#1569: T-Mobile Network Test Drive with eSIM, App Store white paper, best Mac site-specific browsers, OS public betas
For those champing at the bit to try Apple’s forthcoming operating systems, Apple has now released betas of macOS 12 Monterey, iOS 15, iPadOS 15, watchOS 8, and tvOS 15. Apple has also been waging a public relations battle to defend its App Store policies against pressure from the US Congress and Federal Trade Commission—Glenn Fleishman examines Apple’s claims in a recently released white paper. Considering switching your iPhone to T-Mobile? The company has made a tryout easier with its Network Test Drive program, which leverages the eSIM capabilities of recent iPhones to let you use its 5G network side-by-side with your current carrier. Finally, if you find working in Google Docs awkward because of how its tabs get lost in your Web browser, Adam Engst is here to help with a comparison of numerous site-specific browsers for the Mac. Notable Mac app releases this week include Fantastical 3.4.1, Pixelmator Pro 2.1, VLC Media Player 3.0.16, and Carbon Copy Cloner 6.0.2.
Apple Opens Public Betas for macOS 12 Monterey, iOS 15, iPadOS 15, watchOS 8, and tvOS 15
Apple has released public betas for macOS 12 Monterey, iOS 15, iPadOS 15, watchOS 8, and tvOS 15, so you can test out new features like SharePlay and Focus.
As always, while Apple makes these betas available for everyone, you would be foolish to install one on devices that you rely on for, well, anything. Apple has improved its development processes so even early betas are more stable than in the past, but you’re guaranteed to run into bugs, incompatibilities, and possibly even data corruption.
Not only should you relegate these betas to dedicated test devices, but we also recommend that you avoid connecting your main iCloud account with the betas in case some bug causes upstream problems. You wouldn’t want a wonky Photos beta to delete all your custom albums, for instance. Although we always recommend making backups before you install a new version of an operating system, much less a beta, you shouldn’t install these betas on anything that you can’t erase at the drop of a hat without fear of data loss.
Unless you’re a watchOS developer, we suggest that you avoid watchOS betas. While Macs, iPhones, iPads, and even Apple TVs provide methods you can employ to recover from a corrupted install, the Apple Watch does not. If you get into certain types of trouble, you’ll have to get Apple’s help to restore your Apple Watch.
To try one or more of the betas, go to Apple’s public beta page, choose your operating system, and follow the instructions, which usually involve installing a special profile on your device and then updating its operating system through Software Update.
Finally, remember that the main reason to test public betas is so you can report bugs, so be sure to revisit David Shayer’s advice in “How to Report Bugs to Apple So They Get Fixed” (17 June 2020).
T-Mobile’s Network Test Drive Puts 5G on Your iPhone’s eSIM
T-Mobile has emerged as an appealing choice in the United States for those seeking decently speedy 5G cellular-data service with good coverage, as I recently noted in “The iPhone Gets 5G, but What’s It Like in Real-World Use?” (19 November 2020).
The carrier’s challenge is to lure users away from cellular giants AT&T and Verizon, each of which commanded greater market share until recently. T-Mobile’s merger with Sprint leveled the playing field last year.
To that end, T-Mobile has been aggressive in offering free “test drives.” In 2014, it lent me an iPhone 5S to try out its service free of charge. This wasn’t a press perk; anyone could borrow one. In recent years, T-Mobile has been sending out Wi-Fi hotspots with free 5G service to potential customers, who are free to pass along the devices to others for their test drives.
In its latest test-drive twist, T-Mobile has offered to let users temporarily use its service for free on recent-model iPhones—the iPhone XS, XS Max, XR, and later—via their eSIM capability.
An eSIM is the entirely digital equivalent of a physical SIM card. Modern iPhones typically incorporate a slot for a physical SIM along with support for an eSIM, meaning the iPhone can juggle service from two carriers. Apple refers to this as Dual SIM capability.
It’s this Dual SIM scenario that T-Mobile is cleverly exploiting to get you to try out its coverage and speeds.
T-Mobile’s Network Test Drive program for the iPhone provides a Test Drive app that will quickly walk you through the steps to activate its service on your iPhone without purging—or affecting in any way—your primary service. It gives you unlimited voice and text with an assigned phone number, along with 30 days or 30 GB of 5G data service—whichever comes first.
Setting Up: It’s Quick!
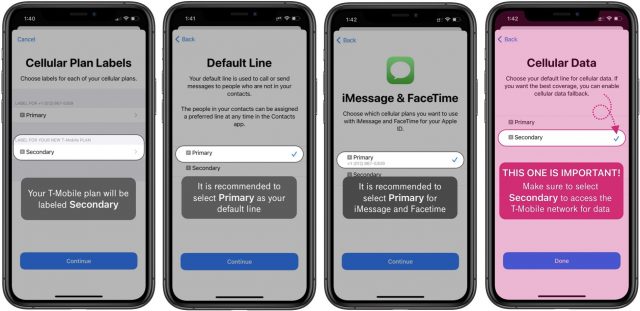
To qualify for the Network Test Drive, your iPhone needs to be unlocked, with (obviously) its eSIM feature inactive. After you download it, the Test Drive app checks whether this is the case before proceeding.
Installation moves quickly after that, with no billing information required. The app walks you through just a few steps to set up T-Mobile—designated as “secondary”—alongside the iPhone’s primary carrier.
Some of the setup options may seem confusing, but I think T-Mobile is making wise choices here. It recommends that you leave your primary carrier as the default for outgoing phone calls, text messages, iMessages, and FaceTime calls while specifying the T-Mobile secondary line as the default for cellular data. That way, when you call or message someone, it will come from your usual number, not the temporary number T-Mobile assigned to your eSIM. But for cellular data, the outgoing number is irrelevant, and that’s mostly what you want to test with the T-Mobile network anyway.
Don’t worry too much about the defaults, though, because you can continue to fiddle with cellular settings after the Network Test Drive installation has concluded.
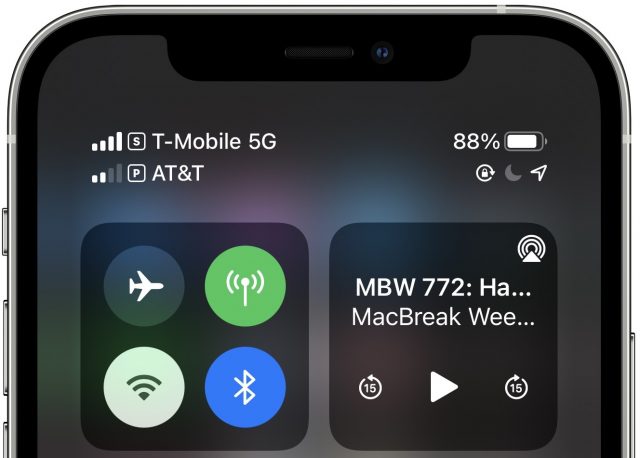
I’ve never had two cellular plans coexisting on my iPhone before—so seeing two signal strength bars at the top left of Control Center was a novelty for me.
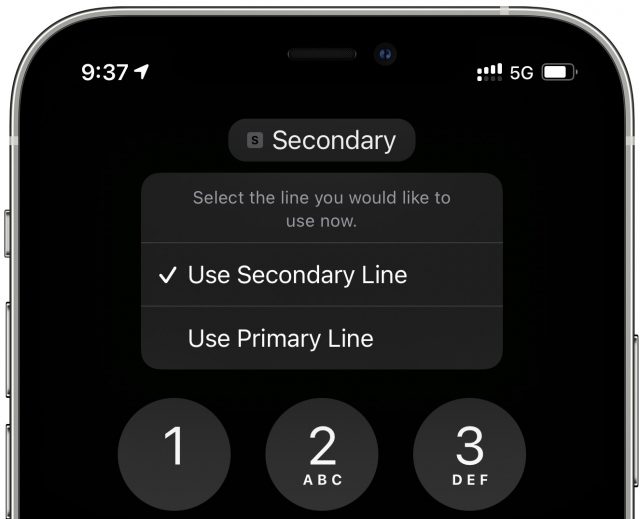
Both accounts are accessible and configurable elsewhere on the phone. In the Phone app, you can choose which line you want to use for outgoing calls. You’ll probably want to make some outgoing calls to friends (warn them ahead of the new number) to evaluate voice quality.
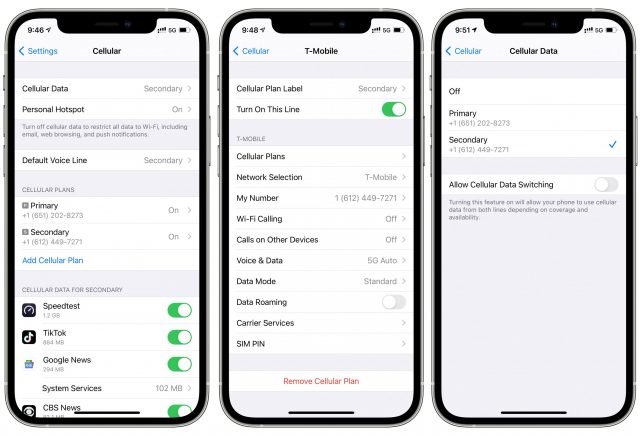
Diving into Settings, you’ll find a bunch of options that will help you get the most out of your test drive. You can:
- Temporarily deactivate your primary carrier to immerse yourself in T-Mobile’s service: Go to Settings > Cellular, tap your primary plan, and tap the toggle at the top to turn the line off.
- Switch on Wi-Fi calling: T-Mobile supports this feature, but it’s deactivated by default. Go to Settings > Cellular, tap T-Mobile’s cellular plan, and look for the Wi-Fi Calling option.
- Allow Cellular Data Switching: With both of your lines activated, this option allows your phone to use cellular data from both, depending on coverage and availability. You’ll find the toggle in Settings > Cellular > Cellular Data.
- Designate a default voice line: Look for this setting in Settings > Cellular.
- Use Personal Hotspot: Your primary plan may support this feature, and so does T-Mobile during your Network Test Drive. Any existing hotspot settings (including your password) remain as they are; you’re just using data from a different carrier.
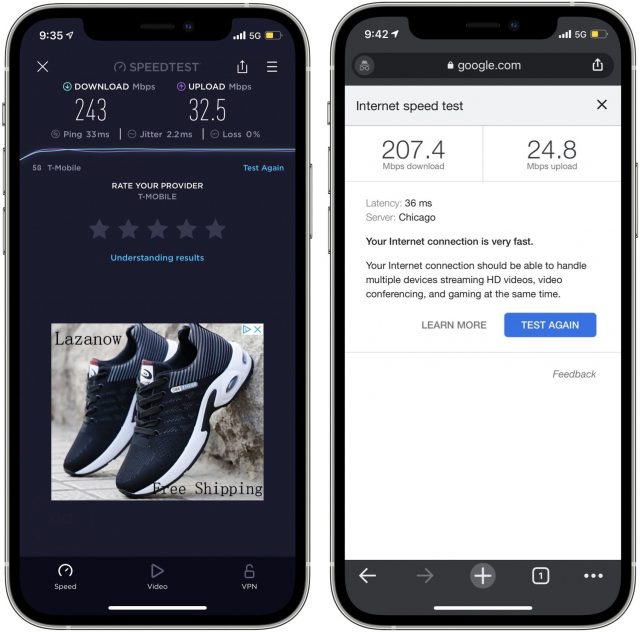
Once you’ve configured all the settings, conduct some speed tests to see how T-Mobile’s data service performs in your area. On an iPhone or iPad, try Ookla’s popular Speedtest app or search Google for “speed test” to try Google’s interactive speed test.
Rise Of The eSIM?
T-Mobile’s Network Test Drive is an ingenious marketing ploy because it nearly instantly exposes potential customers to the company’s 5G service.
T-Mobile is notable for its “middle-band” service (a byproduct of its Sprint merger) that strikes a balance between coverage and speed. It isn’t as blazingly fast as the high-band service all three US carriers provide, but that’s available only in nooks and crannies of certain cities, while middle-band service has a comparably vast footprint. This gives T-Mobile an advantage—albeit a fleeting one as its rivals snap up spectrum to compete—and it’s pressing it.
This resonates with me. If I were considering switching to T-Mobile, a quick install of the Test Drive app and a few minutes of setup would show me that I could get download speeds above 100 Mbps—sometimes even exceeding 200 Mbps!—at my St. Paul home, or more than double what I get with my Comcast Xfinity wired broadband service. The upload speeds are highly variable but often much faster than my excruciatingly slow single-digit Comcast uploads.
T-Mobile’s Test Drive has implications beyond the company’s market aspirations, particularly where its use of eSIM is concerned. This seems like a clarion call for other carriers to offer similar test drives for those who use iPhones and certain Android phones that support one or more eSIMs.
As T-Mobile notes, in marketing-speak that still rings true, “Almost 90% of people want to try a wireless network before they buy. Yet, wireless is one of the only industries in the world that forces customers to buy before they try.”
Once people realize what an eSIM can do, it might become more popular for other uses. Apple lists some of these:
- Use one number for business and another number for personal calls.
- Add a local data plan when you’re traveling outside the country or region.
- Have separate voice and data plans.
If eSIM use spikes in the coming years, we may have T-Mobile to thank. I’m sold on using an eSIM as a way of test-driving a wireless network.
Apple Justifies iOS App Store’s Tight Control in White Paper
On 23 June 2021, Apple released a white paper that shows the company pushing back against the left/right alliance in US politics that threatens to redefine antitrust for today’s digital era. Apple’s white paper, “Building a Trusted Ecosystem for Millions of Apps: The important role of App Store protections,” tries to justify the company’s white-knuckled grip on the iOS App Store as stemming from a desire to protect users from malware and the exfiltration of personal and private data.
After a brief run through the document’s main points, I look at whether Apple’s stance is reasonable.
Apple Warns of Unfettered Harm
Owners of Apple gear and those who follow its technology or the politics of antitrust already know Apple’s core arguments. In this paper, the company puts it all on the table in a structured way. It’s a debate brief for congressional hearings to come and the firm’s attempt to defend itself ahead of six allied bills advancing in the US House that would require platforms to open up to competitors and allow greater user access, among many other changes.
Regulatory action that requires no new laws is also afoot. Lina Kahn, the Federal Trade Commission’s recently confirmed chair, brings a philosophy she developed for antitrust analysis that asserts consumers can be harmed even if a monopoly delivers low prices in the short term. Her position explains why the Department of Justice pursuing Apple rather than Amazon over ebook prices made no sense in the larger scheme of things because it allowed Amazon to increase its dominance and further control the market. Her view ran contrary to popular antitrust frameworks at the time, and her appointment indicates the Biden Administration’s intent to move away from the Robert Bork era’s antitrust focus on consumer harm in favor of a new path towards promoting competition. On 1 July 2021, Kahn achieved a 3-2 win in an FTC commissioner vote to rescind a 2015 FTC memo that reaffirmed the Bork view, seen as a first step towards revising policies.
The changes in law and rules would likely require Apple to open up iOS and iPadOS to allow sideloading, the installation of software by a user without going through an official store. Google’s Android platform already allows this. The current draft of the relevant bill in the House doesn’t suggest a specific mechanism, so Apple wouldn’t have to release an update that allowed the unfettered installation of any app—just some capability to do so. The language in question is:
It shall be unlawful for a person operating a covered platform, in or affecting commerce, to—
(1) restrict or impede the capacity of a business user to access or interoperate with the same platform, operating system, hardware and software features that are available to the covered platform operator’s own products, services, or lines of business;
Apple’s document is quite readable and makes cogent arguments, but it is 26 pages long. Here’s the summary:
- Sideloading would allow malicious apps to trick users into downloading them, resulting in the installation of ransomware, sniffing software, and other unwanted apps.
- Apple’s privacy rules couldn’t be enforced on sideloaded apps, rendering users susceptible to apps extracting personal information and private data. Some of those apps might even come from legitimate companies working within the letter of the law.
- Third-party app stores would be key targets of malicious actors. Those stores could have the best intentions but be unable to match Apple’s resources.
- Children would be able to circumvent parental controls by installing apps that work around them.
- Parents might inadvertently download apps for kids that would allow children to make endless, uncontrolled purchases.
- Even if you never intend to sideload an app, an employer or a school you or your child attends might require that you install apps from a third-party app store, exposing you to subverted apps or intentionally malicious ones. Even apps chosen by the business or school might engage in surveillance Apple would never approve, with or without properly disclosing it to you.
- Users could accidentally purchase and install pirated apps from third-party app stores.
- Developers could see their apps become available in pirated form in app stores without any reasonable way to stop it.
The document then explains the App Review process, in which humans and automated systems examine submitted apps to make sure they do what they say, are not malicious, and are not misleading. In this section, Apple notes that some of its privacy and purchase features—including privacy limitations, purchase controls for children, and subscription management—could be ignored or overridden by sideloaded apps, lead to unwanted exposure, recurring charges, or kid-initiated purchases: “These controls could not be fully enforced on sideloaded apps.” (Note the passive voice!)
This is all quite reasonable in form, but it provokes two separate questions: Why don’t these same problems apply to macOS? And how is this different from the state of things today? Let’s start with the Mac.
Why Is the Mac Different?
Is the Mac not subject to concerns about sideloading already? macOS currently has three tiers of app installation. The first tier allows only apps from the Mac App Store. The second allows Mac App Store apps plus apps that have passed a vulnerability and malware-testing stage (known as notarization) and then been cryptographically signed by Apple. If the second tier option still prevents you from launching apps you trust, you can then use a sequence in the Finder to open unsigned or unnotarized apps. This third tier (without any special sequence) was of course the status quo before the Mac App Store came to macOS.
The second- and third-tier options have retroactively become sideloading, and they remain the primary way that many users get their Mac software. That may be because the developer doesn’t wish to sell through the Mac App Store or because the app in question—like Keyboard Maestro, dearly beloved by some TidBITS editors—can’t meet the App Store’s sandboxing and other technical requirements and still perform its functions.
Apple’s response is to talk down the Mac. It notes that over a billion people use an iPhone daily—no love here to iPad and iPod touch owners—and as a result:
This large user base would make an appealing and lucrative target for cybercriminals and scammers, and allowing sideloading would spur a flood of new investment into attacks on iPhone, well beyond the scale of attacks on other platforms like Mac.
There’s some logic here—macOS and iOS really do inhabit different worlds in both how they’re used and how at risk they are to attack. At present, iOS is vulnerable almost exclusively to state actors because it’s so locked down that any exploits found are therefore incredibly valuable to governments who want to observe or disrupt criminals, activists, or opposition politicians. (Some governments classify activists and opposition politicians as criminals.) There have been plenty of patched iOS exploits in recent years, but while none have been widely exploited, some have been narrowly deployed against individuals or small classes of targets, like journalists in a given country.
Any hacker or researcher who discovers an effective iOS flaw may choose one of three paths: report it to Apple and potentially claim a cash bounty, report it publicly for personal or professional reasons before or after Apple has patched it, or sell it either to a company that packages exploits for governments or directly to a nation.
Exploits for Windows and Android offer additional revenue opportunities to their discoverers. It’s profitable and sometimes less risky for a hacker to deploy an exploit in malware to reap a reward from ransomware, extract financial information, hijack cryptocurrency balances, or rent out their software to malicious partners.
iOS exploits are rarer and fetch a high price (or provide increased credibility to reputable researchers) but are also restrictive and hard to deploy to unwitting recipients. (Jailbreaks remain feasible but rely on a device’s owner following numerous tricky steps.) It makes little sense to try to make money on the back of one or a combination of them. Windows and Android and Windows have such a huge array of versions, with a significant portion of devices both unpatched and unpatchable—like pirated copies of Windows or forks of Android—that it can be easy to target a large number of vulnerable users.
Relatively few Macs are in use compared to Windows PCs, Android phones, and iPhones. Arguably, Windows 10 offers better or as good security as macOS 11 Big Sur. But the proof is in the hacking: there has been no effective, widespread ransomware or other malware for macOS in ages. Either ne’er-do-wells avoid the Mac because of its small installed base or because it’s just hard enough to exploit that there’s no profit there.
Could Apple produce a hybrid solution that would satisfy demands for sideloading without compromising privacy? Arguably, the Mac App Store’s notarization and signing tier offers that, but it still requires a paid subscription to Apple’s Developer Program and adherence to Apple’s terms, including a round-trip through its automated verification processes.
Could Apple Negotiate Its Way Out of Sideloading?
Unfettered sideloading with no participation from Apple would be a terrible idea. It’s exactly why Apple makes users jump through hoops to open an unsigned and unnotarized app in macOS. If Apple opened iOS to sideloading with no protections, it would turn into the scene from Ghostbusters (1984) in which a government official succeeds in getting the ectoplasmic containment unit shut down. Tens of millions of new malware variations appear each year, developed and deployed by legions of individual, organized crime, and government-backed hackers who already spend their days and nights poking into iOS.
While unfettered sideloading might not be what’s best for users, Apple is using a classic motte-and-bailey tactic to push back: instead of advocating for a position unpopular with its critics and that Apple likes (the bailey), the company instead pushes a connected but much more defensible position (the motte). Apple’s goal is total control of its platform and a generous cut of all revenues that pass through. That’s the bailey in this case—what Apple wants but would struggle to defend if stated openly. The motte, Apple’s easily argued position, is that smartphone users want to be safe and secure. The logical fallacy is Apple’s suggestion that if it were to loosen any control, iOS would fall like Rome to the barbarians when, in fact, there are existing counterexamples inside the Apple ecosystem itself.
Apple already offers both the macOS model and its enterprise support for non-App Store installation. Michael Tsai noted this in a blog entry summarizing reactions to the white paper, “Businesses can already force employees to install certain apps, and these apps can already bypass App Review via Apple’s enterprise program.” (Schools can’t use this to push apps to students, only employees.)
If Mac owners can be trusted with “signed and notarized apps” with a non-obvious override for unsigned and unnotarized ones, and enterprises can be trusted to make apps and release them to millions of employees, why can’t individual users be given some control, too? Apple also has its hidden XProtect and MRT (Malware Removal Tool), which can police all apps, even those installed via the notarization and signing third tier noted above.
Is Apple so paternalistic that this white paper’s summary could be, “We know what’s best for you. Trust us. We’re protecting you.”? This sounds like the opening of every dystopian superhero film and TV show, recently including The Tick (season 2), Invincible, and The Boys. (Weirdly, those three shows were all made by Amazon. Is Jeff Bezos trying to tell us something?) Could overprotection exist to keep us within bounds that benefit others rather than for our own good? It’s also entirely possible that Apple justifies its paternalistic tone because it legitimately believes a firm hand is necessary given the virulence of the threats from sleazy marketers and organized crime alike.
A better approach might be for Apple to negotiate some sort of middle ground with developers, its customers, Congress, and the Biden administration (and the EU and other countries, too) in which it gives up some of its financial leverage in exchange for a more broadly moderated alternative to App Store only installation.
Here are a few areas of contention where Apple could give ground:
- Drop fees from 15% and 30% to 10% and 15%: Developers and users alike are already frustrated that Apple both places itself in the middle and tries to claim that it is not purely out to make money—that it adds value to the system worth 15% or 30% of the price of apps, subscriptions, and digital transactions. The commission has long been seen as too high. Last year, Apple admitted 30% was excessive by offering a program for small and mid-sized developers to drop that to 15%, with some provisos (see “Apple Drops App Store Commission to 15% for Small Developers,” 18 November 2020). In 2016, Apple also shifted subscription renewals to 15% and has reportedly cut private deals for under 30% with some companies. If Apple went further and dropped the fees to 10% for small developers and 15% for larger ones, much developer ill-will would disappear.
- Allow non-Apple payment methods for digital goods: Rather than forcing developers to use Apple’s in-app purchase system, the company should allow digital purchases using methods from which it wouldn’t receive a cut. That would put it in a position of having to compete for developers’ business by being easy to use and price-competitive.
- Allow links from apps to the developer’s site: Apple should allow apps to contain links to a developer’s website, including for off-app subscriptions. Apple has negotiated arrangements with billion-dollar companies for some of this—why not $10,000-per-year developers, too? (Apple should also stop complaining to publishers about hyperlinks in ebooks on its bookstore that point to Amazon and other competitors.)
- Stop “Sherlocking” apps: Apple certainly should have the right to make apps and add features that its customers want. But the company isn’t innovating when it nearly duplicates apps and then uses its App Store control to promote them more heavily in search results. There’s a balance that doesn’t involve undermining app creators.
- Improve protection of customers: The company’s words about how it maintains a safe App Store through strong oversight ring hollow given how easy it is to find apps that use deceptive titles to mimic popular apps from other developers. (In 2018, David Barnard examined the combination of app deception and subscription scams in depth.) Similarly, stories abound of apps charging usurious fees or tricking users into expensive subscriptions.
- Improve protection of developers: Developers lose revenue from apps that hijack consumer attention through misleading titles, ads that impersonate another app, and countless fake reviews. The paper noted, “Apple deactivated 244 million customer accounts due to fraudulent and abusive activity, including fake reviews. It also rejected 424 million attempted account creations due to fraudulent and abusive patterns.” That may be so, and it’s certainly troubling, but Apple is still falling short in this regard.
Will Apple’s white paper be sufficient to deter the US Congress’s and FTC’s desire to offer more choice to consumers and leave them subject to less control? On its own, it seems unlikely. (Never underestimate the power of other forces, such as deep-pocketed lobbying.) I believe Apple has to trade away some control to justify why it should still play an essential role in protecting users without being the sole gatekeeper and toll collector.
Apple and regulators might reach compromises that don’t go as far as my suggestions above, but the paper is convincing only about certain aspects of Apple’s arguments. And there’s something about technology giants that brings politicians in the United States together across the aisle. While liberals, conservatives, and those of other political stripes seldom find commonalities these days, complaining about Big Tech’s moderation, lack of consumer control and protection, and bad behavior towards vendors is one point of agreement. Dissenters appear across the political spectrum, too, but seem to be in the overall minority.
Coda
There are two side notes to end with. First, Apple oddly notes that “A study found that devices that run on Android had 15 times more infections from malicious software than iPhone.” The footnote cites Nokia’s 2020 Threat Intelligence Report 2020. That’s an accurate citation, but a bizarre statistic. The report says an average of 0.23% of mobile devices were estimated to be infected each month. Given that a couple billion Android and iOS/iPadOS smartphones and tablets are in use globally, that means roughly 5 million are infected at any given time…and that over 300,000 of those are iPhones. That number seems quite high relative to what we know about iOS security.
Second, the report opens with a 2007 quotation from a sort of blog post/open letter from Steve Jobs originally posted on apple.com:
We’re trying to do two diametrically opposed things at once: provide an advanced and open platform to developers while at the same time protect iPhone users from viruses, malware, privacy attacks, etc. This is no easy task.
Follow the footnote and you find that Apple didn’t use a permanent link for that public statement. Because of that oversight 14 years ago, Apple was forced to point to a reliable third-party resource. One that has been trusted by Apple users for over 31 years and has worked hard over decades to ensure that old URLs to articles don’t break even across three distinct Web publishing systems.
Yes, it’s little old us. Adam Engst’s mother was for many years the Cornell University Archivist, and I hope she’s proud of her son and daughter-in-law.
The Best Mac Site-Specific Browser for Google Docs
As a writer, I live in my word processor. Precisely which app we rely on for TidBITS has changed over the years, starting with Nisus Writer Classic, then BBEdit, and now Google Docs. When we used Nisus Writer Classic, we also relied on a fileserver running AppleShare over IP to collaborate on files using a classic IN (available for editing) and OUT (checked out by someone) folder/versioning/renaming scheme. During our BBEdit years, we switched the collaboration side to the Subversion version control system, essentially treating our text like code (see “Wanted: Better Document Collaboration System,” 3 April 2006). And when we migrated to our current WordPress-based content management system (see “Next-Generation TidBITS Infrastructure in the Works,” 20 November 2017), we switched to doing all of our article writing and editing in Google Docs, which offers top-notch collaboration capabilities.
Of course, Google Docs is a Web app, and by default, it would nestle in among all the other tabs in a Web browser. That’s unacceptable for me since I often have multiple documents open along with way too many tabs for pages that I need to read, refer back to, or act on. (“Hi, my name is Adam, and I’m a tabaholic.”) As a result, I’ve always run Google Docs in a site-specific browser (SSB)—a utility that lets you turn a particular site or set of sites into a standalone app that has its own identity in the Dock, the App Switcher, and so on. Plus, I always switch to my primary word processor from wherever I am in other apps by pressing F1—that’s a Keyboard Maestro macro now, but I’ve been doing this since before Keyboard Maestro existed.
Apart from the core desire to turn Google Docs into a standalone app, I have several other requirements:
- Window and tab support: I work on a lot of documents, partly while juggling multiple TidBITS articles, but even more so in my role as president of the Finger Lakes Runners Club, which relies heavily on Google Docs and Google Sheets for administration, collaboration, and recordkeeping. I always keep one window open for TidBITS documents and another for FLRC documents; each has between 3 and 20 open tabs at any one time.
- Multiple domain support: I always keep the Google Drive Web app open as the first tab in each of those windows, and I double-click documents in Google Drive to open them in new tabs. The SSB thus needs to allow both drive.google.com and docs.google.com to co-exist in the same app.
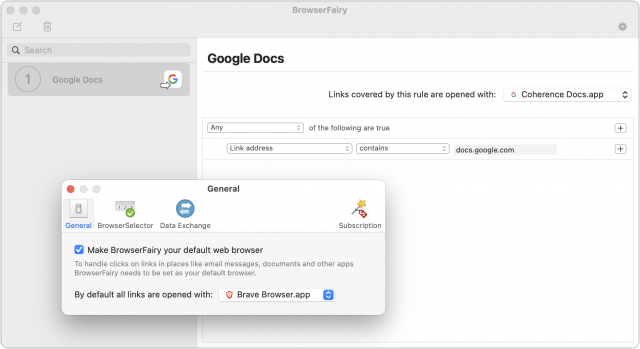
- Receive incoming Google Docs links: When I click a docs.google.com URL in Slack or Trello for TidBITS, or in Mimestream or Discourse for FLRC, I want it to open in a new tab in my Google Docs app. (It very well may open in the wrong window, but that’s a trivial annoyance.) SSBs can’t control URL destinations on their own, of course, but there are Mac utilities that can—I’ve tested BrowserFairy and Choosy and will discuss them more at the end.
- Send external links to my default Web browser: I frequently click links in articles to read them or test that they go to the right place. I want those links to open in my default Web browser—Brave at the moment—for two reasons. First, it’s what I expect—all clicked links other than docs.google.com should open in Brave. Second, having them open in Brave makes it easy for me to view them on my left-hand screen while writing on my right-hand screen.
- Grammarly support: I’m a grudgingly huge fan of the Grammarly writing assistant service. Typos, doubled words, and other mistakes creep through in anyone’s writing, and while I don’t take many of Grammarly’s writing suggestions, it’s essential for catching hard-to-see errors. Grammarly has extensions for Chrome, Firefox, and Safari, but not all SSBs support browser extensions.
For a few years, I’ve relied on the free Epichrome, a Chrome- or Brave-based SSB created by Github user dmarmor (see “Make Site-Specific Browsers with Google Chrome,” 6 March 2015). Epichrome met all my criteria above with help from BrowserFairy or Choosy, although a recent significant update caused it to open external links clicked in Google Docs internally and send them to my main Web browser—an annoying duplication. I reported that bug, but shortly after, dmarmor announced that he would stop development on Epichrome at the end of 2021.
With the writing on the wall about Epichrome’s eventual fate, I decided it was time to look elsewhere. Here’s what I found—if you know of another SSB for the Mac that might meet my criteria, let me know in the comments.
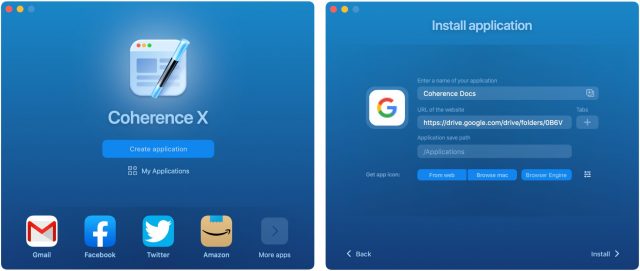
Coherence X
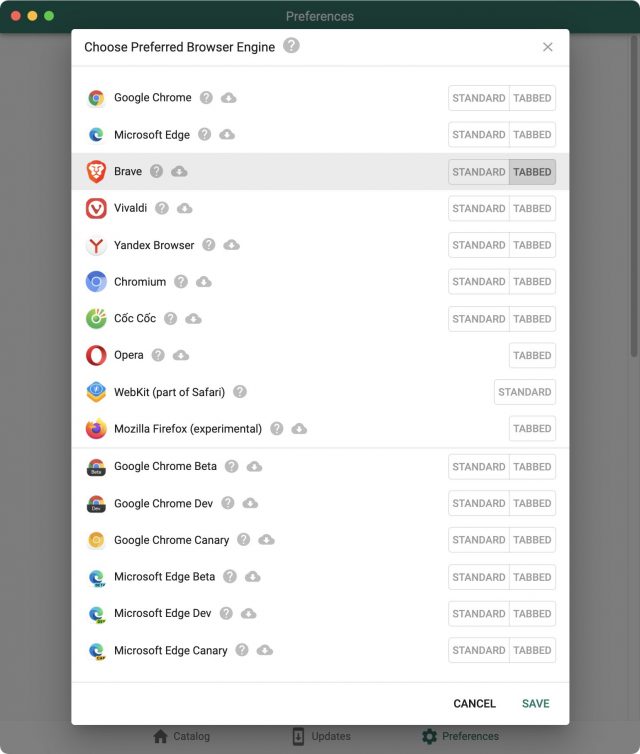
BZG’s Coherence X makes it easy to create SSBs for numerous Web apps with a single click, although it offers configuration options that let you adjust the app name and starting URL. You can of course create an SSB for any other site you wish as well.
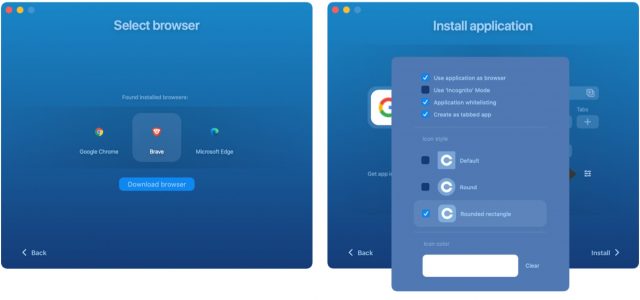
Coherence X’s advanced options are essential. The Get App Icon buttons let you download a different icon from the Web or choose an image file on your Mac (do a Google Images search for “AppName icon” for lots of choices). The Browser Engine button lets you choose between Chrome, Brave, and Edge—all three are Chromium-based engines, but you might prefer the ubiquity of Chrome, the privacy of Brave, or, well, Edge for some reason. (If you have them installed, Google Chrome Canary and Opera are also options.) Finally, the little button of sliders to the right of the three blue buttons provides access to more settings, some of which you’ll need to use:
- Use application as browser: When checked, Coherence X registers the SSB as a Web browser, which is necessary if you want to use a utility like BrowserFairy or Choosy to direct specific URLs to it.
- Use “Incognito” Mode: I have no use for this setting, but I could imagine a situation where you wouldn’t want your SSB to save browsing history, cookies, site data, or information entered in forms. (Remember, private browsing doesn’t hide your activity from websites or the organization that provides your Internet access.)
- Application whitelisting: This option controls how your SSB handles clicks on links within the SSB. When selected, it automatically ensures that links to the same domain as the SSB stay within the SSB. Later, using the Coherence Helper extension, you can set rules for what to do with other links—I prefer that they go to my default Web browser.
- Create as tabbed app: When checked, this option creates an SSB that supports tabs like a regular Web browser. That’s what I want for Google Docs, but if you didn’t want tabs, leave this unchecked to get an SSB that has only a single window.
- Icon style: Pick your preference.
Coherence X works well with BrowserFairy and Choosy. As a Chromium-based browser, it allows the installation of all Chrome extensions, including Grammarly. (BZG claims that you can import extensions and profiles from your browser and use them within created SSBs, but I didn’t run across that feature. It’s not important to me—installing Grammarly is easy enough if you set Coherence Helper to allow browsing to any URL temporarily.) As such, it ticks all my boxes above, and it’s currently my top choice for replacing Epichrome.
I do have one nit. When I click a link in Google Docs, the Coherence X SSB tries to open it in a new tab before the Coherence Helper extension realizes it should go to Brave instead. That results in a flash as a new blank tab opens and immediately closes. Cosmetically annoying, but far less so than the way Epichrome was opening all links in both new tabs and Brave.
Coherence X4 has a trial version that allows you to create three SSBs for free. If you need more than that, a license costs $29.99, or you can get it with a $9.99-per-month Setapp subscription.
Chromeless
As you might expect from its name, Chromeless can create SSBs from any Chromium-based Web browser—even more than Coherence X—and like many others, it lets you create window-only (“standard”) and tabbed apps.
However, Chromeless also lets you create “standard” WebKit-based apps that essentially encapsulate Safari, and it even claims experimental support for creating tabbed apps with the Firefox engine. Such flexibility could be important to some—I just want something that lets me use Grammarly, and Chromeless does that fine with the Brave engine.
Although Chromeless lets you edit the base URL for any SSB and remembers the open tabs across launches like any good Web browser, it always seemed to open a new Google Drive tab for my SSB at launch even though one was already open. A minor annoyance, joined by the fact that you cannot edit either the SSB name or icon.
Because it registers its SSBs as Web browsers, both BrowserFairy and Choosy can direct incoming docs.google.com URLs to the SSB. That was initially a little tricky to set up because Chromeless creates its apps by default in ~/Applications/Chromeless rather than the standard Applications folder. That appears to be a standard thing for Chromium-based browsers, but I was still surprised. It’s also a preference—you can set it to install apps in any location you prefer.
Unfortunately, even though Chromeless installs a Chromeless Helper extension, presumably to handle clicks on URLs, it has no options, and I could discern no way to direct links to open in my default Web browser. Every link I clicked in Chromeless opened in Chromeless itself. That’s a major strike against it.
On the plus side, Chromeless is free and open source, and it’s also available for Windows and Linux if you have SSB needs on those platforms. It’s developed by the same company behind WebCatalog, discussed below.
Flotato
You say Flotāto, I say Flotăto
Let’s call the whole thing off.
Much as I love the name, Flotato is a non-starter for me in nearly every way. At launch, it shows a window full of icons for SSBs you can create by clicking a Get button. Once you’ve made the app, it appears in your Applications folder like any other app, or you can click Open to launch it from Flotato. You can also create an SSB from any URL.
That’s all fine, of course, but the apps Flotato creates are window-based, rather than tab-based. Although I can make a Google Docs app and even have it start with my Google Drive URL, opening a document takes over the entire window. The only way to open another document is to choose App > New Window and go through Google Drive again. Flotato doesn’t remember window sizes either, so you have to resize every new window you create.
I don’t know what Flotato uses under the hood to create its SSBs, but I suspect it’s WebKit because there’s no mention of supporting Chrome extensions. You can ask Flotato to display the mobile version of a Web app, which could be handy for lightweight Web apps with a minimal interface and well-designed mobile versions, but is meaningless for Google Docs, which thrives in a large-window environment.
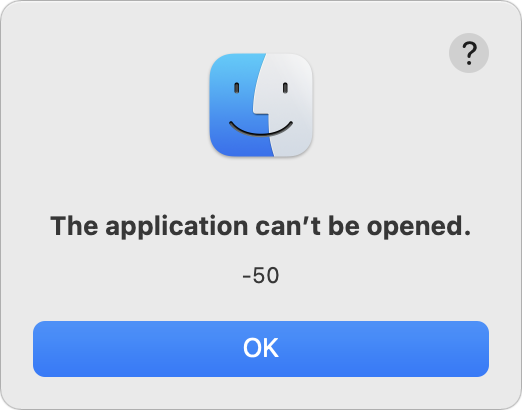 Plus, Flotato doesn’t register its SSBs as Web browsers, so BrowserFairy and Choosy can’t send docs.google.com URLs to a Flotato SSB. By default, clicking a link in a Google Doc within Flotato opens it in a new Flotato window, but you can Shift-click to open in the default browser. In theory, at least—roughly half the links I tried to Shift-click threw an error saying that the application can’t be opened.
Plus, Flotato doesn’t register its SSBs as Web browsers, so BrowserFairy and Choosy can’t send docs.google.com URLs to a Flotato SSB. By default, clicking a link in a Google Doc within Flotato opens it in a new Flotato window, but you can Shift-click to open in the default browser. In theory, at least—roughly half the links I tried to Shift-click threw an error saying that the application can’t be opened.
You can use a single Flotato app at a time for free. You just have to quit one to launch another. To run as many Flotato apps as you want simultaneously, you’ll need to pay $19 for Flotato Pro.
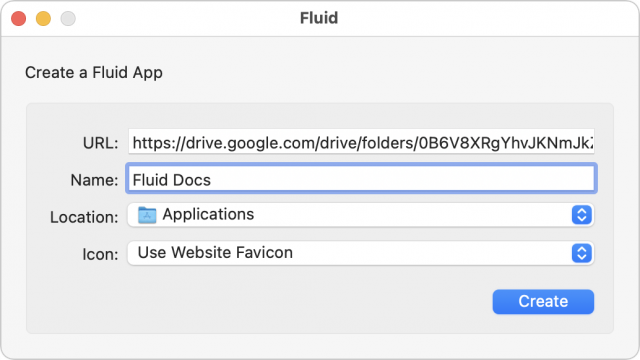
Fluid
Fluid has been around for a long time on the Mac, but it has never worked well for me. Setting up a new SSB requires providing a URL and app name; you can also choose a location on your Mac for the new app and use either the site’s favicon or another image.
But from there, everything goes downhill. To start, Fluid wouldn’t display the Proxima Nova font that we use in Google Docs and replaced it with some serif font, which is just odd. You can choose to display a toolbar (which gets you an address bar and buttons at the top) with a bookmarks bar and a tab bar below. Perhaps it’s related to Fluid not being updated for the Big Sur design, but I found the stacked gray bars at the top jarring.
More problematic was that Fluid was incapable of opening any Google Sheets. Whenever I tried, I got a Google Sheets error about freeing up application resources, followed by a Mac error about JavaScript. I could find no workaround.
Fluid registers its SSBs as browsers, so there was no problem with using BrowserFairy or Choosy to direct incoming docs.google.com URLs to my Fluid SSB. However, even though Fluid has a Whitelist preference pane in which you can theoretically cause clicked links to open your default browser, I found it entirely random. Even clicking the same link twice in quick succession would sometimes result in one click opening the link in Brave and the second click opening it in Fluid’s SSB. Fluid does offer one neat feature—left and right browser panels that can contain their own Web pages. You’ll need to whitelist their URLs, of course.
Because Fluid is based on WebKit, it walks, talks, and quacks like Safari. However, it does not, as far as I can tell, support Safari extensions—or Chrome extensions, of course—which means that I can’t use Grammarly with it. Overall, Fluid just isn’t a contender for use with Google Docs.
Fluid is free for as many SSBs as you’d like to create, but for $5, you can pin Fluid apps to the macOS menu bar, use Userscripts or Userstyles in your apps (I’m not sure what that means either), and use full-screen mode.
Unite
Developed by BZG, the same people behind Coherence X, Unite offers a different take on the SSB concept. The key difference between Coherence and Unite is that Coherence X can use any Chromium-based browser as its engine, whereas Unite leverages WebKit 2, the same engine underneath Safari.
Unite’s use of WebKit makes it more of a first-class Mac citizen, lets it enjoy much smaller app sizes, and allows it to encapsulate Web apps in other forms of app wrappers. It can create status bar apps that live in the menu bar, compact apps that try to recreate a phone-like experience, or tabbed apps. None of its special app forms were of interest to me since my primary use is for Google Docs, where I want a normal tabbed SSB.
When it comes to incoming links, Unite works fine with BrowserFairy and Choosy. With regard to outbound links, it suffers from the same problem as Coherence X—a flash as a tab opens and closes while the link loads in my default Web browser.
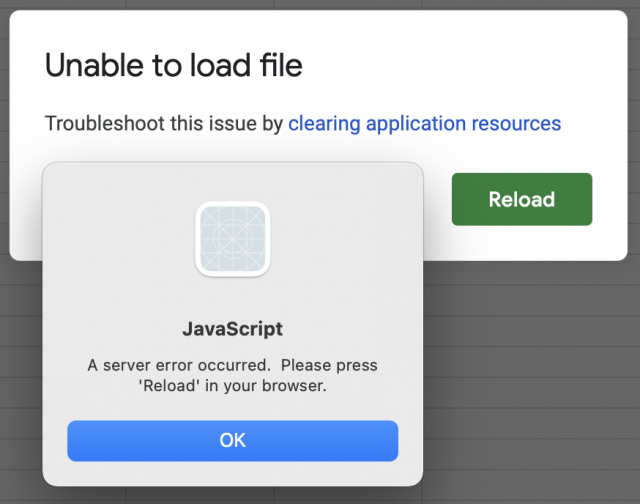
Alas, Unite has two major strikes against it for my purposes. First, much like Fluid, it cannot open any Google Sheets documents. Whenever I try, I get a Google Sheets message about how something went wrong and an error saying it was unable to load the file.
Second, the negative consequence of its reliance on WebKit prevents it from supporting Web extensions like Grammarly. In short, even if Unite worked with Google Sheets, I’d ding it on the lack of Grammarly support.
The trial version of Unite is free for three apps, or you can buy it for $24.99 or get it with a $9.99-per-month Setapp subscription.
Wavebox
Most of the other site-specific browser solutions I tested are fairly simple, letting you create standalone apps for specific websites. Wavebox is not simple. Wavebox wants to give you a single coherent workspace for all your Web apps. You may find this overwhelming—I did.
To start, you need to create an account. I’m not sure why this is necessary—perhaps syncing of workspaces across devices. Then you need to provide your email address(es), after which Wavebox creates a workspace for you with the sites matching your email domains.
Wavebox is based on Chromium, so it does support Chrome extensions, and it goes so far as to help you install some popular extensions, including Grammarly, during setup. Once you’ve finished the setup assistant, you’re dropped into a browser-like environment with a sidebar for your apps. You can add additional apps or websites to the sidebar.
Initially, it seemed as though Wavebox was going to work the way I wanted. My Google workspace had a pinned tab for Google Drive, and double-clicking a Google Doc in there opened it in a new tab in the same window. However, when I clicked a docs.google.com link in Slack and relied on BrowserFairy or Choosy to open it in Wavebox, it always opened in a new Wavebox window. Subsequent clicks on similar external links also opened as new tabs in that window. As a result, I always ended up with two windows, one with tabs for documents opened from Google Drive and another with tabs for documents opened from other apps. It was, like everything else in Wavebox, confusing. I tried adding Google Docs as an app in the Google workspace and as its own workspace, but that muddied the waters even further.
Dealing with outbound links was equally mind-bending. Wavebox offers numerous options for handling them, including specific options for what to do when various modifier keys are down. I struck out in getting the basic behavior I wanted, which was to have all links open in my default Web browser. Wavebox acknowledges the complexity of its situation with a general knowledgebase article and another listing caveats for links opening in the default browser.
In the end, I gave up on Wavebox in frustration. It’s clearly trying to solve some problem that’s far more complex than my simple desire to encapsulate Google Docs in a site-specific browser. It may address that problem well, but it didn’t do what I wanted.
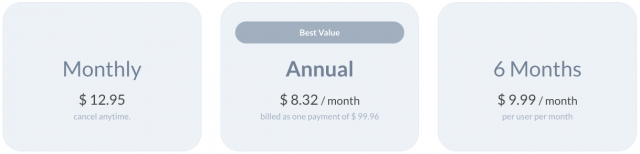
Even Wavebox’s business model is tangled. There are prominent Download buttons on its main page and no information about pricing in the top navigation bar, suggesting that it’s free. However, in the bottom navigation bar, there is a Pricing link that reveals that Wavebox Pro costs $12.95 per month where you can cancel anytime, $8.32 per month if billed annually, or $9.99 per month for six months, with no indication of how that’s billed (the company clarified the interface after publication). And yes, the options are presented in that mixed-up order. Or you could just use Wavebox Basic—the first time I’ve seen that term—for free, although I could find no chart outlining which features are in Wavebox Basic and which are exclusive to Wavebox Pro.
WebCatalog
WebCatalog is the company behind both Chromeless and the WebCatalog SSB solution. You might therefore expect WebCatalog to be an enhanced version of Chromeless, and at a conceptual level, that’s true. Along with the same set of Web apps in the Discover view, WebCatalog adds the idea of Spaces that let you bring together related Web apps, such as the many apps Google provides. You can also create custom spaces and switch between the internal apps with keyboard shortcuts. Spaces even support multiple accounts, so you could have a space that’s logged into different Google accounts, for example.
Apart from some user interface similarities, however, Chromeless and WebCatalog are quite different. WebCatalog doesn’t let you pick a browser engine and instead creates its apps within an Electron shell. Electron is an open-source framework from GitHub that many companies use to create desktop versions of essentially Web-based apps—Slack is an Electron app, for instance. Although Electron relies on the Chromium rendering engine, you can’t make bookmarks, use tabs, or install Chrome extensions.
As such, WebCatalog simply doesn’t work for me. I couldn’t figure out any way to get Google Docs running in a tabbed window, and double-clicking documents from Google Drive opened them in separate windows. Nor could I see any way to install the Grammarly extension. On the plus side, WebCatalog does handle outbound URLs better, so you can specify which should be opened in the SSB and which should be sent to the default Web browser.
You can use WebCatalog for free, but you’re limited to ten installed apps and spaces, and you can have only two accounts per app or space. For $40, the one-time Lifetime plan lifts those restrictions and adds ad blocking and the capability to lock apps with passwords or Touch ID.
Any Old Web Browser
At some point, while writing about how many browser engines Chromeless supported, I had a thought. “Why not just devote an entire browser to Google Docs?” It’s not as though I need to use Microsoft Edge or Opera for anything else. This would work perfectly, with one sticking point: directing clicks on outbound links to my default Web browser.
Both BrowserFairy and Choosy let you create rules that specify where links clicked in a particular app should open, and in quick testing with Slack, those features work correctly. However, they don’t work for links in Web browsers—there’s just no way short of an extension to redirect links from one Web browser to another.
In fact, both BrowserFairy and Choosy offer nearly identical browser extensions, but they provide only two features: a menu bar button in the browser that opens the current page in BrowserFairy/Choosy and a BrowserFairy/Choosy option in the contextual menu when you Control-click a link. Neither captures all clicks by default.
It’s conceivable that there’s some other way to capture all link clicks, even within a Web browser, and redirect them to another browser without additional interaction, but given that Coherence X does everything I want, there’s no need to search further or compromise on dealing with outbound links. Nonetheless, if you can figure out a way to do this, I’m curious.
(Developer Jeff Johnson wrote on Twitter to say that his $9.99 Stop the Madness extension can redirect link clicks, though only in Safari.)
https://twitter.com/lapcatsoftware/status/1406000616078520320?s=20
Comparing BrowserFairy and Choosy
I’ve been testing each of these SSBs with both BrowserFairy and Choosy, under the assumption that there might be a difference. However, as you will have noted, they work equivalently—everything that worked in one worked in the other.
That’s not a guarantee, though. I also tested Bumpr, an attractive link redirector written by Scott Ostler and designed in part by friend-of-TidBITS Khoi Vinh. Although I like Bumpr a lot in general, it doesn’t yet support site-specific browsers. A quick search in the Mac App Store revealed additional utilities in this field, including Browser Ninja, OLW: Open Link With, OpenIn, and Redirector, among others. I don’t know if they support SSBs either.
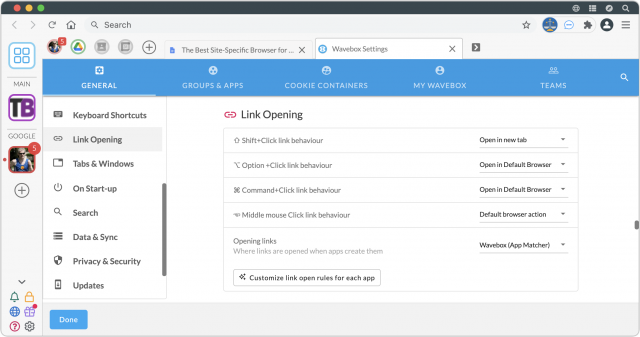
With BrowserFairy, you need to make sure it’s the default Web browser, which is easily done on launch or in the General preference pane. Then you need to add a rule that looks for docs.google.com in the link address and open links covered by that rule in your SSB. It takes only a minute or two to set things up as I have in the screenshot below.
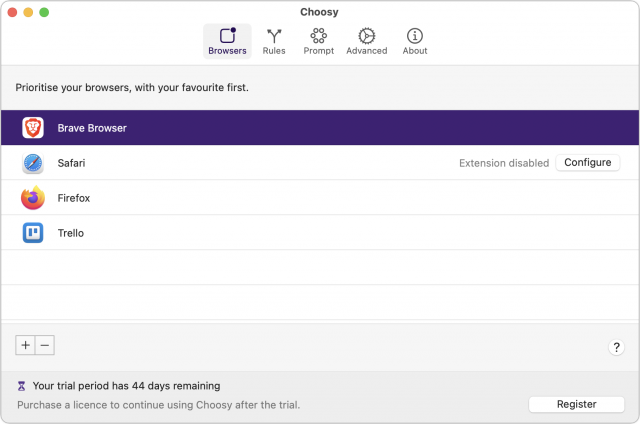
Choosy is slightly more complicated, although more flexible. The first thing to do is add and arrange your Web browsers in the Browsers screen, making sure to put your favorite browser at the top.
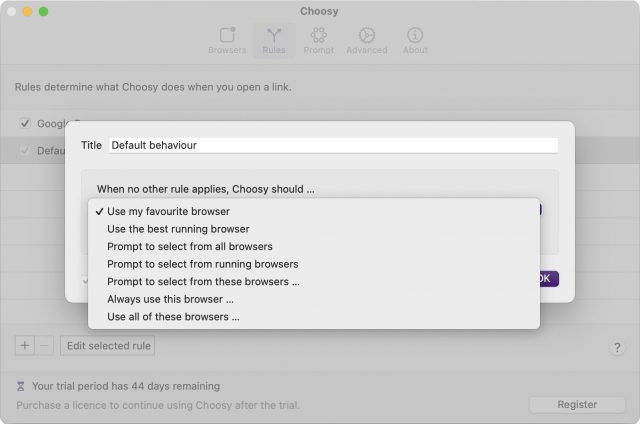
Next, in the Rules screen, double-click the Default Behavior rule that applies when no other rule does. You can choose from using your favorite browser, the best running browser, a specific browser, or even a set of browsers (great if you’re a Web designer testing pages in multiple browsers). Or you can have Choosy prompt you to select a browser from a specific set, from the running browsers, or from all available browsers.
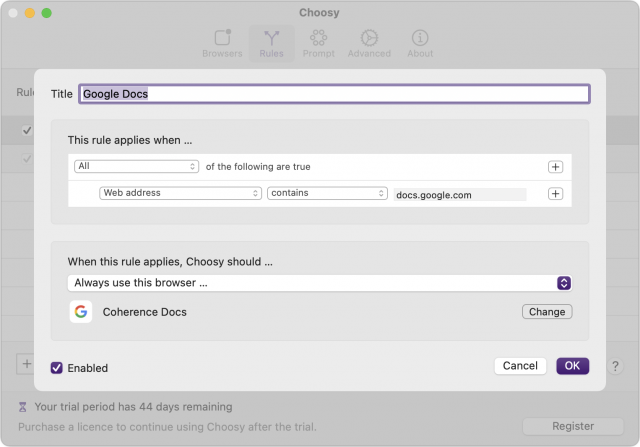
Finally, you’ll want to create a new rule that captures docs.google.com links and sends them to your SSB. That’s easily done as well—just copy the screenshot below.
Given that both work well, my suggestion is as follows:
- If you need three or fewer rules, use BrowserFairy, since you can get by fine with the free version. For more than three rules, you would need to subscribe for $0.99 per month or $8.99 per year.
- If you need more than three rules, buy Choosy, which requires a one-time $10 purchase made via PayPal. Choosy also offers an API that lets you trigger it programmatically if you want direct access.
Going the Coherent Route
In the end, I’m going to use the combination of Coherence X and BrowserFairy. Only Coherence X could satisfy all my criteria, and its cosmetic problem with opening and closing tabs while processing outbound links is annoying but not a deal-breaker. Your needs may differ from mine, and if that’s the case, I hope the evaluations above help you pick the best SSB for your situation.