TidBITS#1267/06-Apr-2015
Settle in for a practical, privacy-focused issue of TidBITS! Josh Centers brings us two how-tos on maintaining your privacy, explaining how to opt out of Verizon Wireless’s “supercookie” and how to make your Twitter history vanish before an ill-considered tweet comes back to haunt you. Then, for TidBITS members, we have the penultimate chapter of Joe Kissell’s “Take Control of Security for Mac Users,” in which Joe explains OS X’s privacy settings. Outside of the privacy realm, Michael Cohen compares the latest Steve Jobs biography, “Becoming Steve Jobs,” to the Jobs-authorized “Steve Jobs.” Julio Ojeda-Zapata joins us again this week to examine Bushel, a device-management service for small businesses. Last but not least, you can get an early look at the forthcoming Photos for Mac with Jason Snell’s ebook, “Photos for Mac: A Take Control Crash Course.” Notable software releases this week include Evernote 6.0.8, iFlicks 2.2, Fantastical 2.0.2, TweetDeck 3.9.482, LaunchBar 6.2, and ChronoSync 4.6 and ChronoAgent 1.5.1.
Get an Early Look with “Photos for Mac: A Take Control Crash Course”
The ten-month limbo Apple left us in after announcing that the forthcoming Photos for Mac would replace both iPhoto and Aperture is nearly over. Photos has finally showed its face in OS X 10.10.3 Yosemite, now in public beta, and we expect it to be released within weeks. But should you trust your irreplaceable photo library to Photos right away? And what capabilities might you lose if you do? We have some early answers in our new “Photos for Mac: A Take Control Crash Course,” penned by Jason Snell, formerly lead editor of Macworld and now at Six Colors.
Based on the public beta, this early-bird version of “Photos for Mac: A Take Control Crash Course” helps you start thinking about making the transition and offers advice to anyone who is already running the beta or who plans to switch once Photos 1.0 ships. Right now, the tightly packed 30-page book assists you with:
- Deciding whether to transition to Photos right away
- Importing iPhoto and Aperture photo libraries
- Getting around in the Photos interface
- Keywording, favoriting, organizing, and finding photos
- Dealing with Photos quirks
Once Photos 1.0 ships and we’ve had time to test it thoroughly and extract its secrets, we’ll release a free update — probably in May — that will more than double the size of the book. Topics it will add include:
- Using iCloud Photo Library
- Editing photos
- Sharing photos with other people
- Viewing photos on an Apple TV
- Having prints made
- Creating projects, such as calendars and cards
- …and much more!
Like our other Crash Courses, this book has concise chunks of content so you can read quickly, all wrapped up in a modern, magazine-like layout in PDF that morphs to a reflowable design for EPUB and Mobipocket. Each chapter ends with discussion and sharing buttons, making it easy to ask a question (and please do ask questions that you want to see answered in the 1.1 update!) or share a chapter with Facebook friends, Twitter followers, and others.
Chapter 11 of “Take Control of Security for Mac Users” Available
The line between security and privacy is fuzzy at best, and the two are inextricably linked. Improving your Mac’s security will often increase your privacy, and keeping certain types of data private is an essential step in maintaining security. So, in Chapter 11, “Keep Personal Data Private,” of “Take Control of Security for Mac Users,” Joe Kissell focuses on the implications of sharing a Mac with other people, the privacy risks you face when using the Internet, and how you can keep your communications private. Finally, he provides an overview of OS X’s main privacy-related settings.
If you’re just now getting started with “Take Control of Security for Mac Users,” note that the first two chapticles are available to everyone, but the rest are limited to TidBITS members. Those generous folks receive other benefits too (like a full-text version of our RSS feed!), but what’s most important is that TidBITS members are the reason you’re reading TidBITS today — we wouldn’t still be publishing without their support. If you’re already a TidBITS member, log in to the TidBITS site using the email address from which you joined to read and comment on these chapters.
- Chapter 1: “Introducing Mac Security”
- Chapter 2: “Learn Security Basics”
-
Chapter 3: “Perform Quick Security Fixes”
-
Chapter 4: “Beef Up Your Security Settings”
-
Chapter 5: “Improve Your Passwords”
-
Chapter 6: “Improve Your Network Security”
-
Chapter 7: “Fortify Your Mac’s Defenses”
-
Chapter 8: “Surf the Web Safely”
-
Chapter 9: “Manage iCloud Security”
-
Chapter 10: “Prevent Data Loss and Theft”
-
Chapter 11: “Keep Personal Data Private”
This is the penultimate chapter, so once we get the next chapter out and take our final edit pass, the full ebook of “Take Control of Security for Mac Users” will be available for purchase by everyone in PDF, EPUB, and Mobipocket (Kindle) formats.
How to Say “No Thanks” to Verizon’s Supercookie
Much virtual ink has been spilled discussing Verizon Wireless’s so-called “supercookie.” While it may sound delicious, it’s actually a threat to your privacy, and Verizon customers can finally opt out of it.
You’re probably familiar with standard Web cookies, which are small pieces of data stored by your browser to retain information. Cookies are mostly used to make Web sites work better, such as by keeping you logged in to a Web site across launches or maintaining the contents of an online cart as you shop. However, cookies can also can be used for less constructive purposes, such as tracking your online activity in order to serve you targeted ads. You may not like everything cookies are used for, but they’re hard to live without. Most Web browsers help you block “third-party cookies” (such as those used by ad networks), and browser plug-ins such as Disconnect can block even more unwanted
cookies while allowing useful ones.
So what makes Verizon’s supercookie different? It’s created not by a Web site you visit, but by Verizon itself. It takes the form of a unique identifying number inserted into all of your HTTP requests to load Web sites, called a Unique Identifier Header (UIDH). Verizon Wireless began setting these supercookies in 2012, and it sells the resulting data to advertisers, who use it to better target advertising to you. It would be like your phone company listening in on your phone calls and interrupting every so often with special offers.
Supercookies are worse than regular cookies for a few reasons:
- They offer no benefit apart from possibly more targeted ads.
- They are inserted by Verizon, whom you’re already paying for service.
- Supercookies can’t be deleted, or avoided with browser privacy modes.
- Because of the way Verizon inserts the UIDH, third parties can intercept it and use it to track your online activity.
Thanks in part to pressure from the U.S. Senate, Verizon is now allowing customers to opt-out of supercookies.
Here’s how:
- Log into your Verizon Wireless account.
- If you’re not taken there automatically, click My Verizon.
- Click Manage Privacy Settings in the left-hand sidebar.
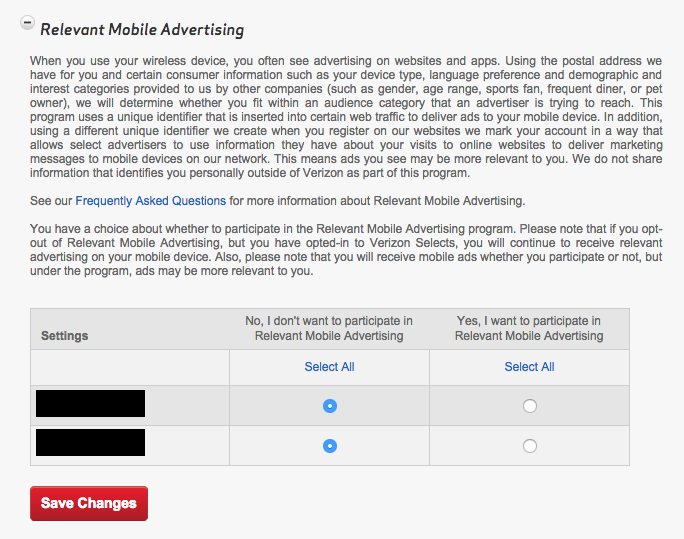
- Under Relevant Mobile Advertising, find the column that says, “No, I don’t want to participate in Relevant Mobile Advertising,” and select each phone line under that column, or click Select All.
- Click Save Changes.
If you see nothing under Relevant Mobile Advertising, your ad blocker may be preventing you from seeing those settings. Either disable it, or disable it for that specific page, and reload.
While you’re reviewing your privacy settings, you may also wish to opt out of Verizon Wireless sharing your Customer Proprietary Network Information Settings and using your mobile usage information for Business & Marketing Reports.
You can also opt-out with a phone call. Here’s how:
- Dial 1-866-211-0874.
- Enter your Verizon Wireless phone number.
- Enter your billing account password.
- Press 3 to edit privacy settings for both Business & Marketing Reports and Relevant Mobile Advertising.
- To opt out for all lines on the account, press 2.
The account owner should receive a free text message to verify the updated privacy settings.
How can you be sure that opting-out worked? Pick up your mobile device, disable Wi-Fi, and head over to amibeingtracked.com via cellular Internet. Tap Test Now, and the site will tell you if Verizon is tracking your Web browsing.
Verizon informs me that it could take up to a week for the updated privacy settings to take effect, so don’t be alarmed if the supercookie doesn’t crumble right away.
Should you be concerned if you use a different cellular carrier? In the United States at least, probably not. AT&T had been testing supercookies, but announced last year that it would phase them out; our tests have confirmed that. Other major carriers, such as Sprint and T-Mobile, have not been known to use supercookies. And given the bad publicity that they’ve garnered for Verizon Wireless, I wouldn’t be surprised to see them tossed in the compost soon.
How to Automatically Delete Your Twitter Trail
Twitter is a recipe for disaster. Its 140-character limit practically begs for you to broadcast short, half-baked thoughts. Combine that with Twitter’s public nature and world-wide network effect, and one misguided tweet could ruin your life. But sometimes Twitter mobs don’t even need a poorly conceived comment to pile onto users — just ask anyone who has been caught in the crosshairs of the Gamergate controversy (not to be confused with the Gamergate ant).
Ideally, we would all avoid Twitter entirely. As the sage producer of Saturday Night Live, Lorne Michaels, once quipped, “I don’t tweet for a very simple reason, which is that I drink.” However, most of us who depend on publicity for our livelihoods don’t have the luxury of being Lorne Michaels. The same Twitter mob that can send one person into hiding can give another person’s work a global audience. If not for Twitter, which I used to promote my early blog posts and pitch new article ideas, I wouldn’t be working for TidBITS now.
Twitter has another issue, in that tweets are a reflection of the moment they are conceived, and often do not age well. Or one brief tweet might have been supported and expanded upon by surrounding tweets, but when taken out of context years later, could send an entirely different message.
There’s probably no one more aware of Twitter’s double-edged sword than Trevor Noah, who is set to take the helm of The Daily Show when Jon Stewart steps down later this year. Noah, like many of us, used Twitter to get his work noticed. He zoomed from about two thousand followers in September 2009 to over two million today. But after his Daily Show announcement, inquiring minds dug up some off-color tweets from his past, sparking outrage. Comedy Central is standing behind him, but his new career is off to a rough start.
While most of us won’t be TV stars, Twitter can affect our careers in similarly negative ways. Despite the danger, many people can’t stay away. What’s to be done?
So-called “tweet deleters” think they have found a compromise by using scripts and services that delete tweets automatically after a given time. As CBC Radio producer Matthew Lazin-Ryder told Kevin Roose of Fusion, “I don’t laminate and frame my note-pad doodles, why would I preserve my tweets for all time?”
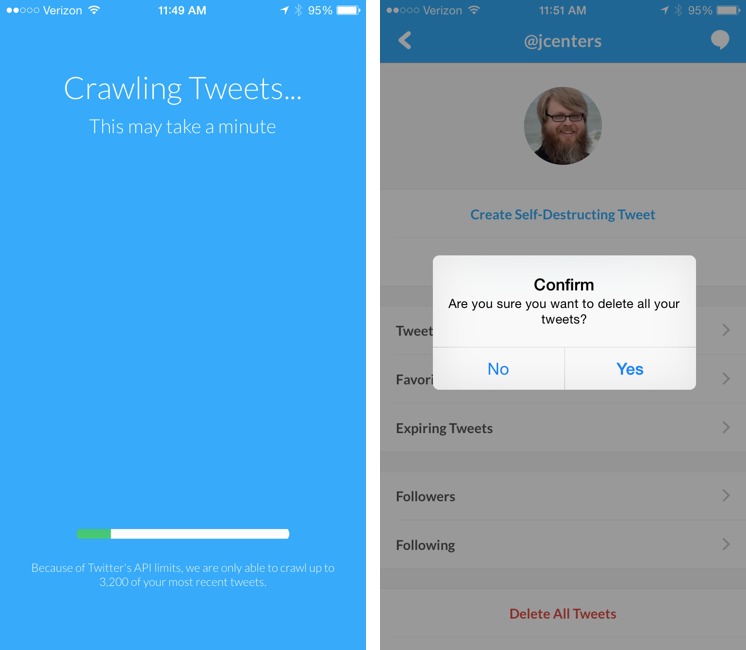
If you wish to become a tweet deleter, there are a few tools that can help. One of the simplest is a free iPhone app, Xpire, which can do four helpful things for your Twitter account:
- Create self-destructing tweets that vanish after a time you specify.
- Calculate your “social score” to tell you how risqué your Twitter stream is.
- Let you quickly select and delete multiple tweets.
- Delete all your tweets.
However, Xpire has one major drawback: due to Twitter’s API limits, it can interact with only your 3,200 most recent tweets. Also, though it’s also supposed to work with Facebook, I couldn’t get that functionality to work. Xpire also supports Tumblr, but I don’t have a public Tumblr account to test against.
An alterative free app on the Web is TweetDelete, which also claims to be able to delete all of your tweets, and even automatically delete new tweets after a set time. It too runs up against the 3,200 tweet limit.
Prefer a nuke-and-pave approach? The Twit Wipe site claims to delete almost everything from your Twitter account, including tweets, favorites, and retweets, leaving only who you follow and who follows you intact.
Beware that even if you do delete your old tweets, they may be archived elsewhere. Services like Topsy archive tweets for search and analysis. But deleting tweets from Twitter itself may at least make them harder to find.
Before you blow your entire Twitter history away, you may want to consider saving it for posterity. Thankfully, that’s a built-in Twitter feature. Here’s how to use it:
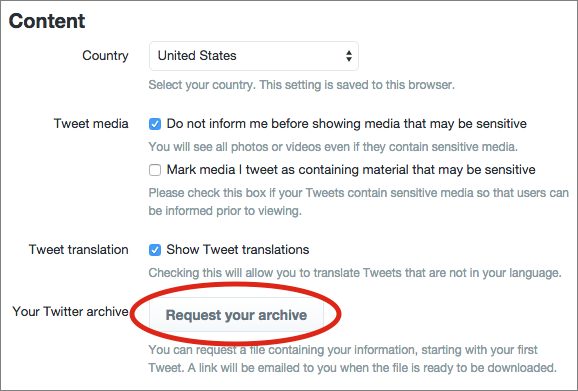
- Open your Twitter account settings.
- Under Account, click Request Your Archive.
It will take some time to compile your archive for download. Twitter will email you a link when it’s ready. The data comes in a Zip file containing both a CSV file (that can be imported into a spreadsheet or database) and a JSON archive (for viewing in a Web browser).
The Future Will Leave No Trace — As Twitter fights to remain relevant in the ever-fickle social media realm, it needs to consider offering its own automatic tweet-deletion feature, unhampered by the current limitations of its public API.
The next generation of social media is clearly headed in that direction. Many teenagers don’t have Twitter accounts, or rarely use the service, but lots rely on Snapchat, which deletes messages after they are read. Snapchat isn’t perfect (it’s easy to take a screenshot), but its automatic deletion is perfect for many situations.
Twitter should already know this. Its own video service, Periscope, automatically deletes videos after 24 hours (see “Twitter’s Meerkat Killer, Periscope, Has Arrived,” 27 March 2015).
It’s only common sense. After all, if Twitter is the world’s bar, who wants their bar talk archived for all time?
The company might be reticent to offer such a feature, since it likely wishes to have as much data as possible to sell to advertisers. But nothing prevents Twitter from extracting what meaning it wants from tweets while they are public, and besides, advertisers are undoubtedly more interested in current data — what’s the benefit in trying to sell me on something I tweeted about five years ago?
The entire business model of social media depends on trust. Users have to trust both that their data won’t be sold in ways that could prove harmful and that ill-conceived statements won’t come back to ruin their lives.
In the meantime, think (don’t drink) before you tweet. You can follow my tweets @jcenters, until they vanish in a puff of smoke.
The Books of Jobs
“What is truth? asked jesting Pilate and would not stay for an answer.” —Francis Bacon, 1601, “Of Truth”
On 24 March 2015, a new book, “Becoming Steve Jobs” by Brent Schlender and Rick Tetzeli, went on sale in the United States, and, as with so many things Apple-related, it garnered a great deal of business and technology press attention. And why not? The story has multiple click-bait hooks: secretive Apple, the mercurial Steve Jobs, and a battle for truth!
Dispatches from the Battlefront — Stephen Levy characterizes the story as “The War Over Who Steve Jobs Was”: he describes how friends, family, and colleagues closest to Steve Jobs have long felt that “Steve Jobs,” the biography that Walter Isaacson published in 2011, “focused too heavily on the Apple CEO’s worst behavior, and failed to present a 360-degree view of the person they knew.”
And now they’ve struck back. Apple executives and Jobs intimates (including Apple’s Tim Cook and Jony Ives, Pixar’s Ed Catmull, and Jobs’s widow, Laurene Powell Jobs) not only granted interviews about Jobs to Schlender and Tetzeli but also encouraged others to do the same. Apple as a corporation jumped on the bandwagon, with a formal statement to the New York Times about the book, saying that “we are happy we decided to participate.” The Schlender-Tetzeli book’s marketing page leads with Ed Catmull’s contentious pull-quote: “I hope that it will be recognized as the definitive history.”
History, it seems, is at stake. Isaacson, who was hand-picked by Jobs to write his biography, and to whom Jobs granted dozens of intimate interviews even as he was dying, can’t be blamed if he feels a little beleaguered at the moment.
One Is a Biography — Isaacson, to be clear, did not set out to write, nor did he publish, a tell-all smear job. He wrote, as he did for Albert Einstein and for Benjamin Franklin, a standard biography, a detailed account of an historical figure’s life, supported by as many documented facts as possible.
What more, it’s an authorized biography, written at the invitation of Jobs himself, and part of the brief he was given, as reiterated by Laurene Powell Jobs (who later criticized the finished product), was this:
There are parts of his life and personality that are extremely messy, and that’s the truth. […] You shouldn’t whitewash it. He’s good at spin, but he also has a remarkable story, and I’d like to see that it’s all told truthfully.
The book, then, has no explicit agenda other than to portray, as objectively as it can (and as any successful biography must), the facts of its subject’s life. Isaacson’s book is not, however, mere reportage: he does state that it is also “a book about innovation,” a topic of great interest to him, and he notes that it offers “lessons about innovation, character, leadership, and values.” But those lessons, for the most part, are for the reader to draw as they emerge from the facts presented.
A biographer needs to cut through the legends to the underlying facts that gave rise to those legends, with a minimum of editorializing, especially when a biography is about a controversial character, like Steve Jobs, about whom many legends have grown. To his credit, Isaacson attempts to do just that, and, for the most part, he succeeds.
It’s Isaacson’s bad luck that Jobs died just as the book was nearing completion, and worse luck that the first time that Jobs’ inner circle saw the manuscript was mere days after his funeral, when the last thing that any of those who loved Jobs wanted or needed to see was a clear-eyed assessment of the man, with all his virtues and flaws in full view — not when his death was a freshly gaping wound in their own lives.
One Is a Bildungsroman — Brent Schlender and Rick Tetzeli, on the other hand, are not attempting an authoritative biography. Theirs is a somewhat novelistic account — for example, though the book is a collaboration, it is presented as Schlender’s first-person account — and it comes with an explicit agenda: to explain how Steve Jobs “turned around his life and became the greatest visionary leader of our time.” If it were an actual novel, it would be a Bildungsroman, a novel about the coming of age and the education and character development of its protagonist.
To that end, the book deals lightly with historical detail, choosing those facts and events that are best suited to support the book’s agenda and arranging them appropriately. One case in point is the early description of how the young Jobs got backing for the early Apple Computer. In the Schlender and Tetzeli account, Jobs used his brashness and persistence, “tirelessly” navigating Silicon Valley’s experts “one phone call and one meeting at a time, until he finally found himself connected with Regis McKenna,” the “marketing whiz” who then put him in touch with the other Silicon Valley players who would help nurture Jobs’ nascent enterprise. As recounted in much more detail by Isaacson, McKenna came on board relatively late in the story, and through a process far more circuitous than Schlender and Tetzeli describe — but that tale does not highlight Jobs’s heroic persistence and is as much about the Silicon Valley culture of the era as it is about Jobs.
Similarly, late in the book, the account of the iPod rollout is portrayed as being an unalloyed success, and that “technology writers and reviewers and other cognoscenti wound up raving in print about features Apple hadn’t even touted.” To be sure, the device was well-received for the most part, but even those who were impressed (such as our own Jeff Carlson in “iPod Makes Music More Attractive,” 29 October 2001), noted the original device’s limitations and high price, and many were skeptical. Such nuances, however, do not fit the heroic narrative arc being constructed at this point in the book.
In fact, accurate detail is not this book’s concern at all, which may be why it includes many minor errors of fact: for example, the original Apple 1 had a 6502 processor, not a “6800” as Schlender and Tetzeli say; the first Macintosh was not “ivory” but beige (Pantone 453, to be exact); nor did the iPad 2 feature a flash to accompany its rear-facing camera.
But such trivial errata are irrelevant. Schendler, reporter though he is, is also someone whom Jobs considered a friend, who frequently visited Jobs and his family at home, who, unlike Isaacson, had been a first-hand witness to many of the major events, both public and private, in Jobs’s later life — and one who knew Jobs intimately enough to have some personal understanding of him as a human being. The book, as told by the lightly fictionalized Schendler-narrator, is as much an intimate memoir as it is a biography, a memoir that attempts to characterize and explain the inner life of the man he knew.
And, just as with Isaacson’s project, Schlender and Tetzeli’s project, for the most part, succeeds.
There Can Be More Than One — If there is a war for who Steve Jobs was, perhaps we need to call an armistice. Both books have their unique virtues as well as shortcomings.
The Isaacson book remains essential reading for anyone who wants a rich compendium of well-researched and annotated details about Steve Jobs, his life and times, and his own late reflections on it. It may not be a perfect book, but it’s an honest one and a good place to start.
For a deeply felt account, albeit in some ways speculative, of the qualities that earned Jobs the abiding respect and love of his closest associates, an account cast (quite deliberately, in fact) as a variation of the Hero’s Journey, the Schlender and Tetzeli book is the best that’s currently available. It shouldn’t be surprising that this is the story Apple and Jobs’s intimates wish to promote.
(The archetypal hero myth, by the way, is not just a conceit on the part of Schlender and Tetzeli; Isaacson also recognizes how curiously well Jobs’s life conforms to its structure: check out his allusion to Shakespeare’s Henry V in his book’s introductory chapter.)
In any case, the Matter of Jobs can encompass both of these books and more. I’m sure that neither volume completely captures the One True Jobs: he was, like all of us, more complicated, and with many more dimensions, than any one tale can tell.
“This is the West, sir. When the legend becomes fact, print the legend.” —from “The Man Who Shot Liberty Valance”
ITbits: Bushel Helps Small Companies Manage Apple Devices
No IT administrator in her right mind would set up Macs and iOS devices individually, installing software, configuring settings, and logging users into organizational services for each one. Powerful device-management tools exist for this purpose, which make it possible to efficiently configure, monitor, and maintain Apple devices en masse.
Many in large organizations turn to JAMF Software’s Casper Suite, the enterprise-grade toolkit for managing fleets of Macs and iOS devices across a corporation, government agency, or school district.
But JAMF recently realized Casper Suite is overkill for smaller organizations that are responsible for fewer Apple devices. JAMF co-founder Chip Pearson said this dawned on him when he saw his support staff spending hours on calls with befuddled small-business owners. For such people, he realized, IT is a task, not a career.
So JAMF went back to the drawing board and created a device-management service for modest-sized organizations. Called Bushel, it’s a Web-based toolkit for managing deployment of Apple devices in the dozens, not the hundreds or thousands.
Bushel is much simpler than Casper Suite, and JAMF has made Bushel free in perpetuity for up to three Apple devices per account — plenty to get your feet wet with device management. Additional devices cost $2 per month each, with no long-term contracts necessary.
I’ve been testing Bushel extensively since its release late last year, pretending to be a small-business owner and using the service to manage a handful of Macs and iOS devices. Though this has been fun, it has made one thing clear to me: Bushel is not for consumers (even super geeky ones). It’s intended for organizations, not individuals, even though anyone can play with it.
Getting Started — One of Bushel’s main strengths is its Web-based nature, unlike Casper deployments that generally require software to be installed on corporate servers. Bushel is a Web app, in essence, and is accessible via a browser window on almost any modern computer or mobile device.
To use Bushel, Apple devices must first be “enrolled.” A company’s IT administrator can do this, as can employees with Apple devices if permitted to do so via an open-enrollment program. Enrollment is merely a matter of logging in and installing a bit of software to create a Bushel certificate on the Mac or iOS device.
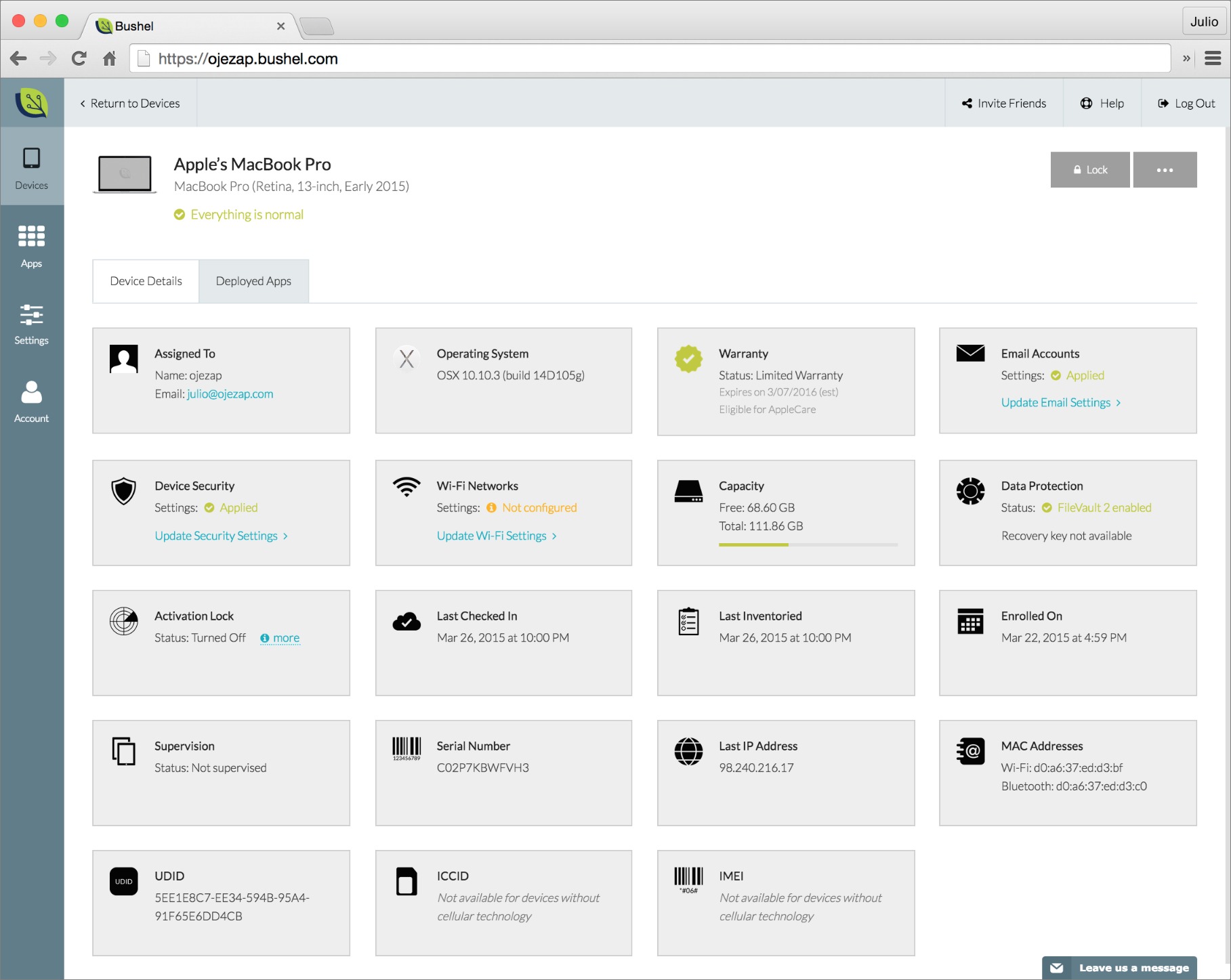
Once a device is enrolled, it shows up on Bushel’s Web console. This is another strength of the service, since the console has a simple, playful design. (It was originally too simple, but JAMF has been steadily improving it.) Each enrolled device is shown on a card with an iconic representation of the hardware type. There is also a prominent Enroll This Device button.
Doughnut-like symbols tell the administrator at a glance if devices are properly enrolled, if storage volumes are properly encrypted, and so on. Fully green doughnuts mean all is well. Any red in the doughnuts means there are problems with one or more devices. If so, an administrator can glance over the device cards to see which don’t show a green “everything is normal” message.
Clicking a gadget card reveals a wealth of data about the corresponding Mac, iPhone, or iPad. The card for my MacBook Pro, for instance, shows which version of Mac OS X is installed, the computer’s warranty status, whether FileVault has been enabled, its available storage capacity, and more. This data is crucial for helping administrators to stay on top of an organization’s device inventory.
The IT administrator can also implement security policies, such as requiring a password or a passcode, limiting iCloud features on iOS devices, determining Wi-Fi settings, and so on.
Apps and Email — Bushel is designed to make life easier for a small company’s harried IT administrator (who is probably juggling this duty with many other ones). It’s pretty good at that, from what I have seen.
For starters, Bushel automates the installation of Mac and iOS apps. With a single mouse click, I installed a variety of apps on all of my Bushel-enrolled iOS devices, all at once. Later, if I enroll more iOS devices, the apps in my Bushel installation list will automatically be installed on those devices.
Given that I’m juggling a bunch of Apple gadgets — three Macs, three iPhones, and an iPad — being able to automate numerous app installs was a huge time saver.
But I couldn’t make full use of this app installation feature without access to Apple’s Volume Purchase Program for Business (there’s also one for education), the service that organizations use to purchase an app once and install it on multiple Macs and iOS devices connected to different iTunes accounts. This is one reason Bushel is not intended for individuals.
Bushel does have access to iOS’s App Store and the Mac App Store built in, making it easier for an administrator to find what she needs.
Bushel also automates the configuration of email accounts on devices. Administrators choose an email service: Exchange, Google, Yahoo, or generic IMAP and/or POP accounts. Employees’ devices are then set up automatically by pairing their user names with an employer’s domain name.
On my Macs and iOS devices, for instance, [email protected], associated with my Google Apps for Work account, popped right up in the Mail app.
Advanced Features — IT administrators can automate device enrollments by letting employees do most of the work via an open-enrollment program.
Users are given a URL that takes them to a Bushel signup page. When they enter their usernames and email addresses (and, optionally, an administrator-supplied code), their devices are brought into the fold.
The administrator can determine how long the open enrollment lasts, and even restrict the enrollment to a designated IP address.
IT administrators can also sign up for Apple’s Device Enrollment Program (DEP). Once in the program, Macs and iOS devices purchased by the organization are automatically enrolled in Bushel on activation. Some basic setup routines are omitted in order to get users up and running quickly. This is another portion of Bushel I was unable to test, for obvious reasons.
A Bushel of Apple Devices — I’ve never tried to get my head around JAMF’s Casper Suite because it’s extremely complicated, not to mention irrelevant to me as individual user.
Realistically, Bushel isn’t for me, either, but I can see where it might be someday, were I to become responsible for a group of people and all their Apple devices. I’d embrace Bushel in a heartbeat if I were starting a small business.
For those already in that situation, Bushel looks to be a godsend. JAMF has clearly worked hard to provide key device management features while avoiding feature bloat, because a new Bushel user can master the service in a couple of hours. Overall, it’s simple, easy to understand, and inexpensive — a perfect combination for allowing the part-time IT administrator to get back to her other tasks.
TidBITS Watchlist: Notable Software Updates for 6 April 2015
Evernote 6.0.8 — Evernote has released version 6.0.8 of its eponymous information management app with several fixes to bugs reported by users in Evernote’s forums since the release of the previous version (see “Evernote 6.0.7,” 14 March 2015). The update ensures that table vertical alignment is top aligned and not middle aligned, fixes a bug that copied an attachment when dragged (rather than moving it), addresses an issue where the formatting toolbar remained and didn’t switch to the info toolbar after switching between notes, and fixes a crash that occurred during
syncing. (Free from Evernote or the Mac App Store, 64.6 MB, release notes, 10.7.5+)
Read/post comments about Evernote 6.0.8.
iFlicks 2.2 — Jendrik Bertram has released iFlicks 2.2 with a number of user interface improvements (see “iFlicks Improves iTunes Imports,” 10 January 2013). The video encoding and metadata management app also adds a Watch Folder agent that monitors folders even when iFlicks isn’t running, provides more accurate metadata lookups, improves video processing (which also improves synchronization), improves support for formatting subtitles, and updates localizations. Normally priced at $24.99, iFlicks is discounted by 25 percent through the month of April. ($18.99 new from the Mac App Store, free update, 17.0 MB, 10.8.3+)
Read/post comments about iFlicks 2.2.
Fantastical 2.0.2 — Flexibits has issued Fantastical 2.0.2, a maintenance update for the recently released major upgrade to the popular calendar app (see “Fantastical 2 Aims to Replace Apple’s Calendar,” 27 March 2015). The update improves iCloud account setup when entering an incorrect password, speeds up loading of Exchange and local calendars, fixes a crash caused by adding a Google account, rejiggers the Today widget to display only upcoming events if there isn’t enough room for a complete schedule, fixes an issue when TextExpander is activated while typing into the
input field, and improves account setup when connecting to CalendarServer and OS X Server. Fantastical 2 has a 14-day free trial, and currently costs $39.99 from either the Flexibits Store or the Mac App Store; the price will go up to $49.99 after an introductory discount period. ($39.99 new, free update from Flexibits and the Mac App Store, 12.1 MB, release notes)
Read/post comments about Fantastical 2.0.2.
TweetDeck 3.9.482 — Twitter has released TweetDeck 3.9.482 for Mac with several new features that had been rolled out to the browser-based TweetDeck earlier this year. The Twitter tracking and engagement app adds the capability to share access to your accounts using the new Teams feature, adds a Group Messaging feature that provides options to create direct messages for private conversations with groups, enables you to add up to four images to each tweet, and adds
support for inline playback of videos and animated GIFs. Additionally, if you haven’t signed into TweetDeck recently, you’ll now be required to log into TweetDeck using a Twitter account instead of your original TweetDeck credentials. (Free from the Mac App Store, 3.8 MB, 10.6+)
Read/post comments about TweetDeck 3.9.482.
LaunchBar 6.2 — Objective Development has released LaunchBar 6.2, chock full of bug fixes and refinements, including new staging capabilities. The keyboard-based launcher enables you to select multiple items from the result list via drag-and-drop, and those staged items can be dragged from LaunchBar to other applications. The update also brings support for the recently released Fantastical 2 calendar app (see “Fantastical 2 Aims to Replace Apple’s Calendar,” 27 March 2015), improves indexing of iCloud Documents and iCloud Drive, tweaks Instant Calculate to better
distinguish between phone numbers and arithmetic expressions, fixes a bug that caused pasting clipboard items into Safari form fields to fail, improves background execution of AppleScripts, and fixes an issue that caused Clipboard History to stop working. ($29 new with a 20 percent discount for TidBITS members, free update, 9.8 MB, release notes, 10.9+)
Read/post comments about LaunchBar 6.2.
ChronoSync 4.6 and ChronoAgent 1.5.1 — Econ Technologies has released ChronoSync 4.6 and ChronoAgent 1.5.1, with the former receiving over a dozen new features as well as a long list of enhancements and fixes. ChronoSync’s biggest addition is the SmartScan feature, an advanced algorithm that analyzes a volume for changes. While files won’t copy any faster, Chronosync promises significant speed gains due to how SmartScan detects which files need to be copied. The synchronization and backup app also adds checksum data
verification for performance increases (especially across slower connections), new scheduling options, an improved user interface for OS X 10.10 Yosemite, rules to include/exclude files based on Finder tags, the capability to mount and unmount locally attached drives, and push notifications sent to an iOS device via the $2.99 ChronoMonitor app (coming in version 1.1). ChronoSync now requires 10.8 Mountain Lion and later.
ChronoAgent 1.5.1 improves SmartScan comparability with ChronoSync 4.6, improves VoiceOver support, and adds a Japanese localization. (Free updates for both apps; $40 new for ChronoSync with a 25 percent discount for TidBITS members, 28.4 MB, release notes, 10.8+; $10 new for ChronoAgent, 10.3 MB, release notes, 10.8+)
Read/post comments about ChronoSync 4.6 and ChronoAgent 1.5.1.
ExtraBITS for 6 April 2015
In this week’s collection of external links, Adam Engst sits in on MacBreak Weekly, Comcast Internet speeds are about to see a big boost, Apple’s Lisa Jackson discusses the company’s environmental efforts, we find out how a stolen iPhone changed a man’s life for the better, and we get a look at the making of the Apple Watch.
Adam Engst Goes Normcore on MacBreak Weekly — TidBITS publisher Adam Engst had a rollicking good time joining Leo Laporte, Andy Ihnatko, and Alex Lindsay on MacBreak Weekly to talk about how the fashion world sees the Apple Watch as “normcore,” the difference between the two most recent Steve Jobs biographies, the rise of Periscope and fall of Meerkat, and much more.
Comcast Introducing 2 Gbps Internet Service — Feeling the pressure from Google Fiber and others, Comcast has announced that it will be rolling out a new 2 Gbps fiber-optic Internet service in Atlanta next month. Comcast said that it plans to expand the service as quickly as possible, covering 18 million American homes by the end of 2015. The company is also planning a 1 Gbps service for 2016, which it said should be available to almost every customer in Comcast’s service areas.
Lisa Jackson on Apple and Renewable Energy — Lisa Jackson, former head of the U.S. Environmental Protection Agency and current Apple vice president of the company’s Environmental Initiatives group, sat down with the Wall Street Journal to discuss Apple’s commitment to renewable energy. While Apple is working to make all of its U.S. interests run on renewable power, there’s much to be done overseas, where most of Apple’s products are manufactured.
Stolen iPhone Turns BuzzFeed Writer into a Celebrity in China — Matt Stopera’s iPhone was stolen at a bar in New York City. Whatever. A year later, photos from a guy in China start appearing in his iCloud photo stream. OK, that’s weird. Then he writes an article about it on BuzzFeed, and his story goes viral. In China. Now things are getting stranger by the minute. Finally, he travels to China to meet the guy who ended up with his phone. That’s where the story becomes truly insane, but also turns into a lovely tale of friendship across language and cultural
barriers. Read it now, or if you’re really busy, you can wait for the movie. Yes, the movie.
Behind the Scenes of the Apple Watch — David Pierce of Wired offers an exclusive inside look at the development of the Apple Watch. While the watch was the vision of Apple senior vice president of design Jony Ive, it was turned into a product by Kevin Lynch, the former Adobe CTO who publicly battled Steve Jobs over Flash. The concept behind the Apple Watch is interesting: the iPhone is ruining your life and it’s up to the Apple Watch to separate you from your iPhone. Pierce gives us a look at the Apple Watch’s rough beginnings as an iPhone app, complete with a velcro strap and a digital crown dongle that
plugged into the bottom. It took more than a year for the Apple Watch team to perfect its sounds and taps to Jony Ive’s satisfaction.