TidBITS#1116/05-Mar-2012
We’re busy preparing for Apple’s iPad announcement on Wednesday, but we have some great articles for you to read in the meantime. Adam leads with a look at how AT&T is now throttling unlimited plan users (their bandwidth, not them personally) when they hit 3 GB of usage and how affected users might be able to fight back. Then Jeff Carlson reviews Reflection, a Mac OS X application that acts as an AirPlay receiver, so you can mirror your iPad 2 or iPhone 4S display on the Mac, which is a boon to speakers, educators, and anyone who needs to demo iOS apps to a group. Finally, we look into Apple’s twice-delayed requirement that apps in the Mac App Store be sandboxed to see how it impacts developers and users alike. Notable software releases this week include Mac OS X 10.7.3 Supplemental Update; Hazel 3.0; GraphicConverter 7.6.2; DEVONthink Personal, Pro, and Pro Office 2.3.3; Firmware Update for MacBook Pro (15-inch, late 2008 models); HandBrake 0.9.6; Fetch 5.7.1; TextExpander 3.4.1; and iMac Wi-Fi Update 1.0.
iPad 3 Expected at March 7th Apple Event
Some rumors do turn out to be true, and this week we’ll see which others become fact as well. 7 March 2012 was the date bandied about online for a media event announcing the third generation of the iPad. Apple sent invitations to media outlets last week beckoning them to the Yerba Buena Center for the Arts in San Francisco.
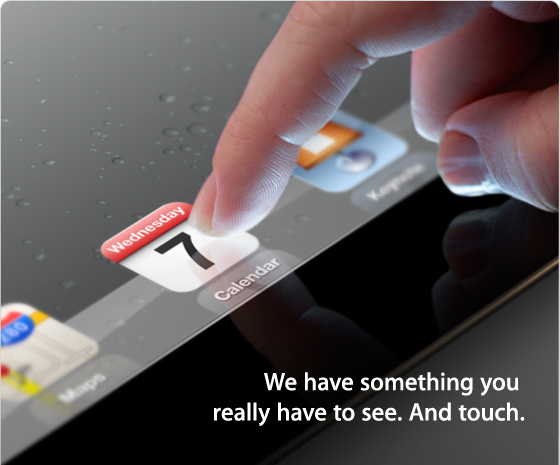
Apple’s invitations are usually teases for what to expect, and although the iPad isn’t specifically mentioned, it’s clear that the iPad 3 (or perhaps an iPad 2S?) will be the star of the show: a finger is tapping an iPad screen above the text, “We have something you really have to see. And touch.” (Apple also enjoys encoding its images; the visible app icons include the Calendar, with its icon set to Wednesday the 7th; Keynote, since it’s a presentation; and Maps, to indicate a location, although the Maps icon sticks to the default of pinpointing Apple’s headquarters in Cupertino.)
We could speculate about the upcoming iPad’s features, but really, what’s the point when we’ll know the real details so soon? I’ll be at the event and the TidBITS staff will be following along with other live coverage so we can provide details here. (And if you want to get a sense of what it’s like to attend an Apple media event, see my report from the first iPad announcement at “Photo Tour of Apple’s iPad Introduction,” 29 January 2010.)
Doxie Sponsoring TidBITS
We’re pleased to welcome as our latest TidBITS sponsor Apparent Corporation, makers of the USB-powered Doxie mobile scanner that debuted at Macworld Expo in 2010 and has now been joined by the battery-powered Doxie Go, which can store hundreds of scans either in internal memory or to a USB flash drive or SD card — no need to connect to a computer. What set the original Doxie apart was its capability to upload scans directly to cloud-based storage services like Google Docs, Dropbox, Evernote, Flickr, and more. Doxie Go extends that with a Wi-Fi option that can send scans to your computer, to a supported cloud service, or even to an iPad or iPhone.
Apparent isn’t new to the Mac world, and we’ve written in the past about their IntelliScanner Wine Collector, which couples a mini portable barcode reader and wine database software for tracking not just all those dusty bottles in your wine cellar but also what you actually drink (see “Macworld Expo San Francisco 2005 Superlatives,” 17 January 2005).
But it’s clear that Doxie is their focus now, and they’re putting attention into both Doxie’s hardware and software. Doxie’s elegant, modern software automatically receives scans from Doxie Go when you plug it in, just like a digital camera, and it performs automatic cropping, rotation, and contrast boosting to improve scan quality. The included ABBYY OCR technology recognizes the text in scanned documents, creating searchable PDFs. The smart stapler tool lets you combine multiple scans into a single multi-page PDF document, and you can send scans to any app on your computer or upload to a cloud service.
Thanks to Apparent for their support of TidBITS and the Apple community!
AT&T Throttles Unlimited Plan Users at 3 GB
It’s hard to know what to think. AT&T — likely prodded hard by Apple — initially offered a $30 unlimited data plan with the iPhone. However, back in June 2010, AT&T dropped its unlimited plan in favor of a pair of tiered plans for 200 MB ($15) and 2 GB ($25) of data (see “AT&T Ends Unlimited iPhone and iPad Data Plans,” 2 June 2010). The tiered plans legitimately reduced costs for many iPhone users, but those who wished to stick with the unlimited plan were grandfathered in, at least as long as they didn’t change their plans in any other way. Earlier this year, AT&T tweaked those plans, increasing prices and raising the data caps to 300 MB ($20) and 3 GB ($30)
(see “AT&T Raises Data Plan Prices for New Customers,” 18 January 2012), and once again grandfathering in those who had either an unlimited plan or the previous tiered plans.
(Similarly, when the iPhone became available for Verizon Wireless customers, Verizon initially offered an unlimited data plan to encourage customers to switch from AT&T. That too was short-lived, lasting only from February 2011 to July 2011.)
However much you might consider any of these moves good or bad, the real problem is that AT&T has reneged on the grandfathered unlimited data plans, starting with a plan to throttle (reportedly to EDGE speeds — about 200–300 Kbps — or slower) the top 5 percent of bandwidth users among the unlimited subscribers. With some 20 million users remaining on the unlimited plans as of the middle of 2011, as many as 1 million users were being throttled each month.
But what put you in the top 5 percent, or what AT&T considers a “small minority”? It turns out that some customers were being throttled when their data usage exceeded 2 GB. That was particularly offensive, given that AT&T earlier this year changed its top-level tiered data plan from 2 GB for $25 to 3 GB for $30 — the same price as the initial unlimited data plan. In essence, unlimited data plan users were paying as much as the 3 GB tiered plan users, but receiving only 2 GB of data before being throttled.
One unlimited data plan subscriber who experienced being throttled decided to fight back. Matt Spaccarelli, an unemployed truck driver and student, took AT&T to small claims court and won $850, with the judge saying that it wasn’t fair for AT&T to have throttled Spaccarelli’s throughput after selling him an “unlimited” data plan. (Somewhat muddying the issue was that Spaccarelli used his unlimited data plan for tethering without paying extra — something he admitted when it came up in the case. Nevertheless, he said he was using only about 5 GB per month total.)
Prompted by Spaccarelli’s case, MacTech has published an article by lawyer Bradley Sniderman explaining what is involved in filing a similar suit against AT&T in small claims court.
AT&T has once again revised its policy, posting a support page explaining the new approach, which is both more generous and more transparent than before, even if the end result is still not unlimited data. In essence, users with grandfathered unlimited plans will now receive 3 GB of data at normal speeds, whatever those may be, but data usage beyond that will be throttled until the end of the billing cycle. The first time this happens, AT&T will send you a warning text message, but should your usage exceed 3 GB in a subsequent month, you won’t receive another warning.
AT&T’s page descends into weasel words with this statement, which willfully ignores the fact that if your throughput has been throttled, you almost certainly cannot use as much data as you want.
You’ll still be able to use as much data as you want. That won’t change. Only your data throughput speed will change if you use 3 GB or more in one billing cycle on a 3G or 4G smartphone.
I started this article saying that it’s hard to know what to think. On the one hand, AT&T says that wireless data traffic has soared, growing 200 times over the last five years, as the number of smartphone users served by the company has grown from 7 million to 39.4 million. There’s no question that the company is desperately paddling upstream, trying to maintain a good mobile broadband experience for the majority of customers, and it’s likely that throttling the users with unlimited data plans was seen as the least bad way of doing that.
On the other hand, AT&T’s reneging on their unlimited data plan contracts is reprehensible. I don’t have one of those contracts around to know if it’s worded in such a way as to give AT&T the right to back out at any time, but regardless, it’s poor business practice to offer an ongoing subscription service and then change the terms in a drastic way. If the company takes a beating from individuals in small claims court for this behavior, so be it.
Plus, throttling unlimited plan users who go above 3 GB of data seems particularly wrong, given that AT&T is more than happy to sell tiered plan users additional gigabytes for $10 each, implying that usage beyond 3 GB isn’t a problem for the network. The guy who won damages from AT&T in small claims court would have paid only about $20 per month more for the 5 GB of data he used, and while that might have been a lot of money for an unemployed truck driver, it doesn’t seem like a major issue for AT&T to keep a loyal customer. If AT&T started throttling these users at 10 GB, say, there would likely be less outcry, since those people would be getting $100 worth of today’s service for their locked-in $30 plans, whereas
now, they’re getting exactly the same $30 worth of today’s service.
Regardless, if you find yourself in this situation, you can either put up with the throttling, or you can switch to the tiered plan, under which you’d pay $30 for 3 GB and $10 for each additional gigabyte. The first option probably makes sense if money is tight, you hover around the 3 GB usage mark, and you don’t care deeply about throughput speed. The second is more compelling if you rely on fast throughput and can afford the overage charges.
Unfortunately, switching carriers may not help, given that Verizon no longer offers an unlimited plan and while Sprint does offer unlimited data as part of their plans, which start at $79.99, it’s unlimited only on the Sprint network and Sprint reserves the right to throttle throughput or to “deny, terminate, modify, disconnect or suspend service” if you go over 300 MB of off-network data use. In the end, if you use vastly more than 3 GB per month, it would probably be smart to see if you can transfer some of that traffic to Wi-Fi.
Reflection Mirrors iOS Devices on the Mac
When Apple first introduced Keynote for the iPad, I thought it was a neat proof of concept. But I had a hard time getting around the disconnect of using a handheld tablet as a presentation device, unless you’re presenting to two people next to you.
Fast-forward two years. (Yes, it has been only two years since the iPad’s introduction.) When I gave a talk about iMovie for iOS at the San Francisco Apple Store during Macworld | iWorld in January, I did it entirely from my iPad 2 using the Keynote and iMovie apps; the iPad was connected via cables and a VGA Adapter to the store’s audio-visual system. (Actually, that’s not completely correct: I ended up setting my 15-inch MacBook Pro on the lectern just to read my session notes, because I forgot to print them out prior to the presentation.)
That event was still fairly low-tech in the sense that a VGA connection is ancient history compared with the capability, introduced in iOS 5 for the iPad 2 and iPhone 4S, to mirror the screen to an Apple TV using Apple’s AirPlay technology. The VGA cable was easiest for the Apple Store staff to set up, but I could just as easily have carried the iPad untethered if an Apple TV had been available; that’s how I rehearsed at home.
But outside of the living room, I’m guessing you won’t find an Apple TV in most settings (although I’ve read reports that the combination of an iPad and an Apple TV is making inroads into the classroom). What has been missing from this scenario is the capability to share the iPad (or iPhone 4S) screen on a Mac.
Now that limitation has crumbled with the release of Reflection, a $14.99 Mac OS X app that makes an iPad 2 — and presumably the next iPad model being introduced this week — or iPhone 4S see the Mac as an AirPlay destination. Older iOS devices lack the necessary hardware for mirroring. (Another application, AirServer 4.0, reportedly also mirrors an iOS device’s display on a Mac, but I haven’t tried it yet.)
From the standpoint of someone creating the content to be presented, having the iPad’s screen on a Mac offers a few advantages:
- Speakers can attach the destination Mac to a projector, so they can both use the iPad untethered and switch to showing Mac applications as necessary.
- Developers can demo iOS software running live on a real device, not in a simulator.
-
Educators (and authors like me) can finally record video of iOS interactions on the Mac without fussing with extra video capture equipment or jailbreaking the device.
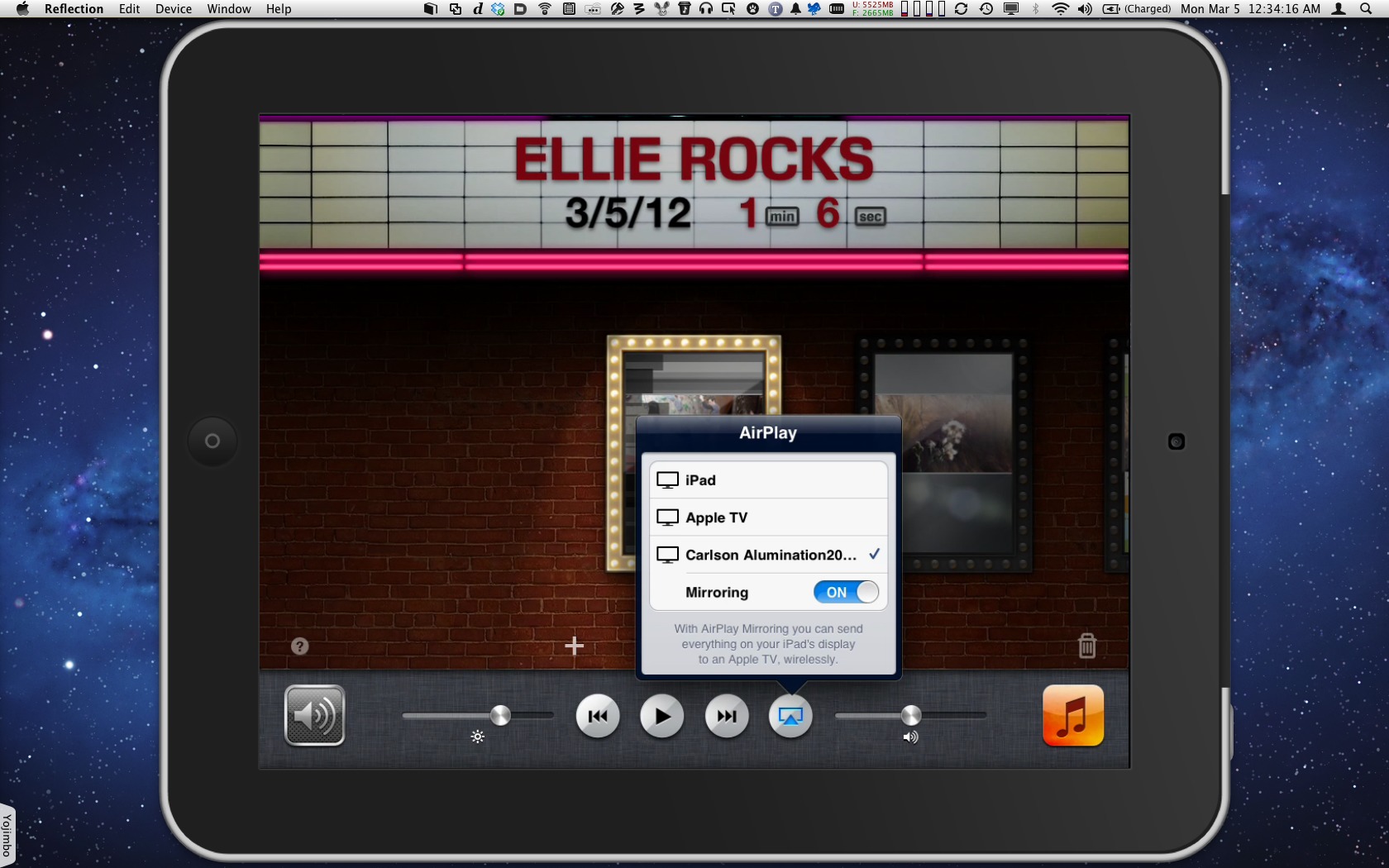
How It Works — Reflection runs as a regular app under Mac OS X, and once you launch it, you may forget it’s there. The rest of the setup is similarly easy.
On the iPad 2 or iPhone 4S, enable AirPlay mirroring: Double-press the Home button to reveal the row of recent apps, swipe left to right to display the playback controls (on the iPhone 4S, you need to swipe twice), and tap the AirPlay button. Your computer will show up as an AirPlay-capable receiver. Select it, and then tap the Mirroring switch to On.
On your Mac, Reflection displays the iOS device’s screen in a device-specific frame. You can get rid of the frame by choosing Device > Show Frame (Command-B) if you find it as distracting as I do.
Other options include forcing landscape or portrait orientation, switching to Full Screen mode (where Reflection runs in its own desktop space), and setting a password to allow the connection (so not just anyone can display their device on your Mac).
Reflection also includes options for “optimizing” the resolution, which means Reflection forces the incoming screen into a set image size rather than zooming to the full screen size. However, it doesn’t stay true to those specs: Connecting my iPhone 4S with the option to optimize for “Retina iPhone (640×960)” gives me a window sized at 685 by 1027 pixels. The iPad 2, when set for “iPad (1024×768)” presents a screen that’s just a hair larger than that at 1052 by 790 pixels.
You can also optimize for “Any Device (1280×720)” or for “Hi-Res (1920×1080),” but those aren’t honored either; Reflection really wants to zoom the screen as large as your Mac’s monitor will allow. That’s fine, to a point — if you’re giving a presentation, you probably want the largest possible version for your audience. But as an author and video producer, I’d like to see an option to force a pixel-accurate resolution. Resizing makes everything a little fuzzy due to anti-aliasing.
Still, that’s not a deal breaker for my main interest: capturing the screen. With Reflection displaying the live contents of your iPad or iPhone, use the screen-recording features of applications such as QuickTime Player, Snapz Pro X, or ScreenFlow. I created a short example in Snapz Pro X of getting video while working in iMovie for iOS.
In general, the response isn’t bad. There’s a slight lag between what you do on the device and what appears on the Mac, but I didn’t notice dropped frames or other performance degradations in normal use.
Where I did occasionally run into spotty performance was playing video content, such as from the Videos app. In that situation, mirroring stops, and Reflection hands the video off to QuickTime Player, which sometimes couldn’t buffer the video fast enough to keep up. However, at other times I had no problem, so I can’t rule out other traffic on my network, such as a local CrashPlan backup of my wife’s laptop downstairs. (Oddly, when viewing movie trailers using Apple’s Trailers app, the video wasn’t passed along to QuickTime Player. Movie trailers exhibited the same video playback controls as usual, but Reflection stayed in its mirrored state.)
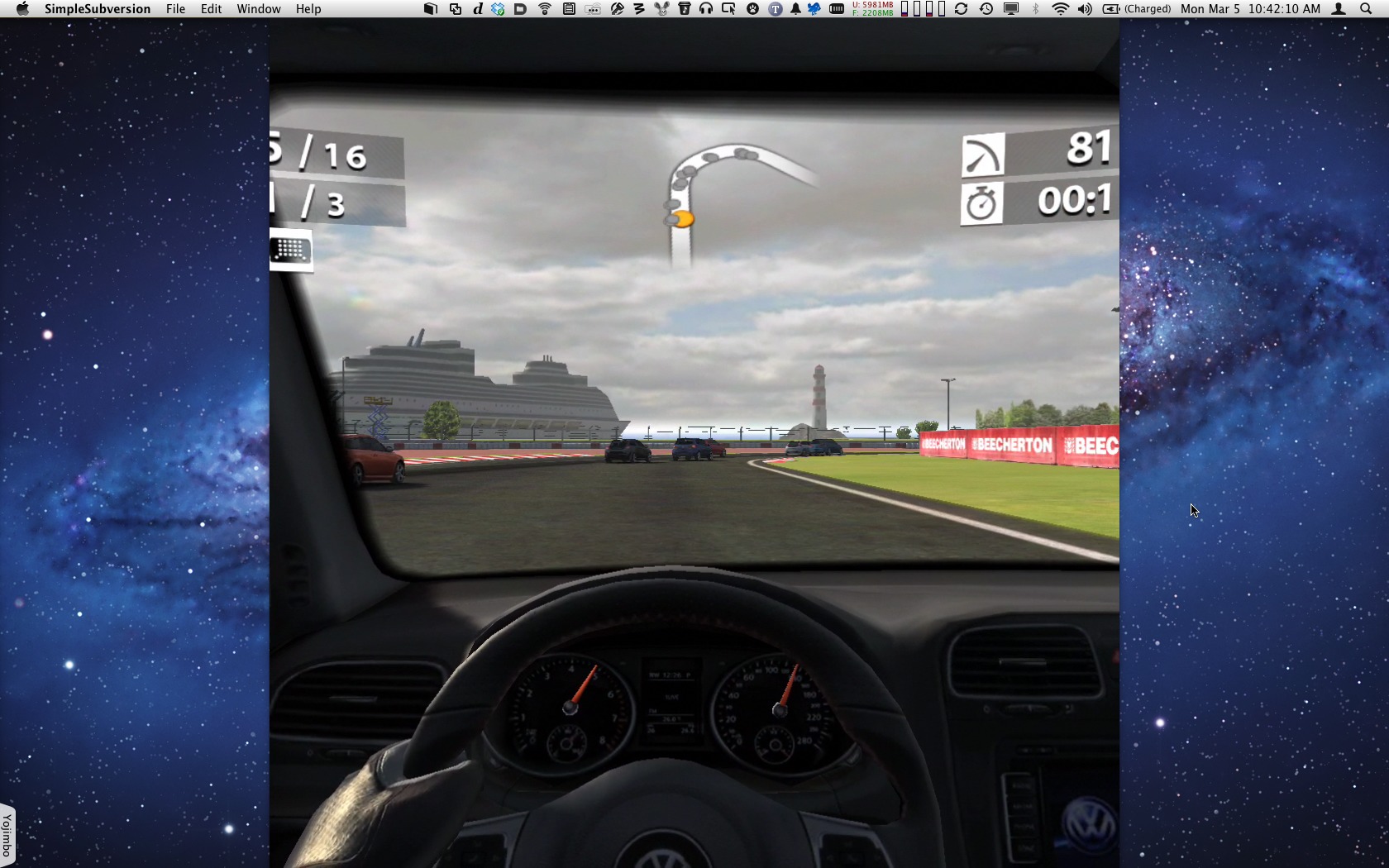
Games that can use AirPlay for output, such as Real Racing 2 HD, didn’t display the correct aspect ratio. (If you don’t own an HDTV, being able to use the iPad as a game controller to play a game like that on a 27-inch iMac would be a lot of fun.) I also noticed that changing the iPad volume didn’t affect the volume coming from Reflection on the Mac, although I suspect that’s by design so you don’t have warring volume levels. Still, it would be nice if you’re already controlling the device and running something like GarageBand to adjust the volume in the app, instead of manipulating it separately on the Mac.
I’d like to see one key feature added: a gesture indicator, so you can see where the iPad user’s fingers make contact with the screen. When doing my iMovie presentation, the audience couldn’t see what I was tapping: I had to vocalize my motions to make sure everyone’s attention was at the appropriate control (“Now I’ll tap the Project Settings button, the one with the gear icon in the upper-right corner”). Having a circle appear for a speaker’s finger touch, for example, would make the interaction immediately
apparent.
Overall, though, Reflection is a good 1.x release that makes AirPlay even more useful to me. As I said earlier, it costs $14.99, or $49.99 for five licenses, and a trial version that shuts off after 10 minutes is available as a free download.
But now I have a new problem: looking at my Mac’s screen and wondering why my mouse isn’t controlling the iPad. Perhaps that, too, will come in time.
The Sandbox Conundrum: Security vs. Innovation
In an email message to all registered developers, Apple announced last week that it has, once again, extended the deadline for developers to comply with new security requirements in order to publish their apps on the Mac App Store — this time until 1 June 2012.
The company had originally required developers to adopt a “sandbox” model for their apps by 1 March 2012 or risk being shut out of the Mac App Store. Sandboxing enables Mac OS X to limit an application’s access to system resources like files stored outside the app’s sandbox and the network in an attempt to limit the possibility that malware will make its way onto a user’s computer (see “Lion Security: Building on the iOS Foundation,” 12 August 2011).
The deadline extension comes hard on the heels of the announcement of OS X 10.8 Mountain Lion, and reveals the extent to which Apple is struggling to bridge its desire for a highly secure environment for users with developers’ desire to have access to every feature of the operating system in order to give their software the features users want.
Pros and Cons of Sandboxing — The basic idea behind sandboxing is simple: Apps that run in a sandboxed environment are prevented from accessing system resources that could lead to the disclosure of sensitive information (like the file system or the Clipboard) or that could be used for nefarious purposes (like the network). Developers must explicitly ask Apple for permission to access each resource and be prepared to justify their request as part of the Mac App Store submission process. Apple, in turn, may grant exceptions, called “entitlements,” that allow an app to work outside of the sandbox under limited circumstances.
In theory, the result is an environment which, as long as every app participates in sandboxing and there are no security issues in the operating system, is entirely safe for the end user. This doesn’t just mean “no malware,” but also (and perhaps more importantly, given that the vast majority of apps are written by honest developers) a computer that is impervious to crashes caused by apps stepping on each other’s toes.
This is how things work in iOS, where apps are sandboxed by default and the App Store is the only distribution channel for developers (barring jailbreaking, which Apple does not support or condone, though a few apps for jailbroken iPhones offer compelling capabilities, some of which Apple has even added to iOS after the fact). There is no denying that, apart from a few hiccups, Apple’s mobile operating system has been successful in both providing a highly reliable system and maintaining security for users.
In practical terms, however, sandboxing prevents applications from interacting with the operating system and with one another. Many popular Mac OS X apps require sweeping access to the operating system to function at all: Audio Hijack Pro, LaunchBar, FastScripts, Default Folder X, and Keyboard Maestro, to list just a few common examples. These apps do nothing harmful, and are in fact providing functionality that their users desperately want, but they are essentially incompatible with the “secure” environment that Apple is trying to implement.
Apple has been working to find a middle ground with the developer community, responding to the criticism that has surrounded sandboxing by introducing more entitlements for developers (so sandboxed apps can do more) and by twice extending the deadline by which apps must be sandboxed to be accepted into the Mac App Store.
So what’s the problem?
Follow the Money — Unfortunately, while sandboxing is certainly a viable technical solution to the problems of security and reliability, Apple has muddied the waters by making it the price of entry into the Mac App Store.
On the one hand, this seems reasonable. Apple is offering a carrot — distribution in the Mac App Store — in exchange for developers sandboxing their apps. This isn’t the iOS world, where the App Store is the only source for software, so it would seem a relatively simple equation. Alas, it’s not nearly so cut and dried, for two reasons.
First, the sandboxing requirement for the Mac App Store is new, and many apps that have already found success in the Mac App Store cannot be sandboxed without losing significant functionality. Apple announced that such apps can remain in the Mac App Store without sandboxing after the deadline, and can even be updated with bug fixes. To be clear, Apple said:
Starting June 1, if you have an existing app on the Mac App Store that is not sandboxed, you may still submit bug fix updates without sandboxing your app. In addition, if you have technical issues that prevent you from sandboxing your app by June 1, let us know.
Left unanswered is the question of what happens when a developer with a Mac App Store app that cannot be sandboxed wants to release a feature update. Will Apple approve such an update, or simply reject it on the grounds that it doesn’t meet the sandboxing requirements?
We would argue that Apple should accept such updates, regardless of the inconsistency, for the simple reason that to reject them would break Apple’s implicit agreement with customers that updates to Mac App Store apps will be made available, for free, through the Mac App Store. Remember, when you purchase something through the Mac App Store, you’re Apple’s customer, not the developer’s, and Apple does not share any customer contact information with developers. So there’s currently no way developers could even take over support for such Mac App Store orphans, leading to a situation where everyone loses: developers lose customers, Apple and the Mac App Store take a reputation hit, and users lose access to updated software they
have purchased.
The second reason the sandboxing for Mac App Store distribution equation isn’t simple is that it won’t be long before many users — particularly those new to the platform — see the Mac App Store as the only source for Mac software and won’t buy software directly from developers. In essence, Apple will end up with nearly the same level of market control as in iOS, while still claiming that the Mac software market is open to all comers.
And that’s where we end up with a chilling effect. Established developers may have sufficiently large audiences and marketing machines to launch new software outside the Mac App Store, but for new developers, the cost and effort may outweigh the possible earnings. As soon as the Mac App Store becomes sufficiently dominant that developers feel they can’t succeed outside of it, we all suffer from the lack of software that might have been.
Where We’re Going — Let’s be real. There’s no question that security and reliability are important, and Apple has no Orwellian plans for world domination that involve getting rid of pesky developers who won’t toe Apple’s corporate line.
Instead, it seems that Apple believes that the success of iOS is due in part to apps that use the operating system in exactly the way Apple intends them to and can never step outside their own sandboxes.
This is not just a matter of freakish control over every detail (goodness knows there is still a vast number of truly awful iOS apps, and even some of Apple’s own apps are pretty weak). When Apple engineers build developer tools with specific usage patterns in mind, they can make sure that, as long as those patterns are followed strictly, the operating system and its apps run in harmony and give users the best possible experience, or at least the most predictable one.
If, on the other hand, developers are given free rein to interact with the operating system in any way they wish, it’s entirely possible that they will stumble upon an approach that works most of the time, but that causes the operating system to become unstable on occasion.
This is nothing new — since the launch of the Mac App Store, apps have had to abide by Apple’s public API policy (which says that developers may use only Apple’s published methods of interacting with the operating system) to be allowed in. Sandboxing simply extends that concept to include techniques and methods that make apps “good citizens” by accessing system resources in a predictable fashion and not creating potential security hazards.
As a result, we think sandboxing is here to stay. Developers will continue to fume, but Apple appears to believe, as a result of its iOS experience, that using a sandboxed model aligns Mac apps better with the needs of its users. Progress will be slow as Apple tries to provide developers more entitlements, but eventually the deadline extensions will stop coming and access to the Mac App Store will only be granted to those who play by its new rules.
Viable Alternatives? — Is there any other approach Apple could use that would provide an equivalent level of security while not stifling developer innovation and the advantages it brings to users?
The big unknown is exactly why Apple feels that sandboxing is sufficiently important to create such headaches for a large segment of the developer community. That’s a particularly interesting question in light of the upcoming Gatekeeper technology in Mountain Lion that will create three classes of applications: those that can be trusted because they are downloaded from the Mac App Store, those that are distributed outside the Mac App Store but can be trusted because they are digitally signed by their developers, and everything else (see “Gatekeeper Slams the Door on Mac Malware Epidemics,” 16 February 2012). Even without sandboxing, it would seem that Apple approval in the Mac App
Store would be sufficient to bump an app into the highest level of trust. (And if it’s not sufficient, doesn’t that imply Apple’s approval process adds little value?)
In a world where sandboxing is required for entry into the Mac App Store, Gatekeeper changes nothing for developers — non-sandboxed apps must still be distributed outside the Mac App Store regardless of whether or not they’re digitally signed, so all the business and innovation concerns remain.
But what if Apple changed the sandboxing carrot and offered sandboxed apps a fast track through the approval process? After all, since sandboxed apps are forced to be good citizens, approval would presumably require less investigation. And with the time saved by streamlining the process for sandboxed apps, Apple could spend more time investigating exactly what non-sandboxed apps are doing. Users would still benefit from the trust engendered by Apple’s approval process, and Apple could even build a revocation capability into the App Store app in the event that something bad were to slip through.
Developers currently find Apple’s approval process frustrating, unpredictable, and opaque, and they would undoubtedly do whatever was technically feasible to smooth it out. Those who couldn’t play within a sandbox would understand that the approval process would be longer and more drawn-out, but they wouldn’t be shut out of the Mac App Store solely for wanting to provide users features that aren’t possible in a sandboxed app.
One of the significant factors in this situation is that Apple’s communication with developers is weak at best. A number of developers we queried said that Apple was relatively communicative and helpful regarding questions about how to make sandboxing work. But for questions whose answers lie outside the sandbox model, developers are told to file bugs, which are then ignored, closed, or moved to “internal tracking.”
Long gone are the days when Apple had evangelists whose job it was to convince developers to adopt new Apple technologies and who in turn served as a communication channel for developers to talk back to Apple. Nowadays, nearly the only way to talk directly to Apple engineers is at the annual Worldwide Developer Conference, and even there, most of the communication travels from Apple to developers.
Perhaps if Apple were to reopen those lines of communication, it would be possible to come up with a solution that would work for everyone. In the meantime, it appears that sandboxing will make the Mac a safer and more reliable environment at the cost of stillborn innovations that would interact with the operating system and with other apps in novel ways. And that seems a shame.
TidBITS Watchlist: Notable Software Updates for 5 March 2012
Mac OS X 10.7.3 Supplemental Update — Apple has released Mac OS X 10.7.3 Supplemental Update, a tiny update to Lion that “resolves an issue when restoring a Mac from a Time Machine backup.” That’s it, Apple offers no other information. We’re guessing the issue in question was important enough to warrant this release now, instead of rolling it into a future system update. The update is small: only 38 KB on my MacBook Pro, although the standalone download is 24.55 MB. (Free, 24.55 MB)
Read/post comments about Mac OS X 10.7.3 Supplemental Update.
Hazel 3.0.1 — Noodlesoft has released Hazel 3.0, a paid upgrade to its file cleanup utility that features a revamped rule engine. At its core, the new rule engine uses a prediction engine so that Hazel wakes up only when it needs to, and it no longer polls the disk (save for a few exceptions), resulting in use of fewer system resources. The new version should also work better with external drives, as it won’t constantly re-run a rule if the drive is unavailable. Among Hazel’s many new features, highlights include scheduling support for rules via the new Current Time attribute, a new Sync action to synchronize
(one-way) a file or folder to another location, conditions for matching files when sorted for most/least recent, the capability to pause rule processing on a folder, and the capability to export custom tokens via AppleScript for use in patterns of subsequent actions. The new user interface enables you to reorder conditions and actions by dragging and uses popovers for easier rule editing. It’s rounded out by “tons of fixes and tweaks.” A quick 3.0.1 release addresses some crashing bugs and user interface problems. ($25 new, $10 upgrade, 4.7 MB, release notes)
Read/post comments about Hazel 3.0.
GraphicConverter 7.6.2 — Lemkesoft has released GraphicConverter 7.6.2, an update to the well-regarded graphics software that adds a number of new features. The new version’s additions include an unexplained Equalizer, support for IptcCore contact data, a shortcut for the Xe847 filter, font preview in the font popup, an indicator for display of images with unapplied XMP changes (used by Adobe Lightroom), and trackpad zooming during a slideshow. The update also fixes a possible bug with the Clipboard on Mac OS X 10.7 Lion, a crash during export of a slideshow as a movie, and many smaller bugs.
($39.95 new from Lemkesoft or from the Mac App Store, free update, 124 MB, release notes)
Read/post comments about GraphicConverter 7.6.2.
DEVONthink Personal, Pro, and Pro Office 2.3.3 — DEVONtechnologies has updated all three editions of DEVONthink (Personal, Pro, and Pro Office) to version 2.3.3. All three of the “smart information assistant” software titles add support for Adium chatlog files and Google Chrome bookmarks, improve indexing of OmniOutliner 3 files, add a contextual menu command for updating saved bookmarks, and provide more reliable indexing of Web archives with Safari 5.1.x or later. The Pro and Pro Office releases add a Delete Database option to the contextual menu for moving databases to the Trash, improve display
of unread items in news feeds when the option to display numbers inside groups is switched off, and fix instances where moving unsaved documents to other databases did not save them. For a complete list of additions, fixes, and improvements, see the release notes for the Pro Office edition, which covers all three editions. ($49.95/$79.95/$149.95 new, free updates, 17.7 to 28.6 MB)
Read/post comments about DEVONthink Personal, Pro, and Pro Office 2.3.3.
Firmware Update for MacBook Pro (15-inch, Late 2008 Models) — Apple has released MacBook Pro EFI Firmware Update 2.8, which specifically targets 15-inch models released in late 2008. This update resolves a graphics issue that may cause the internal display to flicker. To ensure you get the firmware update only if it’s necessary, we recommend relying on Software Update; if the update doesn’t appear for you, it’s not appropriate for your Mac. (Free, 1.8 MB)
Read/post comments about Firmware Update for MacBook Pro (Late 2008 15-inch Models).
HandBrake 0.9.6 — Continuing on its 12- to 14-month release trajectory, version 0.9.6 of the open-source video conversion program HandBrake has been released with a long list of encoding updates, tweaks, and bug fixes. At the top of the list, the release improves audio gain control, adds the MPEG-2 video encoder as well as AAC and FLAC (MKV only) audio encoders, improves handling of DVD subtitles, and improves the decomb filter. The release does not fix a break that occurred when VLC 2.0 was recently released (VLC provides the necessary DVD decrypting libraries) but the release notes provide a link to download the required libdvdcss
library file if you have updated to VLC 2.0. Live Preview window widgets are updated to work under Mac OS X 10.7 Lion, but support for 10.5 Leopard has been taken away. Be sure to read the detailed release notes for a complete list of updates and fixes, and to download the VLC library file. (Free, 7.1 MB)
Read/post comments about HandBrake 0.9.6.
Fetch 5.7.1 — Fetch Softworks has released Fetch 5.7.1, a maintenance update for the venerable file transfer client that’s full of fixes and corrections. The new version features a change in SFTP behavior to honor SSH config settings and avoid requiring a dummy password for connections using public key authentication. It fixes crashes in Mac OS X 10.7 Lion caused by the 3ivx video codec, and in 10.4 Tiger when Fetch was launched; instances where certain failed downloads weren’t automatically retried; and a problem that caused slow file list acquisition for folders with more than 10,000 items. Feedback is improved during
mirror and large transfer operations, as is compatibility with servers that take more than 30 seconds to start or finish a transfer. ($29 new from Fetch Softworks or the Mac App Store with a 20-percent discount for TidBITS members and free for educational users, free update from 5.5 or later, $10 upgrade for earlier purchases, 11.3 MB, release notes)
Read/post comments about Fetch 5.7.1.
TextExpander 3.4.1 — Gearing up for OS X 10.8 Mountain Lion, Smile has released TextExpander 3.4.1, which has been updated with the Smile developer ID that is used by Mountain Lion’s Gatekeeper security feature (see “Gatekeeper Slams the Door on Mac Malware Epidemics,” 16 February 2012). The release also improves expansion reliability in iWork applications, solves many instances of transposed letters, adds two use properties to AppleScript support, and adds a new Sort by Most Used capability. It’s rounded out by several
minor fixes. ($34.95 new with a 20-percent discount for TidBITS members, free update, 5.9 MB)
Read/post comments about TextExpander 3.4.1.
iMac Wi-Fi Update 1.0 — Apple has released the iMac Wi-Fi Update 1.0, which is recommended for all iMacs released since late 2009 that are running Mac OS X 10.7.3. The update resolves an issue that can prevent an iMac from automatically connecting to a known Wi-Fi network after waking from sleep. It’s available for direct download, but it’s easier to get through Software Update, where it will appear only if it’s necessary for your iMac. (Free, 25.81 MB)
Read/post comments about iMac Wi-Fi Update 1.0.
ExtraBITS for 5 March 2012
Two quick bits for you this week — Apple’s 25 billionth App Store download and the New York Times revelation that third-party apps to which you give location permission also get access to your photo library.
Apple Marks 25 Billion App Store Downloads — Apple sent out a press release over the weekend highlighting what just a short time ago sounded like an impossible milestone: the 25 billionth App Store download. (Yes, that’s ‘billion’ with a B — just imagine Carl Sagan saying it in “Cosmos.”) The celebrated app in question was Disney’s Where’s My Water? Free, a game where you help friendly Swampy the Alligator fix the plumbing in the city’s sewers where he lives so he can take a shower. The app was downloaded by Chunli Fu of Qingdao, China, who will be
receiving a $10,000 iTunes gift card.
iOS Apps with Location Permission Can Access Your Photos — Nick Bilton of the New York Times reports that a loophole in iOS’s security infrastructure enables apps you have allowed to determine your current location to access all the photos on your device (presumably due to the location information stored within photos). Although there are no known instances of this capability being abused in the wild, a proof-of-concept app commissioned by the New York Times showed that it could upload photos to a remote server once it had been given location permission.
Apple will likely fix this soon; in the meantime, we recommend turning off unnecessary permissions in Settings > Location Services.