#1473: MacBook Air and 13-inch MacBook Pro updates, fixing the Zoom exploit, analyzing Apple’s privacy initiatives
Apple has updated the MacBook Air with a True Tone display and a price cut, added a Touch Bar to the entry-level 13-inch MacBook Pro, and retired both the basic MacBook and the non-Retina MacBook Air. A nasty vulnerability in the Zoom video conference software sent heads spinning last week—we document the saga and explain how to protect yourself. Finally, Rich Mogull joins us this week to examine Apple’s privacy initiatives in light of this year’s Worldwide Developers Conference. Notable Mac app releases this week include PDFpen and PDFpenPro 11.1 and Logic Pro X 10.4.6.
Apple Updates Air, Pro Laptops, Kills off the MacBook
Apple’s laptop line has long been a bit of a mess, especially on the low end. Those looking for an affordable notebook have faced confusing (and somewhat conflicting) options: The 12-inch, ultraportable MacBook? The low-end MacBook Pro, the one without a Touch Bar? The recently revamped MacBook Air?
The decision is now a lot simpler. Apple has dropped the long-neglected MacBook, notorious for being underpowered and, inconveniently, having only one USB-C port. At the same time, Apple has sweetened the MacBook Pro and MacBook Air, largely with entry-level shoppers in mind.
The Pro model informally known as the “MacBook Escape”—so nicknamed because of its physical Function and Escape keys that the Touch Bar replaces on higher-end versions—is kaput. Now the entry-level MacBook Pro has a Touch Bar and other upgrades—along with a price drop for college students.
The MacBook Air, which saw a top-to-bottom refresh in October (see “New MacBook Air Is a Compelling Upgrade in a Confusing Laptop Lineup,” 30 October 2018), has been tweaked a bit more with display refinements, and comes with a price drop on the low end and an even sweeter deal for college students.
MacBook Pro
Apple updated its high-end MacBook Pro models in May (see “Apple Updates MacBook Pros with 8-core Processors and a Keyboard Fix(?),” 21 May 2019), but left the low-end model sadly neglected. Now that model is getting some love.
The latest low-end MacBook Pro provides a 1.4 GHz quad-core 8th-generation Core i5 processor (with Turbo Boost up to 3.9 GHz), which is part of Intel’s Coffee Lake chipset family. This is an update from the MacBook Escape’s 2.3 GHz dual-core 7th-generation Core i5 offering. For $300 you can upgrade the machine to a 1.7 GHz Intel Core i5 (with Turbo Boost up to 4.5 GHz).
The MacBook Pro includes 8 GB of 2133 MHz LPDDR3 memory, which you can upgrade to 16 GB for $200 (and we strongly recommend that you do).
This new model comes in two stock configurations: one with 128 GB of SSD storage for $1299 and one with 256 GB for $1499. College students get the 128 GB model for $1199. The 128 GB model can be upgraded to 256 GB of storage for $200, 512 GB for $400, 1 TB for $600, or 2 TB for $1000. The 256 GB model can be upgraded to 512 GB for $200, 1 TB for $400, or 2 TB for $800.
The MacBook Pro comes with a 58.2-watt-hour lithium-polymer battery that offers up to 10 hours of battery life.
Whether the entry-level MacBook Pro’s other changes are an improvement is in the eye of the beholder. Not everyone likes the Touch Bar, which many regard as more of a hindrance than a useful tool (see “What’s Wrong with the Touch Bar,” 4 August 2017), and some have been delighted by the existence of a Pro model with physical function keys.
Other changes to the MacBook Pro are likely to be less controversial. Along with the Touch Bar, the MacBook Pro gains Touch ID—useful for log-in authentication and for online purchases on compatible sites—along with Apple’s T2 security chip.
One potential limitation is unchanged: the entry-level MacBook Pro only has two Thunderbolt 3 ports, compared with four ports on the high end models.
The MacBook Pro comes in two colors: silver and space gray.
MacBook Air
Apple’s updates to the MacBook Air line aren’t quite as momentous.
New on all MacBook Air models is the display technology known as True Tone, which adjusts the screen’s white balance to compensate for ambient lighting, making images appear more natural. True Tone is already present on MacBook Pro models and on newer iPhones and iPads.
Those who recently bought a MacBook Air should not feel much upgrade envy since True Tone is a modest enhancement. The line’s internals remain unchanged, with all models running Intel dual-core 8th-generation i5 chips. Still, this might be a good time for MacBook Air holdouts to take the plunge because the next Air refresh is probably at least a year out.
MacBook Air buyers get a price break, as well: $1,099 for the entry-level model with 128 GB of storage, down from $1,199. Upgrading to 256 GB of storage runs $1,299. College students can score the 128 GB model for $999.
A 49.9‑watt‑hour lithium‑polymer battery that provides up to 13 hours of battery life powers the revamped notebook.
The MacBook Air comes with 8 GB of 2133 MHz LPDDR3 memory, which can be upgraded to 16 GB for $200 (again, strongly recommended). The 128 GB model can be upgraded to 256 GB of storage for $200, 512 GB for $400, or 1 TB for $600. The 256 GB model can be upgraded to 512 GB for $200 or 1 TB for $400.
Apple offers the MacBook Air in three colors: gold, silver, and space gray.
About the Keyboard…
As for Apple’s famously problematic butterfly keyboard, the company does not appear to have made any new tweaks since its last attempt in May to address user complaints.
As a sure sign that the keyboards remain largely unchanged, the new notebooks—along with existing MacBook, MacBook Air, and MacBook Pro variations going as far back as 2015—are eligible for an Apple keyboard-repair program intended to address major malfunctions.
Detractors of the butterfly keyboard might want to keep holding out—there are rumors of a revamped scissor-style keyboard just over the horizon, but nothing is confirmed at this point.
Air vs. Pro
Those who find themselves torn between the MacBook Air and Pro should consider the following:
- For a $200 premium, the Pro provides a quad-core speed boost over the Air’s two cores (currently there is no quad-core Air option). As Mac expert Stephen Hackett notes, “While the base clock speed is slower on the Pro, its Turbo Boost frequency is higher, and in its higher-TDP application, the Pro should be able to sustain higher speeds for longer.”
- The Pro screen is brighter at 500 nits, 100 more than the Air’s screen. This isn’t night and day, but noticeable. The Pro also supports the P3 wide color gamut, and the Air doesn’t.
- The Pro has superior graphics capabilities—Intel Iris Plus Graphics 645 compared to Intel UHD Graphics 617 on the Air.
- Touch Bar haters have the Air to adore, and don’t miss out on Touch ID.
- The Air has a gold color option, while the MacBook Pro does not.
- The Air has up to three more hours of battery life than the Pro.
- Going with an Air and putting the $200 savings into extra RAM is not a bad move—extra memory never is. Here at TidBITS, we use a minimum of 16 GB of RAM in our machines.
Bye, MacBook
So what are we to make of the four-year-old MacBook’s demise?
The laptop (see “The 12-inch MacBook: A Different Mac for a Particular User,” 29 April 2015) got mixed reactions from the get-go. Its high portability and lovely Retina screen were welcomed compared to the bulky, non-Retina MacBook Air of the time. But Apple got knocked for minimalist overreach by providing just one USB-C port, forcing its users to get awkward dongles. It was overpriced as a MacBook Air heir apparent, too.
Nor did the MacBook get more appealing with age, especially since Apple didn’t fall over itself to keep the internals up to date. The lack of Thunderbolt 3 connectivity on its single USB-C port was a major issue and created confusion between USB-C-only ports (on MacBook and many devices) and Thunderbolt 3 ports (on all other recent Macs and iPad Pro models). Nonetheless, the MacBook did retain stalwarts, who raved about how small and light it was.
But with last year’s MacBook Air revamp, the MacBook seemed to have been put on life support. Now, with a refreshed Macbook Air and the introduction of a new, far-more-appealing entry-level MacBook Pro, the plug officially has been pulled on the Macbook. The non-Retina MacBook Air is also gone from Apple’s lineup, except for educational institutions.
The good news: Shopping for an entry-level Apple notebook just got much less confusing.
Zoom and RingCentral Exploits Allow Remote Webcam Access
Recently, software engineer Jonathan Leitschuh uncovered a major security flaw in the Mac client for Zoom, a video conferencing system popular with businesses, and RingCentral, which is a rebadged version of Zoom. Zoom made it so that when you clicked a Zoom link and had the client installed, the link automatically opened the Zoom client. It turns out that this implementation isn’t secure, because an attacker can create a link that will automatically join you to a call and turn your video camera on. (Note that it cannot disable the green LED indicator of the FaceTime cameras in the Mac, so if you use that camera exclusively, you always know when it’s on.)
Even worse, you couldn’t eliminate the vulnerability by merely deleting the Zoom app, because Zoom installed a hidden Web server on your Mac that would reinstall the Zoom client for you if necessary when you clicked a Zoom link.
Initially, Zoom defended its use of the hidden Web server, but quickly repented, and released an update, version 4.4.4 (53932.0709), that removes the hidden Web server and offers an option to completely uninstall Zoom. The company has promised additional updates to improve user privacy.
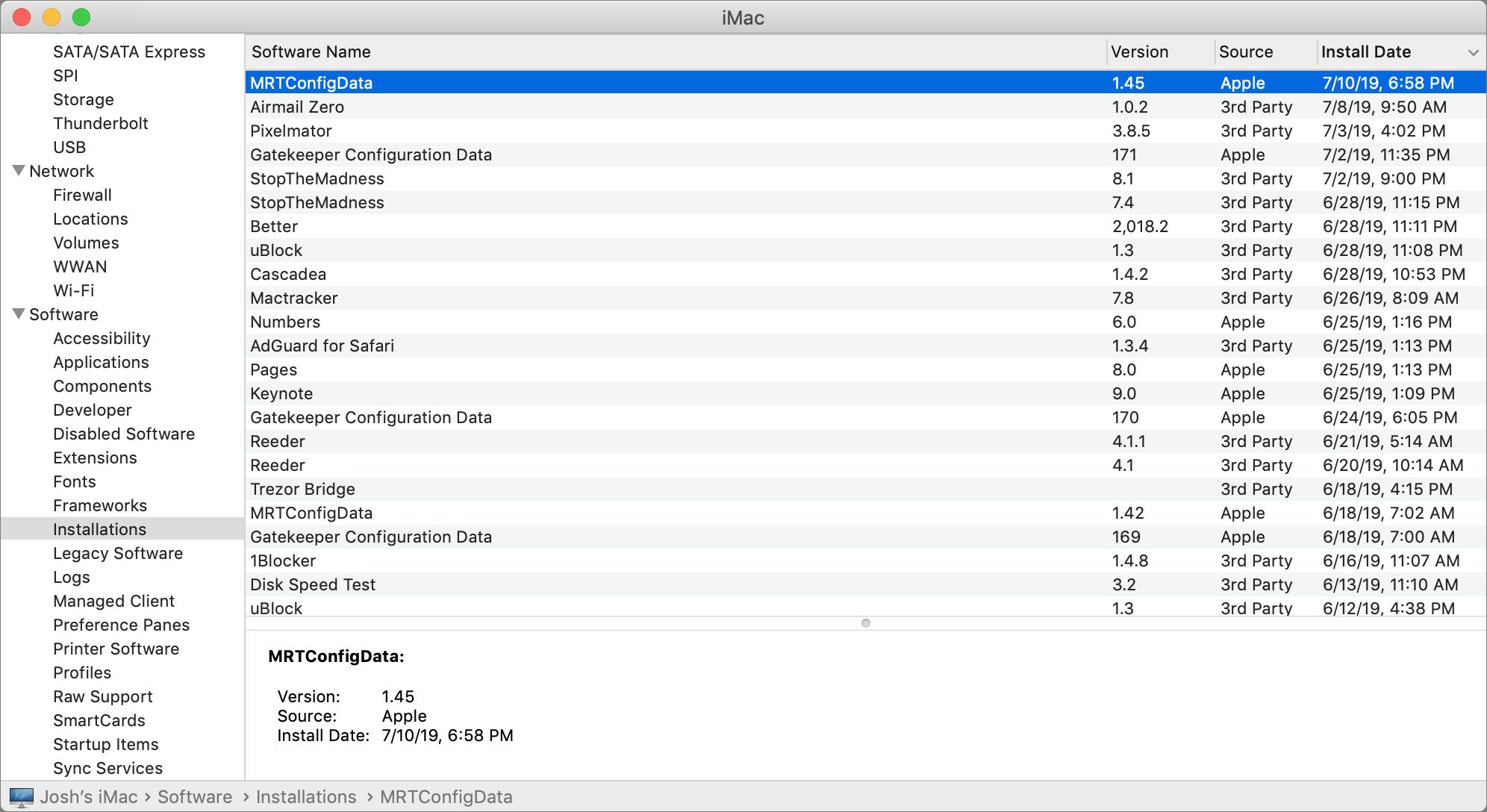
To make sure that users who neglect to update the Zoom app are not exposed, Apple released a silent macOS update that removes the hidden Web server. The update installs automatically without any interaction on your part. To see if it’s installed, open System Information in /Applications/Utilities, and click Installations, which is under Software in the sidebar. Click the Install Date column header so that you see the latest installations first, and look for MRTConfigData, which should be at version 1.45 or above. (Hat tip to Howard Oakley for this tidbit.)
Reader Al Varnell has told us that Apple’s update did not remove the RingCentral Web server, so you’ll have to update its client to the latest version to get rid of it.
Unfortunately, the hidden Web server was only part of the vulnerability. Even after the server is uninstalled, it’s possible for a Mac to inadvertently join a Zoom conference with the Web cam enabled.
How to Tell If You’re Affected
To test for the vulnerability for yourself, the easiest way is to click one of the links below, which Leitschuh set up as proofs of concept. The second link will activate your Web cam automatically. Be warned that if the vulnerability is present clicking either link will drop you into a video conference, likely with other people as freaked out as you are.
https://jlleitschuh.org/zoom_vulnerability_poc/
https://jlleitschuh.org/zoom_vulnerability_poc/zoompwn_iframe.html
Fixing the Zoom Vulnerability
The Apple update takes care of the hidden Web server, but you can still be tricked into clicking a Zoom link that activates your Web cam. Here is how to avoid that.
First, check if you have the latest version of the client by opening Zoom and choosing zoom.us > Check for Updates. If the app prompts you, click Update Now to update it.
Note that version 4.4.4 (53932.0709) adds a Zoom icon to your menu bar. You can disable that by opening Zoom, going to zoom.us > Preferences > General and unchecking “Add Zoom to macOS menu bar.”
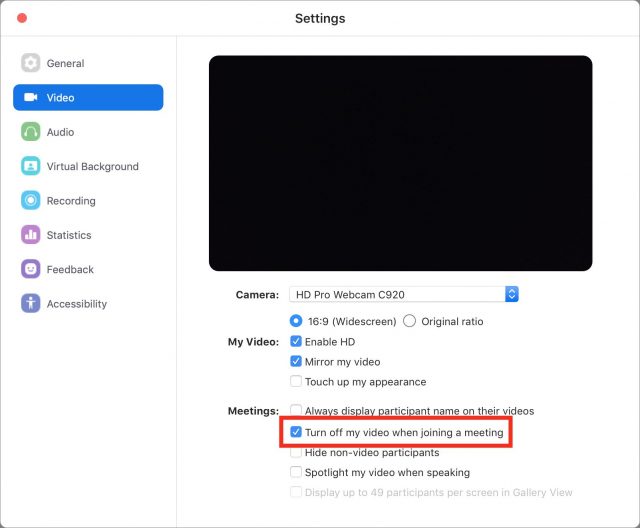
To prevent Zoom from activating your Web cam without your explicit consent, open Zoom and choose zoom.us > Preferences (Command-,), click Video in the Settings window’s sidebar, and check the “Turn off my video when joining a meeting” option.
If you use Chrome or Firefox as your browser, you’ll also want to check and change some settings to prevent Zoom links from opening automatically, per Karan Lyson on GitHub, because it’s possible that you gave Zoom permission to open Zoom conferences automatically when you click a Zoom link. (This doesn’t affect Safari.)
But if you don’t want to fool with these settings, it’s easier to uninstall Zoom entirely (and we wouldn’t blame you if you did). Open Zoom, choose zoom.us > Uninstall Zoom.
To fix this in Chrome:
- Quit Chrome by choosing Chrome > Quit Google Chrome.
- Open your user library folder in the Finder by holding Option, choosing Go in the menu bar, and choosing Library.
- Open the Application Support folder and navigate to
/Google/Chrome/Default. - Double-click the Preferences file, which opens in TextEdit by default.
- Press Command-F to open Find, and search for
"zoommtg":falseand"zoomrc":false(just search for “zoommtg” and “zoomrc” to reveal them). - If these strings exist, delete them and the comma immediately after.
- Choose File > Save, close TextEdit, and re-open Chrome.
Fortunately, this is easier in Firefox:
- Choose Firefox > Preferences.
- Click in the Find in Preferences field.
- Search for
zoommtgandzoomrc. - If these preferences are found, change them to “Always ask.”
As for the Web server that Zoom snuck onto Macs, between Apple’s update and the Zoom update, it should be eliminated. I’ve tested and confirmed this on my machine by deleting the hidden ~/.zoom file I made in Terminal and reinstalling Zoom, which didn’t recreate the directory that older versions kept the Web server in (see my description of the old Terminal method below if you don’t know what I’m talking about). Don’t take my word for it: you can check yourself by opening Terminal, entering the following command, and pressing Return:
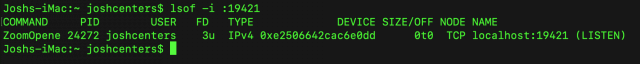
lsof -i :19421
That command searches for services listening on port 19421, which is the port that both Zoom and RingCentral used. After the update, it should dump you back to the command line with no result. Under older versions of Zoom, you’d see an entry called ZoomOpene like in the screenshot below.
You can also enter ls ~/.zoom, which should return with “No such file or directory” after updating to version 4.4.4 (53932.0709).
The Old Terminal Method
Before the Apple update and Zoom’s 4.4.4 (53932.0709) update, you had to use Terminal wizardry to disable the hidden Web server. You no longer need to do any of this to fix Zoom, but I’m leaving it here both for historical reference and because this is a handy technique to be aware of in case another app pulls a stunt like this.
First, open Terminal and enter kill -9 PID, with PID (process identification number) being the PID that you saw when you ran lsof -i :19421. In my case, that PID was 24272, so I ran kill -9 24272. After you kill the process, you can run lsof -i :19421 again to confirm it worked; if successful, Terminal will return with its normal command prompt.
Then, create a new file in the Web server’s place, and set its permissions so Zoom can’t overwrite the file:
rm -rf ~/.zoomus; touch ~/.zoomus && chmod 000 ~/.zoomus;
If you’ve used RingCentral, you’ll have to use a different set of commands to disable the Web server. As I described above, use kill -9 PID to kill any process on port 19421 (which you can find with lsof -i :19421) and then run this command:
rm -rf ~/.ringcentralopener; touch ~/.ringcentralopener &&chmod 000 ~/.ringcentralopener;
Note that you’ll have to follow these steps for every user account on your Mac.
Interestingly, removing the Web server doesn’t disable Zoom or RingCentral functionality at all.
Questionable Judgement
Thankfully, Zoom has (sort of) addressed its issues, but only after intense pressure.
TidBITS Security Editor Rich Mogull had this to say about the vulnerability: “Zoom’s efforts to circumvent Safari’s native security are completely irresponsible. The Web server ‘feature’ merely adds a small amount of convenience at a massive security cost. This is a flagrant and deliberate security and privacy violation that raises serious concerns over Zoom’s internal security prioritization and threat modeling.” We agree. And as Steve Troughton-Smith pointed out, bad actors like Zoom justify Apple’’s continued efforts to lock down macOS.
If you have to use Zoom, you can rest assured for now that the known issues have been addressed. But what’s less assuring is that there may be other security and privacy issues lurking beneath the surface, waiting to be discovered. And with Zoom already showing incredibly poor judgment, we advise uninstalling the client unless you absolutely need it.
Apple Flexes Its Privacy Muscles
Apple events follow a consistent pattern that rarely changes beyond the details of their particular announcements. This consistency becomes its own language. Attend enough Apple events and you start to pick up the deliberate undertones that the company wants to communicate but not directly express. These are the postures and facial expressions that accompany the words of the slides, demos, and videos.
Five years ago I walked out of the WWDC keynote with a feeling that those undertones were screaming a momentous shift in Apple’s direction, that privacy was emerging as a foundational principle for the company. I laid out my interpretation of Apple’s privacy principles in this piece in Macworld. Privacy had been increasing in importance for years before at Apple, but that WWDC keynote was the first time the company clearly articulated that privacy not only mattered but was being built into its foundational technologies.
This year I sat in the WWDC keynote, hearing the undertones, and realized that Apple is upping its privacy game to levels never before seen from a major technology company. That is, beyond improving privacy in its own products, the company is starting to use its market strength to extend privacy through the tendrils that touch the Apple ecosystem.
Regardless of Apple’s motivation—altruism, the personal principles of Apple executives, or a shrewd business strategy—Apple’s stance on privacy is unique and historic in the annals of consumer technology. The real question now isn’t if Apple can succeed at a technical level, but if its privacy push can withstand the upcoming onslaught from governments, regulators, the courts, and its competitors.
Apple executives say that they believe that privacy is a human right. History, however, is strewn with the remains of well-intentioned champions of such rights.
Sign in with Apple
When discussing shifts in strategy, whether at Apple or any other technology firm, we should keep in mind that such changes typically start years earlier and are more gradual than we realize. In the case of Apple, the company’s privacy extension efforts started at least a couple years before WWDC 2014, which was when Apple first started requiring privacy protections for developers who wanted to participate in HomeKit and HealthKit.
The most obvious privacy push to come out of WWDC 2019 is “Sign in with Apple,” which offers benefits to both consumers and developers. Additional WWDC sessions made it clear that Apple is using a carrot-and-stick approach with developers: developers are required to use the service when they include competing offerings from Google and Facebook, but, in exchange, they also gain built-in fraud prevention. Every Apple ID is already vetted by Apple and secured with two-factor authentication, and Apple provides developers with the digital equivalent of a thumbs-up or thumbs-down indicating whether Apple’s monitoring code thinks the connection is from a real human being. Since Apple uses similar mechanisms for iCloud activity, iTunes, and App Store purchases, the odds are that this is a reliable indicator.
Apple also emphasized that Sign in with Apple extends this privacy to the developers themselves, saying that it isn’t Apple’s business to know how developers engage with their users in their apps. Apple serves merely as an authentication provider and collects no telemetry on user activity. This isn’t to imply that Google and Facebook necessarily abuse their authentication services. Google denies these accusations and also offers features to detect suspicious activity. Facebook, on the other hand, has famously abused phone numbers supplied for two-factor authentication.
The difference between Sign in with Apple and previous privacy requirements within Apple’s ecosystems is that the feature extends Apple’s insistence on privacy beyond the company’s walled garden. Previous requirements—from HomeKit’s data use strictures to App Store rules about how apps can collect and use data—applied mostly to apps running on Apple devices. While this is technically true for Sign in with Apple, practically speaking the implications extend much further.
That’s because, when developers add Sign in with Apple to an iOS app, they likely also will need to add it to their apps on other platforms if they expect their customers to ever use anything other than an Apple device. If they don’t, they will create a confusing user experience (which, I hate to say, we will likely see a lot of). Once users create their accounts for an app with their Apple IDs, there are technical complexities in supporting those same user accounts with alternative login credentials. Thus developers likely will support Sign in with Apple across all their different platforms, extending the feature’s inherent privacy beyond Apple’s usual reach.
Intelligent Ad Tracking Prevention
Two other technologies stand out as additional examples of how Apple is extending its privacy regime. The first is an important update to intelligent tracking prevention for advertising. Privacy-preserving ad-click attribution provides (at least some) privacy in the ugly ad-tracking market. The second technology is HomeKit Secure Video, which offers a new privacy-respecting foundation to video security firms that want to be feature-competitive without dealing with the mess of building their own back-end cloud services.
Let’s look first at Intelligent Tracking Prevention. This Safari feature reduces the ability of services to track users across different Web sites. The idea behind it is that users can and should be able to enable cookies for a trusted site without having additional trackers continue to monitor them through the rest of their browsing to other sites. Cross-site tracking is epidemic, with many sites hosting dozens of trackers. Such tracking is meant to support advertising and to provide one key marketing metric: did an ad lead the user to visit the target site and buy something?
Effective tracking prevention is an existential risk to online advertisers and the sites that rely on advertising for income, but increased scrutiny from Apple (and other browser makers) is almost completely the result of overly intrusive tracking by advertisers. While Intelligent Tracking Prevention (combined with other browser privacy and security features) is the stick, privacy-preserving ad-click attribution is Apple’s carrot. Its method of monitoring clicks allows advertisers to track conversion rates without invading user privacy.
This privacy-preserving ad-click attribution is an upcoming feature of Safari (and a proposed Web standard) that enables the browser to remember ad clicks for 7 days. If a purchase is made within that time period, it is marked as a potential ad conversion. After a semi-random time delay to limit user identification, that conversion is then reported as a delayed ephemeral post to the search or advertising provider using a limited set of IDs that can’t be linked back to the actual user.
By building a privacy-preserving advertising technology into the second-most popular Web browser on the planet (Safari’s market share is about 15%, behind Google Chrome with 63%) and by making it an open standard, all while making Herculean efforts to block invasive forms of tracking, Apple is again leveraging its market position to improve privacy beyond its walls. What’s most interesting about the technology is that, unlike Sign in with Apple, it improves user privacy without completely disrupting the business model of Apple’s advertising-driven competitors like Google and Facebook. Those companies can use Apple’s technology and still track ad conversions, and Apple still supports user-manageable ad identifiers for targeted advertisements.
HomeKit Secure Video
As I said above, HomeKit Secure Video is another technology with which Apple is extending its privacy push. Coming in macOS 10.15 Catalina, iOS 13, and iPadOS, it provides HomeKit security cameras with a privacy-preserving update. I’m a heavy user of such cameras myself, even though they are only marginally useful at preventing crime. Nearly all home security camera systems, including my Arlo cameras, record their video directly to cloud-based storage (see “The HomeKit-Compatible Arlo Baby Security Cam Is Not Just for Parents,” 3 September 2018). Cloud storage is a feature you generally want in order to avoid the risk of having bad guys steal your security footage, as happens so often on popular crime shows. Security camera companies also use cloud processing to identify people, animals, and vehicles, and to offer other useful features. Like many customers, I’m not thrilled that these companies also have access to my videos, which is one reason none of their cameras run inside my home when anyone in my family is present.
HomeKit Secure Video will send encrypted video from supported cameras to iCloud, where it’s stored, for free, for 10 days without impacting your iCloud storage limits. If you have an Apple TV or iPad on your network, it will use that device for machine learning analysis and image recognition instead of performing any analysis in the cloud. This is an interesting area for Apple to step into: it certainly doesn’t seem like the sort of thing that would drive profits since Apple doesn’t sell its own cameras, and security camera support isn’t a motivator when customers decide to purchase a phone or tablet. It’s almost as though some Apple executives and engineers were personally creeped out by the lack of privacy protection for existing security camera systems and said, “Let’s fix this.”
HomeKit Secure Video opens the security video market to a wider range of competitors while protecting consumer privacy. It is a platform, not a product, and it eliminates the need for manufacturers to build their own back-end cloud service and machine learning capabilities. Companies using the platform will experience less friction when they bring a product to market, and it simultaneously allows them to provide better user privacy.
Apple Created a Culture of Privacy, but Will It Survive?
These are just a few highlights that demonstrate Apple’s extension of privacy beyond its direct ecosystem, but WWDC featured even more privacy-related announcements.
Apple continues to expand existing privacy features across all its platforms, including the new offline Find My device tracking tool (see “How Apple’s New Find My Service Locates Missing Hardware That’s Offline,” 21 June 2019). Having seen how some apps abuse Wi-Fi and Bluetooth data for ad hoc location tracking, Apple now blocks app access in iOS to such data unless it’s needed as a core feature. Users now can also track the trackers and see when even approved apps accessed their location.
Then there’s the upcoming Apple credit card, which is the closest thing we can get to a privacy respecting payment option. Even speech recognition is getting a privacy polish: developers will soon be able to mandate that speech recognition in their apps runs on-device, without ever being exposed to the cloud. In fact, Apple dedicated an entire WWDC session to examples of how developers can adopt Apple’s thinking to improve privacy within their own apps.
During John Guber’s The Talk Show Live, Craig Federighi said that Apple’s focus on privacy started back in its earliest days, when the company was founded on creating “personal” computers. Maybe it did, maybe it didn’t, but Apple certainly didn’t build a real culture of privacy (or any technical protections) until the start of the iPhone era. When Microsoft launched its highly successful Trustworthy Computing Initiative in 2002 and reversed the company’s poor security record, one of its founding principles was “Secure by Design.” During Apple’s developer-focused Platform State of the Union session, privacy took center stage as Apple talked about “Privacy by Design.”
Apple and other tech firms have already run into resistance when building secure and private devices and services. Some countries, including Australia, are passing laws to break end-to-end encryption and require device backdoors. US law enforcement officials have been laying the groundwork for years to push for laws that permit similar access, even while knowing it would then be impossible to guarantee device security (see “Apple and Google Spark Civil Rights Debate,” 10 October 2014). China requires Apple and other non-Chinese cloud providers to hand over their data centers to Chinese companies who can then feed information to the government. Apple’s competitors aren’t sitting by idly, with Google’s Sundar Pichai muddying the waters in a New York Times opinion piece that equates Google security with privacy, and positioning Apple’s version of privacy as a luxury good. While Google’s security is the best in the industry, equating that security with the kind of privacy that Apple offers is disingenuous at best.
The global forces arrayed against personal privacy are legion. Advertising companies and marketing firms want to track your browsing and buying. Governments want to solve crimes and prevent terrorism whatever the cost. Telecommunication providers monitor all our Internet traffic and locations, just because they can. The financial services industry is sure our data is worth something. And even grocery stores can’t resist offering minor discounts if you just let them correlate all your buying to your phone number. While, theoretically, we have a little control over some of this tracking, practically speaking we have essentially no control over most of it, and even less insight into how it is used. It’s a safe bet that many of these organizations will push back hard against Apple’s privacy promotion efforts, and, by extension, against any of us that care about and want to control our own privacy.
Calling privacy a fundamental human right is as strong a position as any company or individual can take. It was one thing for Apple to build privacy into its own ecosystem, but as it extends this privacy outside its ecosystem, we have to decide for ourselves if we consider these protections meaningful and worthy of support. I know where I stand, but I also recognize that privacy is a highly personal concept and I shouldn’t assume a majority of the world feels the same as I, or that Apple’s efforts will survive the challenges of the next decades.
It’s in our hands now.

 Josh Centers
No
comments
Josh Centers
No
comments
 Josh Centers
9
comments
Josh Centers
9
comments
 Josh Centers
1
comment
Josh Centers
1
comment
 Josh Centers
4
comments
Josh Centers
4
comments