TidBITS#1264/23-Mar-2015
Much noise has been made about the new 12-inch MacBook’s vulnerability to the BadUSB exploit, due to its reliance on the USB-C connector, but a deeper look reveals mostly hyperbole. Likewise, Rich Mogull debunks tales of Apple Pay “insecurity” that are actually related to bank processes. Julio Ojeda-Zapata tries out the new Force Touch trackpad and is impressed by the technology, though not enough to retire his mouse. Former Macworld editor Dan Moren joins us this week to review BusyContacts, a new power-user alternative to Apple’s Contacts app. Finally, we have the latest chapter of Joe Kissell’s “Take Control of Security for Mac Users” for TidBITS members, focusing on what you can do to increase the security of your iCloud account. Notable software releases this week include Safari 8.0.4, 7.1.4, and 6.2.4, Skype 7.6, Voila 3.8.3, Security Update 2015-003 (Yosemite), Typinator 6.5, Audio Hijack 3.0.3, and Nisus Writer Pro 2.1.
Macs Not Vulnerable to BadUSB Attack
“The new MacBook’s single port comes with a major security risk,” proclaims The Verge. Gizmodo took The Verge’s story a step further with, “The NSA Is Going to Love These USB-C Charging Cables.” So what’s the big deal, and is there any fire behind all this hot air?
These articles are pure clickbait. The main exploit in question, called BadUSB, was discovered 8 months ago. In theory, it could be used to attack most USB devices, including Macs, iPads, Windows PCs, and more. But making it seem like the new 12-inch MacBook, and to a lesser degree, Google’s new Chromebook Pixel, has some sort of new vulnerability because of using USB-C is disingenuous at best.
What is BadUSB? It’s a type of attack that overwrites the USB controller on a device — say a USB thumb drive — with malicious code. That compromised device can then attack anything it plugs into by injecting malware, entering keystrokes, or anything else a USB device can do. To work, BadUSB needs to be able to flash the firmware on the target USB device.
Gizmodo seems to believe the 12-inch MacBook is vulnerable to this direct attack, even going so far as to suggest that the NSA will distribute hacked USB-C power adapters designed to take over your notebook. But unlike Thunderstrike on vulnerable Macs (see “Thunderstrike Proof-of-Concept Attack Serious, but Limited,” 9 January 2015), the USB port uses Intel’s xHCI (eXtensible Host Controller Interface), which can’t be placed into a DFU (device firmware upgrade) mode to overwrite the MacBook’s firmware. Thus the MacBook itself can’t be infected with BadUSB, so plugging in an unknown power adapter can’t give someone control of your MacBook.
There are other attack vectors, but none are a serious concern. For instance, USB-C supports direct memory access (DMA), which has been used in the past to attack computers since it allows any connected device direct access to the computer’s memory. An attacker could theoretically use a DMA attack to read memory or overwrite memory locations with his own code. However, Macs now use Intel’s VT-d, which virtualizes the memory DMA devices can access, restricts them to known memory locations, and prevents a DMA attack from overwriting executable memory
and triggering an exploit.
Another vector would be for a BadUSB-controlled device to install malware on the connected computer. But Macs don’t execute files on remote storage automatically, so the user would have to be tricked into launching an app from an unexpectedly mounted drive. That could happen, but seems relatively unlikely.
Lastly, a BadUSB-controlled device could execute keystrokes on a Mac. But this is useful only if the Mac is running, screen unlocked, and the user doesn’t notice or interfere with the string of keystrokes to do something bad. Again, this attack doesn’t seem likely.
We could be missing something, but it looks like The Verge and Gizmodo have it wrong, and USB-C represents no new risk to Macs. The NSA will have to think of something less silly than leaving infected USB-C power adapters throughout the nation’s coffee shops.
Chapter 9 of “Take Control of Security for Mac Users” Available
When it comes to Mac security, Apple’s iCloud online service merits your attention. That’s not because Apple has done a bad job of securing iCloud, but because iCloud is heavily used and stores a vast amount of personal data, rendering it attractive to attackers. So in Chapter 9, “Manage iCloud Security,” this week’s installment from “Take Control of Security for Mac Users,” Joe Kissell helps you understand Apple’s security policies, see where iCloud is more and less secure, and shows you how to increase your overall security level.
In particular, Joe walks you through turning on two-step verification, which protects your account even if your password is compromised, and then looks at which iCloud services you might want to avoid — and why — if you’re particularly concerned about security. Those who turn on two-step verification will also learn how to generate the app-specific passwords that are necessary for third-party apps that rely on iCloud, such as BusyCal and BusyContacts, Outlook, Thunderbird, and so on.
If you’re just getting started with “Take Control of Security for Mac Users” now, the first two chapticles are available to everyone, but all subsequent ones are limited to TidBITS members. Those who join the TidBITS membership program receive other benefits too (like discounts off top Mac software!), but what’s most important is that revenues contributed by TidBITS members have kept TidBITS running the last few years — your support has made all the difference. If you’re already a TidBITS member, log in to the TidBITS site using the email address from which you joined to read and comment on these chapters.
- Chapter 1: “Introducing Mac Security”
- Chapter 2: “Learn Security Basics”
-
Chapter 3: “Perform Quick Security Fixes”
-
Chapter 4: “Beef Up Your Security Settings”
-
Chapter 5: “Improve Your Passwords”
-
Chapter 6: “Improve Your Network Security”
-
Chapter 7: “Fortify Your Mac’s Defenses”
-
Chapter 8: “Surf the Web Safely”
-
Chapter 9: “Manage iCloud Security”
We have three more chapters to go, and once we’ve published those in TidBITS, the full ebook of “Take Control of Security for Mac Users” will be available for purchase by everyone in PDF, EPUB, and Mobipocket (Kindle) formats.
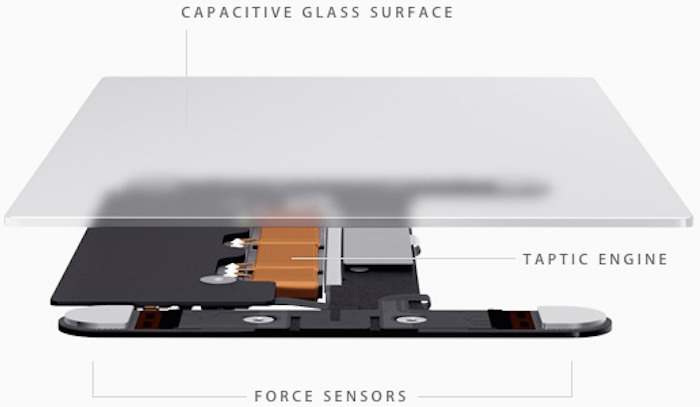
Force Touch Trackpad Makes MacBooks More Compelling
I’ve always been conflicted about Apple’s trackpads. I admire their comfort and precision, but I’m just more effective with a mouse. I’m also overwhelmed by all the trackpad features — I can never remember all the multi-finger taps and gestures, much less put them to practical use. So when Apple announced the Force Touch trackpad, with yet more input options, I was skeptical.
The Force Touch trackpad is currently exclusive to the just-refreshed 13-inch MacBook Pro with Retina display. It will also be found on the new 12-inch MacBook, due early next month (see “New 12-inch MacBook Joins Updated MacBook Air and MacBook Pro,” 9 March 2015). I’ve been using it on a 13-inch MacBook Pro with Retina display for a few days.
“Force Touch,” which sounds like a kung fu fighting move, refers to new capabilities that simulate the sensation of a mechanical click even though the trackpad surface scarcely moves at all. Instead, the trackpad uses sensors to detect finger presses and responds with haptic vibrations.
This is almost indistinguishable from a physical click and is likely to fool anyone who is unaware there is a new trackpad. I had to watch my finger clicking on the new trackpad to be certain I wasn’t using an old Apple trackpad with traditional mechanical movement.
TechCrunch’s Matthew Panzarino does a good job of explaining the trackpad technology:
There is a set of vibrating motors underneath that provides “force feedback,” also known as haptics in some applications. This feedback fools your finger into believing that you’ve pressed down on a hinged button, the way your current trackpad works. This feedback relies on phenomenon called lateral force fields (LFFs), which can cause humans to experience vibrations as haptic “textures.” This can give you the feel of a “clickable” surface or even depth. The Force Touch feature of the new trackpad allows you to press “deeper,” giving you additional levels of tapping feedback. The effect is done so well that you actually feel like you’re pressing down deeper into a trackpad that still isn’t moving at all. It’s
so good it’s eerie.
Force Touch is more than a parlor trick. It brings with it new capabilities. In addition to the standard simulated clicking, you can press down a bit more firmly to “force-click.” When you do so, you feel not one but two distinct clicks. And depending on where your cursor is pointing when you do this, different things happen.
Apple has a long list of capabilities on its site, but key examples include force-clicking a file icon to see a Quick Look preview, a point on a map to put a pin in a location, a reminder or event to see the details inspector, a link in Safari or Mail to see an inline Web preview, and text in a Web page or a Mail message to conjure up a window with relevant dictionary or Wikipedia information. It’s unclear exactly how Apple chose these actions, or how they differ conceptually from Control/right-click actions.
Increasing finger pressure on the trackpad makes video in QuickTime Player and iMovie fast-forward and rewind more quickly, and accelerate zooming in the Maps app. You also feel haptic feedback when aligning annotations in a PDF, dragging an iMovie clip to its maximum length, and snapping an iMovie title into place, among other actions.
Eventually, third-party developers will be able to tap the trackpad’s new capabilities to, for instance, add pressure sensitivity to drawing applications. Such a feature is already present in Apple’s Preview app, which lets you vary the thickness of a line you’re drawing based on how hard you press the trackpad while doing so. This also works when marking up a Mail attachment.
On a more basic level, the new Force Touch trackpad replicates familiar features found on the mechanical trackpad, such as dragging a file with thumb and forefinger. It feels a bit better to do this with the Force Touch trackpad because click pressure can be adjusted from “light” to “firm” in the Trackpad pane of System Preferences, something that wasn’t an option with mechanical clicking. I prefer “medium” pressure.
The Force Touch trackpad retains older capabilities. Tapping lightly with two fingers is still an equivalent of a mouse right-button click. Also present is the one-finger “tap to click” feature that some other Mac users dislike; I’ve long loved it. All the other gestures for dragging, zooming, rotating, and the like are there as well; I’ve just never found them compelling enough to integrate them into my fingers.
I wonder if I’ll come to regard Force Touch as indispensable, or pointless. I can’t answer that with just a few days of use, but I am leaning towards the middle ground of liking, but not needing, the new capabilities.
For example, I typically use Quick Look by selecting a file or folder and then pressing the Space bar. I could force-click the file instead, but is that easier or more convenient? A little bit, maybe.
Going down the list of Force Touch actions, none make me want to cry out, “Wow, I’m glad I can now do that.” But as these become ingrained in the Mac landscape, it’s entirely possible I’ll embrace some of them. They’re not game-changing, but they certainly are cool and fun.
In other words, the Force Touch trackpad alone is no reason to rush out and buy a new MacBook. But the new features are more evidence that Apple leads the way in trackpad design. I expect PC notebook makers to mimic Force Touch capabilities in short order.
Execution is everything, and the Force Touch trackpad has been implemented impeccably as far as I’ve seen so far. It just works, and is a welcome addition to the MacBook line. I hope Apple makes it possible for desktop Mac users to join the Force Touch party too, with an updated Magic Trackpad.
Excellent though it is, I’m still a mouse guy. That said, if key Mac apps start providing interesting Force Touch feedback capabilities that go beyond Apple’s basics, I may have to reconsider.
BusyContacts Turbo Charges Mac Contact Management
Contact management is not generally an area so exciting that you need to have smelling salts handy, but even I, with my modest needs, admit that Apple’s own solution, the Contacts apps in iOS and OS X, falls short in places. Fortunately, the folks at BusyMac, not content with creating their own Calendar replacement in the form of the excellent BusyCal, have now moved on to tackle the contacts part of the equation with the $49.99 BusyContacts.
You may not need everything BusyContacts can do, because it’s a lot. But if you’ve felt limited by Apple’s Contacts (or just hate its interface, as TidBITS publisher Adam Engst does), BusyContacts might fill some of the gaps you’ve encountered. In particular, if you need to share contacts among a group of people, say, in a small business, or if you need to log and manage your interactions with people, then BusyContacts is likely what you’re looking for.
I don’t need to avail myself of every feature BusyContacts has to offer, but there are enough niceties and improvements over Apple’s Contacts that I’ve pondered whether I might be better off switching.
Fortunately, it’s not an irreversible, or even a mutually exclusive, decision. BusyContacts essentially piggybacks on OS X’s built-in contact database, so you don’t need to do anything other than authorize it to slurp up your existing contacts. And any changes made in BusyContacts are reflected in Apple’s Contacts (assuming there’s an analogous field).
But BusyContacts also goes beyond integration with Apple’s own internal contacts. As with the built-in Contacts app, you can also grab data from services like Google, Yahoo, and Office 365, as well as any Exchange or CardDAV server. Plus, as this is the era of social networking, it can also download your contacts from Twitter, Facebook, and LinkedIn, if you so desire.
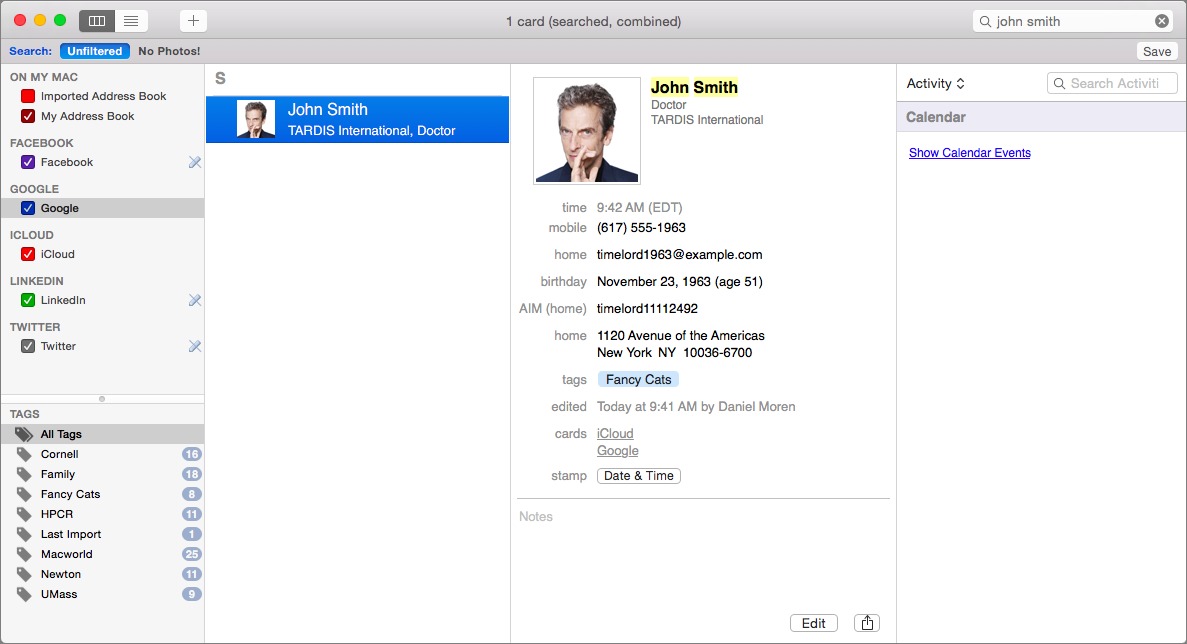
Seeing contacts from all of those different services can be confusing, though like Apple’s Contacts, BusyContacts lets you link cards on different services that belong to the same person. So, for example, rather than seeing separate entries (top screenshot) for John Smith from Facebook and John Smith from your Google Contacts, you instead see a combined version (bottom screenshot) that shows the contact details for both. (Linked contact details are not permanently merged, though if you want to do that, it’s possible too.)
I particularly appreciate that BusyContacts lets you color-code those various accounts, so you can quickly see at a glance which account the information comes from. That carries over to an even more granular level: when you edit a card, icons next to the various entries tell you
if the data comes from a social networking service and, if so, which one.
It’s a bit odd to integrate Twitter into my contacts, in part because not everybody I follow on Twitter is someone I actually know. It’s surreal when scrolling to find celebrities like Nathan Fillion and Neil Gaiman sitting next to my mom and my former boss.
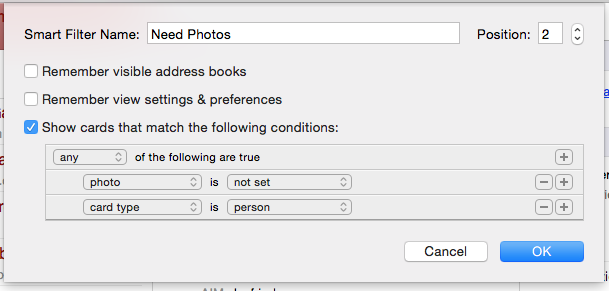
That’s one place where BusyContacts’ useful filtering and tagging tools come in. Tags work essentially like groups in Apple’s Contacts, whereas filters are the equivalent of Smart Groups, letting you specify a set of criteria and then quickly view just the contacts that match them. But BusyContacts’ filters are far more powerful: for one thing, Apple only lets you create Smart Groups where a card matches a single criterion. BusyContacts supports multiple conditions, and you can see cards that match any, all, or none of them. It also lets you match on factors that Contacts doesn’t, so, for example, I can
filter to see just those contacts that don’t have an associated picture.
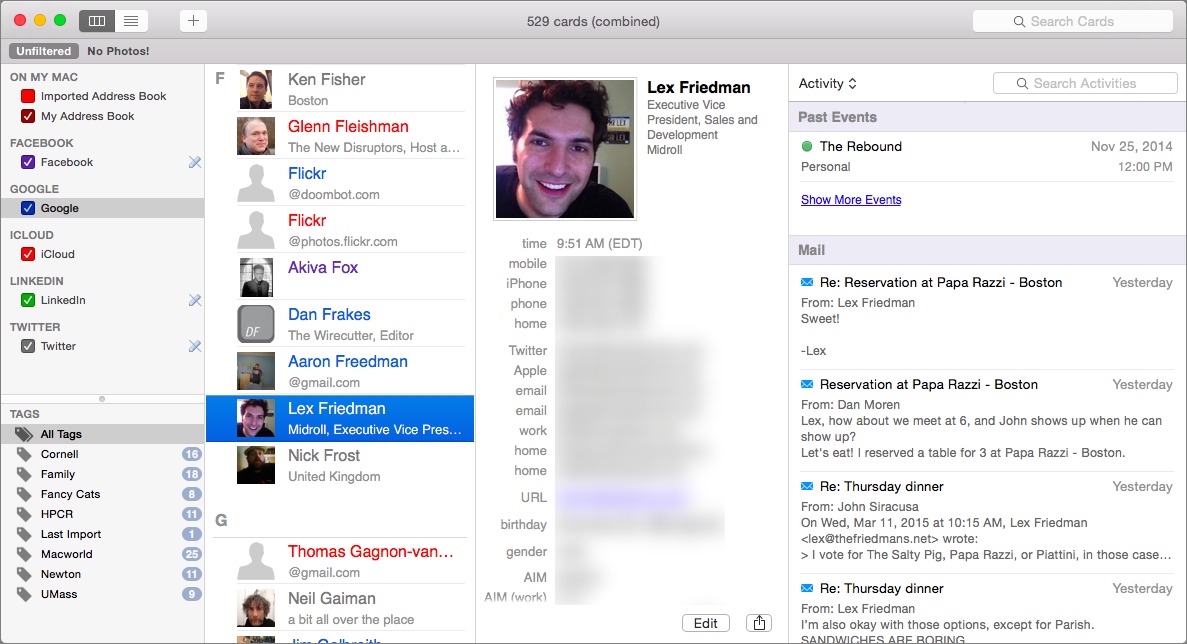
Another of BusyContacts’ standout features is the Activity List. It links to other apps and services to give you an overview of your interactions with the selected contact, showing you related info from calendar events, email messages, Twitter and Facebook updates, and Messages. That makes it easy to search through that correspondence and remind yourself where you’re having dinner tomorrow night, or the last time you corresponded with someone.
There are a couple of limitations to that list, though. For one thing, you can’t reorganize it, say, by moving calendar events down and Messages up. For another, BusyContacts pulls event info only from BusyCal, not from Apple’s own Calendar database (and you need to remember to associate contacts with events in BusyCal); BusyCal needs to be open, too — otherwise, you just see a “Show Calendar Events” hyperlink that, when clicked, opens BusyCal.
I found a few other peculiarities while testing BusyContacts. For example, you can add a handy “local time” field to contact records, which reminds you before you call your cousin in London that it may be the middle of the night there. But to do so, BusyContacts does a reverse lookup on the area code of the first phone number listed in her record. I have a decent number of friends who have kept their cell phone numbers from college or a previous job, and they can often be time zones away from where they now live.
I also wish I could easily rearrange the information in BusyContacts’ contact records. Reordering phone numbers requires a frustrating copy-and-paste dance; it’d be great if, in that aforementioned example with the area codes, I could simply drag my friend’s home phone number to the top of the list.
Finally, sharing. While BusyContacts makes it possible to share an address book between multiple users (say, you and your spouse), it has to work around the limitations of the services themselves. For Google and iCloud, for example, you need to have both people log into their accounts on any machine using BusyContacts. Sharing over your local network works, but is limited to local address books, which cannot be synced with an iPhone.
That brings up another frustration for me, as someone who uses multiple Macs: BusyContacts worked fine once I got it set up on both my MacBook and my iMac, but the setup is a bit of a pain, since I had to log in to each of my accounts on both machines. It would be nice to have a way to expedite the login process for a second Mac.
And, of course, getting the benefits of BusyContacts on your iOS device is also a bit of a pain, due to the limitations of Apple’s mobile platform. There’s no way to easily “sync” your entire BusyContacts database to your iPhone or iPad without merging all of your contacts into one of your existing syncing accounts (like iCloud, Google, or Exchange) — which may have unintended consequences — or by using a service like Fruux to handle all of your syncing needs. Honestly, what’s really needed is a version of BusyContacts for iOS to let iOS users take advantage of all the features the Mac version provides.
So, is BusyContacts right for you? It depends on how intensively you use your contacts list. If you’re in a line of work where it’s important to log all your conversations with people, BusyContacts is a definite step up from Apple’s own offerings. And if you’re already a BusyCal user, BusyContacts will no doubt earn its spot in your heart with ease, especially given the synergy between the two. Much as BusyCal cemented its place as the pro version of Apple’s Calendar, BusyContacts makes a similar play as the pro version of Contacts.
New copies of BusyContacts 1.0 cost $49.99 direct from BusyMac or via the Mac App Store, but upgrades, volume discounts, and special offers are available only directly from BusyMac. For instance, BusyCal owners can sidegrade for $29.99, additional licenses can be added at a discount, staff and students at educational institutions can save 20 percent, and BusyContacts and BusyCal can be purchased in a bundle for $79.98.
Apple Pay Exposes Insecure Bank Policies
On 2 March 2015, The Guardian reported that Apple Pay suffered from unusually high rates of credit card fraud. The Guardian’s report seems to be based on a February blog post by Cherian Abraham, and I was initially skeptical of both. But contacts with deeper ties to the financial services industry quickly verified there was increased fraud… and no shortage of finger pointing.
This is a fascinating issue for two seemingly contradictory reasons. Apple Pay is one of the most secure payment methods in the United States, if not the most secure method, yet its very existence highlights massive weaknesses in the payment system. Let’s explore why and how some lesser known features of Apple Pay could dramatically reduce fraud, if more banks enabled them.
Credit cards in the United States are different from those in nearly every other country. In the U.S. we have what’s known as zero liability. Under federal law, credit card holders are liable for only $50 of fraudulent purchases, while debit card users are liable for only up to $500. But most banks offer greater protection than what’s legally required. If someone uses your card (or card number) fraudulently, assuming you notice it within a generous time period, you aren’t held liable for the fraud. Instead, the merchant and payment processor who handled the transaction pay the costs of the fraud (nearly always the
merchant). So if someone steals your card number, uses it to buy something online, and you notice it within a couple of months, you reverse the charge and the online retailer pays the costs.
The same is also true if the card company (Visa, MasterCard, American Express, etc.) or the issuing bank catches the fraud with their internal systems, at least if the transaction wasn’t stopped at the point of sale. Those fraud-detection systems have managed to keep fraud rates at near-historic lows despite massive breaches, but based on discussions I’ve had with some executives in the industry, the rates have been growing for the first time in over a decade.
This is the exact opposite of most other countries where the cardholder is responsible for the fraud. Few other countries have guaranteed zero liability, although many banks do offer fraud protection as an enticement to use their cards. This is one of the main reasons most other countries use more advanced credit card security technologies, including card-based Chip and PIN systems and mobile payments. Meanwhile, the United States continues to rely on simple magnetic-stripe signature cards, which are incredibly easy to counterfeit. When consumers carry greater liability, security becomes an essential selling point.
I am of course simplifying the issue. There are actually multiple different kinds of payment transactions, each with different requirements for processing. A Chip and PIN card isn’t necessarily any more secure for an online purchase (“cardholder not present” in industry terms) than a magnetic stripe card and most U.S. Chip and PIN cards also have magnetic stripes as well. The systems account for that with different validation requirements, payment limits, fraud analysis, and transaction fees. That’s why when you buy online you typically have to provide your billing address and the CVV (card verification value) number printed on your card, which aren’t stored on the magnetic stripe or in the payment chip. This, ideally, proves
you have the card in hand and know information otherwise not available if someone skimmed the card.
From Target to Apple Pay — Apple Pay is incredibly secure because it never stores or uses your actual credit card information. Instead, when you register your card, a disposable token is sent to your iPhone or (soon) Apple Watch, and stored inside the same super-secure Secure Element chip used by other mobile payments and some cards. After that, there’s little exposure for a stored credit card. Even if someone steals your iPhone, your bank can cut off the token without having to send you an entirely new credit card (see “Apple Pay Aims to Disrupt Payment Industry,” 9 September 2014).
The weak link, it turns out, is the process of registering your card with Apple Pay (“onboarding” in industry terms). Apple built a framework, not a new payment system, and Apple only mediates the connection between your iPhone and your bank. Your bank is supposed to validate that you are who you say you are, based on the Apple Pay registration process.
When you enter your card information, Apple encrypts it, sends it to an Apple server, figures out your credit card company (based on the card number), re-encrypts the data, and finally sends it to your bank for verification. As documented on Apple’s Support site and detailed in the iOS Security Guide, Apple also provides other information to your bank. Here’s an excerpt from the iOS Security Guide describing the process:
Additionally, as part of the Link and Provision process, Apple shares information from the device with the issuing bank or network, like the last four digits of the phone number, the device name, and the latitude and longitude of the device at the time of provisioning, rounded to whole numbers. Using this information, the issuing bank will determine whether to approve adding the card to Apple Pay.
Your bank can immediately approve your card for Apple Pay or decide it needs additional verification, such as sending an email or text message to an address on file. The onboarding decision is completely controlled by the bank, but it’s a new process that has never been previously tested at scale here in the United States.
Credit card theft is rampant, with tens of millions of card numbers exposed over the past couple of years. In many cases, the lost information is never used for a fraudulent transaction. Stolen credit card numbers are sold all over the Internet, with higher prices for cards with more-extensive information, like the address and the CVV number (usually stolen from merchant databases or skimming transactions, even when they aren’t supposed to be stored). Thus the banks always gamble a bit after the big security breaches. They weigh the cost of replacing cards (the printing and mailing costs, the costs of losing a customer, and the inconvenience of re-registering cards for recurring transactions) versus the chance of fraud.
Banks are responsible for determining the rules of their registration process. Some are strict, others less so, and some, it seems, didn’t plan well for handling onboarding fraud. This is similar to the same problems Apple suffers with iCloud account takeovers (see “You Are Apple’s Greatest Security Challenge,” 14 October 2014). Knowing someone is who they say they are is hard enough in person, much less over the Internet.
The entire core of the claims of fraud surrounding Apple Pay comes down to the onboarding process and all those stolen cards. The bad guys don’t need to print up fake cards; they just need to get enough information to register the fake cards with Apple Pay. Some banks are more at risk than others, based on how well they set up their onboarding process. Since Apple Pay is a more secure and trusted form of payment, once a fake card is in the system, the actual fraud is easier to carry out.
This situation was entirely predictable; even the most rudimentary threat modeling exercise would have highlighted the potential problem and solutions. And clearly the direct fault lies with the banks for leaving all those stolen cards active, and for making mistakes with the Apple Pay registration process.
However, some in the payments world claim they were “railroaded” by Apple; rushing to get their banks enrolled without being able to implement additional security controls. There is bitterness among the banks, justified or not. But it wouldn’t surprise me if it was the bank’s executives pushing their internal departments to jump on Apple Pay before they had the onboarding processes fully under control.
In short, Apple Pay’s security, speed, and convenience became a stress test for the banks that could expose otherwise manageable weaknesses in their processes and decisions.
A Temporary Situation — Apple is already trying to work with banks to see how they can improve the process and reduce fraud. Not all banks suffer the same rates of fraud, so the problems are clearly avoidable. It likely won’t take much longer for all banks to tighten the screws and reduce fake registrations to a manageable level.
But banks could also turn on additional features to not only prevent stolen credit cards from being registered with Apple Pay, but also reduce credit card fraud overall. I currently have three cards registered with Apple Pay, but my American Express card stands out. Whenever I make a payment, American Express sends me a push notification. This occurs nearly instantly, making it impossible for someone to charge my card without me immediately knowing about it. These notifications occur for all transactions, not just those mediated through Apple Pay.
Although the bad guys have a window of opportunity now, it likely won’t last for long. Banks will tighten up their registration processes, Apple Pay will reduce card and card number theft, and more banks will enable push notifications for every transaction. The end result will be lower fraud rates across the board.
TidBITS Watchlist: Notable Software Updates for 23 March 2015
Safari 8.0.4, 7.1.4, and 6.2.4 — Apple has released Safari 8.0.4 for OS X 10.10 Yosemite, along with Safari 7.1.4 for 10.9 Mavericks and Safari 6.2.4 for 10.8 Mountain Lion with a collection of WebKit-related security patches. All three releases include fixes for 16 instances of a vulnerability associated with memory corruption issues that could lead to unexpected application termination or arbitrary code execution (for specific CVE IDs, see the security content notes at Apple Support). The updates also fix a user interface inconsistency that could allow an attacker to misrepresent a URL in a phishing scheme. All
three versions of Safari are available from Software Update. (Free)
Read/post comments about Safari 8.0.4, 7.1.4, and 6.2.4.
Skype 7.6 — Microsoft has released Skype 7.5, which significantly reduces CPU consumption from animated emoticons. The Internet telephony and messaging app also reduces the instances of App Nap preventing Skype from reconnecting, fixes a bug that caused the input field to disappear occasionally, fixes an issue that caused the screen to flicker when a Screen Sharing window is off screen, and adds support for 14 new languages (Hindi, Turkish, Czech, Ukrainian, Greek, Hungarian, Romanian, Indonesian, Catalan, Croatian, Slovak, Vietnamese, Thai, and Malay). Additionally, the release notes state that
Skype 7.5 requires OS X 10.9 Mavericks or later, despite the download page claiming “All you need to get started is Mac OS X 10.5.8 or above.” We accidentally failed to publish this piece when it was first written, and Microsoft has now released Skype 7.6, reducing chat memory usage and increasing the maximum height of the chat input field. (Free, 36.9 MB, release notes for 7.5 and 7.6, 10.9+)
Read/post comments about Skype 7.6.
Voila 3.8.3 — Global Delight has released Voila 3.8.3 with support for 64-bit processors, which should improve the screen capture utility’s overall performance and efficiency. The update also manages memory usage better, sends a full image to Skype (instead of just a link), fixes several bugs related to recording system audio, improves the OS X 10.10 Yosemite menu bar and dark mode, and improves recording on the Mac Pro. ($29.99 new from Global Delight with a 25 percent discount for TidBITS members or from the Mac App Store, free update, 30.2 MB, 10.8+)
Read/post comments about Voila 3.8.3.
Security Update 2015-003 (Yosemite) — Apple has issued Security Update 2015-003 for OS X 10.10 Yosemite, the second security update released this month (see “Security Update 2015-002 (Mountain Lion, Mavericks, and Yosemite),” 10 March 2015). Available solely for 10.10.2 Yosemite, this release takes another swing at fixing two vulnerabilities that were originally part of Security Update 2015-002 — improving iCloud Keychain’s bounds checking and IOSurface’s handling of serialized objects (both to prevent execution of arbitrary code). Once again, there are two
updates available: one for Early 2015 Macs (see “New 12-inch MacBook Joins Updated MacBook Air and MacBook Pro,” 9 March 2015) and another for older Macs. (Free. For 10.10.2 Yosemite, 5.3 MB; and for Yosemite on Early 2015 Macs, 4.9 MB)
Read/post comments about Security Update 2015-003 (Yosemite).
Typinator 6.5 — Ergonis has released Typinator 6.5 with new options to help control OS X’s system-wide “smart substitutions” that could lead to problems with expansions that require regular quote characters (but not smart quotes). Typinator 6.5 turns off smart substitutions by default, but they can be enabled by right-clicking within an expansion field and choosing an option from the Substitutions submenu. Speaking of quotes, Typinator 6.5 now supports French quoting style (with double angle quotation marks and non-breaking spaces) for nested abbreviations. The update also no longer displays the “must not
be empty” message immediately after creating a new item, works around a crash when expanding text in OS X 10.10 Yosemite’s sharing window with the “quick expansion” option enabled, fixes a bug related to cursor positioning in apps created by Fluid, and reduces the amount of logging in case of certain events. (€24.99 new with a 25 percent discount for TidBITS members, 6.9 MB, release notes, 10.6.8+)
Read/post comments about Typinator 6.5.
Audio Hijack 3.0.3 — Rogue Amoeba has released Audio Hijack 3.0.3 with a major reduction in overall latency for the audio recording utility. Additionally, improvements have been made to keep latency from growing. Audio Hijack was also hit by a bug associated with the switch over to Daylight Saving Time, and version 3.0.3 corrects this to ensure timers work correctly on all days of the year. The update also improves finalization of AAC and ALAC recordings (such as correctly naming split files), adds Delete Recording and Delete Timer buttons to the Recordings and Schedule tabs, ensures that multiple selection of items
in the Recordings and Schedule tabs works as expected, and makes a variety of interface improvements. ($49 new with a 20 percent discount for TidBITS members, free update for version 3.0 licenses, $25 upgrade from older versions, 14.3 MB, release notes, 10.9+)
Read/post comments about Audio Hijack 3.0.3.
Nisus Writer Pro 2.1 — Nisus Software has released Nisus Writer Pro 2.1 with added support for OS X’s Auto Save and Versions. The word processor now saves changes to all open documents automatically using OS X’s approach instead of its own, enabling you to browse and revert to older versions of any document. The update also switches Nisus Writer Pro to 64-bit, adds support for iCloud, integrates the previously separate Nisus Thesaurus, adds the Edit > Repeat command for repeating the last used menu or palette command, adds the capability to insert a cross-reference that shows the name of the target bookmark, and makes a number of
macro enhancements (for a general feature list, see “Nisus Writer Pro 2.0: The Review,” 8 June 2011). Highlights from the lengthy list of bug fixes include a cure for a potential hang when opening documents with a certain combination of inline images, prevention of some possible crashes related to text layout, and improved behavior when the Apple text engine encounters certain kinds of bugs. Note that Nisus Writer Pro 2.1 is now sandboxed, which may require granting it some additional permissions for accessing macro files or locations outside the app’s own sandbox space. System requirements now specify Mac OS X 10.7.5 Lion or later, though Nisus Writer Pro 2.0.2 remains available for those running 10.4 Tiger through 10.6 Snow Leopard. ($79 new, free update, 188 MB, release notes, 10.7.5+)
Read/post comments about Nisus Writer Pro 2.1.
ExtraBITS for 23 March 2015
In our latest roundup of links, Tim Cook opens up about Steve Jobs and the Apple Watch, modern Photoshop experts try to use Photoshop 1.0, and Managing Editor Josh Centers makes an appearance on the Subjective podcast.
Tim Cook on Jobs’s Legacy and the Apple Watch — In an interview with Fast Company, Apple CEO Tim Cook took questions about the legacy of Steve Jobs, the Apple Watch, and Apple’s future. Cook defended the Apple Watch by comparing it to the original iPod, whose critics questioned its purpose and price. As for those who worry that Apple is changing, Cook points out that the company also changed under Jobs, who Cook described as “the best flipper in the world.” But he said that Apple’s core values will never change.
Photoshop Experts Try Photoshop 1.0 — To celebrate the 25th anniversary of Photoshop, CreativeLive asked eight Photoshop experts to try to complete a project in Photoshop 1.0. The video is funny, and it shows how far photo editing (and computing) has evolved over the past quarter-century.
Josh Centers Discusses Apple’s Announcements on the Subjective Podcast — Managing Editor Josh Centers joined host Victor Johnson on the Subjective podcast to discuss his TidBITS origins, HBO Now, Apple TV, Apple Watch, and his frustrations with the Mac lineup.