#1709: Unsolicited 2FA codes, solving “Failed to personalize” update errors, new features for Kini motion detectors, Apple Hearing Study update
Have you ever received a two-factor authentication code in Messages you didn’t request? That’s a red flag because it could indicate that an attacker has partially compromised one of your accounts. Adam Engst explains what (and what not) to do in such a situation. He also shares a little-known solution for pesky “Failed to personalize” errors when trying to update macOS. The Kini motion detectors can now alert you via email when they’ve been moved and are testing a new Stasis Mode that alerts when there isn’t expected motion. Finally, we briefly look at some early findings about tinnitus from the Apple Hearing Study. Notable Mac app releases this week include BusyCal 2024.2.4, Little Snitch 6.0, Mellel 6.0.4, Mimestream 1.3.4, Parallels Desktop 19.4, and Pixelmator Pro 3.6.
Kini Motion Detector Adds Email Notifications and Previews Stasis Mode
Remember the Kini motion detectors I wrote about last year in “Kini Provides Peace of Mind with Minimalist Motion Detection” (21 October 2023)? They’re simple devices that send you an SMS text message whenever they’re moved, making them highly effective for alerting you to unauthorized access or possible theft.
They have worked well for me since, although losing Internet access, as happened earlier this year during a damaging windstorm, sends them into a minor tizzy of notifications (below left). Also, as I worried, there was indeed a slightly stressful Christmas Day warning of the TV moving when we weren’t home (below right). That there was only one was reassuring—a thief couldn’t have stolen the TV without triggering more notifications. A friend confirmed there was no problem, so I’m blaming our cat. (The December 30th alerts were us moving furniture around in the living room—most of the alerts are triggered by the vacuum cleaner bumping the TV’s stand.)
At Christmas, I appreciated the fact that Kini is chatty by default, but it does provide an option to stay quiet for up to 4 minutes after triggering, which could be welcome if you regularly get multiple notifications for what is essentially a single movement. Kinisium is also testing a pair of new features to reduce the number of alerts you get. The first notices repeated messages within a short time and provides a “tap to silence” URL that offers to silence subsequent messages for set periods. The second lets you set a silence schedule so you can block off times when you don’t want to receive alerts.
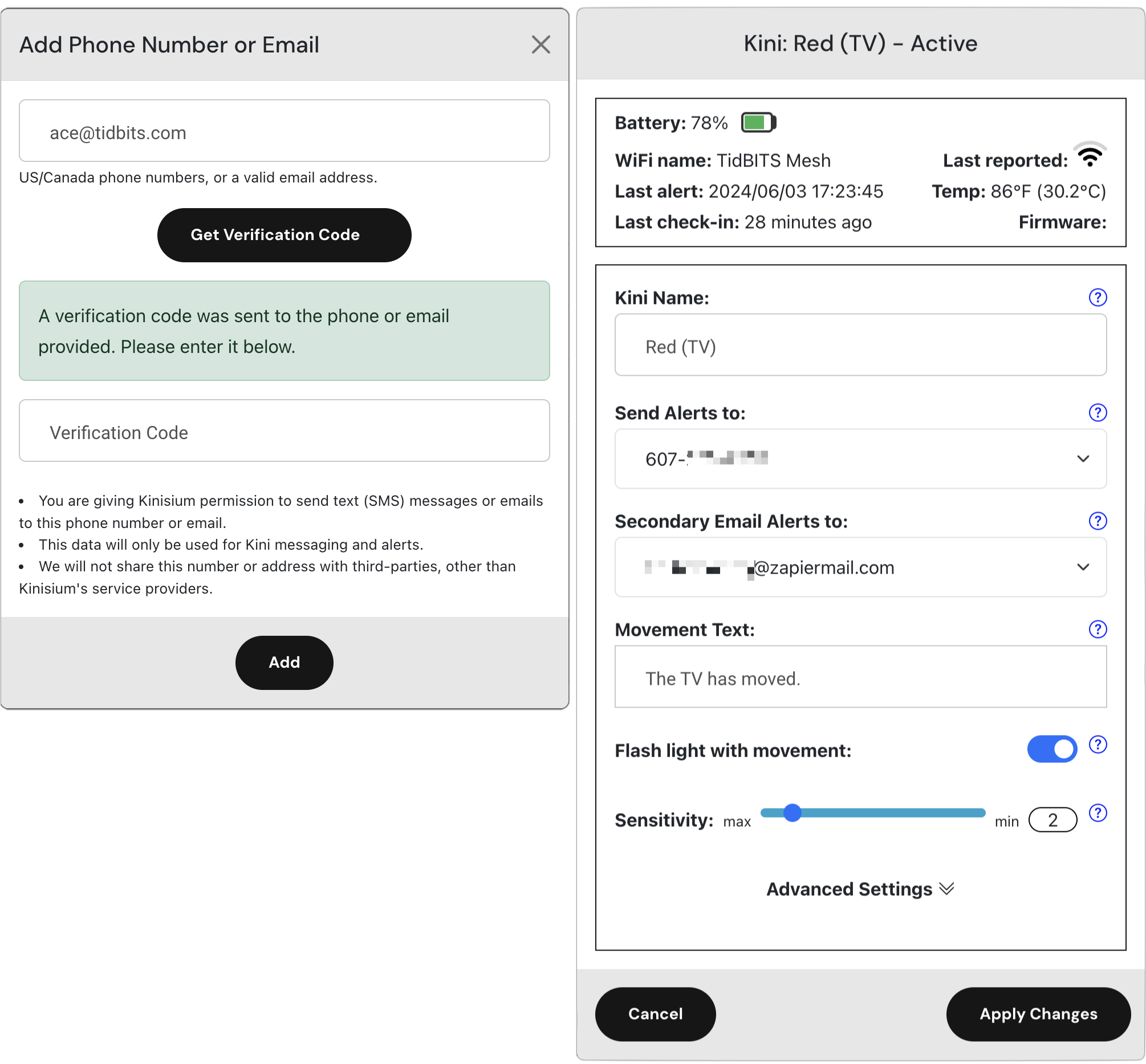
In my previous article, I highlighted two areas where Kini could improve: email notifications and an option for notifications if a Kini fails to move on a particular schedule. I’m pleased to note that Kinisium has now implemented those features.
Email Notifications
Adding email notifications expands Kini’s reach in two ways. First and most importantly, users outside the US and Canada can now use Kini, which was previously limited to SMS messages within North America. I heard from some overseas people who were disappointed that they couldn’t use Kini.
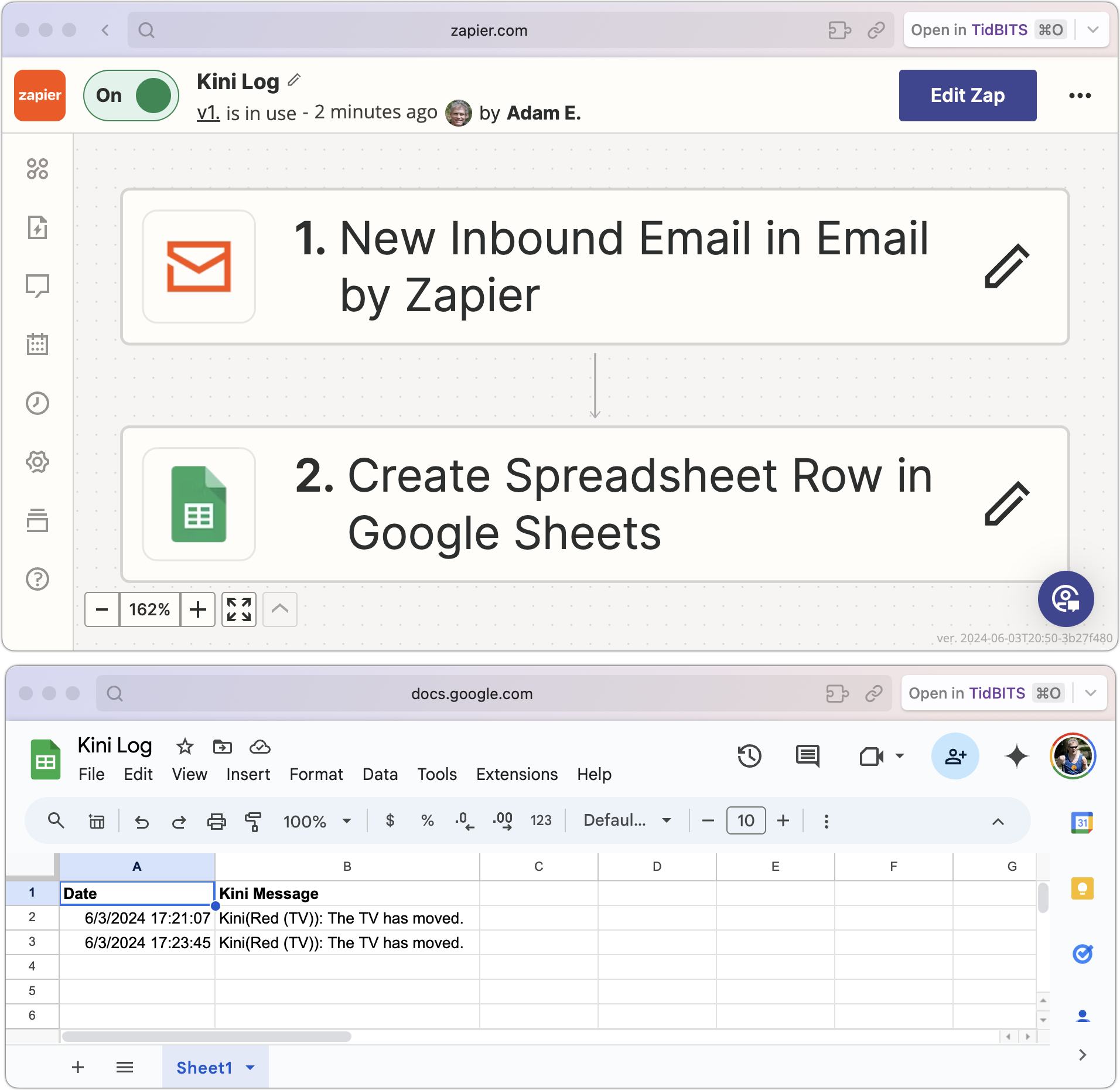
Second, email support opens up additional notification and automation options. You can use email as a primary or secondary notification option or point it at a group of people. By connecting to Internet automation services like IFTTT and Zapier, Kini can now trigger a vast array of automations. Those outside North America could even use email to trigger SMS notifications.
It took me only a few minutes to figure out how to get Zapier to log every Kini activation to a Google Sheet so I don’t have to scroll through Messages to see when things happened.
Stasis Mode
It’s easy to understand how to use a Kini to alert you to something moving, whether it’s a safe, a liquor cabinet door, or a jewelry box. But what if you wanted to know when something didn’t move? That’s called negative knowledge and can be equally important. Did the pet sitter really come by twice daily to walk the dog? Did your elderly parent open the medicine cabinet to take their medications every morning?
With Stasis Mode, you can set a time within which the Kini must move, or else it will send you a separate stasis alert message. Kinisium is still testing Stasis Mode, and if you own a Kini now, you can contact the company to help test it. The company promises that it will be available for all users soon.
It’s great to see Kinisium enhancing the Kini in useful ways. For those who have already started using it, please share your use cases. The Kini is still priced at $65, with a $10 discount for a three-pack and a $15 discount for a five-pack. No subscription is necessary—the cost of the SMS messages is built into the purchase price.
Solving the macOS Installer’s “Failed to Personalize” Error with New Firmware
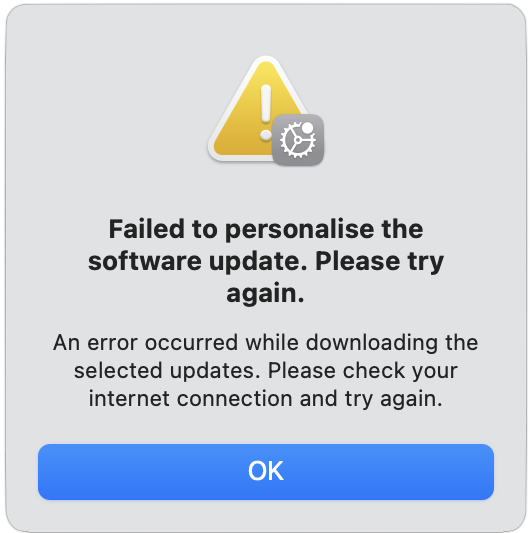
Kudos to user LALicata on TidBITS Talk for sharing a macOS update solution that isn’t widely available on the Internet. Attempting to update an M2 16-inch MacBook Pro from macOS 13.6 Ventura to any subsequent version of Ventura or macOS 14.5 Sonoma always resulted in a “Failed to personalize” error.
This error pops up quickly in Internet searches, and several articles offer possible fixes, including many old standbys:
- Restart your Mac
- Make sure your Internet connection is working
- Clear sufficient space on your Mac
- Repair the boot drive with Disk Utility
- Employ the full installer from the Mac App Store
- Boot into Safe Mode before installing
- Install from macOS Recovery
- Use a bootable USB installer
- Erase the Mac from Recovery Assistant or iCloud before reinstalling
Those are all reasonable troubleshooting steps, but none solved the problem. Apple’s support reps kept focusing on the Internet connection under the assumption that the Mac couldn’t reach a necessary Apple server during the installation process. However, once LALicata mentioned that an M1 MacBook Air was able to download and install macOS updates with no problem, they focused on the Mac itself and eventually provided the solution, which was to restore the MacBook Pro to factory settings using Apple Configurator, which writes a fresh copy of the firmware to the Mac.
Firmware Updates
Typically, Mac firmware is updated whenever a new version of macOS is installed, but if something goes wrong in the process, the Mac can be left with outdated firmware. When automatic firmware updates fail, the solution is to “revive” or “restore” the Mac using another Mac running macOS 12 Monterey or later and a USB-C cable that supports data and charging, such as the Apple USB-C Charge Cable (Apple explicitly warns against trying to use a Thunderbolt 3 cable). Although Macs running Sonoma can update firmware using the Finder, Apple Configurator is necessary for Macs running Monterey or Ventura, and LALicata’s Apple rep said that this particular problem could be resolved only by restoring from Apple Configurator, not the Finder. (Reviving leaves your data in place and is worth trying first; restoring erases the Mac and reverts it to factory defaults.)
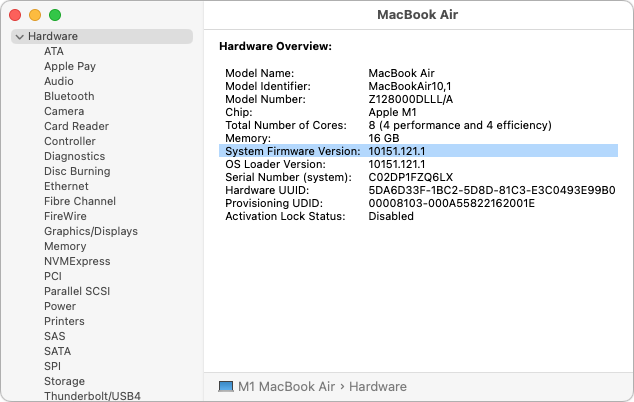
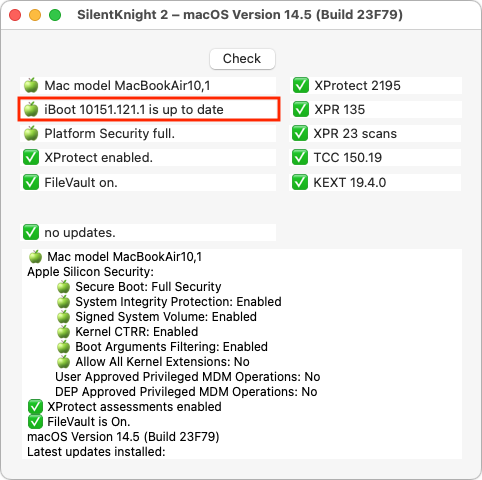
Before LALicata fixed the problem, when the MacBook Pro was still running macOS 13.6.4, its System Firmware Version was 10151.41.12. After using Apple Configurator and upgrading to macOS 14.5, the System Firmware Version jumped 10151.121.1, which is the latest version for all Apple silicon Macs. To check your Mac’s System Firmware Version, Option-click the Apple menu and choose System Information—you’ll see it in the Hardware Overview screen.
This scenario suggests another general avenue of Mac troubleshooting. If you’re having problems associated with startup or updating, compare your Mac’s current firmware version with the latest version. Howard Oakley’s excellent Silent Knight utility, which reports on the update status of various system settings, makes that easier.
The Answer Is Documentation
It’s easy to rail about the technical side of this problem. However, Apple certainly doesn’t want or expect this firmware corruption to happen and is undoubtedly working to prevent it from happening and work around it automatically if it does. But no one is perfect, and it’s impossible to predict every possible occurrence that could corrupt firmware during an update.
Instead, I’d argue that the problem here revolves around documentation. First, the error message is terrible. What does “Failed to personalize” mean (nothing, in at least this context, and not much in any I can imagine), and how is it related to firmware (it’s not)? I suspect that the firmware problem is sufficiently rare and unexpected that it’s triggering an unrelated message. Still, a better-worded error message would go a long way toward helping users (and support reps) figure out what’s going wrong.
The error condition might be rare, but it’s not unheard of, so the second problem is that Apple’s article about reviving and restoring Mac firmware doesn’t include the error message text as one of the symptoms of corrupted firmware. If it had, LALicata and other users could have found the solution with a quick search.
That’s partly why I’m writing this article—to seed Internet search engines with the “Failed to personalize” string and the solution. Anyone running into such a problem in the future should be able to find this article and jump to Apple’s instructions on reviving or restoring firmware. They may be somewhat involved and non-trivial to follow (it matters which USB-C port you use, for instance), but they’ll take far less time than working with remote support reps.
Ideally, no one will run into this problem again, but if someone does, I hope they find their way to the solution here.
Reacting to Unsolicited Two-Factor Authentication Codes
I have long encouraged the use of two-factor authentication (2FA) or two-step verification (2SV) with online accounts whenever possible (for more about the difference, see “Two-Factor Authentication, Two-Step Verification, and 1Password,” 10 July 2023). Either one is a huge security win because, after entering your password, you must enter an authentication code to complete the login.
I standardized as many of my authentication tokens in 1Password as possible because it enters them automatically for me (see “LastPass Publishes More Details about Its Data Breaches,” 3 March 2023), but many online services continue to rely on SMS text messages due to their ease of use, even though authentication apps are more secure than SMS. Don’t let a site’s reliance on SMS dissuade you from turning on two-factor authentication—2FA via SMS is still far more secure than not using 2FA.
The most common problem with SMS is an attack called SIM swapping. An attacker poses as the victim and convinces the carrier to port a phone number to a new device, effectively taking over the victim’s communications. It requires knowing the victim’s username and phone number, as well as additional identifying information like the last four digits of a Social Security Number. Unfortunately, information like that regularly shows up in corporate data breaches, such as the recent Ticketmaster breach of personal data and financial details from 560 million users.
More commonly, you may receive an SMS text message containing a 2FA code you didn’t request. This one caused me a brief moment of concern earlier this year, and a friend asked me about one they received more recently.
What should you do if you get an unsolicited 2FA code? In order:
- Don’t panic. Receiving the code indicates that someone is trying to access your account and has your password, but the additional authentication step has prevented your account from being compromised.
- Never share an authentication code with anyone! A hacker may try to access your account, be blocked by two-factor authentication, and then email, text, or even call you with a trumped-up request for the code. Since authentication codes have a short lifespan, any such contact will typically happen right away. Many companies include advice against sharing along with their codes.
- Change your password without clicking a link in the message. Navigate manually to the account’s website, sign in, and change your password. Make sure the new password is strong, unique, and stored in your password manager. If the account in question relied on an old password that you also used for other accounts, which was common practice long ago, change the passwords on those accounts as well.
What does it mean if you receive an unsolicited 2FA code via SMS? Here are the main possibilities:
- Stolen credentials: The most common and worst-case scenario is that your email address and password were stolen, likely in a data breach, and the attacker is testing to see if they can get in. The Have I Been Pwned site is worth checking to see how many breaches you’ve been caught up in, but features like 1Password’s Watchtower are more helpful for identifying particular sites whose passwords should be changed. Other password managers have similar features. Always change passwords on breached sites.
- Identity theft: I’m having trouble working out all the steps here—I’m not a cybercriminal!—but it feels like there’s an identity theft attack vector that could result in you receiving unsolicited 2FA codes. I can imagine circumstances where an attacker had compromised your email and wanted to set up a new account impersonating you, but couldn’t finish the process without entering a 2FA code sent to your phone. Far-fetched, I know, but sophisticated attacks often sound that way. I don’t recommend automatically changing your email account’s password in response to receiving an unsolicited 2FA code, but consider it a warning to be alert for additional indications of having been hacked.
- Accidental or random triggering: If you have a common email address or phone number, someone could have accidentally entered your address or number instead of theirs while trying to create an account. It’s easy to type [email protected] instead of [email protected] or mistake the upstate New York 607 area code for the Boston 617 area code (a college friend at Cornell who grew up near Boston was once able to explain a wrong number call she received from someone attempting to call MIT, which used the same exchange as Cornell at the time). If you don’t have an account at the site in question and receive only a single authentication code, you can probably ignore it. But again, stay alert for other issues.
- Glitches: There’s no way to know if human or computer error was responsible for a 2FA code being sent out incorrectly, but stuff happens.
Regardless of the cause, if you ever receive an unsolicited 2FA code for a site where you have an account, change the password immediately. It’s easy to do, particularly if you use a password manager, and the extra peace of mind is worth the effort.