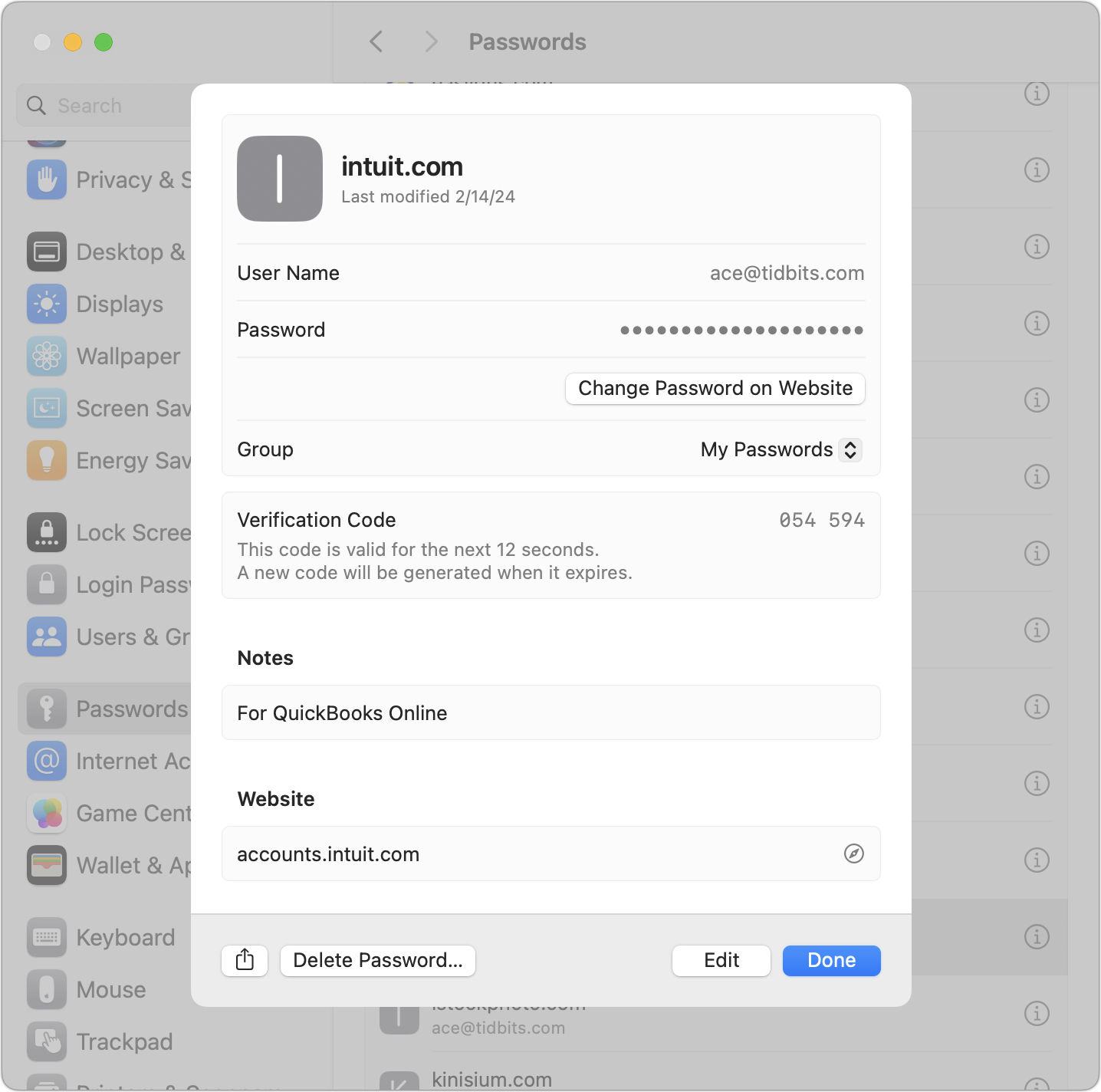
- Edit login: Finally, you can edit any login by clicking its ⓘ button. Happily, double-clicking anywhere on the login item also works, which isn’t true for controls like System Settings > General > Software Update > Automatic Updates. Most of the items here are self-explanatory, though all the Change Password on Website button does is take you to the top level of the site. Note the Verification Code section, which can create and autofill two-factor authentication codes (see “Add Two-Factor Codes to Password Entries in iOS 15, iPadOS 15, and Safari 15,” 7 October 2021). Unfortunately, the Website section, which shows the domain of the site on which iCloud Passwords will autofill your credentials, is not editable. That’s too bad—I’ve had to edit remembered URLs in 1Password occasionally because the URL used for account creation didn’t sufficiently match the login URL.
Nothing in Passwords Settings will set the world on fire, but Apple has provided a solid set of basic features.
iCloud Passwords in a Browser
To autofill your passwords in a Chromium browser like Arc, Brave, or Google Chrome, you need to install Apple’s iCloud Passwords extension from the Chrome Web Store. That’s as simple as clicking the Add to Chrome button and acknowledging that you want to install when prompted.
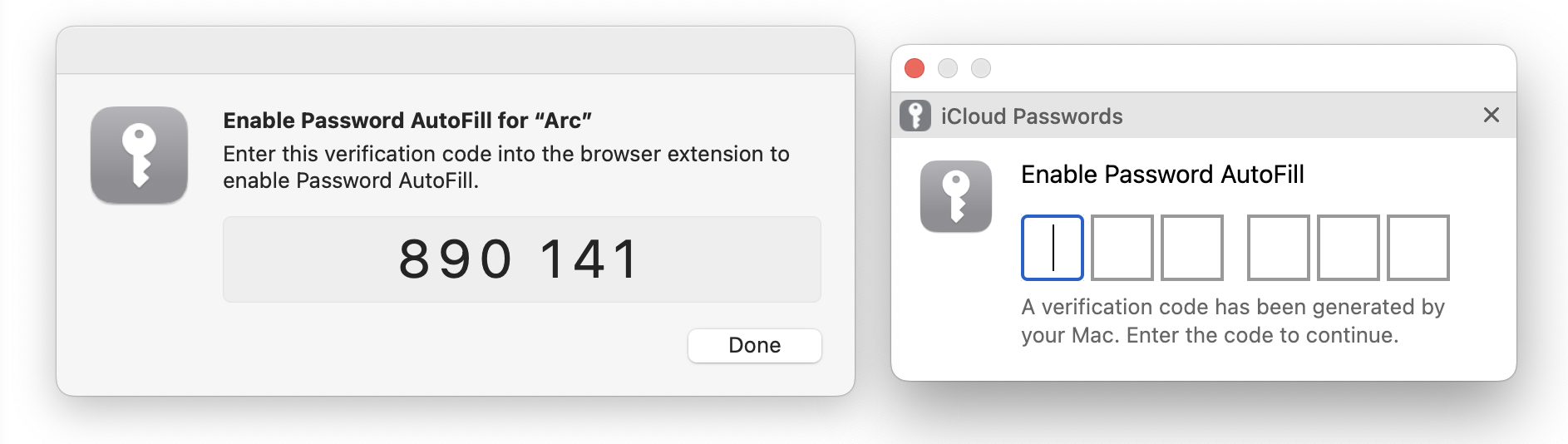
How you interact with extensions varies a bit by browser, though most let you add them to a toolbar. In Chromium browsers other than Arc (which has a bug in this area), clicking a login form displays a notification that you can click to enable Password AutoFill. Arc has no such toolbar, but choosing Extensions > iCloud Passwords has the same effect as clicking the toolbar button or the notification.
However you invoke it, iCloud Passwords presents you with two dialogs: a system-level dialog with a verification code and a browser-level dialog into which you enter it. If you make a mistake typing, you’re instantly presented with another code.
Although this verification approach is straightforward, it’s required for every launch of the Web browser, so you may end up typing a lot of verification codes. It’s much easier to use biometric authentication via Touch ID or an Apple Watch in 1Password; I presume other password managers also support biometric authentication.
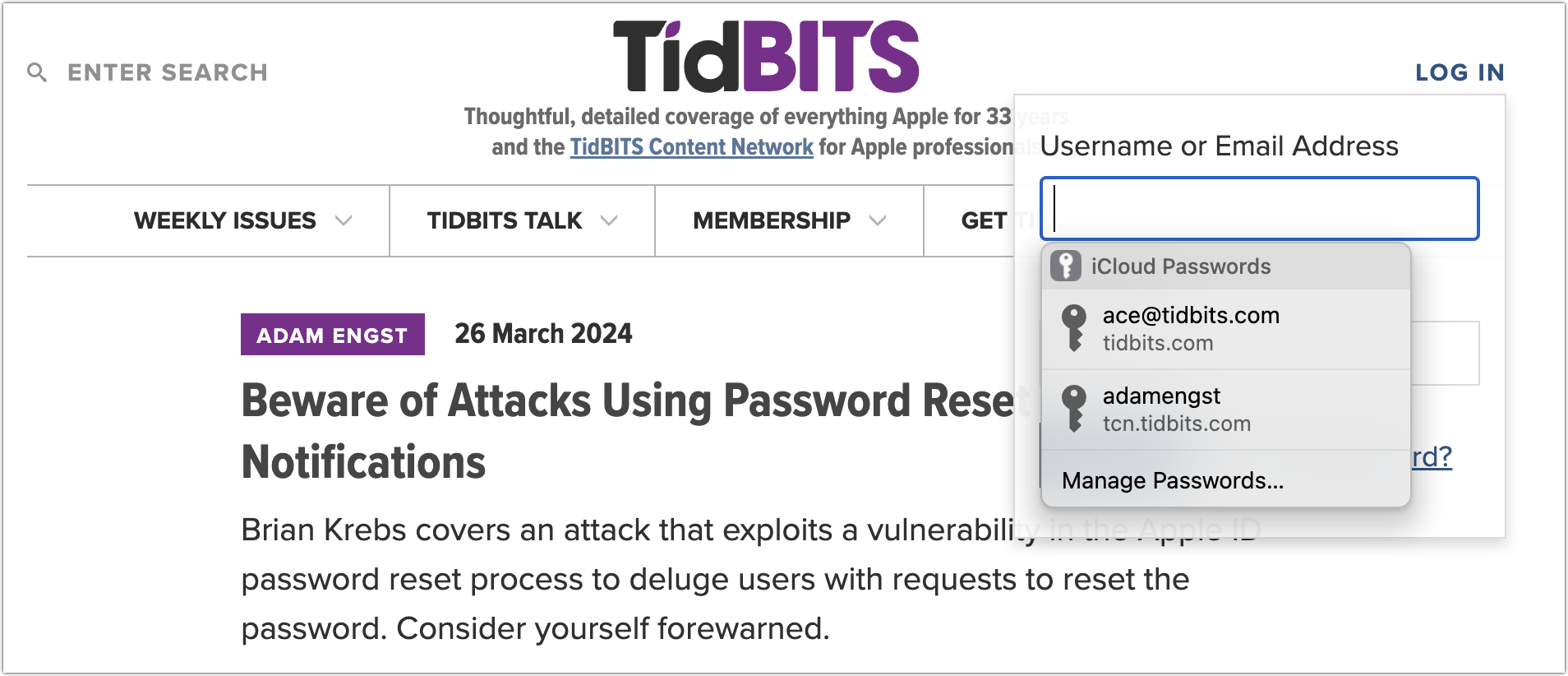
Once you’ve enabled Password AutoFill, it’s trivially easy to use. Just click in a login form, and iCloud Passwords detects that action and presents you with passwords that match the domain of the site you’re on. Click one to enter its information in the login form fields. Typically, only a single password will appear, but if you have multiple logins at different sites within the same domain, as I do in the screenshot below, you get to pick one.
(As an aside, this domain detection is one of the key reasons to use a password manager—they can’t be fooled into helping you enter a password onto a malicious site pretending to be something else. A human might not notice, but app1e.com isn’t apple.com in the eyes of a password manager.)
If a login form has both a username and password field, iCloud Passwords will autofill both. If the login process first requires you to enter your username, followed by the password after a form or page refresh, you’ll likely have to click again to autofill the password separately. 1Password is better at injecting the password into the second field that appears without requiring manual intervention.
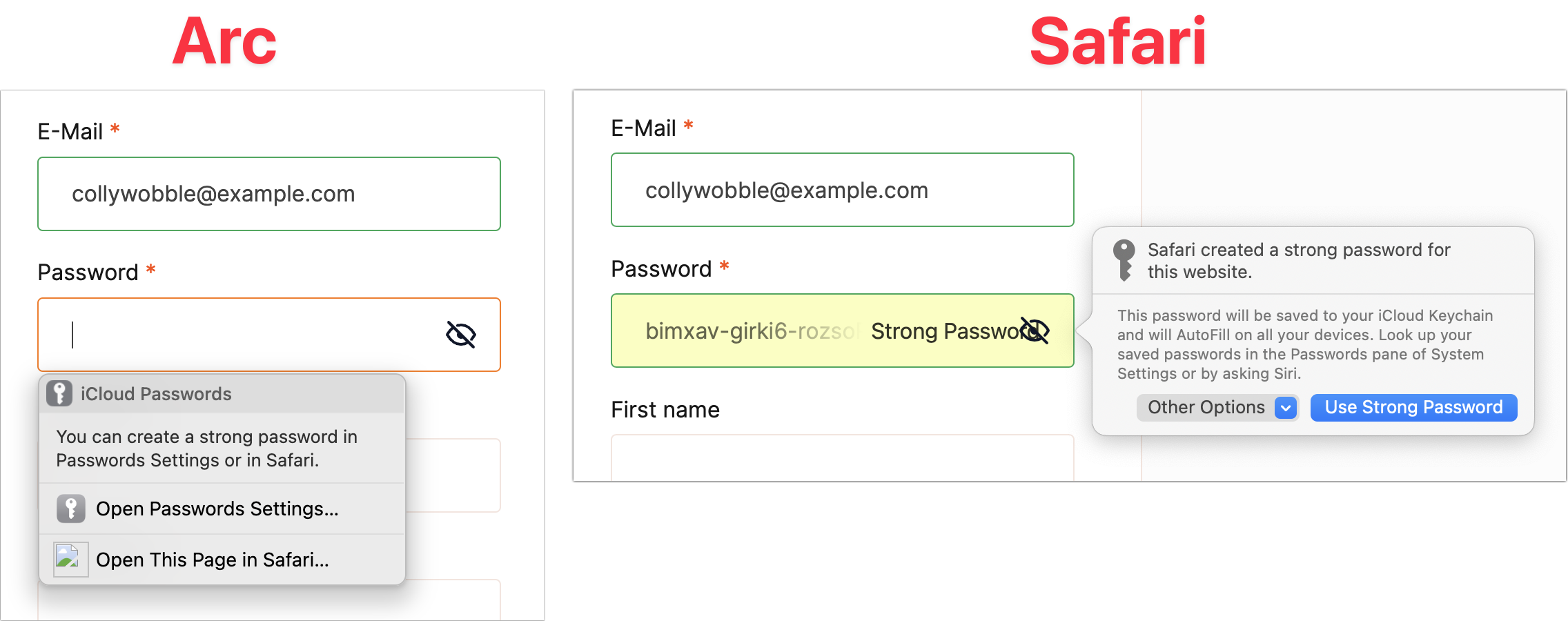
One last thing. If you need to create a new account, iCloud Passwords almost always notices and offers to save your credentials. What it doesn’t do, unfortunately, is create a secure password for you. Instead, it suggests creating a strong password in System Settings > Passwords or opening the page in Safari (below left, ignore the broken graphic icon). Indeed, Safari automatically generates strong passwords and saves them to your password collection when you click Use Strong Password (below right). So, the better part of valor is to switch to Safari when creating new accounts and then switch back to log in with the new credentials. If you instead use System Settings > Passwords, you’ll have to click the + menu, choose New Password, click the Create Strong Password button, copy the password, switch back to your browser, and paste the password.
Limitations Compared to Other Password Managers
I’ve mentioned a few ways that iCloud Passwords fails to match up to the likes of 1Password, but let’s collect all of them here so you get a sense of the differences. The iCloud Passwords extension:
- Generates many more verification requests—one per launch of the browser.
- Doesn’t support biometric authentication, so those verification requests can be answered only by typing in a six-digit code. (Although the code may be easier than typing in a master password.)
- Isn’t quite as capable of autofilling login fields separated by a form or page refresh.
- Sometimes fails to offer to save a manual login.
- Supports only logins, unlike other password managers, which can store many other types of private information, such as identity cards, medical record cards, bank accounts, API credentials, secure notes, and even documents.
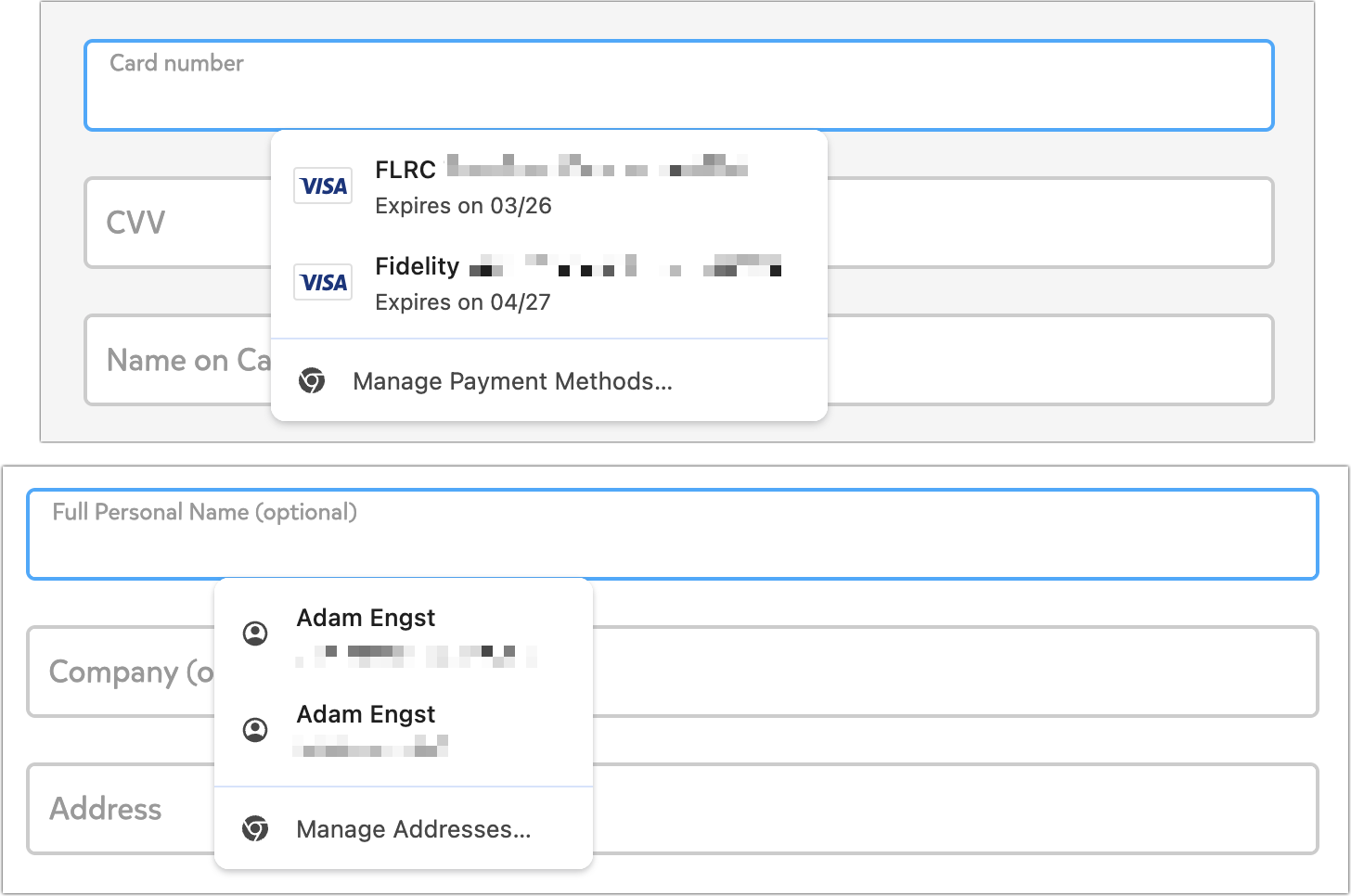
- Can’t autofill credit card or address information.
You can work around this last limitation using browser features. Chromium browsers can all autofill payment methods and addresses, but by default, iCloud Passwords blocks those features from working, even though it won’t help you in that department. If you circumvent the iCloud Passwords block on browser autofill, you can get the best of both worlds. Follow these steps:
- In your Chromium browser, navigate to the Extensions page, usually by choosing Window > Extensions. In Arc, it’s Extensions > Manage Extensions.
- Click the Details button next to iCloud Passwords.
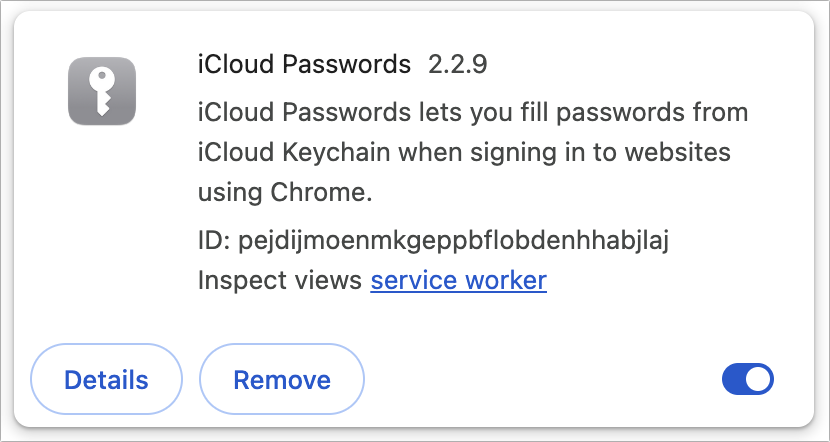
- On the iCloud Password Details screen, click the button next to Extension Options, and in the dialog that opens, deselect Turn Off Chrome AutoFill. That double-negative allows Chrome’s AutoFill to operate independently again.
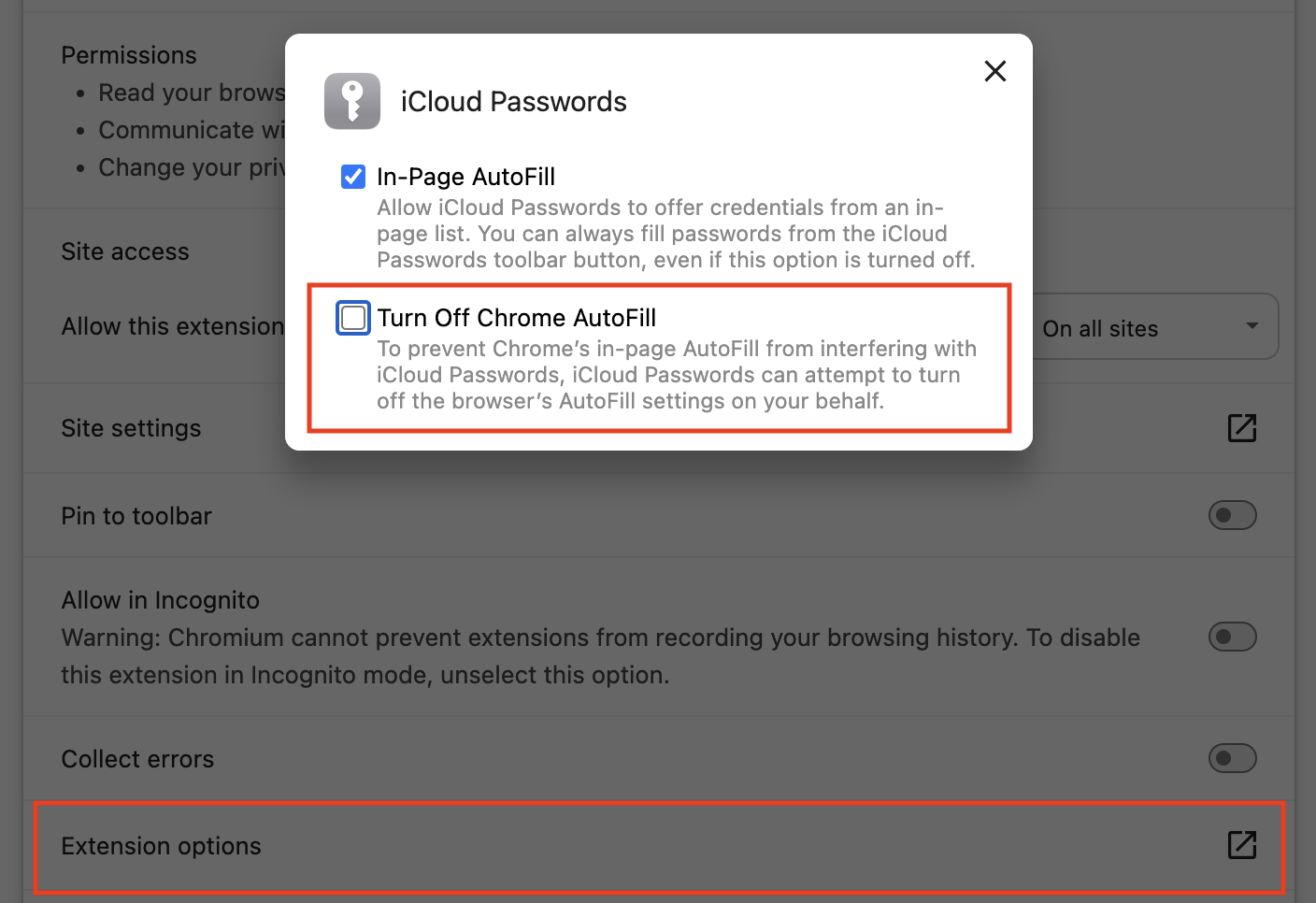
- Navigate to the browser’s Autofill settings, which are usually accessible from the main Settings page under “Autofill and Passwords,” although Microsoft Edge puts it under Profiles. The URL browsername://settings/autofill will always take you there in Chromium browsers.
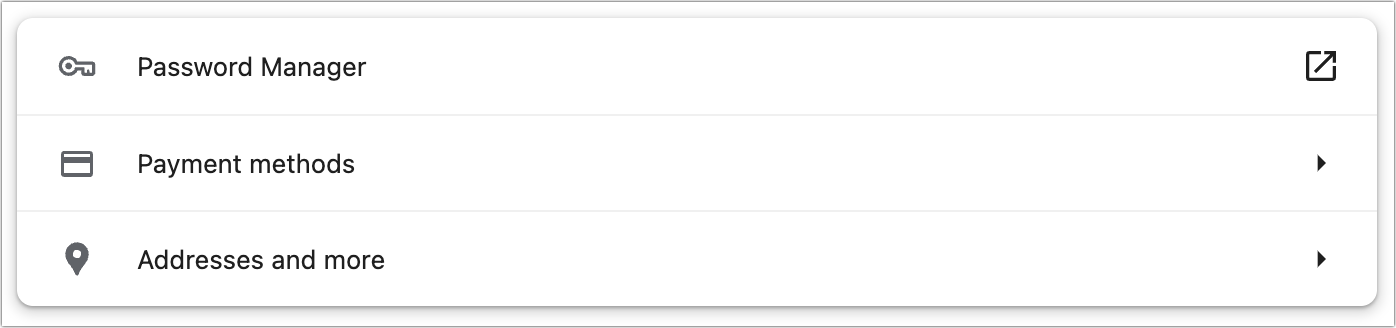
- Start with Payment Methods. Make sure “Save and fill payment methods” is turned on. Use the Add button to add your credit card information. It won’t let you save credit card CVV codes for security reasons, so you must remember and enter them manually. When you’re done, click the Back arrow in the upper left to return to the Autofill and Passwords screen.
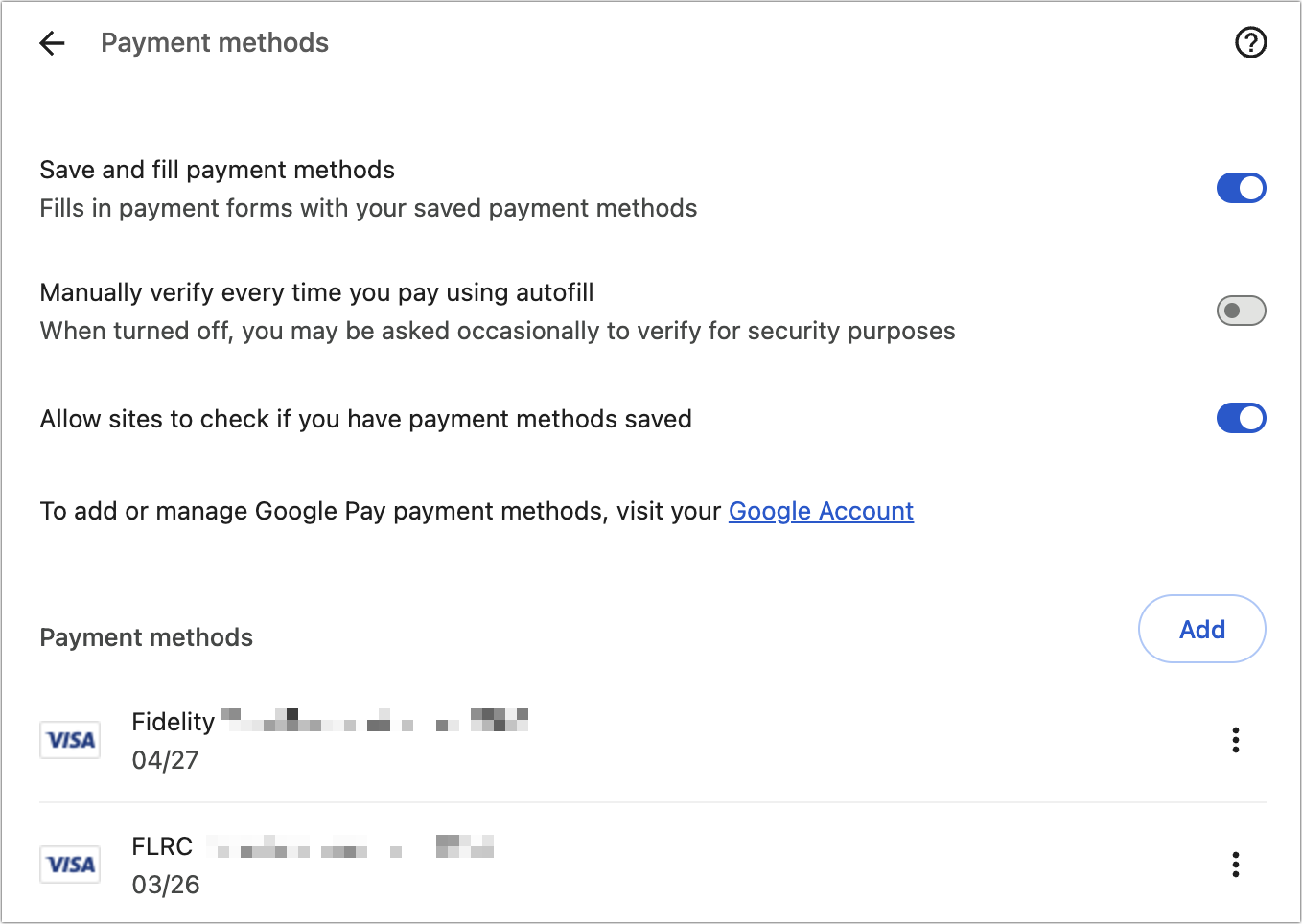
- Next, in Addresses and More, ensure that “Save and fill addresses” is turned on, and enter any addresses you want to autofill. Click Back to return to the Autofill and Passwords screen.
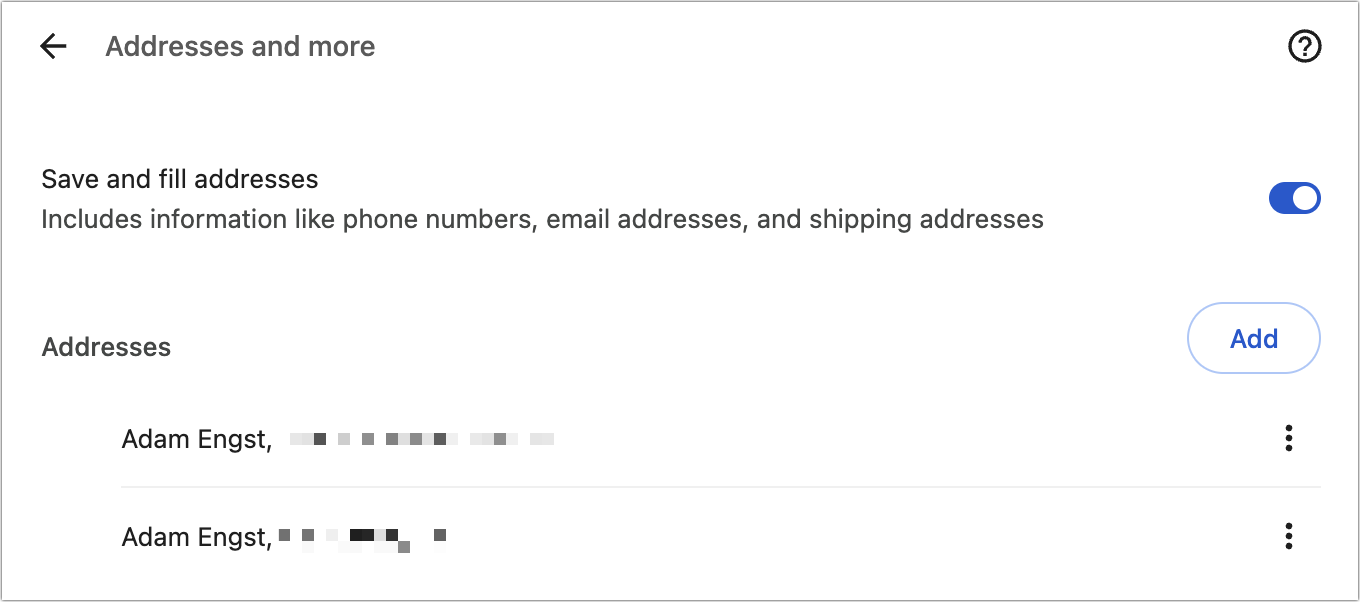
- Finally, click Password Manager, and then click Settings in the sidebar. Deselect “Offer to save passwords” to prevent your browser from asking you to save passwords every time you log in to a site using iCloud Passwords.
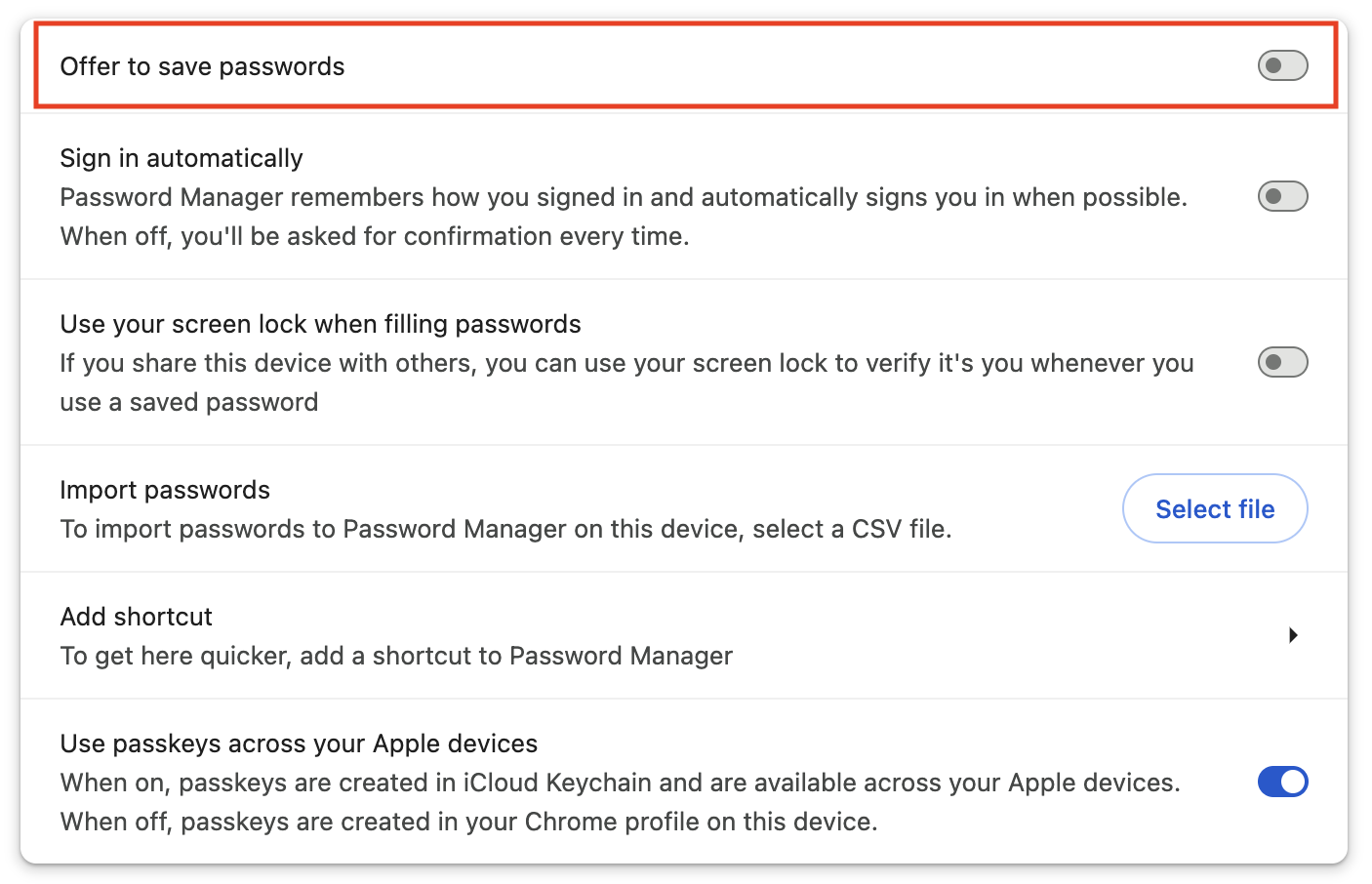
Once you’ve done all that, you should be in a situation where iCloud Passwords autofills your login credentials, and your browser autofills credit card information and addresses. The browser-level interface looks a little different but works well—you simply click in a credit card or address field and then click the desired set of information from the pop-up.
Now that I’ve written this article, I fully admit that I’m going to disable iCloud Passwords and revert to 1Password because it’s easier to use and autofills more information. Plus, my nearly 1000 logins are stored in 1Password—I’ve been using 1Password’s Quick Access pop-up to find and enter credentials in Arc logins so iCloud Passwords could remember them. In the past month, I’ve migrated 73 logins to iCloud Passwords, and although those take care of most of my day-to-day logins, I never get through a week without having to bring more over from 1Password.
But it’s clear that with the addition of the iCloud Passwords extension for Chromium browsers and some judicious browser configuration for payment methods and addresses, it’s entirely possible to rely on Apple’s free password management tools.

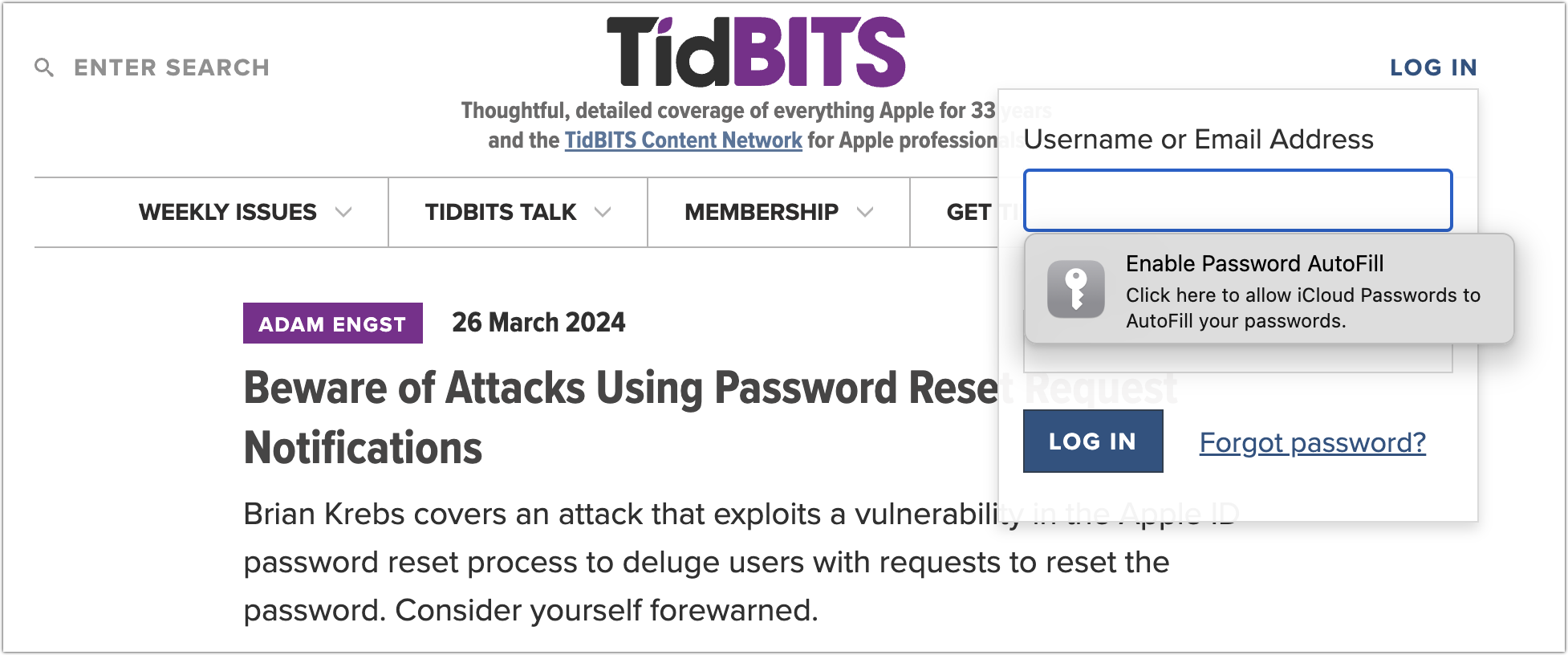
Since I use Safari 99% of the time and have simple needs for a password manager, keychain works very well for me. I also don’t use any non-Apple platforms or Chromium browsers.
My objection to 1Password is based on two principles I try to adhere to: I really don’t like subscription apps and like even less electron based apps, which I consider to be poor Mac citizens. Even though I have 36 GB of RAM on my M3 Pro, it irks me to use a lazily created app which uses electron and, to add insult to injury, needs a subscription fee (even if it is not large).
So far, these principles have not inhibited me in any way in my choice of apps I run on my Mac.
Thank you for yet another thoughtful and informative article.
Don’t beat around the bush, tell me what you really think.
While I agree with you, I would emphasize that what makes “using + and ••• to label menus” a capital crime is to have no hint appear when one hovers over the cryptic symbol.
The Keychain app has for years supported secure notes which offers a safe haven for that kind of information. However, it is true that it unfortunately does not sync to an iOS front-end even when users have iCloud Keychain turned on. So that makes it Mac-only which limits its usefulness I guess.
Of course Notes also offers secure notes and they can hold all kinds of information (including images, PDFs, etc.) and they sync very nicely across iCloud to other devices you have connected to your Apple ID.
I have yet to encounter a true need for a 3rd-party password manager. But then again, I do use Safari as my primary browser and I do not need any of my data to sync to a Windows box. With iCloud Keychain and secure notes I am all set. Especially now that I don’t even need a dedicated app for MFA anymore because iCloud Keychain has even that part covered these days.

For me the greatest limitation of Apple’s inbuilt password manager / keychain is that it is secured by your Mac password. This means that if you take your Mac in for repairs and the technician needs your computer password, they can access all your Keychain passwords as well. In many cases this can be prevented by setting up a separate administrator account, but most home users don’t know to do this and technicians rarely encourage it.
My customers with password managers have bigger issues with passwords than my customers just using keychain-password settings. I juse keychain because I would rather change a password than somehow “find” one and reuse. (this happens more often than expected) - How secure is Chrome/Firefox/etc password management ? You only know of security of these things in past tense. None of these managers resolve the bigger problem - when stuff is breached or a password is ‘uncoordinated’ - there is no AI crawler to remove breachs or faulted passwords. My wife’s online stock manager password system routinely locks you out forever if three attempts fail and then you have to contact a PERSON who then generates a new password request via snailmail. I have their system fail on my (with the correct password-so i imagine an acceptance glitch on their end creates this havoc) The availability of Password in a browser is inherently a security issue in itself. (small bias: don’t entirely feel anything from Alphabet is 'reliable" as to security - my old edict “The Google giveth - the Google taketh away” still stands.) I do trust Apple’s “values system” though.
I use to use 1 Password Application but switched to Enpass and have had no real problems with it on my Mac Studio running Sonoma. I have used it for over two years now and am wondering why you haven’t mentioned it yet? I also use it on my iPhone and Love the fact that is keeps everything updated on both my desk top computer and my iPhone. Is there some potential problem with this software that I am not aware of?
Respectfully yours
Timothy Freitas
Thanks - this is a great introduction to something I didn’t realize was built into Ventura; I had been using Keychain and the Password Manager built into Firefox. Since I find it loaded with the contents of Keychain, I now have a nicer interface to work with. I wish it worked with Firefox.
I did find one thing I consider a problem. All the passwords I checked were listed as last modified 11/28/21, which presumably was the date the password file was created. That unfortunately wiped out the earlier dates when the passwords were created, so I have lost any indication of how old the passwords were created. I often find I need that to pick out passwords that are obsolete because the web site has been redesigned and no longer uses that page.
Purely because I have no experience with Enpass and it doesn’t come up in discussions here as a common choice for password managers. I’ve never heard anything particularly bad about it, though.
As you can see, there are a LOT of options.
Have you tried the iCloud Passwords add-on I mention briefly in the article?
Thanks for your input.
BTW I have always respected TidBITS and trusted their reviews and advice.
Respectfully Yours
Timothy Freitas
I’m still on Ventura, and you said the add-on required Sonora. The last I have heard, Mail still has problems in Sonora, and I don’t want to risk Mail problems.
Ah, sorry, missed that fact. I suspect the iCloud Passwords extension and add-on leverage some new API in Sonoma, but I don’t know for sure.
Hey Adam, Thanks for the article.
My opinion: Apple is providing too little (or too much), too late.
Like you, I am perfectly happy with my 1Password app. Also, while you mention the Apple iClouds Passwords is “free”, this means no financial purchase is necessary. But the feature is not free, in terms of the effort of moving one’s entire set of passwords over to the Apple feature, which apparently would include a learning curve, as well.
Wishing you clear skies on 08 Apr 2024.
I stopped using Apples password manager and went to a app called StrongPassword.app. Strong Password. It has what I need, but eventually passcodes with take over as they have on Gmail
Hey Adam – In the Password Options paragraph, you wrote: “… I’m intrigued by the “Use passwords and passkeys from” section. iCloud Keychain is the only option here … Perhaps Apple will open up macOS to others in the future.”
Well Sonoma actually does have this:
I use Strongbox (by Phoebe Code Ltd.) on my Mac, iPad, and iPhone. The option shown in the screenshot allows me to use Strongbox to autofill on Safari. Plus Strongbox has extensions for Chrome and Firefox.
I believe you still have to have iCloud Keychain enabled as well (and Apple makes it a little clunky when adding new entries from a website). But the overall UX with Strongbox is quite nice.
Yup, essentially going to say this. Strongbox already has an extension, but it’s nice to have options. I don’t like Apple’s extension very much because it’s invasive (turns off Chrome’s autofill until you configure it otherwise, constant prompt for the verification code from the system) but otherwise it’s serviceable enough. Naturally the Safari experience is a great deal more luscious.
Interesting! I wonder what other password managers do this—1Password does not. Perhaps it’s a way that apps that haven’t already put effort into autofill can take advantage of Apple’s built-in code.
I think I’ve tried out several that supported it. I know KeePassium does because I just checked for other apps showing up there on my computer.
For those of you who are using Apple’s password manager and are looking for an easier way to access the password database without digging through Settings, here is a link to a video that shows how to make a password app using Shortcuts and put it right in your Dock.
Password app for iPhone and Mac
GREAT COMMENT THREAD!
I live in password hell as competing programs across devices snatch (autostore) and try to competitively Auto-fill in ways I cannot track.
Often get locked out as a consequence.
“Conflicts” between Windows, Edge, Firefox, 1Password, MacOs/Safari make changes and legacy password management a constant burden.
Note: there are 16+ “What’s my F___ing Password?!” log books for writing them down on Amazon alone.
Complexity without utility,
and the burden to elderly and impaired users “forced to go digital” is pernicious.
Do any of the current lised crop of password apps allow a local encrypted file which I manage myself?
(I’ve been using PasswordWallet since it first came out and have never had any problems with it. It appears to still be available. Is there something wrong with it?)
It still works as it always did…but in 2024 has some drawbacks.
-one man shop so not much support. He’s moved on mostly to other things IMO, hasn’t updated it in a long time, and shows no interest in adding features to make it relevant in 2024.
-features lacking compared to other products…see point above.
-sync between devices is cumbersome…always has been.
Despite that my wife still uses it and refuses to move to 1PW…which despite the flaws in v8 as compared to v7…is still the best player in this space. Unfortunately…their VC investors are now running the show and profit is their main motivator IMO…not service to users or features. They’ve shifted their focus to more enterprise customers at the expense of features that individual users want.
Thanks. I tried 1PW many years ago and did not like it. I’m old and don’t use many of the “new” features. I’ll stick with PW.
Thanks again.
I use Strongbox which, like all the KeePass-compatible apps, works just like that, operating on a local database file over which you have control and in whose care it is maintained, backed up and synced.
Of course, if PW is OK for you, you can keep using it. But though Strongbox doesn’t have quite the polish and flexibility of 1P, it is modern and maintained, supporting among other things the new passkeys. I’m not sure where KeePassium is nowadays but I understand that’s catching up as well.
Thank You. I will check it out.