TidBITS#1239/08-Sep-2014
The big news this week is the theft of nude photos from the iCloud accounts of a number of Hollywood actresses. Rich Mogull brings you analysis of Apple’s official statement, and Josh Centers reports on what Tim Cook says Apple will do to improve iCloud security. OS X Yosemite is coming soon, and you can get ready ahead of time with the early-bird version of Joe Kissell’s “Take Control of Upgrading to Yosemite.” In other Take Control news, we’re excited to publish the final chapter of Charles Edge’s streamed “Take Control of OS X Server” — TidBITS members can learn all about server maintenance. If you sync your music collection between iTunes on the desktop and an iOS device, losing access to that computer could orphan your music collection — Josh Centers has discovered a simple, free app to recover your music. Finally, in FunBITS this week, Julio Ojeda-Zapata explains how you can host your own backyard movie night. Notable software releases this week include VMware Fusion 7.0 and Mailplane 3.3.
iCloud Flaw Not Source of Celebrity Photo Theft
On 31 August 2014, disturbing news broke that criminals had pilfered the private photos of certain celebrities, posted some online, and offered more up to the highest bidder. It is one of the deepest, most disturbing violations of privacy possible, and while this incident focused on the famous, the crime is neither new nor limited to those living public lives. As speculation swirled around the source(s) of the photos, reports emerged on Twitter of the existence of a public tool to brute force iCloud passwords, which may have been involved in the crime.
Apple denies that the iBrute tool was used in the celebrity attacks:
After more than 40 hours of investigation, we have discovered that certain celebrity accounts were compromised by a very targeted attack on user names, passwords and security questions, a practice that has become all too common on the Internet. None of the cases we have investigated has resulted from any breach in any of Apple’s systems including iCloud® or Find my iPhone. We are continuing to work with law enforcement to help identify the criminals involved.
As is nearly always the case in a big security story, it takes time for the facts to emerge. Apple likely didn’t know for sure if iCloud was involved at all, and only after intense investigation was able to better understand the attack.
Thus, despite even my own suspicions that iCloud must have been involved, it appears that some celebrities were deliberately targeted and had their iCloud accounts compromised — not due to the recently patched flaw, but rather by the attackers guessing passwords and/or answers to security questions.
Passwords at the Root — Based on Apple’s statement and similar previous incidents, the criminals appear to have individually compromised a set of targeted accounts. A variety of techniques could have been used, including using one compromised account to attack other celebrities with a relationship to the victim.
At this point, speculation about the exact nature of the attack is just that, and Apple may still hold some responsibility. For example, although Apple supports two-factor authentication, it doesn’t directly restrict the ability to set up a new device with access to your iCloud account (I suspect this will be changed quickly). That doesn’t make Apple responsible (though the company doesn’t make two-factor authentication easy to set up, either), but two-factor authentication is one of the only viable options to protect accounts in a world where passwords are increasingly difficult to manage.
Even if Apple didn’t make any significant security mistakes, as seems to be the case, that doesn’t mean we shouldn’t hold them (and all cloud service providers) to a higher standard as we place more and more trust into our devices and the cloud.
iBrute Limited — On 30 August 2014, someone using the name “hackapper” released a tool called iBrute on the GitHub code sharing service. The tool attacked an account by iterating through the 500 most common passwords (obtained from a large repository of stolen passwords) that met Apple’s password requirements. It did this via a direct connection to iCloud over an application programming interface (API) for Find My iPhone, enabling it to blast through all 500 passwords relatively quickly.
This is known in security circles as a brute force attack, since it doesn’t bypass the password, but merely tries as many passwords as it can until it hits the right one.
Normally, these attacks are thwarted by limiting the number of times passwords can be tried before the user is locked out of the account. In this case, Apple seemed to allow a higher number of password attempts (some claim there is no limit, but I’ve been given conflicting information, and can’t test now that the flaw is fixed).
Apple patched this vulnerability on 1 September 2014, limiting the damage, although we don’t know how long the vulnerability existed or how widespread abuse may have been before the tool was released.
But based on Apple’s statement, the iBrute tool or some other direct attack on iCloud or Find My iPhone in general was not the source of the celebrity photo theft. That statement, however, was carefully constructed in case conflicting information later emerges in the investigation.
This is a terrible situation, and possibly one that started with criminal attacks months or years ago. The only ones to blame are the criminals who stole the photos, and those that support them by looking at or even purchasing the photos.
But Apple, like all major cloud providers, needs to step up its game, especially since it wants to store (or is already storing) our email, chats, photos, medical data, and payment information in the cloud. These kinds of attacks are only going to increase, and cloud services need to make it easier for users to implement higher levels of security, without destroying the user experience. It’s the kind of challenge well suited to Apple’s strengths; now it’s time for the company to apply its vaunted design and user interface chops to the problem.
In the meantime, I recommend following Glenn Fleishman’s directions for setting up two-factor authentication with your Apple ID, as outlined in “Apple Implements Two-Factor Authentication for Apple IDs,” (21 March 2013).
Tim Cook Promises Improved iCloud Security
In the wake of the theft of nude photos from celebrities (see “iCloud Flaw Not Source of Celebrity Photo Theft,” 2 September 2014) — a theft that has been linked to Apple’s iCloud suite of online services — Apple CEO Tim Cook has vowed to improve iCloud security in his first interview about the situation.
Here’s what Apple is planning:
- Starting in two weeks, Apple will send email and push notifications “when someone tries to change an account password, restore iCloud data to a new device, or when a device logs into an account for the first time.”
- Apple will do more to raise user awareness about security, both in terms of the potential dangers and the importance of stronger passwords. Perhaps Apple should give everyone a copy of Joe Kissell’s best-selling “Take Control of Your Passwords.”
-
The company plans to broaden its use of two-factor authentication, and push more aggressively for users to enable it.
-
Apple will extend two-factor authentication to iCloud accounts accessed from mobile devices in iOS 8.
Cook reiterated that the photo theft didn’t happen due to any sort of Apple ID or password leakage, but rather by guessing passwords and/or security questions.
Ashkan Soltani, an independent security researcher, told The Wall Street Journal that the new notifications “will do little to actually protect consumers’ information since it only alerts you after the fact.”
While Soltani has a point, an enhanced focus on two-factor authentication could help prevent future incidents such as this. Two-factor authentication, which requires both something you know (a password), and something you have (a token or an app that generates random numbers every few seconds) is offered by Apple, but isn’t exactly user-friendly (to learn more, see “Apple Implements Two-Factor Authentication for Apple IDs,” 21 March 2013). There’s often a three-day waiting period to enable it, and even then, it protects only payment information, not content you store in iCloud.
Journalists have been doing some sleuthing of their own to discover the holes in iCloud security. Andy Greenberg of Wired scouted the anonymous image board Anon-IB, which specializes in stolen pornographic images, and discovered that attackers were using a combination of a script based on the Find My iPhone rate-limiter vulnerability (which Rich Mogull discusses in “iCloud Flaw Not Source of Celebrity Photo Theft,” 2 September 2014) and Elcomsoft Phone Password Breaker (EPPB) to steal images from victims’ iCloud backups.
Christina Warren of Mashable took things a step further, using EPPB and a bit of guesswork (plus a password cracker) to break into her own iCloud account, as well as her sister’s. Warren used the $199 Professional Edition of EPPB, but the $399 Forensic Edition, marketed toward law enforcement, can pull an iCloud authentication token from a personal computer, bypassing even the password requirement.
Warren points out a number of security flaws in iCloud, including unencrypted backups and iCloud authentication tokens stored in plaintext. Two other points, about two-factor authentication being difficult to set up and protecting only payment information, will hopefully be addressed soon.
In any case, this security breach could not have came at a worse time for Apple. With a major product launch coming up on 9 September 2014, the stakes are high. If the rumors that Apple is set to announce a biometric-tracking smartwatch and a new payment system pan out, Apple will have to go above and beyond to regain the public’s trust.
Prepare for Yosemite Now with Take Control Books
The public beta of OS X 10.10 Yosemite has been out for a bit now, but with no word on when Apple plans to release the final version apart from “this fall,” which could mean anywhere from now through November. For those who don’t want to mess with the beta but are looking forward to Yosemite, we have an early-bird version of Joe Kissell’s “Take Control of Upgrading to Yosemite” to smooth your transition. It’s for sale now, along with three other Yosemite and iOS 8 books available for pre-order in discounted bundles. They include:
- “Yosemite: A Take Control Crash Course,” by Scholle McFarland
- “iOS 8: A Take Control Crash Course,” by Josh Centers
- “Digital Sharing for Apple Users: A Take Control Crash Course,” by Joe Kissell
I’ll explain what a Take Control Crash Course is below, but to cut to the chase, you can save 33 percent on all four books ($45 list, you pay $30), take 25 percent off the two-book bundle of “Take Control of Upgrading to Yosemite” and “Yosemite: A Take Control Crash Course” ($25 list, you pay $18.75), or just save $5 on “Take Control of Upgrading to Yosemite” ($15 list, you pay $10). These offers will expire once we publish the final books.
(Pre-order books come as one-page PDFs; once a final book is out, you can get it from links on the PDF or from your Take Control library, and we’ll send you direct download links in email.)
Joe Kissell’s “Take Control of Upgrading to Yosemite” is the 8th installment in his classic series, which has helped tens of thousands of Mac users upgrade with confidence since 2003. With “Take Control of Upgrading to Yosemite,” you’ll stay in control as Joe explains how to ensure that your hardware and software are ready for Yosemite, prevent problems by making a bootable duplicate of your main drive, eliminate digital clutter, prepare your Mac, and decide on the best installation method for your particular situation, no matter what version of Mac OS X you’re upgrading from,
all the way back to 10.4 Tiger.
Because you may want to start preparing now, we’ve published the 73-page “Take Control of Upgrading to Yosemite” before Yosemite is available. Once Apple releases Yosemite — and our non-disclosure agreement is lifted — we will publish a version 1.1 update with full installation steps, post-installation advice, troubleshooting help, and all the good stuff we can’t talk about yet. Look for “Meet Me Back Here on Upgrade Day” in the ebook to learn how to get the free 1.1 update, or just watch for our email notification with direct download links.
The other three books are in our new Crash Course series, which splits the first-rate content you expect from Take Control into shorter, more digestible chunks of information so you can dip in and read more quickly, picking just those topics that interest you. Crash Courses have a modern, magazine-like layout in PDF while retaining an elegant, reflowable design for the EPUB and Mobipocket versions. Not all topics lend themselves to the Crash Course approach; process-based subjects like upgrading to Yosemite, where we recommend reading the bulk of the book from front to back, are best handled by our traditional Take Control style.
These books can be pre-ordered individually for $10 each, or at a discount in a bundle (either one of the bundles mentioned above or our standard 30 percent discount for three or more books in an order). We anticipate releasing them at some point in September or October, and that they’ll be in the 90- to 100-page range, give or take.
- “Yosemite: A Take Control Crash Course” explains interface changes in Yosemite’s Finder and focuses on new features such as Handoff and iCloud Drive. Former Macworld editor Scholle McFarland also discusses the key Apple apps that are the most changed in Yosemite: Safari, Mail, Messages, and Calendar. Plus, she covers features recently added to OS X, such as notifications, Finder tags, and tabbed Finder windows, along with basic info about under-the-hood topics such as Recovery mode, setting up a new user account, and working with Activity Monitor.
- “iOS 8: A Take Control Crash Course” helps you quickly master new features in iOS 8. Guided by TidBITS Managing Editor Josh Centers, you’ll get an overview of iOS 8’s new capabilities, along with directions for putting them to use right away. In addition to system features like Siri, Spotlight, and Notification Center, Josh explores the new Health app, and takes you through what’s different in iOS 8’s most changed apps: Camera, Phone, Photos, Mail, Messages, and Safari. Additional special topics cover accessibility, privacy, important apps to try, managing data usage, and improving battery life.
-
“Digital Sharing for Apple Users: A Take Control Crash Course” offers quick, easy-to-understand lessons for sharing your data, documents, and devices in over three dozen scenarios. With author Joe Kissell as your teacher, you’ll soon be sharing photos, files, contacts, calendars, reminders, videos, printers, scanners, iTunes Store media, passwords, and quite a bit more. Joe also focuses on Apple’s new Continuity features in Yosemite and iOS 8, including sharing tasks via Handoff, getting phone calls and SMS messages from your iPhone on your Mac, setting up Instant Hotspot on your iPhone, and using AirDrop between Macs and iOS devices. The book goes well
beyond Apple’s built-in sharing options with details about helpful non-Apple products, including 1Password, BitTorrent Sync, Cargo Lifter, CloudyTabs, Dropbox, Exchange, Google Calendar, Google Chrome, Google Docs, Pandora, PhotoCard, Reflector, Spotify, and Xmarks, among others.
Thank you for your support of Take Control! It’s going to be a crazy few months while we keep working with the still-incomplete betas of Yosemite and iOS 8, but we’ll publish as soon as we can once Apple finalizes the features and pushes these operating systems out to users.
Chapter 14 of “Take Control of OS X Server” Now Available
With this week’s installment, we’ve come to the end of the streamed chapters of Charles Edge’s “Take Control of OS X Server.” We started by helping you figure out what sort of Mac you’d need for a server, and then walked you through basic installation of OS X Server before focusing on how to set up each of the services that is relevant to someone running OS X Server in a home, small office, or school environment.
How best to close out this book, then? With advice on how to keep your server running happily. In Chapter 14, “Server Maintenance,” Charles shares tips about how to deal with common situations and recommends maintenance tasks that can stave off problems. He divides these into things you must do as they arise, and those that should be done weekly, monthly, or annually.
Of course, there’s no way the book can anticipate everything that you might run into, so Charles also offers a list of useful resources — both Internet sites and conferences — where you can learn more from your fellow Apple sysadmins. They’re an awfully nice bunch, so you shouldn’t feel shy to ask for help or contribute your own expertise as appropriate.
Everyone is welcome to read the first two chapters of “Take Control of OS X Server” on the TidBITS site to see where the book started. All subsequent streamed chapters will remain accessible only to TidBITS members (log in using the email address from which you joined). The full ebook of “Take Control of OS X Server” will become available for purchase by everyone in PDF, EPUB, and the Kindle’s Mobipocket formats once we’ve addressed all the comments and questions we’ve received and done our final edit pass.
“Take Control of OS X Server” is comprised of:
- Chapter 1: “Introducing OS X Server”
- Chapter 2: “Choosing Server Hardware”
-
Chapter 3: “Preparation and Installation”
-
Chapter 4: “Directory Services”
-
Chapter 5: “DNS Service”
-
Chapter 6: “File Sharing”
-
Chapter 7: “Collaboration Services”
-
Chapter 8: “Mail Services”
-
Chapter 9: “Mobile Device Management”
-
Chapter 10: “Web Services”
-
Chapter 11: “Wiki Services”
-
Chapter 12: “Software Updates”
-
Chapter 13: “Backup”
-
Chapter 14: “Server Maintenance”
If these streamed chapters encouraged you to become a TidBITS member, thank you! And if you were already a TidBITS member, we hope you found the full text of “Take Control of OS X Server” useful. Support from TidBITS members has been essential in enabling us to bring you the professionally written and edited articles you’ve become accustomed to each week. For more details on what the membership program means to us, see “Support TidBITS in 2014 via the TidBITS Membership Program” (9 December 2013).
DeTune Extracts Your Media from an iPad, iPhone, or iPod touch
My wife’s music collection was stuck inside an old iPod touch. It’s so old that the shiny rear panel had rusted, which I didn’t know was even possible. The problem was that she no longer had access to the computer it had synced with — it’s a long and unhappy story, but there are a variety of other ways I could imagine it happening.
This situation exposed one of the annoyances about iOS: its file system is locked down. You can connect most other devices to a computer, move files back and forth, and be done. But the Apple-approved way of transferring files between iOS and Mac is via an iTunes sync, and iOS wants to sync with only one iTunes library at a time.
Fortunately, I discovered a free and easy way to copy my wife’s music files off the iPod touch: the open-source DeTune from HeadLightSoft. It’s a tiny 2.9 MB download and requires only OS X 10.5 Leopard or later, so just about any Mac user can run it.
DeTune can retrieve more than just music. It can also extract movies, TV shows, ringtones, books, and more, none of which were an issue for my wife’s iPod touch. However, it does not display album art or let you see photos on a device (those can usually be recovered with iPhoto or Image Capture). Nor does DeTune remove any DRM “protection” on media files.
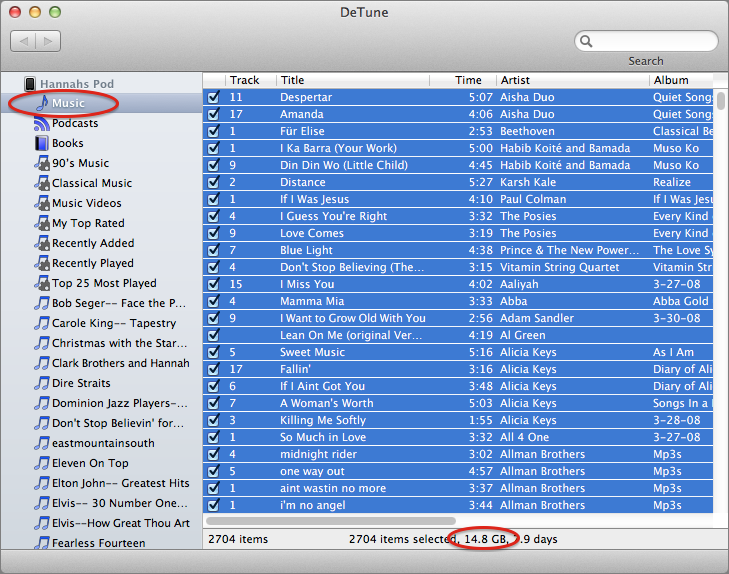
Once you launch DeTune, plug in the device you wish to extract music from and it should appear in the app. If you want to extract all music from the device, that’s easily done. In DeTune’s left-hand sidebar, select Music under your device’s heading, click any song, and then press Command-A to select all songs. Notice the combined size of the files, which is listed at the bottom of the window.
Switch to the Finder, create a new folder to hold your music (making sure you have enough room on that drive!), and drag the songs from DeTune to your new folder. If your collection is as large as my wife’s (14.8 GB), it will take some time for everything to transfer.
You can also view music by playlist if you want to copy only music that’s in a specific playlist, but in this case, I wanted to get everything off the rusting iPod touch so the music could be backed up and loaded on other devices.
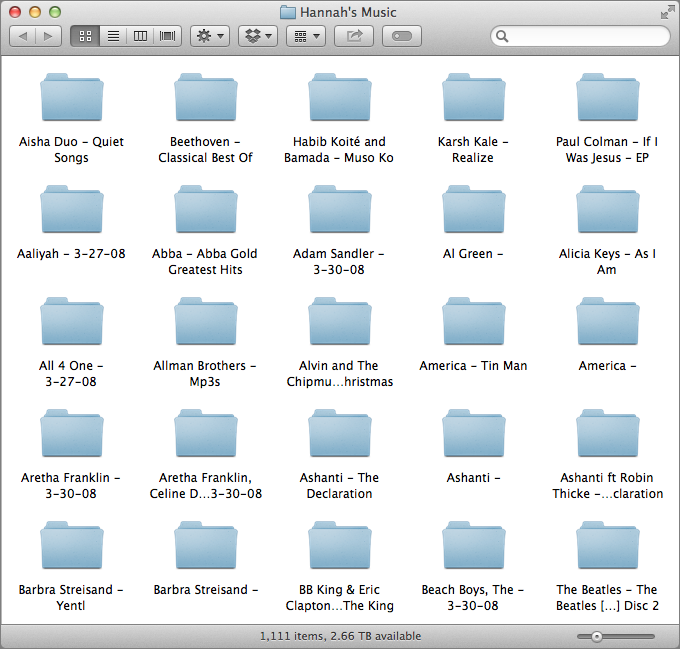
The good news is that when the transfer is finished, your music will be sorted into named folders, instead of being dumped into one messy folder. It may not be arranged exactly as you wish, but you can either let iTunes sort things out using the metadata embedded in the music files (for more information, see Kirk McElhearn’s “Take Control of iTunes 11: The FAQ”) or use a file organization tool like Hazel to do the work for you (for more on Hazel, including a 20-percent-off coupon, check out Joe Kissell’s “Take Control of Automating Your Mac”).
Once I copied the music from the iPod touch to an external hard drive, I simply unmounted the drive, took it over to my wife’s MacBook, copied the music to its internal drive, and added it to her iTunes library. And then basked briefly in my wife’s appreciation of my geek heroism. It’s nice when a seemingly insurmountable problem turns out to have an easy solution.
Thanks to the folks at HeadLightSoft for providing a simple, free tool to recover music from an otherwise inaccessible device.
FunBITS: Hosting Backyard Movie Night
I’ve wanted to host movie nights with a projector and screen in my backyard all my of life. Alas, as a longtime condo and apartment dweller, I did not actually have a yard.
That changed recently when I moved with my family into a nice St. Paul, Minnesota, house with a big yard suitable for all kinds of social gatherings.
Hello, movie night.
Jumping at the chance to create a memorable event for friends and neighbors, I set out to acquire and master the technology required for this.
I ended up putting on three movie nights, the first two screening “Frozen” for kids in my social circle, since these tykes skew female and Elsa-obsessed, and the third a showing of “The Matrix” for my 16-year-old son.
The nights were magical, with the little girls in princess outfits and glow-stick headbands singing along to “Let It Go” and the other “Frozen” tunes.
These were Apple-flavored shindigs, too, with a classic Apple iPod Hi-Fi boombox providing surprisingly rich and powerful sound, along with my MacBook Air to run “Frozen” during one of the showings (for the other, I harnessed a Microsoft Surface Pro tablet).
But figuring out the tech was not always easy. Here are my takeaways for anyone who might wish to take advantage of a warm summer night.
Pick Your Projector Wisely — For my movie-night experimentation, I borrowed a pair of projectors: Acer’s $549.99 H5380BD DLP Projector and Epson’s $799 PowerLite Home Cinema 750HD. They connect to my computers via an HDMI-to-DisplayPort adapter.
Both turned out to be pleasant surprises. Neither suffered from the dreaded dimness that plagued mainstream projectors years ago. Even at dusk, with a streetlight adding to the ambient illumination, the projectors pumped out more than enough light to show three Pixar shorts prior to the main feature.
The Epson projector proved to be problematic because its audio output options don’t include an auxiliary port, which is what my iPod Hi-Fi required. Thankfully, the Acer projector has that port.
On the plus side, the Epson has duplicate sets of controls: one set on its remote and one on the main unit. In contrast, Acer users are dependent on the projector’s remote for many of the projector functions.
Don’t Overreach — My wife and I initially planned to build a screen using white fabric and plastic pipes which would have meant hours, if not days, of toil.
Then she stumbled on a Best Buy 113-inch collapsible screen with tripod-like legs for a reasonable $100. It’s smaller than our handmade screen would have been, in all likelihood, but it took only a few minutes to set up. It’s currently out of stock at Best Buy, but Amazon offers it for $109.
This is a modest setup compared to that of my friend and Apple troubleshooter Mark Fawcett of St. Paul, who told me he once used an old highway billboard as the display centerpiece for his tricked-out movie night, an event attended by neighbors for blocks around. I’m not that ambitious (well, not yet).
Allocate Plenty of Setup Time — Since I had never tackled anything remotely like this, I needed a ton of time — several evenings prior to each of the movie nights — to experiment and perfect my setup.
Just setting up the screen ate up a lot of time. It tended to flap and twist in the wind, so I anchored it to the ground from either side using twine pulled taut (if you need help with this, Knots 3D is a useful app that Josh Centers profiled in “FunBITS: Learn Knot Tying the iPhone Way,” 22 August 2014). Getting the projected imagery to be perfectly rectangular, and to fit precisely within the screen, was another ordeal. Fortunately, both projectors make compensating for angled “keystone” or “tombstone” distortion relatively straightforward.
I’m a raging neatnik with OCD overtones, so I wanted my setup arranged just so with the unsightly cords tucked out of sight, the projector aligned precisely with the iPod Hi-Fi, and so on. This took a while, but I felt oh-so-much-better for it, and I didn’t have to worry about my young moviegoers tripping over cables and potentially hurting themselves or the equipment.
Keep Your Stuff Organized — I was surprised at how many items I had to juggle – cables, adapters, chargers, and so on — and how easily things could go missing in the grass. I even managed to lose the remote for the Acer projector at one point.
It’s a good idea to use a duffle bag or cardboard box to keep all your materials consolidated — with cords wound and wrapped with twist ties or packing tape. I used a little messenger bag to organize my gear for the second showing, which was a big stress reducer.
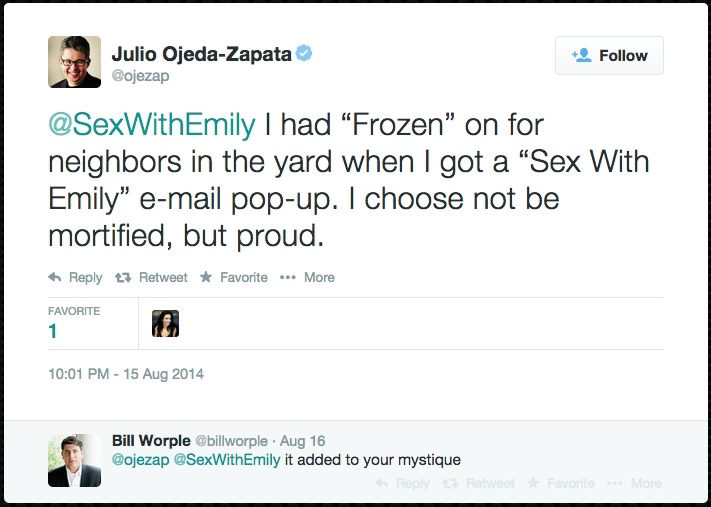
Let It (The Internet) Go — My Surface Pro was about halfway through its “Frozen” showing when a “Sex with Emily” Gmail notification popped up on the lower-right corner of the screen… and stayed there for several minutes until I noticed it.
I’m not embarrassed about subscribing to an email newsletter from Emily Morse, the sex and relationship expert, but it’s not the kind of thing I want appearing on my projection screen during a kid movie night.
I publicly professed not to be mortified, per the tweet below, but, truthfully, I was, a little bit. On the bright side, I learned I have super-cool neighbors.
The moral of the story is that I should have switched the Surface tablet to airplane mode. On a MacBook Air or other laptop, it would have been wise to deactivate Wi-Fi. (An app like CoverDesk may have helped, as well.)
Don’t Stop! — The “Frozen” nights went so well that we decided we were not done for the year.
Giving the big kids their turn, we helped our 16-year-old son organize a screening of “The Matrix” and a bonfire to enjoy with friends (no adults allowed, except for his parents on A.V. and snack-server duty).
This event was also a smash success — except for the surprise return of Minnesota’s state bird, the mosquito, which had been mysteriously absent from the “Frozen” screenings. When we ran out of bug spray, my wife had to make an emergency Target run.
And in a few weeks, my friend and “Minimal Mac” blogger Patrick Rhone and I will be hosting a backyard “Phantom Edit” screening with a version of the vile “Star Wars: The Phantom Menace” that has been re-edited to be, I have been led to understand, actually enjoyable.
Thanks to these movie nights, this has shaped up to be one of my best summers ever.
TidBITS Watchlist: Notable Software Updates for 8 September 2014
VMware Fusion 7.0 and Fusion 7.0 Professional — Ensuring compatibility with OS X Yosemite as well as the latest Mac hardware, VMware has updated its popular virtualization package VMware Fusion to version 7.0 with standard and Professional editions. In addition to adopting Yosemite’s look and feel (with translucent windows and streamlined toolbars), both editions increase energy efficiency to improve battery life when running on a Mac laptop; support the latest Intel Core i5, i7, and Xeon E5 processors (with up to 43 percent improved performance from
multimedia, encryption, and decryption operations); and provide optimized Retina display support for Windows applications. In addition to the features found in the standard edition, Fusion 7 Professional adds support for a wider variety of operating systems, the capability to manage virtual machines remotely on vSphere servers, support for using a Mac’s iSight camera within a Windows virtual machine, and optimization for dual graphics processors on the MacBook Pro (enabling those with discrete and integrated GPUs to choose one or the other).
If you have a license for VMware Fusion 5 or 6, you can upgrade to the standard edition for $49.99, while VMware Fusion Professional 5 or 6 can be upgraded for $79.99. If you purchased version 6 of either edition on or after 1 August 2014, you are eligible for a free electronic upgrade. Note that VMware Fusion’s price has increased for both editions, moving to $69.99 from the $59.99 charged for the standard edition last year (see “VMware Fusion 6 and Fusion 6 Professional,” 8 September 2013) and upping the Professional edition to $149.99 from $129.99. The standard edition upgrade remains the same price, while the Professional edition jumps $10 in price from last year. ($69.99/149.99
new, $49.99/$79.99 upgrade, 341 MB, release notes)
Read/post comments about VMware Fusion 7.0 and Fusion 7.0 Professional.
Mailplane 3.3 — Uncomplex has released Mailplane 3.3, which now automatically signs out accounts with empty passwords as well as clearing cookies and caches when quitting. The Gmail-specific email client also enables you to preview and download attachments shared from Google Drive, plus open Google Docs in an external Web browser. The release also fixes the bulleted list insertion (Command-Shift-8) so that it works in a pop-out window, prevents inline images from being inserted into plain text messages, opens Google Hangouts if opened via a Google Calendar event, and ensures that print works if a language other than English was
selected. ($24.95 new, free update, 17.4 MB, release notes, 10.7+)
Read/post comments about Mailplane 3.3.
ExtraBITS for 8 September 2014
This week in ExtraBITS, we have details on how to watch Apple’s September 9th product announcement, along with information about your personal Apple support page and a list of mistakes that cause iOS apps to be rejected. In other news, Twitpic is shutting down after 6 years, and Verizon is settling with the FCC over privacy violations.
Watch Apple’s September 9th Announcements Live — Apple’s next big media event is set for 9 September 2014 at 10 AM PDT, and you can watch it live in Safari for Mac and iOS or in the Apple TV’s Apple Events app. If you’re busy at that time, the recording usually remains available afterwards. Apple is expected to announce new iPhone models, and other possibilities include updated iPads, the much-rumored smartwatch, and an Apple TV refresh. And, although we’d be surprised to see it mentioned during this event, the Mac mini is long overdue for an update.
Farewell to Twitpic — The image-hosting service Twitpic has announced that it will shut down on 25 September 2014 after over 6 years. Twitpic blames Twitter for the shutdown, saying that the social networking company had threatened to pull API access if Twitpic did not abandon its trademark application. However, as Mashable’s Christina Warren pointed out on Twitter, the service has largely been irrelevant since Twitter added its own image-hosting capability in 2012, so this may simply have been a way to save face.
Verizon Settles with FCC over Privacy Violations — Verizon will pay $7.4 million to the U.S. Treasury for not telling subscribers that they could opt out of their personal information being used for marketing campaigns. Approximately two million customers did not receive the opt-out notice between 2006 and 2012, a violation of the Communications Act. Verizon has also agreed to include opt-out notices on every customer’s bill for three years and to set up a monitoring system to ensure that notices are being sent.
Your Own Personal Apple Support Site — Kirk McElhearn has written an article for Macworld about Apple’s personalized support Web pages, which keep a record of every Apple product you own, as well as warranty coverage, support cases, and repairs. It’s also handy to know how to access these pages in case your gear is stolen, as they store your devices’ serial numbers.
Why Apple Rejected Your App — Apple has released a list of the most common reasons apps are rejected from the App Store. Typical culprits include: broken links, crashes, placeholder content, misleading or inaccurate descriptions, and substandard user interfaces.