TidBITS#1191/16-Sep-2013
We’re sending our summer out in style with a giant-sized issue of TidBITS! Apple has unveiled the latest iPhones — the colorful iPhone 5c and the powerful iPhone 5s, and we have all the details. Note that Apple has lowercased the trailing letters in those iPhone names, and retroactively demoted the S in iPhone 4S as well. Adam Engst fulminates about Apple’s use and abuse of capitalization. The big news about the iPhone 5s is that it includes a fingerprint scanner, called Touch ID, and Security Editor Rich Mogull explains how the technology works. In other Apple news, purchasers of new iOS devices will receive a bevy of free apps from Apple, and OS X 10.8 Mountain Lion has been updated to version 10.8.5 to fix some major security holes. Finally, bibliophile Michael Cohen helps you figure out what to read next with a look at book recommendation engines in our latest FunBITS piece. Notable software releases this week include Microsoft Office 2011 14.3.7, SpamSieve 2.9.8, Security Update 2013-004 for Lion and Snow Leopard, Safari 5.1.10 for Snow Leopard, and Nisus Writer Pro 2.0.5 and Express 3.4.4.
Apple Announces Low-Cost Plastic iPhone 5c, in Five Colors
TidBITS Managing Editor Josh Centers called it, in “The Case for a Low-end Plastic iPhone” (24 July 2013), as Apple last week announced the low-cost iPhone 5c, a new iPhone whose specs are similar to the existing iPhone 5, but housed in a colorful plastic case.
With Apple’s Jony Ive saying “iPhone 5c is beautifully, unapologetically plastic,” the iPhone 5c comes in a single-piece polycarbonate case, with every button and part (other than the screen) in color. As its name implies, it’s available in five colors, all reminiscent of brightly hued Easter eggs: blue, white, pink, yellow, and green.
Also available will be the iPhone 5c Case for $29, a silicone case available in six colors with polka dot-like cutouts on the back, so you get a two-tone effect between the case and the back of the iPhone. The cutouts are an odd design choice, in that they reveal a jumble of the text on the back of the iPhone, and are likely to pick up dirt and pocket lint.
For those more concerned with tech specs than the iPhone 5c’s pretty colors, it sports a 4-inch Retina display, an A6 processor, an 8-megapixel rear-facing camera, 802.11a/b/g/n Wi-Fi in both 2.4 and 5 GHz bands, and Bluetooth 4.0. There’s also a new FaceTime HD front-facing camera that boasts larger pixels, improved backside illumination, and support for FaceTime audio. The iPhone 5c’s battery has a slightly higher capacity than the iPhone 5’s.
Apple emphasized that the iPhone 5c supports more LTE bands than any other phone, which may make it better suited to emerging markets throughout the world, where the iPhone’s higher price has been something of a stumbling block to adoption.
In terms of dimensions, the iPhone 5c is slightly larger than the iPhone 5, gaining 0.6 mm in both height and width, 1.37 mm in depth, and 20 g in weight. The changes aren’t major, but will cause many iPhone 5-specific cases and accessories to need design tweaks.
The real news, though, is the price, which will be $99 for a 16 GB model or $199 for a 32 GB model, with a two-year contract. Off contract, the iPhone 5c will cost $549 for the 16 GB model and $649 for the 32 GB model.
The iPhone 5c, along with the simultaneously announced iPhone 5s, replaces the iPhone 5 entirely (see “iPhone 5s Announced, Knows You by Touch,” 10 September 2013). That’s important, because, as Josh speculated, had Apple stuck to the previous model of iPhone 5 at a lower price, it would likely have been a poor financial move, due to the relatively high cost and low yield of the iPhone 5. The 8 GB iPhone 4S will remain in the lineup for free, with that two-year contract.
Pre-orders opened for the iPhone 5c on 13 September 2013, with in-store availability (and presumably shipped phones) on 20 September 2013. It will be available in the United States, Australia, Canada, China, France, Germany, Japan, Singapore, and the UK to start, with 100 countries and over 270 carriers included by December 2013.
iPhone 5s Announced, Knows You by Touch
Apple last week announced the iPhone 5s in three colors: gold, silver, and “space gray.” No pre-order availability was announced for the 5s, unlike the simultaneously announced iPhone 5c (see “Apple Announces Low-Cost Plastic iPhone 5c, in Five Colors,” 10 September 2013), but the phone itself will be available on 20 September 2013 in the United States, Australia, Canada, China, France, Germany, Japan, Singapore, and the UK to start, with 100 countries and over 270 carriers included by December 2013. The iPhone 5s lineup and pricing remain similar to previous models, with a 16 GB model for $199, a 32 GB model for $299, and a 64 GB model
for $399 (all with, of course, the obligatory two-year contract).
The iPhone 5s is a notable upgrade over last year’s iPhone 5, with identical casing but a number of significant internal improvements. It features Apple’s new A7 system-on-a-chip, with up to 56 times more graphics performance than the original iPhone. The A7 is also the first, and so far only, 64-bit CPU architecture for mobile phones. iOS 7 and its included apps have been re-engineered for 64-bit support, and Apple’s development platform, Xcode, has been updated to enable
developers to develop both 32- and 64-bit versions of their apps simultaneously.
Also new is Apple’s M7 motion coprocessor. The M7 chip takes measurements from the accelerometer, compass, and gyroscope without waking the A7, presumably offering better battery life for motion-sensing apps, like fitness trackers. Apple is integrating M7 support into its Core Motion API, and Nike is already developing an app, called Nike+ Move, that uses the updated API.
Speaking of battery life, the iPhone 5s purportedly can provide 10 hours of 3G talk time (up from 8 on the iPhone 5), 10 hours of browsing over Wi-Fi, 40 hours of life when playing music, and 250 hours (up from 225) of charge on standby.
The camera system in the iPhone 5s also features significant improvements, including a 15 percent larger sensor with larger pixels to provide better color and less noise, an f/2.2 aperture (the iPhone 5 featured an f/2.4 sensor) for better low-light pictures, and a new five-element Apple-designed lens. Also new is the “True Tone” flash, which features two LEDs, one cooler and one warmer, that can be mixed for better skin tones. The camera features an image-stabilization feature that combines multiple shots to produce a sharp photo. It also boasts a burst mode at 10 frames per second, 28-megapixel panoramas, and 120-frames-per-second slow-motion video at 720p. You can even take a still photo while shooting video.
The camera’s software has also been made smarter — for example, it chooses the best of the burst mode pictures to show you first, adjusts the True Tone flash automatically depending on external conditions, and continually alters the exposure as you pan while taking panorama photos.
Perhaps the most drastic outward change to the iPhone 5s is its new Touch ID fingerprint scanner, built into the home button (see “Q&A about Fingerprint Scanning,” 10 September 2013). The capacitive sensor, which is 170 microns thick and has a resolution of 500 pixels per inch, can unlock the iPhone or authorize iTunes purchases with just the touch of a finger. The Touch ID scanner can learn up to five fingerprints and can capture a fingerprint from an angle. Should you not wish to (or be able to) use the fingerprint scanner, there is an option in iOS 7 to use a password instead of a fingerprint scan. The home button itself can still be pressed for standard behaviors, though gone is
the rounded square icon that has been an iPhone standard since day one.
In terms of industrial design, Apple has traded the black and white dichotomy for three options: gray, silver, and gold. In each case, the metallic color occupies the edge of the phone and the bulk of the back. For the gray model, the face (apart from the screen, obviously) is black; for the silver and gold models, it’s white. We’ll be curious to see how the different colors sell — the gold seems pretty gaudy to our eyes.
To be released alongside the iPhone 5s is the iPhone 5s Case, a $39 leather case available in five colors: black, brown, beige, yellow, blue, and Product(RED), the last of which will have proceeds donated to the (RED) AIDS charity. Like the iPad Smart Cover, the iPhone 5s Case features a microfiber lining to keep the phone clean. The dye has been infused into the leather, so hopefully we won’t see the color rub off like it did with the leather Smart Covers. The iPhone 5s Case is also compatible with the iPhone 5, since the two phones have exactly the same dimensions. That should make accessory manufacturers happy too.
Additionally, Apple is getting back into the dock business, with docks for both the iPhone 5s and iPhone 5c. The new iPhone 5s Dock features a Lightning connector, a line-out port to connect your iPhone to powered speakers, and hands-free calling thanks to “special audio porting.” It costs $29 and is also compatible with the iPhone 5, but unfortunately does not include a Lightning-to-USB cable.
OS X 10.8.5 Fixes Nasty Text Rendering Bug
While Apple continues to move toward the upcoming debut of OS X 10.9 Mavericks, the company has quietly pushed out OS X Mountain Lion Update 10.8.5 with a handful of stability and performance fixes. The free update is available via the Mac App Store, with delta (273.72 MB — from 10.8.4) and combo (831.13 MB — from any previous version of 10.8) updaters ready for download from Apple’s Web site. Though we haven’t heard of any significant problems with the update, it’s always a good idea to wait a few days to see if any arise.
Bugs fixed include one that prevented Apple Mail from displaying messages, another that stopped the screensaver from starting automatically, and a third that stopped a smart card from unlocking preference panes in System Preferences. The update also enhances performance in three areas: AFP file transfers over 802.11ac Wi-Fi, large file transfers over Ethernet, and Open Directory authentication. Also, the update improves Xsan reliability and bundles in the bug fixes in MacBook Air (Mid 2013) Software Update 1.0 (for details, see “MacBook Air (Mid 2013) Software Update 1.0,” 22 July 2013).
But perhaps the most important change is one Apple mentioned only in a note at the end of the update’s security release notes: a patch for a nasty text rendering bug that could cause Messages and Safari to crash, and cause Wi-Fi errors if a network was named with the characters in question (see “Text Display Bug Can Render Apps Unusable,” 30 August 2013). After installing 10.8.5, we tested sample URLs that had previously caused crashes, and can confirm that Apple has squashed this bug, which had already been fixed in iOS 7 and Mavericks. It presumably still exists in the current iOS 6.1.3; we anticipate a 6.1.4 update to iOS to fix it as well.
OS X Mountain Lion Update 10.8.5 also includes a variety of security improvements, most notably a fix for an issue where an attacker could gain superuser access by resetting the system clock. (For details, see “Hackers Can Root Macs by Going Back in Time,” 30 August 2013.)
Also plugged are security holes in CoreGraphics, ImageIO, and QuickTime that could permit malicious PDFs or movie files to cause application crashes or arbitrary code execution.
Additionally, the update fixes other user-level vulnerabilities, including Installer packages that could be opened after certificate revocation, a bug that could allow users with screen sharing access to bypass the screen lock, and a vulnerability in Mobile Device Management that could disclose passwords to local users.
Finally, 10.8.5 addresses a number of security vulnerabilities on the Unix end, via updates to the Apache Web server, the BIND DNS server, the ClamAV virus scanner, the IPSec security package, the PHP scripting language, and the PostgreSQL database. Plus, a bug in the kernel was fixed that could enable a local denial of service attack.
iWork, iPhoto, and iMovie Free with New iOS Devices
Along with the major announcements of the iPhone 5c and 5s during last week’s special event, Apple CEO Tim Cook threw in a brief bit of self-congratulatory praise for the company’s iWork suite for iOS — Pages, Keynote, and Numbers — along with the iOS versions of iPhoto and iMovie. And then
he raised the bar significantly for competing apps by announcing that all five would be free for purchasers of new iOS devices from now on, with the option to download appearing during the initial device setup.
Oddly, GarageBand for iOS was not included in the announcement, even though the iLife suite of iPhoto, iMovie, and GarageBand is bundled with all new Macs.
Given that the iWork apps each cost $9.99 and iPhoto and iMovie are $4.99 each, Apple just added nearly $40 worth of software to every new iPhone, iPad, and iPod touch sold, a non-trivial bonus for relatively inexpensive devices. Presumably, those who currently own iOS devices but don’t yet own these apps must still buy them.
Since the announcement was focused entirely on iOS and iOS devices, it wasn’t surprising that Apple failed to say anything about iWork for the Mac, which has seen no significant updates for nearly five years while Apple focused on bringing the suite to iOS. Perhaps iWork for Mac will get some attention at the forthcoming release of OS X 10.9 Mavericks, although we’ve already happily switched from Pages to Nisus Writer Pro for Take Control.
Q&A about Fingerprint Scanning
Apple last week announced a new flagship iPhone, the iPhone 5s (see “iPhone 5s Announced, Knows You by Touch,” 10 September 2013). From a security standpoint, the most interesting addition to the device is its integrated fingerprint scanner, called Touch ID, which enables you to unlock the phone with the touch of a finger, rather than a passcode. You’ll also be able to make purchases from iTunes with a fingerprint scan rather than having to enter your Apple ID password.
But despite the believed uniqueness of fingerprints, using a fingerprint scan as an authentication credential isn’t a panacea for security problems. It’s worth taking a little time to understand the technology, what it can do, and how it will integrate with your digital life.
How does a fingerprint reader work? — Fingerprint recognition technology has been around for decades. It’s a form of authentication, the term used to describe the process of proving you are who you say you are. In this case, the technology scans the provided fingerprint, compares it to a database, and, if there’s a match, allows access just as a password or passcode would. While fingerprint recognition technology can technically identify you as well as authenticate you, most systems still require a username to speed up fingerprint matching and reduce errors. However, since the iPhone
stores your Apple ID username, this won’t be an issue for most users.
Fingerprint readers can rely on a variety of scanning technologies. The two that can be best integrated into a mobile device are optical readers and capacitance sensors. Optical readers are conceptually simple, using what is essentially a digital camera to take an image of your finger surface.
Capacitance sensors are more complex, instead creating an image of your fingerprint by measuring the differences in capacitance between the ridges and valleys of your fingerprint. They leverage the electrical conductivity of your sub-dermal skin layer, and the electrical insulation of your dermal layer (the one where your fingerprint is). Your fingerprint is effectively a non-conductive layer between two conductive plates, which is the very definition of a capacitor. The fingerprint reader senses the electrical differences caused by the varied thickness of your dermis, and can reconstruct your fingerprint from those readings.
The Touch ID sensor in the iPhone 5s is a capacitive reader, embedded in the home button. That was a good choice on Apple’s part, since capacitive scanners are more accurate and less prone to smudgy fingers, and can’t be faked out with a photocopy of a fingerprint.
So the reader takes a picture of my finger and looks it up in a database? — Not quite. Comparing complete images is a complex — and computationally intensive — task that even powerful computers struggle with. Instead, the image from the reader is run through an algorithm that pulls highlights from your fingerprint and converts them into a digital summary — a template — that is easier to work with. This template represents your fingerprint, and varies based on the algorithm used.
The template is then stored in a database, ideally after being run through a cryptographic hashing function, just like your passwords. Passwords themselves are never stored; instead they are converted by a one-way encryption algorithm, with the result being stored in the database. Done properly, this means your password can never be recovered, even if a bad guy gets the database.
Although details aren’t yet known, we expect that Apple uses each iPhone’s unique device code as part of the hashing algorithm. Since it’s embedded in the iPhone’s hardware, it’s effectively impossible to attack off the device with more powerful computers; on-device attacks are much slower and more difficult.
When you use your fingerprint to log in to a device, the technology images your fingerprint and runs the image through its algorithm. Then it compares the result with the value stored in the database. If the two match, you are let in just as with a password.
Apple made it a point to note that your fingerprint will never be uploaded to iCloud or any Internet server. Instead, it will be encrypted and stored in what’s called the Secure Enclave within the A7 chip itself.
Is a fingerprint more secure than a password or passcode? — Not necessarily. In the security world, there are three ways to prove that you are who you say you are, with something you know, something you have, and something you are. Something you know is a passcode or password; something you have is a token, key, or even your phone; and something you are is a “biometric identifier,” like your fingerprint.
Using any one of those identifiers is known as single-factor authentication, and it’s considered strong authentication when you combine two or more factors. If you think about it (or watch enough TV), you can easily imagine ways to fool a fingerprint reader, ranging from a photocopy to a fake finger made from gelatin. Every fingerprint reader can be deceived, and doing so doesn’t necessarily require high technology.
Plus, if you have physical access to the database, you can run attacks against it just as though it contained passwords, by generating and testing fake templates. Not all algorithms and hashing functions are equally good, and it is easy to end up with a system that is weaker than the well-known ways we manage passwords.
In short, nothing is perfect, and a fingerprint alone isn’t necessarily more secure than a password. Worse, you can’t change your fingerprint. That’s why super-secure systems usually require a fingerprint and either a password or smart card.
Doesn’t my phone count as a second factor? — Sort of. Many of you may use your phone as a second factor to log in to services like Dropbox. In that scenario, you log in to the site with your username and password, and then Dropbox sends a one-time code to your phone, which it has on file. Since you know your password and have your phone, this counts as two-factor authentication.
Unfortunately, unlocking your phone is different, since the phone itself is the target. Thus, a fingerprint alone is still single-factor authentication, and not really more secure in a strict sense.
However, you are much less likely to loan someone your fingerprint, and while a bad guy might guess your passcode, the odds of someone stealing a copy of your fingerprint in the real world are very low, unless you are a high-risk target.
If it isn’t more secure, why switch to a fingerprint? — Practically speaking, for most consumers, a fingerprint is more secure than a passcode on your iPhone. It’s definitely more secure than a four-digit passcode.
But the real reason is that using fingerprints creates better security through improved usability. Most people, if they use a passcode at all, stick with a simple four-digit passcode, which is easy for an attacker to circumvent with physical possession of your iPhone. Longer passphrases, like the obscure 16-character one I use, are far more secure, but a real pain to enter repeatedly. A fingerprint reader, if properly implemented, provides the security of a long passphrase, with more convenience than even a short passcode.
As I wrote over at Macworld, Apple’s goal is to improve security while making it as invisible as possible.
Does this mean the death of passcodes on my iPhone — Not at all. First of all, iOS isn’t about to get rid of passcode support since only the iPhone 5s will have a fingerprint reader.
Second, as you can see in this image, you will always have the option of inputting a passcode instead of scanning a fingerprint.
Third, while many of us share our iPhones with our spouses and children, Apple officially supports only a single user per device. However, Apple has said that Touch ID will allow you to set up fingerprints for trusted friends and family, so they can easily access your device.
If someone steals my phone, does that mean they have my fingerprint? — Almost certainly not. There’s no reason to keep the fingerprint itself, just the template. And as mentioned previously, your fingerprints are encrypted on the iPhone 5s (we suspect Apple really means “hashed”).
Can someone gain access to my phone with a copy of my fingerprint? — Probably. As I mentioned earlier, unless you combine your fingerprint with another authentication factor, like a passcode, an attacker needs one piece to pretend to be you.
Realistically, almost no one needs to worry about this, although I fully expect there to be a number of articles written about the efforts of amateur spies to make fake fingers. I will also start being more careful when I attend certain hacker conferences, given my prankster friends.
Will I be able to log in to my bank with my fingerprint, instead of a password? — Using your fingerprint to log in to Web sites and apps, like those from your bank, might happen eventually, but not right away. Apple must first open up API support for it, then developers need to integrate it into both their apps and the back-end authentication databases. Apple said that other apps can use the fingerprint reader, but that your stored fingerprint won’t be available to those apps. Thus we suspect initial support will be using Touch ID to access a password stored in the iOS keychain, using API support of some sort.
App makers and cloud services who want direct fingerprint access, if Apple even supports it, will also need to redesign their systems to deal with scenarios like someone’s fingerprint being compromised, or a user who also logs in from a Windows-based computer that has a different fingerprint scanner. They can’t simply switch everyone to Apple-only fingerprint templates. (And as much as having an open standard for generating the templates might sound like a good idea — there’s even an industry organization called the FIDO Alliance to promote such interoperability — who knows if Apple would eventually support it.)
But again, I highly suspect Apple will, at least for a while, mostly rely on securing credentials on the phone using the venerable Keychain, perhaps adding a feature or API support that asserts the fingerprint for that registered user was authenticated.
Also, banks are legally required to use two forms of authentication. That’s why you likely have to enter a PIN when you log in from a different device, or you must do the email confirmation dance when you log in from a new computer. Technically, though, your phone could count as a second factor, and banks could update their systems to combine the fact of having your phone with your fingerprint for access.
Will I be able to use my fingerprint to log in to my work network? — Not right away. Although Apple is adding enterprise-level single sign-on (SSO) support in iOS 7, your work network and applications will still need you to authenticate using your existing username and password. SSO merely means you don’t have to re-enter those credentials for every work system. Over time I expect to see vendors offer tools to allow you onto your work network after you authenticate using your fingerprint on your iPhone, assuming your IT department approves.
Why is this so important? — Apple isn’t the first company to add a fingerprint reader to a phone. I’ve tested laptops with fingerprint readers and seen phones with embedded readers. The real excitement is that Apple will make this technology accessible to many millions of consumers.
Doing so will dramatically improve the security and usability of the iPhone 5s for average users. I hate needing to enter a strong passphrase on a tiny keyboard, especially when I’m walking around. A fingerprint reader will be far more convenient, and essentially eliminate the less secure four-digit passcodes most people use, if they use one at all.
Combine this with the fact that many users now use their phones as a second factor when logging in to a variety of cloud services, and you can see that improving the security of the iPhone 5s could generally improve the security of significant aspects of the Internet. That won’t happen overnight, but improving security at any access point improves security for the entire system.
Once we see usable fingerprint authentication made widely available for consumers, life for the average attacker is going to get a lot harder.
Ruminating about Apple’s Lowercase Letters
Why do you do it, Apple? Why did you feel the need to switch the iPhone’s trailing letter from uppercase to lowercase?
Tonya and I spend hours every day poring over Take Control manuscripts and TidBITS article drafts, reorganizing sections, recasting awkward sentences, mending grammatical missteps, fixing typos, eliminating errant spaces, and checking for consistency. It’s a compulsion, bordering on a curse, and Strunk knows that we’re far from perfect, but we try.
Most of the time, no one notices, and that’s the goal — such blunders get in the way of our mission, which is to communicate information and ideas clearly and accurately. (I would be remiss if I failed to give a quick shout-out to our friend Chris Pepper, whose skill in spotting mistakes in our articles could land him a lucrative career in proofreading, should he ever tire of Unix system administration.)
Our efforts require constant vigilance and knowledge of a vast amount of arcana, such as the missing space and capitalized P in QuarkXPress. For the most part, we try to honor whatever naming conventions companies come up with, apart from non-acronym all caps (Nvidia, I’m looking at you) and trailing punctuation (perhaps Yahoo’s exclamation point is now meant to be ironic).
Small, but Annoying — So what’s with Apple suddenly changing from uppercase letters in the iPhone model name to lowercase? They started with the iPhone, then jumped to the iPhone 3G, because of its 3G compatibility. Reasonable enough, but when the time came to revise that model, Apple decided to add an S to the name (to indicate that it was speedy, snazzy, and sophisticated, perhaps), and, for one dark week or so, put a space between the 3G and the S, as in “iPhone 3G S.” I don’t know that I can claim credit for Apple’s reversal after having complained vociferously about the name in our initial coverage (see “New
iPhone 3GS Boosts Power, Performance, and More,” 8 June 2009), but I was exuberant to see Apple close up the space (see “Ding, Dong, the iPhone 3GS Space Is Dead,” 22 June 2009). Next came the iPhone 4, and, with no nomenclatural surprise, the iPhone 4S, followed by the iPhone 5. Truth, reason, and the Oxford comma ruled supreme.
(During this time, alas, Apple reverted from the reasonably named iPad and iPad 2 to the confusing iPod naming scheme, such that our article about the iPad 3 had to explain that it would officially be called just “iPad” again, forcing us to prefix it repeatedly with “third-generation” (see “Apple Announces Third-Generation iPad,” 7 March 2012). That continued with the fourth-generation iPad (not iPad 4), likely to make room for the iPad mini. It seems likely that we’ll soon see a fifth-generation iPad instead of an iPad 5 and a second-generation iPad mini in favor of an iPad mini 2.)
With Apple’s announcement of the replacements for the iPhone 5, it was only logical that the new models would be called the iPhone 5S and iPhone 5C, and if you look at liveblogs and early drafts of articles, that’s what everyone wrote. But it wasn’t to be. As part of our consistency checking, we glanced at Apple’s press releases before we published and discovered that Apple had demoted the letters, giving us the iPhone 5s and 5c instead. Worse yet, it was soon discovered that Apple had gone back to rewrite history, renaming the iPhone 4S to the iPhone 4s.
Plurals and Possessives and Bears, Oh My! — From the perspective of someone who lives and breathes text, this is a wrong-headed move, because it both is inconsistent and introduces confusion-causing ambiguity, not just into everything that’s written from now on, but also into the historical record. From now on, whenever you see the phrase “iPhone 5s” in a sentence, you’ll have to read carefully to determine if it’s talking about the new iPhone 5s, or several iPhone 5s. In some cases, there may be no way of knowing what’s meant — you can’t know what I’m referring to when I write “The iPhone 5s flew off shelves.” John Gruber also talked about this briefly on Daring Fireball a year ago. Luckily, the difference is clear in spoken English, where one is “five-ess” and the other is “fivez.”
At least it was possible to pluralize iPhone 5; how would you do that with iPhone 5s? iPhone 5ss? That’s just ssilly. iPhone 5ses? Phonetic, but awful. iPhone 5s’s? This last one looks terrible, like an awkward possessive, but “The Chicago Manual of Style” (our go-to guide for these sorts of questions, as opposed to John Gruber’s preference for “The New York Times Manual of Style and Usage”) says to use the apostrophe to form the plural of lowercase letters, as in: “Mind your p’s and q’s.” It also says to use the apostrophe to form the plural of an abbreviation that combines upper and lowercase
letters or has interior periods, as in: “He has two Ph.D.’s.”
On the other side of the fence, the Chicago Manual says not to use an apostrophe to form the plurals of capital letters used as words, abbreviations that contain no interior periods, and numerals used as nouns, as in: “In education in the 2000s, the three Rs were joined by URLs.” So although the Chicago Manual is silent on the combination of letters and numbers Apple used in “iPhone 5s,” I believe it would come down on the side of an apostrophe-based plural. (We won’t suggest the William Safire approach, at least as satirized by the Onion, which would suggest “iPhones 5s.”)
That then leads to the question of how to form the possessive of the plural, if you wanted to discuss “the cases of the iPhone 5s’s on the table.” The logical conclusion would be to say “the iPhone 5s’s’ cases on the table,” a clause useful mostly for causing copy editors to throw themselves from windows. The carnage would be defenestrating.
Laying Down the Law, or at Least the Style Guide — What then, are our options? I believe strongly in honoring the names chosen by creators, which is one reason why TidBITS follows the style of Tim Berners-Lee and the World Wide Web Consortium in capitalizing “Web” when it stands alone as a word. From that standpoint, we will grin and bear the lowercase “iPhone 5s” and “iPhone 5c.” They are Apple’s names, and Apple gets to say.
However, I stop short of allowing any person or company to decree that previously used names are now wrong, so we will stick with the original “iPhone 4S” capitalization. This is actually the second time Apple has changed the name of a major product mid-stream — at some point during the reign of Mac OS X 10.7 Lion, Apple suddenly started dropping the “Mac” and referring to the operating system as merely “OS X Lion.” We refused to honor that flip-flop, but when it was time for the next big cat, we acceded and called it OS X 10.8 Mountain Lion.
(As an aside, the best snarky comment generated by this discussion on Twitter came from Arik Dreyer, who slyly noted that Apple’s lowercase treatment of the 5s and 5c was consistent with Mavericks and Maverickc.)
In the end, what we’ll actually do is what we’ve done all along, which is write around these awkward constructions. Much as I dislike the inconsistency of having to capitalize some iPhone names and not others, the reality is that plurals in particular have long been worrying, so we try to avoid them. Such rewriting might involve recasting my final example above to something like “the case of each iPhone 5s on the table.”
We hope that, as is always our desire, you simply won’t notice such textual contortions.
Blame the Glyphs — So why did Apple make this change? Apple PR hasn’t deigned to reply to my query on that topic, and I’ve seen speculation that the 5 and the capital S were somehow too similar, particularly in Helvetica Neue. I’m not buying that argument in particular, for the simple reason that Apple almost always uses a special boxed form of the letter when typography is in question, as you can see in my collection of screenshots from Apple’s iPhone pages through the years.
I suspect we’ll never know why Apple decided to switch to lowercase letters, just as we’ll never know why the company decided to drop Mac from the name of its operating system. The reasons might be complex and intertwined with numerous future business decisions (perhaps capital letters are considered bad luck in China?), or they may simply be capricious, because Jony Ive decided it looked better.
It’s worth remembering that, for the most part, the concerns I’ve laid out above seldom come up for Apple itself. Apart from the department that writes support articles (also the only group within Apple that is forced to struggle with the company’s constant reuse of names), it’s uncommon for Apple to depart from the curiously formal trademark usage, where plurals and possessives don’t come into play. Apple marketing material consistently uses iPhone 5s as a proper name, as in: “iOS 7 was designed with iPhone 5s in mind.”
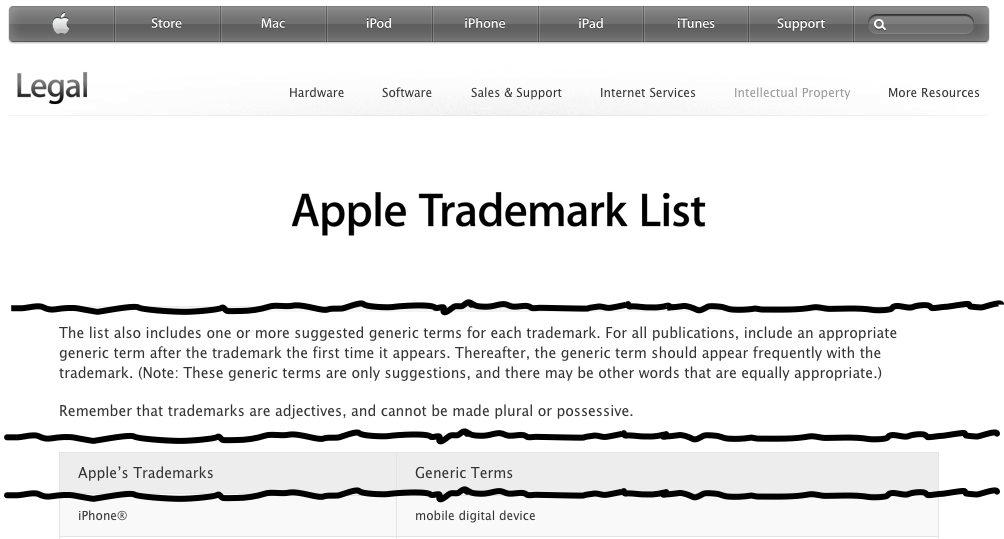
No one but Apple talks that way, but that doesn’t mean Apple wouldn’t like you to. For some wonderfully delusional thinking that may explain Apple’s lack of concern with reader confusion, check out Apple’s Guidelines for Using Apple Trademarks and Copyrights, where you’ll learn that trademarks are adjectives used to modify nouns, where the noun is a generic name of a product or service. As adjectives, Apple says, trademarks may not be used in the plural or possessive form.
Aha! Now we’re getting somewhere! With a quick trip to the Apple Trademark List to discover what the generic term for the iPhone is, we discover that we should actually be using it in a form like this: “I’m sure we’ll be hearing more about the iPhone 5s and iPhone 5c mobile digital devices in the future!” We’ll get right on that.
FunBITS: Finding Something Good to Read
Recently, while TidBITS managing editor Josh Centers was swinging through the virtual air on his Sky-Hook and hurling fireballs at various enemies (see “FunBITS: In Praise of BioShock Infinite for Mac,” 6 September 2013), I was amusing myself with a more traditional form of entertainment (albeit also virtual, courtesy of my iPad): reading a good book or ten.
That “ten” is not a typo: I tend to read books like some people inhale potato chips, and all too frequently the page indicator in iBooks or the Kindle app becomes a harbinger of anxiety as it approaches the right side of the screen, a sign that I’m approaching the end of the current book. Yes, I say “anxiety” because it means I’ll soon have to go questing for another book to avoid being stranded in reality with nothing good to read. So, when Josh took a few minutes off from killing pixelated baddies to ask me to examine a few sites that offer to help readers find their next page-turning adventure, I was intrigued.
Such reader recommendation sites go beyond the typical lists of recommendations that one might find on Amazon or in Apple’s iBookstore. You see, book store recommendation engines work by correlating your purchase history with similar purchases by other customers (along with some algorithmic secret sauce) to suggest books you may want to buy — and that would be OK, I suppose, if you used just one online book store, and bought all of your books through it.
But I don’t. My online purchases tend to be distributed among various vendors, and, even then, those purchases reflect only a fraction of my recent reading; I have a large library of books, digital and physical, that has accumulated over decades, and I also have easy access to a public library, plus bibliophilic friends who often loan me their favorites. The range of books that I read is thus far more varied and extensive than the few hundred book purchases that Amazon and Apple know about.
To come up with recommendations, dedicated book recommendation sites perform a similar set of tricks, but they aren’t limited to your purchase history. Instead, you supply titles and authors that interest you to prime the recommendation pump. Therefore, before I began looking at the sites that Josh had sent me, I compiled a pump-priming list of authors and titles by picking them randomly from both my physical and virtual bookshelves. My list contains authors both popular and obscure, and books that reflect the range of my interests and predilections, with representative titles that run the gamut from pure pulp to post-modern literature. I limited the books on my list to novels for this experiment, and included only books I wouldn’t
mind reading again. (See the full list at the end of the article.)
My goal was to see how easily and quickly I could find good recommendations from these sites. Although most recommendation sites give better results when you give them more time and data to work with, I put myself in the position of someone who just wanted something to read and had stumbled upon a recommendation site for the first time.
(An aside. Some book recommendation sites base their suggestions on your social graph, looking at what your friends read. I believe this approach is largely flawed. In today’s Internet, it’s easy to be “friends” with people whose literary tastes are completely unknown, and just because I’m friends with another tech writer says nothing about overlap in our reading preferences. Even with a real-life friend, while I’m more than happy to accept a recommendation for a book my friend believes I’d like based on our shared history or a conversation we’ve had, that doesn’t mean I’d be interested in everything my friend reads. This, by the way, is a good place to mention Goodreads, which
is a great site to visit for reader reviews of books that you are already considering.)
And so my quest began…
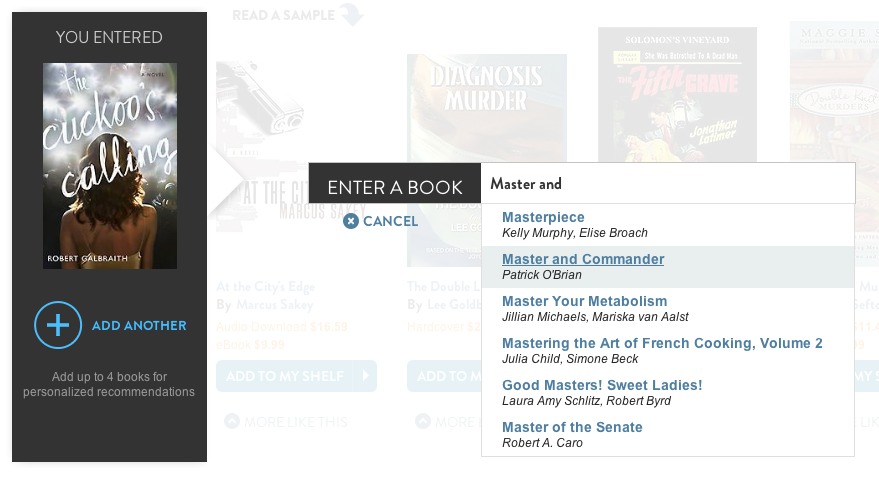
Bookish — The Bookish site is typical of the genre: you can go there and immediately enter a book title to solicit recommendations. You can enter only books from the roughly 250,000 titles that Bookish “knows” about: as you type, a pick list of matching titles appears, and you click an offered title to use it as the basis for generating recommendations — if the title you type doesn’t appear in the pick list, you can’t use it. Fortunately, Bookish knew about each of the titles I submitted.
However, the recommendations produced by a single title submission are as general as you might expect. The more titles you supply, the better the recommendations, but to enter more than one title into Bookish, you must create an account by supplying a valid email address and a password.
With a registered Bookish account, you can enter up to four titles to serve as the basis of your recommendation request. Bookish’s recommendation engine then churns through its database and gives you a side-scrolling list of books you may want to consider reading. I chose four books from my full list:
- “The Cuckoo’s Calling” by Robert Galbraith (a.k.a. J.K. Rowling)
- “Gravity’s Rainbow” by Thomas Pynchon
- “Master and Commander” by Patrick O’Brian
- “The Game of Kings” by Dorothy Dunnett
The Bookish suggestions elicited by my somewhat eclectic set of titles were fascinating: nearly all were well-respected novels that one might find on the syllabus of an undergraduate literature course, and most were books I both owned and had previously read. Kudos for taste, at least, and for discerning something about my literary predilections, but not very useful in this particular instance: I didn’t see anything listed that was both new to me and piqued my interest.
Bookish allows you to save recommended books, and other books as well, to “shelves” when you have an account, but these are only memory aids — you can’t use your shelves’ contents as a source for recommendations. And thus, with a seed of no more than four titles, Bookish isn’t terribly useful as a recommendation engine in general. In fact, the recommendation engine, though prominent on the home page, is not really the site’s reason for existing: Bookish is really an ebook vendor, complete with the Bookish Reader app in the App Store. The recommendation engine exists primarily to sell you more books through Bookish.
What Should I Read Next? — Like Bookish, the What Should I Read Next? (WSIRN) site requires that you register before it lets you enter more than one title as the basis for recommendations; unlike Bookish, it requires only an email address and not a password.
Once you have registered, you can provide multiple titles to get suggestions. What’s more, you can also supply author names and ISBNs. Though the interface is not as visually engaging as the Bookish site’s is, I appreciated the flexibility.
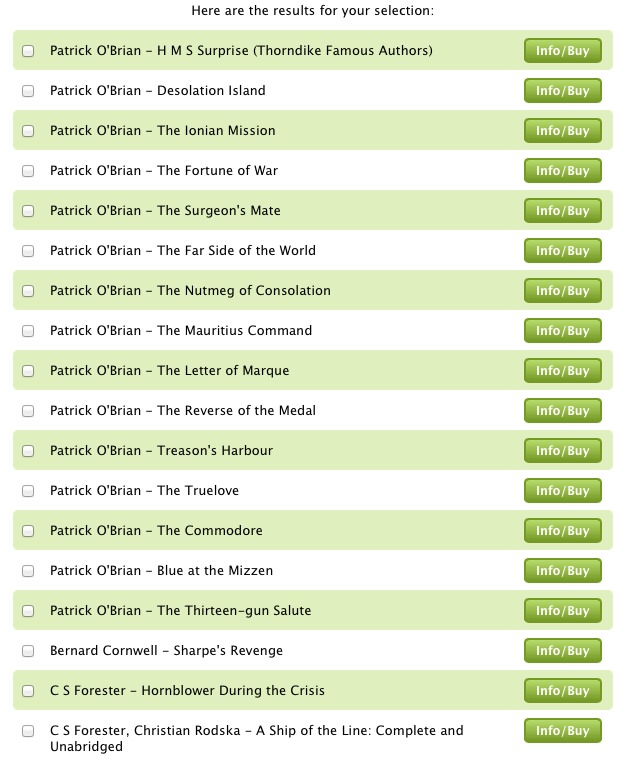
I gave WSIRN the same four books I had entered into Bookish and the results were… interesting. For some reason, the engine fixated on the O’Brian novel and presented me with a list that began with nearly all of O’Brian’s works; I had to scroll down a ways before finding a book by anyone else. As I scrolled through the list (much longer than that provided by Bookish), I came upon a curious entry: “At-Swim-Two-Birds” by Flann O’Brien — a masterpiece of Irish metafictional humor, but a far cry from Napoleonic
naval combat. Whether it appeared on the list because of the author’s (pseudonymous) surname or for some other reason I can’t guess.
However, since WSIRN allows you to enter more than four works to get recommendations, I next gave it the full list of my twelve favorites. The suggestions I got back were more diverse, though they still led off with more O’Brian seafaring yarns, along with maritime tales by others as well. The titles that followed were heavy on classics too (Wordsworth’s “The Prelude”? Really? I have an ugly history with that work.), but the list did contain some promising suggestions.
In practice, here’s how you’d use the site. When it comes up with recommendations for books you’ve already read, such as the O’Brian books, you’d select them in the results screen and add them to your list, via a button at the bottom of the list. That prevents them from showing up in results going forward. Then, when you want a recommendation in the future, you’d scan your list, select a particular set of books on which to base the suggestions (“Perhaps a whodunit today.”) and
run the search.
I give the site points for allowing me to search by book title, author, and ISBN, and while the recommendations generated by my full list were somewhat quirky, I also give WSIRN some additional points for providing me with a few leads.
Each WSIRN recommendation comes with an Info/Buy button that, when clicked, takes you to that book’s page on Amazon, thus reinforcing Amazon’s dominance in the book trade — that might call for deducting a few points!
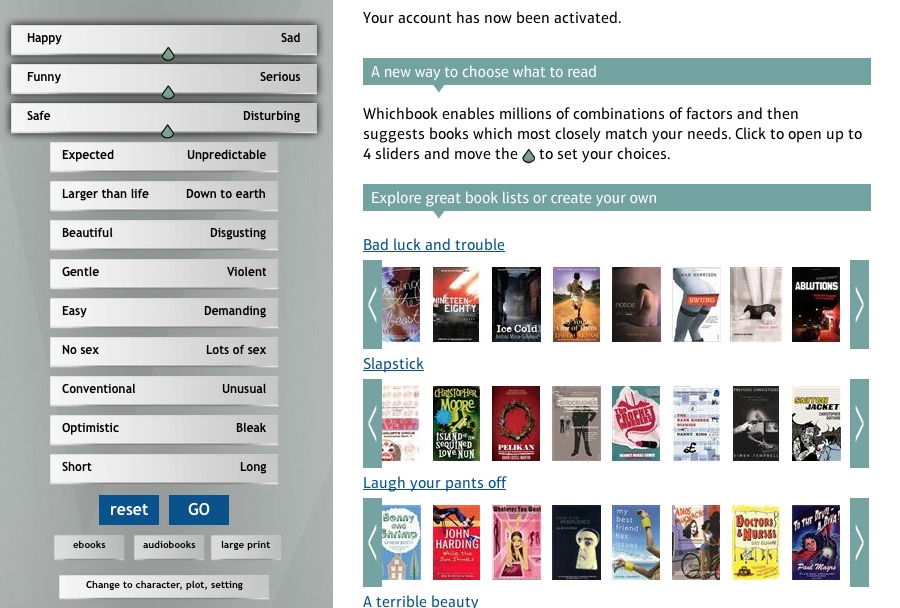
Whichbook — The Whichbook site takes a decidedly different approach: instead of starting with a list of authors and titles, it works from what it calls a “combination of factors” that you supply. You don’t need a registration to use Whichbook, unless you want it to keep track of your various searches.
What “combination of factors” means in actual use is that you employ a bunch of sliders that appear on the home page to select the characteristics of the kind of book you want to read. One slider, for example, goes from “Happy” to “Sad”; another goes from “Funny” to “Serious”; yet another goes from “No sex” to “Lots of sex”; and so on. Alternatively, you can work from checklists for character (with settings for race, age, sexuality, and gender), plot (with mutually exclusive checkboxes for plot types like “Success against the odds” or “Lots of twists and turns”), and setting (a scrolling map of the world that you can click). Or, finally, you can choose from pre-supplied book lists with names like “A
terrible beauty” and “Laughing your pants off.”
This interface turns the book quest into an interactive browsing game, which I found amusing, but not very useful: when I’m looking for something new to read, I may not have any particular set of characteristics in mind other than that the author be skillful and the book engaging. I don’t mind — in fact, I often relish — being surprised by the nature of the content. What really turned me off the site, though, is that the interface is implemented with Adobe’s Flash, a technology that I try to avoid whenever possible.
To be fair, the site also allows you to pick specific titles and authors to serve as the basis for recommendations, but both the title list and author lists are rudimentary: for example, “The Cuckoo’s Calling”, which is currently on the New York Times Best Seller list, does not appear among the offered titles. In fact, not one of the books on my full list appears. Feh!
I give this site points for audacity and cleverness, but deduct many more for lack of depth and for the use of Flash.
LibraryThing — None of the three sites that Josh initially suggested fully met my need for a new read, although, of the three, WSIRN was by far the most promising, even with its idiosyncratic results and spartan appearance.
However, I did find another book recommendation site on my own, LibraryThing, which has the depth that WSIRN does and also offers a more complete feature set for bookish people (you know who you are). Unlike the other sites I looked at, LibraryThing really requires a user account — as far as recommendations go, it is useless without one.
When I gave LibraryThing the four-book version of my list, it offered me a few useful suggestions. And once I fed LibraryThing the dozen books I had originally chosen for this experiment, its recommendations were even more useful. Better yet, the recommendations seem to be dynamic: come back on another day, and, even if you haven’t added any new books to LibraryThing, the recommendations may very well be different.
LibraryThing’s strength lies in its large user community, which seems dedicated to using the service to catalog and rate all of their books. (It does try to get you to connect with your Twitter and Facebook friends; I demurred.) The site even accepts data entry from a free iPhone scanner
app, ZBar Barcode Reader, so you can scan the barcodes on many of your books’ covers for quick data entry. I can easily see myself in the days ahead, iPhone in hand, scanning the books on my shelves to flesh out the list I’ve started in LibraryThing.
But that’s for another time: I just bought “The Bones of Paris,” a brand-new novel by Laurie R. King, one of my favorite mystery writers, and it looks promising. Also, Thomas Pynchon’s latest work, “Bleeding Edge,” is due out this month, and that’s on my “can’t miss” list, too.
So, for now at least, I have two good books waiting to be read. But I know I’ll need more: winter is coming!
My Full List — Should you be wondering precisely what titles I used for my testing, here’s the full dozen. And while I only play a book recommendation engine on the Internet, I heartily recommend all of these titles.
-
“Emma” by Jane Austen, her favorite among her books, and one of my favorites as well
-
“The Adventures of Huckleberry Finn” by Mark Twain, a deeper and darker novel than musical and movie versions would have you think
-
“The Game of Kings” by Dorothy Dunnett, a psychologically complex historical adventure novel set in 16th century Scotland and the first entry in her “Lymond Chronicles”
-
“The Beekeeper’s Apprentice” by Laurie R. King, an entertaining and gripping Sherlock Holmes pastiche, and the first in her Holmes and Russell series
-
“Lamb” by Christopher Moore, a very funny, albeit blasphemous, retelling of the Gospels by Biff, Christ’s childhood pal
-
“Pale Fire” by Vladimir Nabokov, his novel following “Lolita”, comprising a 999 line poem by a renowned poet and its exegesis via annotations by his delusional murderer
-
“Master and Commander” by Patrick O’Brian, the first of a lengthy series of popular novels about naval warfare during the Napoleonic Wars
-
“Gravity’s Rainbow” by Thomas Pynchon, a sprawling and complex post-modern novel from the early 1970s
-
“The Cuckoo’s Calling” by J.K. Rowling (writing as Robert Galbraith), an entertaining detective tale published earlier this year
-
“Gaudy Night” by Dorothy Sayers, the best and deepest of her excellent Lord Peter Wimsey detective stories
-
“Redshirts” by John Scalzi, a funny and surprisingly moving science-fiction novel that won a Hugo Award this year
-
“The Lord of the Rings” by J.R.R. Tolkien, an undoubted masterpiece which I’ve read at least two dozen times and am tempted to reread yet again
TidBITS Watchlist: Notable Software Updates for 16 September 2013
Microsoft Office 2011 14.3.7 — With the release of Office 2011 14.3.7, Microsoft has bashed a number of bugs and closed a security vulnerability in Excel that could allow remote code execution from a specially crafted spreadsheet file. On the Outlook front, the update fixes several issues related to navigation through several panes and using screen reader software. Outlook also now enables you to insert images via the Format menu and adds an item sort order to the View menu. The new release also improves how SharePoint
handles opening and checking out files to avoid a crash, plus it prevents a crash in Excel when a spreadsheet contains several drop-down macros. (Free updates via the Office for Mac Web site or through Microsoft AutoUpdate, 113 MB, release notes)
Read/post comments about Microsoft Office 2011 14.3.7.
SpamSieve 2.9.8 — C-Command Software has released SpamSieve 2.9.8 with a variety of improvements to the app’s filtering accuracy and a change to the Train as Good command in Apple Mail, which now considers the message’s CC recipients when determining the correct destination inbox. The spam-filtering utility has been updated to handle the recently released OS X 10.8.5 Mountain Lion (see “OS X 10.8.5 Fixes Nasty Text Rendering Bug,” 12 September 2013), but not the upcoming OS X 10.9 Mavericks. The release also improves how the installer works around incorrect Apple Mail
folder permissions, removes unused code from the Apple Mail plug-in, and updates several sections of the manual. ($30 new with a 20 percent discount for TidBITS members, free update, 10.8 MB, release notes)
Read/post comments about SpamSieve 2.9.8.
Security Update 2013-004 for Lion and Snow Leopard — Apple has released Security Update 2013-004 for Mac OS X 10.7 Lion and 10.6 Snow Leopard, both of which receive two versions: Lion (113.23 MB) and Lion Server (161.17 MB), plus Snow Leopard (331.5 MB) and Snow Leopard Server (406.49 MB).
Most notably, the updates fix an issue in Lion where an attacker could gain superuser access by resetting the system clock. (For details, see “Hackers Can Root Macs by Going Back in Time,” 30 August 2013.)
Additionally, these updates fix other user-level vulnerabilities in Lion, including security holes in QuickTime that could permit malicious movie files to cause application crashes or arbitrary code execution, Installer packages that could be opened after certificate revocation, and an issue in Mobile Device Management that could disclose passwords to local users.
Also fixed are a number of security vulnerabilities on the Unix end, via updates to the Apache Web server, the BIND DNS server (Lion only), the ClamAV virus scanner, the IPSec security package, the PHP scripting language, and the PostgreSQL database (Lion only). (Free, various sizes)
Read/post comments about Security Update 2013-004 for Lion and Snow Leopard.
Safari 5.1.10 for Snow Leopard — Apple has released Safari 5.1.10 for users of Mac OS X 10.6.8 Snow Leopard. The update addresses an issue with JavaScript that could lead to Safari crashes or arbitrary code execution. (Free, 48.4 MB, release notes)
Read/post comments about Safari 5.1.10 for Snow Leopard.
Nisus Writer Pro 2.0.5 and Express 3.4.4 — Addressing a large number of niggling issues and incorporating a few minor enhancements, Nisus Software has released Nisus Writer Pro 2.0.5 and Nisus Writer Express 3.4.4 to the applause of grateful Take Control writers and editors. Nisus Writer Pro fixes a bug with exported EPUBs that produced validation errors if the file contained multiple chapters, resolves a hang caused by competing TOC inclusion instructions, adds numerous macro enhancements (including the capability to run macros when clicked), and fixes a variety of issues related to indexing.
Both the Pro and Express editions add the capability to use aliases when inserting a link to a file or image that will resolve if the target is moved or renamed, as well as fix bugs related to inline spellchecking, creating PDFs, and printing, and incorrectly creating a new blank document when opening an existing document. (For Nisus Writer Pro: $79 new, free update, 178 MB, release notes. For Nisus Writer Express: $45 new, free update, 51 MB, release notes.)
Read/post comments about Nisus Writer Pro 2.0.5 and Express 3.4.4.
ExtraBITS for 16 September 2013
The TidBITS staff joined Chuck Joiner on his MacJury podcast to render judgment on the new iPhones. What new iPhones? If you missed Apple’s announcement, you can now watch the video on the company’s Web site. Will the Touch ID fingerprint scanner on the iPhone 5s make security more available to the disabled? Accessibility expert Steven Aquino thinks so. While Apple was announcing new products, it quietly shuttered the Cards app and service for sending custom greeting cards from an iPhone or iPad. Finally, find out how Facebook can make you depressed (or not), 1Password’s developers respond to the NSA revelations, and a wistful John Sculley laments the firing of Steve Jobs.
The MacJury’s Verdict on the New iPhones — A punchy TidBITS crew sat on the MacJury to discuss the new iPhone 5c and iPhone 5s. Watch Adam, Tonya, Joe, Michael, and Josh join host Chuck Joiner to talk about the colors of the iPhone 5c, the new A7, and the camera in the iPhone 5s. Lots of fun and laughs were had, so be sure to check it out.
1Password Developer Responds to NSA Concerns — In response to the wave of recent NSA revelations, 1Password developer AgileBits has posted reassurances on its blog that the popular password-storage software has not been compromised. AgileBits cites the verifiability of its data format, its lack of data collection, and the fact that the development team is spread out over the world, making it impossible for the United States government to silence it. AgileBits itself is a Canadian company.
Will Touch ID Make the iPhone 5s More Accessible? — Much has been said about the security implications of Touch ID, the new fingerprint scanner in the iPhone 5s. But TidBITS contributor and accessibility expert Steven Aquino has a different take on it, as a tool for the disabled. Steven argues that Touch ID will be a boon for iPhone users with visual or motor disabilities that make passcodes difficult to enter.
How Facebook Makes You Unhappy. Or Not. — In the New Yorker, psychologist and author Maria Konnikova examines studies showing that Facebook — and Internet use in general — makes people unhappy, along with those showing just the opposite, that Facebook use makes people happier, increasing social trust and engagement. How could this be? She teases out the fact that the research showing negative effects may have focused on passive use (scrolling through newsfeeds), whereas those evincing positive effects looked at active use (posting, “liking,” and so
on). In short, engage with life online, don’t let it just wash over you.
Apple Kills Its Cards App — Apple has killed its Cards app for iPhone and iPad, introduced in 2011 to enable you to create and mail custom greeting cards for a fee. Cards has been removed from the App Store, and if you have it installed, the app will notify you that its associated service is no longer available. If you still want to mail cards, check out Bill Atkinson’s free PhotoCard app, which lets you email cards for free, or send them via postal mail for as
little as $1.50.
Watch Apple’s iPhone 5s and iPhone 5c Special Event — Apple has released the 85-minute video of its September 2013 Special Event, featuring the debut of the iPhone 5s and iPhone 5c. Be sure to check out the end, which features a performance by Elvis Costello.
John Sculley Reflects on the Firing of Steve Jobs — Former Apple CEO John Sculley gave a talk at the 2013 Forbes Global CEO Conference, where he was asked about his split with Steve Jobs, which led to Jobs leaving the company in the mid-1980s. Sculley aimed the blame squarely at Apple’s board at the time and pointed out that Jobs then lacked the business acumen for which he later became famous. Sculley said he regrets not reaching out to Jobs to bring him back to Apple later. “I didn’t do that, it was a
terrible mistake on my part. I can’t figure out why I didn’t have the wisdom to do that. But I didn’t. And as life has it, shortly after that, I was fired,” Sculley said.